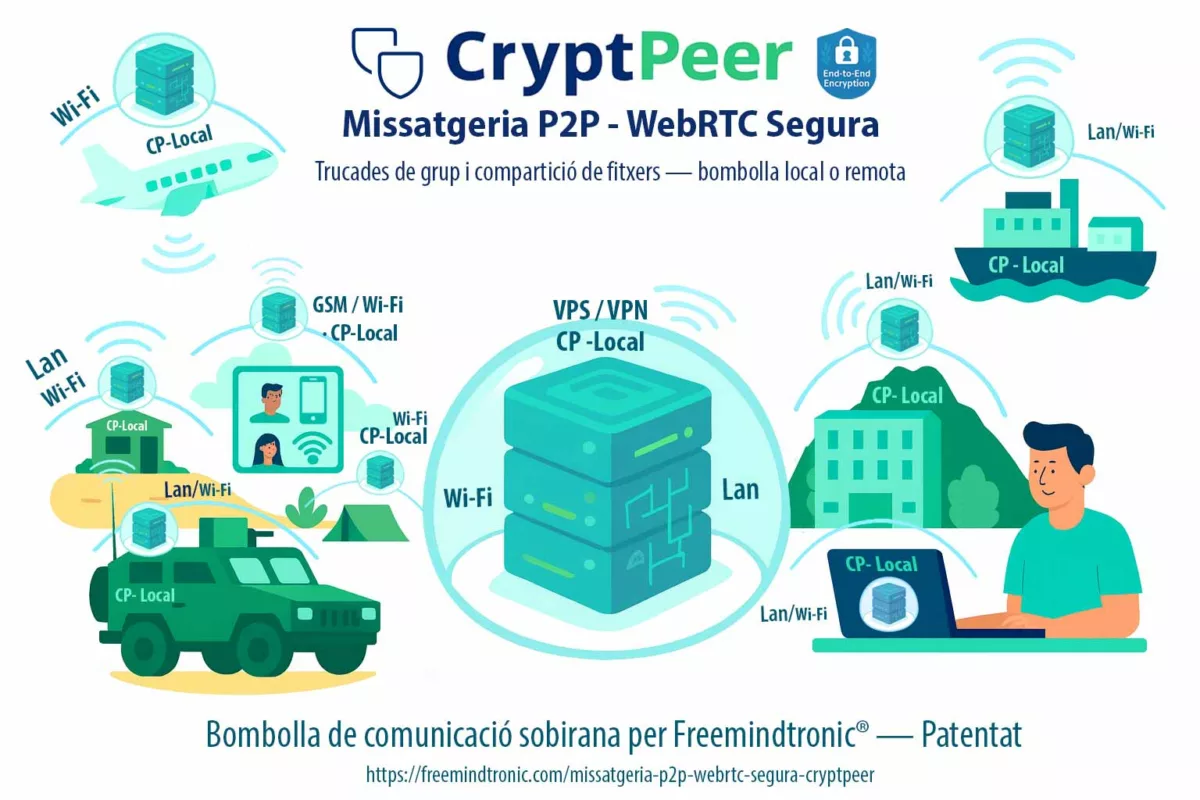
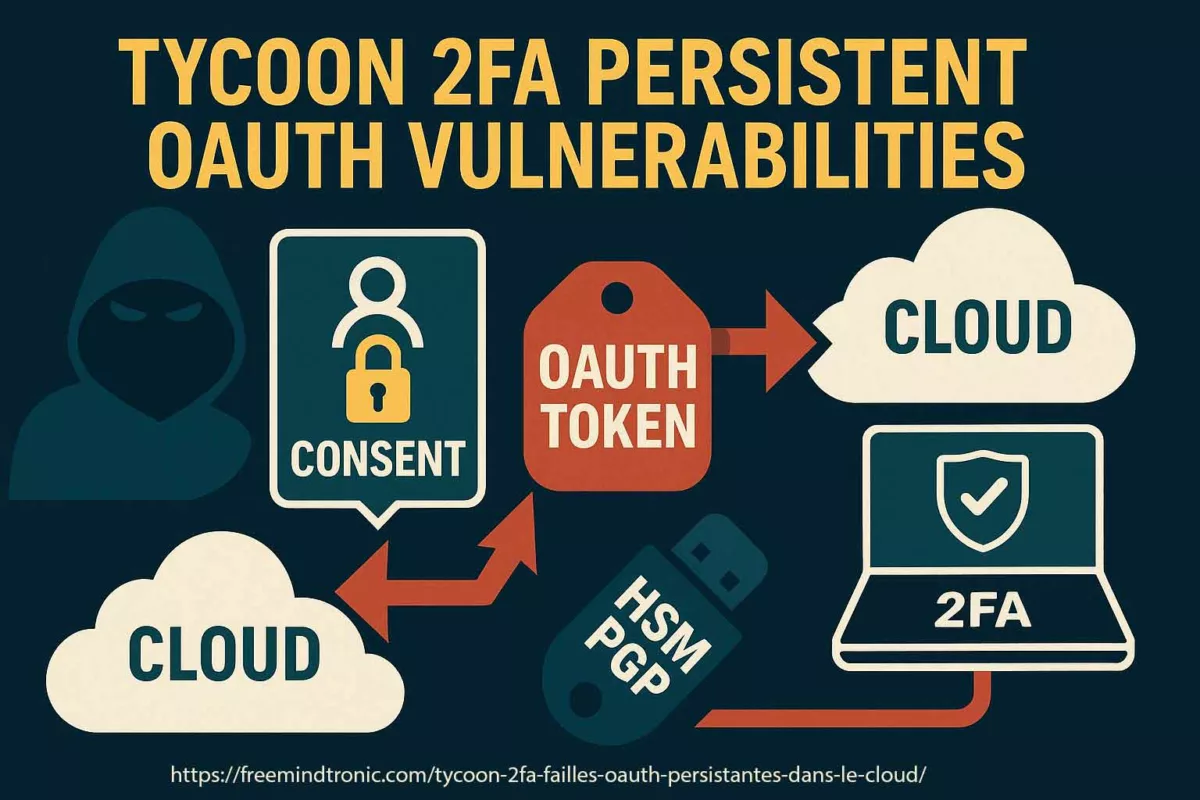
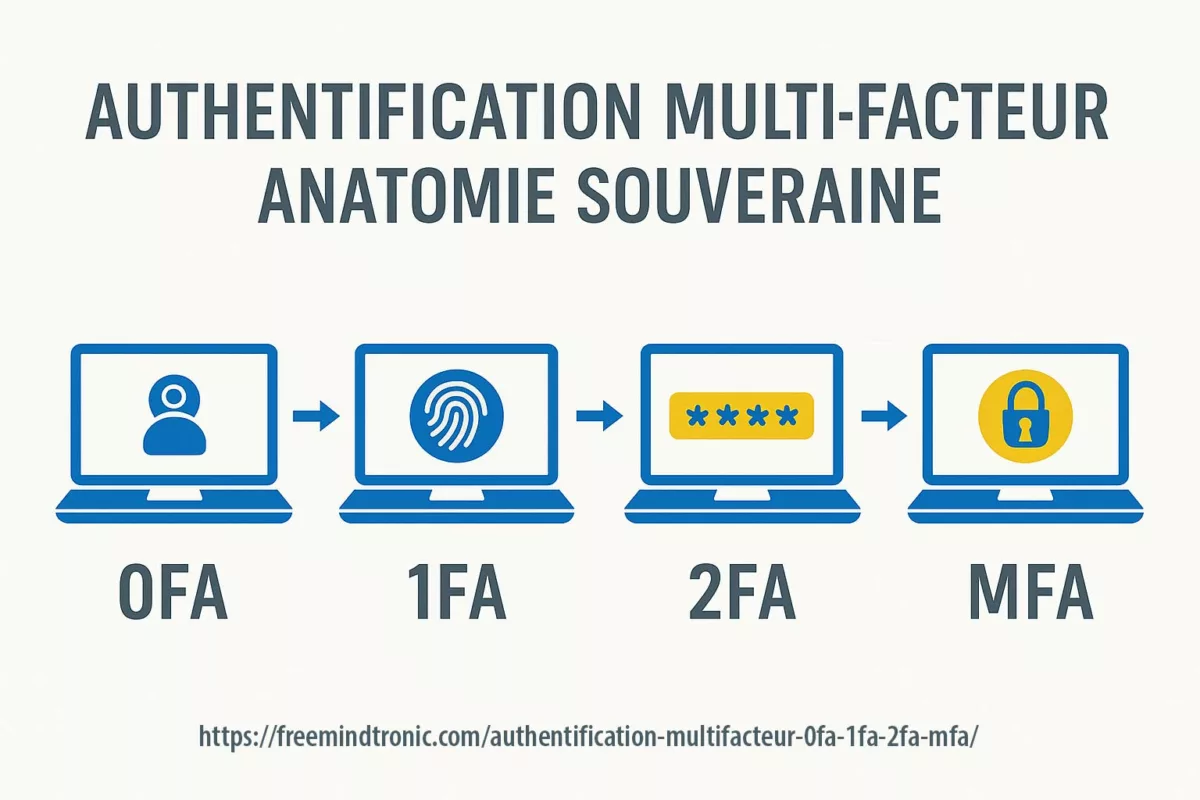
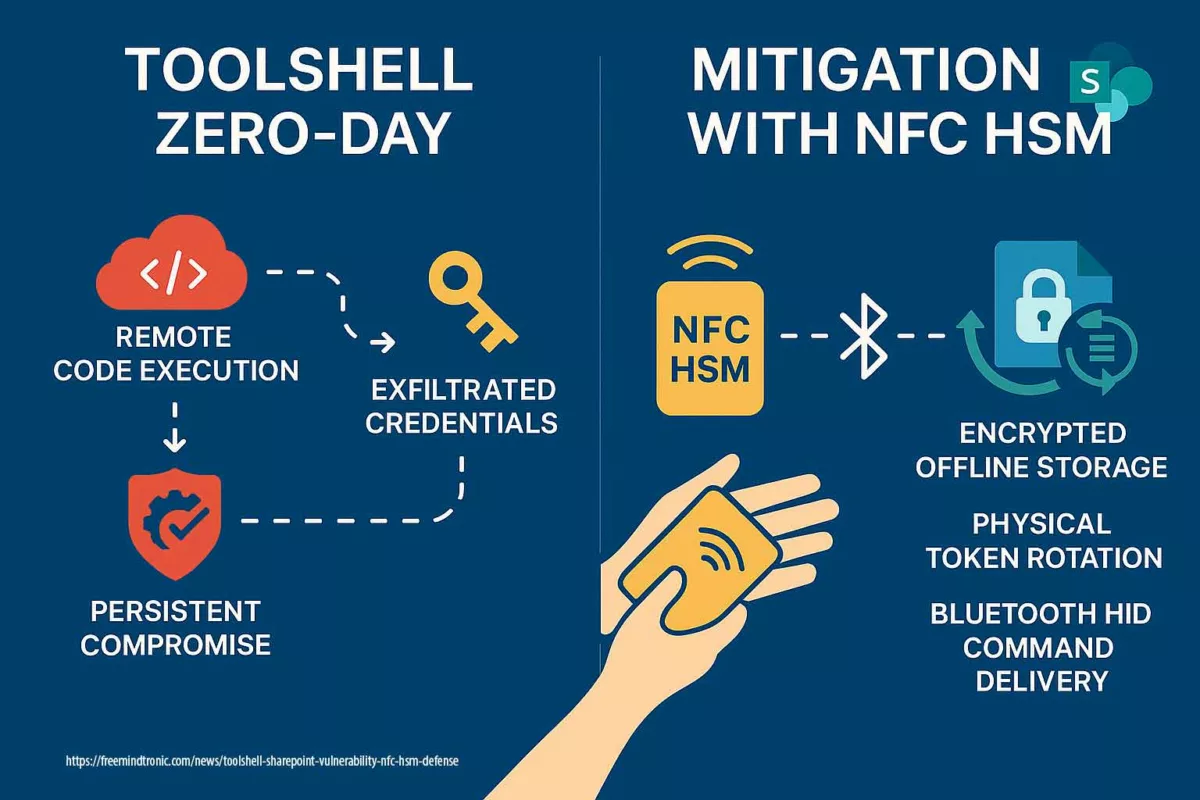
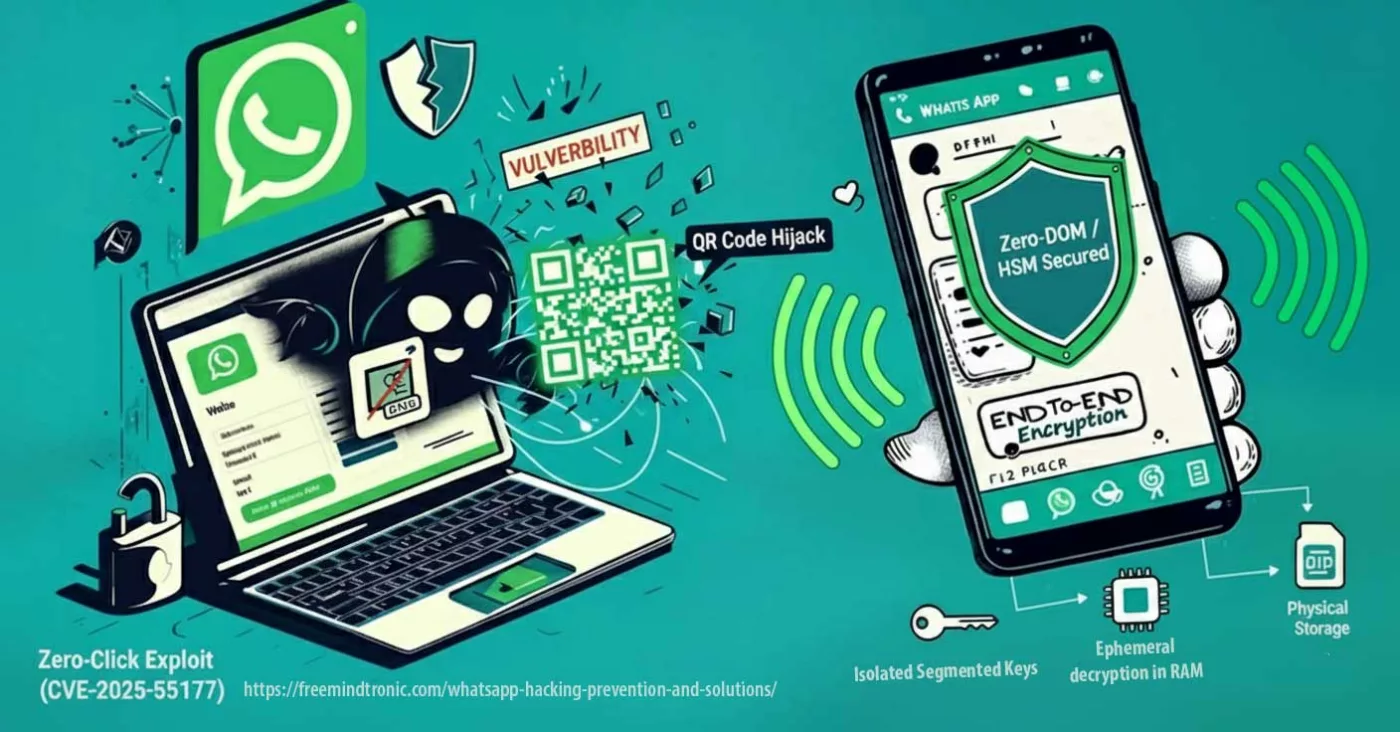
Executive Summary
In the evolving landscape of hybrid warfare, reputation cyberattacks have emerged as a powerful asymmetric tool, targeting perception rather than systems. These operations exploit cognitive vectors—such as false narratives, controlled leaks, and media amplification—to destabilize trust in technologies, companies, or institutions. Unlike conventional cyberattacks, their purpose is not to penetrate networks, but to erode public confidence and strategic credibility. This Chronicle exposes the anatomy, intent, and implications of such attacks, offering sovereign countermeasures grounded in cryptographic attestation and narrative control.
Estimated reading time: 16 minutes
Complexity level: Strategic / Expert
Language specificity: Sovereign lexicon – High concept density
Accessibility: Screen reader optimized – all semantic anchors in place Navigation
In Cyberculture ↑ Correlate this Chronicle with other sovereign threat analyses in the same editorial rubric.
- Executive Summary
- Strategic Definition
- Typology of Reputation Attacks
- Event-Driven Triggers
- Threat Actor Mapping
- Geopolitical Embedding
- Sovereign Countermeasures
- Strategic Case Illustrations
- Intermediate & Legacy Cases
- Common Features & Strategic Objectives
- Strategic Outlook
- Narrative Warfare Lexicon
- Beyond This Chronicle
Strategic Navigation Index
Key insights include:
- Reputation attacks prioritize psychological and narrative impact over system access
- Controlled leaks and unverifiable claims simulate vulnerability without intrusion
- APT actors increasingly combine narrative warfare with geopolitical timing
- Sovereign countermeasures must address both runtime trust and narrative control
- Legal attribution, hybrid doctrines, and military exercises recognize the strategic threat
- IA-generated content and deepfake amplification heighten the reputational asymmetry
About the Author – Jacques Gascuel, inventor of internationally patented encryption technologies and founder of Freemindtronic Andorra, is a pioneer in sovereign cybersecurity. In this Cyberculture Chronicle, he deciphers the role of reputation cyberattacks in hybrid warfare and outlines a sovereign resilience framework based on NFC HSMs, narrative control, and runtime trust architecture.
