2023, Articles, DataShielder, Digital Security, EviCore NFC HSM Technology, EviCypher NFC HSM, EviCypher Technology, NFC HSM technology
FormBook Malware: How to Protect Your Gmail and Other Data
Secure Your Gmail from FormBook Attacks
FormBook is a malware that can steal your Gmail credentials, messages, and attachments. Learn how to use the Freemindtronic devices to encrypt your Gmail data and use passwordless and 2FA.
How to Protect Your Gmail Account from FormBook Malware
Introduction
Imagine that you receive an email from your bank, asking you to confirm your identity by clicking on a link. You open the link, and you find yourself on a page that looks like your bank’s website, but it is actually a fake. You enter your credentials, and you think you are done. But in reality, you have just given access to your bank account to hackers, who will use it to steal your money, or worse. This is what FormBook can do, a malware that can steal your sensitive data, and that Google cannot stop. In this article, we will explain what FormBook is, how it works, and how to protect yourself from this malware.
What is FormBook and why is it a threat?
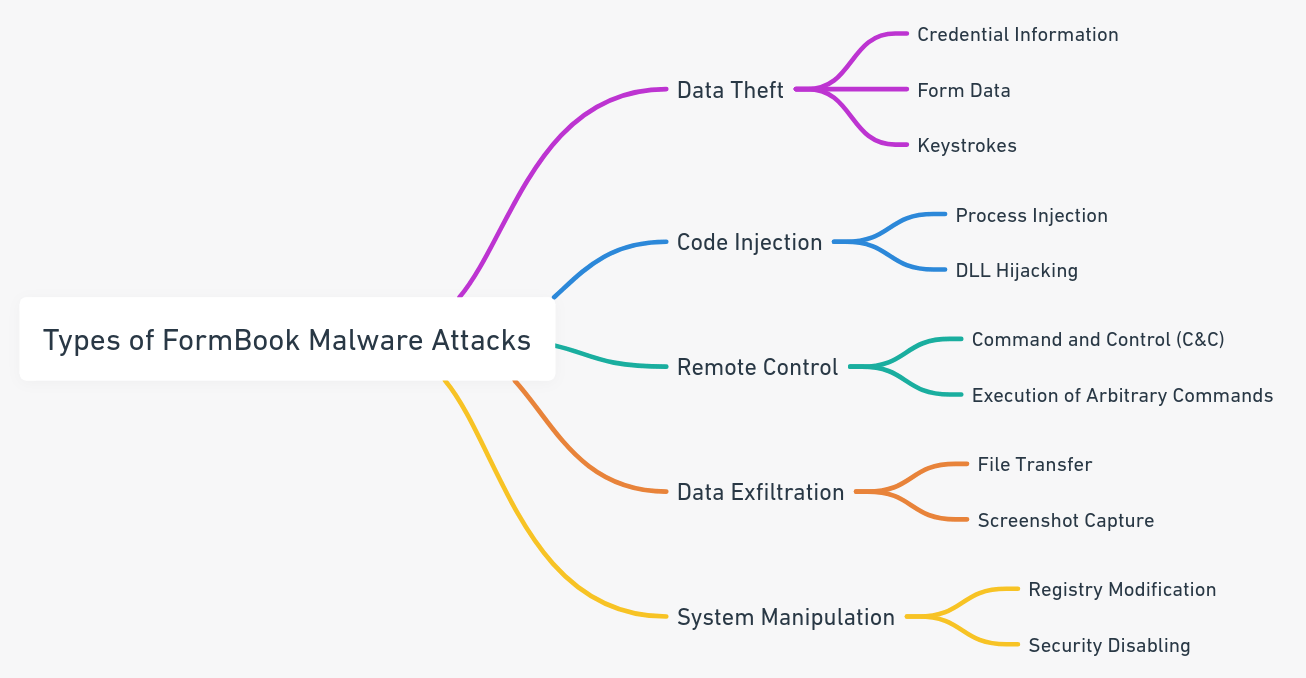
FormBook is a malware that can record your keystrokes, take screenshots, and steal your passwords, cookies, and clipboard data. It can also download and execute other malicious files on your device.
