Delving into the 2░0░2░4░Dropbox Security Breach: A Chronicle of Vulnerabilities, Exfiltrated Data
In 2024, a shadow fell over cloud storage security. The Dropbox breach exposed a shocking vulnerability, leaving user data at risk. This deep dive explores the attack, the data compromised, and why encryption remains your ultimate defense. Dive in and learn how to fortify your digital assets.
Dropbox Security Breach. Stay updated with our latest insights.
Dropbox Security Breach: Password Managers and Encryption as Defense By Jacques Gascuel, this article examines the crucial role password managers and encryption play in mitigating the risks of cyberattacks like the Dropbox Security Breach
Phishing Tactics: The Bait and Switch in the Aftermath of the Dropbox Security Breach
The 2024 Dropbox Security Breach stands as a stark reminder of the ever-evolving cyberthreat landscape and the urgent need for robust security measures. In this comprehensive article, we’ll unravel the intricate details of this breach, examining the tactics employed by attackers, the vast amount of sensitive data compromised, and the far-reaching consequences for affected users. We’ll also delve into the underlying security vulnerabilities exploited and discuss essential measures to prevent similar incidents in the future. Finally, we’ll explore the crucial role of advanced encryption solutions, such as DataShielder and PassCypher, in safeguarding sensitive data stored in the cloud. Through this in-depth analysis, you’ll gain a clear understanding of the Dropbox breach, its impact, and the proactive steps you can take to enhance your own cybersecurity posture.
Crafting Convincing Emails
Attackers meticulously crafted phishing emails, often disguised as notifications or security alerts, to deceive employees.
- Crafting Convincing Emails: Attackers meticulously crafted phishing emails, often disguised as notifications or security alerts, to deceive employees.
- Exploiting Human Trust: By leveraging the trust employees had in Dropbox, attackers successfully persuaded them to divulge sensitive information.
- MFA Circumvention: The compromise of MFA codes highlights the need for additional layers of security beyond passwords.
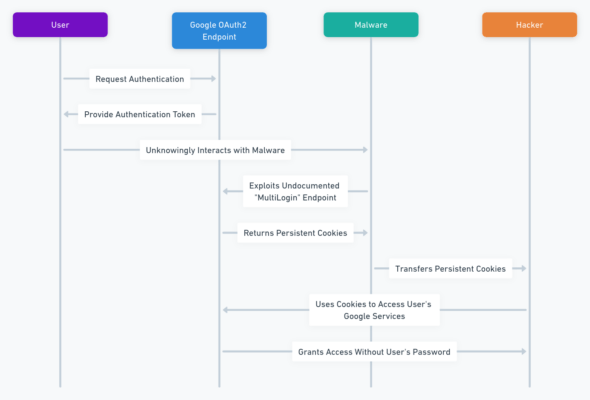
Dropbox Security Breach Attack Flow: Unraveling the Steps of the Cyberattack
- Phishing Emails: Attackers send out phishing emails to Dropbox employees, mimicking legitimate communications.
- Credential Harvesting: Employees fall victim to phishing tactics and reveal their credentials, including MFA codes.
- Unauthorized Access: Attackers gain unauthorized access to Dropbox Sign infrastructure using compromised credentials.
- Exploiting Automated Tools: Attackers exploit automated system configuration tools to manipulate accounts and escalate privileges.
- Data Exfiltration: Attackers extract a vast amount of sensitive data, including emails, usernames, phone numbers, hashed passwords, API keys, OAuth tokens, and MFA data.
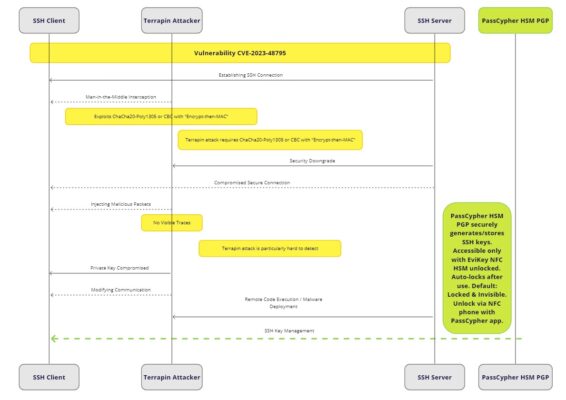
Exploited Vulnerabilities: A Technical Analysis
The attackers behind the Dropbox breach exploited a combination of vulnerabilities to gain unauthorized access and exfiltrate sensitive data.
Specific CVEs Exploited
- CVE-2019-12171: This vulnerability allowed attackers to store credentials in cleartext in memory, posing a significant security risk.
- CVE-2022-4768: This critical vulnerability in Dropbox Merou affected the add_public_key function, leading to injection attacks.
- Automated System Configuration Tools: The exploitation of these tools highlights the need for robust access controls and security measures.
