Introduction
References
- Zscaler, Check Point, HP Threat Research
- Freemindtronic APT36 Analysis
- Download the full APT36 Cyberespionage Group reference document (PDF)
- APT36 साइबर जासूसी समूह तकनीकी दस्तावेज़ हिंदी में डाउनलोड करें (PDF)
Legal Notice:
The content provided herein is for informational and educational use only. Freemindtronic S.L. Andorra disclaims all liability for direct or indirect consequences arising from the use or interpretation of this document. The information is shared without any warranty, and its use is under the full responsibility of the reader.
Any reproduction, adaptation, or redistribution must preserve the original attribution to Freemindtronic Andorra and include this legal disclaimer.
APT36 Cyberespionage Group Documentation
APT36 Cyberespionage Group is the focus of this technical reference, designed as a public documentation annexed to related posts published by Freemindtronic.
This document is a comprehensive technical reference on the APT36 Cyberespionage Group, freely downloadable for research and awareness purposes.It is part of Freemindtronic’s ongoing commitment to sharing threat intelligence and promoting proactive defense practices against advanced persistent threats (APT).
APT36 (Transparent Tribe / Mythic Leopard) Cyberespionage Group
Last Updated: May 16, 2025
Version: 1.1
Source: Freemindtronic Andorra
Introduction to the APT36 Cyberespionage Group
The Advanced Persistent Threat (APT) group known as APT36, Transparent Tribe, and Mythic Leopard has been an active cyber espionage actor for several years. Primarily targeted at India, APT36 is notorious for its persistent campaigns to collect sensitive intelligence from a variety of organizations, including government, military, and potentially the research and education sectors. Their operations are often characterized by the use of sophisticated spearphishing techniques and bespoke malware, such as Poseidon, Crimson RAT, ElizaRAT, and CapraRAT. The purpose of this reference document is to compile and analyze the available information about APT36, its tactics, techniques, and procedures (TTPs), infrastructure, and recommended mitigation measures.
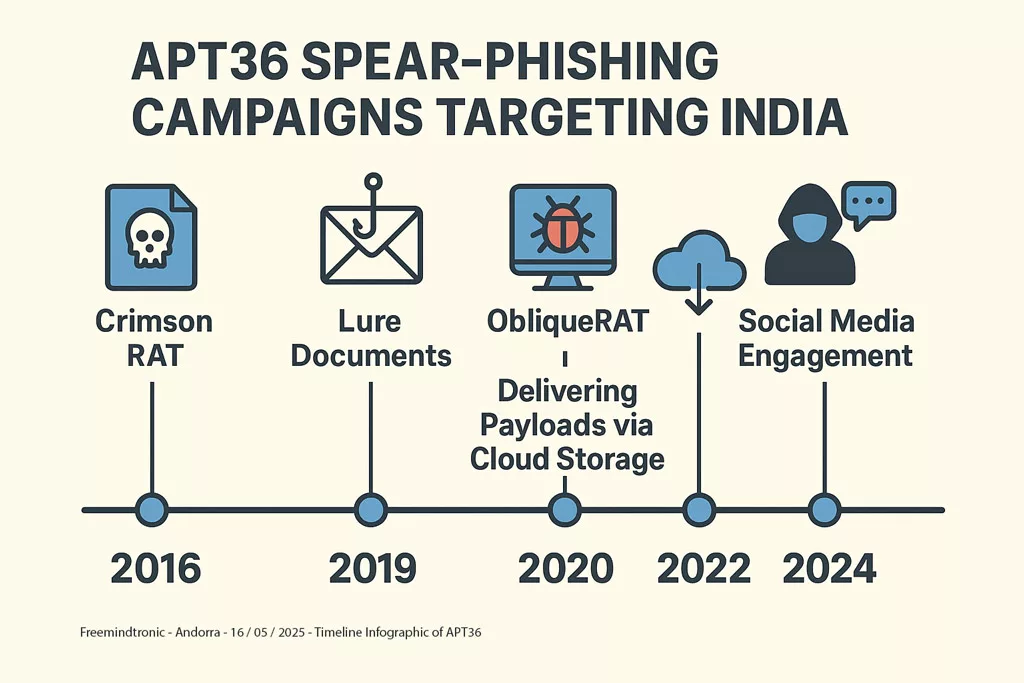
History and Evolution of the APT36 Cyberespionage Group
Freemindtronic Andorra focuses its initial analysis on recent IOCs (2023-2025), but APT36 has been active for several years. Reports from other security organizations confirm that cyber espionage campaigns targeting Indian entities began as early as 2016. Over time, APT36 has continuously adapted its TTPs, refining techniques to bypass security measures and develop new infiltration tools. For example, the emergence of Android RATs like CapraRAT expands their reach to mobile devices, increasing the risk for smartphone users. Meanwhile, leveraging platforms such as Telegram for C2 operations (ElizaRAT) indicates an attempt to exploit less monitored communication channels, enhancing their stealth capabilities.
