Les failles de sécurité Ledger sont au cœur des préoccupations des investisseurs depuis 2017. Cette chronique analyse l’évolution des menaces, du vol de cryptomonnaies par manipulation de firmware à la fuite de données Global-e (2026). Au-delà du phishing Ledger massif, nous explorons les vulnérabilités de la chaîne d’approvisionnement et les risques de doxxing sur le Dark Web. Face à l’obsolescence de la confiance aveugle, la sécurité hardware doit évoluer vers des modèles décentralisés : des architectures qui sécurisent la création, la détention et le transfert des secrets critiques (seed phrases, clés privées, identifiants) — sans dépendance à un tiers et sans fonction de signature transactionnelle exposée.
Synthèse — Failles de Sécurité Ledger
⮞ Note de lecture
Cette synthèse se lit en ≈ 3 à 4 minutes. Elle offre une vision immédiate de la problématique centrale sans nécessiter la lecture de l’analyse technique et historique complète.
⚠️ Note sur la résilience de la Supply Chain
La fuite Global-e de 2026 met en lumière ce que la CISA (Cybersecurity & Infrastructure Security Agency) définit comme des risques critiques de la chaîne d’approvisionnement. Selon leurs directives officielles, la sécurité matérielle n’est aussi forte que son maillon tiers le plus faible.
⚡ Constats Clés
Depuis 2017, Ledger a fait face à plusieurs incidents majeurs : attaques sur la phrase de récupération et le firmware, modification de PCB, fuite de base de données en 2020, compromission du Connect Kit en 2023 et fuite de données Global-e en 2026. Ces incidents démontrent que les menaces ne proviennent pas seulement de failles internes, mais aussi des dépendances externes et des vecteurs de phishing.
✦ Impacts Immédiats
- Exposition massive de données clients (292k en 2020, Global-e en 2026).
- Phishing ciblé et harcèlement utilisant des informations personnelles.
- Manipulation de transactions et vol de clés privées (attaques de 2018).
- Fragilité des chaînes d’approvisionnement logicielles et des partenaires tiers.
⚠ Message Stratégique
Le véritable basculement n’est pas seulement technique, mais réside dans la répétition des failles et leur exploitation systémique. La menace devient structurelle : phishing automatisé, doxxing, érosion de la confiance et dépendance accrue envers des tiers. Le risque n’est plus occasionnel, mais persistant.
Le passage de la Confiance à la Preuve
La répétition des failles de sécurité Ledger prouve que la confiance en une marque ne suffit pas. La souveraineté exige des preuves. En implémentant l’Authentification par Clé Segmentée (WO2018154258), Freemindtronic déplace la sécurité du “serveur de mise à jour de la marque” directement dans la main de l’utilisateur. Cela élimine la dépendance envers des partenaires tiers comme Global-e pour la sécurité fondamentale de vos actifs.
⎔ Contre-mesure Souveraine
Il n’existe pas de solution miracle contre les failles de sécurité. La souveraineté signifie réduire les surfaces exploitables : minimiser les données exposées, utiliser des cold wallets indépendants (NFC HSM), séparer strictement l’identité de l’usage, et maintenir une vigilance constante face aux communications frauduleuses.
Paramètres de lecture
Synthèse exécutive : ≈ 3–4 min
Résumé avancé : ≈ 5–6 min
Chronique complète : ≈ 30–40 min
Première publication : 16 décembre 2023
Dernière mise à jour : 7 janvier 2026
Niveau de complexité : Élevé — sécurité, crypto, supply-chain
Densité technique : ≈ 70 %
Langues disponibles : EN · FR
Cœur de sujet : Failles Ledger, wallets crypto, phishing, souveraineté numérique
Type éditorial : Chronique — Freemindtronic Digital Security
Niveau de risque : 9.2 / 10 — menaces financières, civiles et hybrides
Les chroniques affichées ci-dessus ↑ appartiennent à la section Sécurité Numérique. Elles prolongent l’analyse des architectures souveraines, des marchés noirs de données et des outils de surveillance. Cette sélection complète la présente chronique dédiée aux Failles de Sécurité Ledger (2017–2026) et aux risques systémiques liés aux vulnérabilités matérielles, aux compromissions de la supply-chain et aux prestataires tiers.
- 🔝 Retour en haut
- Synthèse — Failles de sécurité Ledger
- Résumé avancé
- Chronique — Failles de sécurité Ledger (2017–2026)
- 2018 — Récupération de Seed Phrase
- 2018 — Remplacement de firmware
- 2018 — Modification PCB
- 2019 — Vulnérabilité Monero (XMR)
- Risque permanent — Blind Signing
- 2020 — Fuite de données Ledger
- 2023 — Supply-chain : Connect Kit
- 2026 — Fuite de données Global-e
- ↳ Réactions en France : colère & actions
- ↳ Menaces hybrides : phishing → home-jacking
- ↳ SeedNFC : QR chiffré (partage air-gap)
- ↳ Meilleures pratiques
- Comparaison : autres portefeuilles crypto
- Projections techno / régulation / société
- Alternatives souveraines — NFC HSM
- Strategic Outlook
Résumé avancé
Une succession de failles qui révèle un problème de modèle
Depuis 2017, Ledger a été confronté à une série d’incidents majeurs : attaques par récupération de seed phrase, remplacement de firmware, modifications matérielles, vulnérabilités applicatives (Monero), fuite massive de données clients en 2020, compromission de la supply-chain logicielle en 2023, puis fuite de données liée à Global-e en 2026. Pris isolément, chacun de ces événements peut être qualifié d’« incident ». Pris ensemble, ils dessinent un problème de modèle de sécurité.
Le point commun n’est pas la cryptographie de bas niveau, mais la nécessité récurrente pour les secrets critiques (seed phrases, clés privées, métadonnées d’identité) de transiter, à un moment donné, par un environnement non souverain : firmware propriétaire, ordinateur hôte, application connectée, serveur de mise à jour ou partenaire e-commerce.
De la sécurité du composant à la vulnérabilité de l’écosystème
Ledger a historiquement misé sur la robustesse du composant matériel. Or, à partir de 2020, la surface d’attaque s’est déplacée vers l’écosystème périphérique : bases de données clients, services logistiques, dépendances logicielles, interfaces utilisateur, notifications et canaux de support.
La fuite Global-e de 2026 marque un tournant. Même sans compromission directe des clés privées, l’exposition des données de livraison transforme les utilisateurs en cibles persistantes : phishing ultra-ciblé, ingénierie sociale « livreur », doxxing et, dans les cas extrêmes, menaces physiques. La sécurité n’est alors plus seulement numérique ; elle devient civile et personnelle.
Pourquoi le phishing et les attaques hybrides deviennent inévitables
À partir du moment où l’identité réelle d’un utilisateur est corrélée à la possession d’actifs numériques, le phishing cesse d’être opportuniste. Il devient industriel et personnalisé.
Les attaques BITB, les fausses mises à jour, les faux incidents de livraison ou de conformité exploitent moins des failles techniques que le facteur humain, rendu vulnérable par l’exposition des métadonnées.
Dans ce contexte, renforcer un firmware ou ajouter une alerte logicielle ne suffit plus. Le problème n’est pas la signature cryptographique, mais le fait que le secret ou son détenteur soient identifiables, traçables ou sollicitables à distance.
Changement de paradigme : de la confiance à la preuve matérielle
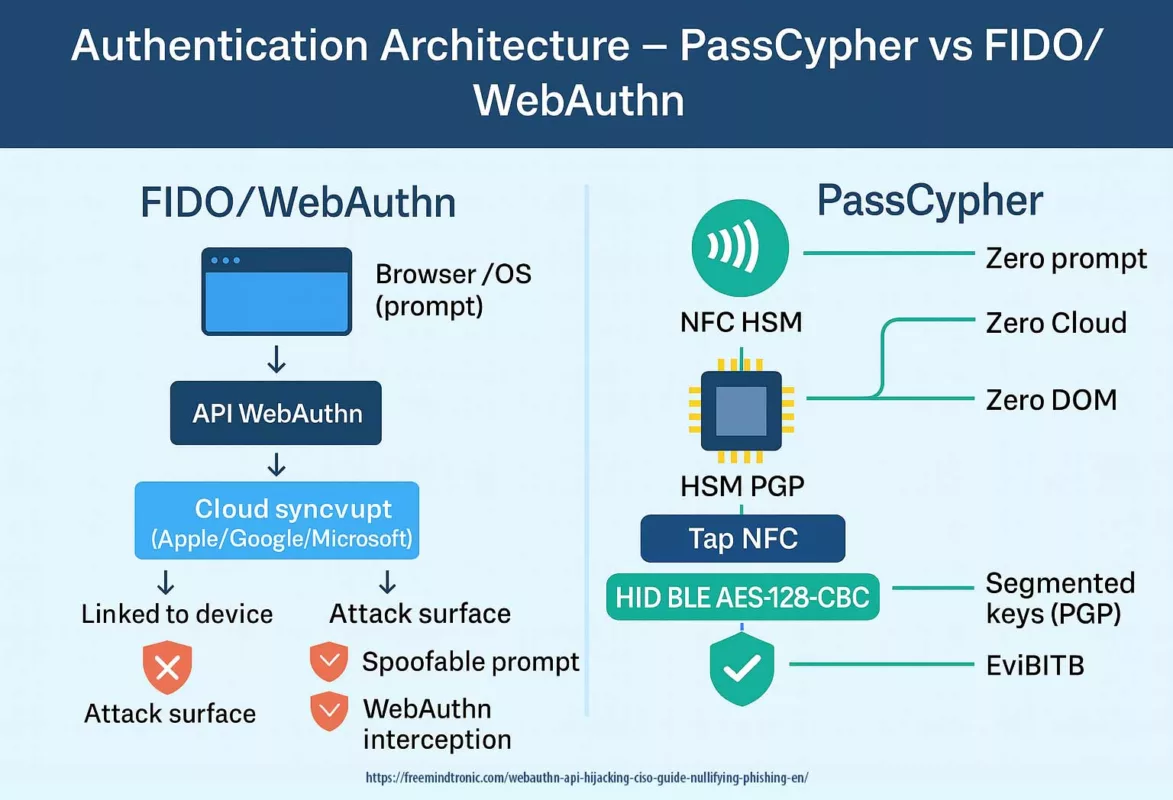
Face à ces limites structurelles, certaines approches ne cherchent plus à renforcer la signature transactionnelle, mais à retirer les secrets critiques de tout écosystème connecté. Les alternatives souveraines proposées par Freemindtronic reposent sur une logique inverse. Plutôt que de chercher à sécuriser un écosystème connecté, elles visent à réduire radicalement les dépendances. Les dispositifs NFC HSM sont sans batterie, sans câble, sans port réseau, et ne nécessitent ni compte, ni serveur, ni synchronisation cloud.
