WebAuthn API Hijacking: A critical vulnerability, unveiled at DEF CON 33, demonstrates that synced passkeys can be phished in real time. Indeed, Allthenticate proved that a spoofable authentication prompt can hijack a live WebAuthn session.
Executive Summary — The WebAuthn API Hijacking Flaw
▸ Key Takeaway — WebAuthn API Hijacking
We provide a dense summary (≈ 1 min) for decision-makers and CISOs. For a complete technical analysis (≈ 13 min), however, you should read the full article.
Imagine an authentication method lauded as phishing-resistant — namely, synced passkeys — and then exploited live at DEF CON 33 (August 8–11, 2025, Las Vegas). So what was the vulnerability? It was a WebAuthn API Hijacking flaw (an interception attack on the authentication flow), which allowed for passkeys real-time prompt spoofing.
This single demonstration, in fact, directly challenges the proclaimed security of cloud-synced passkeys and opens the debate on sovereign alternatives. We saw two key research findings emerge at the event: first, real-time prompt spoofing (a WebAuthn interception attack), and second, DOM extension clickjacking. Notably, this article focuses exclusively on prompt spoofing because it undeniably undermines the “phishing-resistant” promise for vulnerable synced passkeys.
▸ Summary
The weak link is no longer cryptography; instead, it is the visual trigger. In short, attackers compromise the interface, not the cryptographic key.
Chronique à lire
Article to Read
Estimated reading time: ≈ 13 minutes (+4–5 min if you watch the embedded videos)
Complexity level: Advanced / Expert
Available languages: CAT · EN · ES · FR
Accessibility: Optimized for screen readers
Type: Strategic Article
Author: Jacques Gascuel, inventor and founder of Freemindtronic®, designs and patents sovereign hardware security systems for data protection, cryptographic sovereignty, and secure communications. As an expert in ANSSI, NIS2, GDPR, and SecNumCloud compliance, he develops by-design architectures capable of countering hybrid threats and ensuring 100% sovereign cybersecurity.
▸ Official Sources
- Talk « Your Passkey is Weak : Phishing the Unphishable » (Allthenticate) — listed in the DEF CON 33 official schedule
- Presentation « Passkeys Pwned : Turning WebAuthn Against Itself » — available on the DEF CON media server
- Article « Phishing-Resistant Passkeys Shown to Be Phishable at DEF CON 33 » — relayed by MENAFN / PR Newswire, Science & Tech section
TL; DR
- At DEF CON 33 (August 8–11, 2025), Allthenticate researchers demonstrated a WebAuthn API Hijacking path: attackers can hijack so-called “phishing-resistant” passkeys via real-time prompt spoofing.
- The flaw does not reside in cryptographic algorithms; rather, it’s found in the user interface—the visual entry point.
- Ultimately, this revelation demands a strategic revision: we must prioritize device-bound passkeys for sensitive use cases and align deployments with threat models and regulatory requirements.
In Sovereign Cybersecurity ↑ This article is part of our Digital Security section, continuing our research on zero-trust hardware exploits and countermeasures.
Strategic Navigation
- Executive Summary
- What is a WebAuthn Interception Attack?
- History of Passkey / WebAuthn Vulnerabilities
- Vulnerability of the Synchronization Model
- DEF CON 33 Demonstration
- Technical Context
- Prompt Spoofing vs. DOM Clickjacking
- Strategic Implications
- Regulations & Compliance
- European & Francophone Statistics
- Sovereign Use Case
- Why PassCypher Eliminates the WebAuthn Interception Risk
- PassCypher NFC HSM — Hardware Neutralization of Interception
- PassCypher HSM PGP — Segmented Keys Against Phishing
- Attack Surface Comparison
- Weak Signals
- Strategic Glossary
- Technical FAQ (Integration & Use Cases)
- CISO / CSO Advice – Universal & Sovereign Protection
- CISO / CSO FAQ
- CISO / CSO Action Plan
- Strategic Outlook
▸ Key Points
- Confirmed Vulnerability: Cloud-synced passkeys (Apple, Google, Microsoft) are not 100% phishing-resistant.
- New Threat: Real-time prompt spoofing exploits the user interface rather than cryptography.
- Strategic Impact: Critical infrastructure and government agencies must migrate to device-bound credentials and sovereign offline solutions (NFC HSM, segmented keys).