Cybersecurity experts continue to debate APT36’s precise attribution. Although its primary targets are in India, certain indicators suggest possible connections to Pakistani state interests. The choice of decoy themes and the sectors under attack reinforce this hypothesis. However, formal attribution remains challenging, requiring deeper analysis and more conclusive evidence. In the complex world of cyber threat intelligence, determining the true origin of APT groups demands a meticulous and multi-layered approach.
Techniques, Tactics and Procedures (TTPs) Employed by APT36
Reconnaissance: APT36 likely conducts careful reconnaissance of its targets, collecting publicly available information (OSINT) on employees, organizational structures, and sensitive projects. Social media profiles and official websites are potential sources of information. Social engineering can also be used to obtain information from employees.
Initial point of entry:
- Spearphishing: This is APT36’s preferred attack vector. Emails are meticulously designed to mimic legitimate communications (e.g., government notifications, invitations to academic events, security app updates). Malicious attachments (Word documents, PDFs, executables, RTF files, screensavers) or links to compromised websites are used to distribute the initial payloads. Identified filenames (e.g., Briefing_MoD_April25.docx, Alert_Kavach_Update.exe) illustrate this tactic by targeting topical themes or topics relevant to potential victims.
- Exploiting Vulnerabilities: Although not explicitly mentioned in the initial IOCs, it is possible that APT36 could exploit known software vulnerabilities in commonly used applications (e.g., Microsoft Office) to gain initial access. RTF files are often used in such attempts.
- Website Compromise: It is possible, although not directly proven by IOCs, that APT36 could compromise legitimate websites to host payloads or to redirect victims to phishing pages.
Persistence:
Once a system is compromised, APT36 puts mechanisms in place to maintain access even after a reboot. IOCs reveal the use of specific Windows registry keys (HKEY_CURRENT_USERSoftwareCrimsonRAT, HKEY_LOCAL_MACHINESYSTEMElizaRATPersistence, HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunCapraStart) to ensure the automatic execution of malware. On Android, persistence is often achieved by masquerading as legitimate app updates (com.kavach.update.apk).
Lateral Movement:
After obtaining an initial foothold, APT36 attempts to move laterally within the victim’s network to reach more sensitive systems. This can involve exploiting network shares, using stolen credentials (potentially obtained via keylogging), and executing remote commands via deployed RATs.
Command and Control (C2)
The malware used by APT36 communicates with attacker-controlled C2 servers to receive instructions and exfiltrate data. The identified IP addresses (45.153.241.15, 91.215.85.21, etc.) potentially represent this C2 infrastructure. ElizaRAT’s use of TelegramBot suggests leveraging popular messaging platforms for C2, which can make detection more difficult. HTTP and HTTPS are likely used for C2 traffic, potentially hidden within legitimate web traffic.
Data exfiltration
Since APT36’s primary focus is espionage, data exfiltration is a crucial step. The types of data targeted likely include sensitive documents (military, government, research), credentials (usernames, passwords), and other strategic information. Data can be exfiltrated through established C2 channels, potentially compressed, or encrypted to avoid detection.
APT36 Malware and Tools
The APT36 Cyberespionage Group relies on various Remote Access Trojans (RATs) for espionage operations, especially on Indian targets.
- Poseidon malware: A sophisticated RAT with extensive espionage and data theft capabilities. Its hash (3c2cfe5b94214b7fdd832e00e2451a9c3f2aaf58f6e4097f58e8e5a2a7e6fa34) allows it to be identified on compromised systems.
- Crimson RAT: Another RAT commonly associated with APT36, offering keylogging, screen capture, and remote command execution features. Its mutex (GlobalCrimsonRAT_Active) and registry key (HKEY_CURRENT_USERSoftwareCrimsonRAT) are important indicators.
- ElizaRAT: This RAT appears to be using Telegram for C2 communication, which is a potential evasion tactic. Its loader (9f3a5c7b5d3f83384e2ef98347a6fcd8cde6f7e19054f640a6b52e61672dbd8f) and its mutex (LocalElizaRATSession) are key IOCs.
- CapraRAT (Android): Indicates APT36’s ability to target mobile devices. Its features can include stealing SMS, contacts, audio recording, and location tracking. Its package name (com.kavach.update.apk) and mutex (SessionsBaseNamedObjectsCapraMobileMutex) are specific flags.
Obfuscation and Evasion: APT36 uses a variety of techniques to make its malware and communications more difficult to detect and analyze. Examples of these tactics include Base64 encoding of sensitive information (bXlQYXNzd29yZDEyMw==, JAB1c2VyID0gIkFkbWluIg==) and obfuscation of JavaScript code (eval(decodeURIComponent(‘%75%70%64%61%74%65’))) are examples of these tactics.
APT36 Cyberespionage Group Infrastructure
APT36’s infrastructure includes the command and control (C2) servers used to direct malware deployed on victims’ systems. The identified IP addresses (45.153.241.15, 91.215.85.21, 185.140.53.206, 192.241.207.45, 103.145.13.187) are focal points for blocking and monitoring. Analysis of these IP addresses can reveal information about the hosting providers used and potentially other related activities. Malicious domains (kavach-app[.]com, indiapost-gov[.]org, gov-inportal[.]org, indian-ministry[.]com, securekavach[.]in) are used in phishing campaigns to host fake login pages or to distribute malware. These domains often imitate legitimate websites to trick victims. Analyzing the registration information of these domains can sometimes provide clues about the actors behind these activities. It is also possible that APT36 is using compromised servers as relays to hide the origin of its attacks and make tracing more difficult.
Motivations and Targets of the APT36 Cyberespionage Group
The main motivation for APT36 appears to be cyber espionage, with a particular interest in gathering strategic intelligence related to India. Typical targets include:
- Indian government entities (ministries, agencies).
- Military and defense organizations.
- Research institutes and universities.
- Telecommunications companies.
- Potentially other sectors considered strategically important.
The themes of phishing lures (defense, foreign affairs, security updates of government applications) reinforce this assessment of targets and motivations.
Indicators of Compromise (IOCs) Associated with APT36
IP addresses of C2 Servers (2023–2025):
- 45.153.241.15: Observed in C2 communications related to APT36 malware samples.
- 91.215.85.21: Frequently associated with command and control activities for Crimson and Eliza RATs.
- 185.140.53.206: Used as a point of contact for data exfiltration.
- 192.241.207.45: Server potentially hosting malicious web infrastructure components (phishing pages).
- 103.145.13.187: IP address involved in the distribution of malicious payloads.
File Hashes (SHA-256):
- 3c2cfe5b94214b7fdd832e00e2451a9c3f2aaf58f6e4097f58e8e5a2a7e6fa34 (Poseidon malware): Identifies a specific strain of the Poseidon RAT.
- bd5602fa41e4e7ad8430fc0c6a4c5d11252c61eac768835fd9d9f4a45726c748 (Crimson RAT) : Signature unique d’une variante de Crimson RAT.