Ce changement de paradigme se matérialise notamment par le partage de secrets en air-gap : les secrets critiques (seed phrases, clés privées, identifiants de connexion à des hot wallets ou systèmes propriétaires) peuvent être transférés matériel → matériel d’un SeedNFC HSM vers un autre, via un QR code chiffré RSA 4096 avec la clé publique du destinataire — sans blockchain, sans serveur et sans signature de transaction.
Une réponse structurelle aux failles observées depuis 2017
Là où les failles Ledger reposent sur des chaînes d’approvisionnement, des mises à jour ou des relations commerciales, les architectures souveraines suppriment ces points de rupture par conception. Il n’y a rien à pirater à distance, rien à détourner dans un cloud, rien à extraire d’un serveur tiers. Même exposé visuellement, un QR code chiffré reste inexploitable sans possession effective du HSM destinataire.
Ce modèle ne promet pas une sécurité « magique ». Il impose au contraire une responsabilité assumée : irrévocabilité des partages, contrôle physique, discipline opérationnelle. Mais il élimine les vecteurs d’attaque systémiques qui, depuis 2017, n’ont cessé de se répéter.
Failles de sécurité Ledger de 2017 à 2026 : Comment protéger vos cryptomonnaies
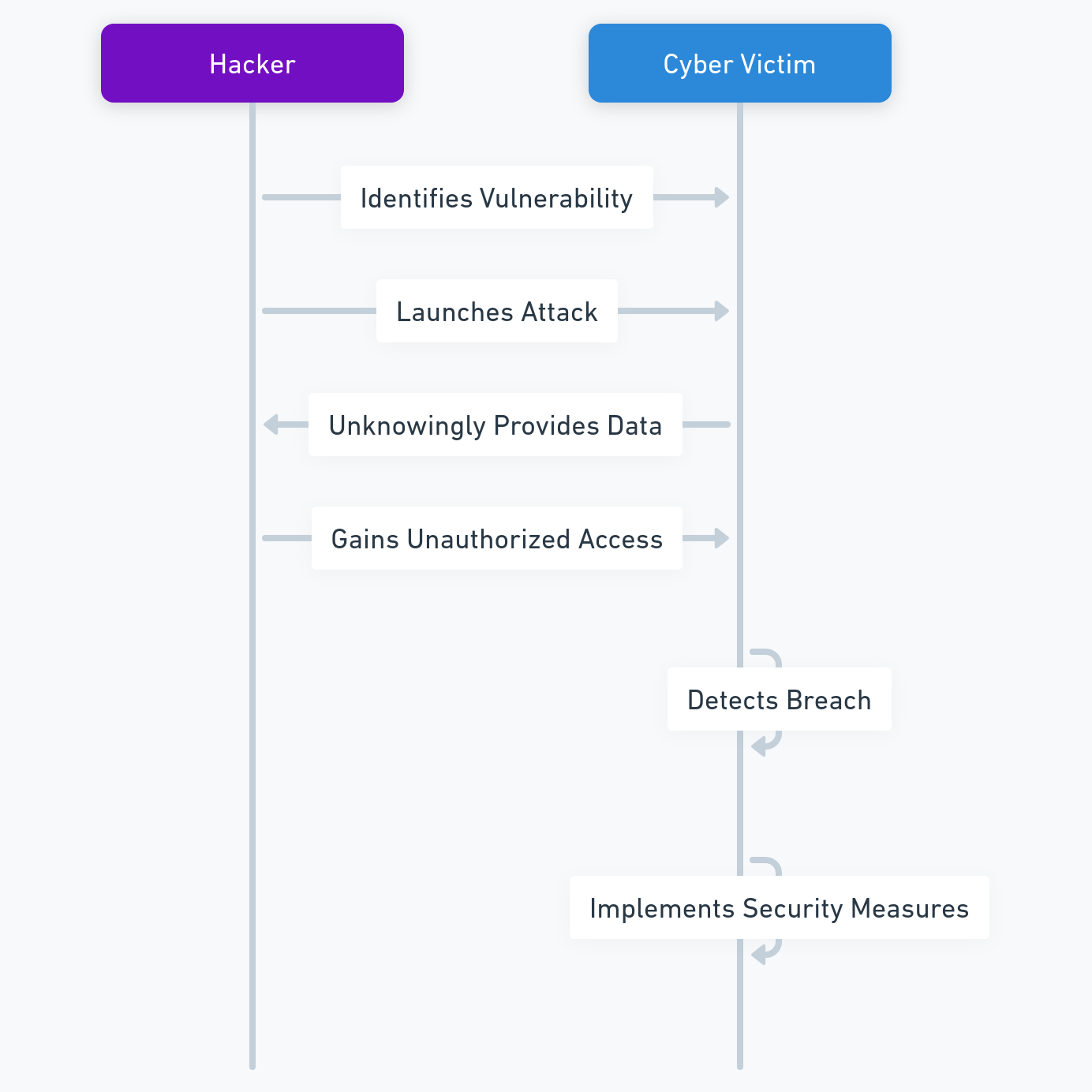
Vous êtes-vous déjà interrogé sur la réelle sécurité de vos actifs numériques ? Si vous utilisez un appareil Ledger, vous pensez probablement être à l’abri des pirates. Ledger est une entreprise française leader dans la sécurité des cryptomonnaies. Elle propose des portefeuilles matériels (hardware wallets) conçus pour isoler vos clés privées des menaces en ligne.
Pourtant, depuis 2017, les failles de sécurité Ledger se sont succédé, exposant parfois les données personnelles, voire les clés privées des utilisateurs. Ces vulnérabilités permettent à des attaquants de dérober vos fonds ou de nuire à votre vie privée. Cet article analyse les différentes brèches découvertes, leurs modes d’exploitation et les solutions pour vous protéger efficacement.
Failles de sécurité Ledger : L’attaque par récupération de Seed Phrase (Février 2018)
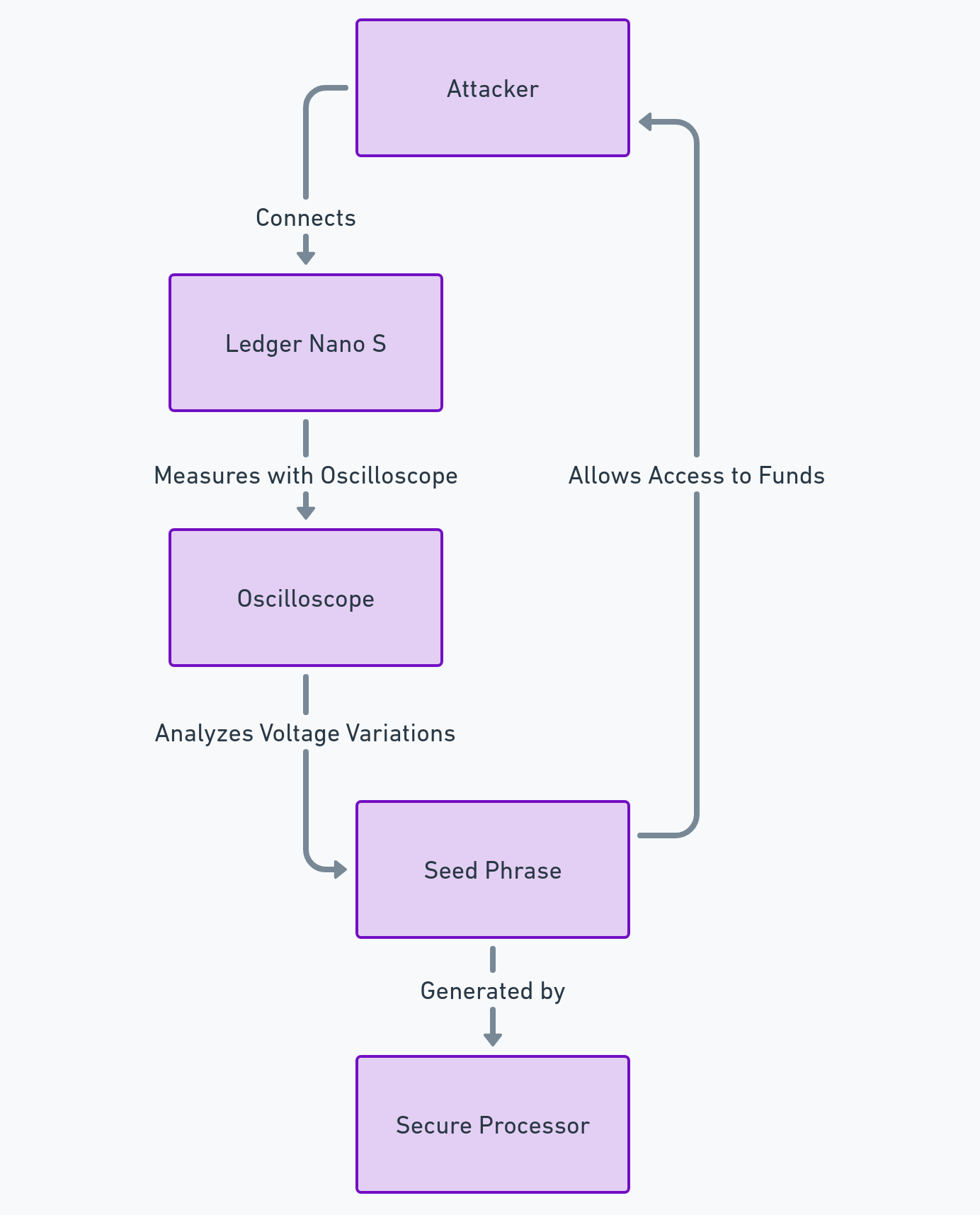
La phrase de récupération (seed phrase) est la clé maîtresse de votre portefeuille. En février 2018, le chercheur Saleem Rashid a découvert une faille sur le Ledger Nano S permettant à un attaquant ayant un accès physique à l’appareil de récupérer cette phrase via une attaque par canal auxiliaire (side-channel attack).