What is a WebAuthn API Hijacking Attack?
A WebAuthn interception attack via a spoofable authentication prompt (WebAuthn API Hijacking) consists of imitating in real time the authentication window displayed by a system or browser. Consequently, the attacker does not seek to break the cryptographic algorithm; instead, they reproduce the user interface (UI) at the exact moment the victim expects to see a legitimate prompt. Visual lures, precise timing, and perfect synchronization make the deception indistinguishable to the user.
A user thinks they are approving a connection to their bank account via a legitimate Apple or Google system prompt. In reality, they are interacting with a dialog box cloned by the attacker. As a result, the adversary captures the active session without alerting the victim.
History of Passkey / WebAuthn Vulnerabilities
Despite their cryptographic robustness, passkeys — based on the open standards WebAuthn and FIDO2 from the FIDO Alliance — are not invulnerable. The history of vulnerabilities and recent research confirms that the key weakness often lies in the user interaction and the execution environment (browser, operating system). The industry officially adopted passkeys on May 5, 2022, following a commitment from Apple, Google, and Microsoft to extend their support on their respective platforms.
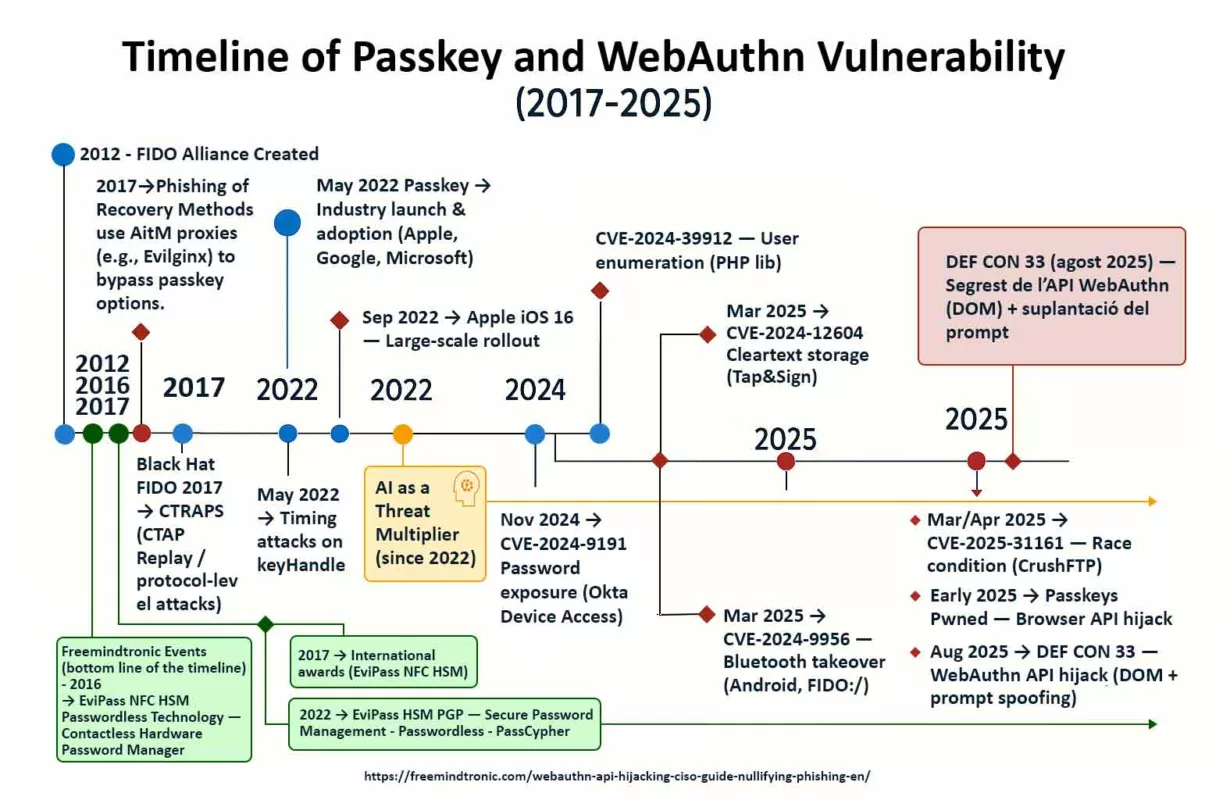
Timeline of Vulnerabilities
-
SquareX – Compromised Browsers (August 2025):
At DEF CON 33, a demonstration showed that a malicious extension or script can intercept the WebAuthn flow to substitute keys. See the TechRadar analysis and the SecurityWeek report.