Strategic Definition
Reputation cyberattacks are deliberate operations that undermine public trust in a targeted entity—governmental, industrial, or infrastructural—without necessitating technical penetration. Unlike classical cyberattacks, these actions do not seek to encrypt, extract, or manipulate data systems directly. Instead, they deploy orchestrated influence tactics to suggest compromise, provoke doubt, and corrode strategic credibility.
Key vectors include unverifiable claims of intrusion, dissemination of out-of-context or outdated data, and AI-generated content posing as evidence. These attacks are particularly insidious because they remain plausible without being technically demonstrable. Their targets are not systems but perceptions—clients, partners, regulators, and the broader strategic narrative.
Reputation cyberattacks weaponize doubt and narrative ambiguity. Their objective is not to compromise infrastructure but to simulate weakness, discredit governance, and manipulate perception within strategic timeframes.
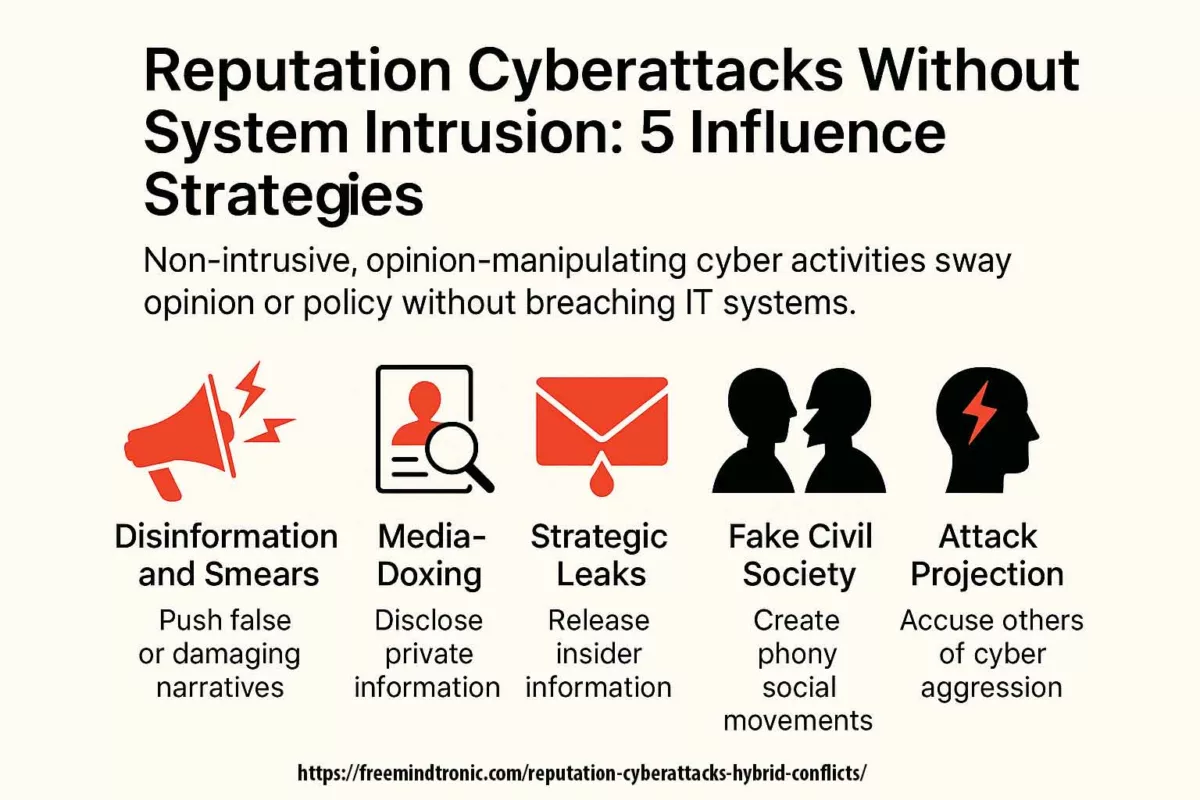
Typology of Reputation Attacks
Reputation cyberattacks operate through carefully structured vectors designed to affect perception without direct intrusion. Their effectiveness stems from plausible ambiguity, combined with cognitive overload. Below is a strategic typology of the most commonly observed mechanisms used in such campaigns.
| Type of Attack | Method | Reputation Objective |
|---|---|---|
| Controlled Leak | Authentic or manipulated data exfiltration | Undermine trust in data integrity or governance |
| Narrative of Compromise | Unverifiable intrusion claim | Simulate vulnerability or technical failure |
| Amplified Messaging | Telegram, forums, rogue media | Pressure decision-makers via public reaction |
| False or Outdated Leaks | Repurposed legacy data as recent | Manipulate interpretation and chronology |
| Brand Cloning / Solution Usurpation | Fake products, clones, apps | Confuse trust signals and damage legitimacy |
Reputation attacks deploy asymmetric cognitive tactics that distort technical signals to generate public discredit. Their sophistication lies in the lack of verifiability and the strategic timing of narrative releases.
