Cryptographic Libraries and Patented Key Management (Protected by International Patent)
The DataShielder HSM PGP system incorporates advanced cryptographic libraries to handle encryption and manage keys securely. This includes AES-256 encryption and a patented key segmentation system, enhancing security by splitting a 512-bit encryption key into two separate 256-bit segments.
- crypto-js (Version: 4.1.1): Manages AES-256 CBC encryption and SHA-256 hashing, both essential for secure operations.
Documentation: CryptoJS
- js-base64 (Version: 3.7.4): Converts binary data into Base64, facilitating safe transmission of encrypted data.
Documentation: JS-Base64
- openpgp (Version: 5.11.2): Implements OpenPGP encryption and signature capabilities.
Documentation: OpenPGP.js
- bip39 (Version: 3.1.0): Generates mnemonic phrases for secure key management.
Documentation: BIP39
Patented Key Segmentation Technology
DataShielder HSM PGP is protected by your international key segmentation patent, which provides a unique approach to key management and authentication. This patent ensures the independence of the two 256-bit key segments. One segment is stored securely in the browser’s localStorage, while the other is kept on an external device, such as a USB, SSD, or NAS drive. The segmentation method ensures that no single location holds the entire key, significantly reducing the risk of compromise.
- Security by Design: The patented segmentation method guarantees that even if one segment is compromised, the full key remains inaccessible without access to the second segment.
- Flexible Key Management: Users can select segments from a variety of storage locations, including local and external devices. This dynamic flexibility in key selection creates numerous secure combinations, ensuring Zero Trust principles are upheld.
Encryption and Decryption with Patented Key Segmentation
The two key segments combine to form a 512-bit key during encryption and decryption, which is then used in AES-GCM. This patented approach strengthens security by ensuring that the key segments remain independent and are never stored together in one place.
Example:
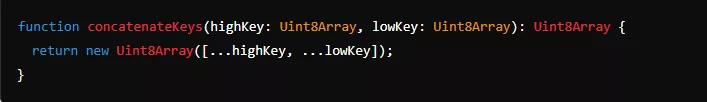
This process, managed by DataShielder Engine, ensures that sensitive information remains protected across various high-risk environments.
Encryption/Decryption
The concatenated 512-bit key is used in AES-GCM for secure handling of data. This method adds an initialization vector (IV) for additional encryption strength.
Example:
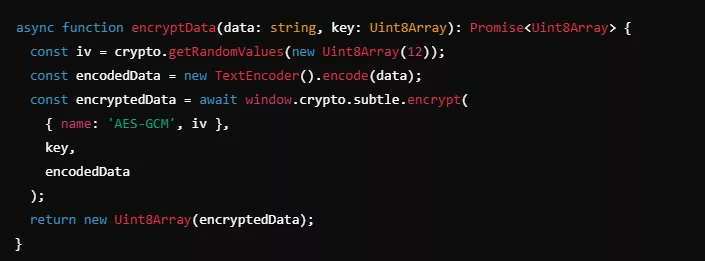
Decentralized Key Management with Segmented Keys
DataShielder HSM PGP enables a decentralized approach to key management where external key segments are stored across various devices (USB, SSD, etc.). Each user can receive a segment via separate channels (such as local storage on their USB), but the external segment may differ between users. This decentralized structure ensures security without relying on servers or databases, allowing complete autonomy over key management.
Following the explanation of both decentralized and intelligent centralized key management, the segmentation technology offers significant security benefits.
Intelligent Decentralized Key Management with EviEngine
Although the system is decentralized, DataShielder HSM PGP also enables intelligent centralized key management. Companies can securely distribute external key segments via shared services without requiring a centralized server or database. Employees can access external key segments stored on enterprise drives or remote storage services. Thanks to DataShielder HSM PGP’s path management system, it supports centralized key segment sharing while maintaining Zero Trust, Zero Knowledge, and avoiding the need for account creation or user identification.
Advantages of Key Segmentation
- Security by Design: Key segments are never stored together, which ensures that even if one segment is compromised, the other remains inaccessible.
- Enhanced Protection: This method resists both local and network-based attacks since access to both segments is required for successful decryption.
Serverless Security with EviEngine (Protected by Copyright)
DataShielder’s EviEngine allows secure communication between the web browser and computer, eliminating the need for external servers or databases. Moreover, it retrieves and stores segmented encryption keys across multiple devices, including USBs and cloud storage, without relying on a central authority or data collection. This architecture ensures privacy while maintaining security.
Protected by copyright, EviEngine automates the management of license keys and activates browser extension features securely, by linking license usage directly to hardware. This provides users with greater flexibility in managing their own keys while ensuring Zero Trust architecture for data security.
Learn more about EviEngine here.
How EviEngine Works:
- Automates Actions in Web Services: EviEngine allows users to store and retrieve data across a variety of devices—removable, online, or networked—without needing a centralized server.
- License Management: License keys, linked to hardware and not user identity, are verified via EviEngine, acting like a dongle to activate features in DataShielder HSM PGP.
- Path Management: EviEngine manages paths where key segments are stored and retrieved, without needing a database, providing seamless integration with DataShielder HSM PGP.
With EviEngine, users enjoy full control over their keys, encrypted communications, and privacy, all protected by copyright innovation, making it the backbone for managing the secure and decentralized features of DataShielder HSM PGP.




Pingback: Software version history application & extension - Freemindtronic