The Technical Guide will be updated to take into account technological developments related to computer systems.
The Freemindtronic App is able to communicate with a computer to share the data stored on the NFC device. More specifically, a browser extension is installed on your computer. This communication between the smartphone and the computer is local and do not pass through any remote servers.This is our choice to protect the user’s privacy and security. However, this leads to an increase of complexity for the user. Indeed, he now needs to discover the communication between two devices on the same network.
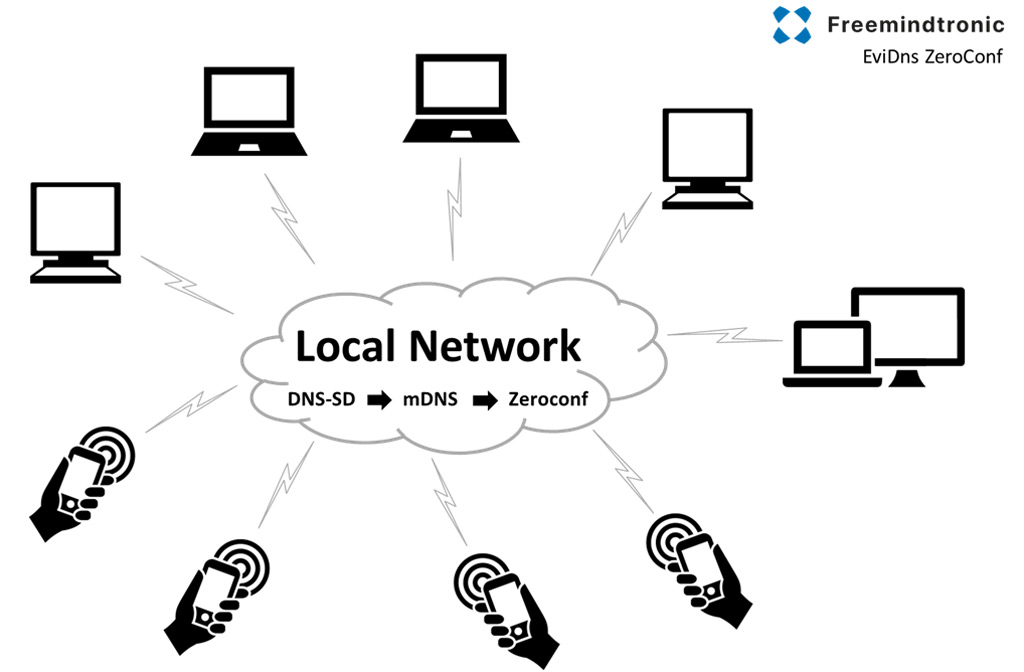
Let’s talk about service discovery. The Freemindtronic application provides an API for other devices to communicate with. Futhermore, each device on the network has a unique IP address. Communication between two devices is only possible if each device knows each other’s IP address. Two technologies are implemented in the extension for discovery of smartphone IP address with a running Freemindtronic application. The first one is called IP scan and the second, EviDNS.
IP scan is a simple way to discover compatible devices on the network. It simply puts all local IP’s of your network in a loop to fetch device’s information. This is similar to a brute force IP scan.
EviDNS is a less network intensive solution. It works by installing a specific software on your computer. This allows mDNS discovery of local services. For more information about mDNS, please visit: https://en.wikipedia.org/wiki/Multicast_DNS.
By default, the extension automaticaly chooses EviDNS if available and IP scan if not. It is possible to choose the technology wanted in the extension settings.