-
CVE-2025-31161 (March/April 2025):
Authentication bypass in CrushFTP via a race condition. Official NIST Source.
-
CVE-2024-9956 (March 2025):
Account takeover via Bluetooth on Android. This attack demonstrated that an attacker can remotely trigger a malicious authentication via a FIDO:/ intent. Analysis from Risky.Biz. Official NIST Source.
-
CVE-2024-12604 (March 2025):
Cleartext storage of sensitive data in Tap&Sign, exploiting poor password management. Official NIST Source.
-
CVE-2025-26788 (February 2025):
Authentication bypass in StrongKey FIDO Server. Detailed Source.
-
Passkeys Pwned – Browser-based API Hijacking (Early 2025):
A research study showed that the browser, as a single mediator, can be a point of failure. Read the Security Boulevard analysis.
-
CVE-2024-9191 (November 2024):
Password exposure via Okta Device Access. Official NIST Source.
-
CVE-2024-39912 (July 2024):
User enumeration via a flaw in the PHP library web-auth/webauthn-lib. Official NIST Source.
-
CTRAPS-type Attacks (2024):
These protocol-level attacks (CTAP) exploit authentication mechanisms for unauthorized actions. For more information on FIDO protocol-level attacks, see this Black Hat presentation on FIDO vulnerabilities.
-
First Large-Scale Rollout (September 2022):
Apple was the first to deploy passkeys on a large scale with the release of iOS 16, making this technology a reality for hundreds of millions of users. Official Apple Press Release.
-
Industry Launch & Adoption (May 2022):
The FIDO Alliance, joined by Apple, Google, and Microsoft, announced an action plan to extend passkey support across all their platforms. Official FIDO Alliance Press Release.
-
Timing Attacks on keyHandle (2022):
A vulnerability allowing account correlation by measuring time variations in the processing of keyHandles. See IACR ePrint 2022 article.
-
Phishing of Recovery Methods (since 2017):
Attackers use AitM proxies (like Evilginx, which appeared in 2017) to hide the passkey option and force a fallback to less secure methods that can be captured. More details on this technique.
AI as a Threat Multiplier
Artificial intelligence is not a security flaw, but a catalyst that makes existing attacks more effective. Since the emergence of generative AI models like GPT-3 (2020) and DALL-E 2 (2022), new capabilities for automating threats have appeared. These developments notably allow for:
- Large-scale Attacks (since 2022): Generative AI enables attackers to create custom authentication prompts and phishing messages for a massive volume of targets, increasing the effectiveness of phishing of recovery methods.
- Accelerated Vulnerability Research (since 2023): AI can be used to automate the search for security flaws, such as user enumeration or the detection of logical flaws in implementation code.
“These recent and historical vulnerabilities highlight the critical role of the browser and the deployment model (device-bound vs. synced). They reinforce the call for sovereign architectures that are disconnected from these vectors of compromise.”
Vulnerability of the Synchronization Model
One of the most debated passkeys security vulnerabilities does not concern the WebAuthn protocol itself, but its deployment model. Most publications on the subject differentiate between two types of passkeys:
- Device-bound passkeys: Stored on a physical device (like a hardware security key or Secure Enclave). This model is generally considered highly secure because it is not synchronized via a third-party service.
- Synced passkeys: Stored in a password manager or a cloud service (iCloud Keychain, Google Password Manager, etc.). These passkeys can be synchronized across multiple devices. For more details on this distinction, refer to the FIDO Alliance documentation.
The vulnerability lies here: if an attacker manages to compromise the cloud service account, they could potentially gain access to the synced passkeys across all the user’s devices. This is a risk that device-bound passkeys do not share. Academic research, such as this paper published on arXiv, explores this issue, highlighting that “the security of synced passkeys is primarily concentrated with the passkey provider.”
This distinction is crucial because the implementation of vulnerable synced passkeys contradicts the very spirit of a so-called phishing-resistant MFA, as synchronization introduces an intermediary and an additional attack surface. This justifies the FIDO Alliance’s recommendation to prioritize device-bound passkeys for maximum security.
