La confidentialité des métadonnées e-mail est au cœur de la souveraineté numérique en Europe : prenez connaissance des risques, le cadre légal UE (RGPD/ePrivacy) et les contre-mesures DataShielder.
Résumé de la chronique — confidentialité métadonnées e-mail
⚡ Objectif
Comprendre ce que révèlent réellement les métadonnées e-mail (adresses IP, horodatages, destinataires, serveurs intermédiaires), pourquoi elles restent accessibles même lorsque le contenu est chiffré, et comment l’Union européenne encadre leur usage (RGPD, ePrivacy, décisions CNIL et Garante).
💥 Portée
Cet article s’adresse aux organisations et individus concernés par la confidentialité des communications : journalistes, ONG, entreprises, administrations.
>Il couvre les e-mails (SMTP, IMAP, POP), les messageries chiffrées de bout en bout, la téléphonie, la visioconférence, le web, les réseaux sociaux, l’IoT, le cloud, le DNS et même les blockchains.
🔑 Doctrine
Les métadonnées sont un invariant structurel : elles ne peuvent être supprimées du protocole mais peuvent être neutralisées et cloisonnées.
>Les solutions classiques (VPN, PGP, SPF/DKIM/DMARC, MTA-STS) protègent partiellement, mais la souveraineté numérique impose d’aller plus loin avec DataShielder HSM (NFC et HSM PGP) qui encapsule le contenu, réduit la télémétrie et compartimente les usages.
🌍 Différenciateur stratégique
Contrairement aux approches purement logicielles ou cloud, DataShielder adopte une posture zero cloud, zero disque, zero DOM. Il chiffre en amont (offline), encapsule le message, et laisse ensuite la messagerie (chiffrée ou non) appliquer son propre chiffrement.
>Résultat ⮞ double chiffrement, neutralisation des métadonnées de contenu (subject, pièces jointes, structure MIME) et opacité renforcée face aux analyses de trafic. Un différenciateur stratégique pour les communications sensibles dans l’espace européen et au-delà.
Note technique
Temps de lecture (résumé) : ≈ 4 minutes
Temps de lecture (intégral) : ~35 minutes
Niveau : Sécurité / Cyberculture / Digital Security
Posture : Encapsulation souveraine, défense en profondeur
Rubriques : Digital Security
Langues disponibles : FR · EN · CAT · ES
Type éditorial : Chronique
À propos de l’auteur : Jacques Gascuel, inventeur Freemindtronic® — architectures HSM souveraines, segmentation de clés, résilience hors-ligne, protection souveraine des communications.
TL;DR — Métadonnées, risques et cadre légal
Les métadonnées e-mail révèlent plus que le contenu. Elles tracent qui parle à qui, quand et via quels serveurs. Les solutions classiques (VPN, TLS, PGP) ne les masquent pas.
>Seule une approche souveraine comme DataShielder (NFC HSM & HSM PGP) permet de réduire la surface, neutraliser les métadonnées de contenu par encapsulation, et empêcher la corrélation abusive.
>En 2025, la Cour de cassation a confirmé que les métadonnées e-mail sont des données personnelles au sens du RGPD, même après rupture de contrat.
La CNIL a sanctionné SHEIN pour dépôt de traceurs sans consentement, renforçant l’exigence de granularité et de transparence.
TL;DR — Architecture souveraine et différenciateur
Face à la montée des attaques par IA générative et quishing, la neutralisation des métadonnées devient une exigence stratégique.
>DataShielder introduit un double chiffrement offline et un mode d’encapsulation segmentée certifié TRL9, rendant les métadonnées de contenu inexploitables par les intermédiaires.
>Ce mécanisme n’est pas un effet secondaire : il est volontairement mis en œuvre pour cloisonner les usages, segmenter les identités et créer une opacité cryptographique.
Un différenciateur souverain pour les communications sensibles dans l’espace européen et au-delà.
En cybersécurité et souveraineté numérique ↑ cette chronique appartient à la rubrique Cyberculture et s’inscrit dans l’outillage opérationnel souverain de Freemindtronic (HSM, segmentation de clés, encapsulation, résilience hors-ligne).
- Résumé de la chronique
- Qu’est-ce qu’une métadonnée ?
- Quelles sont les métadonnées e-mail (RFC 5321/5322) ?
- Ce que voient les fournisseurs
- Statistiques francophones et européennes
- Risques d’exploitation — profilage et surveillance
- Cadre légal UE — RGPD, ePrivacy et vie privée des e-mails
- Usage judiciaire des métadonnées dans les procédures pénales
- Défenses classiques — protocoles de messagerie et limites
- Contre-mesures souveraines — DataShielder™
- Flux souverain — encapsulation hors ligne
- Messageries chiffrées de bout en bout (E2EE)
- Au-delà de l’e-mail — métadonnées des communications
- Autres infrastructures — IoT, cloud, blockchain et traces techniques
- Cybersécurité et espionnage — usages légitimes vs abusifs
- Cas d’usage réels — ONG, journalistes, PME
- Guide pratique — réduire l’exposition des e-mail
- Signaux faibles 2025→2027 — tendances émergentes
- FAQ — questions fréquentes sur les métadonnées e-mail
- Perspectives stratégiques — souveraineté
Définition — Qu’est-ce qu’une métadonnée ?
Le terme métadonnée désigne littéralement une donnée sur la donnée. C’est une information contextuelle qui décrit, encadre ou qualifie un contenu numérique sans en faire partie. Les métadonnées sont omniprésentes : elles accompagnent chaque fichier, chaque communication et chaque enregistrement technique.
- Exemples courants — Par exemple, un document Word contient l’auteur et la date de modification. De même, une photo intègre les coordonnées GPS, tandis qu’un e-mail inclut l’adresse IP de l’expéditeur et l’heure d’envoi.
- Fonction première — Faciliter le tri, la recherche et la gestion des données dans les systèmes numériques.
- Effet secondaire — Exposer des traces exploitables pour le suivi, la surveillance ou la corrélation, même lorsque le contenu est chiffré.
⮞ Résumé
Les métadonnées sont des données de contexte. Elles ne disent pas ce qui est communiqué, mais révèlent plutôt comment, quand, où et par qui. Elles sont indispensables au fonctionnement des systèmes numériques, mais constituent aussi une surface d’exposition stratégique.
Quelles sont les métadonnées e-mail (RFC 5321/5322) ?
La confidentialité des métadonnées e-mail repose sur une distinction protocolaire essentielle. En effet, le contenu d’un message (corps du texte, pièces jointes) n’est pas la même chose que ses métadonnées. Les normes RFC 5321 (SMTP) et RFC 5322 (format des en-têtes) codifient ces informations. Elles définissent quelles données sont visibles et lesquelles sont cachées. Elles incluent : l’adresse expéditeur (From), le ou les destinataires (To, Cc), l’objet (Subject), l’horodatage (Date), l’identifiant unique (Message-ID) et la liste des relais SMTP traversés (Received headers).