Comment les hackers ont-ils exploité cette faille ?
L’attaque consistait à utiliser un oscilloscope pour mesurer les variations de tension sur la broche de réinitialisation (reset pin) de l’appareil. Ces micro-fluctuations reflétaient les opérations du processeur sécurisé lors de la génération de la seed phrase. En analysant ces signaux, un attaquant pouvait reconstruire la phrase et prendre le contrôle total des fonds.
- Utilisateurs potentiellement affectés : Environ 1 million
- Montant total dérobé : Inconnu
- Date de découverte : 20 février 2018
- Auteur de la découverte : Saleem Rashid (Chercheur en sécurité)
- Date du correctif : 3 avril 2018
Scénarios d’attaques
- Accès physique : L’attaquant doit posséder l’appareil (vol, achat d’occasion ou interception durant la livraison). Il connecte le Ledger à un oscilloscope et utilise un logiciel pour extraire la phrase de récupération.
- Accès à distance : Un hacker pourrait piéger l’utilisateur en installant un malware sur son ordinateur pour déclencher la broche de reset, tout en capturant les variations de tension via un équipement compromis à proximité.
- Scénario d’accès à distance : L’attaquant doit inciter l’utilisateur à installer un logiciel malveillant sur son ordinateur. Ce programme communique avec le Ledger pour déclencher la broche de réinitialisation (reset pin). Le hacker capture ensuite les variations de tension à distance, soit via un dispositif sans fil, soit en compromettant l’oscilloscope utilisé. Un outil logiciel permet ensuite de reconstruire la phrase de récupération à partir des mesures.
Sources officielles
1 : Breaking the Ledger Security Model – Saleem Rashid (20 mars 2018).
2 : Analyse de la sécurité du Ledger Nano S – CryptoVantage.
Incidents de sécurité Ledger : Modification du circuit imprimé (PCB) — Novembre 2018
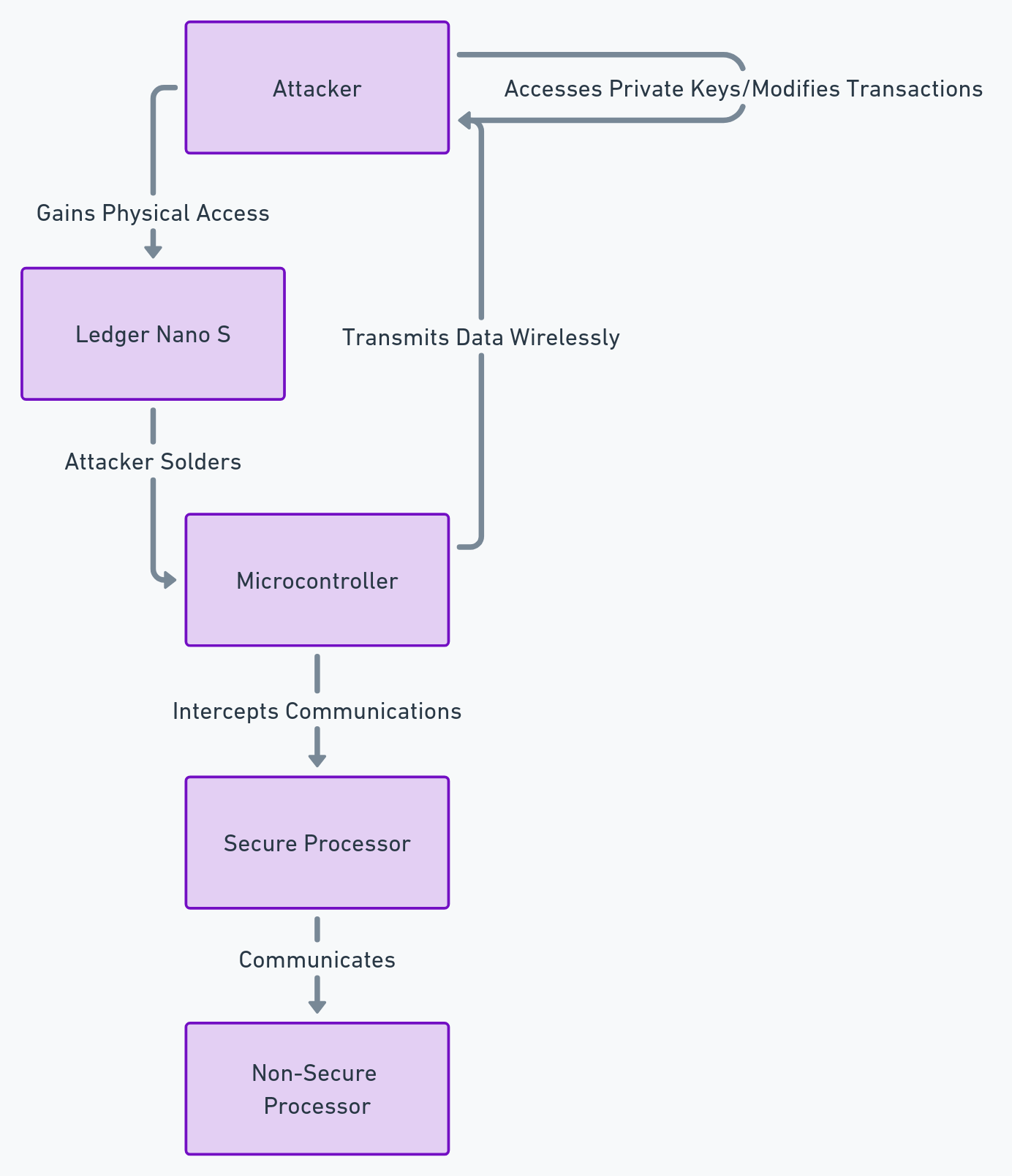
Le circuit imprimé (PCB) contient les composants électroniques du wallet. S’il est modifié physiquement, la sécurité est compromise. En novembre 2018, le chercheur Dmitry Nedospasov a montré qu’il était possible d’installer un microcontrôleur espion à l’intérieur du boîtier afin d’intercepter des échanges internes.
Comment l’attaque peut être menée ?
L’attaque consiste à ouvrir l’appareil et à ajouter une puce capable d’intercepter les communications entre les composants internes. Les données interceptées (transactions, signaux de validation, informations de session) peuvent ensuite être exfiltrées via un canal discret (ex. module radio dissimulé), selon le montage.
Scénarios d’attaque
- Supply chain : interception du wallet avant réception (transport, reconditionnement, revente) pour installer le dispositif.
- Accès physique : vol ou accès temporaire à l’appareil pour le modifier, puis restitution afin d’attendre une transaction.
- Variante avancée : combinaison d’un poste hôte compromis (malware) et d’une instrumentation matérielle — scénario complexe et moins probable, mais théoriquement possible.