The DEF CON 33 Demonstration – WebAuthn API Hijacking in Action
WebAuthn API Hijacking is the central thread of this section: we briefly explain the attack path shown at DEF CON 33 and how a spoofable prompt enabled real-time session takeover, before detailing the live evidence and the video highlights.
Passkeys Pwned — DEF CON 33 Talk on WebAuthn
During DEF CON 33, the Allthenticate team presented a talk titled “Passkeys Pwned: Turning WebAuthn Against Itself.”
This session demonstrated how attackers could exploit WebAuthn API Hijacking to
compromise synced passkeys in real time using a spoofable authentication prompt.
By using the provocative phrase “Passkeys Pwned,” the researchers deliberately emphasized that even so-called phishing-resistant credentials can be hijacked when the user interface itself is the weak link.
Evidence of WebAuthn API Hijacking at DEF CON 33
In Las Vegas, at the heart of DEF CON 33 (August 8–11, 2025), the world’s most respected hacker community witnessed a demonstration that made many squirm. In fact, researchers at Allthenticate showed live that a vulnerable synced passkey – despite being labeled “phishing-resistant” – could be tricked. So what did they do? They executed a WebAuthn API Hijacking attack (spoofing the system prompt) of the spoofable authentication prompt type (real-time prompt spoofing). They created a fake authentication dialog box, perfectly timed and visually identical to the legitimate UI. Ultimately, the user believed they were validating a legitimate authentication, but the adversary hijacked the session in real time. This proof of concept makes the “Passkeys WebAuthn Interception Flaw” tangible through a real-time spoofable prompt.
Video Highlights — WebAuthn API Hijacking in Practice
To visualize the sequence, watch the clip below: it shows how WebAuthn API Hijacking emerges from a simple UI deception that aligns timing and look-and-feel with the expected system prompt, leading to seamless session capture.
▸ Shourya Pratap Singh, Jonny Lin, Daniel Seetoh — Allthenticate researchers, authors of the demo “Your Passkey is Weak: Phishing the Unphishable”.
• Allthenticate Video on TikTok — direct explanation by the team.
• DEF CON 33 Las Vegas Video (TikTok) — a glimpse of the conference floor.
• Highlights DEF CON 33 (YouTube) — including the passkeys flaw.
▸ Summary
DEF CON 33 demonstrated that vulnerable synced passkeys can be compromised live when a spoofable authentication prompt is inserted into the WebAuthn flow.
Comparison – WebAuthn Interception Flaw: Prompt Spoofing vs. DOM Clickjacking
At DEF CON 33, two major research findings shook confidence in modern authentication mechanisms. Indeed, both exploit flaws related to the user interface (UX) rather than cryptography, but their vectors and targets differ radically.
Real-Time Prompt Spoofing
- Author: Allthenticate (Las Vegas, DEF CON 33).
- Target: vulnerable synced passkeys (Apple, Google, Microsoft).
- Vecteur: spoofable authentication prompt, perfectly timed to the legitimate UI (real-time prompt spoofing).
- Impact: WebAuthn interception attack that causes “live” phishing; the user unknowingly validates a malicious request.
DOM Clickjacking
- Authors: Another team of researchers (DEF CON 33).
- Target: Credential managers, extensions, stored passkeys.
- Vecteur: invisible iframes, Shadow DOM, malicious scripts to hijack autofill.
- Impact: Silent exfiltration of credentials, passkeys, and crypto-wallet keys.
▸ Key takeaway: This article focuses exclusively on prompt spoofing, which illustrates a major WebAuthn interception flaw and challenges the promise of “phishing-resistant passkeys.” For a complete study on DOM clickjacking, please see the related article.
Strategic Implications – Passkeys and UX Vulnerabilities
As a result, the “Passkeys WebAuthn Interception Flaw” forces us to rethink authentication around prompt-less and cloud-less models.
- We should no longer consider vulnerable synced passkeys to be invulnerable.
- We must prioritize device-bound credentials for sensitive environments.
- We need to implement UX safeguards: detecting anomalies in authentication prompts and using non-spoofable visual signatures.
- We should train users on the threat of real-time phishing via a WebAuthn interception attack.
