Résumé express — 766 trillion years to find randomly generated 20-character code
⮞ Summary
This express digest takes ≈ 3–4 minutes. It summarizes the simulation that estimates how long a brute-force attempt would take to find a random 20-character password built from printable ASCII symbols.
⚡ The Discovery
Using Bob Beeman’s Password Strength Calculator (default parameters, 60–109 billion attempts/sec), a random 20-character password drawn from 94 symbols requires approximately 766,076,000,000,000,000 years (~766 trillion years) to be found by brute force.
✦ Immediate Impact
- Demonstrates practical infeasibility of brute force against long, full-ASCII random passwords.
- Shows how specialized GPU clusters (e.g. Radeon City) change the practical attack surface for fast hash algorithms.
- Frames EviPass-generated codes as effectively resistant to brute-force when combined with HSM/NFC protections.
⚠ Strategic Message
Randomness + length + secure storage (HSM/NFC) are decisive. Short, human-memorable passwords remain fragile; hardware-anchored secrets and slow, salted algorithms are required for resilient protection.
⎔ Sovereign Countermeasure
Prefer hardware-managed secrets (EviPass / EviTag / EviCard), offline HSM anchoring, and slow key-derivation functions (bcrypt/PBKDF2/Argon2) to mitigate brute-force risk.
Reading Parameters
Express summary reading time: ≈ 4 minutes
Advanced summary reading time: ≈ 6 minutes
Full chronicle reading time: ≈ 36 minutes
Last updated: 2025-10-02
Complexity level: Advanced / Expert
Technical density: ≈ 73%
Languages: CAT · EN · ES · FR
Linguistic specificity: Sovereign lexicon — high technical density
