Step by step, Russia blocks WhatsApp and now openly threatens to “completely block” the messaging app, accused of enabling terrorist plots, sabotage and large-scale fraud. Behind this offensive, the story goes far beyond a legal dispute between Roskomnadzor and Meta. Moscow actively tries to replace a global end-to-end encrypted messenger with a domestic ecosystem that authorities can fully monitor, centred on the Max superapp and the architecture of the Russian sovereign Internet.
Executive Summary — What “Russia blocks WhatsApp” really means
Quick read ≈ 4 min — Russia’s communications regulator Roskomnadzor now states that it may move towards a full ban on WhatsApp if the messenger does not comply with Russian laws against crime, terrorism and “extremism”.
Context — From tolerance to programmed rupture
For years, Moscow tolerated WhatsApp even after it labelled Meta (Facebook, Instagram) an “extremist organisation”. The app had become indispensable to the daily lives of tens of millions of Russians. However, as the Russian sovereign Internet takes shape, this compromise becomes less and less sustainable. The progressive blocking of calls, followed by the threat of a full ban, signals a shift towards an assumed incompatibility between global end-to-end encryption and Russia’s surveillance strategy.
Legal foundation — A framework designed for access to communications
At the same time, the laws on data localisation, the Yarovaya package and the Sovereign Internet law create a legal framework tailored for state access to communications. These texts require telecom operators and messaging services to hand over content, metadata and decryption capabilities to security services. By design, WhatsApp cannot decrypt users’ messages. Therefore, to appear “compliant” with Russian law, the app would have to weaken its security model (backdoors, client-side scanning) or effectively leave the Russian market.
Strategic principle — Replacing WhatsApp with the Max superapp
In parallel, Russia promotes a national alternative, Max, developed by VK and marketed as the “national messenger”. VK positions Max as a superapp that combines chat, payments and e-government services. The app does not offer verifiable end-to-end encryption. Consequently, the more difficult and risky WhatsApp becomes to use, the more Russians drift towards Max, where security services enjoy maximum visibility over data flows.
Sovereign stakes — From counter-terrorism to social control
Official Russian discourse now frames WhatsApp as a major vector for fraud, sabotage and terrorism. Yet Russian statistics still show that classic phone calls remain the leading fraud channel. Moreover, in a system where “extremism” covers opposition movements, NGOs and the LGBT community, asking WhatsApp to “exclude criminal activities” effectively means building a political police inside the messenger. The sequence “Russia threatens to completely block WhatsApp” therefore reveals a deeper strategic choice: replacing global encrypted services with controlled national solutions, and redefining digital sovereignty around surveillance rather than around encryption.
Reading Parameters
Executive summary: ≈ 4 min
Core analysis: ≈ 10–12 min
Full chronicle: ≈ 25–30 min
Publication date: 2025-11-29
Last update: 2025-11-29
Complexity level: Sovereign & Geopolitical
Technical density: ≈ 70%
Languages available: FR · EN
Main focus: Russia blocks WhatsApp, Roskomnadzor, Max, sovereign Internet, end-to-end encryption
Editorial type: Chronicle — Freemindtronic Cyberculture Series
Strategic impact: 8.4 / 10 — sovereignty & encrypted communications
Table of Contents
- Executive summary — What to remember
- Context — From Meta “extremist” to full-ban threat
- Legal framework — Data localisation, Yarovaya and sovereign Internet
- WhatsApp — End-to-end encryption and a technical dead end
- Programmed escalation — Telegram, Meta, then WhatsApp
- Max — Domestic superapp and WhatsApp replacement
- Fraud, terrorism, extremism — Official narrative vs reality
- Roskomnadzor — Technical and political hub of the Runet
- Prospective scenarios — What future for the Russian Internet?
- Weak signals — Balkanisation and control-oriented superapps
- Sovereign use case — Messaging outside jurisdiction
- Related content (Cyberculture & Tech Fixes)
- FAQ — Russia blocks WhatsApp, Max and the sovereign Internet
- What we did not cover
- Official sources and references
Key Insights — Main fault lines
- The sequence “Russia blocks WhatsApp” results from a gradual strategy: Yarovaya laws, sovereign Internet, Meta as “extremist”, then increasing pressure on encrypted messengers.
- Russia does not primarily reproach WhatsApp for failing to fight crime. Instead, the state sees the app as structurally incompatible with full state surveillance.
- The Max superapp plays the role of domestic replacement for WhatsApp, without verifiable end-to-end encryption, deeply integrated with payments and e-government services and supervised by the security apparatus.