Event-Driven Triggers
Reputation cyberattacks rarely occur randomly. They are most often synchronized with sensitive diplomatic, commercial, or regulatory events, maximizing their narrative and psychological effect. These timings allow threat actors to amplify tension, delegitimize negotiations, or destabilize political outcomes with minimum technical effort.
The following correlations have been repeatedly observed across high-impact campaigns:
| Trigger Type | Typical Context | Observed Examples |
|---|---|---|
| Diplomatic Events | G7, NATO, BRICS, UNSC debates | Jean-Noël Barrot’s G7 breach via spyware |
| Contract Finalization | Strategic defense or tech exports | Naval Group leak during Indonesian negotiations |
| Critical CVE Disclosure | Zero-day or CVSS 9+ vulnerabilities | Chrome CVE-2025-6554 exploited alongside eSIM JavaCard leaks |
| Political Transitions | Election cycles, leadership change | GhostNet during 2009 leadership reshuffles in Asia |
| Telecom Infrastructure Breach | U.S. regulatory hearings on 5G security | Salt Typhoon breach of U.S. telecom infrastructure |
| Military Retaliation | India–Pakistan border escalation | APT36 campaign post-Pahalgam attack |
– Surge in Telegram disinformation threads one week before BRICS 2025 summit
– Anonymous claims targeting SM-DP+ infrastructures prior to Kigen certification review
– Attribution disclosures by 🇨🇿 Czechia and 🇬🇧 UK against APT31 and GRU respectively, correlating with vote censure periods
– Military-grade leaks repurposed via deepfake narratives hours before defense debates at the EU Parliament
Threat Actor Mapping
Several Advanced Persistent Threat (APT) groups have developed and deployed techniques specifically tailored to reputation disruption. These actors often operate under, or in coordination with, state objectives—using narrative projection as a form of geopolitical leverage. Freemindtronic has documented multiple such groups across past campaigns involving mobile identity, supply chain intrusion, and staged perception attacks.
| APT Group | Origin | Strategic Focus | Regalian Link |
|---|---|---|---|
| APT28 / Fancy Bear | Russia | Media influence, strategic sabotage | GRU |
| APT29 / Cozy Bear | Russia | Diplomatic espionage, discrediting campaigns | SVR |
| APT41 / Double Dragon | China | eSIM abuse, supply chain injection | MSS |
| Lazarus / APT38 | North Korea | Crypto theft, industrial denigration | RGB |
| APT36 / Transparent T. | Pakistan | Military perception ops, Android surveillance | ISI |
| OceanLotus / APT32 | Vietnam | Telecom narrative control, political espionage | Ministry of Public Security |
Weak Signals:
- Surge in Telegram threads 72h prior to geopolitical summits
- Anonymous code disclosures targeting certified infrastructure
- OSINT forums hinting at state-level leaks without attribution
Timeline of Geopolitical Triggers and Corresponding Leaks
This sovereign timeline reveals how state-sponsored leak campaigns align tactically with geopolitical milestones, transforming passive narrative exposure into calibrated instruments of reputational destabilization.
| Date | Geopolitical Trigger | Leak Activity / APT Attribution |
|---|---|---|
| 11–12 June 2025 | NATO Summit | Massive credential dump via Ghostwriter |
| 18 July 2025 | U.S.–China Trade Talks | Strategic policy leak via Mustang Panda |
| 5 September 2025 | EU–Ukraine Association Agreement | Media smear leaks via Fancy Bear |
| 2 October 2025 | U.S. Sanctions on Russia | Source code exposure via Sandworm |
| 16 November 2025 | China–India Border Standoff | Fake news spike via RedEcho |
| 8 December 2025 | G7 Foreign Ministers’ Meeting | Diplomatic email leak via APT31 |
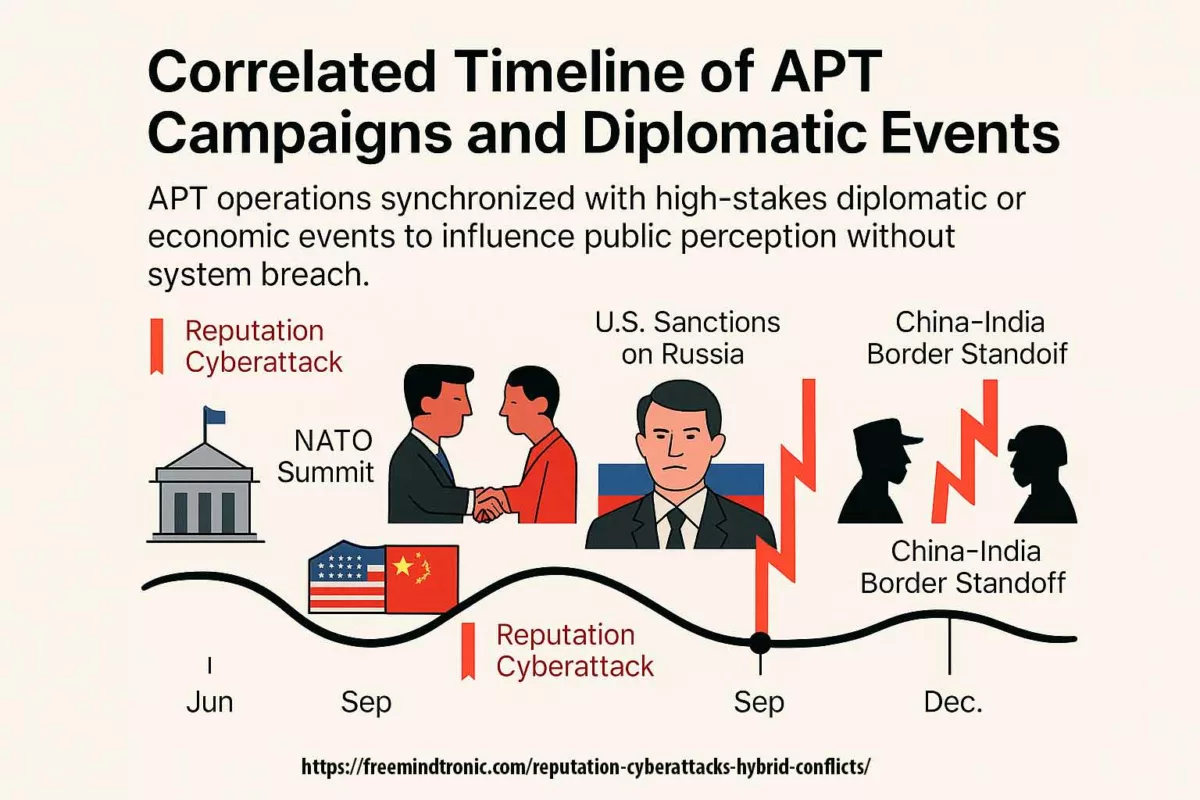
These APTs combine stealth, timing, and plausible deniability to weaponize trust decay. Their toolkit includes mobile clone propagation, certificate revocation simulation, and adversarial AI-driven content generation.
Medium Signals:
- Reactivation of domains previously linked to APT41 and APT36
- Spam waves targeting sectors previously affected (e.g., eSIM, military)
- Cross-platform narrative amplification combining Telegram, deepfakes, and dark web leaks

Geopolitical Embedding
Reputation cyberattacks are rarely isolated actions. They are often embedded within broader geopolitical manoeuvers, aligned with strategic objectives of national influence, dissuasion, or economic disruption. Below are detailed illustrations of how states integrate reputation-based cyber operations within their doctrine of influence.
🇷🇺 Russia – Narrative Sabotage and Attribution Management
APT28 and APT29 operate as complementary arms of Russian strategic disinformation. APT28 performs media amplification and tactical leaks, while APT29 infiltrates strategic diplomatic channels. Both benefit from GRU and SVR coordination, with plausible denial and a focus on exploiting trust asymmetries within European security frameworks.
🇨🇳 China – Espionage Hybridization and Runtime Subversion
APT41 is a paradigm of China’s fusion between state-sponsored espionage and monetized cybercrime. Their use of eSIM runtime abuse and compromised SM-DP+ provisioning chains illustrates a shift from direct intrusion to sovereignty degradation via runtime narrative manipulation. The Ministry of State Security provides structural protection and strategic targeting objectives.
🇰🇵 North Korea – Financial Subversion and Mobile Identity Hijacking
Lazarus Group (APT38) leverages breaches to undermine trust in certified systems. By targeting crypto wallets, blockchain nodes, and mobile identity providers, they transform technical compromise into economic destabilization narratives. These attacks often coincide with international sanctions debates or military exercises, and are directed by the Reconnaissance General Bureau (RGB).
🇵🇰 Pakistan – Military Psychological Pressure on India
APT36 deploys persistent mobile malware and SIM/eSIM spoofing against Indian military actors. These attacks are not solely technical; they aim to discredit Indian defense systems and pressure procurement diplomacy. The Inter-Services Intelligence (ISI) integrates these cyber tactics within regional destabilization agendas.
🇻🇳 Vietnam – Political Control via Telecom Targeting
OceanLotus (APT32) focuses on dissidents, journalists, and telecom infrastructure across ASEAN. Their aim is to dilute external perceptions of Vietnamese governance through discreet leaks and selective disclosure of surveillance capabilities. The Ministry of Public Security provides operational coverage and mission framing.
All of these actors embed their reputation attacks within state-approved strategic cycles. Cyberwarfare thus becomes an extension of diplomacy by other means—targeting trust, not terrain.
Sovereign Countermeasures
Defending against reputation cyberattacks requires more than perimeter security. Sovereign actors must combine cryptographic integrity enforcement, dynamic runtime assurance, and narrative discipline. Reputation attacks flourish in ambiguity—effective defense mechanisms must therefore be verifiable, attestable, and visible to the strategic environment.