Ces données ne disparaissent pas lors du chiffrement du message par PGP ou S/MIME. Elles restent exposées aux fournisseurs, FAI et opérateurs intermédiaires. En pratique, elles constituent une véritable cartographie sociale et technique de vos échanges.
Chez les journalistes, ces traces suffisent à révéler des contacts supposés confidentiels.
Du côté des ONG, elles exposent réseaux de partenaires, bailleurs de fonds et relais locaux.
Quant aux entreprises, elles révèlent les flux d’affaires, rythmes décisionnels et horaires d’activité. Cette granularité invisible rend les métadonnées extrêmement puissantes. Elles deviennent ainsi un outil de surveillance souvent plus efficace que le contenu lui-même.
⮞ Résumé
Définies par les RFC 5321/5322, les métadonnées e-mail regroupent les en-têtes et traces de transport. Elles sont indispensables au routage mais impossibles à masquer. Résultat : elles révèlent identité, chronologie et infrastructures des échanges, même lorsque le contenu est chiffré.

Ce que voient les fournisseurs
La confidentialité des métadonnées e-mail se heurte à une réalité technique. En effet, les fournisseurs d’accès à Internet et les opérateurs de messagerie disposent d’une visibilité quasi totale sur les en-têtes et les flux. À chaque connexion, les serveurs enregistrent l’adresse IP de l’expéditeur et les horodatages. Ils notent également les serveurs relais traversés. Même si le contenu est chiffré, cette télémétrie reste exploitable.
Chez Google, l’infrastructure Gmail conserve systématiquement les en-têtes complets. Cela permet une corrélation fine entre utilisateurs et appareils.
Microsoft (Outlook/Exchange Online) applique des politiques similaires. Il intègre ces données aux systèmes de détection d’anomalies et de conformité.
De même, les fournisseurs européens tels qu’Orange ou SFR conservent également les journaux SMTP/IMAP/POP. Ils le font en vertu des obligations légales de conservation dictées par les régulateurs nationaux et européens.
Le minimum reste visible : l’adresse IP du serveur est toujours exposée. Par ailleurs, selon la configuration du client (webmail, application mobile, client lourd), l’adresse IP de l’utilisateur peut également apparaître dans les en-têtes. Cette exposition, cumulée aux métadonnées de routage, suffit à construire un profil technique. De plus, elle permet de créer un profil comportemental des correspondants.
Les fournisseurs (Google, Microsoft, Orange) conservent systématiquement les en-têtes et adresses IP. Même sous chiffrement, ces données restent visibles et permettent de profiler les échanges. Les adresses IP serveur sont toujours exposées, et selon le client utilisé, l’IP utilisateur peut l’être également.
Actualités récentes — e-mail (2024→2025)
CNIL — Pixels de suivi dans les e-mails : la CNIL a lancé une consultation publique afin de cadrer les tracking pixels par le consentement RGPD. Les synthèses publiques confirment la volonté d’encadrement strict (juin–juillet 2025).
UE — EDPB : rappel que les pixels traquent la lecture d’e-mails et constituent des traitements soumis au cadre RGPD/ePrivacy.
Gmail/Yahoo → Microsoft/Outlook : après Google/Yahoo (02/2024), Microsoft aligne ses exigences pour gros émetteurs (SPF, DKIM, DMARC) avec mesures renforcées à partir du 05/05/2025.
Italie — Garante : durcissement sur la rétention des métadonnées d’e-mail des salariés (référence 7 jours, prorogeable 48h) et première amende GDPR 2025 pour conservation illicite de métadonnées.
⮞ Synthèse e-mail
L’écosystème impose DMARC/SPF/DKIM aux gros émetteurs et encadre les pixels de suivi. La conformité devient un prérequis de délivrabilité, alors que la confidentialité des métadonnées e-mail reste un enjeu RGPD central.
Événements récents — La pertinence des métadonnées en 2025
Les derniers mois de l’année 2025 ont été marqués par des évolutions majeures. Jurisprudence, sanctions, protocoles et menaces émergentes confirment que les métadonnées ne sont plus un détail technique, mais un enjeu central de souveraineté numérique.
Actualités — Messageries & E2EE
Les débats autour du chiffrement de bout en bout et des métadonnées résiduelles s’intensifient. Plusieurs événements récents illustrent cette tension.
- Proton : En juin et juillet 2025, Proton a mis à jour ses politiques de confidentialité et renforcé son système de blocage des pixels espions. Les URLs de suivi sont désormais bloquées par défaut, et un outil d’importation sécurisé permet de migrer depuis les webmails classiques sans exposer les métadonnées. Consulter les politiques de Proton.
- WhatsApp (Meta) : En juin 2025, WhatsApp a étendu le chiffrement de bout en bout à tous les fichiers et plateformes, y compris WhatsApp Web, en s’appuyant sur le protocole Signal. Toutefois, l’introduction de publicités ciblées dans l’onglet “Updates” montre que les métadonnées restent exploitées à des fins commerciales. Lire l’analyse sur WhatsApp 2025.
Événements juridiques & techniques
L’enjeu des métadonnées e-mail ne cesse de croître. Voici les faits marquants qui confirment la pertinence de cette chronique.
- Jurisprudence & droits des salariés : En juin 2025, la Cour de cassation a confirmé que les métadonnées e-mail sont des données personnelles, même après rupture de contrat. Ce droit d’accès postérieur renforce l’obligation de maîtrise souveraine des traces numériques.
- Cybersécurité & IA générative : Le rapport HarfangLab “State of Cybersecurity 2025” révèle que 58 % des entreprises européennes considèrent désormais l’IA comme leur menace principale. Les attaques par quishing, deepfakes et scripts polymorphes se multiplient. Lire le rapport HarfangLab.
- Sanctions CNIL & infrastructures centralisées : En septembre 2025, la CNIL a sanctionné Shein pour dépôt de traceurs sans consentement, et clôturé l’injonction contre Orange après vérification du retrait effectif des cookies tiers. Ces décisions confirment l’exigence de granularité et de traçabilité dans la gestion des métadonnées. Voir la décision CNIL contre Orange.
⮞ Synthèse
Ces développements confirment un signal fort : la confidentialité des métadonnées est désormais un enjeu juridique, stratégique et opérationnel. Elle dépasse les considérations techniques pour devenir un pilier de la souveraineté numérique. L’approche défendue par DataShielder™ — encapsulation offline, cloisonnement des usages, neutralisation granulaire — s’inscrit pleinement dans cette dynamique.