- Official fraud statistics still show that traditional phone calls remain the main vector. This point relativises the narrative that presents WhatsApp as the primary problem.
- Serverless or keyless architectures — local HSMs (DataShielder NFC HSM, DataShielder HSM PGP) and self-hostable relay servers with no keys (CryptPeer) — offer an alternative where no state can demand a single exploitable central backdoor.
Context — How “Russia blocks WhatsApp” went from scenario to real threat
2022 — Meta labelled “extremist”, WhatsApp spared
In March 2022, shortly after the full-scale invasion of Ukraine, a Russian court declared Meta an “extremist organisation”. Authorities blocked Facebook and Instagram in Russia. However, one detail immediately attracted attention. The ruling explicitly stated that it did not apply to WhatsApp, which remained the main messaging app of the Meta group in Russia.
A messenger embedded in everyday life
At that time, WhatsApp permeated Russian society. Families, small businesses and local administrations relied on it. Schools, universities and some public services also used it to coordinate day-to-day information. A brutal ban would have disrupted the daily lives of millions of people. At that stage, no credible domestic alternative could fully replace the app.
The rise of the Russian sovereign Internet
Gradually, however, the technical and political context shifted. On one side, the architecture of the Russian sovereign Internet (Runet) took shape. Telecom operators deployed Deep Packet Inspection equipment and centralised routing capabilities. They also implemented technical mechanisms able to isolate the Runet from the wider Internet when the state decides to do so. On the other side, political discourse hardened around “information warfare”. Authorities increasingly invoked “extremism” and the fight against allegedly hostile foreign platforms.
2025 — From call restrictions to an explicit “Russia blocks WhatsApp” threat
On 13 August 2025, Russia crossed a new threshold in this gradual strategy. Roskomnadzor announced restrictions on audio calls via WhatsApp and Telegram. Officials justified the decision by referring to the fight against fraud and terrorism. Text messages remained technically possible. Nevertheless, in many regions, users already experienced a degraded service and unreliable voice calls.
A few months later, Roskomnadzor publicly mentioned the option of a complete ban on WhatsApp in Russia if the app did not adapt to Russian law. The regulator framed the situation as a binary choice. Either WhatsApp complies with Russian requirements on data and decryption, or it accepts disconnection from the Runet.
A political turn, not a simple technical incident
In other words, the phrase “Russia blocks WhatsApp” no longer describes a distant scenario. It now points to a political horizon that Russian authorities assume and openly discuss. In this context, it becomes important to analyse the legal foundation that makes this scenario plausible. That foundation also reveals the deeper logic behind the confrontation with WhatsApp and the trajectory chosen by the Russian state.
Legal framework — The laws that let Russia block WhatsApp
To understand why Russia can threaten a complete WhatsApp ban, we need to look at the legal architecture built over the past decade. This architecture rests on three complementary pillars.
Data localisation — Keeping personal data “within reach”
First, the data localisation law requires that Russian citizens’ personal data stay on servers located inside Russia. Services that refuse localisation face fines and, ultimately, blocking. Roskomnadzor maintains a list of offenders and orchestrates technical sanctions.
For a global messaging service like WhatsApp, this requirement already creates a serious constraint. The infrastructure of the app is distributed and designed for an Internet without hard borders. Forcing a strict separation between “Russian data” and “non-Russian data” means challenging the very design of the platform.
Yarovaya package — Mass storage and decryption obligations
Next comes the Yarovaya package, adopted in 2016. It requires telecom operators and “organisers of information distribution” to:
- store the content of communications for several months,
- retain metadata for a longer period,
- and, crucially, provide security services with the means to decrypt communications, including handing over encryption keys.
In plain language, any messenger used at scale in Russia must at least in theory deliver the content of conversations in cleartext when authorities request it. This requirement collides directly with genuine end-to-end encryption, where the provider holds no decryption keys.
Sovereign Internet — DPI and central control over the Runet
Finally, the Sovereign Internet law completes the framework:
- ISPs must install Deep Packet Inspection (DPI) equipment under Roskomnadzor’s control;
- the state can redirect, filter, throttle or cut specific services;
- the Russian Internet segment (Runet) can be isolated from the global network in case of crisis or political decision.
Taken together, these three pillars (“data localisation”, “Yarovaya”, “sovereign Internet”) converge towards a model where, on paper, no mass communication service remains out of reach. This applies to hosting, to encryption and to network routing.