- 9f3a5c7b5d3f83384e2ef98347a6fcd8cde6f7e19054f640a6b52e61672dbd8f (ElizaRAT loader): Allows you to detect the initial ElizaRAT deployment program.
- 2d06c1488d3b8f768b9e36a1a5897cc6f87a2f37b8ea8e8d0e3e5aebf9d7c987 (CapraRAT APK) : Hash de l’application Android malveillante CapraRAT.
Malicious domains:
- kavach-app[.]com: Imitation of the security application “Kavach”, probably used to distribute CapraRAT.
- indiapost-gov[.]org: Impersonates the Indian Postal Service site, used for phishing or distributing malicious attachments.
- gov-inportal[.]org: Attempt to imitate an Indian government portal to target civil servants.
- Indian-Ministry[.]com: Generic but credible domain name to target Indian ministries.
- securekavach[.]in: Another attempt to imitate “Kavach”, aimed at appearing legitimate to Indian users.
Suspicious URLs:
- http://kavach-app.com/update: Fake update URL for the “Kavach” app, potential distribution point for CapraRAT.
- http://gov-inportal.org/download/defense-docs.exe: Link to a malicious executable disguised as a defense document.
- http://securekavach.in/assets/login.php: Potential phishing page to steal credentials.
- https://indiapost-gov.org/track/status.aspx: A sophisticated phishing page that mimics package tracking to trick sensitive information into entering or downloading malware.
Phishing File Names:
- Briefing_MoD_April25.docx: Decoy potentially targeting the Ministry of Defense.
- Alert_Kavach_Update.exe: False update alert for “Kavach” probably distributing a RAT.
- IndiaDefense2025_strategy.pdf: Decoy containing strategic information on Indian defense.
- MoEA_internal_memo_23.rtf: Fake internal memo from the Ministry of Foreign Affairs.
- academic-research-invite.scr: Malicious screensaver masquerading as an academic invite.
Fake Android Application Package Names:
- com.kavach.update.apk: Malicious package masquerading as an update of “Kavach”.
- com.defensebriefing.alert.apk: Malicious Android app related to defense.
- com.india.education.portal.apk: Fake app linked to an Indian educational portal.
Mutexes:
- GlobalCrimsonRAT_Active: Indicates the active presence of the Crimson RAT on a Windows system.
- LocalElizaRATSession: Indicates an active Eliza RAT session.
- SessionsBaseNamedObjectsCapraMobileMutex: A Mutex specific to the Android version of CapraRAT.
Registry Keys (Windows):
- HKEY_CURRENT_USERSoftwareCrimsonRAT: Key used by Crimson RAT to store its configuration.
- HKEY_LOCAL_MACHINESYSTEMElizaRATPersistence: A key indicating a persistence mechanism for ElizaRAT.
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunCapraStart: Automatic startup key for CapraRAT.
Known User-Agents:
- Mozilla/5.0 (Windows NT 10.0; Win64; x64) APT36Client/1.0: User-agent potentially used by a communication tool or an APT36-specific implant.
- TelegramBot-ElizaRAT/2.5: Indicates the use of the Telegram API by the Eliza RAT for C2 communication.
- CapraAndroidAgent/1.4: User-agent identifying the Capra malicious agent on Android devices.
Encoded/Obfuscated Strings Used in Payloads:
- bXlQYXNzd29yZDEyMw==: A Base64-encoded string, decoding as “myPassword123”, potentially hard-coded identifiers or configuration strings.
- JAB1c2VyID0gIkFkbWluIg==: Another Base64 string, decoding to $user=”Admin”, suggesting the use of PowerShell for malicious operations.
- eval(decodeURIComponent(‘%75%70%64%61%74%65’)): Obfuscated JavaScript code that, when de-encoded and evaluated, executes the “update” function, potentially indicating a malicious update or dynamic code execution feature.