Statistiques francophones et européennes sur la confidentialité des métadonnées e-mail
📊 Tendances générales
La confidentialité des métadonnées e-mail n’est pas qu’un enjeu théorique : elle est mesurable. Plusieurs études en Europe et dans l’espace francophone démontrent l’ampleur du phénomène et ses impacts sur la vie privée, la cybersécurité et la souveraineté numérique.
🇪🇺 Europe et espace francophone
- France — Selon la CNIL, plus de 72 % des plaintes liées à la vie privée en 2024 concernaient la collecte excessive de données de communication, dont les métadonnées e-mail. En 2025, la CNIL a renforcé sa stratégie européenne pour encadrer les flux transfrontaliers et les métadonnées techniques.
- Union européenne — L’EDPB indique que 85 % des fournisseurs européens conservent les adresses IP et les en-têtes SMTP entre 6 mois et 2 ans. Les lignes directrices 01/2025 sur la pseudonymisation rappellent que les métadonnées doivent être cloisonnées dès la collecte.
- Italie — En 2025, le Garante a limité la rétention des métadonnées de géolocalisation des salariés à 24h sans justification. Il a également fixé une limite stricte de 21 jours pour les métadonnées d’e-mails professionnels, sauf accord syndical ou autorisation de l’inspection du travail.
- Suisse — L’OFCOM impose une rétention légale des métadonnées de messagerie de 6 mois, même pour les services sécurisés.
- Belgique et Luxembourg — Les régulateurs télécom (IBPT et ILR) confirment que les fournisseurs locaux conservent systématiquement les journaux SMTP pour répondre aux demandes judiciaires, jusqu’à 18 mois.
- Monaco — La CCIN applique une réglementation proche de la CNIL, avec conservation encadrée des métadonnées dans les services publics.
Francophonie hors UE
- Canada (Québec) — Le CRTC impose une conservation proportionnée. En pratique, la durée moyenne varie entre 6 et 12 mois pour les journaux SMTP.
- Maroc — L’ANRT oblige les opérateurs à conserver les métadonnées d’e-mail et de connexion pendant au moins 12 mois.
- Sénégal — La CDP confirme que les fournisseurs doivent stocker les journaux de messagerie pour une durée minimale d’un an.
⮞ Synthèse
Dans l’espace francophone et l’Union européenne, la rétention des métadonnées e-mail est quasi-systématique : de 6 mois (Suisse) à 2 ans (France/UE). Elle s’étend aussi au Québec, au Maroc, au Sénégal, à Monaco et désormais à l’Italie, où des limites strictes sont imposées dans le cadre professionnel.
Face à cette standardisation, l’approche souveraine — encapsulation offline, cloisonnement des usages, neutralisation granulaire — devient non seulement pertinente, mais nécessaire.
Cartographie réglementaire — Durées de rétention par pays
| Pays | Durée de rétention | Cadre légal |
|---|---|---|
| France | Jusqu’à 2 ans | CNIL, RGPD |
| Union européenne | 6 mois à 2 ans | EDPB, RGPD |
| Italie | 24h (géoloc), 21 jours (e-mail pro) | Garante, Statut des travailleurs |
| Suisse | 6 mois | OFCOM |
| Belgique / Luxembourg | Jusqu’à 18 mois | IBPT / ILR |
| Canada (Québec) | 6 à 12 mois | CRTC, LPRPDE |
| Maroc | 12 mois | ANRT |
| Sénégal | 1 an | CDP |
| Monaco | Encadrée | CCIN |
Cette cartographie confirme que la rétention des métadonnées est encadrée, mais rarement minimisée. L’approche souveraine — cloisonnement, encapsulation, neutralisation — devient essentielle pour reprendre le contrôle.
Risques d’exploitation — profilage et surveillance via métadonnées
Les métadonnées e-mail sont un outil d’analyse d’une puissance redoutable. En agrégeant adresses IP, en-têtes SMTP et horodatages, il devient possible de reconstruire un graphe social. Ce graphe révèle qui échange avec qui, à quelle fréquence et dans quel contexte. Ce simple réseau de relations suffit d’ailleurs à cartographier des communautés entières, qu’il s’agisse de journalistes, d’ONG ou d’entreprises.
Dans le domaine économique, ces mêmes données nourrissent des systèmes de profilage publicitaire ou d’espionnage industriel. Les grandes plateformes peuvent ainsi corréler des adresses techniques avec des comportements d’achat. Elles les associent également à des connexions géographiques ou des cycles de production sensibles.
Les autorités publiques ne sont pas en reste. Plusieurs États européens recourent aux métadonnées pour des fins de surveillance judiciaire et de sécurité nationale. Or, la frontière entre usage légitime et exploitation abusive demeure fragile. C’est particulièrement visible avec les pixels de suivi intégrés dans les e-mails marketing. À ce sujet, l’ EDPB et la CNIL ont récemment rappelé qu’ils sont soumis à consentement explicite.
En additionnant ces vecteurs — publicité, espionnage, surveillance étatique — les métadonnées deviennent un levier central. Elles permettent en effet d’anticiper comportements, d’identifier des cibles et d’orienter des décisions. Leur exploitation abusive fragilise la vie privée et ouvre la porte à des dérives systémiques.
⮞ Résumé
Les métadonnées e-mail permettent de tracer des graphes sociaux, d’alimenter le profilage commercial et d’outiller la surveillance. Un usage légitime existe (sécurité, enquête judiciaire), mais l’exploitation abusive expose individus et organisations à un risque stratégique majeur.
Cadre légal UE — RGPD, ePrivacy et vie privée des e-mails
La confidentialité des métadonnées e-mail est encadrée par un arsenal juridique européen complexe. Le RGPD impose aux acteurs de limiter la collecte aux seules données nécessaires. Pourtant, les métadonnées de communication sont souvent conservées bien au-delà du principe de minimisation.
Le règlement ePrivacy, via son article 5(3), renforce l’exigence de consentement préalable pour tout dispositif de suivi, y compris les pixels invisibles insérés dans les e-mails marketing. En 2025, la CNIL a rappelé que ces traceurs électroniques constituent une donnée personnelle et doivent être soumis à un choix explicite de l’utilisateur.
En parallèle, certaines autorités nationales affinent leur doctrine. En juin 2025, le Garante italien a sanctionné une entreprise pour conservation excessive des métadonnées d’e-mails professionnels. Il a fixé une limite stricte : 21 jours maximum sans accord syndical ou autorisation de l’inspection du travail. Cette décision s’appuie sur l’article 4 du Statut des travailleurs et l’article 114 du Code italien de la vie privée.
À l’échelle européenne, le Comité européen de la protection des données (EDPB) a publié en 2025 ses lignes directrices 01/2025 sur la pseudonymisation. Elles précisent que les métadonnées doivent être cloisonnées dès la collecte, et que leur traitement à des fins de cybersécurité ou de conformité doit faire l’objet d’une analyse d’impact.