Accessibility: Screen-reader optimized — semantic anchors included
Editorial type: Strategic Chronicle — Digital Security ·Technical News· Quantum Computing · Cyberculture
About the author: Jacques Gascuel, inventor and founder of Freemindtronic®, embedded cybersecurity and post-quantum cryptography expert.
A pioneer of sovereign solutions based on NFC and hardware encryption, his work focuses on system resilience against quantum threats and multi-factor authentication without cloud dependency.
it will evolve with new attacks, standards, and technical demonstrations related to quantum computing.
Check back regularly.
Résumé avancé — Simulation, Radeon City & cost of brute force
⮞ Summary
Numbers, reference machines and economic scale: what 766 trillion years means in practice.
Why we used Bob Beeman’s simulator
We used the Password Strength Calculator by Bob Beeman (last updated January 4, 2013) available on www.bee-man.us. The code is public and transparent, allowing parameter control (attempts/sec, symbol set, length).
Radeon City: reference attacker
⮞ Summary
Radeon City (Jeremi Gosney / Stricture Consulting) used five servers with AMD Radeon HD7970 GPUs to reach ~350 billion NTLM guesses/sec in 2012 — a practical baseline for fast algorithms.
Simulation parameters & formula
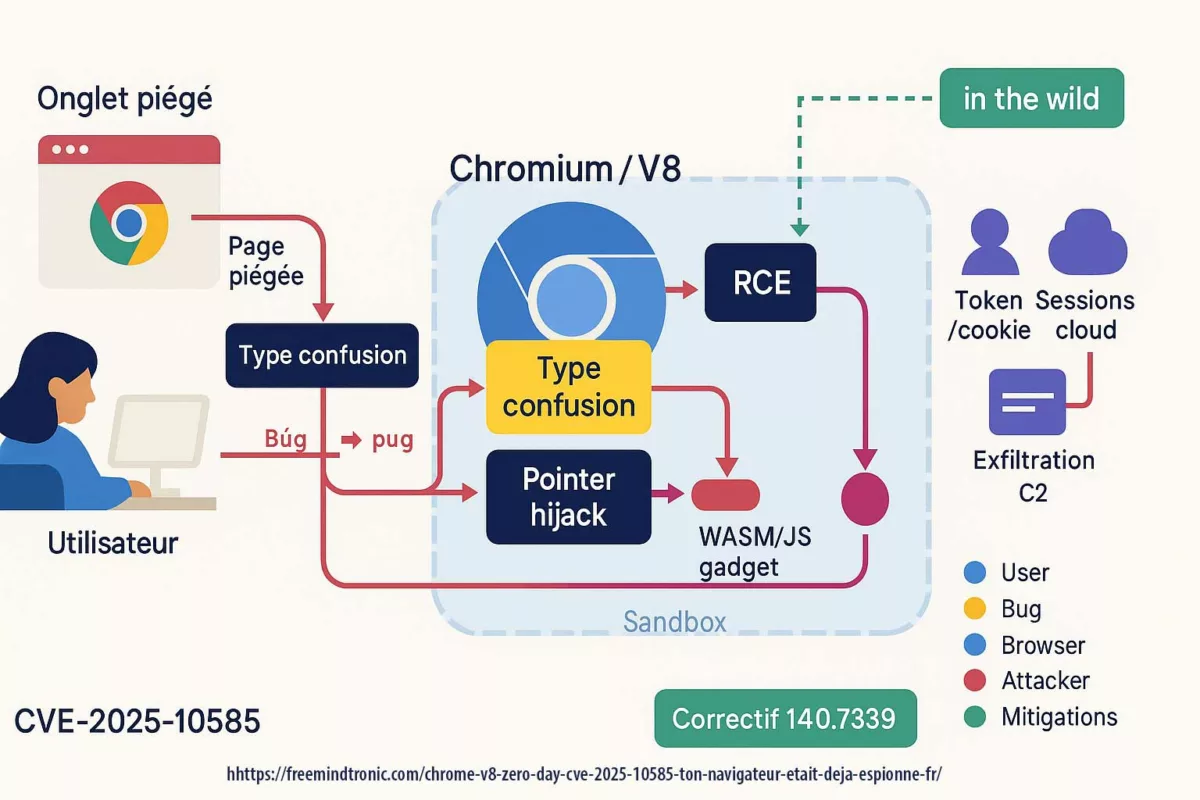
We applied the common brute-force formula: a^b / (c * 2), where “a” = possible symbols (94), “b” = password length (20), and “c” = hash computations/sec. With a 50% chance benchmark (divide by 2) and default Beeman values (60–109 billion/sec), the result is ~766,076,000,000,000,000 years.
Financial implications
Using Gosney’s reference machine cost (~$30,000 in 2012 for the Radeon cluster at scale), extrapolating to achieve brute force capabilities to invert such a password within feasible time would require astronomical investment — the article estimates nearly $25 billion to reach parity with the simulation’s target workload, a figure compared to global military spending references.
Beyond brute force
This analysis focuses strictly on brute force. Other countermeasures (physical blockchain anchoring, jamming, HSM protections) further increase attack cost and complexity — topics to be addressed in follow-ups.
- 🔝 Back to top
- Executive Summary
- Advanced Summary
- Headline & Origin
- Discovery & Context
- Methodology
- Radeon City
- Advantages & Disadvantages
- Simulation Parameters & Results
- ANSSI Simulator
- Password Generation Options
- Use Cases — EviPass
- References
- Strategic Outlook
- What We Didn’t Cover
- Weak Signals
- Glossary
- FAQ
Key Insights
- Full-ASCII 20-char random passwords are effectively uncrackable by brute force with current public GPU technology.
- Fast hash algorithms (NTLM, MD5, SHA1) massively reduce brute-force cost; prefer slow, salted KDFs.
- Hardware anchoring (NFC HSM / EviPass family) materially increases attack complexity and cost.
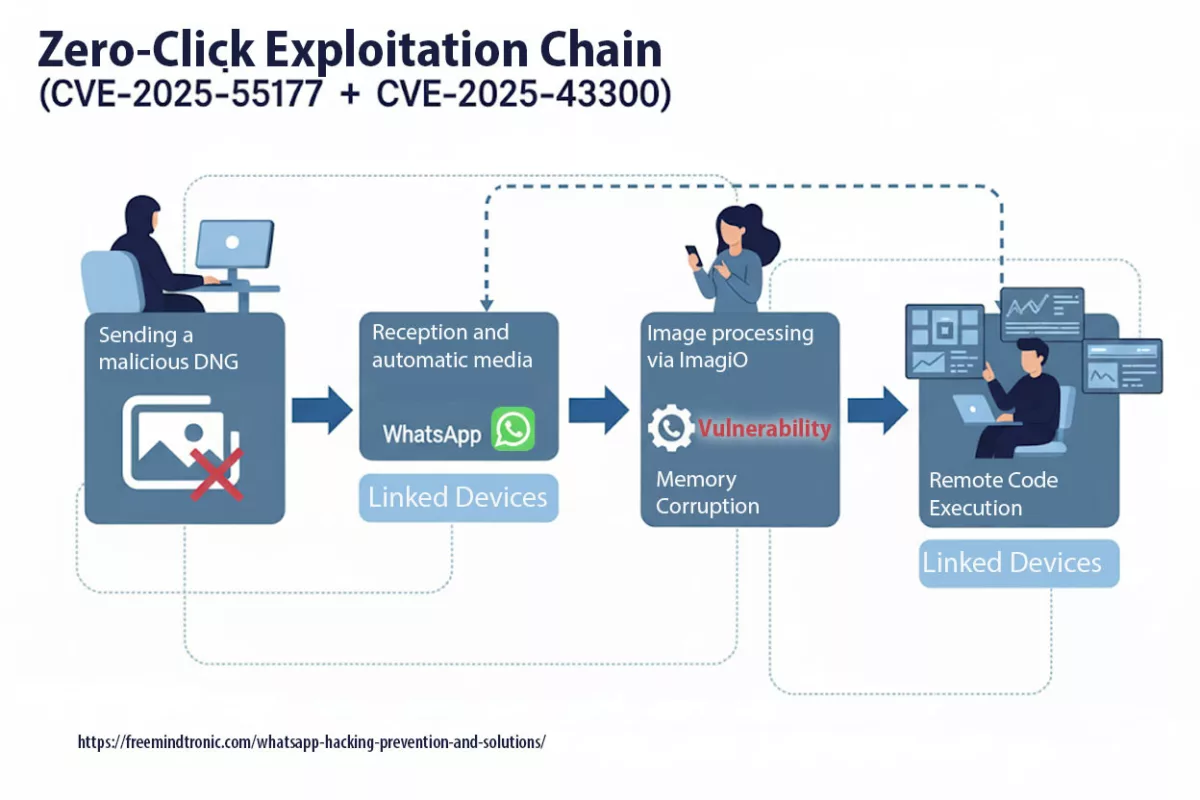
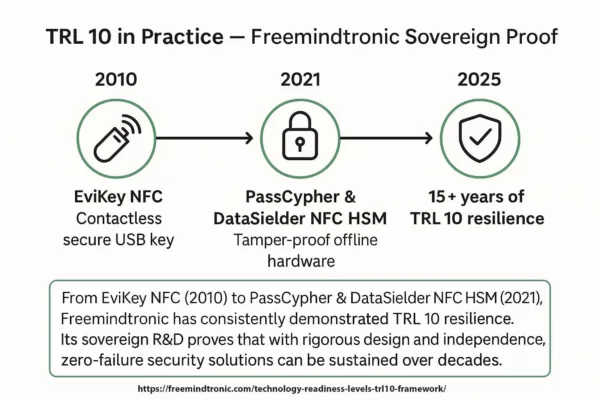
766 trillion years to find randomly generated 20-character code
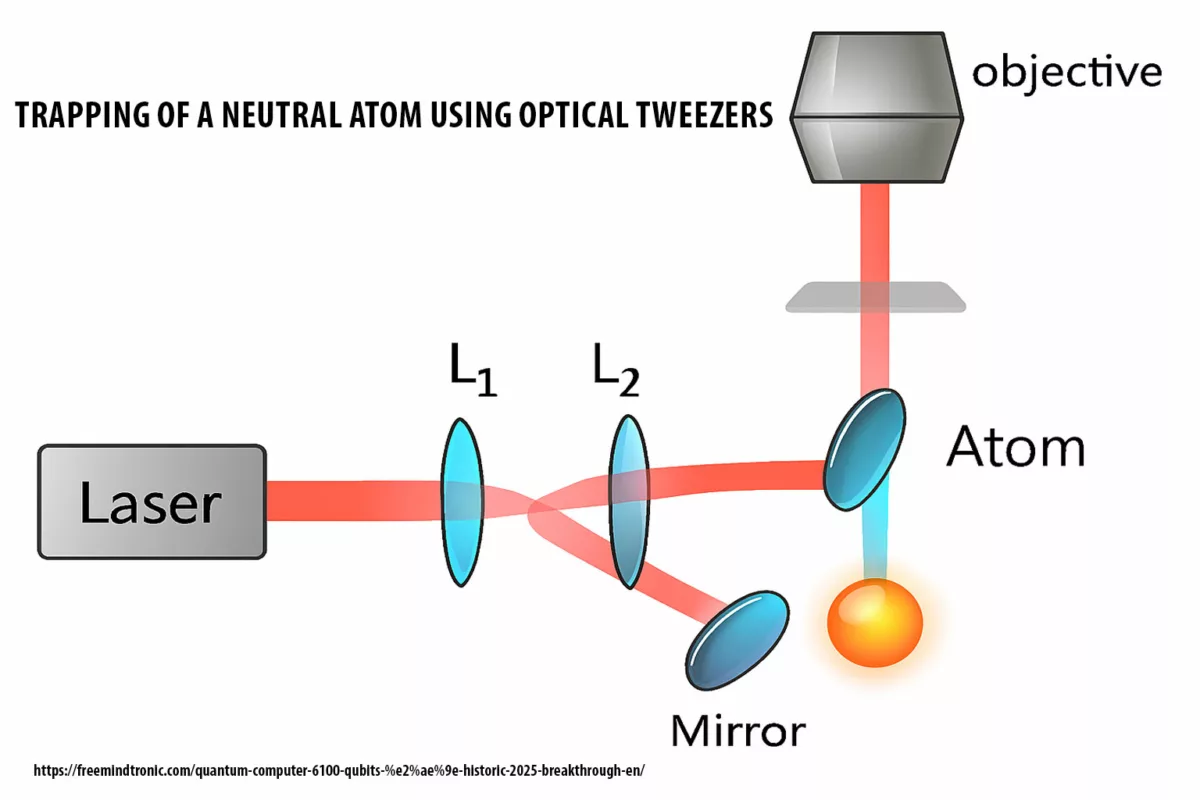
766 trillion years to find randomly generated 20-character code is the result of a simulator to find a 20-character generated by technology EviPass. The age of the universe is estimated at only 14 billion years, this gives you an idea of comparison.
Discovery & Context
⮞ Summary
We ran Bob Beeman’s Password Strength Calculator with default parameters (60–109 billion attempts/sec) and a 94-symbol alphabet for a 20-character random string. The computed time to find the password by brute force is ~766 trillion years.
How did I find this result that you can control on your own?
We used the Password Strength Calculator developed by Bob Beeman [1] which was last updated on January 4, 2013. This simulator is freely available on the www.bee-man.us website as well as the source code used.
Why We Chose Bob Beeman’s Simulator
In our quest to estimate the time it would take to crack a random 20-character code, we had several simulation tools at our disposal, including lastbit.com [2], password-checker.online-domain-tools.com [3], and ANSSI’s [4] simulator from ssi.gouv.fr. However, we ultimately opted for Mr. Bob BEEMAN’s simulator due to its transparent calculation method and its technical approach to brute force attacks.
Acknowledging Mr. Bob BEEMAN
Before delving into the details of our simulation, we must extend our gratitude to Mr. Bob BEEMAN for making his code freely accessible and copyable while upholding his copyrights, as explained on his website. We hope our research can contribute to his already impressive achievements, including a record-breaking 15-millisecond feat.
Reference to Ultra-Powerful Computers
To provide you with a comprehensive understanding of the state-of-the-art technology for brute force attacks in 2013, we examined Bob Beeman’s simulator’s reference to an ultra-powerful computer designed in 2012 specifically for password cracking.
Considering Computational Capacity
Bob Beeman’s simulator takes into account the computational capabilities of computers, including the 2012 design, for executing brute force attacks on passwords. It allows for adjustments in the “Values of Hacker: Axes/Second,” providing a valuable point of reference and comparison.
Staying with Default Parameters
For the sake of consistency, we maintained the default example provided by Bob Beeman, which assumed a rate of 60-109 (billion) attempts per second.
Radeon City: Revolutionizing Password Security
Jeremi Gosney, the visionary behind Radeon City and the CEO of Stricture Consulting Group, sought to create a powerhouse capable of cracking passwords with unprecedented speed and efficiency. His solution? Virtual OpenCL (VCL), a groundbreaking virtualization software. Gosney assembled five servers, each armed with five AMD Radeon HD7970 graphics cards, interconnected through VCL. The cluster, aptly named Radeon City, was born at a cost of approximately $30,000 in 2012.
Radeon City Specifications

Here’s a snapshot of Radeon City’s technical specifications:
- Servers: 5
- Graphics Cards: 25 AMD Radeon GPUs
- Model: AMD Radeon HD7970
- Memory: 3 GB GDDR5
- Clock Speed: 925 MHz
- Compute Units: 32
- Stream Processors: 2048
- Peak Performance: 3.79 TFLOPS
- Virtualization Software: Virtual OpenCL (VCL)
- Password-Cracking Software: ocl-Hashcat Plus
- Cost: $30,000 (2012)
This powerhouse enables Radeon City to achieve unprecedented speeds in password cracking, making it a game-changer in the realm of data security.
Advantages & Disadvantages of Radeon City
⮞ Summary
A high-throughput GPU cluster is powerful and flexible, yet costly and demanding to operate.
Advantages
- Power: can attack both fast and, to a degree, slow algorithms with extensive rules and wordlists.
- Flexibility: supports many attack modes (brute-force, dictionary, combinator, hybrid).
- Innovation: virtualization (VCL) overcame hardware limits in 2012.
Disadvantages
- Cost: build & operation are expensive (electricity, cooling).
- Noise & Cooling: requires specialized environment.
- Ethics: legal/ethical concerns about use.
Simulation Parameters and Results
To calculate the estimated time required to find a 20-character code with 94 symbols, we used the formula:
a^b / (c * 2)
Where:
- “a” represents the number of possible characters,
- “b” denotes the number of characters in the password,
- “c” indicates the number of hash calculations achievable per second.
By selecting 94 symbols, a password length of 20 characters, and a 50% probability of success compared to the theoretical result, our simulation yielded an astonishing result: 766.076,000,000,000,000 years or 766 trillion [5] years.
Understanding the Financial Implications
This simulation approach not only provides insights into the time required but also sheds light on the financial investments necessary to establish a computer system capable of cracking such a password.
Consider this: The reference computer, as configured by Gosney, relies on a pool of 25 virtual AMD GPUs to crack even robust passwords. Yet, a single unit of this type, priced at approximately $30,000 in 2012, can generate just 348 billion hashes of NTLM passwords per second. To achieve results within the realm of 766 trillion years, one would need to acquire multiple such machines.
Hence, to decipher only a 20-character password generated with EviPass technology, residing within an EviTag NFC HSM or EviCard NFC HSM device, an investment of nearly $25 billion would be required. A remarkable comparison, given that global military expenses were estimated at 1.7 billion dollars [6].
Beyond Brute Force
It’s important to note that this test focused solely on brute force attacks without taking into account the activation and utilization of additional countermeasures, such as physical blockchain and jamming, which will be explored in future articles.
ANSSI’s Simulator — a point of reference
⮞ Summary
ANSSI’s online simulator (ssi.gouv.fr) limits inputs to 20 characters and 90 symbols and returns a maximum score of 130, comparable to a 128-bit AES key. Our generator uses 95 printable ASCII symbols and 20 chars, exceeding ANSSI’s standard presets.
Diverse Password Generation Options
Our password creation options offer versatility. Users can either select passwords from the pool of 95 available characters, opt for a semi-automatic generation followed by modification, or automate the process entirely according to default criteria, allowing passwords of up to 20 characters.
Adaptability to Website Constraints
For websites that impose restrictions on symbols or character limits, users can customize their password generation preferences, choosing between identifiers, letters, and/or numbers, with or without symbols.
Hexadecimal Generator for Added Utility
We’ve also introduced a hexadecimal generator to facilitate programming of digital codes. This feature proves invaluable in various domains, including electronics, electromechanics, and maintenance services, enabling the creation and modification of digital access codes with ease. Furthermore, codes can be securely shared with building residents through functions like “scrambling” or encryption via a QR Code, all made possible by EviCore technologies from Freemindtronic.
Forming Your Own Opinion
The aim of this article is to empower you to form your own assessment of the resilience of our password generators against brute force attacks. While we are not the sole providers of powerful password generators, our test stands as a benchmark against other comparable implementations.
Ensuring Ongoing Security
Our embedded password generator undergoes regular updates to maintain its complexity and withstand the evolving landscape of brute force attacks. Our commitment is to enhance security without compromising user convenience—a complex yet vital undertaking.
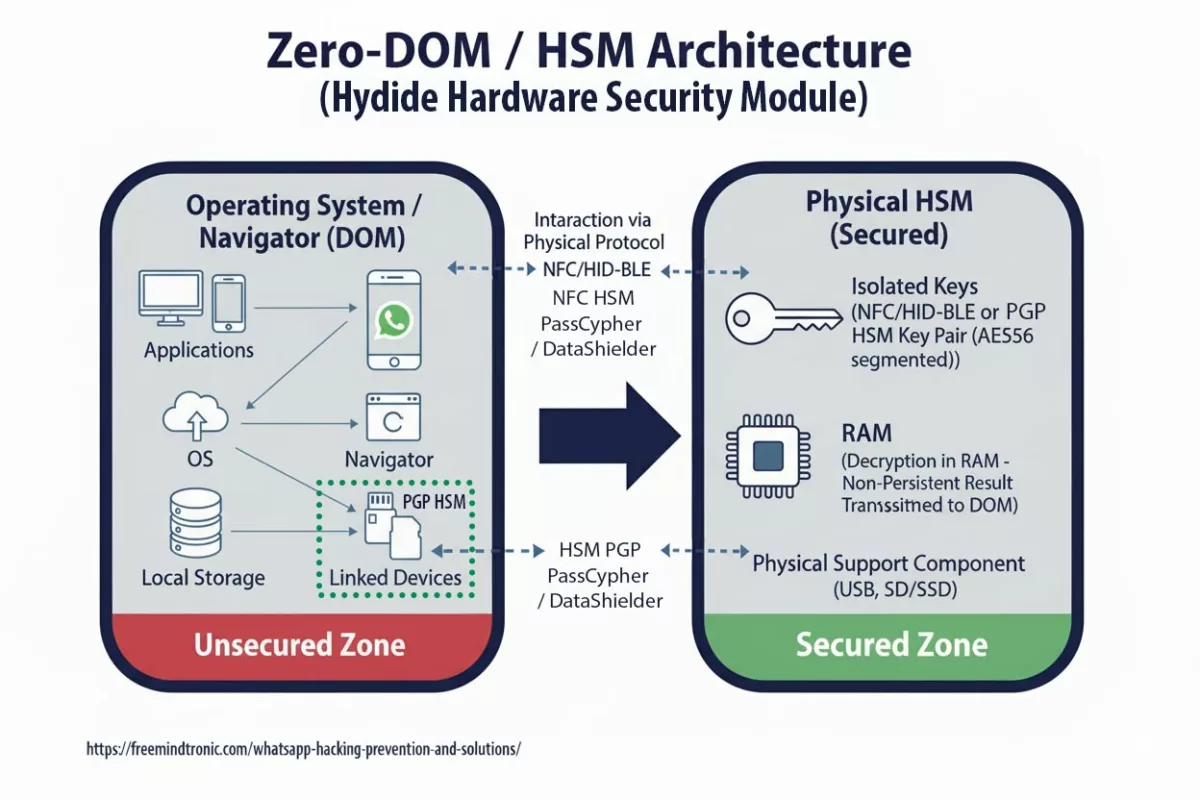
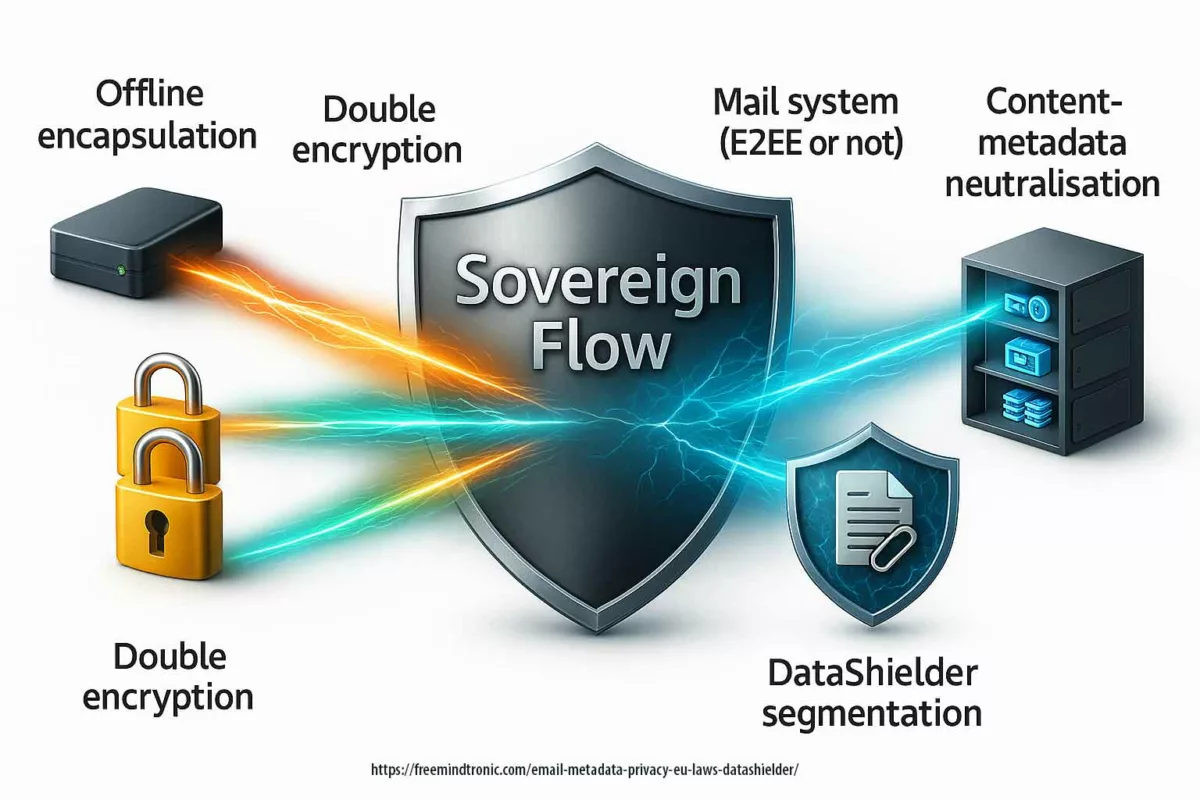
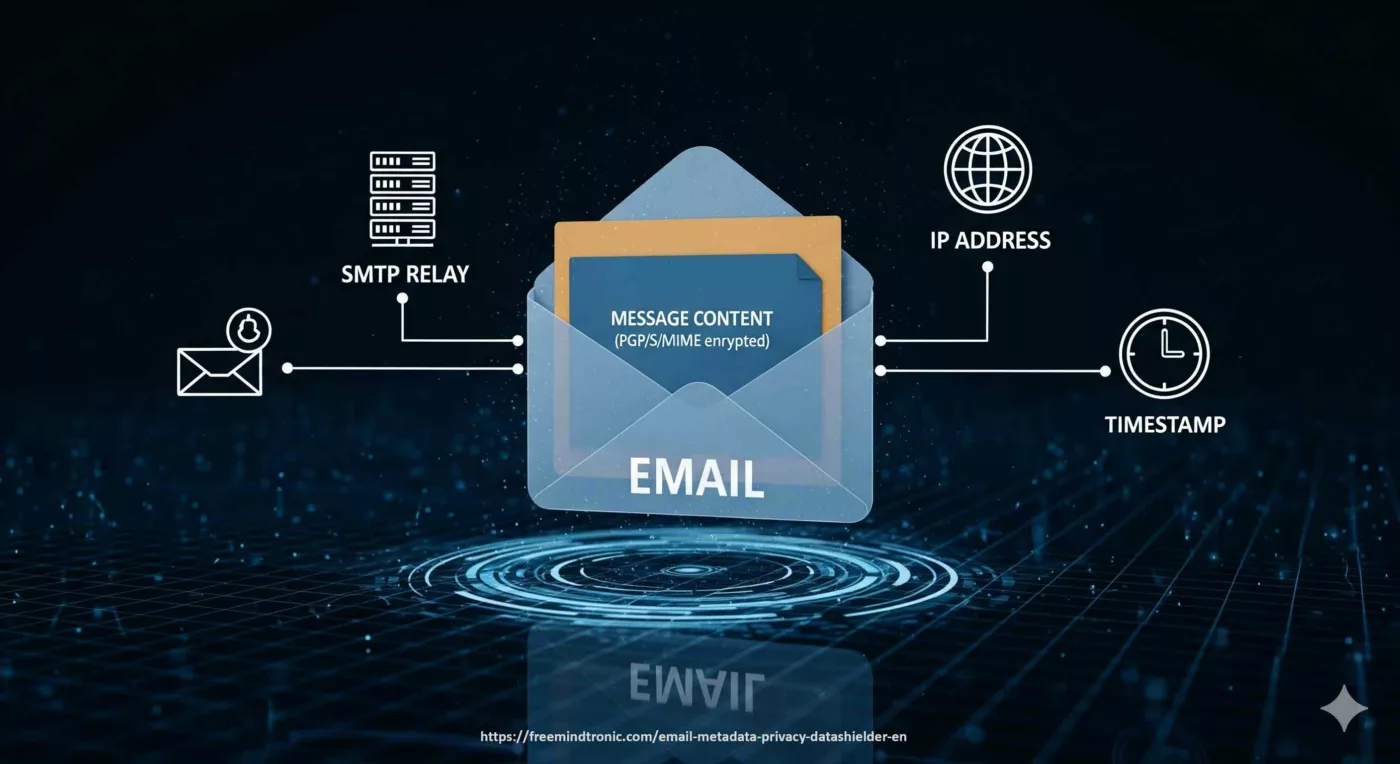
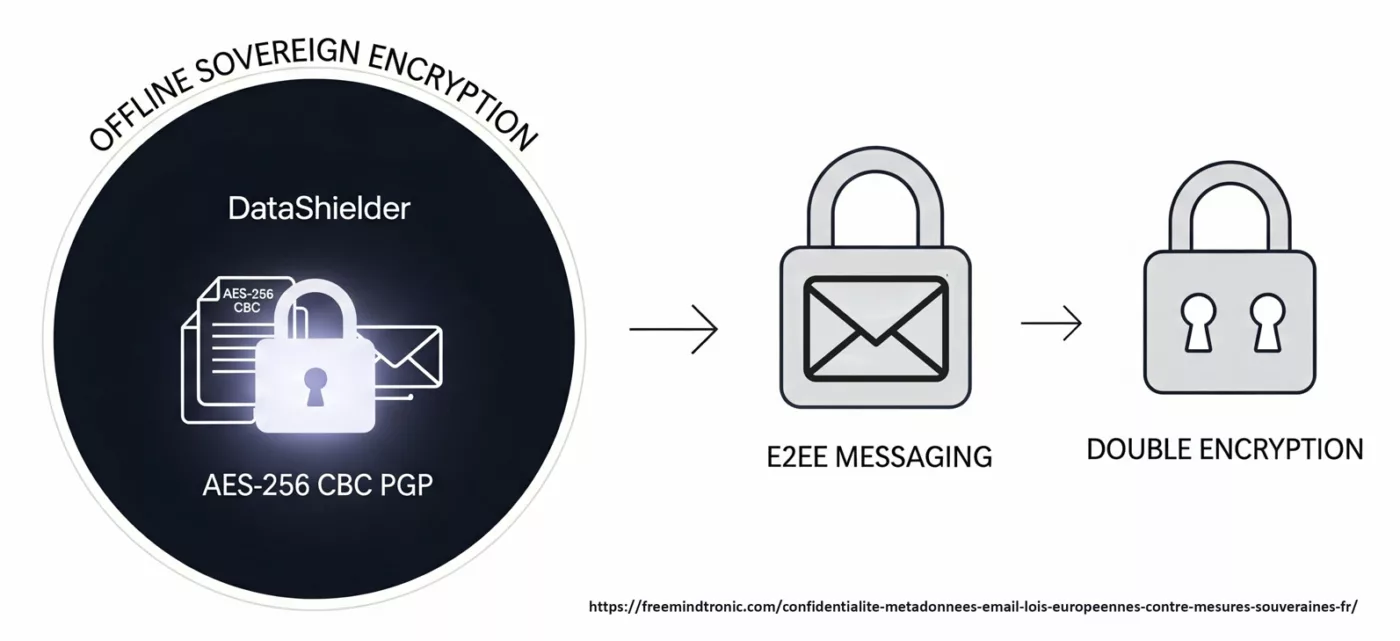
Cas d’usage souverain — EviPass & Freemindtronic
Storing long random passwords inside an NFC HSM device (EviTag / EviCard) managed by the Freemindtronic app reduces attack surface: secrets never transit the DOM, access is hardware-gated and audit trails are preserved.
References & links
- [1] https://www.bee-man.us/computer/password_strength.html
- [2] http://lastbit.com/pswcalc.asp
- [3] http://password-checker.online-domain-tools.com/
- [4] https://www.ssi.gouv.fr/administration/precautions-elementaires/calculer-la-force-dun-mot-de-passe/
- [5] https://www.btb.termiumplus.gc.ca/tpv2guides/guides/clefsfp/index-fra.html?lang=fra&lettr=indx_catlog_m&page=9-nI6-pQZOTM.html
- [6] https://www.lesechos.fr/24/04/2017/lesechos.fr/0212007699237_les-depenses-militaires-atteignent-2-2–du-pib-mondial.htm
- [7] https://www.ssi.gouv.fr/administration/precautions-elementaires/calculer-la-force-dun-mot-de-passe/
- [8] EviPass uses all the symbols of the printable ASCII table, i.e., 95 symbols. The NFC EviPass device can store contactless up to 51 randomly generated characters with the Freemindtronic app.
- [9] https://fr.wikipedia.org/wiki/American_Standard_Code_for_Information_Interchange
- Bee-Man home: https://www.bee-man.us/
Strategic Outlook
The brute-force infeasibility demonstrated here strengthens the case for combining cryptographic best practices (KDFs, salts), hardware anchoring (HSM/NFC), and user-friendly password managers (EviPass). Future research will compare operational attack chains, side-channels and hybrid attacks to refine protective doctrines.
What We Didn’t Cover
This article focuses on brute force estimates. Physical countermeasures (blockchain anchoring, jamming), side-channel attacks, and full operational attack chains are for future work.
Weak Signals — Emerging Threats
- AI-assisted brute-force optimizations could reduce entropy exploration, though current gains remain marginal vs 20-char ASCII codes.
- Quantum computing acceleration for hash inversion (beyond Shor’s factoring) remains theoretical but under exploration.
- Specialized ASICs for password cracking may alter economics but not exponential scales.
Glossary
- ASCII — American Standard Code for Information Interchange; 95 printable characters used for passwords.
- Brute force — Exhaustive testing of all possible combinations to guess a secret.
- GPU cluster — Array of graphics processors used for parallel computation in password cracking.
- HSM — Hardware Security Module; secure enclave for managing secrets like cryptographic keys.
FAQ
Why is a 20-character ASCII password unbreakable?
Because the keyspace (94^20 possibilities) is astronomically large. Even with modern GPU clusters, brute force would take ~766 trillion years.
What makes Radeon City significant?
It set a benchmark in 2012 by reaching 350 billion NTLM guesses/sec, showing how GPU parallelism changed brute-force feasibility for short passwords.
Is ANSSI’s simulator still relevant?
Yes, as a reference point. However, it caps inputs at 20 chars / 90 symbols, while Freemindtronic generators use 20 chars / 95 symbols, exceeding its scope.