Freemindtronic’s PassCypher NFC HSM / HSM PGP and DataShielder NFC HSM / HSM PGP exemplify sovereign countermeasures in action. Their air‑gapped hardware ensures that integrity attestations and encryption proofs are generated and verified at runtime—securely, transparently, and independently from compromised infrastructure.
Out-of-Band Attestation with NFC HSM
Architectures based on NFC HSMs (Hardware Security Modules) enable offline cryptographic proof of integrity and identity. These devices remain isolated from network vectors and can confirm the non-compromise of key credentials or components, even post-incident. Freemindtronic’s PassCypher NFC HSM, PassCypher HSM PGP, DataShielder NFC HSM and Datashielder HSM PGP technologies patented exemplify this paradigm.
Real-Time Message Provenance Control
DataShielder NFC HSM Auth et DataShielder NFC HSM M-Auth chiffrent toutes les communications par défaut, sur n’importe quel canal, à l’aide de clés matérielles souveraines qui ne peuvent pas être clonées, copiées ou extraites. Ce paradigme offre :

NFC HSM encryption draws a definitive boundary between authentic messages and fabricated narratives—making AI-forged disinformation both detectable and diplomatically indefensible.
- Verified encrypted messages sharply contrast with plaintext impersonations or unverifiable sources.
- Default encryption affirms authorship and message integrity without delay or user intervention.
- Falsehood becomes inherently visible, dismantling the ambiguity required for narrative manipulation.
This architecture enforces trust visibility by default—even across untrusted or compromised platforms—transforming every encrypted message into a sovereign proof of authenticity and every anomaly into a potential reputational alert.
Dynamic Certification & Runtime Audit
Static certification loses relevance once a component enters operational use. Reputation attacks exploit this gap by suggesting failure where none exists. Runtime certification performs real-time behavioural analysis, issuing updated trust vectors under sovereign control. Combined with policy-based revocation, this hardens narrative resilience.
Strategic Narrative Control
State entities and critical industries must adopt coherent, pre-structured public response strategies. The absence of technical breach must be communicated with authority and technical grounding. Naval Group’s qualified denial following its 2025 reputation leak demonstrates such sovereign narrative calibration under pressure.
This approach embodies dynamic certification, up to a temporal blockchain of trust. Unlike static attestations bound to deployment snapshots, sovereign systems like PassCypher NFC HSM and DataShielder NFC HSM perform ongoing behavioral evaluation—logging and cryptographically sealing runtime states.Each trust update can be timestamped, signed, and anchored in a sovereign ledger—transforming integrity into a traceable, irreversible narrative artifact. This not only preempts disinformation attempts but establishes a visible cryptographic chronicle that renders forgery diplomatically indefensible.
Sovereign cyberdefense means mastering time, integrity, and narrative. Out-of-band attestation and dynamic certification are not just security features—they are diplomatic weapons in an asymmetric reputational battlefield.
Strategic Case Illustrations
Reputation cyberattacks are no longer incidental. They are increasingly doctrinal, mirroring psyops in hybrid conflicts and weaponizing cognitive ambiguity. Below, we analyze three emblematic case studies where strategic visibility became a vulnerability—compromised not by code, but by coordinated narratives.
Morocco — CNSS Data Breach & Reputational Impact (April 2025)
- Major incident: In April 2025, Morocco’s National Social Security Fund (CNSS) experienced what is widely described as the largest cyber incident in the country’s digital history. The breach exposed personal data of approximately 2 million individuals and 500,000 enterprises, including names, national IDs, salaries, emails, and banking details. [Content verified via: moroccoworldnews.com, therecord.media, resecurity.com]
- Claimed attribution: The Algerian group JabaRoot DZ claimed responsibility, citing retaliation for an alleged breach of the APS (Algerian Press Service) account by Moroccan-linked actors.
- Technical vulnerability: The attack reportedly exploited “SureTriggers,” a WordPress module used by public services that auto-connects to Gmail, Slack, and Google APIs—identified as a likely vector in the incident.
- Collateral effects: The breach prompted temporary shutdowns of key Moroccan ministerial websites (Education, Tax), and government portals were disabled as a preventive cybersecurity measure. [Confirmed via moroccoworldnews.com]
- Institutional response: The NGO Transparency Maroc publicly criticized the lack of disclosure, urging authorities to release investigation findings and audit results to restore public confidence under data protection law 09‑08.
- Continental context: Kaspersky ranked Morocco among Africa’s top cyberattack targets, registering more than 12.6 million cyber threats in 2024, with significant increases in spyware and data exfiltration attempts.
The Moroccan breach illustrates the duality of hybrid threats: a massive technical compromise coupled with reputational erosion targeting public trust. By compromising legitimate governmental interfaces without penetrating core infrastructures, this attack typifies silent reputation warfare in a sovereign digital context.
United Kingdom — Reputation Warfare & Cyber Sabotage (2025)
- Contextual trigger: In May 2025, the UK government formally accused Russian GRU units 26165, 29155, and 74455 of coordinating cyber sabotage and influence operations targeting Western democracies, including the 2024 Paris Olympics and Ukrainian allies. The attribution was backed by the UK’s National Cyber Security Centre (NCSC). [gov.uk — Official Statement]
- Narrative dimension: Public attribution functions as a geopolitical signaling strategy—reasserting institutional legitimacy while projecting adversarial intent within a hybrid warfare doctrine.
- Institutional framing: The UK’s NCSC framed the attacks as hybrid campaigns combining technical compromise, reputational disruption, and online disinformation vectors. [NCSC Report]
The UK case underscores how naming threat actors publicly becomes a sovereign narrative tool—transforming attribution from defensive posture into reputational counterstrike within hybrid strategic doctrine.
Australia & New Zealand — AI‑Driven Reputation Campaigns & SME Disruption (2025)
- Threat escalation: In its July 2025 cyber threat bulletin, CyberCX raised the national threat level from “low” to “moderate” due to increased attacks by pro‑Russia and pro‑Iran hacktivists targeting SMEs and trust anchors. [CyberCX Report]
- AI impersonation cases: The Australian Information Commissioner reported a rise in deepfake voice-based impersonation (“vishing”) affecting brands like Qantas, prompting enhanced institutional controls. [OAIC Notifiable Data Breaches Report]
- Asymmetric reputational vectors: These campaigns leverage low-cost, high-impact impersonation to seed public distrust—especially effective when targeting service-based institutions with high emotional value.
In Australia and New Zealand, deepfake-enabled vishing attacks exemplify the evolution of hybrid threats—where brand trust, rather than infrastructure resilience, becomes the primary vector of reputational compromise.
Côte d’Ivoire — Symbolic Rise in Targeted Attacks (2024–2025)
- Threat profile: In 2024, Côte d’Ivoire recorded 7.5 million cyberattack attempts, including 60 000 identity theft attempts targeting civilian services, military infrastructures, electoral registries, and digital payment platforms.
- Targets: Military, electoral systems, and digital payment systems—underscoring both technical and narrative-driven attack vectors.
- Electoral context (2025): Ahead of the October presidential election, major opposition figures—including Tidjane Thiam, Laurent Gbagbo, Charles Blé Goudé, and Guillaume Soro—were excluded from the final candidate list published on 4 June 2025.
- List finality: The Independent Electoral Commission (CEI), led by Coulibaly‑Kuibiert Ibrahime, announced no further revision of the electoral register would occur before the vote..
- Narrative risk vector: The legal exclusion combined with a fixed submission window (July 25–August 26) constructs a narrow, information‑scarce environment—ideal for reputation attacks via bogus leaks, document falsification, or spoofed portals.
- Strategic interpretation: The limited electoral inclusivity and rigid timelines magnify potential narrative manipulation by actors seeking to simulate fraud or institutional incapacity.
- Sources: Reuters reports (June 4, 2025 – candidate exclusions) ; CEI confirmation of no further register revision :content.
In Côte d’Ivoire, structural cyber intrusions in 2024 and systemic electoral restrictions in 2025 converge into a hybrid threat environment: narrative ambiguity becomes a strategic tool, allowing reputation-based operations to undermine institutional credibility without requiring technical compromise.
AFJOC — Coordinated Regional Cyber Defense (Africa, 2025)
- Continental response: INTERPOL’s 2025 African Cyberthreat Report calls for regional coordination via AFJOC (Africa Joint Operation against Cybercrime).
- Threat evolution: AI-driven fraud, ransomware, and cybercrime-as-a-service dominating the threat landscape.
- Strategic implication: Highlights the necessity of sovereign runtime attestation and regional policy synchronization.
- Source: INTERPOL Africa Cyber Report 2025
AFJOC exemplifies a pan-African response to hybrid cyber threats—moving beyond technical patchwork to coordinated defense governance. Its operational scope highlights runtime integrity as a sovereign imperative.
Naval Group — Strategic Exposure via Reputation Leak
- Modus operandi: “Neferpitou” publishes 13 GB of allegedly internal data, claims 1 TB tied to Naval CMS systems, coinciding with high-level Indo-Pacific negotiations.
- Sovereign framing: Naval Group dismisses technical breach, insists on reputational targeting.
- Narrative vulnerability: Ambiguous provenance (possible reuse of Thales 2022 breach), lack of forensic certitude fuels speculation and diplomatic pressure.
- Systemic insight: CMS systems’ visibility within defense industry increases attack surface despite zero intrusion.
Naval Group’s incident shows how reputation can be decoupled from system security—exposure of industrial branding alone suffices to pressure negotiations, irrespective of intrusion evidence.
Dassault Rafale — Disinformation Post-Skirmish and Trust Erosion
- Tactic: Synthetic loss narratives post-Operation Sindoor. Gameplay footage (ARMA 3), AI-enhanced visuals, and bot networks flood social media.
- Strategic intent: Shift procurement trust toward Chinese J-10C alternatives. Undermine India-France defense collaboration.
- Corporate response: Dassault CEO publicly debunks losses; Indian MoD affirms Rafale superiority.
- Attack vector: Exploits latency in real-world combat validation versus immediate online simulation. Tempo differential becomes narrative leverage.
Dassault’s case highlights digital asymmetry: speed of synthetic disinformation outpaces real-time refutation. Trust erosion occurs before fact-checking stabilizes perceptions.
Kigen eSIM — Certified Component, Runtime Failure, Sovereign Breach
- Flawed certification chain: Java Card vulnerability in GSMA-certified Kigen eUICC enables runtime extraction of cryptographic keys and profiles.
- Collateral impact: >2 billion devices vulnerable across consumer, industrial, and automotive sectors.
- Strategic blind spots: TS.48 test profile lacks runtime attestation, no revocation mechanism, no post-deployment control layer.
- Geopolitical exploitation: APT41 and Lazarus repurpose cloned eSIM profiles for state-level impersonation and tracking.
- Sovereign countermeasure: NFC HSM runtime attestation proposed to separate dynamic trust from static certification.
