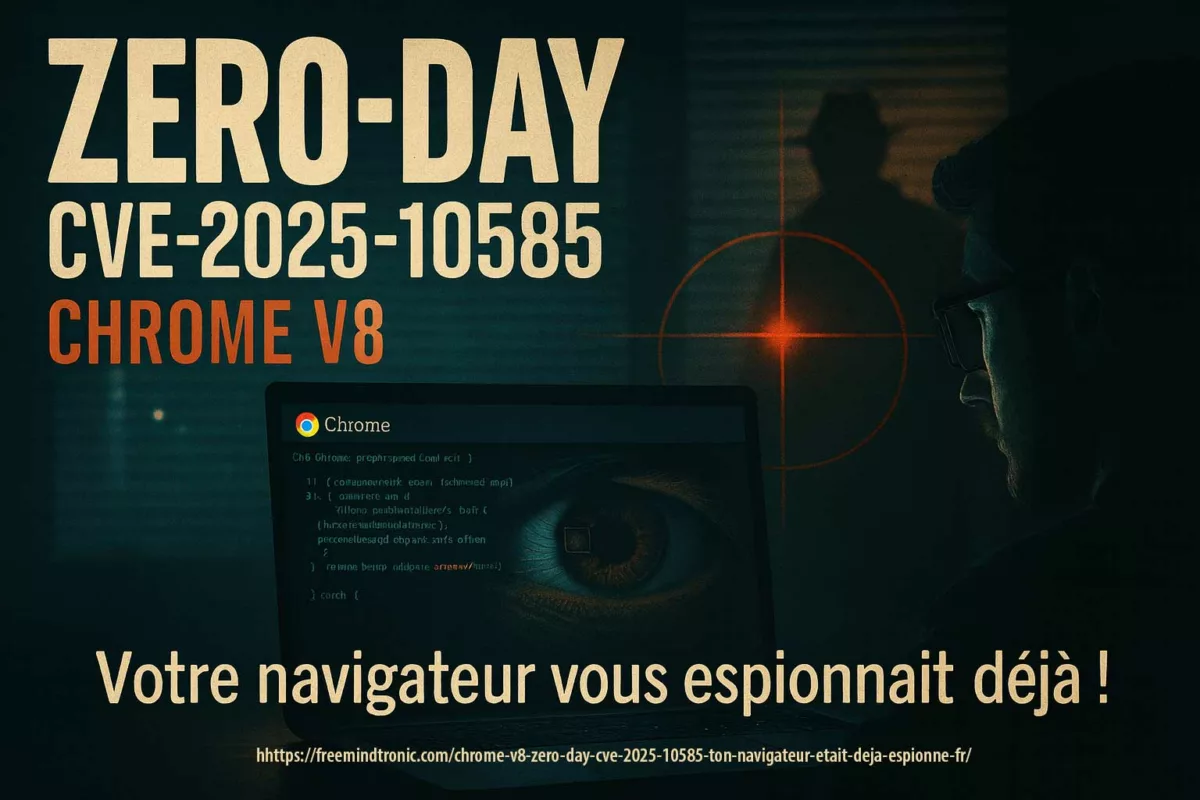
Chrome V8 zero-day CVE-2025-10585 — Votre navigateur n’était pas vulnérable. Vous étiez déjà espionné !
Résumé express
Tu ouvres un onglet. La page paraît ordinaire. Au cœur de V8, une valeur se fait passer pour une autre. Les pointeurs glissent, la mémoire se brouille, et un script façonné s’engouffre. Ce CVE-2025-10585 est une faille mémoire dans le moteur V8 — une type confusion dans V8 qui permet une exécution de code à distance dès la visite d’une page piégée. Le Threat Analysis Group de Google a confirmé une exploitation déjà active. Le correctif est publié sur le canal Stable : 140.0.7339.185/.186 (Windows/Mac) et 140.0.7339.185 (Linux) ; Android : 140.0.7339.155.
🚨 En bref Mettez à jour maintenant. Traitez le navigateur comme un runtime hostile. Séparez les usages sensibles du quotidien. Adoptez une posture Zero-Dom – Installer PassCypher HSM PGP gratuit et activer la fonction anti “BITB”
Chronique à lire
Temps de lecture résumé : 3–4 minutes
Temps de lecture estimé : 36–38 minutes
Date de mise à jour : 2025-09-19
Niveau de complexité : Avancé / Expert
Spécificité linguistique : Lexique souverain — densité technique élevée
Densité technique : élevée ≈ 72 %
Langues : CAT · EN · ES · FR
Accessibilité : Optimisé lecteurs d’écran — ancres sémantiques incluses
Type éditorial : Chronique stratégique (narrative)
À propos de l’auteur : Jacques Gascuel, inventeur et fondateur de Freemindtronic®.
Points clés
- Une page suffit : RCE « drive-by » via confusion de types V8.
- Exploitation reconnue au moment du correctif.
- Versions corrigées : 140.0.7339.185/.186 (Win/Mac) · 140.0.7339.185 (Linux) · Android 140.0.7339.155.
- Réflexe souverain : isolation des usages, réduction de la confiance navigateur, flux Zero-DOM matériels (HSM/NFC).
Il vous reste trois minutes ? Lisez la suite du resumé : l’instant où la compromission devient routinière.
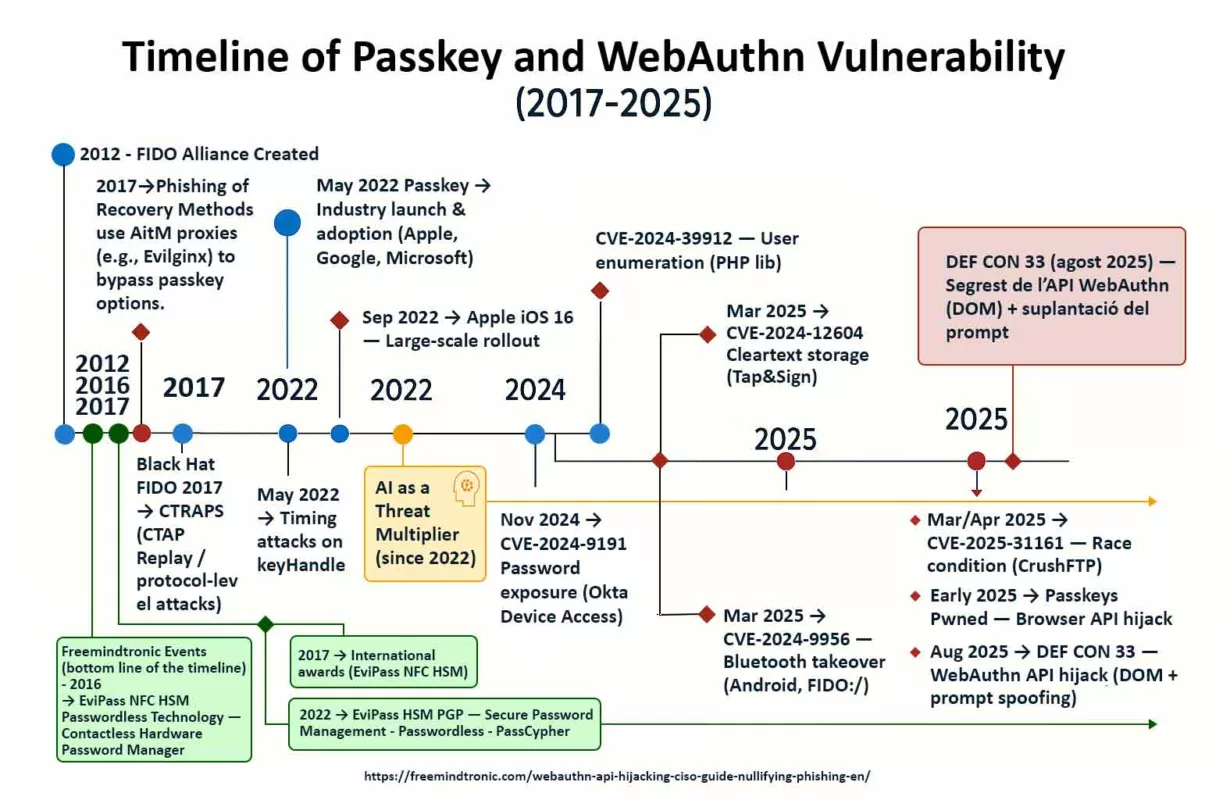
Failles en série, défenses en retard — Posture Zero-DOM
2025 se lit comme une série de films d’espionnage où les attaquants ont toujours une longueur d’avance. CVE-2025-2783 en mars, CVE-2025-4664 en mai, CVE-2025-5419 en juin, et Chrome V8 zero-day CVE-2025-10585 en septembre. À chaque épisode, la même trame : tordre juste assez la mémoire pour obtenir un point d’appui. Le marché récompense ces pages au-delà de 500 000 $ lorsqu’une RCE fiable est en jeu. Pendant ce temps, les défenseurs négocient du temps : des mises à jour qui courent derrière des campagnes déjà en mouvement.
En cybersécurité souveraine ↑ Cette chronique appartient à la rubrique Digital Security, tournée vers les exploits, vulnérabilités systémiques et contre-mesures matérielles zero-trust.