FormBook is distributed through phishing emails that contain malicious attachments. These attachments are usually disguised as invoices, receipts, or shipping confirmations. When you open them, they ask you to enable macros or content. If you do, the malware will be installed on your device.
FormBook can target any web browser, but it has a special feature for Chrome. It can inject a fake Gmail login page into your browser, and trick you into entering your credentials. The malware will then send your Gmail username and password to a remote server controlled by the hackers.
FormBook is a threat because it can compromise your Gmail account and access your personal and professional information. It can also use your Gmail account to send spam or phishing emails to your contacts, or to access other online services that are linked to your Gmail account, such as Google Drive, Google Photos, or Google Pay.
How to protect yourself from FormBook?
Google has not yet found a way to detect and block FormBook. Therefore, you need to be extra careful when you use Gmail and other online services. Here are some tips to protect yourself from FormBook and other malware:
- Do not open or download attachments from unknown or suspicious senders. If you are not sure about the legitimacy of an email, contact the sender directly or check the official website of the company or organization.
- Do not enable macros or content in any document unless you trust the source. Macros are small programs that can run malicious code on your device.
- Use a strong and unique password for your Gmail account and other online accounts. Do not reuse the same password for different services. Change your password regularly and use a password manager to store and generate your passwords.
- Enable two-factor authentication (2FA) for your Gmail account and other online accounts. 2FA adds an extra layer of security by requiring a code or a device confirmation in addition to your password.
- Use a reputable antivirus software and keep it updated. Antivirus software can scan your device for malware and remove it. You can also use a browser extension that can block malicious websites and pop-ups.
How to encrypt your Gmail messages and attachments with DataShielder NFC HSM
DataShielder NFC HSM is a device that allows you to encrypt and decrypt your Gmail messages and attachments with your own encryption keys that you create and store offline. It uses the EviCypher NFC HSM technology, which is a contactless hardware security module (NFC HSM) that won the Gold Medal for International Inventions in Geneva on March 2021.
With DataShielder NFC HSM, you can encrypt and decrypt your data with AES-256 keys that are randomly generated and stored in the NFC HSM. You can store up to 100 keys and one pair of RSA-4096 keys in the NFC HSM. You can also use different keys for the message and the attachment.
To encrypt your Gmail message and attachment, you need to use the EviCrypt and EviFile applications that are embedded in the DataShielder NFC HSM. These applications allow you to encrypt and decrypt your data with a simple tap of your NFC phone on the DataShielder NFC HSM. You can also share your encrypted data with other users who have the same device and the same key.
By using DataShielder NFC HSM, you can protect your Gmail messages and attachments from FormBook or any other malware that can access your Gmail account. Even if your Gmail account is hacked, your encrypted data will remain encrypted and unreadable by the hackers. Only you and the authorized recipients can decrypt your data with the DataShielder NFC HSM.
How to protect your web Gmail account with passwordless and 2FA using PassCypher NFC HSM
Do you want to manage your web accounts with complicated and complex passwords that you do not need to know, remember, or type? If yes, then you should try PassCypher NFC HSM. This device uses the EviPass NFC HSM technology, which is a contactless hardware password manager that won the Silver Medal for International Inventions in Geneva on March 2021.
With PassCypher NFC HSM, you can create and store your usernames and passwords of more than 256-bit in the NFC HSM. Moreover, you can store your OTP TOTP or HOTP secret keys in the NFC HSM to generate the 2FA code for your web accounts. The NFC HSM can store up to 100 web accounts and one pair of RSA-4096 keys.
To use PassCypher NFC HSM, you need to install the Freemindtronic extension for your web browser based on Chromium or Firefox. This extension uses the EviCore NFC HSM Browser technology, which allows you to communicate with the NFC HSM via your NFC phone. You also need to use the EviPass and EviOTP applications that are embedded in the PassCypher NFC HSM. These applications allow you to create, edit, and delete your web accounts and OTP secret keys with a simple tap of your NFC phone on the PassCypher NFC HSM.
