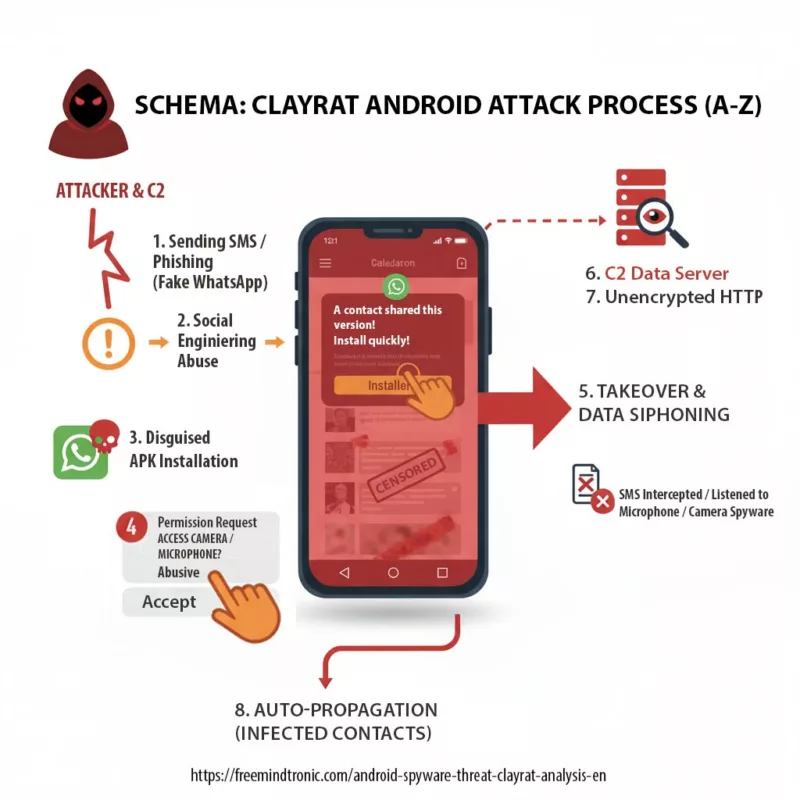
Louvre security weaknesses: a cyber-physical blind spot that points to sovereign offline authentication as a cost-effective lever for museum safety. This piece connects the 2014 findings, the 2024 budget snapshot, and a 100% offline remediation path—under €96 incl. VAT / computer / year for 2,100 staff, using passwordless museum security, RAM-only HSM, and an offline-first doctrine.
🏛️ Louvre Security Weaknesses: ANSSI findings, tiny costs, sovereign offline fix < €96/seat/year
In 2014, ANSSI’s IT audit of the Musée du Louvre uncovered glaring vulnerabilities: weak/default passwords (LOUVRE, THALES) on safety systems, outdated operating systems, and plausible internal attack surfaces. Resurfacing through media investigations and international coverage, these issues return to the spotlight after the October 2025 heist and the public report from the Cour des comptes released on November 6, 2025.
Quick take — What to remember
- 2014: ANSSI audit — trivial passwords (
LOUVRE,THALES), unpatched software, Windows 2000/XP hosts. Reported via press reviews citing documents consulted by CheckNews. - 2025: the Cour des comptes confirms major delays: in 2024, only 39% of rooms had cameras; upgrades stretch to 2032.
- 2024 budgets: public accounts and RA2024 indicate room to fund a sovereign rollout at <0.2% of operating revenue — order of magnitude: < €96 incl. VAT / seat / year for 500–800 seats.