Sources
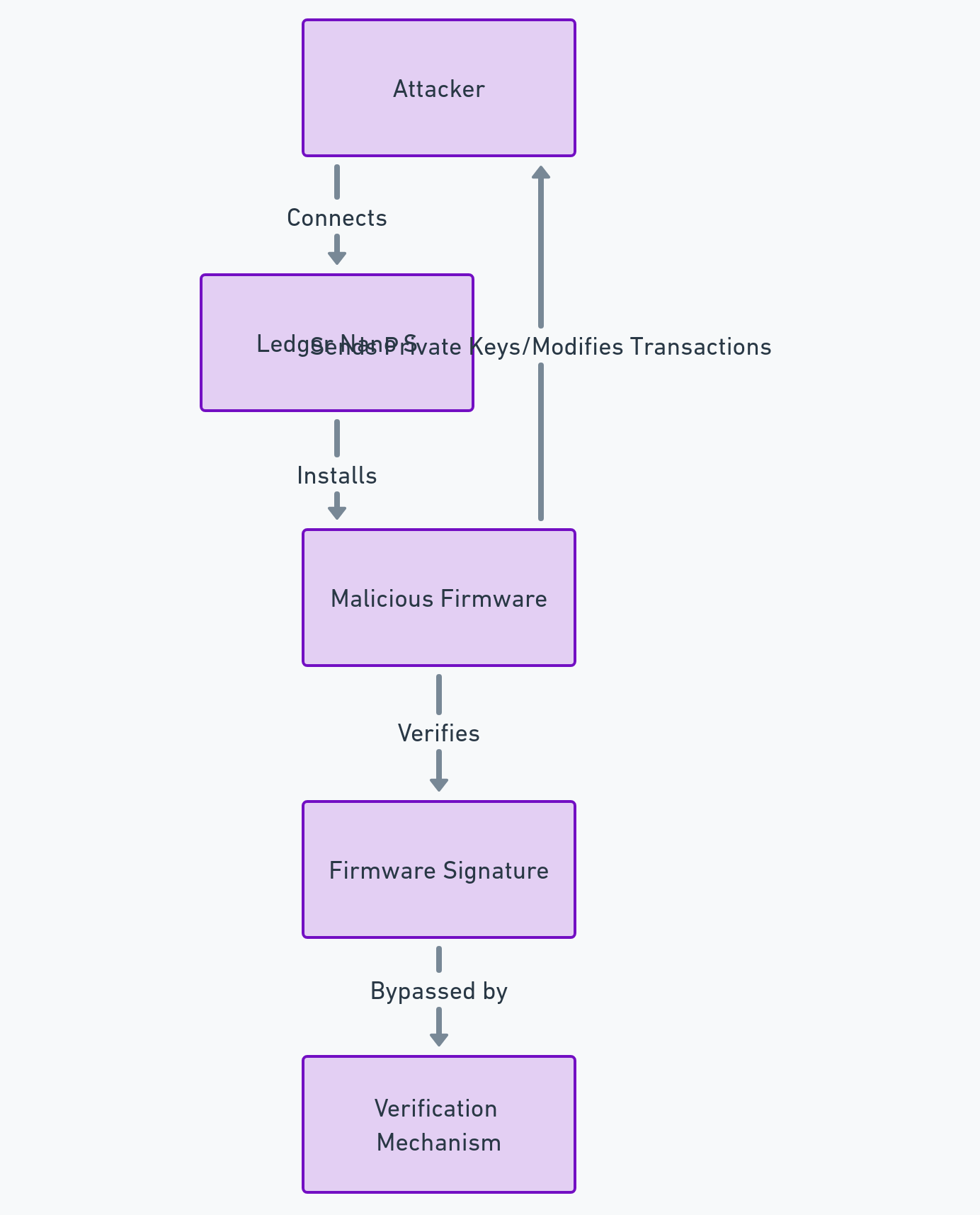
Défauts de sécurité Ledger : Attaque par remplacement de firmware — Mars 2018
Le firmware est le logiciel interne qui contrôle le fonctionnement du wallet matériel. Son intégrité repose sur un mécanisme de signature cryptographique censé empêcher l’installation de code non autorisé. En 2018, le chercheur Saleem Rashid a démontré qu’il était possible, sous certaines conditions, de contourner ce modèle sur le Ledger Nano S.
Comment l’attaque pouvait être exploitée
L’attaque reposait sur une faiblesse du processus de mise à jour et de vérification du firmware. Un attaquant capable d’installer un firmware modifié pouvait introduire un code malveillant se faisant passer pour légitime. Une fois en place, ce firmware était en mesure :
- d’extraire ou reconstruire des clés privées,
- de modifier les adresses de destination affichées à l’écran,
- ou d’altérer silencieusement la logique de signature des transactions.
Schéma simplifié de l’attaque
Données clés
- Appareils concernés : Ledger Nano S (générations initiales)
- Impact potentiel : Compromission totale du wallet après installation du firmware
- Date de divulgation : Mars 2018
- Correctif : Mise à jour firmware 1.4.1 (avril 2018)
Scénarios d’attaque
- Accès physique : l’attaquant dispose temporairement du wallet (vol, interception, revente). Il installe un firmware modifié avant restitution ou utilisation ultérieure.
- Ingénierie sociale : l’utilisateur est incité à installer une fausse mise à jour via un email ou un site frauduleux imitant Ledger.
⚠️ Point structurel : même si cette faille a été corrigée, elle illustre un risque fondamental : dès qu’un wallet dépend d’un processus de mise à jour centralisé, la confiance se déplace du matériel vers la chaîne logicielle.
Sources
- [1] Saleem Rashid — Breaking the Ledger Security Model (2018).
- [2] Ledger — Ledger Nano S Firmware 1.4.1 : What’s new.
De la faille corrigée au risque structurel
La vulnérabilité de remplacement de firmware découverte en 2018 a été corrigée rapidement par Ledger. Sur le plan strictement technique, le mécanisme de signature du firmware a été renforcé et l’attaque n’est plus exploitable dans les mêmes conditions.
Cependant, cet épisode révèle un point fondamental : la sécurité d’un hardware wallet ne dépend pas uniquement de la puce sécurisée, mais aussi de tout ce qui l’entoure — processus de mise à jour, interfaces logicielles, messages utilisateur et canaux de distribution.
À partir de 2019, la surface d’attaque ne se concentre plus sur la compromission du firmware lui-même, mais sur un vecteur plus insidieux : l’utilisateur devient le point faible.
Le contrôle ne passe plus par l’installation de code malveillant, mais par la signature volontaire d’actions que l’utilisateur ne peut pas réellement vérifier.
C’est dans ce contexte qu’émerge le problème du Blind Signing — non pas comme une faille ponctuelle, mais comme un risque permanent, inhérent à l’interaction entre hardware wallets et écosystèmes Web3 complexes.
En d’autres termes : après 2018, l’attaque ne cherche plus à tromper la machine, mais à convaincre l’humain de signer à l’aveugle.
Failles de sécurité Ledger : La vulnérabilité de l’application Monero (Mars 2019)
Toutes les cryptomonnaies ne sont pas gérées de la même manière par le hardware. En mars 2019, une faille critique a été découverte dans l’application Monero (XMR) pour Ledger. Contrairement aux failles physiques, celle-ci résidait dans le protocole de communication entre le wallet et le logiciel client sur ordinateur.
Comment les hackers ont-ils exploité cette faille ?
La faille permettait à un attaquant, via un logiciel client malveillant, de forcer le Ledger à envoyer des données de transaction erronées. En exploitant un bug dans la gestion du “change” (la monnaie rendue lors d’une transaction), le hacker pouvait détourner les fonds vers une adresse qu’il contrôlait, sans que l’utilisateur ne s’en aperçoive sur son écran, ou même extraire la clé de dépense privée (spend key) du Monero.
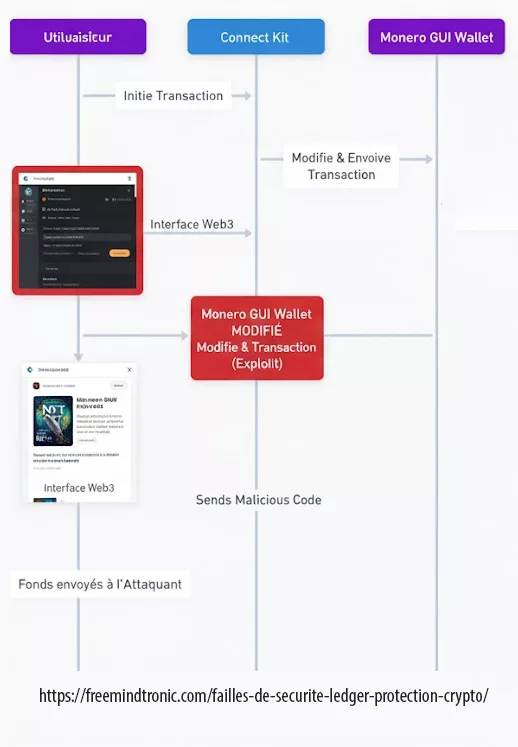
- Utilisateurs potentiellement affectés : Tous les détenteurs de Monero (XMR) sur Nano S et X
- Montant total dérobé : Un cas rapporté de 1600 XMR (env. 83 000 $)
- Date de découverte : 4 mars 2019
- Auteur de la découverte : Communauté Monero & Ledger Donjon
- Date du correctif : 6 mars 2019 (Version 1.5.1)
Scénarios d’attaques
- Logiciel compromis : L’utilisateur utilise un portefeuille Monero GUI infecté ou non officiel. Lors d’une transaction légitime, le logiciel modifie les paramètres envoyés au Ledger pour vider le solde.
- Extraction de clé : Un attaquant ayant infecté l’ordinateur de la victime pouvait techniquement reconstruire la clé privée Monero en interceptant plusieurs échanges de données entre l’appareil et le PC.
Vulnérabilité structurelle « Blind Signing » : la signature à l’aveugle par conception (Permanent)
Le Blind Signing n’est pas une faille ponctuelle ni un bug corrigeable par mise à jour. Il s’agit d’un défaut structurel inhérent à la conception même des hardware wallets face à la complexité croissante des smart contracts.
En 2026, il constitue le vecteur n°1 de vol de fonds en Web3, devant les exploits techniques classiques.
Pourquoi le Blind Signing est fondamentalement dangereux
Un hardware wallet est censé permettre une validation consciente et vérifiable des opérations sensibles. Or, dans le cas du Blind Signing, l’appareil est incapable de restituer l’intention réelle du contrat signé.
L’utilisateur se retrouve face à :
- la mention générique « Data Present »
- des chaînes hexadécimales illisibles
- ou une description partielle, non interprétable humainement
La signature devient alors un acte de foi.
L’utilisateur ne valide plus une action comprise, mais obéit à une interface opaque.