Kigen illustrates how certification without runtime guarantees collapses in sovereign threat contexts. Attestation must be dynamic, portable, and verifiable—independent of issuing authority.
Israel–Iran — Predatory Sparrow vs Deepfake Sabotage
- Israeli offensive: In June 2025, Predatory Sparrow disrupted the digital services of Iran’s Sepah Bank, rendering customer operations temporarily inoperative.
- Iranian retaliation: Fake alerts, phishing campaigns, and deepfake operations aimed at creating panic.
- Narrative warfare: Over 60 pro-Iranian hacktivist groups coordinated attacks to simulate financial collapse and fuel unrest.
- Source: DISA escalation report
This conflict pair showcases dual-track warfare: targeted digital disruption of critical banking infrastructure, countered by synthetic information chaos designed to manipulate public perception and incite instability.
Intermediate & Legacy Cases
Recent campaigns reveal a growing sophistication in reputation cyberattacks. However, foundational cases from previous years still shape today’s threat landscape. These legacy incidents actively illustrate persistent vectors—ransomware amplification, unverifiable supply chain compromises, and narrative manipulation—that inform current defense strategies.
Change Healthcare Ransomware Attack (USA, 2024)
- Attack type: Ransomware combined with political reputational sabotage
- Immediate impact: Threat actors exposed over 100 million sensitive medical records, causing $2.9 billion in direct losses and paralyzing healthcare payments for weeks
- Narrative shift: The breach transformed into a media symbol of systemic vulnerability in U.S. healthcare infrastructure, influencing regulatory debates
- Source: U.S. HHS official statement
SolarWinds Software Supply Chain Breach (USA, 2020)
- Attack type: Covert infiltration through compromised update mechanism
- Systemic breach: APT29 infiltrated U.S. federal networks, including the Pentagon and Treasury, sparking concerns over supply chain certification trust
- Strategic consequence: Cybersecurity experts advocated for zero-trust architectures and verified software provenance policies
- Source: CISA breach alert
Colonial Pipeline Critical Infrastructure Sabotage (USA, 2021)
- Attack type: Ransomware disrupting fuel distribution logistics
- Operational impact: The attack triggered massive fuel shortages across the U.S. East Coast, igniting panic buying and public anxiety
- Narrative angle: Policymakers used the incident to challenge America’s energy independence and highlight outdated infrastructure protections
- Source: FBI attribution report
Estée Lauder Cloud Security Exposure (2020)
- Incident type: Public cloud misconfiguration without encryption
- Data disclosed: 440 million log entries surfaced online; none classified as sensitive but amplified for reputational damage
- Narrative exploitation: Media outlets reframed the incident as emblematic of weak corporate data governance, despite its low-risk technical scope
- Source: ZDNet technical analysis
GhostNet Global Cyber Espionage Campaign (2009)
- Origin point: China
- Infiltration method: Long-range surveillance across embassies, ministries, and NGOs in over 100 countries
- Reputational effect: The attack revealed the reputational power of invisible espionage and framed global cyber defense urgency
- Source: Archived GhostNet investigation
Signal Clone Breach – TeleMessage Spoofing Campaign (2025)
- Vector exploited: Brand mimicry and codebase confusion via Signal clone
- Security breach: Attackers intercepted communications of diplomats and journalists, casting widespread doubt on secure messaging apps
- Source: Freemindtronic breach analysis
Change Healthcare — Systemic Paralysis via Ransomware
- Incident: In February 2024, the ransomware group Alphv/BlackCat infiltrated Change Healthcare, disrupting critical healthcare operations across the United States.
- Impact: Over 100 million medical records exposed, halting prescription services and claims processing nationwide.
- Reputational fallout: The American Hospital Association labeled it the most impactful cyber incident in U.S. health system history.
- Aftermath: A $22 million ransom was paid; projected losses reached $2.9 billion.
Snowflake Cloud Breach — Cascading Reputation Collapse
- Event: In April 2024, leaked credentials enabled the Scattered Spider group to access customer environments hosted by Snowflake.
- Affected parties: AT&T (70M users), Ticketmaster (560M records), Santander Bank.
- Strategic gap: Several Snowflake tenants had no multi-factor authentication enabled, revealing governance blind spots.
- Reputational impact: The breach questioned shared responsibility models and trust in cloud-native zero-trust architectures.
Salt Typhoon APT — Metadata Espionage and Political Signal Leakage
- Threat actor: Salt Typhoon (Chinese APT), targeting U.S. telecoms (AT&T, Verizon).
- Tactics: Passive collection of call metadata and text records involving politicians such as Donald Trump and JD Vance.
- Objective: Narrative manipulation through reputational subversion and diplomatic misattribution.
- Official coverage: Documented by U.S. security agencies, cited in Congressional Research Service report IF12798.
Legacy is not just history; it’s doctrine.
Common Features & Strategic Objectives
Despite their varied execution, reputation cyberattacks exhibit a set of common features that define their logic, timing, and psychological impact. Recognizing these patterns allows sovereign actors and industrial targets to anticipate narrative shaping attempts and embed active countermeasures within their digital resilience strategy.
Common Features
- Non-technical vectors: Some attacks do not involve system compromise—only plausible disinformation or brand usurpation.
- Perception-centric: They aim at clients, partners, regulators—not infrastructure.
- Strategic timing: Aligned with high-value geopolitical, economic, or regulatory events.
- Narrative instruments: Use of Telegram, forums, deepfakes, AI-generated content, and synthetic media.
- Attribution opacity: Exploits legal and technical gaps in global cyber governance.
Strategic Objectives
- Erode trust in sovereign technologies or industrial actors
- Influence acquisition, regulation, or alliance decisions
- Create asymmetric narratives favoring the attacker
- Delay, deflect, or preempt defense procurement or certification
- Prepare cognitive terrain for future technical or diplomatic intrusion
Reputation cyberattacks blur the lines between cybersecurity, psychological operations, and diplomatic sabotage. Their prevention requires integration of threat intelligence, strategic communications, and runtime trust mechanisms.
Common Features & Strategic Objectives
Despite their varied execution, reputation cyberattacks exhibit a set of common features that define their logic, timing, and psychological impact. Recognizing these patterns allows sovereign actors and industrial targets to anticipate narrative shaping attempts and embed active countermeasures within their digital resilience strategy.
Common Features
- Non-technical vectors: Some attacks do not involve system compromise—only plausible disinformation or brand usurpation.
- Perception-centric: They aim at clients, partners, regulators—not infrastructure.
- Strategic timing: Aligned with high-value geopolitical, economic, or regulatory events.
- Narrative instruments: Use of Telegram, forums, deepfakes, AI-generated content, and synthetic media.
- Attribution opacity: Exploits legal and technical gaps in global cyber governance.
Strategic Outlook
Reputation cyberattacks are no longer peripheral threats. They operate as strategic levers in hybrid conflicts, capable of delaying negotiations, undermining certification, and shifting procurement diplomacy. These attacks are asymmetric, deniable, and narrative-driven. Their true target is sovereignty—technological, diplomatic, and communicational.
The challenge ahead is not merely one of defense, but of narrative command. States and sovereign technology providers must integrate verifiable runtime trust, narrative agility, and resilience to perception distortion. Silence is no longer neutrality; it is vulnerability.
Strong Signals:
- Coordinated leaks following high-level diplomatic statements
- Multiple unverifiable claims against certification authorities
- Escalation in deepfake dissemination tied to defense technologies
Imagine a defense consortium deploying a real-time, attested HSM-based runtime environment that logs and cryptographically proves system integrity in air-gapped mode. A leaked document emerges, claiming operational failure. Within 48 hours, the consortium publishes a verifiable attestation proving non-compromise—transforming a potential discredit into a sovereign show of digital force.
To sustain trust in the era of information warfare, sovereignty must be demonstrable—technically, legally, and narratively.
Narrative Warfare Lexicon
To fortify sovereign understanding and strategy, this lexicon outlines key concepts deployed throughout this chronicle. Each term reflects a recurring mechanism of hybrid influence in reputation-centric cyber conflicts.
Sovereign Attestation:
Verifiable proof of message origin and integrity, enforced by hardware-based cryptography and runtime sealing mechanisms.
Perception Latency:
Delay between technical compromise and public interpretation, allowing adversaries to frame or distort narratives in real-time.
Runtime Ambiguity:
Exploitation of unverified system states or certification gaps during live operation, blurring accountability boundaries.
Trusted Silence:
Intentional lack of institutional response to unverifiable leaks, contrasted by provable data integrity mechanisms.
Strategic Leakage:
Deliberate release of curated data fragments to simulate broader compromise and provoke institutional panic.
Attested Narrative Artifact:
Communication whose authenticity is cryptographically enforced and auditably traceable, independent of central validation.
Adversarial Framing:
Use of metadata, linguistic bias, or visual overlays to recontextualize legitimate content into hostile perception.
Out-of-Band Attestation (NFC HSM):
Isolated cryptographic proof of key integrity, resistant to network manipulation. These air-gapped modules independently enforce the origin and authenticity of communications.
Real-Time Integrity Proof:
Continuous sealing and audit of system states during live operation. Prevents the exploitation of momentary ambiguity or delay in narrative framing.
Dynamic Certification:
Adaptive verification mechanism that evolves with runtime behavior. Unlike static seals, it updates the trust status of components based on real-time performance and sovereign policy triggers.
Temporal Blockchain of Trust:
Time-stamped ledger of cryptographically sealed events, where each proof of integrity becomes a narrative checkpoint. This chained structure forms a verifiable, sovereign memory of truth—resilient against falsification or post-hoc reinterpretation.
Temporal Ledger of Attestation:
A chronologically ordered record of integrity proofs, allowing for verifiable reconstruction of system trust state over time. Especially useful in forensic or diplomatic contexts.
Runtime Proof Anchoring:
Technique by which runtime attestation outputs are immediately sealed and anchored in sovereign repositories, ensuring continuity and traceability of system integrity.
Distributed Sovereign Chronicle:
Federated attestation system in which multiple sovereign or institutional nodes validate and preserve cryptographic proofs of trust, forming a geopolitical ledger of resilience against coordinated narrative subversion.
Beyond This Chronicle
The anatomy of invisible cyberwars is far from complete. As sovereign digital architectures evolve, new layers of hybrid reputational threats will emerge—possibly automated, decentralized, and synthetic by design. These future vectors may combine adversarial AI, autonomous leak propagation, and real-time perception manipulation across untrusted ecosystems.
Tracking these tactics will require more than technical vigilance. It will demand:
- Runtime sovereignty: Systems must cryptographically attest their integrity in real time, independent of external validators.
- Adversarial lexicon auditing: Monitoring how language, metadata, and synthetic narratives are weaponized across platforms.
- Neutral trust anchors: Deploying hardware-based cryptographic roots that remain verifiable even in contested environments.