Exfiltrated Data: The Scope of the Breach
The sheer volume of data compromised in the Dropbox breach is staggering, raising serious concerns about the potential impact on affected users.
Types of Data Exposed
- Exposed Emails: Attackers now possess email addresses, potentially enabling them to launch targeted phishing attacks or engage in email scams.
- Vulnerable Usernames: Usernames, often coupled with leaked passwords or other personal information, could be used to gain unauthorized access to other online accounts.
- Misused Phone Numbers: Exposed phone numbers could be used for unwanted calls, text messages, or even attempts to reset passwords or gain access to other accounts.
- Hashed Passwords: A Target for Cracking: While not directly readable, hashed passwords could be subjected to brute-force attacks or other cracking techniques to recover the original passwords.
- Compromised Authentication Tokens: API keys and OAuth tokens, used for app authentication, could enable attackers to impersonate users and access their Dropbox accounts or other connected services.
The Dropbox Breach Fallout: Unraveling the Impact and Consequences
The ramifications of the Dropbox breach extend far beyond the compromised data itself. The incident has had a profound impact on both affected users and Dropbox as a company.
Consequences of the Breach
- User Privacy Concerns: The exposure of personal information has left users feeling vulnerable and at risk of identity theft, phishing attacks, and other cyber threats.
- Reputational Damage: Dropbox’s reputation as a secure cloud storage provider has taken a significant hit, potentially affecting user trust and future business prospects.
- Financial Costs: Dropbox has incurred substantial expenses in investigating the breach, notifying affected users, and implementing additional security measures.
Lessons Learned: Preventing Future Breaches and Strengthening Security
In the aftermath of the Dropbox breach, it’s crucial to identify key takeaways and implement preventive measures to safeguard against future incidents.
Essential Security Practices
- Secure Service Accounts: Implement strong passwords for service accounts and enforce strict access controls, adhering to the principle of least privilege. Consider using Privileged Access Management (PAM) solutions to manage and monitor service account activity.
- Regular Penetration Testing: Conduct regular penetration tests (pen tests) to identify and remediate vulnerabilities in systems and networks before they can be exploited by attackers. Engage qualified security professionals to simulate real-world attack scenarios.
- Continuous Monitoring and Incident Response: Establish a robust incident response plan to effectively address security breaches. This plan should include procedures for identifying, containing, and remediating incidents.
- Patch Management: Prioritize timely patching of software and systems with the latest security updates. Implement a comprehensive patch management strategy to ensure the prompt deployment of critical security updates.
Beyond the Breach: Enhancing Proactive Defense with Advanced Encryption
While robust security practices are essential for preventing breaches, additional layers of protection can further safeguard data. Advanced encryption solutions play a pivotal role in this regard. Here, we’ll delve into two such solutions – DataShielder HSM PGP and NFC HSM, and PassCypher HSM PGP and NFC HSM – and explore how they address the vulnerabilities exploited in the 2024 Dropbox breach.
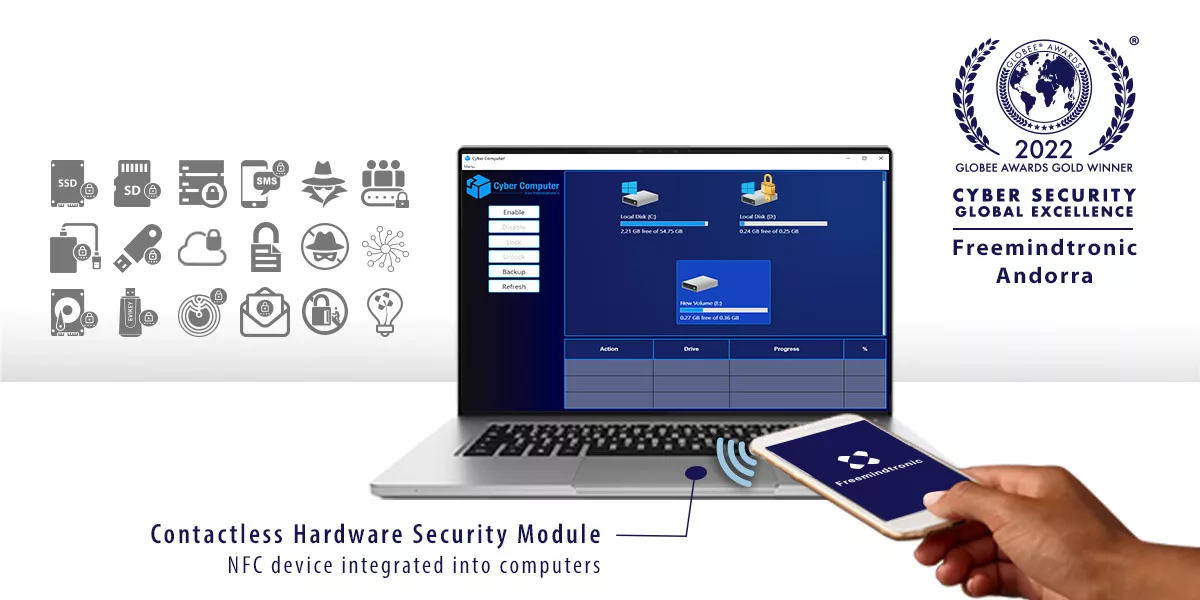
DataShielder HSM PGP and NFC HSM
DataShielder HSM PGP and NFC HSM provide client-side encryption for data stored in the cloud. By encrypting data at rest and in transit (as depicted in the following diagram [Insert DataShielder Diagram Here]), DataShielder ensures that even if an attacker gains access to cloud storage, the data remains inaccessible. This robust protection is achieved through:
- Client-Side Encryption: Data is encrypted on the user’s device before being uploaded to the cloud.