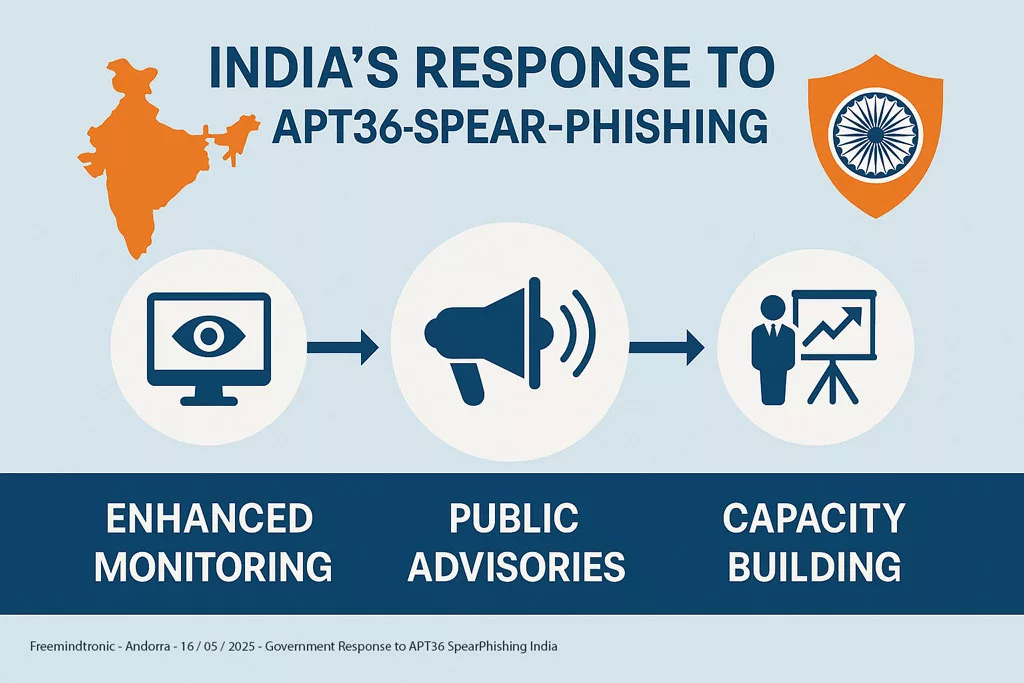
Mitigation and Detection Measures Against the APT36 Cyberespionage Group
Mitigating threats from the APT36 Cyberespionage Group requires layered defenses, active monitoring, and awareness training.
General recommendations:
- Awareness of the threat of spearphishing: Train employees to identify suspicious emails, verify the authenticity of senders, and not click on links or open attachments from unknown or unsolicited sources.
- Implement multi-factor authentication (MFA): Strengthen account security by requiring a second form of authentication in addition to the password.
- Keeping systems and software up to date: Regularly apply security patches for operating systems, applications, and web browsers to reduce the risk of vulnerability exploitation.
- Network segmentation: Limit the spread of threats by segmenting the network and enforcing strict access control policies.
- Network traffic and log monitoring: Implement monitoring systems to detect suspicious network activity, communications to known IP addresses and C2 domains, and unusual access attempts. Regularly analyze system and application logs.
- Use robust security solutions: Deploy and maintain anti-virus solutions, endpoint detection and response (EDR) systems, and intrusion prevention and detection (IDS/IPS) systems.
Specific measures based on IOCs:
- IOC Blocking: Integrate identified IP addresses, domains, and file hashes into firewalls, DNS servers, antivirus solutions, and web filtering systems to block communications and malware associated with APT36.
- Rule-Based Detection: Implement Yara and Sigma rules (if available) to identify patterns and characteristics of malware and APT36 activities on systems and in logs.
- Traffic Inspection: Configure security systems to inspect network traffic for suspicious user agents (APT36Client/1.0, TelegramBot-ElizaRAT/2.5, CapraAndroidAgent/1.4).
- Registry and Mutex Monitoring: Use endpoint monitoring tools to detect the creation of registry keys and mutexes associated with RATs used by APT36.
- Email Scanning: Implement spam filters and email scanning solutions to identify and block messages containing known file names and phishing URLs.