It is not cryptography that is failing, but the illusion of immunity. WebAuthn interception demonstrates that the risk lies in the UX, not the algorithm.
Regulations & Compliance – MFA and WebAuthn Interception
Official documents such as the CISA guide on phishing-resistant MFA or the OMB M-22-09 directive insist on this point: authentication is “phishing-resistant” only if no intermediary can intercept or hijack the WebAuthn flow.
In theory, WebAuthn passkeys respect this rule. In practice, however, the implementation of vulnerable synced passkeys opens an interception flaw that attackers can exploit via a spoofable authentication prompt.
In Europe, both the NIS2 directive and the SecNumCloud certification reiterate the same requirement: no dependence on un-mastered third-party services.
As such, the “Passkeys WebAuthn Interception Flaw” contradicts the spirit of a so-called phishing-resistant MFA, because synchronization introduces an intermediary.
In other words, a US cloud managing your passkeys falls outside the scope of strict digital sovereignty.
▸ Summary
A vulnerable synced passkey can compromise the requirement for phishing-resistant MFA (CISA, NIS2) when a WebAuthn interception attack is possible.
European & Francophone Statistics – Real-time Phishing and WebAuthn Interception
Public reports confirm that advanced phishing attacks — including real-time techniques — represent a major threat in the European Union and the Francophone area.
- European Union — ENISA: According to the Threat Landscape 2024 report, phishing and social engineering account for 38% of reported incidents in the EU, with a notable increase in Adversary-in-the-Middle methods and real-time prompt spoofing, associated with WebAuthn interception. Source: ENISA Threat Landscape 2024
- France — Cybermalveillance.gouv.fr: In 2023, phishing generated 38% of assistance requests, with over 1.5M consultations related to this type of attack. Fake bank advisor scams jumped by +78% vs. 2022, often via spoofable authentication prompts. Source: 2023 Activity Report
- Canada (Francophone) — Canadian Centre for Cyber Security: The National Cyber Threat Assessment 2023-2024 indicates that 65% of businesses expect to experience a phishing or ransomware attack. Phishing remains a preferred vector for bypassing MFA, including via WebAuthn flow interception. Source: Official Assessment
Real-time prompt spoofing is not a lab experiment; it is part of a trend where phishing targets the authentication interface rather than algorithms, with increasing use of the WebAuthn interception attack.
Sovereign Use Case – Neutralizing WebAuthn Interception
In a practical scenario, a regulatory authority reserves synced passkeys for low-risk public portals. Conversely, the PassCypher choice eliminates the root cause of the “Passkeys WebAuthn Interception Flaw” by removing the prompt, the cloud, and any DOM exposure.
For critical systems (government, sensitive operations, vital infrastructure), it deploys PassCypher in two forms:
- PassCypher NFC HSM — offline hardware authentication, with no server and BLE AES-128-CBC keyboard emulation. Consequently, no spoofable authentication prompt can exist.
- PassCypher HSM PGP — sovereign management of inexportable segmented keys, with cryptographic validation that is cloud-free and synchronization-free.
▸ Result
In this model, the prompt vector exploited during the WebAuthn interception attack at DEF CON 33 is completely eliminated from critical pathways.