Chrome V8 zero-day CVE-2025-10585 : pourquoi ce pivot change tout
La Faille critique V8 — CVE-2025-10585 n’est pas un accident isolé mais le symptôme d’un modèle où le navigateur exécute du code non fiable au plus près de vos secrets. Tant que les identifiants, sessions et clés croisent le DOM ou la mémoire du navigateur, une faille « drive-by » suffit à les exposer. La suite explique ce qui se passe concrètement, qui l’exploite et comment reprendre l’ascendant.
- Résumé express — CVE-2025-10585
- Failles en série, défenses en retard — Posture Zero-DOM
- Pourquoi ce pivot change tout
- Ce que révèle le zero-day
- Zero-day Chrome V8 en 2025 : la cadence
- Qui l’exploite ?
- Impact sur les utilisateurs
- Que faire ?
- Pourquoi c’est lié au DOM
- Versions corrigées & timeline
- Statistiques d’exposition
- Check-list admins
- Anatomie — V8 type confusion
- Après le franchissement
- Acteurs & incitations
- Réécriture souveraine (Zero-DOM)
- Signaux faibles
- À relier avec…
- FAQ
- Ce que nous n’avons pas couvert
- Glossaire
- Changelog
Ce que révèle le Chrome V8 zero-day CVE-2025-10585
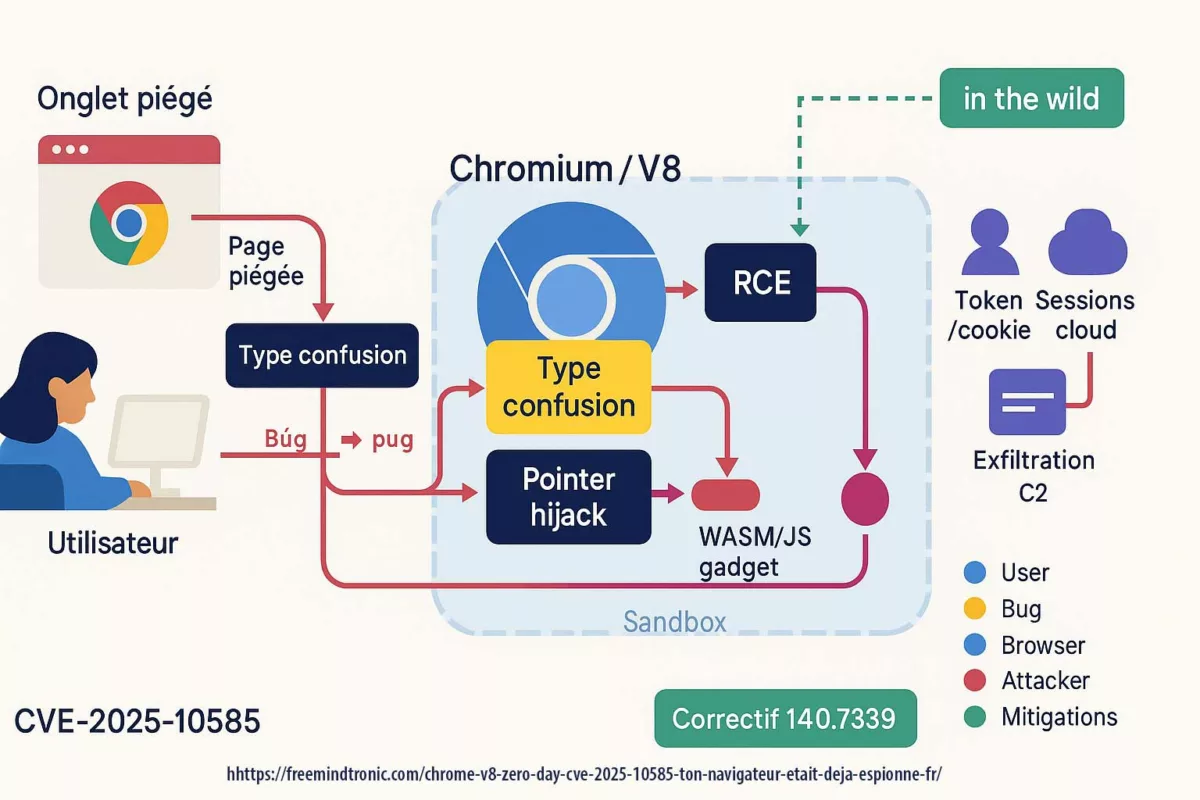
CVE-2025-10585 — faille mémoire dans le moteur V8 est une type confusion dans le moteur V8, celui qui interprète JavaScript et WebAssembly. Une valeur prise pour une autre ouvre un passage où un script façonné peut exécuter du code dès la visite d’une page piégée. Le Google Threat Analysis Group a confirmé une exploitation déjà active au moment du correctif Stable 140.0.7339.185/.186 (Windows/Mac) et 140.0.7339.185 (Linux) ; Android 140.0.7339.155. Autrement dit : l’attaque précède la mise à jour.
Deux conséquences en découlent. D’abord, la compromission peut rester silencieuse : rien n’indique à l’écran que le navigateur a franchi la frontière. Ensuite, une fois le code lancé, le navigateur cesse d’être un conteneur et devient un corridor : cookies, tokens, extensions et sessions cloud sont autant de portes latérales à portée de main.
Zero-day Chrome V8 en 2025 : la cadence
En 2025, la trame se répète : des failles mémoire dans V8 jalonnent l’année et s’alignent sur des campagnes déjà en marche. Ce rythme entretient un écart persistant entre exploitation et patch, surtout lorsque la vulnérabilité permet une exécution de code à distance.
| CVE | Type | Correction | Lien officiel |
|---|---|---|---|
| CVE-2025-2783 | Corruption mémoire | Mars 2025 | Fiche cve.org |
| CVE-2025-4664 | Use-after-free / politique (Loader) | 14 mai 2025 | Chrome Releases — Desktop |
| CVE-2025-5419 | Out-of-bounds R/W | 3 juin 2025 | Chrome Releases — Extended Stable |
| CVE-2025-10585 | Type confusion (V8) | 17 sept. 2025 | Chrome Releases — Desktop · Android |
Sur les marchés gris/noirs, un Chrome V8 zero-day fiable (RCE/contournement sandbox) se négocie souvent > 500 000 $.
Qui exploite un Chrome V8 zero-day comme CVE-2025-10585 ?
Trois sphères se croisent. Des équipes cybercriminelles monétisent l’accès aux sessions et comptes via publicité malveillante et sites compromis. Des groupes alignés sur des États emploient la faille avec parcimonie et précision pour franchir silencieusement les frontières techniques d’organisations ciblées. Entre les deux, des courtiers évaluent fiabilité et portée avant de chaîner les maillons d’un kit d’exploitation. L’attribution au TAG laisse penser que CVE-2025-10585 s’inscrit dans ce théâtre étatique.
Impact sur les utilisateurs : du clic ordinaire à la perte de souveraineté
Une seule page peut suffire à installer un code qui observe et détourne la vie d’un onglet. L’utilisateur ne voit rien ; le navigateur, lui, transporte cookies, tokens et extensions, autant d’éléments qui deviennent des leviers d’élévation et de persistance. Dans l’espace francophone, l’enjeu est systémique : services publics, messageries, consoles d’administration s’appuient sur le navigateur comme s’il était une zone de confiance. Un Chrome V8 zero-day rappelle qu’il ne l’est pas.
Que faire face à CVE-2025-10585 ? Repenser le navigateur comme un runtime hostile
Mettez à jour vers 140.0.7339.185/.186 (Windows/Mac) ou 140.0.7339.185 (Linux) via Aide → À propos de Google Chrome ; Android : 140.0.7339.155. Séparez les usages (profil/VM dédiée pour l’administratif et les opérations sensibles), réduisez la surface (désactivez WebAssembly si possible, limitez le JIT sur les tiers sensibles), gouvernez strictement les extensions (liste d’autorisation, audit, pas de sideloading) et alimentez votre veille avec les bulletins officiels.
En un trait : patcher vite, isoler ce qui compte, désencombrer le navigateur.
google-chrome --version (ou chromium --version selon distribution). Android : Google Play → Mises à jour → Chrome, puis relance.Bloc IT — politiques d’entreprise (exemple)
{
"ExtensionInstallAllowlist": ["<IDs>"],
"ExtensionInstallBlacklist": ["*"],
"URLAllowlist": ["https://intra.example.tld/*"],
"URLBlacklist": ["*"],
"DefaultPopupsSetting": 2,
"JavascriptAllowedForUrls": ["https://intra.example.tld/*"],
"AutofillAddressEnabled": false,
"PasswordManagerEnabled": false,
"WebAssemblyEnabled": false
}
Adapter aux besoins ; appliquer par GPO, Intune/MDM ou JSON de politiques gérées.