Within such a normative universe, a global messenger with end-to-end encryption like WhatsApp becomes a legal and technical anomaly. This anomaly largely explains why the sequence “Russia blocks WhatsApp” does not simply reflect a passing mood. Instead, it expresses a deep conflict between two philosophies of encryption.
WhatsApp — End-to-end encryption at the heart of the “Russia blocks WhatsApp” conflict
A technical model built around end-to-end encryption
Once we understand the legal framework, we can return to WhatsApp’s technical model. The messenger relies on end-to-end encryption (E2EE). Concretely:
- the app encrypts messages on the sender’s device;
- only the recipient’s device can decrypt them;
- Meta has no direct access to cleartext content, only to metadata.
A Russian demand incompatible with WhatsApp’s design
We can now compare this model with Russian legal requirements. In an E2EE system, laws that demand providers to submit keys or plaintext content cannot be satisfied without a deep redesign of the service. The tension does not simply come from political refusal. It arises from a design incompatibility between the messenger and the Russian legal environment.
Three theoretical outcomes for WhatsApp in Russia
To become compliant with Russia, WhatsApp only sees three realistic options:
- Introduce a backdoor or client-side scanning. In this scenario, the app would scan messages on the device before encryption, detect prohibited content or behaviour and send reports to servers that authorities can query.
- Abandon end-to-end encryption for all or part of Russian users. The service would then revert to a model where servers can read messages and hand them over to security services.
- Refuse and accept a full ban, thereby becoming a niche app mainly used via VPNs and technical workarounds.
Two irreconcilable models of sovereignty over communications
So far, Meta publicly defends E2EE as essential for protecting private communications. As a result, the phrase “Russia blocks WhatsApp” functions less as a rhetorical threat and more as a collision point between two security models. One model treats encryption as a strong shield, including against states. The other rejects the idea that a mass-market service might escape state surveillance.
From this point on, it becomes useful to place this impasse within a clear timeline. That timeline retraces Russia’s previous attempts to control encrypted messengers.
Programmed escalation — Telegram, Meta, then WhatsApp
To gauge the significance of the current threat, we must look back at previous episodes and see how they prepare the ground.
Attempted Telegram ban (2018–2020)
In 2018, Russian authorities tried to block Telegram after the company refused to hand over encryption keys. Roskomnadzor ordered the blocking of millions of IP addresses, including infrastructure that belonged to Amazon and Google. Collateral damage proved massive, while Telegram remained largely accessible through mirrors and circumvention tools. In 2020, the regulator officially abandoned the ban.
This failed attempt revealed two important lessons. First, without a fully operational sovereign Internet, blocking a popular messenger remains technically difficult and politically costly. Second, regulatory pressure alone does not suffice when the state lacks a credible alternative platform to propose.
Meta as “extremist”, WhatsApp tolerated (2022)
In 2022, Russia took a new step by declaring Meta an “extremist organisation”. Authorities blocked Facebook and Instagram. Yet the court ruling explicitly spared WhatsApp. This choice reflected a form of pragmatic realism: target social networks that the Kremlin viewed as politically sensitive, while preserving the messenger that much of the population relied on.
Sovereign Internet, legal hardening and call restrictions (2024–2025)
Between 2024 and 2025, the landscape changed again. DPI equipment became widespread. The notion of “extremism” broadened. New provisions criminalised even the online search for content branded “extremist”. In parallel, lawmakers increasingly targeted the use of VPNs to access such content.
On 13 August 2025, Roskomnadzor announced targeted restrictions on audio calls via WhatsApp and Telegram, once again justified by “anti-fraud” and “anti-terrorism” arguments. In practice, voice communications deteriorated to the point of becoming unusable in many areas, while text messages continued to function.
A few months later, the threat of a full WhatsApp ban in Russia entered the public debate. Consequently, the sequence “Russia blocks WhatsApp” does not fall from the sky. It extends a gradual escalation, technically prepared and politically deliberate.
This escalation only makes sense because, in parallel, a domestic alternative was already under construction: the Max superapp, designed to replace WhatsApp within the Russian sovereign Internet ecosystem.
Max — Domestic superapp and WhatsApp replacement
An “all-in-one” superapp at the heart of the Runet
As Russia turns up the pressure on WhatsApp, another key piece already sits on the board. This is the Max superapp, developed by VK Group and promoted as the “national messenger”.