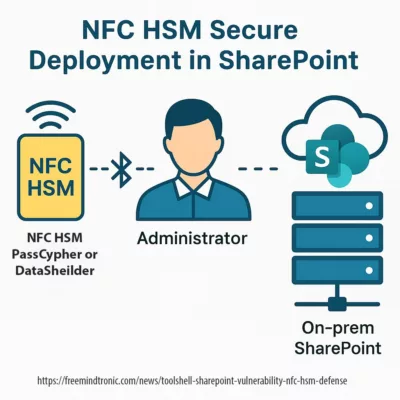
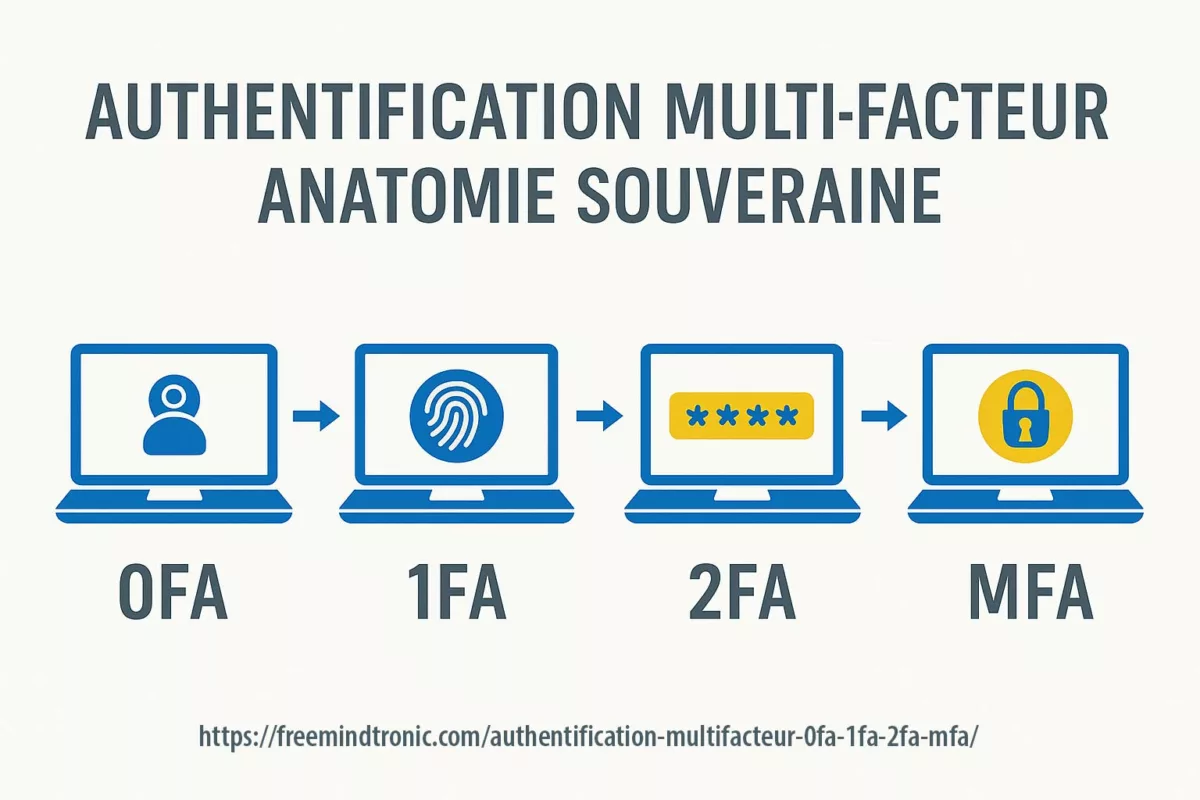
- Sovereign response: offline passwordless deployment (proof of possession, RAM-only), no cloud or database, interoperable with legacy fleets (including Windows XP/2000).
- Recognition: the PassCypher ecosystem is a Finalist for the Intersec Award 2026 — Best Cybersecurity Solution 2026.
Reading parameters
Quick take : ≈ 4 minutes
Extended summary: ≈ 6 minutes
Full chronicle : ≈ 35–40 minutes
Publication date: 2025-11-08
Last update: 2025-11-08
Complexity level: Advanced — Governance, sovereignty & digital security
Technical density: ≈ 78%
Languages available: FR · EN · CAT · ES · AR
Topical focus: Digital sovereignty, museum security, ANSSI audit & offline authentication
Suggested reading order: Quick take → Paradox → ROI → Doctrine → Outlook
Accessibility: Screen-reader optimized — anchors & structured tags
Editorial type: Security Chronicle — Freemindtronic Sovereign Insight
Risk level: 7.9 / 10 — institutional, heritage, strategic
About the author — Jacques Gascuel, founder of Freemindtronic Andorra, invented PassCypher, the first 100% offline hardware authentication solution. A specialist in sovereign HSMs, he focuses on access security and resilience of critical systems.