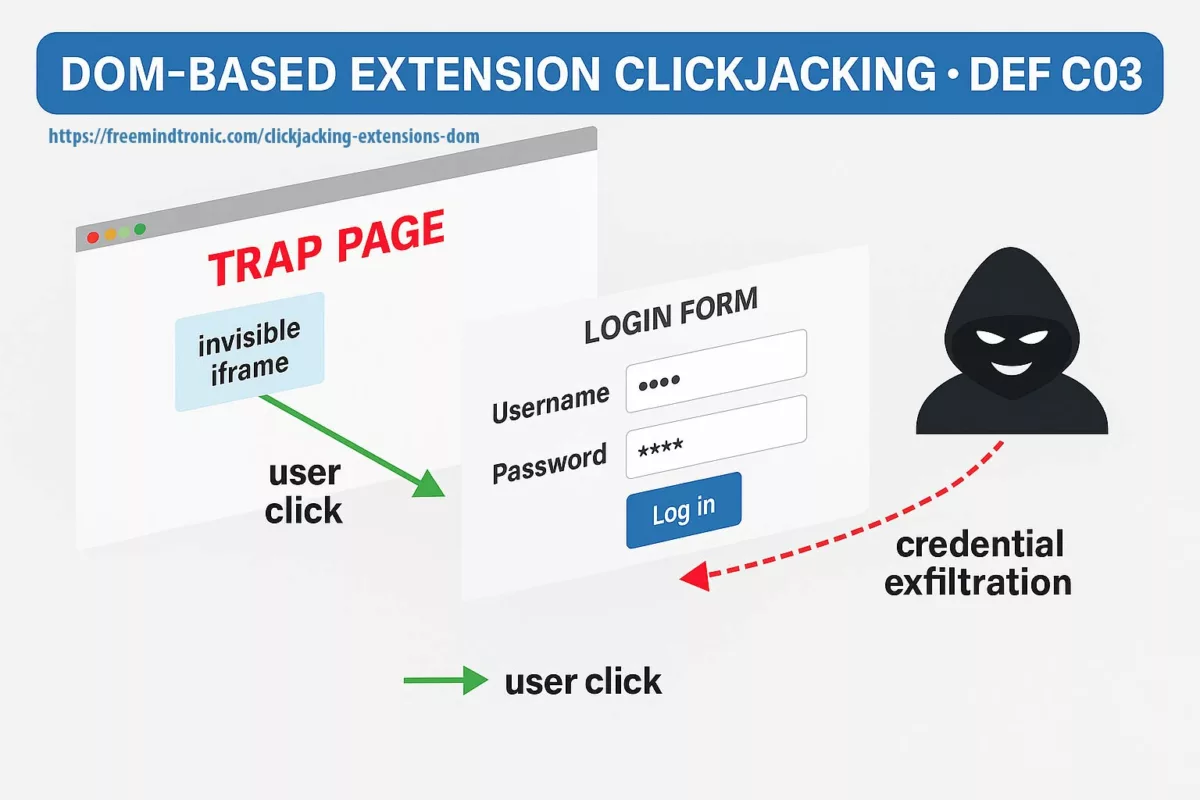
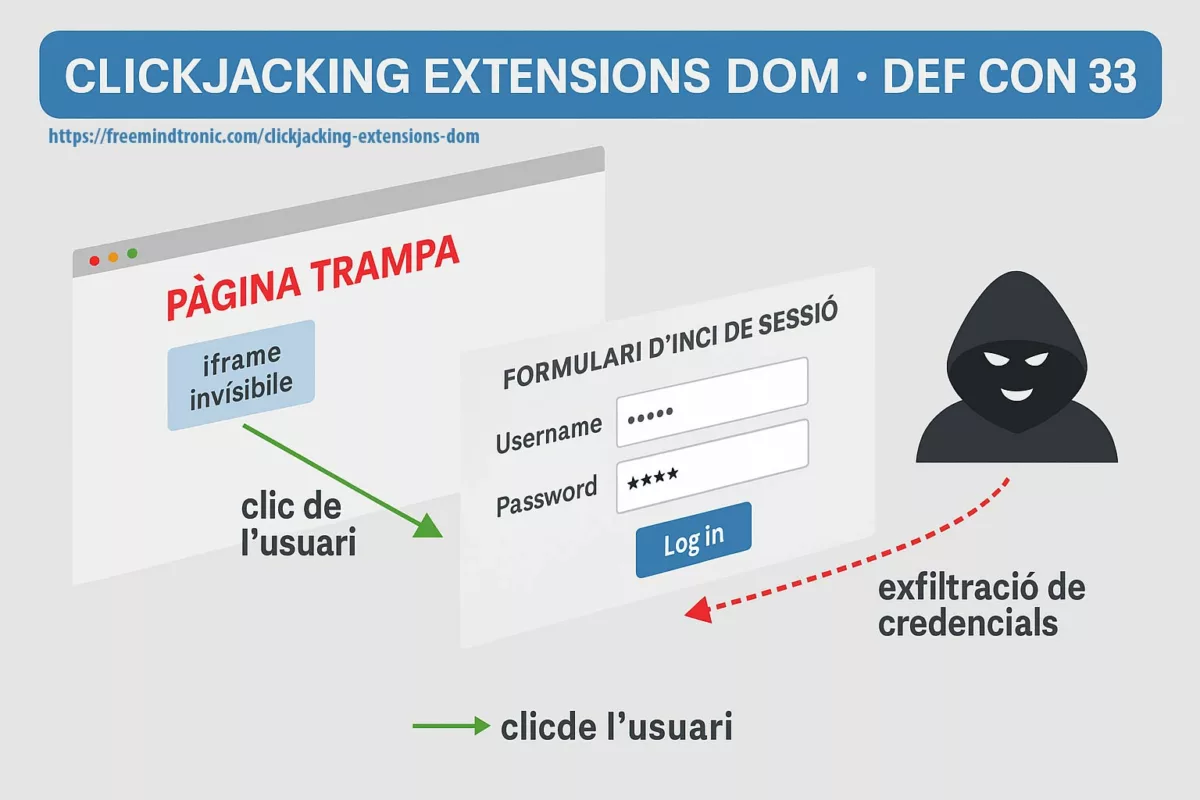
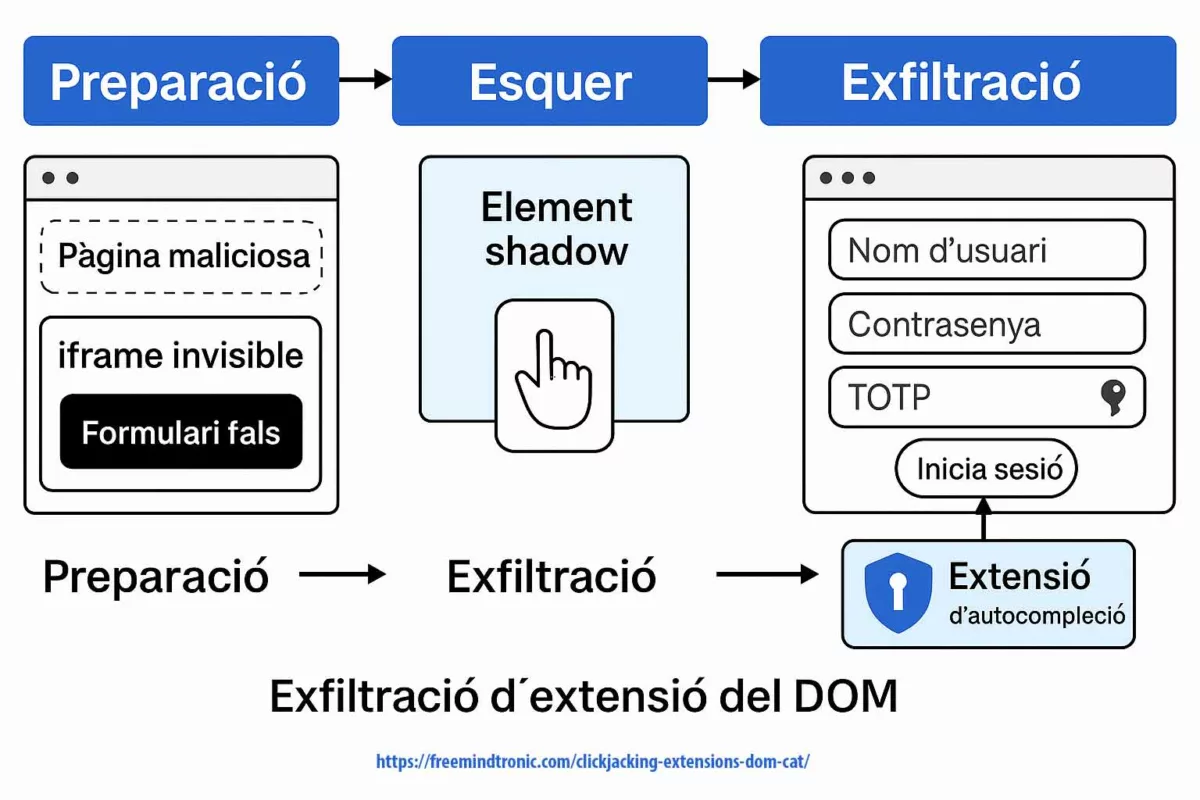
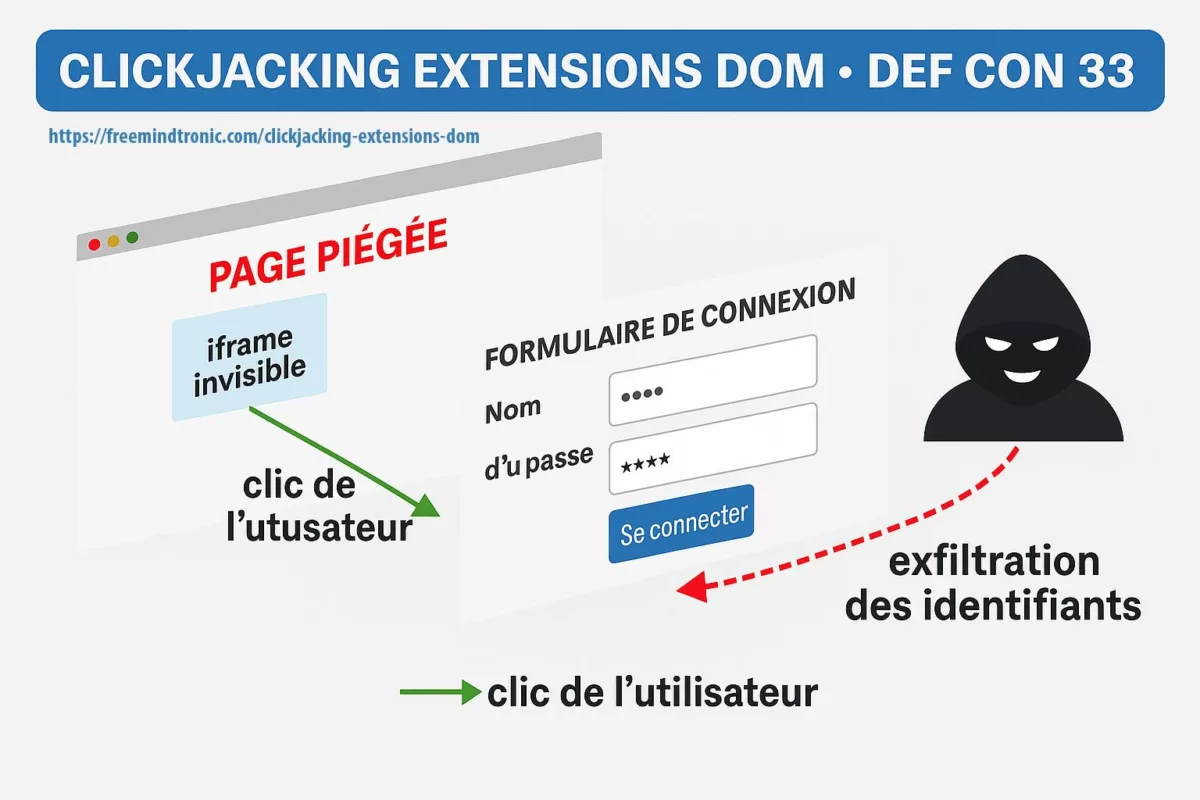
Pourquoi c’est lié au DOM — et à notre chronique Clickjacking
Exécution de code à distance via V8 (CVE-2025-10585) et le clickjacking d’extensions basé DOM mènent au même résultat : si des secrets passent par le DOM ou résident dans la mémoire du navigateur, ils deviennent accessibles. La première voie (RCE V8) prend le contrôle du processus ; la seconde (UI redressing/BITB) force l’injection de secrets dans un DOM piégé. Dans les deux cas, le DOM est la surface d’exfiltration.
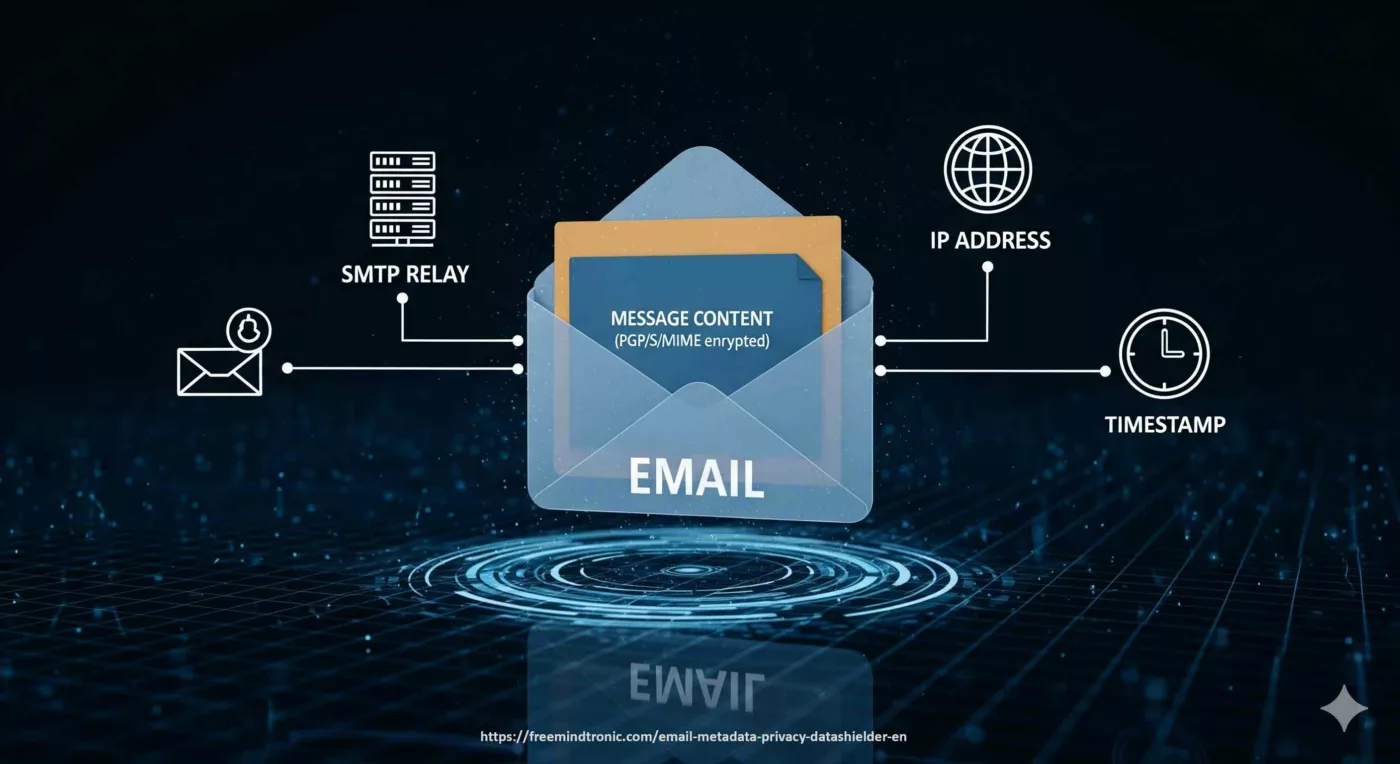
- Surface commune : DOM & mémoire du navigateur (autofill, cookies, tokens, passkeys synchronisées, extensions).
- Voies d’attaque : moteur (RCE V8) ou interface (overlays, iframes,
focus(), Shadow DOM). - Mitigation convergente : isolation des usages, gouvernance des extensions, et Zero-DOM (secrets hors DOM/processus, RAM éphémère, consentement physique).
À relier avec… ⤵
Clickjacking des extensions DOM : DEF CON 33 révèle 11 gestionnaires vulnérables
Versions corrigées & timeline
| Date | Canal / Plateforme | Version | Remarque |
|---|---|---|---|
| 17 sept. 2025 | Stable Desktop (Win/Mac) | 140.0.7339.185/.186 | CVE-2025-10585 listée, exploit in the wild reconnu. |
| 17 sept. 2025 | Stable Desktop (Linux) | 140.0.7339.185 | Déploiement progressif. |
| 17 sept. 2025 | Chrome pour Android | 140.0.7339.155 | Correctifs de sécurité alignés sur Desktop. |
Statistiques d’exposition
En août 2025, Chrome capte ~69 % de parts d’usage navigateur dans le monde. Concrètement : un Chrome V8 zero-day touche mécaniquement une part significative des internautes francophones — particuliers, administrations, entreprises. D’où l’importance de corriger vite et de compartimenter les usages sensibles.
Anatomie — V8 type confusion
Le curseur clignote. Derrière l’écran, le script a préparé la mémoire : tas groomés, objets mal étiquetés, garde-fous écartés. V8 prend une valeur pour ce qu’elle n’est pas ; la page devient un véhicule. Aucun message, aucun avertissement. L’exploit parle la langue du web ordinaire — événements, focus, rendu — et s’en sert pour atteindre l’exécution.
Après le franchissement — du conteneur au corridor
Une fois le code lancé, le navigateur cesse d’être une boîte et devient un couloir. Cookies et jetons deviennent des bagages ; les extensions, des portes latérales ; les sessions cloud, une enfilade de pièces ouvertes. L’attaquant n’a pas besoin d’un bélier, seulement d’un passage routinier.
Acteurs & incitations
D’un côté, des équipes cybercriminelles collectent des sessions revendues en lot. De l’autre, des groupes alignés sur des États visent avec précision, reliant des zero-days à des portails familiers. Entre les deux, des courtiers achètent des chaînes comme on achète de l’infrastructure : fiabilité, portée, discrétion.
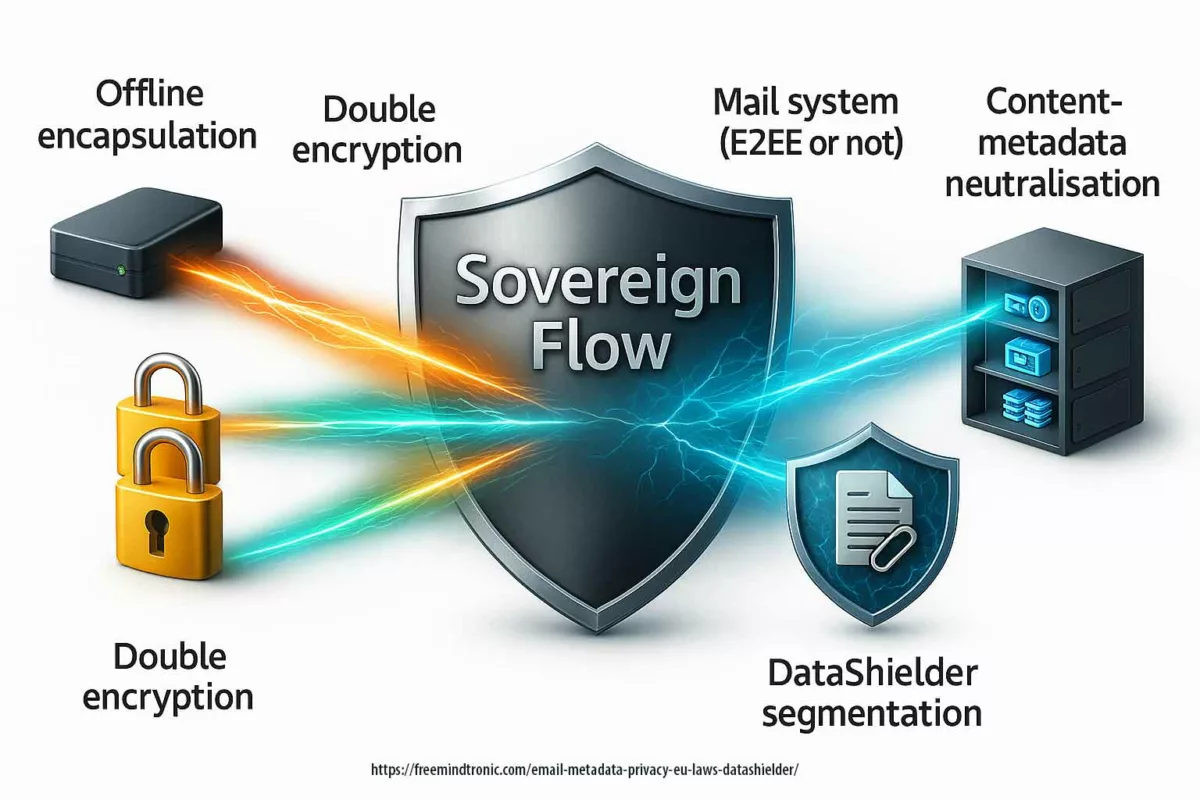
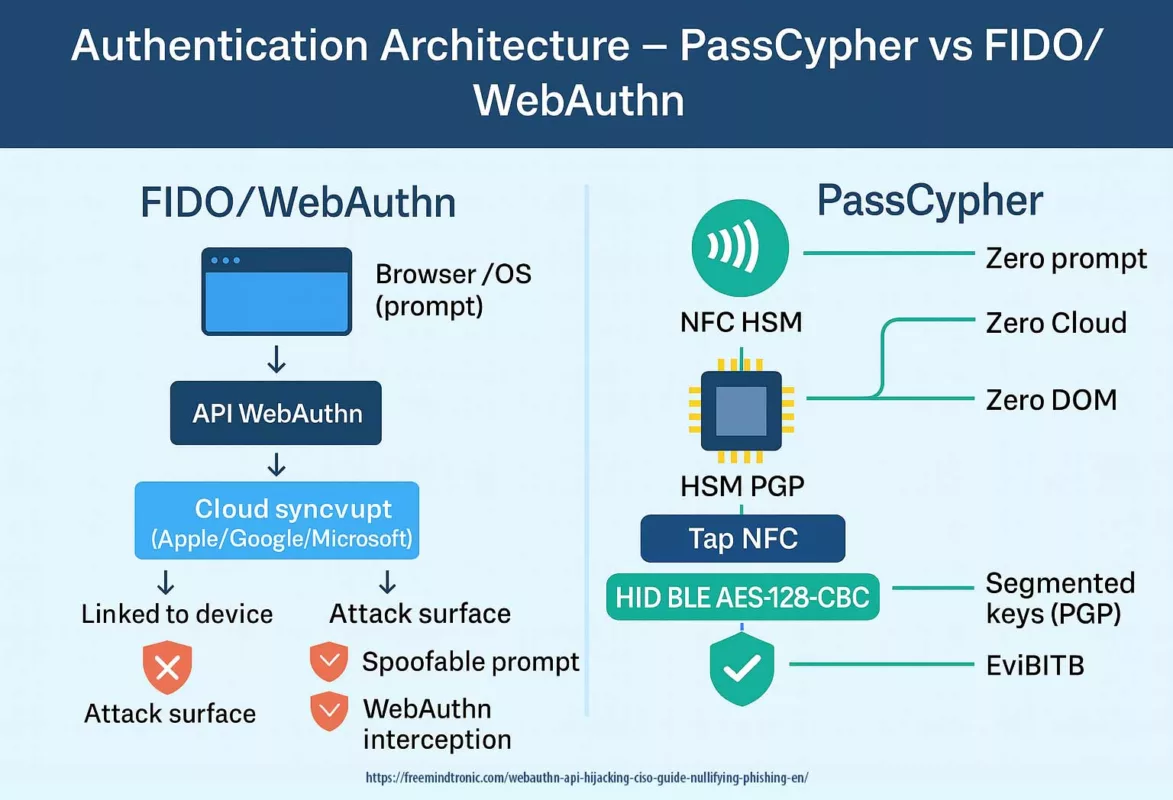
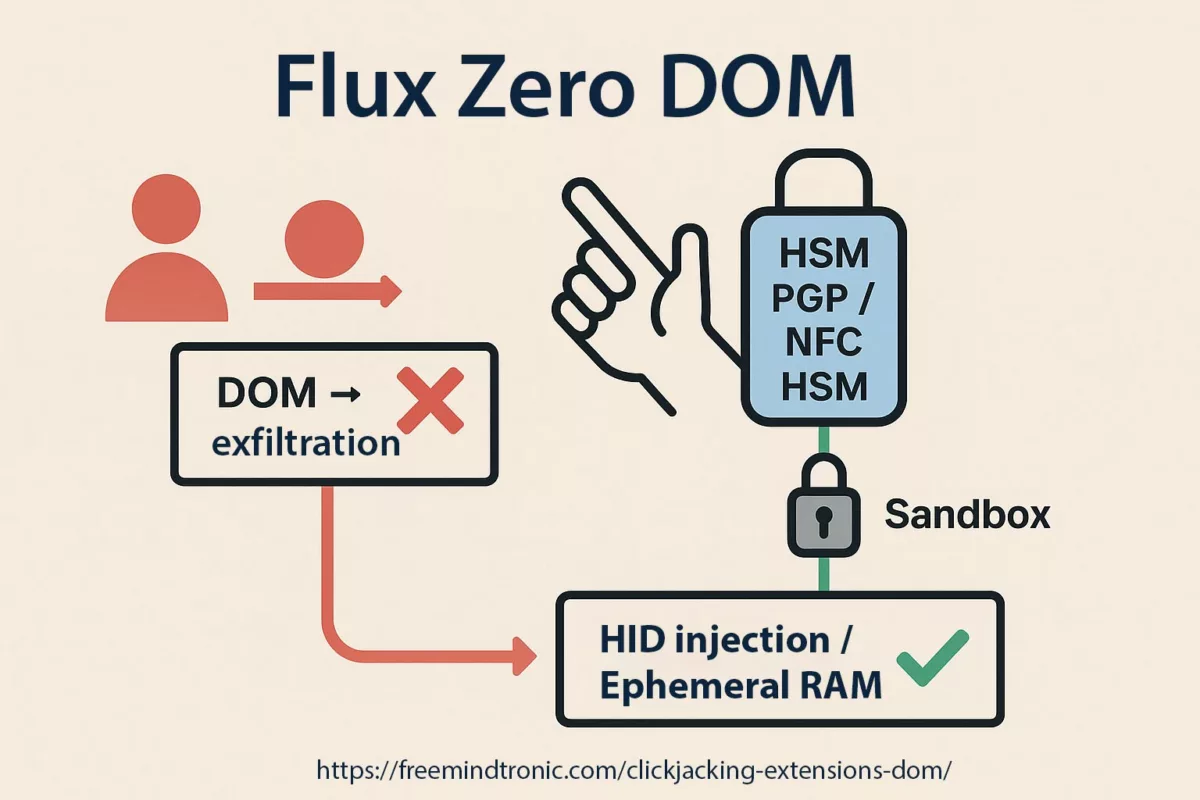
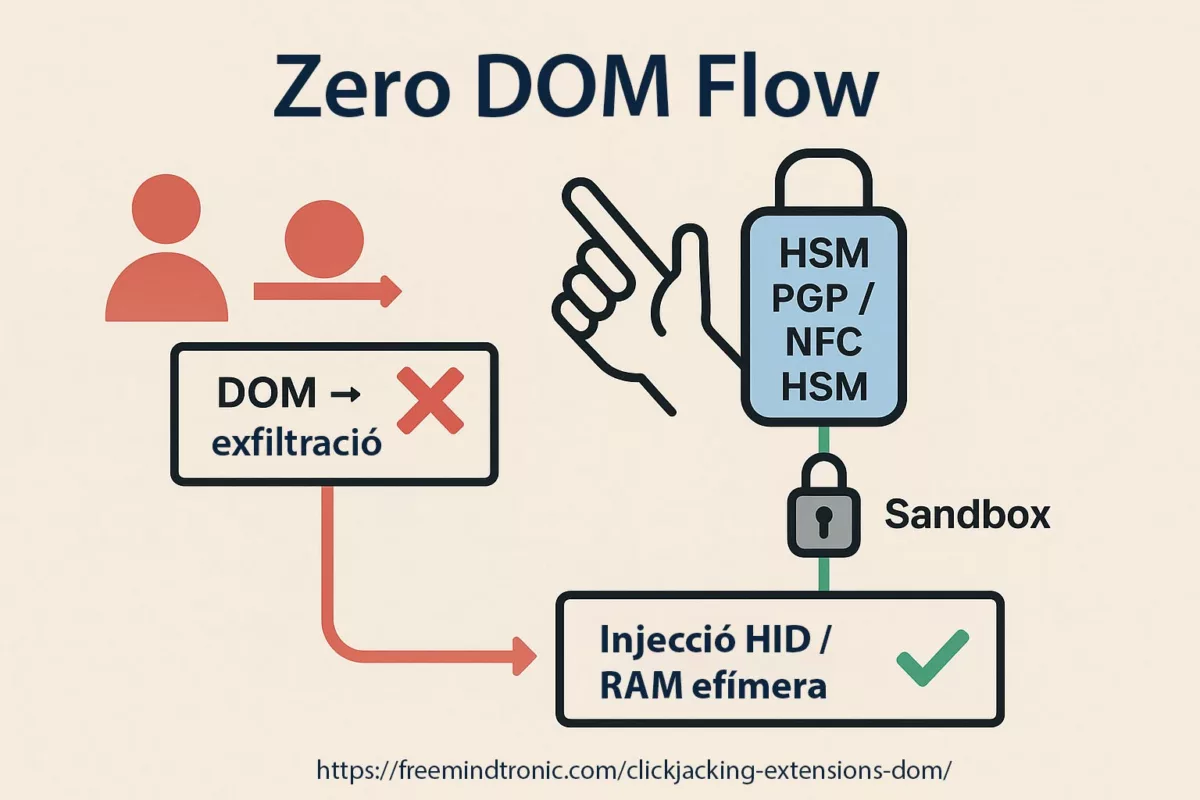
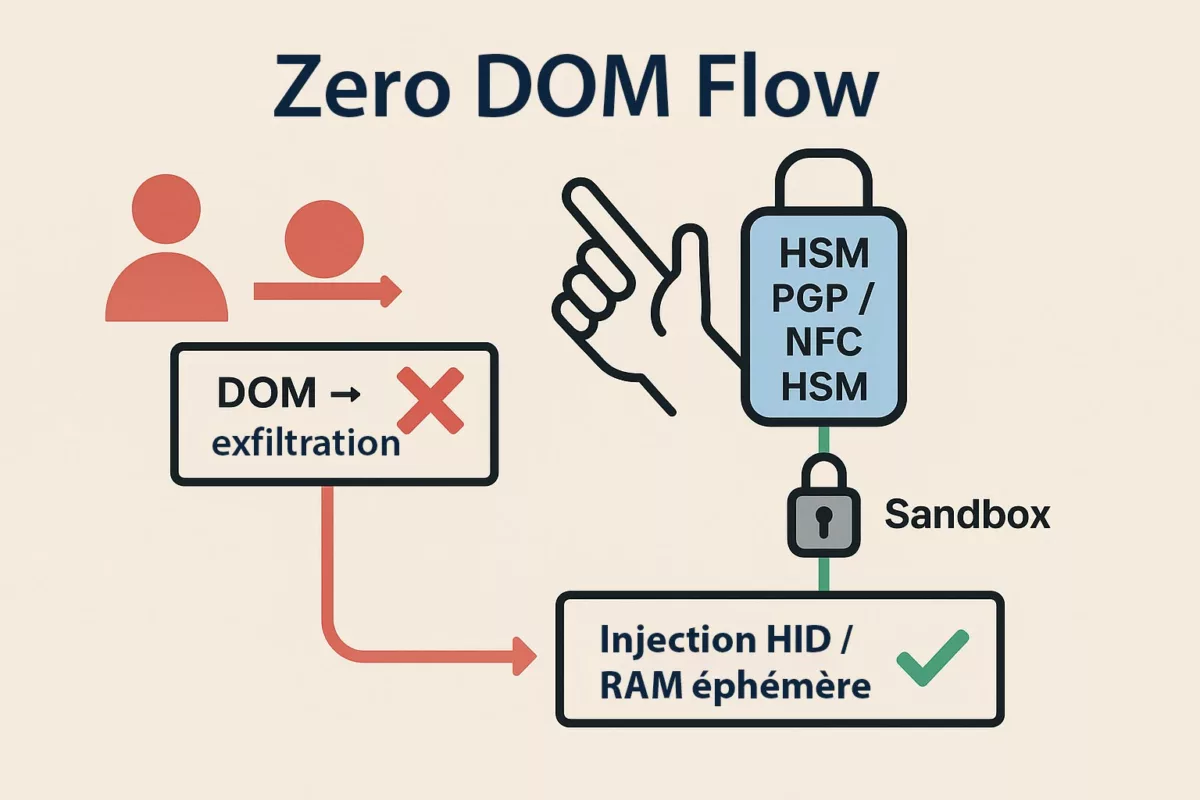
Réécriture souveraine (Zero-DOM)
Il existe une version de cette histoire où l’onglet compromet le navigateur… sans rien trouver à voler.
Dans cette version, les secrets :
- ne touchent jamais le DOM,
- ne résident pas dans le processus navigateur,
- ne circulent jamais en clair.
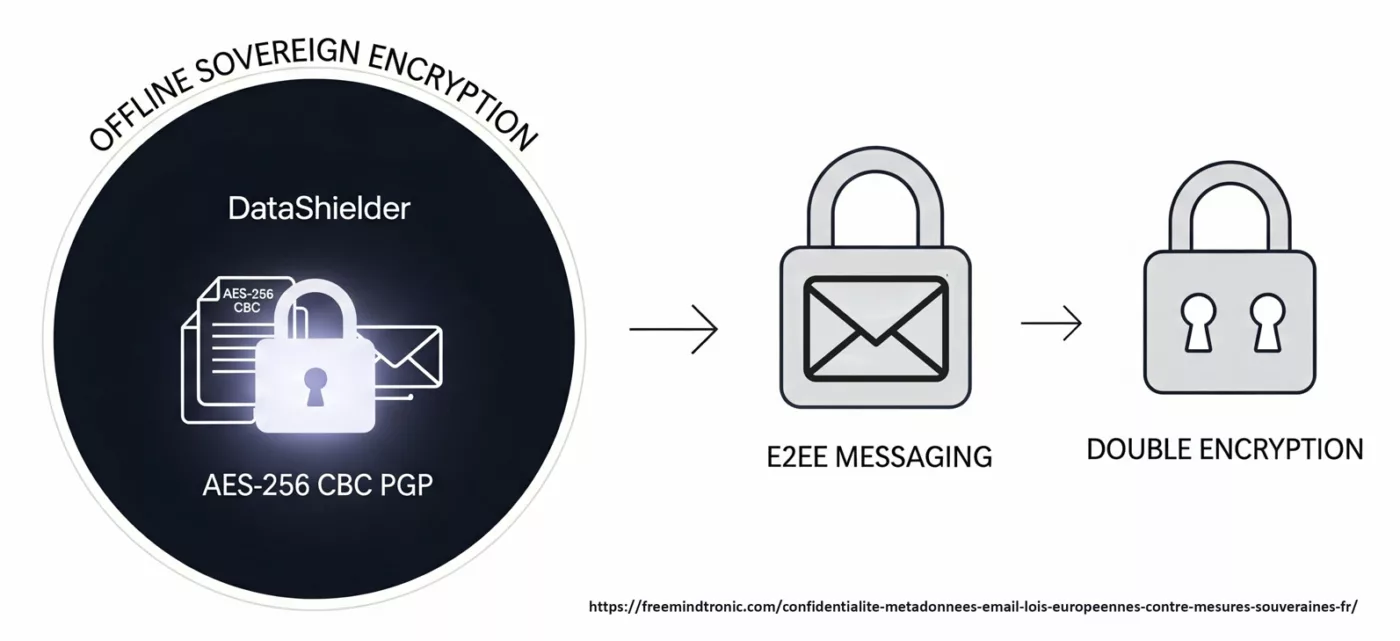
Identifiants, OTP, passkeys et clés privées vivent dans du matériel hors-ligne. Ils n’apparaissent qu’en fantômes éphémères en RAM, déclenchés par une action physique de l’utilisateur.
Technologies souveraines
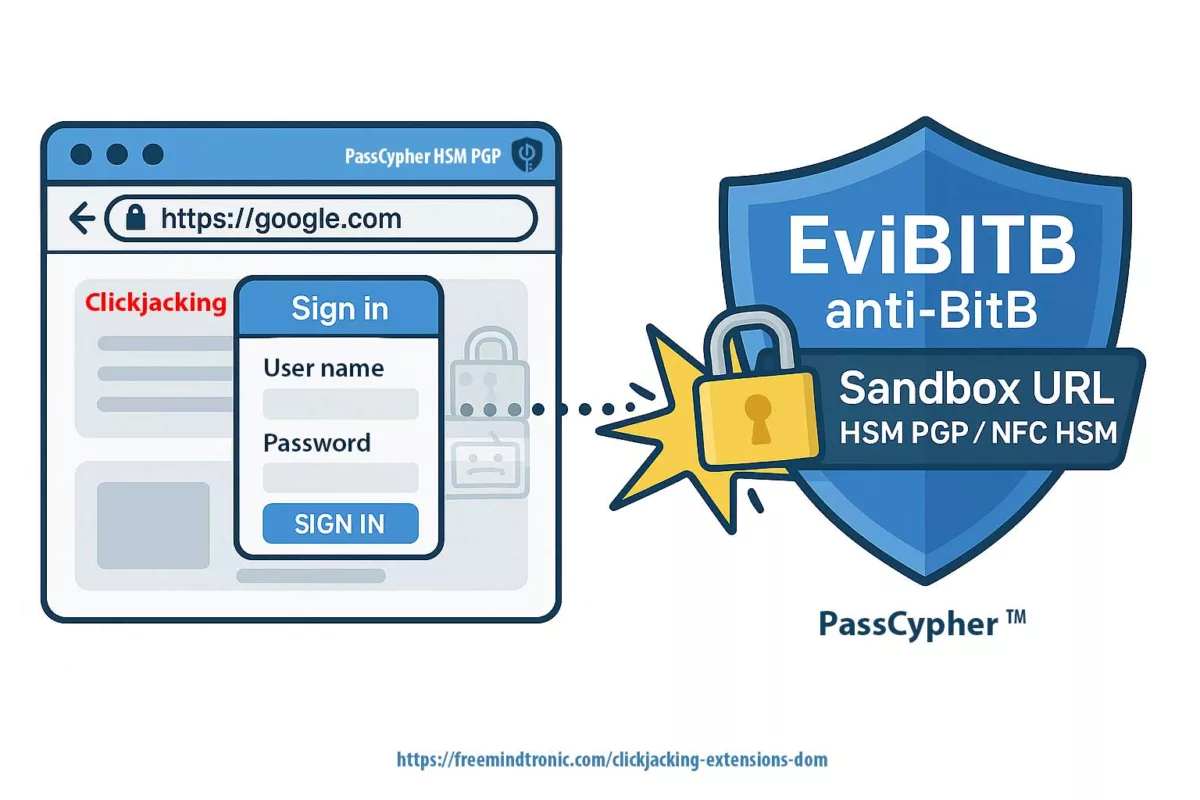
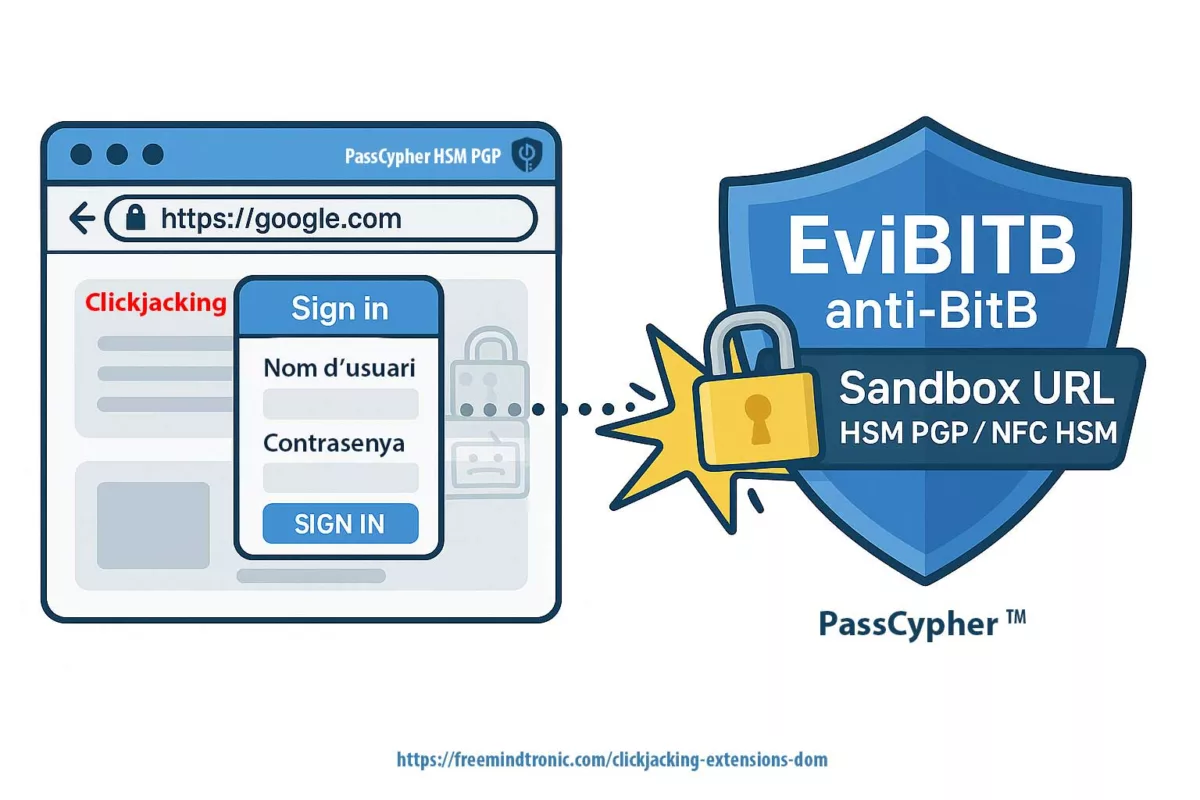
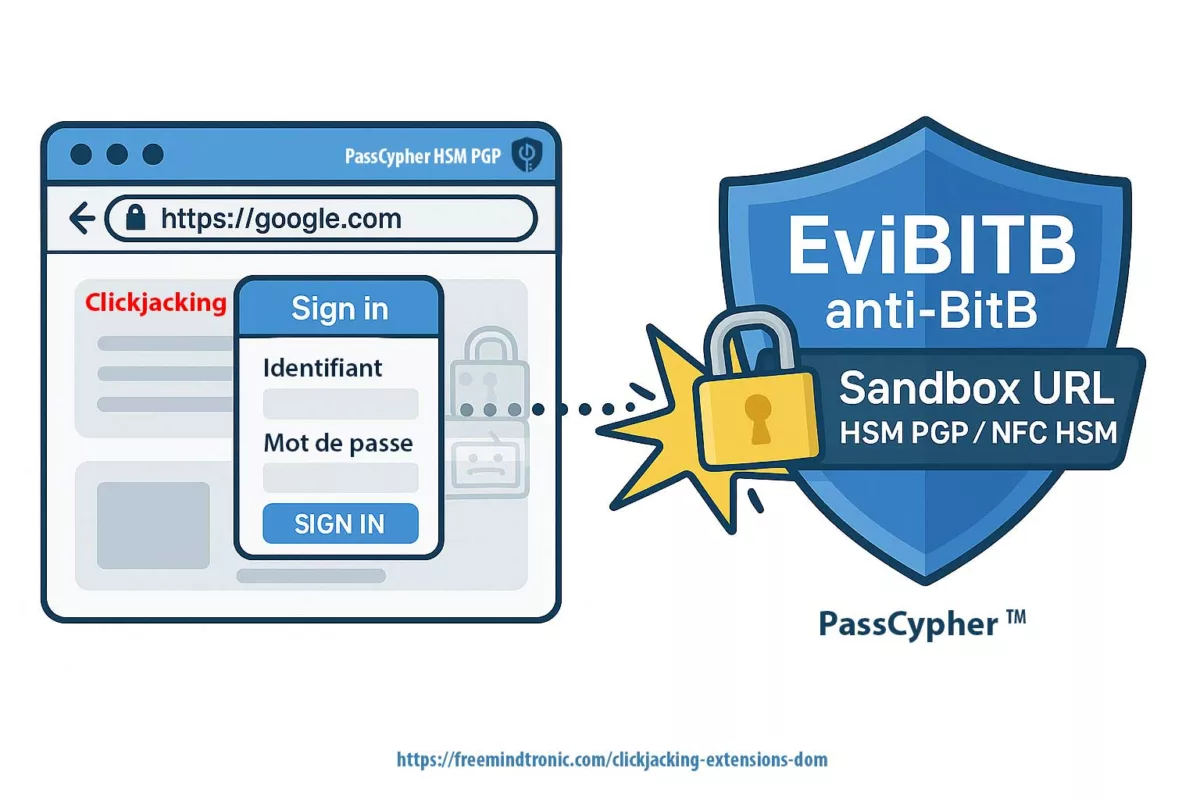
- PassCypher HSM PGP : chaque secret est lié à une URL attendue. Refus des écarts. Conteneurs chiffrés jusqu’à décision physique vérifiable.
- PassCypher NFC HSM : geste physique (tap NFC) avant toute injection. Le navigateur ne voit que le transport, jamais le contenu.
- SeedNFC HSM : cold wallet NFC HSM simplifié. Appairé à un smartphone Android NFC + émulateur HID-BLE, il injecte les clés publiques et privées de crypto-monnaies sans presse-papiers ni DOM.
- Émulateur de clavier Bluetooth HID-BLE — EviKeyboard BLE : signal BLE chiffré en AES-128-CBC. Appairé à l’application Freemindtronic (PassCypher, SeedNFC, DataShielder), il injecte les secrets en HID-BLE, hors DOM, hors clipboard. Les overlays et techniques de redressing deviennent inopérants.
Secrets hors navigateur + consentement physique = une zero-day V8 devient un incident confiné, pas une brèche système.
Signaux faibles
Ce que nous n’avons pas couvert
Cette chronique omet volontairement les PoC d’exploitation et les pas-à-pas de reproduction. Elle laisse de côté les bases sectorielles d’hardening et l’économie détaillée des marchés d’exploits. Objectif : exposer le risque systémique et montrer pourquoi une approche matérielle Zero-DOM change l’issue. Perspective — Concevez pour l’échec gracieux : supposez que le navigateur puisse tomber sans emporter votre identité. Ancrez les secrets dans le matériel, exigez un consentement physique, traitez chaque onglet comme provisoire.
FAQ CVE 2025-10585
Mon Chrome est-il à jour ?
Ouvrez Menu → Aide → À propos de Google Chrome. Recherchez 140.0.7339.185/.186 (Win/Mac) ou .185 (Linux).
Et Android ?
Mettez à jour vers 140.0.7339.155 via Google Play, puis relancez l’app. Vérifiez dans Paramètres → À propos → Version.
Edge, Brave, Opera, Vivaldi ?
Oui, ces navigateurs Chromium-based embarquent le moteur V8. Appliquez leurs mises à jour éditeur sans délai. Vérifiez les notes de version pour confirmer l’intégration du correctif CVE-2025-10585.
Faut-il désactiver WebAssembly ?
Si vos usages sensibles le permettent, oui : surface d’attaque réduite. En entreprise, appliquez la politique via GPO ou MDM, et limitez le JIT (Just-In-Time compilation) pour les profils à risque.
« Zero-DOM », qu’est-ce que ça change ?
Les secrets ne transitent pas par le DOM ni ne résident dans le processus navigateur. Ils restent en matériel hors-ligne (HSM) et n’apparaissent qu’éphémèrement en RAM sur action physique. Une RCE V8 trouve alors peu ou pas de matière à exfiltrer.
PassCypher, SeedNFC ou DataShielder — pourquoi maintenant ?
SeedNFC est un cold wallet NFC HSM (technologie EviPass NFC HSM).
PassCypher NFC HSM et DataShielder NFC HSM embarquent la même brique souveraine.
Ce que ça apporte face à CVE-2025-10585 (V8) et au BITB/overlays :
- Secrets hors navigateur : identifiants, OTP, clés privées jamais stockés dans le processus/DOM du navigateur.
- Consentement physique : chaque utilisation requiert un geste NFC/HSM ; sans action de l’utilisateur, rien ne sort.
- Appariement URL (PassCypher/DataShielder) : secrets liés à des URL attendues ; en cas d’écart (phishing/BITB), le HSM refuse.
- Injection anti-keylogger : mode HID-BLE via port USB, signal chiffré AES-128-CBC, sans presse-papiers ni DOM.
- Éphémère en RAM : les données ne persistent pas côté hôte ; l’attaque « drive-by » V8 trouve peu de matière à exfiltrer.
Modes d’usage :
- Android NFC + application Freemindtronic (inclut PassCypher, SeedNFC, DataShielder) pour piloter le HSM.
- HID-BLE : émulation de clavier Bluetooth Low Energy vers le poste, compatible USB, champs de saisie standards.
À retenir :
- Ne remplace pas les mises à jour Chrome/Chromium ; complète la défense en retirant les secrets du navigateur.
- Idéal pour comptes à privilèges, consoles d’admin, messageries sensibles et transactions critiques.
Prérequis : smartphone Android NFC, app Freemindtronic, appareil HSM (SeedNFC / PassCypher NFC HSM / DataShielder NFC HSM).
Les secrets ne sont pas stockés sur le téléphone ; ils restent scellés dans le NFC HSM.
Comment vérifier si mon navigateur est vulnérable ?
Consultez les bulletins officiels : [Chrome Releases — 17 juin 2025](https://chromereleases.googleblog.com/2025/06/stable-channel-update-for-desktop_17.html) et [CERT-FR — CVE-2025-10585](https://www.cert.ssi.gouv.fr/avis/CERTFR-2025-AVI-0518/). Comparez votre version avec celles corrigées.
Dois-je changer de navigateur ?
Changer n’est pas suffisant. Tous les navigateurs Chromium partagent V8. La posture Zero-DOM et la séparation des rôles sont plus efficaces que le simple remplacement.
Ouvrez Menu → Aide → À propos de Google Chrome. Recherchez 140.0.7339.185/.186 (Win/Mac) ou .185 (Linux).
PassCypher NFC HSM et DataShielder NFC HSM embarquent la même brique souveraine.
Ce que ça apporte face à CVE-2025-10585 (V8) et au BITB/overlays :
- Secrets hors navigateur : identifiants, OTP, clés privées jamais stockés dans le processus/DOM du navigateur.
- Consentement physique : chaque utilisation requiert un geste NFC/HSM ; sans action de l’utilisateur, rien ne sort.
- Appariement URL (PassCypher/DataShielder) : secrets liés à des URL attendues ; en cas d’écart (phishing/BITB), le HSM refuse.
- Injection anti-keylogger : mode HID-BLE via port USB, signal chiffré AES-128-CBC, sans presse-papiers ni DOM.
- Éphémère en RAM : les données ne persistent pas côté hôte ; l’attaque « drive-by » V8 trouve peu de matière à exfiltrer.
Modes d’usage :
- Android NFC + application Freemindtronic (inclut PassCypher, SeedNFC, DataShielder) pour piloter le HSM.
- HID-BLE : émulation de clavier Bluetooth Low Energy vers le poste, compatible USB, champs de saisie standards.
À retenir :
- Ne remplace pas les mises à jour Chrome/Chromium ; complète la défense en retirant les secrets du navigateur.
- Idéal pour comptes à privilèges, consoles d’admin, messageries sensibles et transactions critiques.
Prérequis : smartphone Android NFC, app Freemindtronic, appareil HSM (SeedNFC / PassCypher NFC HSM / DataShielder NFC HSM).
Les secrets ne sont pas stockés sur le téléphone ; ils restent scellés dans le NFC HSM.
Changer n’est pas suffisant. Tous les navigateurs Chromium partagent V8. La posture Zero-DOM et la séparation des rôles sont plus efficaces que le simple remplacement.
Glossaire
V8 — Moteur JavaScript/WebAssembly de Chrome et navigateurs Chromium.
Type confusion — Bug mémoire où un objet est traité comme un autre type ; mène à corruption contrôlée.
HID-BLE — Émulation de clavier en Bluetooth Low Energy ; permet l’injection de secrets “comme si” tapés au clavier, sans presse-papiers et hors DOM.
RCE — Remote Code Execution : exécution de code arbitraire à distance.
Zero-day — Vulnérabilité exploitée avant correctif public.
DOM — Modèle objet de document : structure mémoire des pages web.
BITB — Browser-in-the-Browser : faux cadres imitant une fenêtre d’authentification.
WebAssembly — Format binaire portable exécuté côté navigateur.
JIT — Just-in-Time compilation : optimise, mais agrandit la surface d’attaque.
Zero-DOM — Doctrine Freemindtronic : aucun secret dans le DOM/Processus ; libération RAM éphémère, ancrage matériel (HSM/NFC).
Références officielles :
• Chrome Releases — Stable Desktop (17 sept. 2025) (CVE-2025-10585).
• Chrome Releases — Android (17 sept. 2025).
• Chrome Releases — Stable Desktop (14 mai 2025) (CVE-2025-4664).
• Chrome Releases — Extended Stable (3 juin 2025) (CVE-2025-5419).
• cve.org — CVE-2025-2783. ([Chrome Releases][1])
• Statistiques : StatCounter — Monde (août 2025). ([StatCounter Global Stats][2])
Changelog
- 2025-09-19 (v1.2) — Ajout liens officiels pour chaque CVE ; consolidation FAQ Android ; section statistiques ; signaux avec barres 4 px colorées ; bloc politiques entreprise ; snippet « vérifier sa version » ; timeline structurée.
- 2025-09-19 (v1.1) — Harmonisation des versions 140.0.7339.x (Desktop/Android) ; ancrages FR.
- 2025-09-19 (v1.0) — Publication initiale : « Ton navigateur était déjà espionné »
Check-list admins (entreprise)
- Forcer la relance du navigateur après mise à jour ; fenêtre de redémarrage contrôlée.
- Désactiver l’autofill sur périmètres sensibles ; audit des permissions d’extensions ; pas de sideloading.
- Segmenter par profil/VM : navigation standard vs opérations à privilèges (consoles, SI critiques).
- Désactiver WebAssembly là où non nécessaire ; limiter le JIT sur périmètres critiques.
- Déployer une solution de secrets hors-navigateur (HSM/NFC) pour MFA et gestion d’identifiants.
Précisions techniques : SeedNFC est un cold wallet NFC HSM intégrant EviPass NFC HSM (également présent dans PassCypher NFC HSM et DataShielder NFC HSM).Il est compatible avec l’émulation clavier HID-BLE via port USB, avec un signal BLE chiffré AES-128-CBC, et s’emploie avec l’app Freemindtronic (Android NFC) pour l’injection de secrets anti-keylogger hors presse-papiers et hors DOM.Objectif : permettre au lecteur d’évaluer en toute connaissance de cause d’éventuels conflits d’intérêts.