VK presents Max as an “all-in-one” application:
- one-to-one and group messaging;
- payments, digital wallet and transfers;
- access to selected government services (Gosuslugi);
- planned integration with digital identity and electronic signatures.
Limited encryption and structural compatibility with the sovereign Internet
Two features weigh heavily in the balance. The first concerns encryption.
Public information and independent analyses indicate that Max does not provide verifiable end-to-end encryption. At best, the app encrypts traffic in transit. In practice, the operator can still read messages and deliver them to authorities when required. This design makes the superapp structurally compatible with the requirements of the Russian sovereign Internet.
Mandatory pre-installation and growing dependency
The second feature concerns distribution. From 1 September 2025, Russian regulations require Max to be pre-installed on all smartphones and tablets sold in the country. At the same time, several administrations already encourage or impose its use for communication with parents, schools and public services. Step by step, Max becomes a compulsory gateway to digital everyday life.
From WhatsApp to Max — An assumed substitution strategy
In this context, the phrase “Russia blocks WhatsApp” does not simply describe a punitive measure. It forms part of a broader substitution strategy.
The more painful or risky the use of WhatsApp becomes, the more Max imposes itself as the default channel. It turns into the unavoidable hub to communicate, pay and interact with the state. As a result, the potential WhatsApp ban and the rise of Max reinforce each other.
This dynamic forces analysts to examine Moscow’s narrative that justifies this shift — fraud, terrorism, extremism. Understanding that discourse helps to see how the sequence “Russia blocks WhatsApp” also serves a wider project of social control.
Fraud, terrorism, extremism — Official narrative vs reality
An official storyline centred on fraud and terrorism
In its press releases, Roskomnadzor claims that WhatsApp and Telegram have become central tools for:
- mass fraud and financial scams;
- recruitment for terrorism and sabotage;
- coordination of criminal actions and “extremism”.
At first glance, this narrative appears consistent with public-security concerns. However, official data paint a more nuanced picture.
The Central Bank of Russia tells a different story
Reports from the Central Bank of Russia highlight another reality. They show that:
- traditional phone calls still represent the main fraud channel;
- encrypted messengers remain only one vector among many;
- restrictions on WhatsApp/Telegram calls mainly triggered a rebound in classic voice traffic rather than eliminating fraud.
In other words, the “fraud” angle operates as a legitimising narrative at least as much as a technical justification. This gap opens the way to a second, more political shift.
An ever-expanding definition of “criminal behaviour”
At the same time, constant references to “criminal activities” and “extremism” play a structuring role. By 2025, these categories in Russia cover:
- organisations linked to Alexei Navalny, labelled “extremist” and then “terrorist”;
- the international LGBT movement, classified as an extremist organisation;
- numerous NGOs, independent media and human-rights organisations;
- many anti-war expressions and criticisms of the army.
Gradually, the boundary between actual criminality and political dissent becomes blurred. The language of criminal law then reshapes public space instead of merely addressing precise offences.
From anti-fraud measures to an embedded political police
Within this context, demanding that WhatsApp “exclude criminal activity” means several concrete things:
- proactively censoring conversations on sensitive topics;
- identifying people who participate in these exchanges;
- and sending data to the relevant security agencies.
An end-to-end encrypted messenger cannot deliver this programme without sacrificing its security model. Adding such functions would effectively turn the app into a tool for political surveillance.
Therefore, the sequence “Russia threatens to completely block WhatsApp” acts as a revealing moment. The state asks a global tool to become an embedded political-police device, which WhatsApp neither can nor wants to be. This observation leads directly to Roskomnadzor’s pivotal role as legal enforcer, technical orchestrator and official narrator of the confrontation.
Roskomnadzor — Technical and political hub of the Runet
A regulator at the core of the sovereign Internet
To understand Roskomnadzor’s role, we must look at its operational responsibilities. The agency cumulates several key functions within the Russian sovereign Internet:
- it maintains the central blocklist of sites and online services subject to restriction;
- it monitors compliance with data localisation obligations;
- it supervises the roll-out of DPI equipment at ISPs;
- it coordinates throttling or cut-off operations on foreign services (social networks, VPNs, video platforms, analytics tools, etc.).
In other words, Roskomnadzor does not merely issue rules. It also orchestrates their technical enforcement within the Runet’s infrastructure.
Technical arm of a progressive Runet lockdown
In the official narrative, Roskomnadzor acts to “protect citizens” and ensure “infrastructure stability”. In practice, however, it has become the technical arm of a policy aimed at progressively locking down the Runet. Its statements on WhatsApp therefore carry significance far beyond the messaging app itself. They signal the overall direction of Russian digital policy.
The threat of a full ban as strategic signalling
The threat of a full WhatsApp ban illustrates this signalling role particularly well. It fits into a coherent pattern of actions and messages:
- pressure on foreign services that the state labels as “non-cooperative”;
- active promotion of the Max superapp as a “patriotic” alternative;
- constant reminders of data-sharing, localisation and decryption obligations.
Each statement by Roskomnadzor therefore goes beyond a warning to a single platform. It contributes to redefining what remains tolerated within the Russian digital space.
A triptych that redefines freedom of communication
The triptych “Russia blocks WhatsApp”, “Max as national superapp” and “sovereign Internet” sketches a new model. Under this model, freedom of communication becomes conditional on alignment with the surveillance architecture. Mass-market messengers appear legitimate only if they fully integrate into this control framework.
The next step consists in projecting this model into the future through several realistic scenarios. These scenarios help evaluate how far Runet lockdown and the marginalisation of global encrypted services might go.
Prospective scenarios — What future for the Russian Internet?
Starting from the current situation, we can outline several realistic trajectories for the relationship between Russia, WhatsApp and the sovereign Internet.
Scenario 1 — Progressive de facto ban
In the first scenario, the state does not announce a brutal “ban”. Instead, authorities organise a slow erosion of WhatsApp usage.
- call restrictions remain in place for the long term;
- file transfers are throttled or intermittently disrupted;
- new accounts sometimes struggle to register;
- official discourse describes the service as “unreliable” or “dangerous”.
In such a scenario, WhatsApp does not fully disappear from the Runet, but its use concentrates among:
- more tech-savvy users, able to manage VPNs and circumvention tools;
- cross-border communications with the diaspora and foreign partners.
Consequently, “Russia blocks WhatsApp” becomes a day-to-day reality without a single spectacular decision. At the same time, Max automatically gathers mass-market users.
Scenario 2 — Opaque deal with client-side surveillance
The second scenario revolves around a discreet compromise. WhatsApp remains accessible in Russia, but only at the price of client-side scanning or specific integrations.
For example, authorities could demand:
- automatic analysis of selected content on the device before encryption;
- mandatory reporting of patterns associated with “extremism” or fraud;
- enhanced logging of metadata for domestic security agencies.
This trajectory would not formally break end-to-end encryption, yet it would seriously weaken its substance. Security would then depend less on cryptography and more on the integrity of control mechanisms imposed by the Russian state.
Scenario 3 — Assumed rupture and a full WhatsApp ban in Russia
The third scenario involves an openly total rupture with WhatsApp.
- the state blocks the messenger at network level;
- using VPNs to access it becomes criminalised or treated as suspicious behaviour;
- Max becomes the near-exclusive entry point for everyday communication, e-government and part of the payment ecosystem.
In this configuration, the Runet looks increasingly like a state intranet. Data flows are filtered, global services are replaced by local equivalents, and the remaining pockets of real encryption move to marginal, high-risk niches.
Whatever the scenario, one open question remains. How can encryption sovereignty survive when the messaging infrastructure lies under the control of a state that rejects the very idea of opacity? At this point, sovereign architectures outside mainstream platforms become crucial.
Weak signals — Balkanisation and control-oriented superapps
Weak-signals block
1. Accelerated Balkanisation of the Internet — Russia’s trajectory reinforces a vision of the Internet split into spheres (Russia, China, Western bloc, etc.), each with its own platforms, “sovereign clouds” and surveillance rules. The sequence “Russia blocks WhatsApp” now serves as a textbook case of this Balkanisation.
2. Superapps as state-control vectors — After WeChat in China, Max in Russia illustrates a model where a single app concentrates messaging, payments, e-government and identity. The more central the superapp becomes, the broader the surface for state control grows.
3. Permanent security narrative — Anti-fraud, child protection, counter-terrorism: these themes, legitimate in themselves, increasingly act as rhetorical levers to challenge end-to-end encryption and to normalise backdoors.
4. Fault lines around encryption — The encryption issue no longer concerns authoritarian regimes only. Several democracies now debate “lawful access” and “exceptional access” backdoors. These debates provide rhetorical ammunition to states that want to go significantly further.
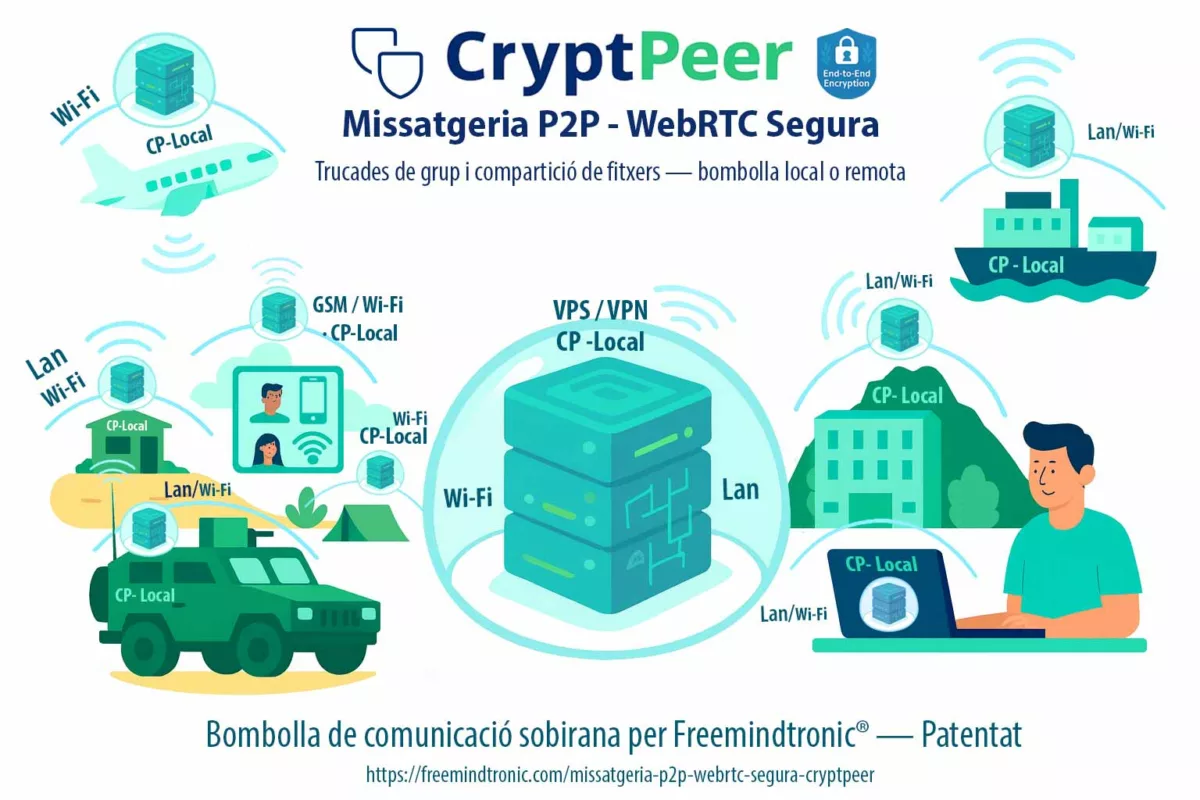
5. Strategic role of off-platform solutions — As global messengers become trapped between states with conflicting demands, off-jurisdiction solutions based on local encryption gain importance: serverless models (DataShielder NFC HSM, DataShielder HSM PGP) and models with a self-hostable relay server that never holds keys (CryptPeer). In both cases, the server cannot decrypt messages, which radically changes the balance of power.
In the background, these weak signals suggest that answering the formula “Russia blocks WhatsApp” cannot remain a narrow debate about messengers. It must address the design of encryption architectures at the level of states, organisations and individuals.
Sovereign use case — Protecting messages beyond any future “Russia blocks WhatsApp” scenario
A textbook case: when the state controls the messenger and can block WhatsApp
Ultimately, the sequence “Russia blocks WhatsApp” raises a broader question. What happens when a state demands that a messaging provider hand over content, metadata or encryption keys? As long as security depends on a central platform, that platform becomes the obvious pressure point. It concentrates technical, legal and economic leverage.
In a centralised model:
- even encrypted messaging relies on servers and infrastructure that a state can compel;
- the provider may face pressure to add exceptions, backdoors or client-side scanning mechanisms;
- users do not control where their data resides or how it flows across borders.
In short, the promise of encryption remains fragile if the root of trust stays concentrated in a single actor.
Reducing trust in platforms with segmented-key HSMs
Architectures like DataShielder and CryptPeer start from a different premise. They aim to minimise the trust placed in platforms and networks, and to move the root of security as close as possible to the user.
- DataShielder NFC HSM and DataShielder HSM PGP: there is no decryption server and no central database. The system can operate 100% offline, without cloud or account. A hardware HSM (NFC HSM or HSM PGP) performs encryption. Keys (AES-256, RSA-4096 depending on the use case) are generated and stored locally. A system of segmented keys splits trust between the Main Operator and module holders.
- CryptPeer: end-to-end encryption occurs at the peers. A self-hostable, self-portable relay server only receives already encrypted data. It holds no encryption or decryption keys. The server simply forwards packets and cannot read content or reconstruct secrets shared between peers.
Encryption encapsulation — One encrypted message inside another
Even when users continue to rely on a mainstream messenger such as WhatsApp or Telegram, they can shift the balance by using encryption encapsulation.
Concretely:
- the user encrypts sensitive content locally inside an NFC HSM (for example, DataShielder NFC HSM);
- what travels through WhatsApp appears only as an opaque encrypted block;
- even if the messenger or network becomes compromised, the attacker sees nothing more than “encryption inside encryption”.
From a state’s perspective, demanding keys from the messenger provider then becomes ineffective. Critical keys are not held by that provider. They reside in sovereign hardware HSMs or cryptographic pairs managed at peer level, as with CryptPeer. Meanwhile, the relay server only sees encrypted data it cannot open.
Encryption sovereignty beyond WhatsApp and Max
In a world where “Russia blocks WhatsApp” may become a precedent, these architectures serve as demonstrators. They show that it is possible to:
- keep using mainstream messengers for ergonomics;
- make data structurally unusable without the HSM or peer key, even in case of seizure or blocking;
- remain compliant with export-control frameworks for dual-use encryption goods, such as the one that applies to DataShielder in Europe.
In other words, real sovereignty does not boil down to a choice between WhatsApp and Max. It lies in the ability to design systems where neither Moscow nor any other state can demand an exploitable central backdoor. This boundary separates nominal security from true operational encryption sovereignty.
Related content
To be linked with other Freemindtronic chronicles and publications
- https://freemindtronic.com/digital-security-articles-freemindtronic/ — Collection of strategic chronicles on digital security.
- https://freemindtronic.com/cyberculture-a-collection-of-articles/ — Cyberculture and geopolitical shifts of the Internet.
- https://freemindtronic.com/technical-news/ — Technical and cryptographic news related to Freemindtronic products.
- https://freemindtronic.com/tech-fixes-security-solutions/ — Technical counter-espionage and resilience solutions.
FAQ — Russia blocks WhatsApp, Max and the sovereign Internet
Frequently asked questions about “Russia blocks WhatsApp”
A clash between end-to-end encryption and the sovereign Internet
The threat of a complete WhatsApp ban does not operate as a simple one-off political gesture. Instead, it stems from a structural clash between, on one side, a end-to-end encrypted messenger that Meta cannot decrypt and, on the other, a Russian legal framework (data localisation, Yarovaya law, sovereign Internet) that expects communication services to hand over content and decryption capabilities to authorities.
As long as WhatsApp maintains its E2EE security model, it remains structurally non-compliant with Moscow’s expectations. This position makes the threat of a ban logical within the doctrine of the Russian sovereign Internet.
Partial restrictions today, threat of a full ban tomorrow
At this stage, Russia already restricts audio calls on WhatsApp (and on Telegram), which seriously degrades everyday use of the messenger. Text messages remain accessible for most users, but the threat of a “complete ban” now appears explicitly in Roskomnadzor’s statements.
In practice, Russia is moving towards a scenario where:
- “normal” WhatsApp use becomes increasingly difficult;
- key features such as calls and large file transfers are targeted first;
- remaining use concentrates among people able to handle VPNs and workarounds, with growing legal risks.
Max, domestic superapp and pivot of Russia’s sovereign Internet
Max, developed by VK, is promoted as the national messenger. It does much more than simply replicate WhatsApp:
- it combines messaging, payments, digital wallet and access to some government services;
- it is pre-installed on smartphones sold in Russia and pushed by public bodies;
- it does not provide verifiable end-to-end encryption, which makes it compatible with the sovereign Internet framework.
By progressively making WhatsApp more difficult to use, the state creates a trap effect. Citizens who want to keep communicating and interacting with public services are strongly incentivised to move to Max, where state visibility is maximal.
VPNs, circumvention and the rising risk of criminalisation
Technically, any WhatsApp ban can be partly bypassed using VPNs, proxies and anti-censorship tools. However, Russian authorities now deploy DPI capabilities that allow them to detect and disrupt some VPN traffic. In addition:
- accessing banned content and using blocked services can be treated as suspicious behaviour;
- recent laws already target the search for “extremist” content online;
- legal and technical pressure is likely to increase against VPN providers themselves.
Therefore, circumvention remains technically possible, but it becomes increasingly risky and uncertain from a legal and operational standpoint, especially in an environment where “extremism” receives a very broad definition.
From simple regulation to the power to cut, filter and isolate
Most states regulate the Internet: data protection, crime fighting, platform oversight. The Russian sovereign Internet goes further by combining:
- forced localisation of data and large-scale storage of communications;
- deployment of Deep Packet Inspection equipment at ISPs, under Roskomnadzor’s control;
- the legal and technical capacity to isolate the Runet from the global Internet upon political decision.
This evolution moves from regulation to a real-time intervention capability on traffic, services and architectures. It offers enough leverage to de facto invalidate security models such as large-scale end-to-end encryption.
Local encryption, HSMs and keyless relay servers
When the messaging infrastructure is controlled by the state, confidentiality cannot rely solely on a provider’s goodwill. Two major families of architectures stand out:
- No decryption server models such as DataShielder NFC HSM and DataShielder HSM PGP: a hardware HSM performs encryption, without cloud or central database. Keys are generated and stored locally, using segmented keys, which makes it impossible to hand over a single “master key” to any state.
- Keyless relay server models such as CryptPeer: peers encrypt directly between themselves. A self-hostable, self-portable relay server only forwards already encrypted traffic, without holding any encryption or decryption keys. Even if the server is seized, contents remain unusable.
These designs do not remove the need to comply with local laws, but they show that engineers can build systems where no central entity holds all keys. This choice drastically limits the impact of political pressure on a single provider.
A global fault line around encryption
No. While the “Russia blocks WhatsApp” sequence looks particularly stark, the encryption debate already extends far beyond authoritarian regimes. In several democracies, policymakers periodically advocate “lawful access” backdoors or “exceptional access” to encrypted messaging for counter-terrorism or child protection.
The Russian case acts as a magnifying mirror. It shows how far a state can go when it controls a sovereign Internet, domestic superapps and a permanent security narrative. It also reminds us that, once societies accept the principle of a backdoor, the boundary between legitimate and political uses becomes extremely difficult to define.
What we did not cover
This chronicle focuses on the “Russia blocks WhatsApp” sequence, the legal and technical architecture of the Russian sovereign Internet, the rise of Max and sovereign encryption architectures.
It deliberately leaves aside several dimensions that could justify dedicated chronicles:
- a detailed map of the global superapp ecosystem and their governance models (WeChat, Max, future superapps in other geopolitical zones);
- a fine-grained comparison of legal frameworks on encryption (Europe, United States, Russia, China) and their possible convergence around the idea of “lawful” backdoors;
- an operational analysis of Russian DPI capabilities (equipment types, vendors, crisis-time scenarios);
- a deeper exploration of overlay-encryption strategies (DataShielder, CryptPeer, other serverless or keyless models) tailored to an increasingly fragmented Internet.
These topics can be developed in future Cyberculture chronicles, with a specific focus on operational encryption sovereignty in a Balkanised Internet.
Official sources and references
- “Yarovaya” laws — Federal Laws No. 374-FZ and 375-FZ of 06.07.2016, official text (Russian) on the Russian legal portal: http://pravo.gov.ru; English overview: https://en.wikipedia.org/wiki/Yarovaya_law
- Federal Law No. 90-FZ on the “sovereign Internet” (amending the communications and information laws) — official text available via the legal portal: http://pravo.gov.ru; comparative analyses in NGO reports (Access Now, Human Rights Watch).
- Roskomnadzor releases on WhatsApp, Telegram and Max (call restrictions, potential full ban, promotion of Max as national messenger): https://rkn.gov.ru
- Central Bank of Russia — data on fraud and financial losses linked to social-engineering attacks and communication channels (official reports and statistical bulletins): https://www.cbr.ru
- Court decision classifying Meta as an “extremist organisation” and explicitly excluding WhatsApp from the ban — documents and releases from the Russian Prosecutor General’s Office: https://genproc.gov.ru, with additional context from international press coverage.
- Analyses of the Max superapp and its role within the Russian sovereign Internet — Russian specialised media and digital-sovereignty observatories (e.g. reports by journalists and NGOs, financial press analysis).