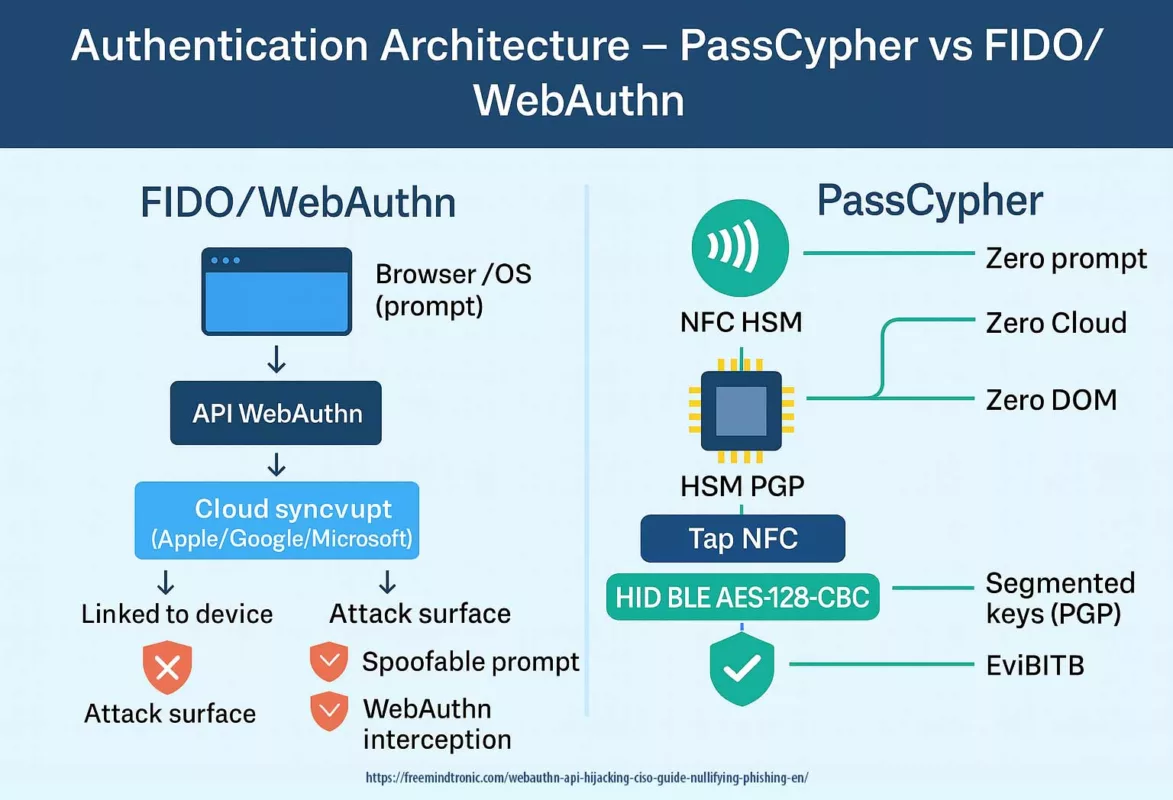
Why PassCypher Eliminates the WebAuthn Interception Risk
PassCypher solutions stand in radical contrast to FIDO passkeys that are vulnerable to the WebAuthn interception attack:
- No OS/browser prompt — thus no spoofable authentication prompt.
- No cloud — no vulnerable synchronization or third-party dependency.
- No DOM — no exposure to scripts, extensions, or iframes.
PassCypher NFC HSM — Eliminating the WebAuthn Prompt Spoofing Attack Vector
Allthenticate’s attack at DEF CON 33 proves that attackers can spoof any system that depends on an OS/browser prompt. PassCypher NFC HSM removes this vector: there is no prompt, no cloud sync, secrets are encrypted for life in a nano-HSM NFC, and validated by a physical tap. User operation:
- Mandatory NFC tap — physical validation with no software interface.
- HID BLE AES-128-CBC Mode — out-of-DOM transmission, resistant to keyloggers.
- Zero-DOM Ecosystem — no secret ever appears in the browser.
▸ Summary
Unlike vulnerable synced passkeys, PassCypher NFC HSM neutralizes the WebAuthn interception attack because a spoofable authentication prompt does not exist.
WebAuthn API Hijacking Neutralized by PassCypher NFC HSM
| Attack Type | Vector | Status |
|---|---|---|
| Prompt Spoofing | Fake OS/browser dialog | Neutralized (zero prompt) |
| Real-time Phishing | Live-trapped validation | Neutralized (mandatory NFC tap) |
| Keystroke Logging | Keyboard capture | Neutralized (encrypted HID BLE) |
PassCypher HSM PGP — Segmented Keys Against Phishing
The other pillar, PassCypher HSM PGP, applies the same philosophy: no exploitable prompt.
Secrets (credentials, passkeys, SSH/PGP keys, TOTP/HOTP) reside in AES-256 CBC PGP encrypted containers, protected by a patented system of segmented keys.
- No prompt — so there is no window to spoof.
- Segmented keys — they are inexportable and assembled only in RAM.
- Ephemeral decryption — the secret disappears immediately after use.
- Zero cloud — there is no vulnerable synchronization.
▸ Summary
PassCypher HSM PGP eliminates the attack surface of the real-time spoofed prompt: it provides hardware authentication, segmented keys, and cryptographic validation with no DOM or cloud exposure.