- Mobile device security: Deploy mobile security solutions and educate users about the risks of installing apps from unknown sources. Monitor Android devices for the presence of malicious package names.
Incident response strategies:
- Response Plan: Develop and maintain a cybersecurity incident response plan specific to APT threats, including steps to follow in the event of detection of APT36-related activity.
- Isolation: In the event of a suspected compromise, immediately isolate the affected systems from the network to prevent the spread of the attack.
- Forensic Analysis: Perform in-depth forensic analysis to determine the scope of the breach, identify compromised data, and understand the tactics used by attackers.
- Eradication: Completely remove malware, persistence mechanisms, and tools used by attackers from compromised systems.
- Restore: Restore systems and data from clean, verified backups.
- Lessons learned: After an incident, analyze causes and processes to improve security measures and response procedures.
References
- https://www.zscaler.com/blogs/security-research/transparent-tribe-apt-targeting-india
- https://research.checkpoint.com/2023/transparent-tribe-evolution-of-a-cyber-espionage-threat/
- https://threatresearch.ext.hp.com/transparent-tribe-apt-group/
- This technical reference document is based on the original analysis published by Freemindtronic Andorra, available at: https://freemindtronic.com/apt36-spearphishing-india/
Strengthening Security Posture: The Freemindtronic HSM Ecosystem Against APT36
The table below summarizes how each threat vector used by APT36 is mitigated by Freemindtronic’s sovereign tools — whether mobile or desktop, fixed or remote, civilian or military-grade. It compares threat by threat how DataShielder and PassCypher mitigate attacks — whether on mobile, desktop, or air-gapped infrastructure.
To facilitate adoption and use by organizations in India, the interfaces and documentation for our DataShielder and PassCypher solutions are also available in Hindi.
| APT36 Tactic / Malware | DataShielder NFC HSM (Lite/Auth/M-Auth) | DataShielder HSM PGP (Win/macOS) | PassCypher NFC HSM (Android) | PassCypher HSM PGP (Win/macOS) |
|---|---|---|---|---|
| Spearphishing (India Post, Kavach) | ✔ QR-code encryption + sandbox | ✔ Signature check + offline PGP | ✔ URL sandbox + no injection | ✔ Sandboxed PGP container |
| Crimson RAT | ✔ NFC avoids infected OS | ✔ No system-stored keys | ✔ Secrets off-device | ✔ No memory exposure |
| CapraRAT | ✘ | ✘ | ✔ Not stored in app | ✔ Desktop-paired use only |
| Telegram C2 | ✔ 100% offline | ✔ No cloud | ✔ Offline | ✔ Offline |
| ApolloStealer | ✔ Credentials never exposed | ✔ Key never loaded in system | ✔ Immune to clipboard steal | ✔ Phishing-proof login |
| Poseidon (Fake Kavach on Linux) | ✔ NFC-only: bypasses compromised OS | ✘ Not Linux-compatible | ✘ Not on Android | ✔ No OS dependency |
| ClickFix (command injection) | ✔ No shell interaction possible | ✔ PGP validation | ✔ No typing / no pasting | ✔ No terminal interaction |
| CEO Fraud / BEC | ✔ Auth/M-Auth modules encrypt orders | ✔ Digital signature protection | ✔ No spoofing possible | ✔ Prevents impersonation |
Outlook and Next Steps Regarding APT36
APT36 (Transparent Tribe / Mythic Leopard) embodies a persistent and structured threat, primarily targeting strategic Indian entities for cyberespionage purposes. Its campaigns rely on sophisticated decoys, custom RATs, and an agile C2 infrastructure. A thorough understanding of their tactics, techniques, and procedures (TTPs), as well as the currently known Indicators of Compromise (IOCs), provides a solid foundation to guide detection, defense, and response policies. Faced with the constant evolution of the techniques used by this group, a posture of continuous vigilance is essential. This document is produced in an evolving manner. We believe it is essential to keep it up to date with new threats and tools observed in order to maintain a proactive security posture aligned with the latest available APT36 intelligence.