Freemindtronic’s work on DataShielder NFC HSM and PassCypher HSM PGP exemplifies this shift. These technologies enforce message provenance, runtime attestation, and sovereign encryption—transforming each communication into a verifiable narrative artifact.
Future chronicles will deepen these vectors through:
- Case convergence: Mapping how reputation attacks evolve across sectors, regions, and diplomatic cycles.
- Technological foresight: Anticipating how quantum-safe cryptography, AI-generated disinformation, and decentralized identity will reshape the reputational battlefield.
- Strategic simulation: Modeling sovereign response scenarios to reputational threats using attested environments and synthetic adversaries.
In the next phase, reputation defense will not be reactive—it will be declarative. Sovereignty will be demonstrated not only through infrastructure, but through narrative control, cryptographic visibility, and strategic timing.
Spearphishing APT29 Europe: Unveiling Russia’s Cozy Bear Tactics
APT29 SpearPhishing: Russia’s Stealthy Cyberespionage Across Europe APT29, also known as Cozy Bear or The Dukes, a highly sophisticated Russian statesponsored cyberespionage group, has conducted persistent spearphishing campaigns against a wide range of European entities. Their meticulously planned attacks often target diplomatic missions, think tanks, and highvalue intelligence targets, with the primary objective of longterm intelligence gathering and persistent access. This article provides an indepth analysis of the evolving spearphishing techniques employed by APT29 and outlines essential strategies for robust prevention and detection.
APT29 SpearPhishing Europe: A Stealthy LongTerm Threat
APT29 spearphishing Europe campaigns highlight a persistent and highly sophisticated cyberespionage threat orchestrated by Russia’s Foreign Intelligence Service (SVR), known as Cozy Bear. Active since at least 2008, APT29 has become synonymous with stealthy operations targeting European institutions through phishing emails, Microsoft 365 abuse, supply chain compromises, and persistent malware implants. Unlike APT28’s aggressive tactics, APT29’s approach is patient, subtle, and highly strategic—favoring covert surveillance over immediate disruption. This article examines APT29’s tactics, European targeting strategy, technical indicators, and how sovereign solutions like DataShielder and PassCypher help organizations defend against Russian longterm cyber espionage campaigns.
APT29’s Persistent Espionage Model: The Art of the Long Game in Europe
APT29’s operational model is defined by stealth, longevity, and precision. Their goal is not shortterm chaos but sustained infiltration. Their campaigns frequently last months—or years—without being detected. APT29 rarely causes disruption; instead, it exfiltrates sensitive political, diplomatic, and strategic data across Europe.
APT29 often custombuilds malware for each operation, designed to mimic legitimate network activity and evade common detection tools.
Covert Techniques and Key Infiltration Methods
APT29’s longterm access strategy hinges on advanced, covert methods of penetration and persistence:
Custom Backdoors
Backdoors like “WellMess” and “WellMail” use encrypted communications, steganography, and cloud services to evade inspection. They also include antianalysis techniques such as antiVM and antidebugging code to resist forensic examination.
Supply Chain Attacks
The SolarWinds Orion attack in 2020 remains one of the largest breaches attributed to APT29. This compromise of the supply chain allowed attackers to infiltrate highvalue targets via trusted software. The SUNBURST and TEARDROP implants enabled stealthy lateral movement.
SpearPhishing from Compromised Diplomatic Sources
APT29’s phishing operations often originate from hijacked diplomatic email accounts, lending legitimacy to phishing attempts. These emails target government bodies, international organizations, and embassies across Europe.
Credential Harvesting via Microsoft 365
APT29 abuses cloud infrastructure by executing OAuth consent phishing, targeting legacy authentication protocols, and compromising user credentials to access SharePoint, Outlook, and cloudstored documents.
GRAPELOADER and WINELOADER: New Malware Lures in 2025
In April 2025, APT29 launched a phishing campaign dubbed SPIKEDWINE, impersonating a European Ministry of Foreign Affairs and inviting victims to fake winetasting events. These emails, sent from domains like bakenhof[.]com and silry[.]com, delivered malware via a file named “wine.zip.”
The attack chain begins with GRAPELOADER, a previously undocumented loader, followed by a new variant of the WINELOADER backdoor. This multistage infection shows evolving sophistication in malware design, timing of payload execution, and evasion techniques. The campaign’s targets include multiple European Ministries of Foreign Affairs and nonEuropean embassies in Europe.
Geopolitical Implications of APT29’s European Operations
APT29’s spear-phishing activities are not just technical threats—they are instruments of Russian geopolitical strategy. The group’s consistent targeting of ministries, embassies, and think tanks across Europe aligns closely with key diplomatic and policy moments.
APT29’s operations often intensify ahead of European elections, EU-NATO summits, or major sanctions announcements. Their goal is not only to steal sensitive intelligence, but to subtly influence policymaking by gaining access to classified assessments, private negotiations, or internal dissent.
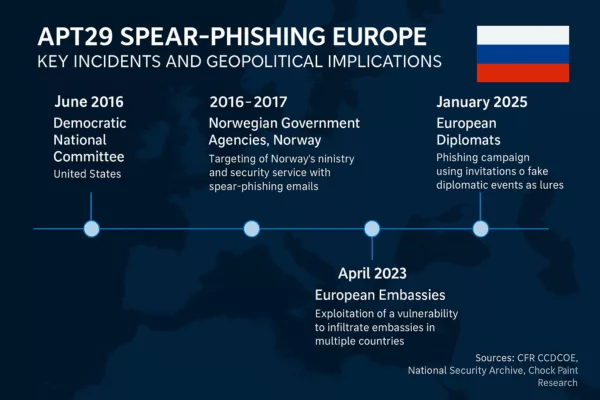
Notable examples include:
- The 2016 and 2017 attacks on Norwegian government agencies, including the Ministry of Defense and the Norwegian Labour Party (CCDCOE)
- The 2025 campaign targeting diplomats with wine-tasting lures (Check Point Research)
- The 2023 exploitation of WinRAR CVE-2023-38831 against embassies in Greece, Italy, Romania, and Azerbaijan (National Security Archive)
- APT29’s targeting of German political parties ahead of the 2021 elections (Google Cloud Blog, CSO Online)
APT29 acts as a digital vanguard for Russian hybrid warfare, where cyber operations feed into diplomatic leverage, information warfare, and strategic disruption. Understanding this broader agenda is crucial for shaping European cyber defense beyond the technical dimension.
European Government Responses to APT29: A Patchwork Defense

This comparison illustrates the fragmented nature of Europe’s institutional responses to state-sponsored cyber threats. While some nations have clearly identified and named APT29, others remain more cautious or reactive.
What if APT29 Had Not Been Detected?
While some operations were eventually uncovered, many persisted for months or years. Had APT29 remained entirely undetected, the implications for Europe’s political and strategic landscape could have been far-reaching:
- Diplomatic Blackmail: With access to confidential negotiations, APT29 could have leaked selective intelligence to disrupt alliances or blackmail key figures.
- Policy Manipulation: Strategic leaks before elections or summits could steer public opinion, weaken pro-EU narratives, or stall collective defense decisions.
- NATO Cohesion Threats: Exfiltrated defense policy data could be used to exploit divisions between NATO member states, delaying or undermining unified military responses.
- Influence Campaign Fuel: Stolen data could be recontextualized by Russian disinformation actors to construct persuasive narratives tailored to fracture European unity.
This scenario highlights the necessity of early detection and sovereign countermeasures—not merely to block access, but to neutralize the geopolitical utility of the exfiltrated data.
Notable APT29 Incidents in Europe
| Date | Operation Name | Target | Outcome |
|---|---|---|---|
| 2015 | CozyDuke | U.S. & EU diplomatic missions | Long-term surveillance and data theft |
| 2020 | SolarWinds | EU/US clients (supply chain) | 18,000+ victims compromised, long undetected persistence |
| 2021–2023 | Microsoft 365 Abuse | EU think tanks | Credential theft and surveillance |
| 2024 | European Diplomatic | Ministries in FR/DE | Phishing via embassy accounts; linked to GRAPELOADER malware |
| 2025 | SPIKEDWINE | European MFA, embassies | GRAPELOADER + WINELOADER malware via wine-tasting phishing lure |
Timeline Sources & Attribution
This infographic is based on verified public threat intelligence from:
- Council on Foreign Relations
- Check Point Research
- National Security Archive
- Google Cloud Blog (Mandiant)
- CSO Online
- KnowBe4 Security Blog
These sources confirm that APT29 remains a persistent threat actor with geopolitical aims, leveraging cyber operations as a tool of modern espionage and strategic influence.
APT29 vs. APT28: Divergent Philosophies of Intrusion
| Tactic/Group | APT28 (Fancy Bear) | APT29 (Cozy Bear) |
| Affiliation | GRU (Russia) | SVR (Russia) |
| Objective | Influence, disruption | Longterm espionage |
| Signature attack | HeadLace, CVE exploit | SolarWinds, GRAPELOADER, WINELOADER |
| Style | Aggressive, noisy | Covert, patient |
| Initial Access | Broad phishing, zerodays | Targeted phishing, supply chain |
| Persistence | Common tools, fast flux | Custom implants, stealthy C2 |
| Lateral Movement | Basic tools (Windows) | Stealthy tools mimicking legit activity |
| AntiAnalysis | Obfuscation | AntiVM, antidebugging |
| Typical Victims | Ministries, media, sports | Diplomacy, think tanks, intel assets |
Weak Signals and Detection Opportunities
European CERTs have identified subtle signs that may suggest APT29 activity:
- Unusual password changes in Microsoft 365 without user request
- PowerShell usage from signed binaries in uncommon contexts
- Persistent DNS beaconing to rare C2 domains
- Abnormal OneDrive or Azure file transfers and permission changes
- Phishing emails tied to impersonated ministries and fake event lures
Defensive Strategies: Building European Resilience
Effective defense against APT29 requires:
- ⇨ Hardwarebased MFA (FIDO2, smartcards) to replace SMS/app OTPs
- ⇨ Enforcing least privilege and strict access policies
- ⇨ Monitoring DNS traffic and lateral movement patterns
- ⇨ Deploying EDR/XDR tools with heuristic behavior analysis
- ⇨ Ingesting threat intelligence feeds focused on APT29 TTPs
- ⇨ Running regular threat hunts to detect stealthy TTPs early
Sovereign Protection: PassCypher & DataShielder Against APT29
To counter espionage tactics like those of APT29, Freemindtronic offers two offline, hardwarebased solutions:
- DataShielder NFC HSM: A fully offline, contactless authentication tool immune to phishing and credential replay.
- PassCypher HSM PGP: Stores passwords and cryptographic secrets in a hardware vault, protected from keylogging, memory scraping, and BITB attacks.
Both tools decrypt only in volatile memory, ensuring no data is written locally, even temporarily.