Le débat reste vif : faut-il autoriser la conservation massive des métadonnées pour la cybersécurité et la justice, ou renforcer le principe de proportionnalité pour éviter les dérives de surveillance généralisée ?
⮞ Résumé
Le RGPD et l’ePrivacy encadrent strictement l’usage des métadonnées e-mail. Consentement explicite, minimisation et cloisonnement sont des principes cardinaux. Mais leur mise en œuvre varie selon les États. Entre sécurité, droit du travail et vie privée, l’Europe cherche un équilibre encore fragile — et les métadonnées sont au cœur de cette tension.
Usage judiciaire des métadonnées — preuve, traçabilité et responsabilité
Les métadonnées e-mail et de messagerie sont devenues des éléments probatoires dans les enquêtes pénales. Leur croisement avec d’autres sources (logs réseau, DNS, cloud, géolocalisation) permet de reconstituer des chaînes d’action, d’authentifier des échanges, et d’établir des responsabilités techniques.
En juin 2025, la Cour de cassation a confirmé que les courriels professionnels, y compris leurs métadonnées (horodatage, destinataires, serveurs), sont des données personnelles au sens du RGPD. Cette reconnaissance ouvre la voie à leur exploitation comme preuve dans les litiges prud’homaux, mais aussi dans les enquêtes pénales.
Dans les affaires de cybercriminalité, les enquêteurs exploitent :
- Les horodatages SMTP pour établir une chronologie d’envoi
- Les adresses IP pour géolocaliser ou corréler des connexions
- Les identifiants de canal (Telegram, Signal, Matrix) pour relier des pseudonymes à des actions
- Les logs DNS et cloud pour confirmer l’usage d’un service à un instant donné
Dans l’affaire Telegram (2024–2025), les autorités françaises ont démontré l’usage criminel de la plateforme via l’analyse croisée de métadonnées réseau, de logs d’interconnexion et de signalements externes. Ce n’est pas le contenu des messages qui a été exploité, mais leur structure technique et leur fréquence d’usage.
⮞ Synthèse
Les métadonnées sont des preuves numériques à part entière. Leur traçabilité, leur horodatage et leur capacité à relier des identités techniques à des faits concrets en font un levier judiciaire puissant.
L’approche souveraine — encapsulation, cloisonnement, neutralisation — devient une stratégie défensive autant que préventive.
Défenses classiques — protocoles de messagerie et limites
Face aux risques pesant sur la confidentialité des métadonnées e-mail, plusieurs mécanismes techniques sont couramment déployés. Les standards SPF, DKIM et DMARC renforcent l’authentification des expéditeurs et réduisent les usurpations d’adresse. MTA-STS et TLS-RPT visent quant à eux à garantir la livraison sécurisée en forçant l’usage du chiffrement TLS entre serveurs de messagerie.
Ces dispositifs améliorent l’intégrité et l’authenticité du flux, mais ils laissent intacts les en-têtes de transport et les adresses IP. En clair, ils ne protègent pas les métadonnées elles-mêmes.
Les solutions de chiffrement de contenu, telles que PGP ou S/MIME, ajoutent une couche précieuse pour la confidentialité des messages. Toutefois, elles ne masquent que le corps du texte et les pièces jointes. Les champs sensibles comme Subject, To, From et les Received headers restent accessibles à tout fournisseur ou relais SMTP.
Enfin, certains utilisateurs se tournent vers des outils réseau comme le VPN ou Tor. Ces solutions peuvent anonymiser l’adresse IP côté client, mais elles ne neutralisent pas la conservation des en-têtes par les serveurs de messagerie. La défense reste donc partielle.
⮞ Résumé
SPF, DKIM, DMARC, MTA-STS et TLS-RPT sécurisent la messagerie, mais pas les métadonnées. PGP et S/MIME chiffrent le contenu, non les en-têtes. VPN et Tor masquent l’IP utilisateur, sans empêcher la collecte des traces par les serveurs.
Contre-mesures souveraines — DataShielder™ et protection des échanges
Pourquoi dépasser les limites des solutions classiques ?
Les solutions traditionnelles (VPN, PGP, SPF/DKIM/DMARC) protègent partiellement la confidentialité des métadonnées e-mail. Pour aller plus loin, Freemindtronic déploie des contre-mesures souveraines avec DataShielder™, une architecture matérielle conçue pour cloisonner les usages et réduire la surface d’exposition.
Conformité réglementaire et usage critique
En octobre 2024, DataShielder HSM NFC, classé produit à double usage civil et militaire selon le règlement (UE) 2021/821, a obtenu l’autorisation d’importation délivrée par l’ANSSI. Puis, en février 2025, sa réexportation vers les États membres de l’Union européenne a été validée, confirmant son usage en environnement critique.
Encapsulation segmentée et double chiffrement
En parallèle, un mode d’encapsulation segmentée avancée a été introduit dans DataShielder HSM PGP. Il permet de dissocier les métadonnées MIME (pièces jointes, structure, types MIME) en blocs chiffrés indépendants.
L’objet (Subject) reste volontairement visible pour préserver la recherche et l’ergonomie des messageries — un compromis stratégique assumé par l’inventeur.
Ensuite, les données encapsulées sont injectées dans les canaux de communication (SMTP, E2EE, cloud), qui les rechiffrent automatiquement. Ce double chiffrement anticipé complexifie toute tentative de corrélation abusive.
>Cette architecture est dédiée aux usages de contre-espionnage, où la segmentation des identités et la neutralisation des traces techniques sont des impératifs opérationnels.
Stockage souverain et cloisonnement hors ligne
DataShielder HSM NFC assure le stockage hors ligne des clés et identités numériques. Son isolement physique empêche toute fuite vers le cloud ou le disque dur, garantissant une maîtrise locale et segmentée.
De son côté, DataShielder HSM PGP desktop encapsule le message avant envoi en AES-256 CBC PGP avec des clés segmentées. Ce verrouillage souverain précède le chiffrement natif de la messagerie (PGP, S/MIME, E2EE), assurant une protection en deux couches.
Ce qui reste visible — et pourquoi
Seules les métadonnées de transport (adresses IP, serveurs traversés, horodatages) restent visibles, car elles sont indispensables au routage SMTP. Leur présence est un invariant technique, mais leur valeur est fortement réduite par l’opacité du contenu.
✓ Synthèse des contre-mesures souveraines
– Cloisonnement hors ligne des clés avec DataShielder HSM NFC
– Encapsulation offline → chiffrement AES-256 CBC PGP avec clés segmentées
– Double chiffrement : encapsulation souveraine + chiffrement standard messagerie
– Neutralisation des métadonnées de contenu (pièces jointes, structure MIME)
– Objet visible par choix stratégique pour garantir la recherche
– Réduction des traces locales et segmentation des identités
Distribution exclusive en France
Le distributeur officiel exclusif de DataShielder™ HSM NFC en France est AMG PRO. Spécialisé dans les équipements tactiques et les solutions de cybersécurité à double usage, AMG PRO assure la distribution auprès des administrations, des forces de l’ordre et des entreprises privées sensibles.
Cette exclusivité garantit une traçabilité souveraine, une conformité réglementaire et un accompagnement dédié pour les déploiements en environnement critique.
Les produits DataShielder™ sont également soutenus par Bleu Jour, partenaire technologique d’AMG PRO, reconnu pour ses solutions informatiques industrielles et ses engagements en matière de fabrication française.
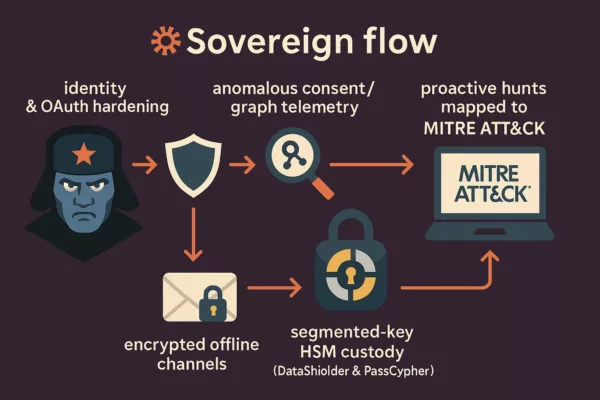
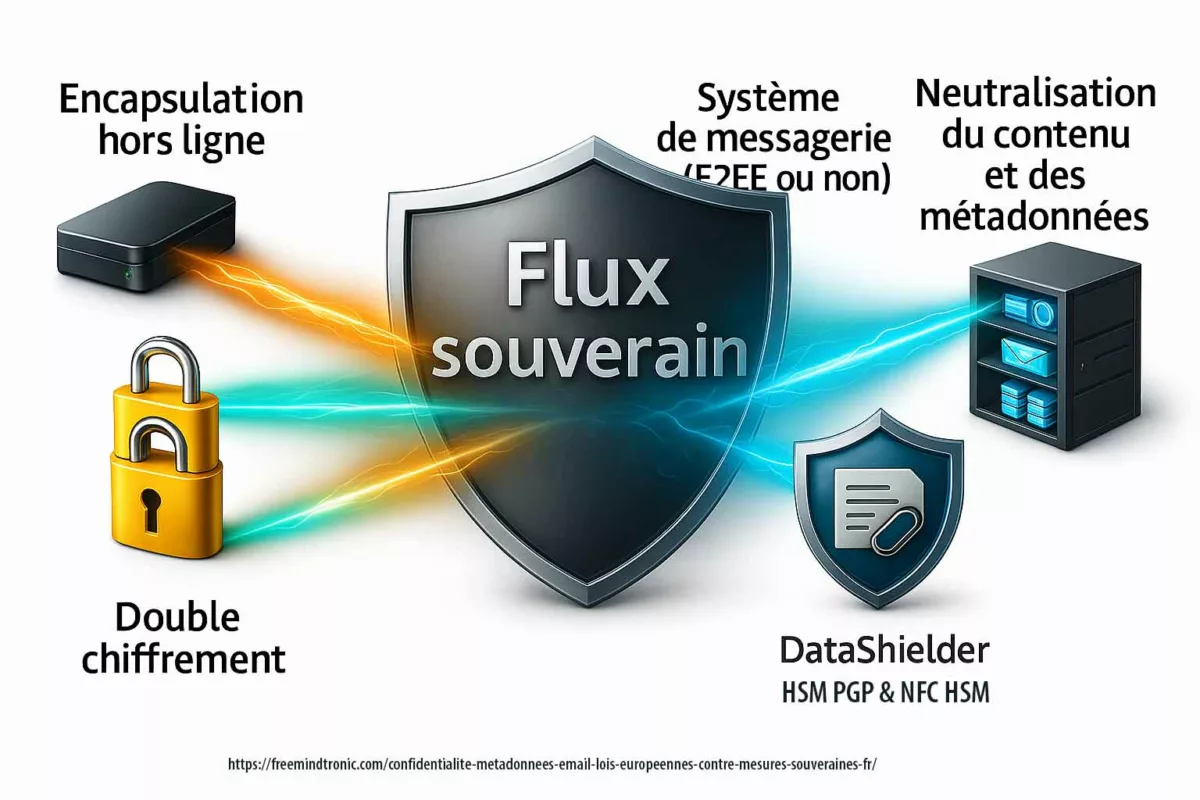
Flux souverain — encapsulation offline et double chiffrement
Le flux souverain mis en œuvre par DataShielder™ repose sur un enchaînement précis, conçu pour neutraliser les métadonnées de contenu et compartimenter les usages. L’objectif est de réduire au strict minimum ce qui demeure exploitable par des tiers.
- Encapsulation offline — Le message et ses fichiers attachés sont d’abord chiffrés hors ligne en AES-256 CBC PGP avec des clés segmentées stockées dans DataShielder HSM NFC ou DataShielder HSM PGP desktop. Le contenu (texte, pièces jointes, structure MIME) devient totalement opaque.
- Double chiffrement — Une fois encapsulé, le message est remis à la messagerie, qui applique son propre protocole de chiffrement (PGP, S/MIME ou E2EE selon le service). Résultat : un verrouillage en deux couches.
- Neutralisation des métadonnées de contenu — Objet, pièces jointes et structure MIME sont encapsulés dans la charge utile chiffrée, empêchant toute analyse par les fournisseurs.
- Persistance des métadonnées de transport — Les seules informations visibles restent les adresses IP, les serveurs traversés et les horodatages. Elles sont indispensables au routage SMTP et ne peuvent être supprimées.
Cette architecture introduit une complexité analytique qui dépasse les capacités classiques de corrélation automatisée. Elle crée un bruit cryptographique rendant tout profilage ou interception beaucoup plus coûteux et incertain.
⮞ Résumé
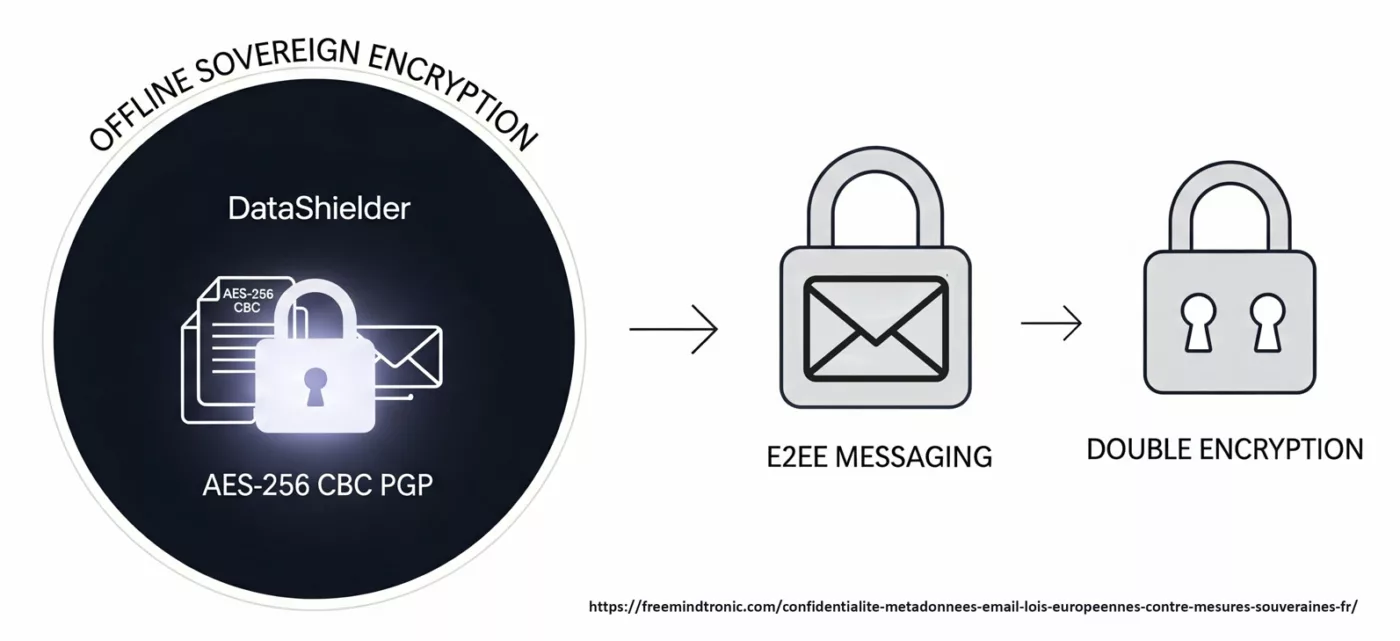
Le flux souverain DataShielder combine encapsulation offline (AES-256 CBC PGP + clés segmentées, couvrant messages et pièces jointes) et chiffrement de messagerie (PGP, S/MIME ou E2EE). Résultat : double chiffrement, neutralisation des métadonnées de contenu et réduction de la corrélation. Seules les métadonnées de transport restent visibles pour le routage.
Messageries chiffrées de bout en bout (E2EE) et métadonnées résiduelles
Les services de messagerie chiffrée de bout en bout comme ProtonMail, Tutanota, Signal, Matrix, Olvid ou encore WhatsApp garantissent qu’aucun tiers ne peut lire le contenu des communications. Seuls l’expéditeur et le destinataire détiennent les clés nécessaires pour déchiffrer le message.
Toutefois, même avec l’E2EE, certaines informations restent visibles. Les métadonnées de transport (IP d’origine, relais SMTP, horodatages) ne peuvent être masquées. De plus, certaines métadonnées de contenu comme l’objet (Subject), la taille ou le type des pièces jointes (MIME) peuvent encore être accessibles aux fournisseurs de service.
En 2025, plusieurs évolutions confirment cette limite :
- WhatsApp applique désormais le protocole Signal sur toutes ses plateformes, y compris WhatsApp Web et les fichiers partagés. Le contenu est chiffré, mais les métadonnées (fréquence, destinataires, IP) restent exploitables.
- ProtonMail bloque désormais par défaut les pixels espions et URLs de suivi, et propose un outil d’importation sécurisé pour migrer depuis les webmails classiques sans exposer les métadonnées historiques.
- Olvid, certifiée deux fois CSPN par l’ANSSI, fonctionne sans numéro ni adresse e-mail. Son architecture peer-to-peer sans serveur central garantit l’absence de collecte de métadonnées critiques. Elle est utilisée par des journalistes, des ONG, et des institutions sensibles.
C’est pourquoi l’approche souveraine de DataShielder™ complète ces messageries. En encapsulant message et fichiers en AES-256 CBC PGP hors ligne, via des clés segmentées, avant leur envoi, le contenu devient opaque pour les serveurs. Le service E2EE ajoute ensuite sa propre couche de chiffrement, aboutissant à un double chiffrement : offline souverain + chiffrement natif de la messagerie.
⮞ Résumé
Les messageries E2EE protègent le contenu, mais pas toutes les métadonnées. Avec DataShielder, messages et pièces jointes sont encapsulés offline, puis chiffrés à nouveau par l’E2EE. Résultat : un double verrouillage qui réduit la surface exploitable.
>Les évolutions 2025 confirment que même les messageries réputées sécurisées doivent être complétées par une encapsulation souveraine pour neutraliser les métadonnées résiduelles.
Au-delà de l’e-mail — métadonnées de toutes les communications
La problématique de la confidentialité des métadonnées ne se limite pas aux e-mails. Chaque service de communication numérique génère ses propres traces, souvent invisibles pour l’utilisateur mais hautement exploitables par les fournisseurs, plateformes et autorités.
- Messageries instantanées — Slack, Teams, Messenger ou Telegram enregistrent les horaires de connexion, les groupes rejoints et les adresses IP associées.
- VoIP et visioconférences — Zoom, Skype ou Jitsi exposent des données sur la durée des appels, les participants et les serveurs relais.
- Téléphonie mobile et SMS — Les opérateurs conservent les métadonnées d’appel (numéros appelant/appelé, cell-ID, durée, localisation approximative).
- Navigation web — Même sous HTTPS, l’adresse IP, les résolutions DNS et l’SNI TLS révèlent les sites visités.
- Réseaux sociaux et cloud — Les plateformes comme Facebook, Google Drive ou Dropbox exploitent les journaux d’accès, les appareils utilisés et les partages de fichiers.
- VPN et Tor — Ces solutions masquent l’adresse IP d’origine, mais ne suppriment pas les journaux conservés par certains nœuds ou opérateurs.
Pris séparément, ces éléments paraissent anodins. Agrégés, ils dessinent un profil comportemental complet capable de révéler des habitudes de travail, des relations sociales, voire des opinions politiques ou syndicales.
⮞ Résumé
Les métadonnées dépassent le cadre des e-mails : messageries instantanées, VoIP, SMS, web, réseaux sociaux et cloud en produisent continuellement. Isolées, elles semblent anodines ; agrégées, elles deviennent un outil de surveillance globale.
Autres infrastructures — IoT, cloud, blockchain et traces techniques
La confidentialité des métadonnées concerne aussi les infrastructures numériques et industrielles. Chaque interaction technique laisse une trace exploitable, souvent plus persistante que les communications humaines.
- Objets connectés (IoT) — Assistants vocaux (Alexa, Google Home), montres médicales ou capteurs domotiques émettent en continu des journaux d’activité, incluant heures d’utilisation et identifiants uniques.
- Stockage cloud et collaboration — Services comme Google Drive, OneDrive ou Dropbox conservent les horodatages d’accès, les appareils utilisés et les historiques de partage, même si les fichiers sont chiffrés.
- DNS et métadonnées réseau — Chaque résolution DNS, chaque SNI TLS et chaque log de firewall expose la destination et la fréquence des connexions, indépendamment du contenu échangé.
- Blockchain et crypto — Les transactions sont immuables et publiques ; les adresses utilisées constituent des métadonnées permanentes, traçables à grande échelle via l’analyse de graphe.
Ces infrastructures démontrent que les métadonnées sont devenues un invariant structurel du numérique. Elles ne peuvent être supprimées, mais doivent être neutralisées ou cloisonnées pour limiter leur exploitation abusive.
⮞ Résumé
IoT, cloud, DNS et blockchain produisent des métadonnées persistantes. Elles structurent l’infrastructure numérique mais exposent aussi des traces exploitables en continu, même en l’absence de contenu lisible.
Cybersécurité et espionnage — usages légitimes vs abusifs
Les métadonnées ont une valeur ambivalente. D’un côté, elles sont un outil essentiel pour la cybersécurité et la justice. Les journaux de connexion, les adresses IP et les horodatages permettent aux équipes SOC et aux enquêteurs de détecter des anomalies, d’identifier des attaques et d’établir des preuves judiciaires.
De l’autre, ces mêmes données deviennent un instrument d’espionnage lorsqu’elles sont exploitées sans cadre légal. Des acteurs étatiques ou industriels peuvent cartographier des réseaux de relations, anticiper des décisions stratégiques ou suivre en temps réel des organisations sensibles. Les campagnes publicitaires intrusives reposent également sur ces mécanismes de corrélation clandestine.
C’est précisément pour limiter ces usages abusifs que DataShielder™ apporte une réponse souveraine. L’encapsulation offline, le double chiffrement et la segmentation des identités réduisent les traces locales et complexifient la corrélation. Ainsi, les usages légitimes (cybersécurité, enquêtes judiciaires) demeurent possibles via les métadonnées de transport, mais l’exploitation abusive des métadonnées de contenu est neutralisée.
⮞ Résumé
Les métadonnées sont un outil à double usage : légitime pour la cybersécurité et la justice, mais aussi illégitime pour l’espionnage et le profilage abusif. La souveraineté consiste à encadrer les premiers et à neutraliser les seconds.
Cas d’usage réels — ONG, journalistes, PME
La problématique des métadonnées n’est pas théorique : elle se traduit en risques concrets pour les organisations et individus. Voici trois scénarios illustratifs où la souveraineté apportée par DataShielder™ change la donne.
Journalistes — Les métadonnées suffisent à révéler les contacts confidentiels d’une rédaction. Grâce à DataShielder HSM PGP, les messages et pièces jointes sont encapsulés offline, puis chiffrés à nouveau par la messagerie E2EE (ProtonMail, Signal). Les sources sont protégées contre les corrélations abusives.
ONG — Les réseaux de partenaires, bailleurs de fonds et relais locaux sont exposés via les horodatages et adresses IP. En combinant DataShielder HSM NFC pour la segmentation des identités et une messagerie chiffrée, les ONG cloisonnent leurs échanges et limitent les risques d’espionnage ou de surveillance intrusive.
PME — Les cycles de décision, flux d’affaires et horaires d’activité peuvent être déduits des simples en-têtes SMTP. Avec un déploiement DMARC + MTA-STS complété par DataShielder HSM, les entreprises réduisent les attaques par usurpation et renforcent la confidentialité de leurs communications internes.
⮞ Résumé
Journalistes, ONG et PME sont exposés différemment mais tous vulnérables aux métadonnées. Avec DataShielder, ils bénéficient d’une encapsulation offline, d’une segmentation des identités et d’une réduction des corrélations abusives.
Guide pratique — réduire l’exposition des métadonnées e-mail
Protéger la confidentialité des métadonnées e-mail nécessite d’allier standards techniques et mesures souveraines. Voici une check-list opérationnelle adaptée aux entreprises, ONG et administrations.
- Authentification des domaines — Activer
SPF,DKIMetDMARC(mode reject) pour limiter les usurpations et renforcer la confiance des échanges. - Transport sécurisé — Déployer
MTA-STSetTLS-RPTpour imposer l’usage du chiffrement TLS entre serveurs de messagerie. - Neutralisation des traceurs — Bloquer le chargement automatique des images distantes et utiliser des filtres anti-pixels pour empêcher la collecte clandestine.
- Minimisation de la rétention — Limiter la durée de conservation des journaux de messagerie. L’Italie impose par exemple quelques jours pour les e-mails salariés.
- Encapsulation souveraine — Utiliser DataShielder HSM NFC ou HSM PGP desktop pour chiffrer offline messages et pièces jointes en AES-256 CBC PGP avec clés segmentées, avant tout envoi.
Ainsi, cette combinaison permet de réduire la surface d’exposition, de renforcer la souveraineté numérique et de compliquer toute tentative d’exploitation abusive des métadonnées.
⮞ Résumé
SPF, DKIM, DMARC, MTA-STS et TLS-RPT sécurisent le transport et l’authentification. Anti-pixels et rétention minimale limitent la collecte. DataShielder apporte la couche souveraine : encapsulation offline et neutralisation des métadonnées de contenu.
Signaux faibles 2025→2027 — tendances émergentes
Les prochaines années verront s’intensifier les débats autour de la confidentialité des métadonnées e-mail et des communications numériques. Plusieurs signaux faibles se dessinent déjà, annonçant des évolutions structurelles.
- Encadrement renforcé du tracking — De nouvelles recommandations européennes devraient limiter l’usage des pixels invisibles et autres traceurs, avec des sanctions accrues pour non-conformité.
- Généralisation de DMARC et MTA-STS — L’adoption de ces standards pourrait devenir quasi obligatoire, imposée par les grands opérateurs et les régulateurs nationaux.
- Rétention ciblée et proportionnée — Plusieurs autorités envisagent d’encadrer plus strictement la durée de conservation des métadonnées, afin d’éviter la surveillance massive et permanente.
- IA de corrélation massive — L’émergence d’outils d’intelligence artificielle capables de croiser logs, DNS, IP et données publiques rendra la corrélation de métadonnées plus rapide et intrusive.
- Hybridation souveraine + cloud — Le modèle mixte associant encapsulation offline (DataShielder) et services cloud E2EE pourrait s’imposer comme standard pour les organisations sensibles.