Attack Surface Comparison
| Criterion | Synced Passkeys (FIDO) | PassCypher NFC HSM | PassCypher HSM PGP |
|---|---|---|---|
| Authentication Prompt | Yes | No | No |
| Synchronization Cloud | Yes | No | No |
| Exportable Private Key | No (attackable UI) | No | No |
| WebAuthn Hijacking/Interception | Present | Absent | Absent |
| FIDO Standard Dependency | Yes | No | No |
Weak Signals – Trends Related to WebAuthn Interception
▸ Weak Signals Identified
- The widespread adoption of real-time UI attacks, including WebAuthn interception via a spoofable authentication prompt.
- A growing dependency on third-party clouds for identity, which increases the exposure of vulnerable synced passkeys.
- A proliferation of bypasses through AI-assisted social engineering, applied to authentication interfaces.
Strategic Glossary
A review of the key concepts used in this article, for both beginners and advanced readers.
-
Passkey / Passkeys
A passwordless digital credential based on the FIDO/WebAuthn standard, designed to be “phishing-resistant.”
- Passkey (singular): Refers to a single digital credential stored on a device (e.g., Secure Enclave, TPM, YubiKey).
- Passkeys (plural): Refers to the general technology or multiple credentials, including synced passkeys stored in Apple, Google, or Microsoft clouds. These are particularly vulnerable to WebAuthn API Hijacking (real-time prompt spoofing demonstrated at DEF CON 33).
-
Passkeys Pwned
Title of the DEF CON 33 talk by Allthenticate (“Passkeys Pwned: Turning WebAuthn Against Itself”). It highlights how WebAuthn API Hijacking can compromise synced passkeys in real time, proving that they are not 100% phishing-resistant.
-
Vulnerable synced passkeys
Stored in a cloud (Apple, Google, Microsoft) and usable across multiple devices. They offer a UX advantage but a strategic weakness: dependence on a spoofable authentication prompt and the cloud.
-
Device-bound passkeys
Linked to a single device (TPM, Secure Enclave, YubiKey). More secure because they lack cloud synchronization.
-
Prompt
A system or browser dialog box that requests a user’s validation (Face ID, fingerprint, FIDO key). This is the primary target for spoofing.
-
WebAuthn Interception Attack
Also known as WebAuthn API Hijacking, this attack manipulates the authentication flow by spoofing the system/browser prompt and imitating the user interface in real time. The attacker does not break cryptography, but intercepts the WebAuthn process at the UX level (e.g., a cloned fingerprint or Face ID prompt). See the official W3C WebAuthn specification and FIDO Alliance documentation.
-
Real-time prompt spoofing
The live spoofing of an authentication window, which is indistinguishable to the user.
-
DOM Clickjacking
An attack using invisible iframes and Shadow DOM to hijack autofill and steal credentials.
-
Zero-DOM
A sovereign architecture where no secret is exposed to the browser or the DOM.
-
NFC HSM
A secure hardware module that is offline and compatible with HID BLE AES-128-CBC.
-
Segmented keys
Cryptographic keys that are split into segments and only reassembled in volatile memory.
-
Device-bound credential
A credential attached to a physical device that is non-transferable and non-clonable.
Technical FAQ (Integration & Use Cases)
-
Q: Are there any solutions for vulnerable passkeys?
A: Yes, in a hybrid model. Keep FIDO for common use cases and adopt PassCypher for critical access to eliminate WebAuthn interception vectors.
-
Q: What is the UX impact without a system prompt?
A: The action is hardware-based (NFC tap or HSM validation). There is no spoofable authentication prompt or dialog box to impersonate, resulting in a total elimination of the real-time phishing risk.
-
Q: How can we revoke a compromised key?
A: You simply revoke the HSM or the key itself. There is no cloud to purge and no third-party account to contact.
-
Q: Does PassCypher protect against real-time prompt spoofing?
A: Yes. The PassCypher architecture completely eliminates the OS/browser prompt, thereby removing the attack surface exploited at DEF CON 33.
-
Q: Can we integrate PassCypher into a NIS2-regulated infrastructure?
A: Yes. The NFC HSM and HSM PGP modules comply with digital sovereignty requirements and neutralize the risks associated with vulnerable synced passkeys.
-
Q: Are device-bound passkeys completely inviolable?