- Hardware Security Module (HSM) or NFC HSM: Encryption keys are stored within a secure HSM or NFC HSM, offering physical separation and robust protection against unauthorized access.
- Offsite Key Management: Encryption keys are never stored on the cloud or user devices, further minimizing the risk of compromise (as illustrated in the diagram).
- Post-Quantum Encryption: Additionally, DataShielder incorporates post-quantum encryption algorithms to safeguard against future advancements in code-breaking techniques.
DataShielder HSM PGP and NFC HSM: Ensuring Dropbox security breach protection with AES-256 encryption and offsite key management
PassCypher HSM PGP and NFC HSM
PassCypher HSM PGP and NFC HSM go beyond traditional password management, offering a comprehensive security suite that directly addresses the vulnerabilities exploited in the 2024 Dropbox breach. Here’s how PassCypher strengthens your defenses:
- Multi-Factor Authentication (MFA) with Hardware Security: PassCypher NFC HSM offers additional protection for logins by securely managing Time-based One-Time Passwords (TOTP) and HOTP keys. Users can scan a QR code to automatically store the encrypted TOTP secret key within the NFC HSM, adding a layer of hardware-based authentication beyond passwords.
- Real-Time Password Breach Monitoring: PassCypher HSM PGP integrates with Have I Been Pwned (HIBP), a constantly updated database of compromised passwords. This real-time monitoring allows users to be instantly notified if their passwords appear in any known breaches.
- Phishing Prevention: In addition to the URL sandbox system and protection against typosquatting and BITB attacks mentioned earlier, PassCypher’s comprehensive approach empowers users to identify and avoid malicious attempts (as detailed in the diagram).
- Client-Side Encryption: PassCypher utilizes client-side encryption to ensure data remains protected even if attackers manage to exfiltrate it (as shown in the diagram).
By combining these features, PassCypher HSM PGP and NFC HSM provide a robust defense against the social engineering tactics and credential theft exploited in the Dropbox breach.
Statistics of the 2024 Dropbox Security Breach
While verifying the exact number of users affected by data breaches can be challenging, security experts estimate that the Dropbox breach could have impacted a substantial number of users. Some reports suggest that the breach may have affected up to 26 billion records, making it one of the largest data breaches in history. However, it is crucial to note that this figure is unconfirmed and may not reflect the actual number of individuals impacted.
Key Takeaways for Enhanced Cybersecurity
- Uncertain Numbers: The exact number of affected users remains unclear, highlighting the challenges in verifying breach statistics.
- Potential for Massive Impact: The estimated 26 billion records underscore the potential scale of the breach and its far-reaching consequences.
- Importance of Reliable Sources: Relying on reputable sources for breach information is crucial to ensure accurate and up-to-date data.
Conclusion: A Call for Vigilance and Enhanced Security in the Wake of the Dropbox Security Breach
The 2024 Dropbox security breach serves as a stark reminder of the ever-evolving cyberthreat landscape and the urgent need for vigilant security practices. Organizations must prioritize robust security measures, including strong access controls, regular vulnerability assessments, and timely patching. Additionally, advanced encryption solutions, such as DataShielder HSM PGP and NFC HSM and PassCypher HSM PGP and NFC HSM, can provide an extra layer of protection for sensitive data.
Key Takeaways for Enhanced Cybersecurity
- Collective Responsibility: Cybersecurity is a shared responsibility, requiring collaboration between organizations and individuals.
- Continuous Learning and Awareness: Staying informed about emerging threats and adopting best practices are essential for effective cybersecurity.
- Protecting Sensitive Data: Prioritizing data protection through robust security measures and advanced encryption is paramount.
The 2024 Dropbox security breach serves as a cautionary tale, highlighting the vulnerabilities that can exist even in large, established organizations. By learning from this incident and implementing the recommendations discussed, we can collectively strengthen our cybersecurity posture and protect our valuable data from the ever-evolving threat landscape.