Louvre security weaknesses — the posts shown above ↑ belong to the same editorial section, Awards & distinctions — Digital Security. They extend the analysis of sovereignty, Andorran neutrality, and offline secrets management, directly tied to PassCypher’s Intersec Dubai recognition and to passwordless museum security with an offline-first, RAM-only HSM approach.
Advanced Summary — ANSSI Louvre Audit: facts, figures, and sovereign doctrine
Established facts: the ANSSI audit (2014) identified elementary failures (passwords, obsolete OS). International media summarized these points, citing documents reviewed by CheckNews. In 2025, the Cour des comptes published a damning report: limited video coverage (39% of rooms in 2024) and safety investments delayed until 2032.
| Vector | Finding | Sovereign Measure |
|---|---|---|
| Default passwords | Safety access (LOUVRE, THALES) |
Eliminate passwords entirely; proof of possession |
| OS obsolescence | Windows 2000/XP in 2014 (press recaps) | Offline authentication independent of the OS |
| Cloud dependencies | Server/browser chains | Air-gap; zero persistence; RAM-only |
1) The flaw is governance, not budget;
2) A serverless model fixes faster;
3) The XP/2000 legacy is handled via offline first.
Full chronicle — Weaknesses, figures, and a sovereign remediation
This chapter traces the technical weaknesses identified by the 2014 ANSSI audit of the Louvre, their media reappearance in 2025, and the official sources that document the security posture and budget latitude for remediation. It links the vulnerability findings, consistent press coverage, and the sovereign, passwordless authentication frameworks.
ANSSI Louvre Audit (2014) — weaknesses and verifiable recaps
In 2014, ANSSI auditors uncovered high-risk practices at the Musée du Louvre:
- Trivial passwords (
LOUVREfor video surveillance;THALESfor an associated application) - Unpatched workstations, obsolete OS (Windows 2000/XP)
- Lack of technical governance and server dependency
These points were echoed and corroborated by tech and mainstream outlets, citing documents reviewed by CheckNews / Libération.
⮞ Summary — Governance before tooling: remove shared identifiers and server dependency.
Official sources — primary evidence
- Cour des comptes — Public report “Établissement public du musée du Louvre” (Nov 06, 2025, PDF, 128 p.):
Download the report - Cour des comptes — Official summary (PDF):
Read the summary - Musée du Louvre — Activity Report 2024 (official annexes) (PDF):
RA2024 — Annexes - Musée du Louvre — Institutional page “Our missions”:
Access the reports
Standards & reference frameworks (authentication)
- NIST — SP 800-63B Digital Identity Guidelines:
View the standard - ISO/IEC — 29115 (Entity Authentication Assurance Framework):
ISO official page - Microsoft — Passwordless authentication methods (official Entra docs):
See the docs
Serious coverage (corroborating ANSSI 2014 elements)
- Tom’s Hardware — summary of weaknesses:
Read the article - ArtNews — “THALES” password:
Read the article - Snopes — fact-check on the “LOUVRE” password:
Read the analysis
Budget paradox in the ANSSI Louvre Audit: securing for less than 0.2% of revenue
The 2024 public accounts published by the Cour des comptes indicate a consolidated turnover of €137.2 million for the Louvre public institution, with a positive accounting result of €19 million (RA 2024). For a fleet estimated at 500–800 workstations, deploying a sovereign hardware solution at under €96 incl. VAT per seat per year would represent less than 0.12% of the museum’s annual profit—a negligible expense given the strategic protection stakes. In other words, financial sustainability is unquestioned; what’s missing is technical and doctrinal execution. The question is no longer “what does it cost,” but “what does inaction cost.”
According to the Freemindtronic study, employees lose on average over 11 hours per year managing credentials (entry, resets, session loss).
Across an organization of 2,100 staff, that lost time equals over €300,000 in hidden costs per year.
Implementing sovereign offline authentication—passwordless, serverless, no IT support—turns this invisible spend into immediate productivity gains.
In short: sovereignty reduces both cyber risk and the human cost of security.