A: No, but they do eliminate the risk of cloud-based WebAuthn interception. Their security then depends on the hardware’s robustness (TPM, Secure Enclave, YubiKey) and the physical protection of the device.
-
Q: Can a local malware reproduce a PassCypher prompt?
A: No. PassCypher does not rely on a software prompt; the validation is hardware-based and offline, so no spoofable display exists.
-
Q: Why do third-party clouds increase the risk?
A: Vulnerable synced passkeys stored in a third-party cloud can be targeted by Adversary-in-the-Middle or WebAuthn interception attacks if the prompt is compromised.
CISO/CSO Advice – Universal & Sovereign Protection
To learn how to protect against WebAuthn interception, it’s important to know that EviBITB (Embedded Browser-In-The-Browser Protection) is a built-in technology in PassCypher HSM PGP, including its free version. t automatically or manually detects and removes redirection iframes used in BITB and prompt spoofing attacks, thereby eliminating the WebAuthn interception vector.
- Immediate Deployment: It is a free extension for Chromium and Firefox browsers, scalable for large-scale use without a paid license.
- Universal Protection: It works even if the organization has not yet migrated to a prompt-free model.
- Sovereign Compatibility: It works with PassCypher NFC HSM Lite (99 €) and the full PassCypher HSM PGP (129 €/year).
- Full Passwordless: Both PassCypher NFC HSM and HSM PGP can completely replace FIDO/WebAuthn for all authentication pathways, with zero prompts, zero cloud, and 100% sovereignty.
Strategic Recommendation:
Deploy EviBITB immediately on all workstations to neutralize BITB/prompt spoofing, then plan the migration of critical access to a full-PassCypher model to permanently remove the attack surface.
Frequently Asked Questions for CISOs/CSOs
Q: What is the regulatory impact of a WebAuthn interception attack?
Q: Is there a universal and free protection against BITB and prompt spoofing?
Q: Are there any solutions for vulnerable passkeys?
Q: What is the average budget and ROI of a migration to a prompt-free model?
Q: How can we manage a hybrid fleet (legacy + modern)?
Q: What metrics should we track to measure the reduction in attack surface?
CISO/CSO Action Plan
| Priority Action | Expected Impact |
|---|---|
| Implement solutions for vulnerable passkeys by replacing them with PassCypher NFC HSM (99 €) and/or PassCypher HSM PGP (129 €/year) | Eliminates the spoofable prompt, removes WebAuthn interception, and enables sovereign passwordless access with a payback period of days according to the study on authentication time |
| Migrate to a full-PassCypher model for critical environments | Removes all FIDO/WebAuthn dependency, centralizes sovereign management of access and secrets, and maximizes productivity gains measured by the study |
| Deploy EviBITB (embedded technology in PassCypher HSM PGP, free version included) | Provides immediate, zero-cost protection against BITB and real-time phishing via prompt spoofing |
| Harden the UX (visual signatures, non-cloneable elements) | Complicates UI attacks, clickjacking, and redress |
| Audit and log authentication flows | Detects and tracks any attempt at flow hijacking or Adversary-in-the-Middle attacks |
| Align with NIS2, SecNumCloud, and GDPR | Reduces legal risk and provides proof of compliance |
| Train users on spoofable interface threats | Strengthens human vigilance and proactive detection |
Strategic Outlook
The message from DEF CON 33 is clear: authentication security is won or lost at the interface. In other words, as long as the user validates graphical authentication prompts synchronized with a network flow, real-time phishing and WebAuthn interception will remain possible.
Thus, prompt-free and cloud-free models — embodied by sovereign HSMs like PassCypher — radically reduce the attack surface.
In the short term, generalize the use of device-bound solutions for sensitive applications. In the medium term, the goal is to eliminate the spoofable UI from critical pathways. Ultimately, the recommended trajectory will permanently eliminate the “Passkeys WebAuthn Interception Flaw” from critical pathways through a gradual transition to a full-PassCypher model, providing a definitive solution for vulnerable passkeys in a professional context.










































































