Regulatory Compliance
- ⇨ French Decree No. 20241243: Encryption devices for dualuse (civil/military)
- ⇨ EU Regulation (EU) 2021/821 (latest update 2024)
- ⇨ Distributed exclusively in France by AMG PRO:
Threat Coverage Table: PassCypher & DataShielder vs. APT29
This table evaluates sovereign cyber defenses against known APT29 TTPs.
| Threat Type | APT29 Presence | PassCypher Coverage | DataShielder Coverage |
|---|---|---|---|
| Targeted spearphishing | ✔ | ✔ Secure Input, No Leakage |
✔ Offline Authentication |
| Supply chain compromise | ✔ | ✔ Endtoend encrypted communication; passwords and OTPs decrypted in volatile memory only |
✔ Offline preencryption; data decrypted only in memory during reading |
| Microsoft 365 credential harvesting | ✔ | ✔ Offline Storage, BITB Protection |
✔ Offline Authentication |
| Trusted cloud abuse (OneDrive, Azure) | ✔ | ✔ URL Filtering, Secure Vault |
✔ Offline Authentication |
| Persistent implants | ✔ | ✔ Encrypted session use; keys and OTPs inaccessible without HSM |
✔ Offline encrypted data cannot be used even with full system compromise |
| Exploits via infected documents | ✔ | ✔ Encrypted Sandbox Links |
✔ Encrypted Key Context |
| Phishing via diplomatic accounts | ✔ | ✔ Secure Input, Spoofing Protection |
✔ Offline Credential Isolation |
| Lateral movement (PowerShell) | ✔ | ✔ Credentials isolated by HSM; attacker gains no usable secrets |
✔ Persistent encryption renders accessed data useless |
| DNS beaconing | ✔ | ✔ Decryption keys never online; exfiltrated data stays encrypted |
✔ Offline encrypted messages never intelligible without HSM |
Legend: ✔ = Direct mitigation | ⚠ = Partial mitigation | ✘ = Not covered
Note: PassCypher and DataShielder focus not on preventing all access, but on neutralizing its strategic value. Isolated credentials and persistently encrypted data render espionage efforts ineffective.
Towards a Sovereign and Proactive Defense Against the APT29 Threat in Europe
APT29’s quiet and persistent threat model demands proactive, sovereign responses. Passive, reactive security measures are no longer enough. European organizations must integrate national technologies like PassCypher and DataShielder to ensure digital sovereignty, compartmentalization, and offline security.
The adoption of segmented, resilient, and hardwarebacked architectures enables:
- Independence from cloudbased MFA
- Resistance to credential reuse and session hijacking
- Full data lifecycle control with no data remnants
CISOs, critical infrastructure operators, and government entities must evaluate the security coverage and complementarity of each tool to craft a cohesive strategy against persistent Russian cyber threats.
To explore our full methodology and technical breakdown APT29 read the complete article.
Glossary (for Non-Technical Readers)
- Spear-phishing: A targeted email attack that appears personalized to trick specific individuals into clicking malicious links or attachments.
- C2 (Command and Control) Infrastructure: A network of hidden servers controlled by attackers to manage malware remotely and exfiltrate stolen data.
- OAuth Consent Phishing: A technique where attackers trick users into granting access permissions to malicious applications through legitimate cloud services.
- Anti-VM / Anti-Debugging: Techniques used in malware to avoid being detected or analyzed by virtual machines or security researchers.
- Supply Chain Attack: An attack that compromises trusted software or service providers to distribute malware to their clients.
- Volatile Memory Decryption: A security method where sensitive data is decrypted only in the device’s memory (RAM), never stored unencrypted.
- Persistent Threat: An attacker who remains within a network for a long time without being detected, often for intelligence gathering.
Russian Espionage: How Western Hacking Tools Were Turned Against Their Makers
Russian cyberattack on Microsoft by Midnight Blizzard (APT29) highlights the strategic risks to digital sovereignty. Discover how the group exploited password spraying, malicious OAuth applications, and legacy exposure — and the sovereign countermeasures offered by DataShielder and PassCypher.
Executive Summary — Midnight Blizzard (APT29) vs Microsoft
⚡ Objective
Understand how Midnight Blizzard (aka APT29, Cozy Bear) leveraged password spraying, malicious OAuth apps, and legacy exposure to access Microsoft’s internal email and escalate risks across tenants — and how sovereign HSM controls would have contained impact.
💥 Scope
Microsoft corporate mailboxes, executive communications, and internal collaboration workflows; spillover risk to customers and partners via token reuse and app-consent abuse.
🔑 Doctrine
APT29 favors low-noise, cloud-adjacent persistence without obvious malware. Defenders must harden identity (conditional access), monitor OAuth consent creation, rate-limit auth anomalies, and treat encrypted-egress analytics as first-class telemetry.
🌍 Strategic differentiator
Unlike cloud-only defenses, DataShielder & PassCypher adopt a zero cloud, zero disk, zero DOM posture with segmented-key HSM custody (NFC/PGP). Result ⮞ encrypted content remains unreadable even under mailbox compromise; credentials/OTP remain offline and non-replayable.
Technical Note
Reading time (summary): ≈ 3 minutes
Reading time (full): ≈ 15 minutes
Level: Cyberculture / Digital Security
Posture: Identity-first hardening, sovereign encryption (HSM)
Section: Digital Security
Language: FR · EN · CAT · ES
Editorial type: Chronicle
About the author: Jacques Gascuel — Inventor of Freemindtronic®, expert in sovereign HSM architectures, segmented keys (NFC/PGP), and offline, resilient communications.
TL;DR —
Midnight Blizzard (APT29) combined password spraying with malicious OAuth to access Microsoft internal mail. Even with rapid containment (SFI), token-based lateralization and app-consent persistence raised downstream risk. DataShielder keeps content end-to-end encrypted with volatile-memory decryption only; PassCypher stores credentials/OTP offline in HSM, defeating replay and loginless phishing sequences.
- Executive Summary — Midnight Blizzard vs Microsoft
- Microsoft Admits Russian Cyberattack Was Worse Than Expected
- Background & Technical Details
- Immediate Response from Microsoft
- Impact of Compromised Emails
- Statistical Consequences of the Cyberattack
- Ongoing escalation & data reuse
- October 2024 RDP spear-phishing campaign
- Midnight Blizzard Threat Timeline (HC3)
- Advanced Encryption & Sovereign HSM Solutions
- Global Reactions & Security Measures
- Best Practices to Prevent Russian Cyberattacks
- Comparison with Other Cyberattacks
- Strategic Aftermath — Outlook beyond Midnight Blizzard
- Related links — Russian APT actors
- Weak Signals — Trends to watch
Microsoft Admits Russian Cyberattack Was Worse Than Expected
What changed vs. initial reports
- Discovery of legacy account exposure used as the initial foothold, then pivot to internal email.
- Evidence of token-based lateralization (OAuth consent misuse) across tenants and partners.
- Tenfold increase in password-spray attempts in the weeks that followed, expanding downstream risk.
Why it matters
Midnight Blizzard is a state-sponsored actor assessed as part of Russia’s foreign-intelligence ecosystem, historically targeting governments, NGOs, and IT/service providers in the US and Europe. The campaign underscores how cloud-adjacent identity abuse (OAuth, tokens, legacy accounts) can bypass classical malware-centric defenses and compromise digital sovereignty at scale.
Authoritative references
See Microsoft’s Secure Future Initiative (SFI), Microsoft’s incident communications on Midnight Blizzard (MSRC/On the Issues), and the U.S. CISA Emergency Directive ED-24-02 for official guidance and required mitigations.
This section is part of our in-depth coverage of the Russian Cyberattack Microsoft incident involving Midnight Blizzard.
Background & Technical Details — Russian Cyberattack Microsoft
The Russian Cyberattack Microsoft incident, orchestrated by Midnight Blizzard (APT29/Cozy Bear), revealed a sophisticated combination of password spraying at scale (CISA ED-24-02) and the abuse of malicious OAuth applications. By exploiting a legacy non-production account, attackers gained foothold into Microsoft’s corporate mailboxes, including executive and legal teams.
This operation mirrors past campaigns such as SolarWinds supply-chain compromise, but with a focus on cloud tokens and stealth persistence. The breach emphasized weaknesses in tenant isolation, consent governance, and token refresh lifecycles.
Technical analysis shows how Midnight Blizzard avoided traditional endpoint detections by staying cloud-adjacent: no heavy malware, only abused credentials and trusted OAuth flows. This approach drastically reduced IOC visibility and prolonged dwell time inside Microsoft systems.
Microsoft responded with its Secure Future Initiative (SFI), which prioritizes identity hardening, OAuth monitoring, and sovereign-aligned mitigations. Still, the attack highlights a systemic risk: when cloud identity is compromised, mailbox confidentiality collapses unless sovereign HSM solutions (DataShielder, PassCypher) are enforced.
Immediate Response from Microsoft
On January 12, 2024, Microsoft detected unauthorized access to its internal systems. The security team immediately activated a response process to investigate and mitigate the attack. Midnight Blizzard compromised a legacy non-production test account, gaining access to several internal email accounts, including those of senior executives and critical teams like cybersecurity and legal.
Impact of Compromised Emails from the Russian Cyberattack
Midnight Blizzard managed to exfiltrate internal Microsoft emails, including sensitive information shared between the company and its clients. The attackers used this information to attempt access to other systems and increased the volume of password spray attacks by tenfold in February 2024. This led to an increased risk of compromise for Microsoft’s clients.
Statistical Consequences of the Russian Cyberattack on Microsoft
- Increase in Attacks: In February 2024, the volume of password spray attacks was ten times higher than in January 2024.
- Multiple Targets: The compromised emails allowed Midnight Blizzard to target not only Microsoft but also its clients, thereby increasing the risk of compromise across various organizations.
- Access to Internal Repositories: The attackers were able to access some source code repositories and internal systems, although no customer-facing systems were compromised.
Statistical Consequences of the Russian Cyberattack on Microsoft
Analysis of the Midnight Blizzard (APT29) incident highlights the statistical footprint left on Microsoft and its ecosystem. According to CISA Emergency Directive ED-24-02, downstream exposure went far beyond initial intrusion:
- 10× increase in password-spray attacks during February 2024 compared to January, escalating brute-force telemetry.
- Multiple targets compromised: from Microsoft executive teams to strategic partners, amplifying the risk of supply-chain lateralization.
- Internal repositories accessed: some source code and mailbox content exfiltrated — while Microsoft stressed that no customer-facing systems were breached.
- Regulatory alert: U.S. federal agencies were ordered by CISA to reset credentials and secure Entra ID/Azure privileged authentication tools.
This statistical aftermath confirms the systemic risks of cloud-identity compromise: once OAuth tokens and mailbox credentials are stolen, propagation extends across tenants and partners. Without sovereign HSM custody (DataShielder & PassCypher), organizations remain exposed to credential replay and stealth exfiltration.
Ongoing Escalation & Data Reuse — Russian Cyberattack Microsoft
After the January 2024 compromise, APT29/Midnight Blizzard did not stop at Microsoft’s initial remediation. Instead, the group weaponized data already stolen to sustain access and broaden espionage reach. According to CISA alerts and Microsoft’s own Secure Future Initiative (SFI), adversaries systematically:
- Replayed OAuth tokens harvested from compromised accounts to bypass fresh credential resets.
- Exfiltrated mail archives used to craft targeted spear-phishing campaigns against partners and governments.
- Leveraged leaked correspondence to execute disinformation and hybrid-conflict narratives.
- Expanded persistence through new malicious OAuth application consents, evading traditional MFA checks.
This escalation phase illustrates that the Russian Cyberattack Microsoft was not a one-time event but an ongoing campaign with iterative exploitation. For defenders, this confirms the need for sovereign cryptographic containment: while cloud identities can be replayed, DataShielder and PassCypher ensure that exfiltrated data remains undecipherable and credentials are non-replayable due to offline segmented-key HSM custody.
October 2024 RDP Spear-Phishing Campaign — Russian Cyberattack Microsoft
.RDP files. These attachments initiated covert remote desktop sessions, bypassing traditional email security and extending persistence.On October 16, 2024, Microsoft confirmed that Midnight Blizzard actors were distributing .RDP attachments in targeted phishing campaigns. When opened, the files automatically launched remote desktop sessions to attacker-controlled infrastructure, effectively granting adversaries direct access to victim environments.
This new tactic leveraged trusted file types and signed components to evade standard email filters and sandboxing. The campaign primarily targeted government entities, NGOs, and IT providers in Europe and North America, aligning with APT29’s long-term espionage doctrine.
According to CISA alerts and ENISA threat bulletins, the malicious RDP sessions allowed attackers to:
- Establish persistent remote control bypassing traditional login prompts.
- Harvest additional credentials through Windows authentication requests inside the RDP session.
- Deploy secondary payloads undetected by endpoint monitoring, as the activity was masked as legitimate remote access.
For defenders, this October 2024 escalation illustrates how Russian APTs adapt quickly, shifting from OAuth abuse to remote desktop weaponization. Without sovereign safeguards, even encrypted mail channels remain insufficient against file-based phishing vectors.
Here, DataShielder and PassCypher deliver layered resilience: offline decryption ensures malicious .RDP payloads cannot auto-open decrypted content, while HSM-segmented key custody prevents credential replay inside remote sessions.
Midnight Blizzard Threat Timeline (HC3) — Russian Cyberattack Microsoft
The U.S. Department of Health and Human Services Health Sector Cybersecurity Coordination Center (HC3) published a June 2024 threat profile detailing APT29’s operational history. Key stages align with the escalation observed in the Russian Cyberattack Microsoft:
- 2018–2020: Initial reliance on spear-phishing and credential harvesting, including campaigns against U.S. and European institutions.
- 2020–2021: SolarWinds supply-chain compromise, marking APT29’s ability to exploit trusted third-party software ecosystems.
- 2022–2023: Transition to cloud identity abuse, including malicious OAuth applications and stealthy persistence.
- 2024: Large-scale escalation with Microsoft corporate mailbox compromise, password spraying at scale, and token replay — culminating in October spear-phishing via
.RDPfiles.
According to CISA and ENISA, APT29 demonstrates a doctrine of hybrid conflict cyber-espionage: combining stealth persistence, identity abuse, and information operations. This timeline confirms the progressive escalation model of Midnight Blizzard campaigns.
Defensive takeaways: only sovereign HSM architectures (e.g., DataShielder, PassCypher) can neutralize token replay and ensure that exfiltrated data remains encrypted and non-exploitable across campaign phases.
Advanced Encryption and Security Solutions
To resist state-grade threats, organizations should enforce robust encryption with sovereign key custody. Technologies like
DataShielder NFC HSM, DataShielder HSM PGP, and DataShielder Auth NFC HSM encrypt emails and attachments end-to-end while keeping decryption keys offline inside an HSM (NFC/PGP).
If Midnight Blizzard had accessed an executive mailbox protected by DataShielder, message bodies and files would have remained unreadable. Decryption occurs only in volatile memory after physical HSM presence and multi-factor checks. This neutralizes token replay and limits the blast radius of OAuth or identity abuse.
Beyond confidentiality, the sovereign design simplifies incident response: keys are never hosted in the provider’s cloud, and credentials or OTPs managed with segmented keys are not replayable across OAuth/RDP sessions.
Global Reactions and Security Measures
This attack highlights the ongoing risks posed by well-funded state actors. In response, Microsoft launched the Secure Future Initiative (SFI). This initiative aims to strengthen the security of legacy systems and improve internal processes to defend against such cyber threats. The company has also adopted a transparent approach, quickly sharing details of the attack and closely collaborating with government agencies to mitigate risks.
Microsoft’s Secure Future Initiative (SFI) aims to harden legacy infrastructure. In parallel, CISA and ENISA coordinate sectoral resilience guidance for critical operators.
Best Practices in Cybersecurity to Prevent Russian Cyberattacks
To protect against these threats, companies must adopt robust security measures. Multi-factor authentication and continuous system monitoring are crucial. Additionally, implementing regular security updates is essential. The CISA emergency directive ED 24-02 requires affected federal agencies to analyze the content of exfiltrated emails, reset compromised credentials, and secure authentication tools for privileged Azure accounts (CISA).
Beyond classical defenses, sovereign encryption and segmented HSM custody ensure that even if OAuth tokens or mailboxes are compromised, sensitive data remains cryptographically unusable.
Comparison with Other Cyberattacks
This attack is reminiscent of other major incidents, such as those against SolarWinds and Colonial Pipeline. These attacks demonstrate the evolving techniques of attackers and the importance of maintaining constant vigilance. Companies must be ready to respond quickly and communicate transparently with stakeholders to minimize damage and restore trust.
See CISA SolarWinds advisory and Colonial Pipeline cyberattack report for context.
The Sovereign Takeaway — Russian Cyberattack Microsoft
Only a sovereign HSM posture — with DataShielder and PassCypher — ensures that exfiltrated data or stolen tokens remain cryptographically unusable.
This doctrine of zero cloud, zero disk, zero DOM with segmented HSM custody is what transforms a breach into a contained incident rather than a systemic crisis. It marks the line between conventional cloud security and sovereign cryptographic resilience.
Further Reading: For extended analysis, see our chronicle on the Midnight Blizzard cyberattack against Microsoft & HPE, authored by Jacques Gascuel.
Strategic Aftermath — Outlook beyond the Russian Cyberattack Microsoft
A sovereign posture treats cloud identity as ephemeral and sensitive content as persistently encrypted under offline HSM custody.
In the wake of the Russian Cyberattack Microsoft, three shifts are non-negotiable. First, identity becomes telemetry-driven: conditional access, consent creation, and token lifecycles are continuously scored, not merely logged. Second, communications become sovereign by default: message bodies and files remain unreadable without physical HSM presence, even if mailboxes are accessed. Third, credentials and OTPs leave the cloud: segmented-key custody prevents reuse across OAuth, Graph, or RDP flows.
- Containment by design — Enforce zero cloud, zero disk, zero DOM decryption paths; treat tokens as hostile until proven otherwise.
- Operational continuity — Maintain an out-of-band sovereign channel for IR, so investigations never depend on compromised tenants.
- Partner hygiene — Require OAuth consent baselines and cross-tenant anomaly sharing; audit refresh-token lifetimes.
Practically, this outlook translates into DataShielder for end-to-end content encryption with volatile-memory decryption, and PassCypher for offline credential custody and non-replayable OTP. Together, they narrow the blast radius of future APT29-style campaigns while preserving mission continuity.
Real-world sovereign use case — Russian Cyberattack Microsoft (executive mailbox compromised)
- During the Russian Cyberattack Microsoft (Midnight Blizzard / APT29), an executive’s mailbox is accessed via token replay.
- Emails & attachments remain unreadable: content is end-to-end encrypted with DataShielder; decryption occurs only in volatile memory after NFC HSM presence.
- Credentials & OTP are never exposed: PassCypher stores them offline with segmented keys, preventing replay inside OAuth/RDP sessions.
- Operations continue seamlessly: an out-of-band sovereign channel maintains secure communications during incident response, with no cloud keys to rotate.
Related links — Russian APT actors
- APT28 — Outlook spear-phishing & NotDoor backdoor in Europe
GRU-linked APT28: Outlook zero-days, mailbox-resident malware (NotDoor), and information ops across EU & France. - APT29 — Spear-phishing in Europe: stealthy Russian espionage
SVR/Cozy Bear: stealth campaigns leveraging cloud relays and low-persistence tactics, complementary to Midnight Blizzard’s methods. - APT29 — Exploitation of app passwords
Bypassing classical credentials via OAuth/app passwords; illustrates why sovereign identity hardening is crucial. - Russian espionage hacking tools revealed
Technical inventory of Russian cyber-espionage arsenals, shedding light on APT29’s evolving toolkit. - Reputation & cyberattacks in hybrid conflicts
Strategic analysis: how Russian APT campaigns (including APT29) fuel hybrid warfare and influence operations. - APT44 — QR-code phishing & blended info-ops
Sandworm/GRU: QR-code phishing, mobile-first vectors, and hybrid information warfare converging with Russian spear-phishing doctrines.
Weak Signals — Trends to Watch Beyond the Russian Cyberattack Microsoft
These evolutions are consistent with the Russian hybrid warfare doctrine, where cyber-espionage (APT29) and influence operations converge to destabilize strategic sectors.
Looking ahead, the aftermath of the Midnight Blizzard (APT29) intrusion offers insights into future trends in Russian cyber-espionage:
- AI-augmented spear-phishing: Generative AI may increase the credibility and linguistic adaptation of phishing lures, complicating detection (ENISA reports).
- Encrypted C2 channels inside cloud apps: Expect wider abuse of collaboration platforms (Teams, SharePoint) with end-to-end encrypted exfiltration masquerading as normal traffic.
- OAuth & token lifecycle attacks: Beyond classic consent abuse, attackers may pivot to refresh token manipulation and multi-cloud federation exploits.
- Hybrid conflict synchronization: Cyber intrusions paired with influence campaigns targeting elections, energy policy, and EU institutional trust.
- Regulatory misalignment: While frameworks such as EU CRA and NIS2 strengthen defenses, uneven adoption leaves OIV/OES with exploitable gaps.
These signals reinforce the necessity of sovereign cryptographic architectures. With DataShielder and PassCypher, organizations can enforce offline key segmentation, volatile-memory decryption, and encrypted egress control, making exfiltrated data strategically useless to adversaries.