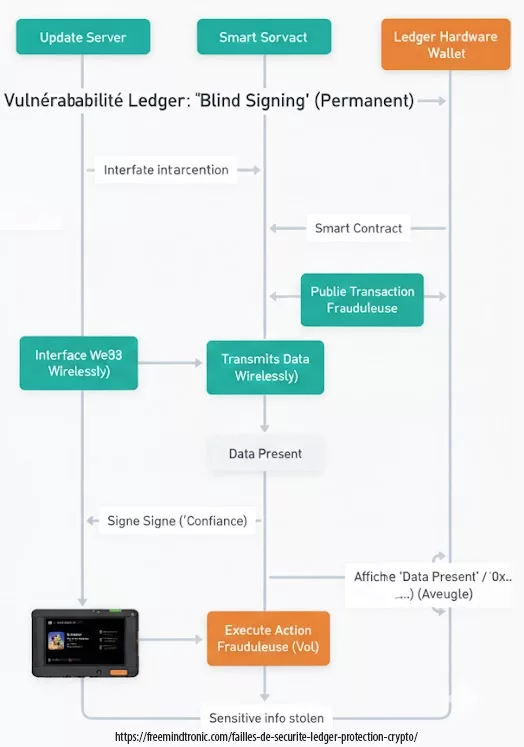
Figure — Le Blind Signing : quand l’utilisateur signe une transaction dont il ne peut pas vérifier l’intention réelle.
Une attaque par consentement, pas par contournement
Contrairement aux failles de 2018 (seed, firmware, PCB), le Blind Signing ne cherche pas à casser la sécurité matérielle.
Il la retourne contre l’utilisateur.
Tout est :
- cryptographiquement valide
- signé avec la vraie clé privée
- irréversible sur la blockchain
Il n’y a ni malware détectable, ni extraction de clé, ni compromission du firmware. La perte est juridiquement et techniquement imputable à la signature elle-même.
Impact et portée
- Utilisateurs concernés : 100 % des utilisateurs DeFi / NFT / Web3
- Montants détournés : centaines de millions de dollars (cumulés)
- Statut : risque permanent et systémique
- Cause racine : impossibilité de vérifier l’intention signée
Scénarios d’attaques typiques
- Drainer de portefeuille : un faux mint ou airdrop entraîne la signature d’un contrat autorisant le transfert illimité de tous les actifs.
- Approbation infinie masquée : l’utilisateur signe une autorisation invisible. Le wallet est vidé ultérieurement, sans interaction supplémentaire.
Conclusion :
Le Blind Signing marque une rupture : la clé privée reste protégée, mais la sécurité réelle disparaît.
La question n’est plus « mon wallet est-il sécurisé ? », mais :
« Suis-je capable de prouver ce que je signe ? »
Failles de sécurité Ledger : L’attaque du Connect Kit (Décembre 2023)
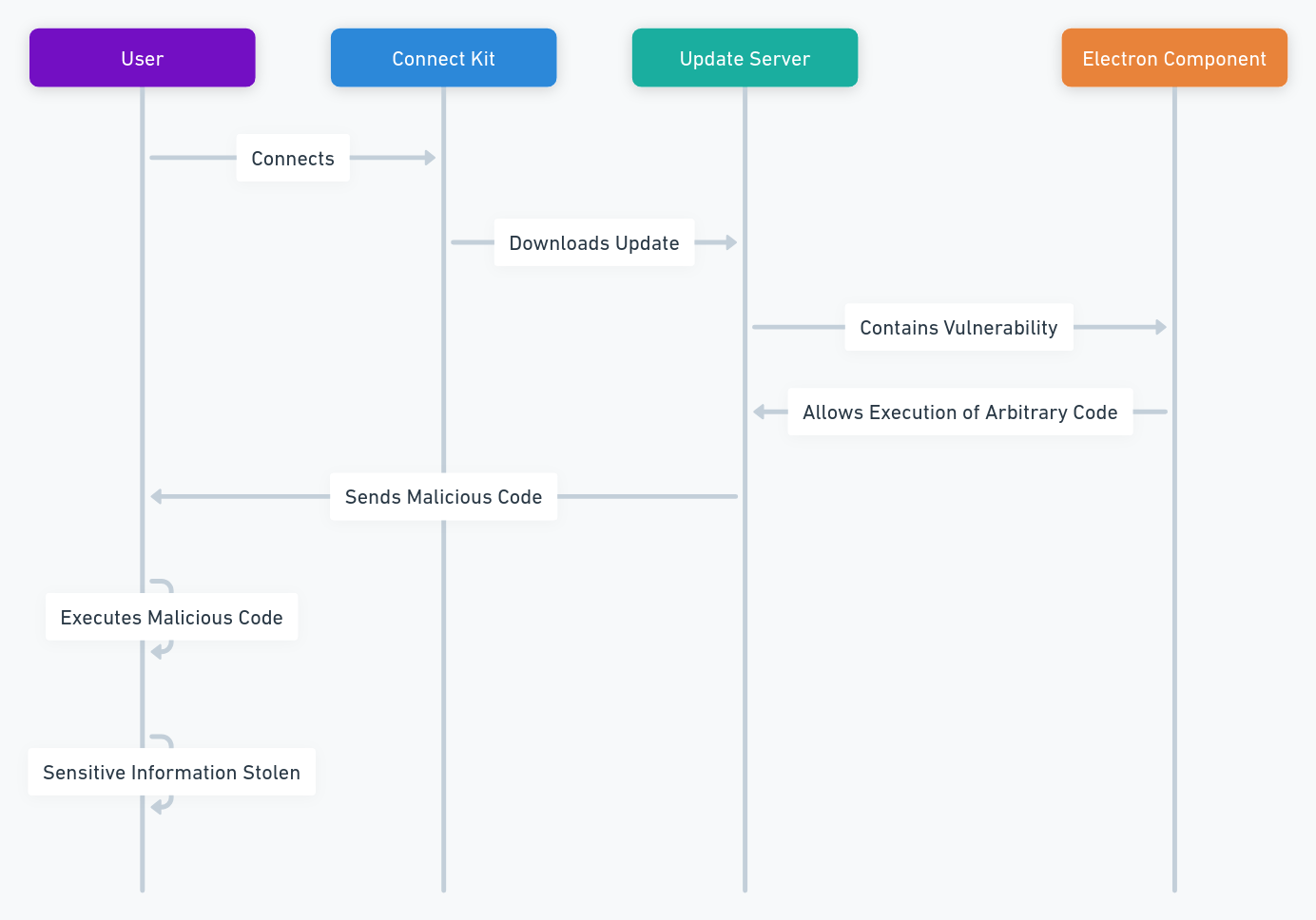
Le Connect Kit est un logiciel permettant aux utilisateurs de gérer leurs cryptomonnaies depuis un ordinateur ou un smartphone en se connectant à leur appareil Ledger. Il permet de consulter les soldes, d’effectuer des transactions et d’accéder à des services de staking ou de swap.
La faille du Connect Kit a été découverte par les équipes de sécurité de Ledger en décembre 2023. Elle provenait d’une vulnérabilité dans un composant tiers, Electron, un framework utilisé pour créer des applications de bureau. La version obsolète utilisée présentait une brèche permettant aux hackers d’exécuter du code arbitraire sur le serveur de mise à jour.
Validation technique : Ce type d’attaque de la chaîne d’approvisionnement (Supply Chain Attack) est classé sous la référence CWE-494 (Téléchargement de code sans vérification d’intégrité). Vous pouvez suivre les vulnérabilités similaires sur la base de données MITRE CVE.
Comment les hackers ont-ils exploité cette faille ?
Les pirates ont injecté un code malveillant directement sur le serveur de mise à jour du Connect Kit. Ce code était ensuite téléchargé et exécuté par les utilisateurs mettant à jour leur logiciel, avec pour objectif de voler des informations sensibles : clés privées, mots de passe, emails et numéros de téléphone.
Schéma simplifié de l’attaque
Statistiques sur la faille
- Utilisateurs potentiellement affectés : Environ 10 000
- Montant total des fonds dérobés : Inconnu
- Date de découverte : 14 décembre 2023
- Responsable de la découverte : Pierre Noizat, directeur de la sécurité chez Ledger
- Date du correctif : 15 décembre 2023
Scénarios d’attaques
- Accès à distance : Le hacker incite l’utilisateur à mettre à jour son Connect Kit via un faux email ou une notification de phishing. Le code malveillant s’exécute alors pour subtiliser les fonds.
- Capture clavier (Keylogger) : Le code malveillant enregistre les frappes au clavier de l’utilisateur (codes PIN, phrases de secours) et les transmet au hacker.
- Capture d’écran : Un enregistreur d’écran capture les QR codes, les adresses et les confirmations de transaction pour permettre au pirate de modifier les flux financiers.
Sources
- [1] The Hacker News – Crypto Hardware Wallet Ledger’s Supply Chain Attack (15 décembre 2023).
Failles de sécurité Ledger : La fuite de données massive (Décembre 2020)
La base de données clients de Ledger stocke des informations telles que les noms, adresses, numéros de téléphone et emails. En décembre 2020, Ledger a révélé qu’une faille majeure avait exposé les données personnelles de 292 000 clients, dont 9 500 en France.
Comment les hackers ont-ils exploité la brèche ?
La faille a été exploitée dès juin 2020 via une clé API mal configurée. Le hacker a ensuite publié ces données sur un forum de hackers, les rendant accessibles à tous. Les clients de Ledger sont depuis la cible de campagnes de phishing ultra-personnalisées, de harcèlement et même de menaces physiques par des acteurs cherchant à obtenir leurs clés privées.
Schéma simplifié de l’attaque
Statistiques sur la faille
- Nombre d’utilisateurs affectés : 292 000, dont 9 500 en France
- Montant total des fonds potentiellement volés : Inconnu
- Date de découverte par Ledger : 25 juin 2020
- Auteur de la découverte : Ledger, après avoir été notifié par un chercheur
- Date de publication du correctif : 14 juillet 2020
Scénarios d’attaques par hackers
- Scénario de Phishing : Le hacker envoie un email ou un SMS en se faisant passer pour Ledger. Il demande à l’utilisateur de cliquer sur un lien, de saisir ses identifiants ou de mettre à jour son appareil sur un faux site pour voler ses fonds.
- Scénario de Harcèlement : Le hacker utilise les données personnelles pour intimider l’utilisateur par téléphone. Il menace de révéler son identité ou de s’en prendre à ses biens si une rançon n’est pas versée en cryptomonnaies.
- Scénario de Menaces : En croisant les données avec les réseaux sociaux, le hacker identifie les proches de la victime. Il envoie des messages menaçants pour forcer l’utilisateur à donner ses clés privées.
Source : Ledger Blog : Mise à jour sur la cybersécurité (Janvier 2021)
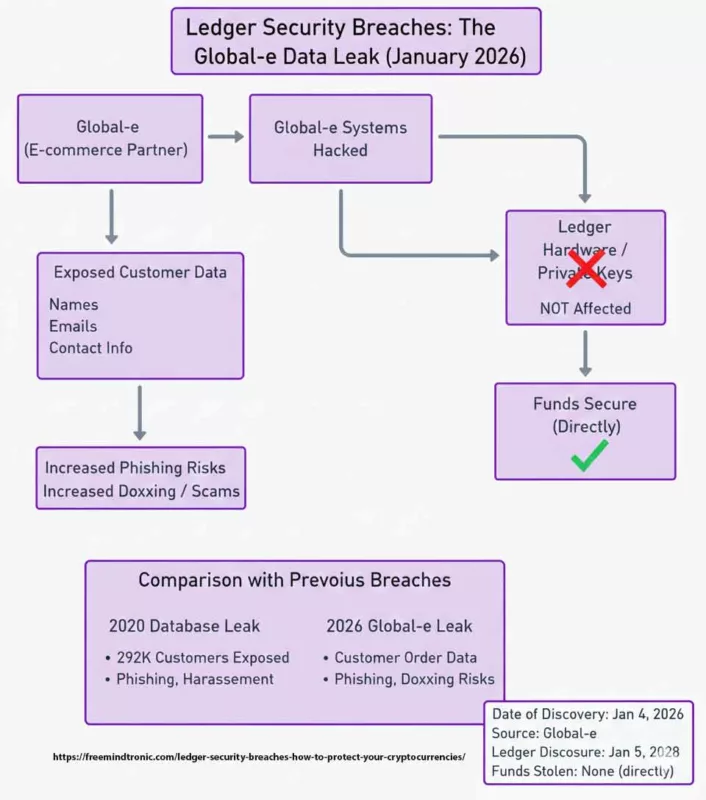
Failles de sécurité Ledger : La fuite de données Global‑e (Janvier 2026)
En janvier 2026, Ledger a révélé une nouvelle brèche causée par son partenaire e‑commerce Global‑e. Des hackers ont compromis les systèmes de ce prestataire, exposant les noms, adresses email et coordonnées de contact utilisés pour les commandes en ligne. Contrairement aux incidents précédents, aucune phrase de récupération (seed phrase), clé privée ou donnée de carte de paiement n’a été touchée. Cependant, cette fuite augmente considérablement les risques de phishing ciblé, de doxxing et d’escroqueries.

Défense Active : Neutraliser les risques de la fuite Global-e
L’écosystème SeedNFC HSM, couplé à PassCypher HSM PGP Free, apporte une réponse structurelle à ces risques en déplaçant la sécurité entre les mains de l’utilisateur :
- Réduction des métadonnées d’achat : en minimisant la collecte et la rétention de données (nom, adresse, téléphone), on réduit l’impact des fuites e-commerce/logistiques type 2020 et Global-e (2026) : moins de doxxing, moins de phishing “livreur”, moins de ciblage physique.
- Preuve d’intention matérielle : certaines opérations critiques exigent une action physique (NFC). Après une fuite de données, cela réduit l’efficacité des attaques à distance (phishing, faux support) car un attaquant ne peut pas “finaliser” l’action sans présence physique.
- Anti-BITB & Anti-Iframe : réduit les faux écrans de connexion utilisés dans les campagnes de phishing post-fuite (fausses pages Ledger Live, faux support, redirections).
- Détection d’identifiants compromis : vérifie si des emails/mots de passe ont déjà fuité afin d’éviter leur réutilisation (réduction du risque de prise de compte et d’ingénierie sociale).
Statistiques sur la faille Global-e
- Nombre d’utilisateurs affectés : Non communiqué (enquête en cours en janv. 2026).
- Données exposées : Noms, emails et coordonnées de livraison des commandes.
- Impact sur les actifs sensibles : Aucun (clés privées et fonds en sécurité).
- Date de découverte : 4 janvier 2026.
- Source de la brèche : Système cloud de Global-e.
⚠️ Alerte Critique : Revente sur le Dark Web
Une fuite de données est permanente. Une fois votre nom associé à l’achat d’un portefeuille crypto, vous restez une cible prioritaire pour les années à venir.
Défense Souveraine : Pour dissocier votre identité numérique de ces fuites récurrentes, utilisez SeedNFC HSM. En gérant vos clés dans un environnement exclusivement matériel, vous éliminez la traçabilité via les bases de données e-commerce centralisées.
Finaliste : Intersec Expo Awards 2026
Sécurité Post-Quantique & Sans Mot de Passe
Le PassCypher HSM PGP de Freemindtronic (sans FIDO, RAM-only) est reconnu parmi les meilleures solutions mondiales pour lutter contre les cyberattaques sophistiquées.
Sources Officielles et Experts
- [1] Ledger Support : Rapport d’incident Global‑e (Janvier 2026)
- [2] Europol (IOCTA) : Marché de la revente d’identifiants volés.
- [3] ANSSI / Cybermalveillance.gouv.fr : Conseils officiels sur les fuites de données.
- [4] CoinDesk : Ledger alerte sur les risques de phishing après le piratage d’un partenaire (5 janv. 2026).
Réactions en France : Entre Colère et Actions Collectives
La fuite Global-e de janvier 2026 a provoqué une onde de choc particulièrement vive dans la communauté crypto francophone. Déjà échaudés par les incidents de 2020 et 2023, de nombreux utilisateurs français expriment un sentiment de “trahison numérique” envers un fleuron national.
L’impact spécifique sur le marché français en 2026
- Crise de confiance de la “French Tech” : Ledger, autrefois symbole de la souveraineté technologique française, fait face à une remise en question sans précédent. Sur les forums spécialisés (JVC, CryptoFR) et les canaux Telegram, l’indignation ne porte plus sur la robustesse du composant physique, mais sur la porosité répétée de l’écosystème de vente.
- Ingénierie sociale “Livreur” : La France est la cible privilégiée d’une campagne de phishing SMS massive. Profitant des données de commande volées, des pirates simulent des anomalies de livraison Chronopost ou Colissimo. L’objectif : inciter l’utilisateur à saisir sa phrase de récupération sur un faux portail de “déblocage de colis”.
- La psychose du “Home-jacking” : La divulgation des adresses physiques est le point le plus critique. Dans un contexte de hausse des vols ciblés, la publication de listes de “possesseurs de crypto” sur les forums du Dark Web expose les foyers français à des risques de menaces physiques et d’extorsion à domicile.
Vers une judiciarisation massive : Les recours en France
Pour les investisseurs français, la sécurité ne peut plus être uniquement logicielle ; elle doit être juridique et relationnelle. Plusieurs collectifs d’utilisateurs préparent des actions d’envergure :
- Plaintes auprès de la CNIL : Des milliers de signalements ont été déposés en vertu du RGPD pour défaut de sécurisation des données par un tiers (Global-e). La responsabilité solidaire de Ledger est ici pointée du doigt.Déposer une plainte officielle à la CNIL
- Signalements SignalConso : La DGCCRF a été saisie par de nombreux clients pour “pratiques commerciales trompeuses”, estimant que la promesse de sécurité absolue est rompue par les fuites répétées de métadonnées. Signaler un litige sur SignalConso
- Action de groupe (Class Action) : Des cabinets d’avocats parisiens spécialisés en droit numérique étudient une action collective pour obtenir réparation du préjudice moral et du risque sécuritaire permanent induit par l’exposition des données.
« Le hardware est solide, mais la gestion des données est poreuse. En 2026, on ne peut plus accepter qu’une faille marketing mette en péril notre sécurité physique et l’anonymat de notre patrimoine. » – Synthèse des avis relevés sur les plateformes communautaires françaises.
L’escalade des menaces : Du Phishing Livreur au Home-jacking
La compromission des données de livraison via Global-e en janvier 2026 n’est pas qu’une simple fuite d’emails. Elle ouvre la porte à des attaques hybrides d’une violence et d’une précision inédites, transformant une vulnérabilité numérique en une menace vitale.
Le Phishing “Livreur” : L’arnaque de précision
C’est la menace la plus immédiate en France et en Europe. Les pirates utilisent l’historique de commande pour envoyer des SMS ultra-crédibles :
- Le scénario : Un SMS simulant Chronopost ou Colissimo indique un “blocage de douane” ou une “adresse incomplète” pour votre colis Ledger.
- Le piège : Le lien renvoie vers une copie parfaite de l’interface Ledger Live demandant votre phrase de 24 mots pour “débloquer” la livraison.
- Pourquoi ça marche : Parce que l’utilisateur attend réellement un produit ou une mise à jour, rendant sa garde beaucoup plus basse.
Le Home-jacking et l’extorsion physique
C’est le risque le plus sombre lié à la divulgation des adresses physiques. Ce n’est plus un “mal français” mais un fléau mondial (UK, Espagne, USA, Brésil).
- Ciblage à domicile : La liste Global-e permet à des groupes criminels locaux de planifier des “visites” à domicile. Contrairement à un cambriolage classique, le but est ici le Home-jacking : vous contraindre, sous la menace, à effectuer un transfert irréversible.
- L’ultra-violence : Les faits divers internationaux rapportent des cas de séquestration et de mutilations (doigts coupés pour forcer l’accès ou terroriser la victime). En crypto, l’agresseur sait que s’il part avec les fonds, il n’y a pas de bouton “annuler”.
- L’enlèvement de proches : La menace se déplace parfois sur les membres de la famille (conjoint, enfants) pour briser la résistance de l’investisseur.
« La fuite d’une adresse de livraison Ledger est une signature : elle indique aux criminels exactement où se trouve le coffre-fort et qui en a la clé. » Cette réalité impose une remise en question totale de la manière dont nous acquérons nos outils de sécurité.
Comparaison avec d’autres portefeuilles crypto
Ledger n’est pas la seule solution pour sécuriser vos cryptomonnaies. Il existe d’autres options, telles que d’autres portefeuilles matériels, des portefeuilles logiciels ou des plateformes d’échange. Chaque option présente des avantages et des inconvénients, selon vos besoins et vos préférences.
Autres Portefeuilles Matériels (Hardware Wallets)
Par exemple, d’autres portefeuilles comme Trezor offrent des fonctionnalités et des niveaux de sécurité similaires à Ledger, mais peuvent présenter des designs, des interfaces ou des tarifs différents.
Portefeuilles Logiciels (Software Wallets)
Les portefeuilles logiciels, comme Exodus ou Electrum, sont plus pratiques et accessibles, mais ils sont moins sécurisés et plus vulnérables aux logiciels malveillants ou au piratage informatique.
Plateformes d’Échange (Exchanges)
Les plateformes comme Coinbase ou Binance sont plus conviviales et offrent plus de services (trading, staking), mais elles sont centralisées et risquées : elles peuvent être piratées, fermées ou soumises à des restrictions réglementaires soudaines.
| Vecteur de Sécurité | Portefeuille USB Traditionnel | Freemindtronic NFC HSM |
|---|---|---|
| Surface d’Attaque Physique | Élevée (Ports USB, Batterie, Écran) | Minimale (Sans port, Sans batterie) |
| Persistance des Données | Risque d’usure de la mémoire flash | Élevée (Intégrité long terme EviCore) |
| Fuite par Canal Auxiliaire | Possible (Analyse de consommation électrique) | Immunisé (Induction passive) |
Alternatives en Cold Storage
Une autre option consiste à utiliser un “cold wallet” tel que le SeedNFC HSM. Il s’agit d’un HSM breveté utilisant la technologie NFC pour stocker et gérer vos cryptomonnaies hors ligne, sans aucune connexion Internet ou physique à un ordinateur. Il permet de créer jusqu’à 50 portefeuilles (Bitcoin & Ethereum, génération en un clic, stockage chiffré dans le HSM de la seed phrase, clé privée et adresse, plus QR de clé publique) et de consulter les soldes directement depuis ce HSM NFC.
Technologie Souveraine Brevetée Internationalement
Pour répondre aux failles structurelles identifiées dans les portefeuilles matériels traditionnels, Freemindtronic utilise une architecture unique protégée par des brevets internationaux (OMPI). Ces technologies garantissent que l’utilisateur reste le seul maître de son environnement de sécurité.
- Système de Contrôle d’Accès — Brevet WO2017129887Garantit l’intégrité physique vers le numérique en s’assurant que le HSM ne peut être déclenché que par une action humaine spécifique et intentionnelle, empêchant toute exploitation à distance.
- Système d’Authentification par Clé Segmentée — Brevet WO2018154258Offre un mécanisme de défense en profondeur où les secrets sont fragmentés. Cela évite un “point de défaillance unique”, rendant inefficaces les attaques de type “Connect Kit” ou les remplacements de firmware.
Projections Technologiques, Réglementaires et Sociétales
L’avenir de la sécurité des cryptomonnaies est parsemé de défis. Plusieurs facteurs peuvent impacter Ledger et ses utilisateurs, qu’il s’agisse d’évolutions technologiques, législatives ou sociétales.
Évolutions Technologiques
Ces changements pourraient apporter de nouvelles menaces, comme l’informatique quantique capable de briser le chiffrement actuel, mais aussi de nouvelles solutions. L’authentification biométrique ou l’authentification par clé segmentée brevetée par Freemindtronic permettent déjà d’anticiper ces risques.
Évolutions Réglementaires
De nouvelles règles pourraient affecter les fabricants de Cold Wallets et leurs utilisateurs. Par exemple, les exigences de KYC (Know Your Customer) ou de lutte contre le blanchiment (AML) pourraient compromettre la vie privée et l’anonymat. Voici quelques exemples de cadres réglementaires majeurs :
- Le règlement MiCA (Markets in Crypto-Assets), et spécifiquement le titre V sur les obligations des prestataires de services, est désormais la norme de référence. Les technologies de Freemindtronic sont conçues pour s’aligner sur le Règlement Officiel (UE) 2023/1114, garantissant la confidentialité tout en répondant aux besoins de conformité.
- Le rapport inter-agences américain sur les stablecoins recommande que les portefeuilles numériques soient soumis à une surveillance fédérale.
- Les directives révisées du GAFI (Financial Action Task Force) introduisent la “Travel Rule”, imposant l’échange d’informations sur les expéditeurs et destinataires de transactions virtuelles.
Évolutions Sociétales
La perception et l’adoption des cryptomonnaies évoluent vers une exigence de transparence. L’éducation accrue des utilisateurs augmente la méfiance envers les solutions centralisées. Par exemple, la technologie EviSeed NFC HSM répond à cette demande en permettant la création de jusqu’à 100 portefeuilles sur 5 blockchains différentes, choisies librement par l’utilisateur sans intermédiaire.
Alternatives technologiques pour une souveraineté absolue
La persistance des failles de sécurité Ledger démontre que s’appuyer sur un seul fabricant centralisé crée un risque systémique. Aujourd’hui, les alternatives décentralisées développées par Freemindtronic en Andorre proposent un changement de paradigme : une sécurité basée sur la preuve matérielle et l’intention physique, plutôt que sur la confiance envers une marque.
Les technologies telles que EviCore NFC HSM et EviSeed NFC HSM ne sont pas de simples portefeuilles ; ce sont des écosystèmes de cybersécurité sans contact. Contrairement à Ledger, ces dispositifs sont sans batterie et sans câble, éliminant les ports physiques (USB/Bluetooth) comme vecteurs d’attaque.
Sécurité brevetée internationalement
L’architecture de Freemindtronic s’appuie sur deux brevets internationaux fondamentaux (OMPI) qui résolvent les failles structurelles des portefeuilles matériels traditionnels :
- Système d’Authentification par Clé Segmentée (WO2018154258) : Empêche la compromission de l’intégralité de la seed ou de la clé privée, même en cas d’attaque de l’environnement numérique.
- Système de Contrôle d’Accès (WO2017129887) : Garantit que le HSM ne peut être déclenché que par l’intention physique de l’utilisateur via NFC, neutralisant les menaces logicielles distantes.
Partage définitif de secrets en air-gap : QR code chiffré entre SeedNFC HSM
SeedNFC met en œuvre un mécanisme de partage de secrets en air-gap total reposant sur un QR code chiffré en RSA 4096 avec la clé publique du destinataire.
Le destinataire est obligatoirement un autre SeedNFC HSM, garantissant que lui seul peut déchiffrer et importer le secret directement dans son module matériel.
Le QR code n’est qu’un vecteur de transport chiffré. Il peut être affiché localement, transmis sous forme d’image ou présenté en visioconférence.
Sans possession effective du SeedNFC HSM destinataire, le contenu demeure mathématiquement inexploitable.
- Chiffrement asymétrique hors ligne : le secret n’est jamais exposé en clair dans le QR code.
- Zéro infrastructure : aucun serveur, aucun compte, aucune base de données, aucun cloud.
- Air-gap logique et opérationnel : le partage reste possible sans connexion réseau.
Ce mécanisme n’intègre ni révocation, ni temporisation, ni expiration : le partage est définitif, assumé comme tel.
Il autorise le transfert direct matériel → matériel de secrets critiques (seed phrases, clés privées, identifiants d’accès) entre deux HSM matériels isolés, sans intermédiaire logiciel et sans passage par la blockchain.
Clarification : transfert de secrets ≠ signature de transactions
SeedNFC HSM n’est pas présenté ici comme un signataire de transactions. Son rôle se situe en amont : créer, stocker et transférer des secrets (seed phrases, clés privées) ou des informations d’identification (identifiant/mot de passe, accès hot wallets, systèmes propriétaires) dans un cadre matériel souverain. Il peut notamment stocker de manière chiffrée des seed phrases issues de wallets tiers (Ledger, Trezor, hot wallets logiciels, etc.), ainsi que leurs clés privées associées, sans jamais dépendre du firmware, du logiciel ou de l’infrastructure du fabricant d’origine.
Selon le contexte, ces données peuvent aussi être saisies de manière contrôlée dans un champ applicatif via un mécanisme d’émulation clavier Bluetooth HID (ex. migration, restauration, connexion).