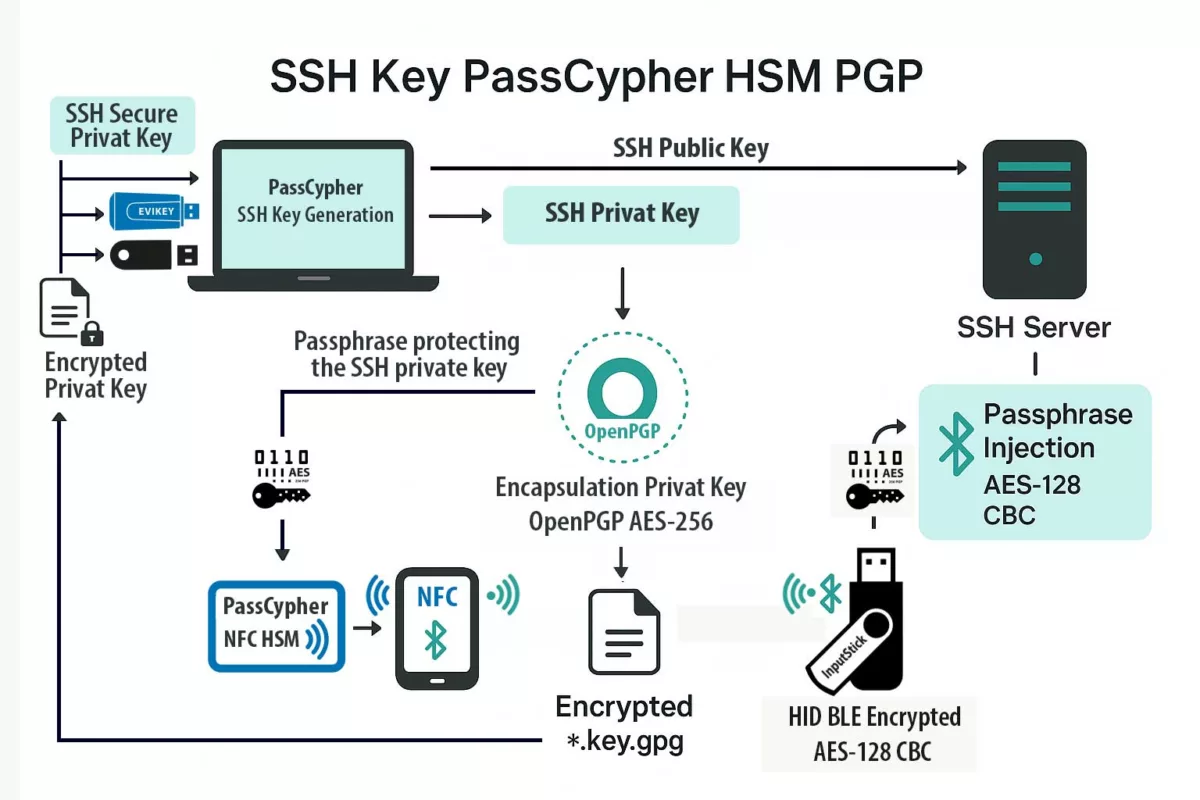
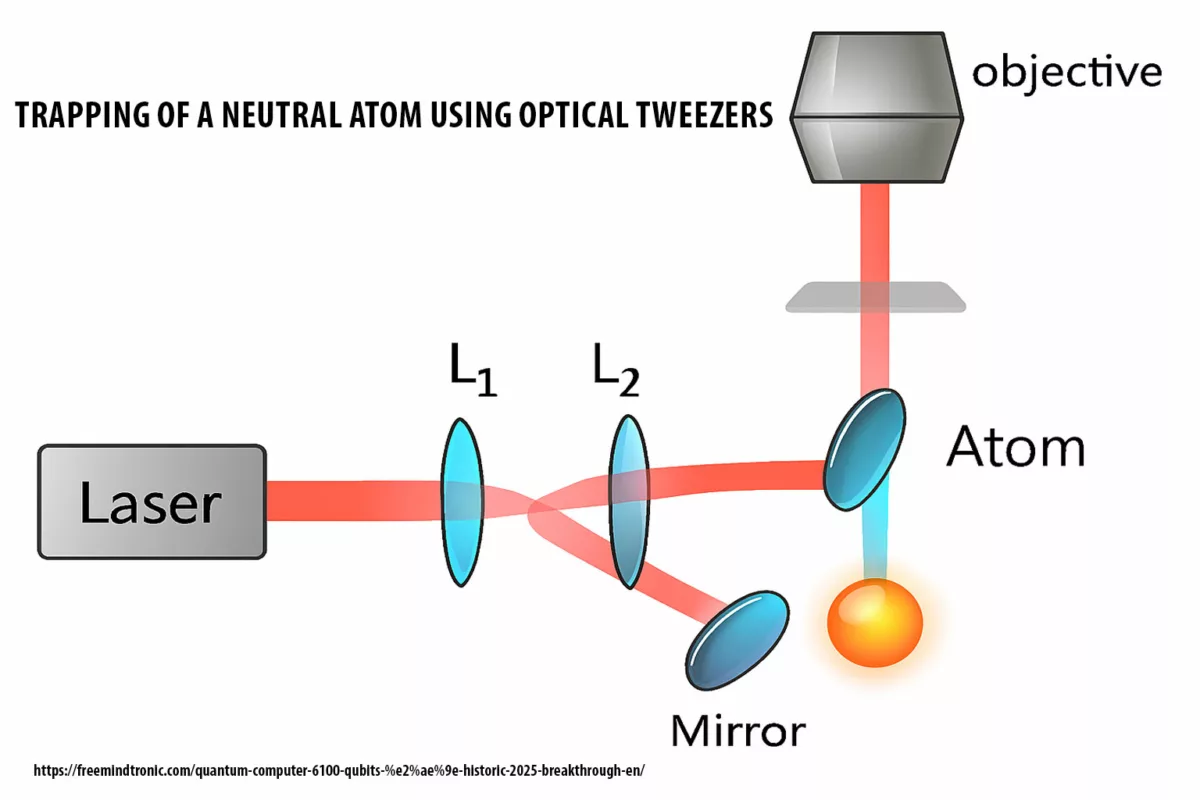
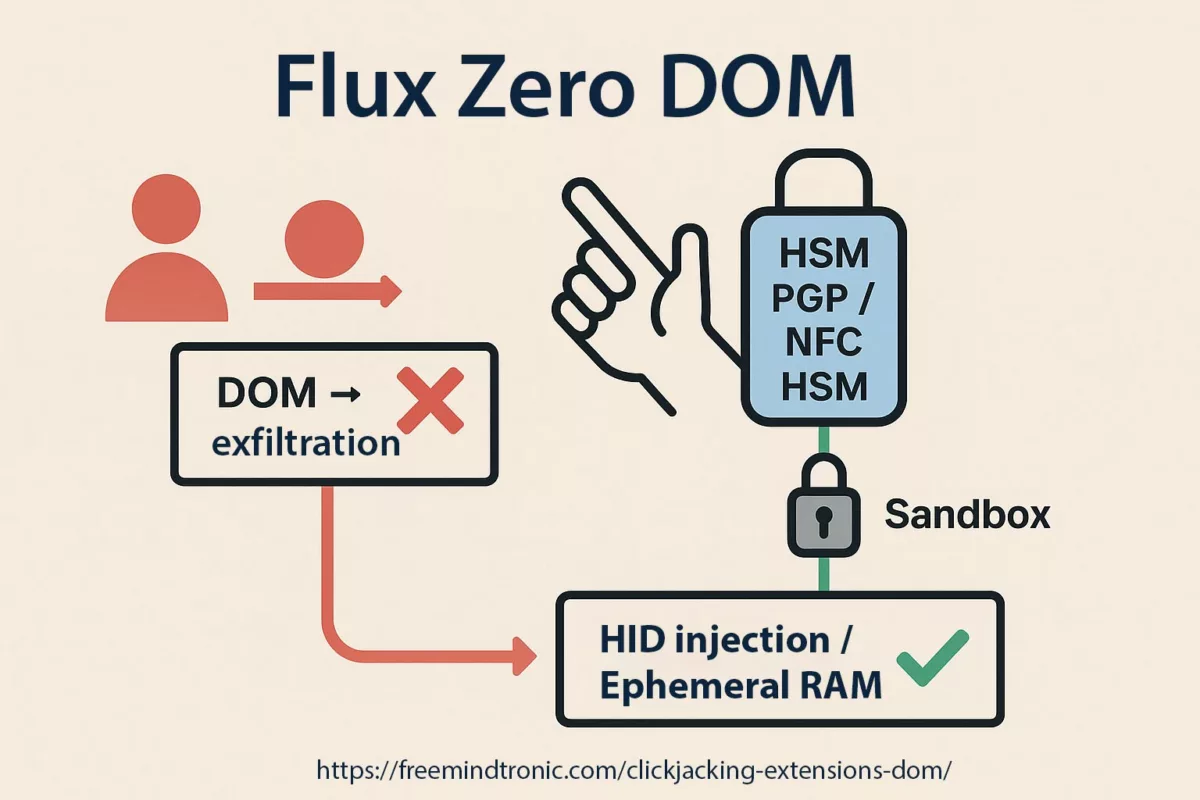
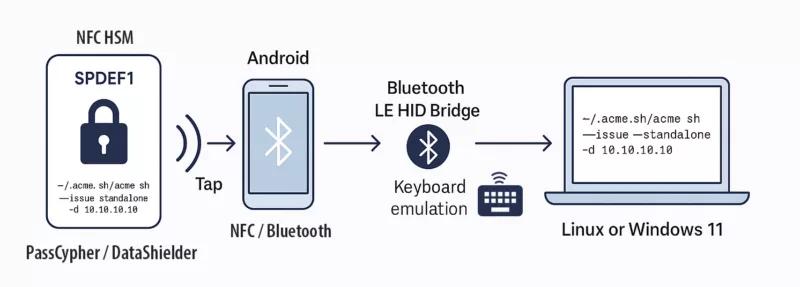
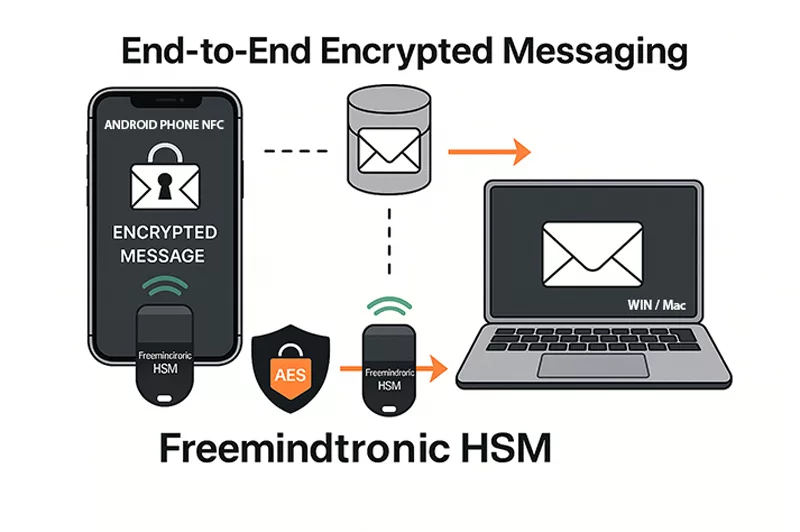
PassCypher — sovereign, patented, 100% offline response
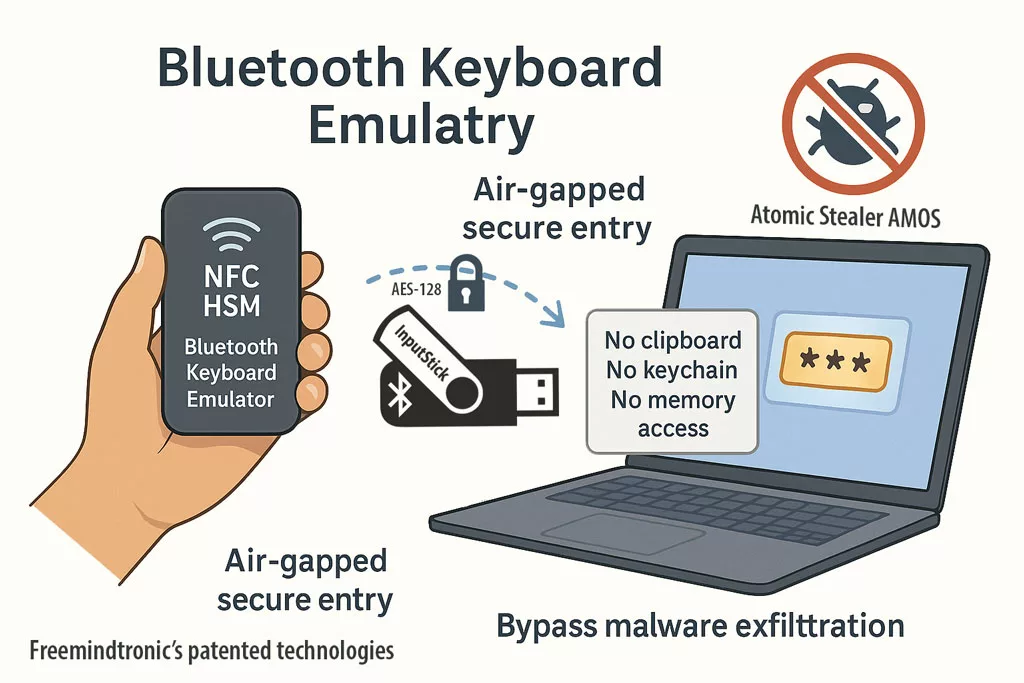
Louvre security weaknesses — launched in 2022 with PassCypher NFC HSM, Freemindtronic introduced the first hardware offline authentication and encryption by proof of possession, compatible with any OS, including legacy environments (Windows XP, 2000). In 2024, PassCypher HSM PGP extended this model to multi-identity PGP management, offline signing, and encryption—delivering full sovereign control with no server, no cloud, and no third-party software dependency. These patented solutions, developed and manufactured in Andorra, rely on a 100% hardware, volatile enclave that stores no persistent data and requires no network connection to operate—passwordless, serverless, and offline-first with RAM-only HSM.
