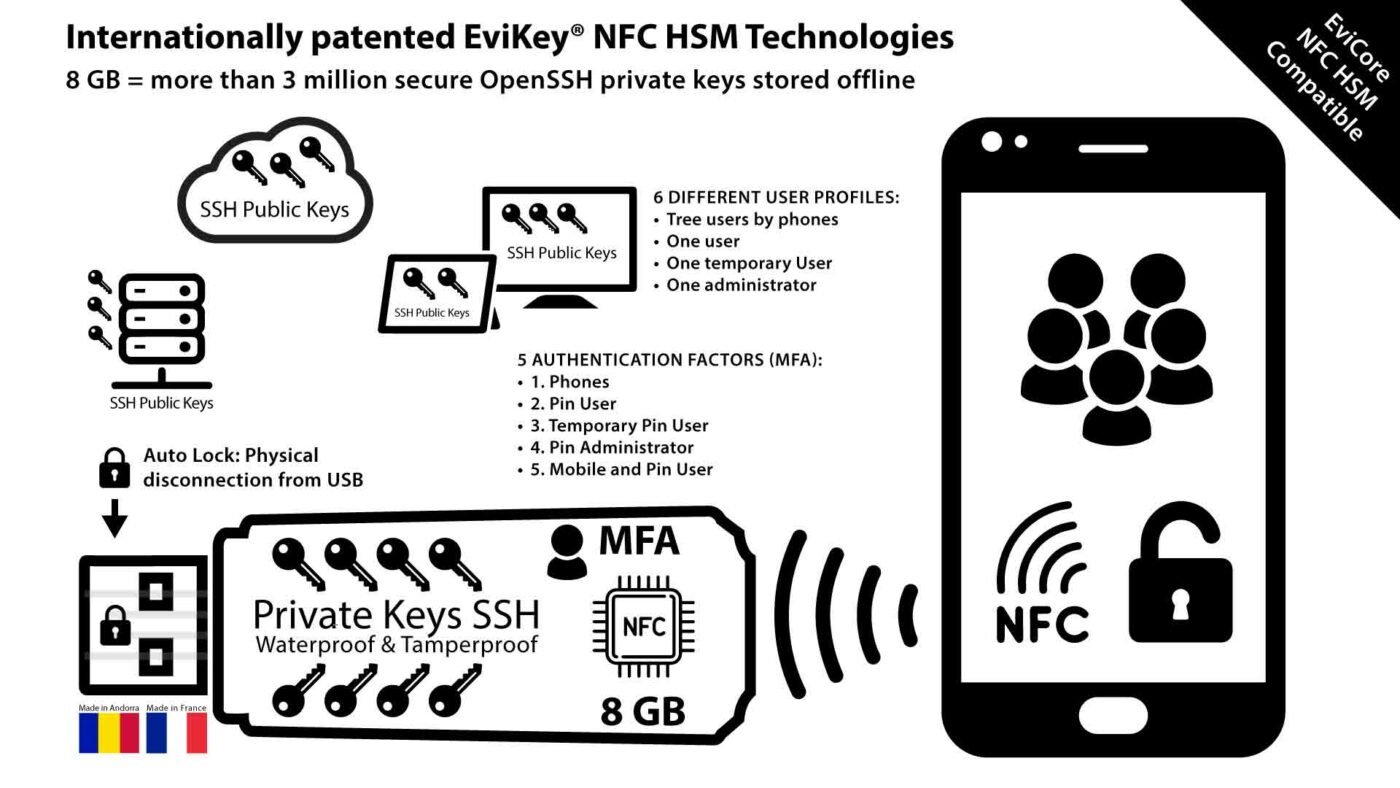
Protect Yourself from the Terrapin Attack: Shield Your SSH Security with Proven Strategies SSH is a widely used protocol for secure communication over the internet. It allows you to remotely access and control servers, transfer files, and encrypt data. However, SSH is not immune to attacks, and a recent vulnerability OpenSSH before 9.6 (CVE-2023-48795) has exposed […]
Stay informed!
Join our community of technology enthusiasts! Subscribe to our newsletter and receive exclusive updates on the latest news, special offers, and tips from Freemindtronic. Stay informed on the latest technology trends, discover new products, and be among the first to take advantage of them. Sign up now by entering your email address below. Don't miss any updates from Freemindtronic!