Complément : pour les usages Web, une saisie contrôlée équivalente peut être déclenchée via l’extension navigateur Freemindtronic (sélection explicite du champ). Ce qui a pour effet d’éliminer l’exposition via presse-papiers, fichiers temporaires ou synchronisations cloud, et réduit fortement les risques liés aux keyloggers logiciels classiques (capture de frappes), puisque l’utilisateur ne tape rien au clavier.
Note de périmètre : comme toute saisie, la donnée peut redevenir observable au point d’affichage ou sur un poste hôte compromis (capture d’écran, malware applicatif). L’objectif est de supprimer les vecteurs “copier-coller/fichiers” et la frappe humaine, pas de “rendre invulnérable” un système infecté.
Important : transférer une clé privée revient à transférer la propriété (accès total aux fonds associés). Ce mécanisme est donc pertinent pour des usages comme backup, migration, succession ou transfert de propriété hors-chaîne, mais il doit être utilisé avec une discipline opérationnelle stricte.
SeedNFC : génération native de wallets (Bitcoin & Ethereum)
Un seul SeedNFC HSM peut générer jusqu’à 50 portefeuilles Bitcoin et Ethereum en un clic, avec création automatique et stockage chiffré dans le HSM de la seed phrase, de la clé privée et de l’adresse, ainsi que la génération d’un QR code de clé publique pour la réception et la consultation.
Lecture transversale : pourquoi ce mécanisme répond aux failles Ledger depuis 2017
Depuis 2017, les failles de sécurité Ledger révèlent un même point de rupture : la nécessité pour la seed phrase ou la clé privée de transiter, à un moment, par un environnement logiciel, un firmware ou une infrastructure tierce.
Le mécanisme de partage de secrets de SeedNFC adopte une approche radicalement différente.
La seed ou la clé privée ne quitte jamais le domaine matériel souverain : elle est transférée directement d’un SeedNFC HSM vers un autre SeedNFC HSM, via un QR code chiffré avec la clé publique du destinataire.
Il n’existe aucun serveur à compromettre, aucun logiciel à détourner, aucune base client à fuiter, aucun partenaire tiers à infiltrer. Même exposé visuellement, le QR code reste inexploitable sans possession physique du HSM destinataire.
Ce modèle neutralise, par conception, les vecteurs d’attaque observés chez Ledger (firmware, supply-chain, phishing, e-commerce, partenaires logistiques), en supprimant la dépendance à toute infrastructure connectée.
Sécurité unifiée : Gestion des mots de passe par le matériel
Extension naturelle : la même logique matérielle peut aussi protéger des identifiants (hot wallets / services), cible privilégiée des campagnes de phishing amplifiées par les fuites de données.
Accès universel : Intégration Smartphone et Bureau
Accès universel : Extension navigateur & saisie contrôlée (crypto)
En complément des mécanismes air-gap (QR chiffré) et des modes de saisie universels, SeedNFC HSM peut interagir avec l’extension navigateur Freemindtronic pour faciliter certains usages Web/crypto.
- Anti-copier/coller : évite les fuites via presse-papiers, fichiers temporaires ou synchronisations.
- Réduction du risque “keylogger” : l’utilisateur ne tape pas au clavier.
- Contrôle d’intention : aucune injection sans action explicite de l’utilisateur (sélection du champ + action volontaire).
Note de périmètre : ce mécanisme ne constitue pas une signature de transaction. Il s’inscrit dans des usages de saisie sécurisée, migration, restauration ou transfert hors-chaîne de secrets. Comme toute saisie, un poste compromis peut rester observable au point d’affichage (capture d’écran / malware applicatif).
Lorsque l’usage ne passe pas par un navigateur web ou nécessite une compatibilité universelle avec des systèmes propriétaires, SeedNFC HSM propose également des modes de saisie matérielle alternatifs, sans dépendre du presse-papiers ni d’une interaction clavier humaine classique.
Saisie contrôlée sans copier-coller : émulation clavier (HID)
Dans certains scénarios sensibles (migration, restauration, accès à un hot wallet ou à un système propriétaire), la saisie d’un secret reste nécessaire.
L’émulation de clavier matériel (Bluetooth HID) de Freemindtronic permet alors d’éviter les vecteurs les plus exposés observés dans les incidents Ledger depuis 2017.
Cas d’usage : lorsque l’opération ne passe pas par un navigateur (ex. Ledger Live ou tout logiciel propriétaire via USB), l’émulation clavier permet une saisie contrôlée sans copier-coller.
- Suppression du copier-coller : aucun passage par le presse-papiers, les fichiers temporaires ou la mémoire applicative intermédiaire.
- Réduction de l’exposition aux keyloggers classiques : l’utilisateur ne tape rien au clavier, ce qui rend inopérants les logiciels fondés exclusivement sur la capture de frappes clavier.
- Canal chiffré : les données restent chiffrées jusqu’à l’injection finale (NFC HSM → Bluetooth chiffré), limitant les interceptions passives.
Note de périmètre : comme toute saisie, la donnée peut redevenir observable au point d’affichage ou sur un poste hôte compromis (capture d’écran, malware applicatif). L’objectif n’est pas de « sécuriser un OS infecté », mais de supprimer les vecteurs les plus exploités : frappe humaine, copier-coller, fichiers et synchronisations cloud.
Défense Active : Neutraliser les attaques BITB et les redirections
L’écosystème SeedNFC HSM, couplé à la version gratuite de PassCypher HSM PGP et à l’extension de navigateur, offre un bouclier multicouche contre les menaces web modernes :
- Anti-BITB (Browser-In-The-Browser) : L’extension intègre un système anti-iframe dédié. Il détecte et bloque les fenêtres malveillantes simulant de faux écrans de connexion Ledger.
- Vérification de Corruption : Intégré avec Have I Been Pwned, le système vérifie automatiquement si vos identifiants ont été compromis dans des fuites historiques.
- Auto-remplissage chiffré de bout en bout : Les données sensibles sont chiffrées dans le HSM. Elles ne sont déchiffrées qu’à la milliseconde finale de l’injection dans le navigateur, garantissant qu’aucune donnée en clair ne réside en mémoire vive.
Utilisation : Ouvrez l’application Freemindtronic Android, posez votre HSM sur votre téléphone, et laissez le pont sécurisé gérer l’injection chiffrée directement dans votre navigateur Chrome ou Edge.
Meilleures pratiques pour se protéger
- Ne partagez jamais votre seed phrase ou vos clés privées (email, messagerie, cloud, capture d’écran, documents, support) —
aucune procédure légitime ne les exige. - Considérez toute communication entrante comme potentiellement hostile (email, SMS, appel, réseaux sociaux) et vérifiez systématiquement via un accès manuel aux canaux officiels.
- Évitez la “signature à l’aveugle” : ne signez jamais une transaction, une approbation ou un contrat dont vous ne pouvez pas vérifier clairement l’intention.
- Compartimentez strictement votre identité : utilisez un email dédié aux cryptomonnaies, évitez les noms réels, et limitez l’exposition des métadonnées d’achat et de livraison.
- Privilégiez des solutions de cold storage souveraines (NFC HSM) qui éliminent les dépendances aux firmwares, serveurs, mises à jour distantes et écosystèmes e-commerce.
- Maintenez les secrets hors des environnements connectés : évitez le presse-papiers, les fichiers temporaires, les captures d’écran,
la synchronisation cloud et la frappe manuelle. - Utilisez des mécanismes d’authentification et de gestion de secrets matériels pour neutraliser le phishing, le BITB, les keyloggers logiciels et la réutilisation d’identifiants.
- Anticipez les scénarios irréversibles : sauvegarde, migration, succession, transfert de propriété hors-chaîne doivent être définis à l’avance, avec des procédures claires.
- Acceptez la responsabilité opérationnelle : la souveraineté implique discipline, contrôle physique et acceptation de l’irrévocabilité de certaines actions.
Sécuriser l’avenir : De la vulnérabilité à la souveraineté numérique
Depuis 2017, la trajectoire des failles de sécurité Ledger sert d’étude de cas critique pour tout l’écosystème crypto. Si Ledger reste un pionnier, la répétition des incidents — des premiers exploits physiques à la fuite massive Global‑e de 2026 — démontre qu’un “appareil sécurisé” ne suffit plus. La menace s’est déplacée de la puce vers la chaîne d’approvisionnement systémique et l’exposition des données relationnelles.
L’incident de janvier 2026 confirme une réalité persistante : même si les clés privées restent protégées, la fuite des métadonnées clients crée un risque permanent de phishing ciblé et d’ingénierie sociale. Cela souligne le danger inhérent aux bases de données e-commerce centralisées.
L’alternative souveraine : La sécurité par le design
Pour briser ce cycle de dépendance, le paradigme doit évoluer vers une sécurité matérielle décentralisée. C’est là que les technologies brevetées de Freemindtronic en Andorre apportent une réponse structurelle :
- Intention physique et contrôle d’accès (WO2017129887) : Élimine la surface d’attaque distante par une validation sans contact infalsifiable.
- Authentification par clé segmentée (WO2018154258) : Protège contre les failles systémiques en garantissant que les secrets ne sont jamais centralisés.
Pour les utilisateurs de Ledger, la vigilance reste la première ligne de défense. Cependant, pour ceux qui souhaitent éliminer totalement le “risque tiers”, la transition vers des solutions NFC HSM brevetées représente l’étape ultime vers une véritable souveraineté numérique.
“Ne faites pas seulement confiance à la marque, faites confiance à l’architecture.”
Référence technique : Les architectures EviCore et SeedNFC reposent sur les brevets WO2017129887 et WO2018154258. Développées par Freemindtronic Andorre pour une souveraineté numérique absolue.