By using PassCypher NFC HSM, you can secure your web accounts with passwordless and 2FA. You do not need to display, know, or type your username and password. You just need to tap your NFC phone on the PassCypher NFC HSM and the extension will autofill and auto login your web account. You also do not need to check for a typosquatting attack, since the extension will verify the URL of the website before logging in. And you do not need to use another device or application to generate the 2FA code, since the PassCypher NFC HSM will do it for you.
How to protect your Gmail account from FormBook with PassCypher NFC HSM
FormBook is a dangerous malware that can access your Gmail account and other sensitive data. Google has not yet found a solution to stop it. Therefore, you need to be vigilant and follow the best practices to protect yourself from cyberattacks. One of them is to use PassCypher NFC HSM to secure your Gmail account with passwordless and 2FA.
By using PassCypher NFC HSM, you can protect your Gmail account from FormBook or any other malware that can access your web browser. Even if your web browser is hacked, your usernames and passwords will remain encrypted and inaccessible by the hackers. Only you can decrypt your Gmail account with the PassCypher NFC HSM. And even if the hackers manage to steal your session cookies, they will not be able to log in to your Gmail account without the 2FA code that is generated by the PassCypher NFC HSM.
To use PassCypher NFC HSM with your Gmail account, you need to follow these steps:
- Create a Gmail account in the EviPass application on the PassCypher NFC HSM. You can use the default username and password, or you can generate a random and complex password with the EviPass application.
- Enable 2FA for your Gmail account on the Google website.
- Choose the option to use an authenticator app, and scan the QR code with the EviOTP application on the PassCypher NFC HSM. This will store your OTP secret key in the NFC HSM.
- Log in to your Gmail account with the Freemindtronic extension on your web browser. Tap your NFC phone on the PassCypher NFC HSM and the extension will autofill and auto login your Gmail account. You will also see a pop-up window with the 2FA code that you need to enter on the Google website.
By following these steps, you can use PassCypher NFC HSM to secure your Gmail account with passwordless and 2FA. You can also use PassCypher NFC HSM with other web accounts that support 2FA, such as Facebook, Twitter, or Amazon. This way, you can protect yourself from FormBook and other malware that can access your web browser.
Recent statistics on FormBook
FormBook is a malware that was first discovered in 2016, but it remains very active and dangerous. According to the Check Point report on cybersecurity in 2022, FormBook was the third most widespread malware in 2021, attacking 5% of enterprise networks. It was also the most prolific infostealer malware, accounting for 16% of attacks worldwide.
FormBook spreads mainly through phishing emails that contain malicious attachments. These attachments are often RAR self-extracting archives, which are compressed files that can run malicious code when opened. The RAR files contain a legitimate document, such as a PDF or a Word file, and a hidden executable file, which is the FormBook malware. When the user opens the RAR file, the document is displayed, but the malware is also installed in the background.
FormBook can also spread through other methods, such as drive-by downloads, malicious links, or removable media. The malware can infect any Windows device, from Windows XP to Windows 10. The malware can also evade detection and removal by using various techniques, such as encryption, obfuscation, or anti-analysis.
Here are some recent statistics on FormBook, based on the data from Check Point and ANY.RUN:
- FormBook was the most popular malware in August 2021, affecting 4.5% of organizations worldwide, followed by Trickbot and Agent Tesla, affecting respectively 4% and 3% of organizations worldwide.
- FormBook was the fourth most common malware in 2020, according to the ranking of malware families by ANY.RUN. It accounted for 8% of the samples analyzed by the online sandboxing service.
- FormBook was used in many phishing campaigns targeting various industries, such as defense, aerospace, health, education, finance, retail, etc. It was also used to attack Ukrainian targets during the war between Russia and Ukraine in 2022.
- FormBook has a successor called XLoader, which appeared in 2020 and which is able to infect macOS users. XLoader is sold on the dark web for $59 for a Windows license and $49 for a macOS license.