🏛️ ANSSI report on the Louvre: critical weaknesses, tiny costs, sovereign fix < €96/seat/year
In 2014, an ANSSI IT security audit of the Musée du Louvre found serious vulnerabilities: trivial passwords (LOUVRE, THALES) on safety systems, obsolete operating systems, and plausible internal attack surfaces. Unearthed by media investigations and echoed internationally, these issues returned to the spotlight after the October 2025 heist and the Cour des comptes public report issued on November 6, 2025.
⮞ Typology of weaknesses: failed technical governance, software dependency, lack of a sovereign doctrine.
⮞ Strategic response: offline, RAM-only, passwordless authentication with no server, scalable to the Louvre’s 2,100 employees.
Budget extension — projection across 2,100 seats
The per-seat cost of sovereign protection is estimated at < €96 incl. VAT/year. For a fleet covering all 2,100 Louvre staff (guards, curators, administrative), this amounts to:
- Estimated annual total: €201,600 incl. VAT
- Share of 2024 turnover: ≈ 0.15% (on €137.2M)
- Share of 2024 net profit: ≈ 1.06% (on €19M)
⮞ Conclusion: fully securing staff is budget-negligible yet doctrinally decisive.
Sovereign ROI — productivity and security
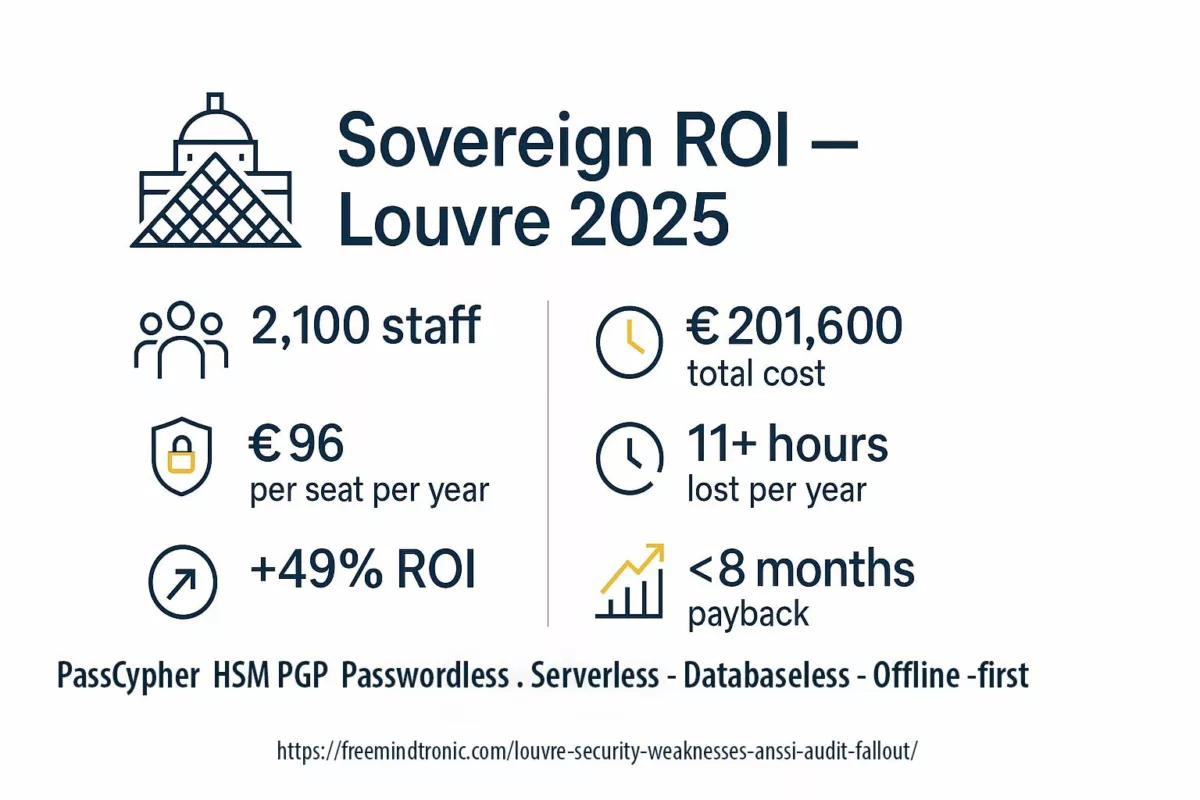
For the 2,100 Louvre seats, that equals a hidden cost of nearly €300,000 per year.
At €96 incl. VAT per seat per year, full sovereign protection would cost €201,600 — yielding a direct ROI of +49% and payback in under eight months.
In other words, offline sovereignty not only protects; it restores economic value.
Sovereign doctrine — remediation principles
- Proof of possession: eliminate shared passwords; remove social-engineering vectors.
- Secret volatility: no persistent data, no databases, no sync.
- Backward interoperability: compatible with Windows XP/2000, no update required.
- Authentication air-gap: no server, no network dependency, no external exposure.
- Hardware auditability: physical enclave, local traceability, GDPR/NIS2 alignment without data collection.
⮞ Outcome: security by design, not by software stacking.
Comparative typology — from the Louvre to the State
| Criterion | Legacy (ANSSI audit 2014) | PassCypher (sovereign model) |
|---|---|---|
| Passwords | LOUVRE, THALES (press reports) |
No passwords; proof of possession |
| Dependency | Vendors / OS / servers | 100% offline, no server or cloud |
| Updates | Unmaintained software | Not required server-side |
| Sovereignty | Multiple external chains | Local, volatile, auditable |
| Cost/seat/year | Not documented | < €96 incl. VAT (order of magnitude) |
| Data | Traceability not specified | 0% collection, 100% local anonymity |
⮞ The Louvre becomes a case study: sovereignty isn’t bought; it is engineered.
Sector implications — museums, archives, libraries
- National museums: secure staff and workstations without network overhauls.
- Public archives: protect access without cloud exposure.
- Heritage libraries: extend legacy workstations without cyber risk.
- Agencies under supervision: GDPR/NIS2 alignment without IAM or SIEM.
⮞ Recommendation: embed offline authentication in physical and digital safety master plans.
Strategic Outlook — 2026 as a doctrinal turning point
The Louvre illustrates a paradox: trivial failures, an affordable solution, yet doctrinal inertia. In 2026, public operators should:
- Break with the password/server paradigm
- Adopt proof of possession as a standard
- Align cybersecurity with physical sovereignty
⮞ Goal: make offline authentication a pillar of museum, archival, and heritage safety.
– Tech Fixes & Security Solutions
– Technical News
– Cyberculture
– The 2014 ANSSI report remains non-public; only consistent media recaps are cited.
– For any legal or regulatory action, request an official ANSSI attestation.