- Corrélation post-quantique — Premiers tests de corrélation SMTP par IA quantique simulée. La neutralisation des métadonnées devient une exigence stratégique.
- Pseudonymisation dynamique — L’EDPB envisage d’imposer des journaux SMTP pseudonymisés dans les infrastructures publiques.
De faits, ces tendances confirment que la maîtrise des métadonnées deviendra un enjeu stratégique central entre 2025 et 2027, tant pour la souveraineté numérique que pour la cybersécurité européenne.
⮞ Résumé
D’ici 2027 : encadrement accru du tracking, généralisation des standards DMARC/MTA-STS, rétention plus stricte, montée en puissance de l’IA et hybridation souveraine + cloud. Les métadonnées deviennent un champ de bataille stratégique.
FAQ — questions fréquentes sur les métadonnées e-mail
Non, pas complètement. PGP chiffre le contenu (texte + pièces jointes). Cependant, il laisse visibles les métadonnées de transport, comme les en-têtes SMTP (From, To, Date), les en-têtes Received, les adresses IP et les horodatages. Par conséquent, pour réduire l’exposition du contenu (objet, structure MIME), il est nécessaire de l’encapsuler en amont avec DataShielder HSM.
En 2025, plusieurs événements ont renforcé le cadre légal : la CNIL</strong a sanctionné Shein pour usage abusif de traceurs ; la Cour de cassation</strong a reconnu les métadonnées comme données personnelles ; et le Garante italien a limité leur rétention à 24h sans justification. Ces évolutions confirment que la confidentialité des métadonnées est désormais un enjeu juridique central.
Non, il n’anonymise pas les échanges. MTA-STS force le protocole TLS entre serveurs pour sécuriser le transport et limiter les attaques de type downgrade. Cependant, il n’anonymise ni les adresses IP ni les en-têtes. Les métadonnées nécessaires au routage SMTP restent donc observables.
Non, elle ne supprime pas toutes les métadonnées. DataShielder neutralise les métadonnées de contenu (objet, pièces jointes, structure MIME) via une encapsulation offline en AES-256 CBC PGP (clés segmentées). Ensuite, elle laisse la messagerie appliquer son chiffrement (PGP, S/MIME ou E2EE). En conséquence, les métadonnées de transport (IP, relais, horodatages) demeurent pour assurer le routage.
Oui, elles sont utiles à la cybersécurité. Elles servent notamment à la détection d’anomalies (SOC/SIEM) et aux enquêtes judiciaires. Toutefois, leur usage doit rester proportionné et conforme au cadre légal (RGPD/ePrivacy). L’approche souveraine consiste donc à neutraliser les métadonnées de contenu tout en conservant le minimum requis pour la sécurité et la conformité.
Selon le RGPD, les métadonnées (adresses IP, horodatages, etc.) sont considérées comme des données à caractère personnel. Par conséquent, leur collecte, leur stockage et leur traitement doivent être justifiés par une base légale valide. C’est pour cette raison que la CNIL et l’EDPB (Comité européen de la protection des données) exigent un consentement explicite pour leur usage.
En fait, DataShielder™ ne les supprime pas, car elles sont indispensables au routage des e-mails. En revanche, le système les rend moins utiles au profilage en les isolant du contenu. En effet, en encapsulant le message en amont, il s’assure que seules les informations de transport minimales restent visibles aux intermédiaires, ce qui complique l’agrégation de données.
Non. Si ces services sécurisent le contenu de manière très efficace, les métadonnées de transport (adresses IP, horodatage) restent visibles pour eux. Pour cette raison, ces fournisseurs peuvent être contraints par la loi de conserver ces traces. De plus, les courriels envoyés à des destinataires sur d’autres plateformes (Gmail, Outlook) révéleront toujours des métadonnées lisibles pour le fournisseur tiers.
C’est une notion clé. Bien que le contenu du message puisse être chiffré, les métadonnées révèlent une cartographie sociale et technique précise. Elles permettent d’établir qui parle à qui, quand, à quelle fréquence et d’où (géolocalisation par IP). Ces informations suffisent à reconstituer un graphe de connexions. Elles sont donc plus puissantes pour le profilage et la surveillance que le contenu lui-même.
C’est une distinction fondamentale. Le chiffrement en transit (par exemple, via TLS/SSL) protège le message pendant son voyage entre les serveurs, mais il ne le protège pas une fois qu’il est stocké. Le chiffrement au repos protège le message lorsqu’il est stocké sur un serveur ou un disque dur. Par conséquent, pour une sécurité complète, il faut les deux, car les messages peuvent être interceptés à l’arrivée (au repos) s’ils ne sont pas chiffrés.
Oui, mais c’est complexe. Les services de messagerie Web comme Gmail affichent l’adresse IP de l’expéditeur (celle du serveur Gmail). Cependant, des services comme ProtonMail suppriment l’adresse IP de l’expéditeur de l’en-tête du message. Il est également possible d’utiliser un VPN ou un service de relais comme Tor pour masquer votre adresse IP réelle.
⮞ Résumé
PGP et MTA-STS protègent respectivement le contenu et le transport, sans masquer les métadonnées de routage. Par conséquent, DataShielder HSM ajoute une encapsulation offline qui réduit l’exposition des métadonnées de contenu pour une meilleure confidentialité des métadonnées e-mail.
Perspectives stratégiques — souveraineté numérique et communications
La maîtrise des métadonnées e-mail et des traces associées dépasse la simple cybersécurité technique. En réalité, elle ouvre la voie à une doctrine souveraine qui articule la protection de la vie privée, la conformité réglementaire et la résilience face aux menaces hybrides.
Dans les années à venir, la convergence entre chiffrement de bout en bout, encapsulation hors ligne et infrastructures décentralisées redéfinira l’équilibre entre sécurité et efficacité. Par conséquent, une perspective clé sera la mise en place de standards européens contraignants sur la conservation des métadonnées. Ces standards devront intégrer à la fois les besoins judiciaires et les impératifs de protection individuelle. De plus, l’essor de l’IA de corrélation massive accentuera le besoin d’outils matériels souverains. Ainsi, des solutions comme DataShielder™ seront nécessaires pour rétablir une symétrie stratégique entre les citoyens, les entreprises et les institutions.
À plus long terme, il s’agira d’orchestrer une résilience hybride. Cette dernière combine des solutions locales (HSM hors ligne, cloisonnement segmenté) et des services cloud chiffrés. L’objectif est d’assurer la continuité opérationnelle même dans des scénarios de rupture géopolitique ou technologique.
Cette chronique s’est concentrée sur les métadonnées e-mail et leurs contre-mesures souveraines.
>Restent à approfondir : l’impact des réseaux quantiques émergents, les standards de pseudonymisation dynamique et les mécanismes de souveraineté algorithmique appliqués à la corrélation massive.
Ces thèmes feront l’objet de développements ultérieurs.