Danger level of FormBook compared to other malware
FormBook is a very dangerous malware, because it can steal sensitive information, such as credentials, passwords, credit card numbers, 2FA codes, etc. It can also download and execute other malware, such as ransomware, banking trojans, spyware, etc. It can also remotely control the infected device and perform various malicious actions, such as deleting browser cookies, taking screenshots, restarting or shutting down the system, etc.
FormBook is also hard to detect and remove, because it uses advanced evasion techniques, such as code injection, string obfuscation, data encryption, anti-analysis, etc. It also changes frequently its name, path, and file extension, and uses random Windows registry keys to maintain its persistence.
To compare the danger level of FormBook with other known malware in its category, we can use the following criteria:
- The number of organizations affected worldwide
- The type and amount of information stolen
- The ability to download and execute other malware
- The ability to remotely control the infected device
- The evasion techniques used
- The ease of detection and removal
Here is a table that compares FormBook with other popular infostealer malware, such as Trickbot, Agent Tesla, LokiBot, and Raccoon:
| Malware | Number of organizations affected | Type and amount of information stolen | Ability to download and execute other malware | Ability to remotely control the infected device | Evasion techniques used | Ease of detection and removal |
|---|---|---|---|---|---|---|
| FormBook | 4.5% in August 2021 | Credentials, passwords, credit card numbers, 2FA codes, screenshots, keystrokes, etc. | Yes | Yes | Code injection, string obfuscation, data encryption, anti-analysis, etc. | Hard |
| Trickbot | 4% in August 2021 | Credentials, passwords, banking information, personal data, etc. | Yes | Yes | Code injection, string obfuscation, data encryption, anti-analysis, etc. | Hard |
| Agent Tesla | 3% in August 2021 | Credentials, passwords, banking information, personal data, screenshots, keystrokes, etc. | No | Yes | String obfuscation, data encryption, anti-analysis, etc. | Medium |
| LokiBot | 1.5% in August 2021 | Credentials, passwords, banking information, personal data, etc. | No | Yes | String obfuscation, data encryption, anti-analysis, etc. | Medium |
| Raccoon | 0.8% in August 2021 | Credentials, passwords, banking information, personal data, etc. | No | Yes | String obfuscation, data encryption, anti-analysis, etc. | Medium |
From this table, we can see that FormBook is the most dangerous infostealer malware, because it affects the most organizations, steals the most types of information, and can download and execute other malware. It is also the hardest to detect and remove, because it uses more evasion techniques than the other malware.
Forms of attacks of FormBook
FormBook can be delivered through different forms of attacks, depending on the delivery mechanism chosen by the malicious actor. Here are some forms of attacks of FormBook:
- Phishing: FormBook can be sent by email as a malicious attachment, such as a Word, Excel, PDF, or ZIP or RAR file. The email can have a misleading subject, such as an invoice, a receipt, a contract, a job offer, etc. When the user opens the attachment, the malware runs and infects the device.
- Exploitation of vulnerabilities: FormBook can exploit vulnerabilities in popular software, such as Microsoft Office, Windows, Adobe Reader, etc. For example, FormBook used the vulnerability CVE-2017-8570 in Microsoft Office to run malicious code from a RTF file. FormBook also used the vulnerability CVE-2021-40444 in Microsoft MSHTML to run malicious code from a CAB file.
- Drive-by downloads: FormBook can be downloaded without the user’s knowledge when they visit a compromised or malicious website. The website can use a script or an exploit kit to trigger the download and execution of the malware on the user’s device.
- Removable media: FormBook can be copied to removable media, such as USB drives, external hard drives, memory cards, etc. When the user connects the removable media to their device, the malware runs automatically and infects the device.
- Social media: FormBook can be spread by messages or posts on social media, such as Facebook, Twitter, Instagram, etc. These messages or posts can contain links or images that redirect to malicious websites or infected files. When the user clicks on the link or image, the malware is downloaded and executed on their device.
Here is a type of formbook malware attacks image: