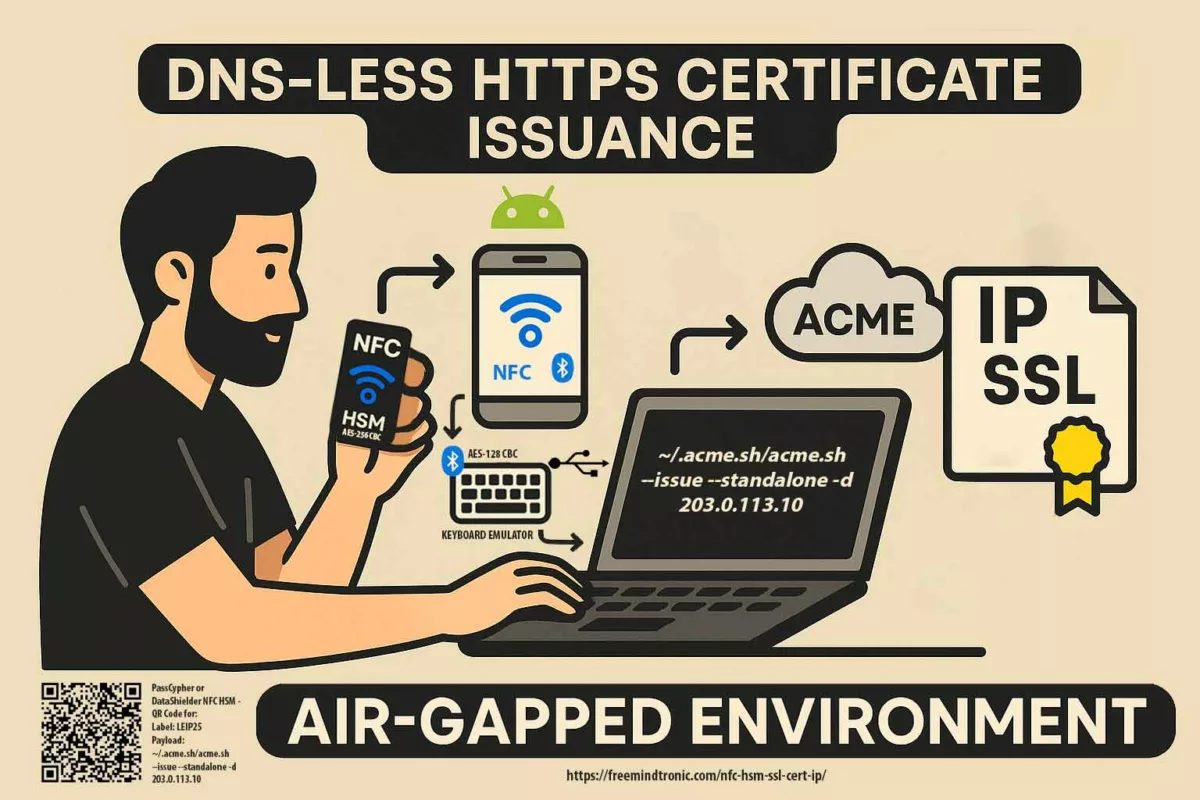
Critical Vulnerability in Microsoft Multi-Factor Authentication
A newly discovered vulnerability, nicknamed “AuthQuake,” allows hackers to bypass Microsoft’s MFA system. This significant flaw, now widely known as the Microsoft MFA Flaw Exposed, demonstrates the persistent risks associated with even seemingly robust authentication methods. Consequently, understanding this vulnerability and the proactive measures needed to counter similar threats remains crucial for individuals and organizations alike. It exposes sensitive user data, financial details, and internal communications to cyber threats. Read on to uncover the risks, methods used by attackers, and actionable steps to protect your accounts and systems.
Explore More Digital Security Insights
🔽 Discover related articles on cybersecurity threats, advanced solutions, and strategies to protect sensitive communications and critical systems.
Quick Navigation
- Critical Vulnerability in Microsoft Multi-Factor Authentication
- Microsoft MFA Security Flaw: AuthQuake Exposes Risks
- The Importance of MFA for Account Security
- How Researchers Bypassed Microsoft MFA
- AuthQuake Timeline: From Discovery to Resolution
- AuthQuake vs. Other MFA Vulnerabilities: A Comparative Analysis
- Microsoft’s Response and Mitigation Measures
- How PassCypher NFC HSM Prevents AuthQuake-like Vulnerabilities
- Proactive Data Protection with DataShielder Solutions
- Consequences for Businesses and Individuals
- Recommendations for Critical Sectors
- Taking Action for a Safer Future
Microsoft MFA Flaw Exposed: AuthQuake Exposes Risks
Summary
The discovery of the “AuthQuake” vulnerability highlights critical risks in Microsoft’s MFA system, often referred to as the “Microsoft MFA Flaw Exposed.” This security flaw exposes sensitive data, enables fraud, and compromises account protection, leaving millions at risk. Learn about the breach, its consequences, and how tools like PassCypher NFC HSM and DataShielder solutions can strengthen your security. Even as we navigate the cybersecurity landscape of 2025, the “AuthQuake” vulnerability, which initially surfaced in Microsoft’s Multi-Factor Authentication (MFA) system, still casts a long shadow.
The Importance of MFA for Account Security
Microsoft’s MFA system aims to strengthen account protection by requiring multiple verification factors. These typically include passwords combined with one-time passwords (OTP) or app confirmations. Despite its intended robustness, recent research has shown that even MFA can fall short when attackers exploit gaps in its design.
How Researchers Bypassed Microsoft’s MFA
Microsoft accounts, including Outlook, OneDrive, Teams, and Azure Cloud, lacked proper rate-limiting mechanisms. This allowed attackers to guess authenticator app codes without restriction, significantly increasing the risk of account compromise. Additionally, no user notifications or alerts were provided during these suspicious activities, leaving users unaware of potential threats to their accounts.
A team from Oasis Security, led by Elad Luz and Tal Hason, uncovered a method to bypass Microsoft MFA. Here’s how they did it:
- Brute-Forcing OTP Codes Attackers tested thousands of OTP combinations. Surprisingly, no effective system blocked their attempts after multiple failures.
- No Attempt Restrictions Without strict limits on login attempts, attackers freely guessed OTPs, drastically increasing the risk of compromise.
- Exploiting MFA Apps Applications reliant on OTPs, such as SMS-based or third-party tools, were particularly vulnerable due to synchronization delays. This time gap provided attackers with critical windows to test codes.
For more details, you can consult the full report published by Oasis Security here: Oasis Security Research Team Discovers Microsoft Azure MFA Bypass.
AuthQuake Timeline: From Discovery to Resolution
June 2024: Researchers at Oasis Security discover the “AuthQuake” vulnerability in Microsoft’s MFA system.
Late June 2024: Oasis Security informs Microsoft of the vulnerability, enabling the company to begin mitigation efforts.
July 2024: Microsoft deploys temporary fixes to address immediate threats, including enhanced monitoring.
October 9, 2024: Microsoft releases a permanent fix, introducing stricter rate-limiting and account lockout mechanisms to mitigate brute-force attacks.
AuthQuake vs. Other MFA Vulnerabilities: A Comparative Analysis
The “Microsoft MFA Flaw Exposed” serves as a wake-up call for organizations relying heavily on multi-factor authentication systems. This comparison highlights why this issue is one of the most impactful security breaches in recent years.
Ironically, Microsoft has been a strong advocate for MFA, claiming it makes accounts 99% less likely to be hijacked. However, this vulnerability highlights a glaring contradiction in its security promise. Millions of Office 365 accounts were left exposed due to a critical flaw in implementation, impacting sensitive business and personal data stored on Microsoft’s widely used platforms.
The “AuthQuake” vulnerability is not the first incident exposing flaws in MFA systems. Other notable examples include:
- Okta MFA Attack (2022): Cybercriminals exploited weak session management to bypass MFA and gain unauthorized access to corporate accounts.
- Google MFA Exploit (2021): Attackers leveraged phishing campaigns combined with OTP interception to compromise accounts.
These incidents highlight the need for continuous improvements in MFA systems and underline the importance of transitioning to hardware-based or advanced cryptographic solutions for enhanced security.
Microsoft’s Response and Mitigation Measures
Microsoft’s implementation of multifactor authentication had a critical oversight that left millions of accounts vulnerable. The lack of rate-limiting mechanisms across services such as Outlook, OneDrive, Teams, and Azure Cloud, combined with the absence of user notifications during suspicious activities, highlights significant gaps in their approach to security. While Microsoft has introduced stricter measures, this issue serves as a reminder of the importance of robust and proactive security frameworks.
After being informed by Oasis Security in June 2024, Microsoft implemented a temporary fix within days and released a permanent solution on October 9, 2024. The update introduced stricter rate-limiting mechanisms to prevent brute-force attacks on Time-based One-Time Passwords (TOTPs). These measures include:
- Temporary account lockouts after multiple failed login attempts.
- Enhanced monitoring and logging of suspicious login activities.
For more details, you can refer to Microsoft’s official statement here: [Insert official Microsoft link].
Currently, there is no specific Common Vulnerabilities and Exposures (CVE) identifier associated with this vulnerability.
Users and administrators are advised to:
- Keep systems updated with the latest security patches.
- Follow best practices for account security, such as enforcing strong password policies.
- Monitor for unusual login attempts.
How PassCypher NFC HSM Prevents AuthQuake-like Vulnerabilities
Advanced solutions, such as PassCypher NFC HSM offer robust protection against vulnerabilities like AuthQuake by combining multiple security features into a single, hardware-based device. Here’s why it stands out:
- Built-in OTP Manager (TOTP and HOTP) PassCypher NFC HSM integrates an OTP manager, providing a secure way to generate and manage time-based and event-based one-time passwords.
- Material Password Manager It stores and manages passwords securely, ensuring that sensitive information remains protected.
- Contactless Functionality Its NFC capabilities allow for quick, contactless access, reducing the risk of interception during login processes.
Use Case Demonstration: Watch how PassCypher NFC HSM enhances security in this video: 🔒 PassCypher NFC HSM | Auto-Login, Contactless Access, & 2FA Security Demo.
These features not only address vulnerabilities like AuthQuake but also provide a comprehensive solution for secure communication and authentication in both personal and professional environments.
Proactive Data Protection with DataShielder Solutions
In the wake of the Microsoft MFA Flaw Exposed, organizations must prioritize encryption tools like DataShielder NFC HSM and DataShielder HSM PGP. These solutions safeguard sensitive data even if authentication systems are compromised, underscoring the need for proactive measures against such flaws.
- Ensuring Always-On Encryption These solutions keep data encrypted at all times, mitigating the risks of zero-day vulnerabilities or system corruption.
- Local Key Management Encryption keys are securely stored locally, preventing remote access or tampering.
- Adapting to Industry Needs DataShielder products are designed to meet the security requirements of industries such as finance, healthcare, and government, where data integrity is critical.
By adopting DataShielder solutions, organizations can reinforce their cybersecurity posture and protect their most valuable assets.
Encryption is a vital layer of defense that ensures sensitive data remains inaccessible even in the event of a breach. Tools like DataShielder NFC HSM and DataShielder HSM PGP provide proactive data protection by:
- Ensuring Always-On Encryption These solutions keep data encrypted at all times, mitigating the risks of zero-day vulnerabilities or system corruption.
- Local Key Management Encryption keys are securely stored locally, preventing remote access or tampering.
- Adapting to Industry Needs DataShielder products are designed to meet the security requirements of industries such as finance, healthcare, and government, where data integrity is critical.
By adopting DataShielder solutions, organizations can reinforce their cybersecurity posture and protect their most valuable assets.
Data Breaches
Unauthorized access exposes sensitive information, including financial data, strategic documents, and personal communications.
Fraudulent Activities
Compromised accounts can lead to fraud, identity theft, and even financial losses through unauthorized transactions.
Damaged Reputation
For businesses, such incidents erode customer trust and may result in fines or regulatory penalties like GDPR violations.
Recommendations for Critical Sectors
Certain sectors, such as government, finance, and healthcare, face heightened risks from MFA vulnerabilities due to the sensitive nature of their data. Recommendations include:
- Government Agencies: Implement hardware-based MFA like PassCypher NFC HSM to safeguard classified information and critical infrastructure.
- Financial Institutions: Use advanced encryption tools like PassCypher HSM PGP to protect transactional data and customer records.
- Healthcare Providers: Strengthen patient data security with multi-layered authentication methods and frequent security audits.
By tailoring solutions to sector-specific needs, organizations can significantly reduce their exposure to cyber threats.
Recommended Steps for Improved Security
Enforce Attempt Limits
Implement strict restrictions on the number of allowed login attempts to deter brute-force attacks.
Encrypt Sensitive Data
Ensure sensitive data remains encrypted at all times using advanced tools like DataShielder NFC HSM or DataShielder HSM PGP. These solutions safeguard data proactively, ensuring that even in the event of a breach or corruption, the encrypted information remains inaccessible to attackers.
Adopt Hardware-Based MFA
Secure your systems using products like PassCypher NFC HSM, which integrates OTP management (TOTP and HOTP) for robust, hardware-based protection.
Use Advanced Encryption Solutions
Tools such as PassCypher HSM PGP offer enhanced identity management and data protection, further minimizing risks from compromised MFA systems.
Conduct Frequent Security Audits
Regularly assess your systems to identify and address vulnerabilities before attackers exploit them.
Educate Users
Teach users to detect suspicious activities and respond quickly to potential account compromises.
Taking Action for a Safer Future
The revelation of the Microsoft MFA Flaw Exposed served as a critical reminder in 2024, and its lessons remain pertinent in 2025. Therefore, adopting a multi-faceted security approach is essential. This includes implementing hardware-based MFA solutions like PassCypher NFC HSM to fortify authentication processes and deploying robust encryption tools such as DataShielder to safeguard data at rest and in transit. Ultimately, by staying informed about evolving threats and embracing proactive security measures, individuals and organizations can build a more resilient digital environment for the future.
Understanding why encrypt SMS is crucial in today’s cybersecurity landscape by Jacques Gascuel – This post in the Digital Security section highlights a cybersecurity wake-up call, addressing the growing cyber threats to government agencies and presenting solutions for secure communication. Updates will be provided as new information becomes available. Feel free to share your comments or suggestions.
Understanding why encrypt SMS is crucial in today’s cybersecurity landscape by Jacques Gascuel – This post in the Digital Security section highlights a cybersecurity wake-up call, addressing the growing cyber threats to government agencies and presenting solutions for secure communication. Updates will be provided as new information becomes available. Feel free to share your comments or suggestions.
Summary: Why Encrypt SMS Is Essential for Cybersecurity
The recent cyberattacks orchestrated by Salt Typhoon emphasize the vulnerabilities in telecom infrastructure, exposing sensitive government communications. This article explores these risks, highlights advanced threats targeting global telecom networks, and presents DataShielder NFC HSM Defense as a sovereign solution for regalian institutions.
Explore More Digital Security Insights
→ Discover related articles on cybersecurity threats, advanced solutions, and strategies to protect sensitive communications and critical systems.
Why Encrypt SMS? Understanding the Critical Flaws in MMS, and RCS Protocols
In 2024, telecom network vulnerabilities have become a major threat to both governmental and commercial communications. These weaknesses in protocols such as SS7 and Diameter highlight the urgency of addressing telecom vulnerabilities this year with robust encryption measures.
While SMS, MMS, and RCS remain widely used, their reliance on outdated and vulnerable protocols makes them prime targets for exploitation. The FBI and CISA identified the following key risks:
- Interception of Messages: Unencrypted SMS and MMS are transmitted in plaintext, making interception relatively easy for cybercriminals.
- SIM Swapping Attacks: Threat actors take control of victims’ phone numbers, granting them access to sensitive accounts secured by SMS-based two-factor authentication (2FA).
- Telecom Infrastructure Exploits: Weaknesses in protocols such as SS7, Diameter, and RCS allow adversaries to compromise entire networks, intercepting metadata, call records, and live communication streams.
IMSI Catchers: A Hidden Threat
IMSI catchers, also known as Stingrays, exploit weaknesses in telecom infrastructure to intercept unencrypted SMS and voice communications. Both Salt Typhoon and Flax Typhoon have used such methods to target sensitive government and corporate data. These attacks underscore why SMS encryption is no longer optional but a critical measure for safeguarding sensitive information.
Related Threats Protocols
Protocols like SS7, originally designed in the 1970s for 2G and 3G networks, were never built with modern security standards in mind. Vulnerabilities in SS7 and related protocols, including Diameter (4G/5G) and SIP (VoIP), further exacerbate the risks of telecom-based attacks.
📑 Explore SS7 vulnerabilities in detail:
- CISA 2025 Guidance: Why Encrypt SMS for Mobile Communication Security
- Why Encrypt SMS: A Crucial Step for Mobile Communication Security
- Summary: Why Encrypt SMS Is Essential for Cybersecurity
- Why Encrypt SMS? Understanding the Critical Flaws in MMS and RCS Protocols
- IMSI Catchers: A Hidden Threat
- Related Threats Protocols
- Salt Typhoon: The Scope of Cyberespionage
- Salt Typhoon: A Case Study in Telecom Exploitation
- Global Implications
- International Cooperation to Combat Telecom Threats
- Regulatory Responses to Salt Typhoon: FCC’s Call to Action
- Practical Steps to Secure Communication: Why Encrypt SMS Matters
- Why Secure Messaging Platforms Are Critical for Government Enterprises Under CISA Guidance
- Expanding Beyond SMS: Aligning with CISA for Universal Communication Encryption
- Why Choose DataShielder?
- Proactive Cybersecurity for Regalian Institutions
- A Sovereign Solution: DataShielder NFC HSM Defense
- Expanding Encryption: Universal Communication Protection
- How CISA Cybersecurity Guidance Supports Secure Messaging Platforms
- Best Tools for SMS Encryption in Government
- Related Threats Protocols
- Proactive Cybersecurity for Regalian Institutions
- Explore Official Reports and Recommendations
- DataShielder NFC HSM and HSM PGP: A Comprehensive Product Line for Strategic and Corporate Needs
- Dual Civilian and Military Applications
- Comparison Table: DataShielder NFC HSM Product Line
- CISA Cybersecurity Guidance for Mobile Communication Security
CISA 2025 Guidance: Importance of SMS Encryption
On December 3, 2024, the FBI and CISA, joined by global cybersecurity agencies, issued a stark warning about the vulnerabilities of unencrypted SMS, MMS, and RCS communications. Highlighting exploits by state-sponsored groups like Salt Typhoon, a Chinese cyberespionage campaign, the alert underscores the urgent need for end-to-end encryption to strengthen mobile communication security and protect sensitive government and institutional data. This alert emphasizes why encrypting SMS is no longer just a precaution but an essential strategy for safeguarding communications in a rapidly evolving cybersecurity landscape.
In this context, solutions such as DataShielder NFC HSM Defense are designed to offer sovereign-grade protection against the growing threats targeting mobile networks. With encryption methods tailored to protect both governmental and institutional communications, adopting these technologies is a crucial step in maintaining the confidentiality and integrity of sensitive data.
Updated CISA 2025 Guidance & Implications
The Cybersecurity and Infrastructure Security Agency (CISA) has updated its recommendations on mobile communication security in the November 2025 edition of the “Mobile Communications Best Practice Guidance.” Some key updates include:
- Strengthening the importance of E2EE (End-to-End Encryption) for all forms of messaging, including SMS, MMS, and RCS.
- Advising against the use of SMS for OTPs and 2FA due to ongoing exploitation risks.
- Advanced security practices for iOS and Android, such as enabling encrypted DNS, Lockdown Mode, and reviewing mobile app permissions.
These updated recommendations further emphasize the need for end-to-end encryption (E2EE) and sovereign-grade solutions like DataShielder NFC HSM, which provide robust protection against these emerging threats.
2026 Authentication Evolution: MFA Without SMS and Hardware Solutions
In line with this evolution, authorities now recommend phishing-resistant MFA solutions, excluding SMS and OTP via SMS as authentication mechanisms. This shift aligns with a broader trend towards more secure methods, such as FIDO2 and hardware keys, which offer enhanced resistance to phishing attacks and other cyber threats. Solutions like PassCypher HSM PGP and PassCypher NFC HSM stand out in this domain by offering robust, password-free authentication, completely offline and serverless. These tools are the ideal alternative to traditional MFA solutions based on SMS or OTP codes, which have been increasingly recognized as vulnerable.
Why Encrypt SMS: A Crucial Step in Mobile Communication Security
As noted by the FBI and CISA in their 2024 warning, unencrypted SMS, MMS, and RCS communications pose a significant risk, highlighting the necessity of encryption in securing mobile communications. The need to protect sensitive government and institutional communications from cyberespionage, especially by state-sponsored groups like Salt Typhoon, has made encryption an essential strategy rather than an option.
Understanding how telecom protocols, such as SS7 and Diameter, can be exploited by cybercriminals and state-sponsored actors is crucial for mitigating these risks. With sovereign-grade encryption solutions like DataShielder, organizations can protect sensitive communications and critical infrastructure globally, ensuring their integrity and confidentiality.
Unencrypted SMS, MMS, and RCS leave crucial gaps in mobile communication security. These gaps can be exploited to intercept and steal sensitive data. By adopting encryption methods, organizations can mitigate such risks, safeguarding against cybercriminals and other malicious actors. This makes encrypting SMS a critical element of any security strategy, ensuring data confidentiality and protecting sensitive information from interception.
📍 Learn from official sources:
Read the full article to understand the risks and the solutions that can help secure your communications. Share your thoughts and take action to protect your systems.
Updated CISA 2025 Guidance & Implications
La Cybersecurity and Infrastructure Security Agency (CISA) a mis à jour ses recommandations sur la sécurité des communications mobiles dans la version de novembre 2025 du “Mobile Communications Best Practice Guidance”. Parmi les évolutions importantes :
- Renforcement de l’importance de l’E2EE (chiffrement de bout en bout) pour toutes les formes de messagerie, incluant SMS, MMS, et RCS.
- Déconseil de l’utilisation de SMS pour les OTP et 2FA en raison des risques d’exploitation persistants.
- Pratiques de sécurité avancées pour iOS et Android, telles que l’activation du DNS chiffré, Lockdown Mode, et la révision des permissions pour les applications mobiles.
Ces nouvelles recommandations renforcent l’argument en faveur du chiffrement de bout en bout (E2EE) et des solutions souveraines comme DataShielder NFC HSM, qui offrent une protection robuste contre ces menaces.
Spyware Risks on E2EE Platforms
Emerging threats now include the use of commercial spyware targeting encrypted messaging apps like Signal and WhatsApp. Cybercriminals exploit QR codes, linked devices, and other vectors to bypass encryption protections, highlighting the need for an additional layer of hardware-based security.
Solutions like PassCypher NFC HSM and DataShielder NFC HSM provide enhanced protection against these attacks by incorporating physical security mechanisms to ensure the integrity of exchanged data. These hardware-based solutions offer critical safeguards, making them indispensable in the battle against evolving cybersecurity threats.
CISA Cybersecurity Guidance: Why Encrypt SMS for Mobile Communication Security?
On December 3, 2024, the FBI and CISA, joined by global cybersecurity agencies, issued a stark warning about the vulnerabilities of unencrypted SMS, MMS, and RCS communications. Highlighting exploits by state-sponsored groups like Salt Typhoon, a Chinese cyberespionage campaign, the alert underscores the urgent need for end-to-end encryption to strengthen mobile communication security and protect sensitive government and institutional data. Understanding why encrypt SMS is essential helps organizations mitigate risks and enhance communication security. Learn how solutions like DataShielder NFC HSM Defense offer sovereign-grade security against these growing threats.
Why Encrypt SMS: A Crucial Step for Mobile Communication Security
On December 3, 2024, the FBI and CISA, joined by global cybersecurity agencies, issued a stark warning about the vulnerabilities of unencrypted SMS, MMS, and RCS communications. This highlights why encrypt SMS is no longer optional but a necessity for securing mobile communications. Highlighting cyberespionage by state-sponsored groups like Salt Typhoon, the alert underscores the necessity for encryption to protect sensitive government and institutional communications.
Discover how vulnerabilities in telecom protocols, from SS7 to Diameter, are exploited, and explore sovereign-grade encryption with DataShielder, solution designed to secure sensitive communications and critical infrastructure globally.
Unencrypted SMS, MMS, and RCS leave critical gaps in mobile communication security. This demonstrates why encrypt SMS is crucial for protecting sensitive data from interception and exploitation. Cybercriminals and state-sponsored actors can exploit these vulnerabilities to intercept sensitive information. By adopting encrypted communication methods, organizations can mitigate these risks, ensuring data integrity and confidentiality.
📍 Learn from official sources:
Read the full article to understand the risks and solutions. Share your thoughts and secure your communications.
Summary: Why Encrypt SMS Is Essential for Cybersecurity
The recent cyberattacks orchestrated by Salt Typhoon emphasize the vulnerabilities in telecom infrastructure, exposing sensitive government communications. This article explores these risks, highlights advanced threats targeting global telecom networks, and presents DataShielder NFC HSM Defense as a sovereign solution for regalian institutions.
Explore More Digital Security Insights
→ Discover related articles on cybersecurity threats, advanced solutions, and strategies to protect sensitive communications and critical systems.
Salt Typhoon: The Scope of Cyberespionage
Salt Typhoon’s impact on global telecom networks highlights the importance of securing sensitive data with sovereign-grade encryption solutions. The Salt Typhoon campaign demonstrates the global impact of cyberattacks on telecom networks. By targeting operators in the U.S., Europe, and other strategic regions, Salt Typhoon underscores the critical need for sovereign security solutions to protect sensitive communications worldwide.
State-Sponsored Cyber Attacks
Salt Typhoon, a Chinese state-affiliated group, exemplifies the modern-day cyberespionage threat. This group bypasses traditional endpoint security measures by directly targeting telecom infrastructure. Their tactics include:
- Exploiting Zero-Day Vulnerabilities: Leveraging unpatched software flaws in telecom systems to gain unauthorized access.
- Misconfiguration Exploits: Exploiting poorly configured core network components, enabling large-scale data extraction.
- Intercepting Call Detail Records (CDRs): Accessing metadata, live call data, and surveillance logs.
Salt Typhoon’s activities have compromised sensitive data involving high-ranking officials, security agencies, and critical businesses. The breach extends beyond the U.S., affecting telecom operators in France (SFR), Spain (Telefónica), and other global entities.
Global Implications
The breach highlights the structural vulnerabilities of international telecom networks. The PRC uses these intrusions to:
- Gather Strategic Intelligence: Inform military and economic policies.
- Undermine U.S. and Allied Credibility: Compromise allied infrastructure, including NATO and Five Eyes.
- Proliferate Cyber Tactics: Inspire other state-sponsored actors to replicate similar attacks.
These vulnerabilities underline the urgent need for coordinated international efforts to mitigate risks and safeguard sensitive communications.
International Cooperation to Combat Telecom Threats
The response to Salt Typhoon underscores the importance of global cooperation. Agencies from the Five Eyes alliance (USA, UK, Canada, Australia, and New Zealand) and European counterparts are actively working together to mitigate risks, share intelligence, and strengthen cybersecurity defenses globally.
Regulatory Responses to Salt Typhoon: FCC’s Call to Action
The Federal Communications Commission (FCC) has taken decisive steps to strengthen the resilience of telecommunications infrastructure following the Salt Typhoon cyberattack. This attack, confirmed on December 4, 2024, compromised sensitive systems in at least eight U.S. telecom companies and exposed vulnerabilities in critical infrastructure.
Key FCC Measures:
- Cybersecurity Obligations:
- Telecommunications carriers must comply with Section 105 of the Communications Assistance for Law Enforcement Act (CALEA) to secure their networks.
- Legal obligations extend beyond equipment to include network management practices.
- Compliance Framework:
- Annual certification for cybersecurity risk management plans.
- Expanded obligations for all communications providers to implement robust security measures.
- National Security Focus:
- Recognizing the critical role of telecom networks in defense, public safety, and economic systems, the FCC’s actions aim to build resilience against future cyberattacks.
📍 Read the FCC Fact Sheet for more details:
Salt Typhoon: A Case Study in Telecom Exploitation
The Salt Typhoon attack is a stark reminder of how state-sponsored actors bypass traditional security measures to target telecom infrastructure directly. Operating under the guise of Earth Estries—a Chinese cyberespionage group—their tactics reveal a sophisticated approach to large-scale data theft and network manipulation.
Salt Typhoon Tactics and Techniques:
- Zero-Day Exploits:
- Unpatched vulnerabilities in core telecom systems.
- Misconfigurations:
- Exploiting poorly configured network components to gain unauthorized access.
- Interception of Call Detail Records (CDRs):
- Accessing metadata, live communications, and surveillance logs without targeting individual devices.
Global Implications of Salt Typhoon Attacks:
Salt Typhoon has impacted major telecom operators globally, including:
- U.S. carriers (AT&T, Verizon, T-Mobile).
- European providers like SFR (France) and Telefónica (Spain).
Telecom protocols like SS7 and Diameter, though foundational to mobile communication, are plagued by vulnerabilities that open the door to cyber espionage. We will discuss by following how these weaknesses are exploited and why it is essential to address them.
Protocol Vulnerabilities: A Gateway for Cyber Espionage
While Salt Typhoon focuses on telecom infrastructure, vulnerabilities in SS7, Diameter, and related protocols serve as entry points for cyber adversaries.
Understanding the risks associated with outdated and vulnerable telecom protocols like SS7, Diameter, and RCS is essential for safeguarding mobile communication infrastructure.
Key Protocol Risks
- SS7 (Signaling System 7):
- Designed for 2G/3G networks, SS7 was never intended for secure communication, making it vulnerable to message interception and location tracking.
- Diameter Protocol:
- Used in 4G/5G networks, Diameter faces similar risks, including denial-of-service attacks and message tampering.
- RCS (Rich Communication Services):
- A modern SMS replacement, RCS still lacks robust encryption, leaving it open to interception and spoofing.
📑 Learn more about SS7 vulnerabilities:
IMSI catchers, or Stingrays, pose a critical threat by intercepting mobile communications through deception. Learn how these devices are leveraged by cyber adversaries to compromise sensitive data.
IMSI Catchers: A Gateway for Mobile Communication Interception
IMSI catchers, also known as Stingrays, are devices used to intercept mobile communications by mimicking legitimate cell towers. These tools are commonly employed by state-sponsored actors, such as Salt Typhoon and Flax Typhoon, to capture sensitive data, including SMS, calls, and metadata.
To learn more about IMSI catchers and their impact on mobile communication security, consult this detailed explanation provided by the Electronic Frontier Foundation (EFF).
Practical Steps to Secure Communication: Why Encrypt SMS Matters
One of the first steps to achieve this is to understand why encrypt SMS is a priority in cybersecurity strategies. Here’s how organizations and individuals can enhance their security posture, particularly around telecom network vulnerabilities in 2024 and the risks associated with unencrypted messaging:
- Adopt Encrypted Messaging Platforms
Leverage secure apps like Signal or Telegram, which provide end-to-end encryption to ensure the confidentiality of your communications. - Implement Secure Hardware Solutions
Utilize hardware-based tools such as the DataShielder NFC HSM Defense for sovereign-grade encryption. These solutions are specifically designed to protect against threats like Salt Typhoon and ensure data integrity. - Conduct Regular Audits
Evaluate and update telecom protocols such as SS7 and Diameter to address potential vulnerabilities. Auditing ensures that your systems stay ahead of evolving cyber risks. - Leverage International Guidelines
Follow frameworks and recommendations from global cybersecurity organizations, including CISA and FCC, to strengthen your defenses. These guidelines provide actionable steps to safeguard your communication infrastructure. - Use Multi-Factor Authentication (MFA)
Combine encrypted platforms with MFA to add an extra layer of security, mitigating the risks of SIM-swapping attacks and unauthorized access. - Train Employees on Cybersecurity Awareness
Educate staff on recognizing phishing attempts and other cyber threats. Awareness is a crucial defense against insider and external threats. - Perform Penetration Testing
Conduct regular penetration tests to uncover weaknesses in your telecom infrastructure. This proactive approach ensures that vulnerabilities are identified and resolved before they are exploited.
The answer is clear: unencrypted SMS, MMS, and RCS leave organizations exposed to interception and exploitation. Tools like DataShielder NFC HSM Defense and secure practices such as those outlined above provide critical safeguards against global telecom threats and state-sponsored cyberattacks.
Why Encrypt SMS Best Tools for SMS Encryption in Government
Securing SMS communications for government institutions and enterprises is no longer optional—it is essential to safeguard sensitive exchanges. Why encrypt SMS? Unencrypted messages remain vulnerable to interception and cyberattacks, making encryption a critical component of modern cybersecurity strategies. Among the top solutions available is the DataShielder NFC HSM Defense, tailored to meet the highest standards for sovereign entities and highly sensitive government communications:
- Hybrid Encryption (AES-256 CBC): Ensures all data is encrypted locally before transmission.
- Cross-Platform Compatibility: Works seamlessly with Android NFC devices, ensuring secure communication across various platforms.
- Offline Functionality: Eliminates the risk of internet-based vulnerabilities, providing unmatched security.
Why Encrypt SMS to Prevent Data Breaches?
Why encrypt SMS? Enterprises classified as ultra-sensitive or of national interest must protect their communications to prevent data breaches and safeguard operational security. Freemindtronic offers the DataShielder NFC HSM Master, a double-use version specifically designed to meet these rigorous demands:
- DataShielder NFC HSM Master: Balances enterprise flexibility with sovereign-grade encryption, making it ideal for strategic organizations working closely with government entities. This solution ensures data confidentiality, integrity, and accessibility.
Encryption Solutions for All Enterprises
For other businesses seeking advanced yet versatile encryption solutions, the DataShielder NFC HSM Lite and its complementary modules offer powerful data protection in a double-use capacity. These versions ensure comprehensive security without compromising accessibility:
- DataShielder NFC HSM Lite: Designed for enterprises needing reliable encryption for communication and data protection.
- DataShielder NFC HSM Auth: Provides authentication alongside encryption for streamlined security management.
- DataShielder NFC HSM M-Auth: Facilitates multi-authentication scenarios, ensuring secure access across distributed teams.
For businesses that require desktop-based encryption compatible with NFC HSM modules, Freemindtronic also offers the DataShielder PGP HSM Data Encryption. This solution extends protection to computers, ensuring comprehensive data security.
Regalian Security Through Sovereign Solutions
To address these vulnerabilities, DataShielder NFC HSM Defense offers a sovereign-grade encryption tool for regalian institutions, government agencies, and enterprises.
How DataShielder NFC HSM Defense Protects Communications:
Hybrid Encryption (AES-256 CBC):
- Encrypts data locally before transmission, ensuring total protection.
Cross-Platform Compatibility:
- Works with all Android NFC devices (version 6+), including:
- Fairphone (Netherlands).
- Shiftphone (Germany).
- Sonim Technologies (USA).
- Crosscall (France).
- Bullitt Group (UK).
Future-Ready Encryption:
- Secures current and emerging communication platforms, including SMS, MMS, RCS, and satellite messaging.
Sovereign Manufacturing
Built in France (Syselec) and Andorra (Freemindtronic SL), DataShielder is developed using STMicroelectronics components to meet the highest security standards.
Expanding Beyond SMS: Aligning with CISA for Universal Communication Encryption
The sovereign-grade encryption with DataShielder secures more than just SMS. It acts as a comprehensive encryption tool for:
- MMS, RCS, and Email: Encrypts messages and attachments.
- Instant Messaging: Secures full platforms like Signal, Telegram, WhatsApp, LinkedIn…
- File Transfers: Encrypts sensitive documents prior to sharing.
- Satellite Messaging: Extends protection to off-grid communication.
By encrypting data at the source, DataShielder ensures that even intercepted messages are unreadable to adversaries.
Why Choose DataShielder?
By incorporating solutions like DataShielder NFC HSM Defense, government entities, strategic enterprises, and businesses of all sizes can mitigate risks associated with unencrypted communications. Whether addressing Why encrypt SMS? or securing data across platforms, DataShielder offers scalable and tailored solutions to meet diverse security needs.
- Complete Offline Operation: Functions without internet, eliminating server-based vulnerabilities.
- Segmented Key Authentication: Patented technology ensures unmatched encryption trust.
- Proven Sovereignty: Designed and manufactured in Europe using defense-grade components.
Proactive Cybersecurity for Regalian Institutions
The Salt Typhoon cyberattack and its associated vulnerabilities underscore the urgent need for robust, proactive measures to safeguard critical communications in the regalian sector. In December 2024, the Cybersecurity and Infrastructure Security Agency (CISA) published its Mobile Communications Best Practices Guidance to address these pressing challenges. These recommendations align seamlessly with the core principles of secure communication solutions like DataShielder NFC HSM Defense, designed to meet the highest standards for protecting sensitive government and enterprise communications.
Key Highlights from CISA’s Guidance
- Adopt End-to-End Encryption: Transition to secure messaging platforms like Signal to ensure all communications remain private and protected.
- Phishing-Resistant Authentication: Replace SMS-based MFA with FIDO security keys for maximum resilience against cyberattacks.
- Platform-Specific Recommendations:
- iPhone: Enable Lockdown Mode and utilize encrypted DNS services like Cloudflare’s 1.1.1.1 Resolver.
- Android: Prioritize devices with secure hardware features and enable Private DNS for enhanced protection.
By adopting solutions that align with the CISA Cybersecurity Guidance, such as DataShielder NFC HSM Defense, organizations can enhance their mobile communication security while mitigating the growing threats identified by global cybersecurity agencies, including the FBI and CISA.
These best practices not only emphasize the importance of secure communications but also highlight the critical need for solutions that integrate these principles effectively, such as DataShielder NFC HSM Defense.
Why Secure Messaging Platforms Are Critical for Government Enterprises Under CISA Guidance
- End-to-End Encryption: The CISA guidance emphasizes the need for encrypted messaging platforms to secure sensitive communications—an area where DataShielder NFC HSM Defense excels with its AES-256 encryption.
- Phishing-Resistant Authentication: Transitioning away from SMS-based MFA aligns with the Zero Trust framework of DataShielder, which ensures offline security and eliminates internet-based vulnerabilities.
- Platform Compatibility: DataShielder’s seamless integration with Android NFC devices addresses the secure hardware requirements outlined in the CISA guidance, ensuring protection across modern communication platforms.
Building on the importance of secure messaging platforms, the recent CISA Cybersecurity Guidance highlights actionable recommendations to strengthen mobile communication security. Here’s how DataShielder NFC HSM Defense aligns with these guidelines:
How CISA Cybersecurity Guidance Supports Secure Messaging Platforms
The newly released CISA Cybersecurity Guidance for Mobile Communication Security emphasizes the importance of robust measures such as end-to-end encryption, phishing-resistant MFA, and platform-specific security features to combat evolving cyber threats. These recommendations align seamlessly with DataShielder NFC HSM Defense, which provides sovereign-grade security tailored to meet these exact needs. Here’s how:
| CISA Recommendation | How DataShielder NFC HSM Defense Aligns |
|---|---|
| End-to-End Encryption | Implements AES-256 CBC encryption to secure sensitive communications locally before transmission. |
| Phishing-Resistant MFA | Integrates Zero Trust architecture, replacing vulnerable SMS-based MFA with secure offline authentication. |
| Offline Functionality | Operates entirely offline, eliminating internet-based vulnerabilities. |
| Platform-Specific Compatibility | Fully compatible with Android NFC devices and supports encrypted DNS, meeting CISA’s security criteria. |
| Sovereign Manufacturing | Designed and manufactured in Europe with STMicroelectronics components for ultimate trust and reliability. |
By choosing DataShielder NFC HSM Defense, organizations gain a cutting-edge solution aligned with the best practices outlined by CISA.
Explore Official Reports and Recommendations
CISA Guidance: Practical Solutions for Today’s Threats
📤 Download the full CISA Mobile Communications Best Practices Guidance (PDF)
Explore how these recommendations align with sovereign-grade security solutions like DataShielder NFC HSM Defense, providing unmatched protection for critical communications.
- CISA Mobile Communications Best Practices Guidance
- FBI-CISA Joint Statement on PRC Cyberespionage
- CISA Enhanced Visibility and Hardening Guidance
- FCC Fact Sheet on Salt Typhoon
- Salt Typhoon Cyber Threats
- 5Ghoul: 5G Vulnerabilities
DataShielder NFC HSM and HSM PGP: A Comprehensive Product Line for Strategic and Corporate Needs
In an era where robust security is paramount, the DataShielder NFC HSM and HSM PGP product line offers versatile solutions tailored for a range of applications—from civilian to military, and enterprise to sovereign institutions. Explore how these innovative tools provide unmatched protection for sensitive data and communications.
Product Highlights
- DataShielder NFC HSM Master
A flagship product designed for the most demanding security requirements. Perfect for:- Sovereign institutions: Encrypting highly sensitive data.
- Strategic enterprises: Securing internal communications.
📍 Key Features:
- Hybrid encryption with AES-256 CBC.
- Advanced key management with Android NFC compatibility.
- Fully offline functionality to eliminate internet vulnerabilities.
➡️ Learn more
- DataShielder NFC HSM Lite
A lightweight yet powerful solution for businesses requiring accessible yet robust security.
📍 Ideal for:- SMEs and startups seeking cost-effective security.
- Sectors requiring localized control over sensitive data.
➡️ Discover the details
- DataShielder NFC HSM Auth and M-Auth
- NFC HSM Auth: Tailored for secure authentication and basic encryption.
- NFC HSM M-Auth: Advanced multi-authentication, ideal for:
- Decentralized teams.
- Segmented access with fine-tuned permission management.
- Dynamic AES-256 CBC key replacement via RSA 4096 encrypted key sharing.
➡️ Explore NFC HSM Auth
➡️ Explore NFC HSM M-Auth
- DataShielder NFC HSM Defense
📍 Exclusive Features:- Externalized contact management via NFC HSM: Make calls or send SMS, MMS, and RCS messages directly from the NFC HSM.
- Automatic deletion of call history and messages from the phone after use.
📍 Target Audience:
- Defense, government institutions, and industries requiring unmatched security for communications and data.
➡️ Learn more
- DataShielder Starter Kit
An all-in-one solution to introduce enterprises to the DataShielder ecosystem.
📍 Includes:- NFC HSM Lite for a seamless start.
- Comprehensive user guide and support.
➡️ View the Starter Kit
- DataShielder HSM PGP Data Encryption
Designed for dual civilian and military use, offering robust encryption for:- Multinational enterprises: Protecting sensitive data during cross-border exchanges.
- Military applications: Securing strategic communications.
➡️ Discover HSM PGP
Dual Civilian and Military Applications
DataShielder products are engineered to address diverse security needs:
- Civilian Use: Protecting digital assets, intellectual property, and sensitive communications for businesses.
- Military Use: Sovereign-grade security aligned with national and international defense standards.
Comparison Table: DataShielder NFC HSM Product Line
| Product | Usage | Key Features | Link |
|---|---|---|---|
| NFC HSM Master | Sovereign and strategic | AES-256 CBC, offline, advanced trust criteria, fleet management, NFC | Learn more |
| NFC HSM Lite | SMEs and startups | AES-256 CBC encryption, streamlined interface, essential security features | Learn more |
| NFC HSM Auth | Authentication and encryption | Identity protection + SMS, MMS, RCS encryption | Learn more |
| NFC HSM M-Auth | Multi-authentication scenarios | Dynamic AES-256 CBC key replacement via RSA 4096 encrypted key sharing | Learn more |
| NFC HSM Defense | Sovereign, defense, military | Externalized contact management, secure calls and SMS/MMS/RCS, automatic call/message log deletion | Learn more |
| Starter Kit | Cost-effective enterprise security | NFC HSM Lite + second module for key personnel | Learn more |
| HSM PGP Data Encryption | Dual-use civil/military | PGP encryption, offline operation, tailored for strategic communications | Learn more |
CISA Cybersecurity Guidance for Mobile Communication Security
The vulnerabilities in telecom networks and the global impact of cyberattacks like Salt Typhoon highlight the importance of adopting secure, sovereign-grade solutions. DataShielder NFC HSM Defense provides a trusted, scalable option for regalian institutions and strategic enterprises, offering unmatched protection in alignment with global best practices.
📍Don’t wait for vulnerabilities to be exploited. Secure your organization’s mobile communication today with DataShielder, the sovereign-grade encryption solution trusted for its alignment with CISA cybersecurity recommendations. Contact us for a personalized quote.
Secure your organization’s mobile communication today with DataShielder, the sovereign-grade encryption solution trusted for its alignment with CISA cybersecurity recommendations.
Best Practices Techniques (2025)
En complément du chiffrement de bout en bout, CISA recommande plusieurs pratiques avancées pour sécuriser les appareils mobiles :
- DNS Chiffré: Utilisation du DNS chiffré pour éviter les attaques de type Man-in-the-Middle.
- Lockdown Mode: Activation de ce mode pour restreindre l’accès aux applications et services critiques.
- Revue des Permissions: Revoir et limiter les permissions des applications pour minimiser les risques.
Ces pratiques doivent être accompagnées de solutions de chiffrement robustes comme DataShielder NFC HSM pour garantir une protection maximale.
KEESPER GEOLOCATION
Keepser Geolocation offers cutting-edge technology to secure digital assets in today’s digital age, where data security holds immense importance. With the surge in cyber threats, safeguarding sensitive information has become a top priority for individuals and businesses alike. This is where the Keepser® NFC Cold Wallet excels, offering innovative geolocation technology to protect your valuable data no matter where you are.
Understanding KEESPER Geolocation Security
Geolocation security is a location-based technology that uses a device’s real-time physical location to determine access permissions and safeguard sensitive information. While geolocation has traditionally been utilized across various applications, Keepser brings this innovative approach into the realm of advanced data security.
How Keepser Utilizes Geolocation for Data Protection
1. Customizable Safe Zones
Keepser® allows users to create custom safe zones on a map through an intuitive app. These zones might include your home, office, or any secure location where your data remains accessible.
2. Automatic Lock
When your Keepser card exits the pre-defined safe zone, it automatically locks your data. This ensures that your sensitive information stays inaccessible until you’re back in the secure location.
Summery
Keepser® integrates state-of-the-art geolocation technology to redefine security standards for digital assets. Whether you’re at work, traveling, or at home, Keepser® ensures your data is always secure, empowering you with confidence and control over your valuable information.
Stay Ahead in Data Security with Keepser®.

Av. Copríncep De Gaulle, Núm. 13,
AD700 - Escaldes-Engordany - Andorra
- Youtube
- X
- Tiktok
- Telegram-plane
Menu
Shop
Solutions
Keepser PASS
Keepser PRO Crypto
Keepser PRO+ Crypto
Individual Keepser Card
Keepser Safe Clone
Technology
Apps & Plugins
News / Blog
Contact
Support
6 Reasons Why Keepser Is the Best Solution for Your Data Storage and Cryptocurrency
ARE YOU TIRED OF WORRYING ABOUT THE SECURITY OF YOUR IMPORTANT DATA AND INFORMATION?
HAVE YOU BEEN LOOKING FOR A RELIABLE AND EFFICIENT DATA STORAGE SOLUTION THAT CAN GIVE YOU PEACE OF MIND?
6 Reasons Why Keepser Is the Best Solution for Your Data Storage and Cryptocurrency
ARE YOU TIRED OF WORRYING ABOUT THE SECURITY OF YOUR IMPORTANT DATA AND INFORMATION?
HAVE YOU BEEN LOOKING FOR A RELIABLE AND EFFICIENT DATA STORAGE SOLUTION THAT CAN GIVE YOU PEACE OF MIND?
LOOK NO FURTHER THAN KEEPSER!
HERE ARE 6 REASONS WHY KEEPSEER IS THE ULTIMATE SOLUTION FOR ALL YOUR DATA STORAGE NEEDS:
1- SECURITY 🔒
6 Reasons Why Keepser prove why it’s the ultimate solution for protecting your data. Keepser’s state-of-the-art technology actively safeguards your information against potential cyber-attacks. The Keepser Cold Wallet Card keeps your data offline and completely out of hackers’ reach.
2- LIFE ⏳
Keepser ensures your data stays safe for over 40 years. You never have to worry about the card becoming obsolete, as Keepser technology remains functional indefinitely. Furthermore, the more you use it, the longer it serves you, offering unparalleled longevity.
3- NO ACCESSORIES NEEDED 🛠️
Keepser eliminates the hassle of additional accessories. Unlike other data storage solutions, you don’t need cables or batteries. This design makes it a highly cost-effective and efficient choice for your data storage needs.
4- ECO-FRIENDLY ♻️
Keepser takes sustainability seriously. Our solution is 100% recyclable and environmentally friendly. With no reliance on batteries or plastic components, it stands as the perfect option for those committed to eco-conscious practices.
5- EASY TO USE 💼
Keepser makes portability and usability effortless. You can transport it anywhere and access it anytime. Thanks to its compact and user-friendly design, Keepser provides a hassle-free experience for your data storage needs.
6- GEOLOCATION 🌍
Keepser offers a unique geolocation feature that restricts access based on your location. This added layer of security ensures your data remains protected wherever you go.
Keepser’s Cold Wallet Card is the ultimate solution for anyone who seeks reliability, longevity, eco-friendliness, and ease of use. Don’t wait any longer—invest in Keepser today and secure your data for a lifetime.
Explore Keepser in Action 🎥
Discover the cutting-edge features and benefits of Keepser products. Watch in-depth demos, tutorials, and real-world applications on our official YouTube channel.
🎯 Stay informed, stay secure! Subscribe now to access exclusive content and updates on the Keepser Cold Wallet range.

Av. Copríncep De Gaulle, Núm. 13,
AD700 - Escaldes-Engordany - Andorra
- Youtube
- X
- Tiktok
- Telegram-plane
Menu
Shop
Solutions
Keepser PASS
Keepser PRO Crypto
Keepser PRO+ Crypto
Individual Keepser Card
Keepser Safe Clone
Technology
Apps & Plugins
News / Blog
Contact
Support
Phone Hack of French Minister Jean-Noël Barrot: A Cybersecurity Wake-Up Call
The phone hack of French Minister Jean-Noël Barrot during the G7 summit in November 2024 in Italy highlights critical vulnerabilities in high-level government communications. This sophisticated attack underscores the escalating cyber threats targeting global leaders. In this article, we examine the circumstances surrounding this breach, its profound implications for national security, and innovative solutions, such as DataShielder NFC HSM Defense, to effectively prevent such attacks in the future.
The G7 Summit and Its Strategic Importance
On November 24, 2024, Jean-Noël Barrot, the French Minister for Europe and Foreign Affairs, attended a bilateral meeting in Rome with his Italian counterpart, Antonio Tajani. This meeting laid the groundwork for discussions at the G7 Summit, held on November 25–26, 2024, in Fiuggi, near Rome.
The summit brought together foreign ministers from G7 nations to address critical global issues, including:
The war in Ukraine, with a focus on international coordination and humanitarian efforts.
Rising tensions in the Middle East, particularly the impact of regional conflicts on global stability.
Cybersecurity and disinformation, emerging as key topics amidst escalating cyber threats targeting governments and public institutions.
This context underscores the sensitivity of the discussions and the importance of secure communication channels, especially for high-level officials like Minister Barrot.
Explore More Digital Security Insights
🔽 Discover related articles on cybersecurity threats, advanced solutions, and strategies to protect sensitive communications and critical systems.
Quick Navigation
- The G7 Summit and Its Strategic Importance
- How the French Minister Phone Hack Exposed Cybersecurity Flaws
- ANSSI Investigations: Balancing Confidentiality and Speed
- Phishing: When the Hunter Becomes the Prey
- Expanding Risks Beyond Messaging Apps
- Challenges in Risk Management at the Highest Levels
- How DataShielder Could Have Prevented This Breach
- Recent Hacks Targeting French and European Officials
- Cyber Threats Across Europe: Why Encryption Is Vital
- Strengthening French Cybersecurity
- Unmatched Security and Encryption with DataShielder
- Closing the Loop: A Unified Cybersecurity Strategy
- From Personal Devices to National Threats: The Ripple Effects
- Key Takeaways for Cybersecurity
How the French Minister Phone Hack Exposed Cybersecurity Flaws
On November 25, 2024, cybercriminals targeted Jean-Noël Barrot, the French Foreign Minister, during the G7 summit. They launched the attack when Barrot unknowingly clicked on a malicious link sent through Signal, immediately granting them access to sensitive data. This breach underscores the urgent need for advanced encryption for national security to protect high-level communications from sophisticated cyber threats.
Shortly after, Bahrain’s Foreign Minister, Abdullatif Bin Rashid Al Zayani, noticed suspicious messages originating from Barrot’s device. This unusual activity quickly raised alarms and prompted further investigation. The incident demonstrates the importance of government cybersecurity solutions capable of mitigating threats from phishing, spyware, and other evolving attack vectors. (Mediapart)
Initial Investigations by ANSSI: Why Speed Matters
The Agence nationale de la sécurité des systèmes d’information (ANSSI), recognized for its ANSSI accreditation at the highest security levels (“Secret Défense”), quickly ruled out well-known spyware like Pegasus or Predator. However, the investigation faced delays due to Minister Barrot’s diplomatic commitments.
For detailed insights into similar spyware threats:
Phishing: When the Hunter Becomes the Prey
Ironically, Jean-Noël Barrot, who spearheaded a 2023 law against phishing, fell victim to this very tactic. This incident underscores how even cybersecurity-savvy individuals can be deceived by increasingly sophisticated attacks. This case underscores the critical need for robust tools in phishing attack mitigation. As attackers evolve their methods, even trusted platforms like Signal are exploited to orchestrate highly targeted phishing attacks.
Lessons from the Incident
- Phishing Evolution: Attackers exploit human vulnerabilities with precise, targeted messages.
- No One Is Immune: Even those fighting cyber threats can fall prey to them, highlighting the importance of robust defenses.
This case emphasizes the need for constant vigilance and tools like DataShielder NFC HSM Defense to mitigate such risks.
A Case Study: The French Minister’s Messaging Practices
In a public statement on November 29, 2023, Jean-Noël Barrot, French Minister for Europe and Foreign Affairs, revealed on X (formerly Twitter) that he and his team have been using Olvid, an ANSSI-certified messaging application, since July 2022. The minister described Olvid as “the most secure instant messaging platform in the world,” emphasizing its encryption and privacy features.
“It is French, certified by @ANSSI_FR, encrypted, and does not collect any personal data. We have been using it with my team since July 2022. In December, the entire government will use @olvid_io, the most secure instant messaging tool in the world.”
— Jean-Noël Barrot on X
Despite Olvid’s certification, the G7 summit breach in November 2024 occurred via Signal, another widely used secure messaging app. This raises critical questions:
- Inconsistent Platform Use: Even with access to highly secure tools like Olvid, alternative platforms such as Signal were still employed, exposing potential gaps in security practices.
- Persistent Human Vulnerabilities: Cybercriminals exploited human behavior, with Minister Barrot unknowingly clicking on a malicious link—a reminder that even the most secure tools cannot compensate for user error.
How DataShielder Could Have Prevented This Breach
Unlike standalone secure messaging apps, DataShielder NFC HSM Defense provides proactive multichannel encryption, ensuring the security of all communication types, including SMS, MMS, RCS, and messaging platforms such as Signal and Olvid. Sensitive communication protection is a cornerstone of DataShielder NFC HSM Defense. This advanced tool offers significant counter-espionage benefits, including:
- Cross-Platform Security: All communications are encrypted with AES-256 CBC, a quantum-resistant algorithm, via an NFC-secured device with patented segmented keys and multifactor authentication. This ensures robust protection across any platform used.
- Device Compromise Mitigation: Even if an Android phone, computer, or cloud-based messaging service is compromised, encrypted messages and files remain completely inaccessible. This ensures that sensitive data is protected against unauthorized access, whether from legitimate or illegitimate actors.
- Automated Call and Contact Protection: Sensitive contact data is securely stored outside the device, preventing theft. Additionally, all traces of calls, SMS, MMS, and related logs are automatically erased from the phone after use, significantly reducing the risk of exposure. Powered by the innovative EviCall NFC HSM technology, this feature ensures unparalleled communication security. Watch the video below to see how EviCall protects calls and contact information:
For additional details, visit: EviCall NFC HSM – Phone & Contact Security
- Seamless Integration: Officials can maintain their current habits on any platform while benefiting from elevated security levels, eliminating reliance on platform-specific encryption protocols.
By leveraging DataShielder NFC HSM Defense, governments can bridge the gap between user convenience and robust security, ensuring that high-level communications are safeguarded against sophisticated attacks exploiting human vulnerabilities or platform inconsistencies.
The Challenges of Risk Management at the Highest Levels
Jean-Noël Barrot’s refusal to hand over his hacked phone to ANSSI investigators raises questions about balancing confidentiality and collaboration. The incident also highlights the broader G7 cybersecurity challenges, particularly the complexity of securing sensitive communications in a rapidly evolving threat landscape. Solutions like DataShielder NFC HSM Defense are pivotal in addressing these challenges while safeguarding data sovereignty.
Implications of Non-Cooperation
- Delayed Investigations: Slows response times to attacks.
- Public Trust: Questions arise about leadership transparency and risk management.
- Solutions: DataShielder NFC HSM Defense allows secure investigation without exposing sensitive data, ensuring both collaboration and confidentiality.
Such tools could resolve the dilemma of balancing privacy with the need for swift cybersecurity responses.
Institutional Trust and National Cybersecurity: The Role of the ANSSI
The involvement of ANSSI in managing incidents like the French Minister Phone Hack raises important questions about institutional trust and operational protocols. While ANSSI is the national authority for cybersecurity, accredited to handle even the most sensitive information, this case exposes potential hesitations among top officials to fully cooperate during crises. As an organization with ANSSI accreditation, the agency is responsible for certifying tools used in national defense. Yet, the hesitations highlight a need for greater institutional trust, especially in the context of the G7 cybersecurity challenges.
Why ANSSI’s Role Is Pivotal
As the leading agency for protecting France’s critical infrastructures and sensitive information systems, ANSSI holds the highest levels of security clearance, including “Secret Défense” and “Très Secret Défense.” It has the technical expertise and legal mandate to investigate cyber incidents affecting government officials, such as:
- Cyberattack response to safeguard critical systems and recover compromised data.
- Certification of security solutions used in national defense and high-level communications.
- Collaboration with international agencies to combat global cyber threats.
These capabilities make ANSSI indispensable in incidents like the G7 phone hack, where sensitive diplomatic communications are at risk.
Perceived Hesitations: A Question of Trust?
Despite ANSSI’s credentials, Minister Jean-Noël Barrot’s delayed cooperation in submitting his device for forensic analysis raises questions:
- Could there be a lack of trust in sharing sensitive data with ANSSI, even though it operates under strict confidentiality protocols?
- Is this delay a reflection of the need for even greater assurances regarding data sovereignty and privacy during investigations?
While ANSSI adheres to strict security standards, the hesitations underscore a potential gap between technical accreditation and political confidence. This gap is where tools like DataShielder could make a critical difference.
DataShielder: Bridging the Gap Between Security and Trust
Solutions like DataShielder NFC HSM Defense address both the technical and trust-related challenges highlighted in this case:
- Preserving Data Sovereignty: DataShielder ensures that encrypted communications remain inaccessible to any unauthorized party, even during forensic investigations.
- Facilitating Confidential Collaboration: With tools like encrypted logs and automated data management, sensitive data can be analyzed without compromising its confidentiality.
- Building Institutional Confidence: The use of DataShielder demonstrates a proactive approach to protecting national interests, providing additional assurance to government leaders that their data remains fully secure and private.
Key Takeaway
The French Minister Phone Hack not only underscores the need for robust cybersecurity tools but also highlights the importance of strengthening trust between national institutions and decision-makers. By integrating advanced encryption solutions like DataShielder, governments can ensure both the security and confidence needed to navigate the complex challenges of modern cyber threats.
How DataShielder Could Have Changed the Game
The French Minister Phone Hack highlights the urgent need for advanced cybersecurity tools. If Jean-Noël Barrot had used DataShielder NFC HSM Defense, this innovative solution could have provided unparalleled safeguards while enabling seamless collaboration with cybersecurity investigators like ANSSI. Sensitive communications and data could have remained secure, even under intense scrutiny, mitigating risks associated with platform vulnerabilities or human errors.
Moreover, DataShielder aligns with international cybersecurity standards such as NIS2, positioning governments at the forefront of digital security while offering a proactive defense against escalating global cyber threats.
These challenges underline why solutions like DataShielder NFC HSM Defense are critical to addressing the rising threats effectively and safeguarding sensitive communications at all levels.
Unmatched Security and Encryption with DataShielder
DataShielder NFC HSM Defense ensures end-to-end encryption for all communication channels, including SMS, MMS, RCS, and messaging platforms like Signal, Olvid, and LinkedIn, using AES-256 CBC encryption, a quantum-resistant algorithm.
- Automated Protection: Sensitive contacts are stored securely outside devices, and all traces of calls, messages, and logs are automatically erased after use, ensuring no exploitable data remains.
- Device Compromise Mitigation: Even if devices or platforms are breached, encrypted data remains inaccessible, preserving confidentiality.
Seamless Integration and Compatibility
DataShielder’s Zero Trust and Zero Knowledge architecture eliminates reliance on third-party platforms while ensuring user convenience:
- Cross-Platform Functionality: Works with the DataShielder HSM PGP, EviCypher Webmail, and Freemindtronic Extension to encrypt and decrypt communications across all devices, including mini-computers like Raspberry Pi.
- User-Friendly Interface: Compatible with existing habits and workflows without sacrificing security.
Future-Proof Cybersecurity
DataShielder ensures communications are protected against emerging threats with:
- Resilience Against Quantum Attacks: Leveraging AES-256 CBC encryption.
- Sensitive communication protection: Maintaining full control of critical information while mitigating risks of compromise.
Phishing: A Persistent Threat to National Security
Phishing remains one of the most dangerous cyberattack vectors, with over 90% of cyberattacks originating from phishing emails, as reported by StationX. This alarming statistic underscores the critical need for robust security solutions like DataShielder to counter this pervasive threat.
Attackers now employ advanced tactics, such as highly convincing links and exploiting trusted platforms like Signal, to bypass basic defenses. This highlights the urgency for government cybersecurity solutions that integrate spyware protection tools and advanced encryption technologies, ensuring sensitive communications remain secure against evolving threats.
Expanding Risks Beyond Messaging Apps
Although Minister Barrot indicated that the attack originated from a link received via Signal, this incident is part of a broader trend of cyberattacks targeting communication platforms. These attacks are not limited to cybercriminals but often involve **state-sponsored cyberespionage groups** seeking to exploit trusted channels to gain access to sensitive government communications.
On December 4, 2024, the FBI and CISA (Cybersecurity and Infrastructure Security Agency) issued a joint advisory warning about the rise of SMS-based phishing attacks (smishing). These attacks use malicious links to lure victims into compromising their devices, exposing sensitive data. The advisory highlighted that these techniques are increasingly used by advanced persistent threats (APTs), often linked to nation-states.
The advisory emphasized that all communication platforms—SMS, messaging apps like Signal, and even emails—are vulnerable without robust security practices. Key recommendations include:
- Using strong encryption tools to safeguard communication.
- Carefully verifying links before clicking to avoid malicious redirects.
- Adopting advanced security devices, such as the DataShielder NFC HSM Defense, which protects sensitive communications even during espionage attempts. By encrypting data and implementing proactive defense mechanisms, this tool ensures that even if a platform is compromised, critical information remains secure.
This broader threat landscape underscores the increasing sophistication of cyberespionage actors and cybercriminals alike, who exploit trusted communication channels to target high-level government officials and agencies. In light of evolving cyber threats, these measures are indispensable for protecting national security and ensuring secure communication channels.
With advanced features like Zero Trust architecture and quantum-resistant encryption, tools like DataShielder provide unparalleled sensitive communication protection against both cybercriminal and cyberespionage threats.
Recent Hacks Targeting French and European Officials
Confirmed Espionage or Acknowledged Incidents
Over the years, reports and investigations have highlighted multiple high-ranking French officials as alleged targets of spyware like Pegasus and Predator. While some cases have been acknowledged, others remain under investigation or unverified. These incidents underscore vulnerabilities in governmental communication systems and the critical need for advanced cybersecurity measures.
Examples of High-Profile Targets
- Emmanuel Macron (President of France, 2021) – Confirmed as a target of Pegasus. Source
- Édouard Philippe (Former Prime Minister, 2021) – His phone was targeted by Pegasus. Source
- Jean-Yves Le Drian (Minister of Foreign Affairs, 2021) – Confirmed as a target of Pegasus. Source
- Christophe Castaner (Former Minister of the Interior, 2021) – Confirmed targeted by Pegasus. Source
- Gérald Darmanin (Minister of the Interior, 2021) – His phone was also targeted by Pegasus. Source
- Bruno Le Maire (Minister of Economy, Finance, and Recovery, 2021) – His phone was targeted by Pegasus. Source
- François Molins (General Prosecutor at the Court of Cassation, 2021) – His phone was targeted by Pegasus. Source
- Richard Ferrand (President of the National Assembly, 2021) – His phone was targeted by Pegasus. Source
- Éric Dupond-Moretti (Minister of Justice, 2021) – His phone was infected by Pegasus. Source
- François Bayrou (High Commissioner for Planning, 2021) – His phone was infected by Pegasus. Source
- Marielle de Sarnez (Former Minister of European Affairs, 2021) – Confirmed as a target of Pegasus. Source
Potential Targets (Presence on Pegasus List)
Some officials were identified as potential targets based on their presence in leaked surveillance lists, though there is no conclusive evidence of device compromise.
Examples of Potential Targets
- Jean-Noël Barrot (Minister for Europe and Foreign Affairs, 2024) Source
- Florence Parly (Former Minister of the Armed Forces, 2023) Source
- Jacqueline Gourault (Minister of Territorial Cohesion, 2020) source
- Julien Denormandie (Minister of Agriculture, 2020) source
- Emmanuelle Wargon (Minister of Housing, 2020) source
- Sébastien Lecornu (Minister of Overseas Territories, 2020) source
- Jean-Michel Blanquer (Minister of Education, 2019) source
- François de Rugy (Minister of Ecological Transition, 2019) source
Given these challenges, it becomes imperative to explore innovative solutions to address espionage risks effectively.
Challenges in Understanding the Full Extent of Espionage
Why Is the Full Extent of Espionage Unclear?
Understanding the full scope of spyware-related incidents involving government officials is fraught with challenges due to the complex nature of such cases.
Key Factors Contributing to Ambiguity
- Secrecy of Investigations: Details are often classified to protect evidence and avoid tipping off attackers.
- Political Sensitivity: Acknowledging vulnerabilities in official communication channels may erode public trust.
- Unconfirmed Compromises: Being listed as a potential target does not guarantee successful exploitation.
Strengthening French Cybersecurity with NFC Smartphones and DataShielder NFC HSM Defense
Sophisticated cyberattacks, such as the hacking of Jean-Noël Barrot’s phone, have exposed critical vulnerabilities in government communication systems. These threats highlight the urgent need to prioritize digital sovereignty and protect sensitive government communications. Combining French-designed NFC smartphones with the DataShielder NFC HSM Defense offers an effective and cost-controlled cybersecurity solution.
French Smartphone Brands Equipped with NFC Technology
Several French smartphone brands stand out for their NFC-equipped models, which integrate seamlessly with the DataShielder NFC HSM Defense. These brands, including Wiko, Archos, Kapsys, and Crosscall, cater to diverse users ranging from professionals to public agencies. Their NFC capabilities make them ideal for secure communication.
Brands Already Serving French Government Entities
Certain brands, including Crosscall and Kapsys, already supply French government entities, making them strong candidates for further adoption of advanced encryption solutions.
- Crosscall: Widely trusted by law enforcement and field professionals for its durable designs and reliability in harsh conditions.
- Kapsys: Kapsys delivers secure communication tools tailored for users requiring accessibility features and users with specific accessibility needs.
This established trust demonstrates the potential for these brands to further integrate cutting-edge tools like the DataShielder NFC HSM Defense into their offerings.
Unlocking Strategic Potential Through Collaboration
French smartphone brands can accelerate their contribution to national cybersecurity efforts by partnering with AMG Pro, the exclusive distributor of DataShielder NFC HSM Defense in France. Such collaboration enables the creation of comprehensive security packages, bundling NFC-enabled smartphones with state-of-the-art encryption technology.
A Strategic Synergy for Digital Sovereignty
Through collaboration with AMG Pro, French smartphone brands could:
By partnering with AMG Pro, French brands can:
- Enhance their reputation as leaders in sovereign technology through the integration of advanced cybersecurity tools.
- Offer comprehensive turnkey solutions, seamlessly combining smartphones with robust encryption to address the specific requirements of government entities.
- Contribute to advancing French digital sovereignty by promoting locally developed solutions designed to secure critical operations.
A Clear Path Toward Secure and Sovereign Communications
This strategy aligns with both economic priorities and national security goals, providing a robust response to the growing threat of cyberattacks. By leveraging French innovation and integrating advanced tools like the DataShielder NFC HSM Defense, French smartphone brands can pave the way for a secure, sovereign future in government communications.
Preventive Strategies for Modern Cyber Threats
The Importance of Preventive Measures
Governments must prioritize robust encryption tools like DataShielder NFC HSM Defense to counter espionage and cyber threats effectively.
Advantages of DataShielder
- Strong Encryption: Protecting communications with AES-256 CBC encryption, resistant to interception and exploitation.
- Proactive Surveillance Mitigation: Safeguarding sensitive communications, even if devices are targeted.
- User-Centric Security: Minimizing risks by automating data protection and erasure to counter human error.
Governments and organizations must prioritize these measures to mitigate risks and navigate the complexities of modern espionage.
Global Repercussions of Spyware Attacks
Global Impacts of Pegasus Spyware on World Leaders
Beyond France, global leaders have faced similar surveillance threats, highlighting the need for advanced encryption technologies to protect sensitive information.
Key Insight
These revelations emphasize the urgent need for robust encryption tools like DataShielder NFC HSM Defense to secure communications and mitigate risks. As cyber threats evolve, governments must adopt advanced measures to protect sensitive information.
Cyber Threats Across Europe: Why Encryption Is Vital
The issue of spyware targeting government officials is not limited to France.
European Parliament Members Targeted
In February 2024, traces of spyware were discovered on phones belonging to members of the European Parliament’s Subcommittee on Security and Defence. These findings emphasize the global scale of cyber surveillance and the need for robust security measures across governments. (Salt Typhoon Cyber Threats)
Key Takeaway
Cybersecurity is no longer optional—it is a strategic necessity for national sovereignty.
Why Encryption Tools Like DataShielder Are Crucial for Sensitive Communications
The French Minister Phone Hack demonstrates how advanced encryption for national security can mitigate risks associated with breaches. Tools like DataShielder NFC HSM Defense offer a proactive defense by ensuring end-to-end encryption for sensitive communications, making them an indispensable part of government cybersecurity solutions.This tool ensures comprehensive security for sensitive communications across platforms, safeguarding national interests.
Key Benefits of DataShielder
- Comprehensive Protection: Encrypts SMS, emails, chats, and files.
- Technological Independence: Operates without servers or central databases, reducing vulnerabilities.
- French Innovation: Built with 100% French-made origine components from French STMicroelectronics, leveraging patents by Freemindtronic founder Jacques Gascuel.
- Local Manufacturing: Designed and produced in France and Andorra, ensuring sovereignty and compliance.
- Ease of Use: Compatible with both mobile and desktop devices.
Cybersecurity: A Collective Responsibility
The hack targeting Jean-Noël Barrot shows that cybersecurity is not just an individual responsibility—it’s a collaborative effort.
Steps to Strengthen Cybersecurity
- Awareness Campaigns: Regular training for government officials to recognize cyber threats.
- Collaboration Across Agencies: Seamless cooperation for quick responses to threats.
- Adopting Encryption Tools: Technologies like DataShielder protect critical communications while ensuring compliance.
Governments must prioritize education, collaboration, and technology to safeguard national security.
Why Choose DataShielder?
- Comprehensive Protection: Encrypt SMS, emails, chats, and files.
- Technological Independence: Operates without servers or central databases, significantly reducing vulnerabilities.
- French and Andorran Innovation: Built with French-origin components and patents.
From Personal Devices to National Threats: The Ripple Effects of Cyberattacks
Breaches like the French Minister Phone Hack illustrate how compromised devices can have far-reaching implications for national security. Employing advanced encryption for national security through tools like DataShielder ensures that government cybersecurity solutions remain robust and future-proof.
Consequences of Breached Devices
- Diplomatic Risks: Compromised communications, such as those during the G7 summit, can strain alliances or expose strategic vulnerabilities, potentially leading to geopolitical tensions.
- Classified Data Leaks: Exposing sensitive plans or confidential discussions could provide adversaries with critical intelligence, undermining national interests.
How DataShielder NFC HSM Defense Helps
- Encrypted Protection: Ensures sensitive data remains secure even during investigations, preventing unauthorized access to classified information.
- Automatic Data Management: Removes sensitive logs, safeguarding user privacy while streamlining investigative processes.
Such tools bridge the gap between personal device security and national cybersecurity needs. Adopting tools like DataShielder is not just a technological upgrade—it’s a strategic necessity to safeguard national interests in a rapidly evolving digital landscape.
Strengthening Cybersecurity with Encryption Tools
Adopting tools like DataShielder NFC HSM and HSM PGP is a proactive step toward protecting sensitive communications. These devices provide security for governments, organizations, and individuals, ensuring sovereignty over critical data.
Secure Your Communications with DataShielder
To address the growing risks of cyber threats, DataShielder NFC HSM and HSM PGP provide robust encryption solutions designed to protect sensitive communications for both sovereign entities and professional applications.
Exclusivity in France
For users in France, DataShielder products are distributed exclusively through AMG Pro, offering tailored solutions to meet local regulatory and operational needs.
Availability in Other Countries
For international users, these solutions are available via FullSecure in Andorra. Explore the range of products below:
Available from FullSecure in Andorra. Explore the range of products below:
- DataShielder NFC HSM Master: A master encryption tool offering advanced security features for organizations and individuals.
- DataShielder NFC HSM Lite: A lightweight encryption solution perfect for everyday secure communication needs.
- DataShielder NFC HSM Auth: Ensures secure authentication and encryption for sensitive operations.
- DataShielder NFC HSM Starter Kit: An ideal entry point for comprehensive encryption and security.
- DataShielder NFC HSM M-Auth: Provides mobile-friendly encryption for on-the-go secure communication.
- DataShielder PGP HSM Data Encryption: A robust solution for secure file and email encryption.
Key Takeaways for Cybersecurity
The phone hack of French Foreign Minister Jean-Noël Barrot and similar breaches targeting other officials underline the critical need for strong cybersecurity protocols. Robust encryption tools like DataShielder NFC HSM and HSM PGP not only protect against known threats like Pegasus but also future-proof sensitive data from emerging cyber risks.
Now that we’ve highlighted the unique strengths of DataShielder, let’s discuss how governments can integrate this solution effectively to mitigate cyber threats and enhance operational security.
Implementing DataShielder in Government Operations
The French Minister Phone Hack demonstrates that advanced encryption solutions like DataShielder NFC HSM Defense are no longer optional—they are essential. Governments must act decisively to address escalating cyber threats and protect sensitive communications.
Why DataShielder Is the Answer:
- Fortify Communications
Cyberattacks on high-ranking officials, as seen in the G7 breach, expose the vulnerability of current systems. DataShielder offers unmatched encryption, shielding classified communications from prying eyes and ensuring uninterrupted confidentiality. - Enable Secure Investigations
By facilitating seamlThis tool facilitates seamless collaborationess collaboration with cybersecurity agencies like ANSSI while preserving the confidentiality of encrypted content, DataShielder strikes a perfect balance between privacy and judicial cooperation. This allows investigators to focus on analyzing attack methods without risking sensitive data. - Set a Gold Standard
Adopting DataShielder demonstrates a commitment to proactive cybersecurity measures. It establishes a precedent for managing sensitive data with operational transparency and national sovereignty, setting an example for global cybersecurity practices.
Protecting the Future
Integrating DataShielder NFC HSM Defense into government operations is not just a technological upgrade—it’s a necessary step toward a secure digital future. By equipping officials with cutting-edge tools, governments can:
- Safeguard classified data from cybercriminals and state-sponsored actors, ensuring the highest levels of security.
- Streamline investigative processes without compromising privacy, making crisis responses faster and more effective.
- Build public trust by showcasing robust and transparent management of cyber threats and national security.
Closing the Loop: A Unified Cybersecurity Strategy
As highlighted in the Key Takeaways for Cybersecurity, the need for robust encryption tools has never been more urgent. DataShielder NFC HSM Defense aligns perfectly with the priorities of governments seeking to protect national sovereignty and sensitive operations. With a future-proof solution like DataShielder, governments can confidently face emerging cyber risks, safeguard communications, and maintain trust in an increasingly digital world.
Adopting advanced encryption tools like DataShielder NFC HSM Defense is no longer optional—it is a strategic necessity. By acting decisively, governments can safeguard sensitive communications, protect national sovereignty, and set global standards in cybersecurity.
French Surveillance: Data Sharing and Hacking Concerns
French surveillance practices include data-sharing with the NSA and state hacking activities. These raise pressing privacy and legal concerns. Without robust oversight, these actions risk undermining democratic values and citizens’ trust. This complicates balancing national security and personal freedoms in the digital era. Join the conversation on the evolving balance between national security and individual freedoms. Discover actionable reforms that could shape the future of digital governance.
A Growing Threat to Privacy
Social media platforms like Facebook and X are critical tools for public discourse. They are also prime targets for intelligence monitoring, further complicating oversight.
French intelligence’s surveillance practices face increasing scrutiny due to significant oversight gaps. Recent reports reveal significant gaps in oversight, allowing these agencies to monitor social media platforms like Facebook and X (formerly Twitter) without robust legal frameworks. Concerns about privacy, state accountability, and democratic safeguards are escalating. Moreover, these operations extend to international data-sharing agreements and advanced hacking activities, raising further questions about the ethical implications of mass surveillance in a democratic society.
As these concerns grow, understanding the legal and ethical challenges of oversight becomes essential.
A Systemic Lack of Oversight in French Digital Surveillance
French intelligence agencies rely on vague legal provisions to justify mass surveillance activities. These operations often bypass judicial or legislative scrutiny, leaving citizens vulnerable. For instance, the Commission nationale de contrôle des techniques de renseignement (CNCTR) identified major failings in its June 2024 report, including:
- Retaining excessive amounts of data without justification.
- Transcribing intercepted communications unlawfully.
These practices highlight a lack of transparency, especially in collaborations with foreign entities like the (National Security Agency). A Le Monde investigation revealed that the DGSE (Direction Générale de la Sécurité Extérieure) has transmitted sensitive data to the NSA as part of intelligence cooperation. The collaboration between the DGSE and the NSA highlights the lack of transparency in international data-sharing agreements. This data-sharing arrangement, criticized for its opacity, raises concerns about the potential misuse of information and its impact on the privacy of French citizens. (Source: Le Monde)
Advocacy groups, including La Quadrature du Net (LQDN), have called for urgent reforms to address these issues and safeguard citizens’ rights. (LQDN Report)
The Role of CNCTR in French Digital Surveillance
The Commission Nationale de Contrôle des Techniques de Renseignement (CNCTR), established in 2015, serves as the primary independent oversight body for surveillance practices in France. Every technique employed by intelligence services—whether it involves wiretapping, geolocation, or image capture—requires a consultative opinion from this commission before receiving final approval from the Prime Minister.
According to Serge Lasvignes, CNCTR president since 2021, this oversight is crucial in limiting potential abuses. In an official statement, he asserted:
“The law is now well understood and accepted by the services. Does this fully prevent deviations from the legal framework? No. But in such cases, the Prime Minister’s legal and political responsibility would clearly be engaged.”
This declaration highlights the need to strengthen both legislative frameworks and political accountability to prevent misconduct.
For instance, in 2022, the CNCTR intervened to revise proposed geolocation practices that lacked sufficient safeguards, showcasing its importance as a counterbalance to unchecked power.
In its June 2024 report, the CNCTR also identified critical failings, such as excessive data retention and the unlawful transcription of intercepted communications. While most of its recommendations are adhered to, the commission remains concerned about the opacity of international collaborations, including data-sharing agreements with the NSA.
For further information on the CNCTR’s role and reports, visit their official website.
Impact on Society: Real-World Examples
The societal effects of unchecked French digital surveillance are vast and troubling. Here are key examples:
| Case | Description | Implications |
|---|---|---|
| Yellow Vest Movement | Authorities digitally profiled activists, raising concerns about suppressing political dissent. | Reduced trust in government institutions and limitations on free expression. |
| Terror Investigations | Monitoring social media helped thwart attacks but revealed accountability gaps. | Increased risks of misuse, particularly against marginalized groups. |
| Public Figures | Journalists and influencers faced unwarranted surveillance. | Threats to press freedom and public discourse. |
| Whistleblower Case | A whistleblower reported intercepted encrypted communications, prompting legal challenges. | Showcases the misuse of surveillance tools against individuals. |
An Expanding Scope of Surveillance
According to the 2023 annual report by the Commission Nationale de Contrôle des Techniques de Renseignement (CNCTR), 24,209 individuals were placed under surveillance in France in 2023. This marks a 15% increase compared to 2022 and a 9% rise from 2019. The report highlights a significant shift in priorities: the prevention of delinquency and organized crime has become the primary reason for surveillance, surpassing counter-terrorism efforts. This trend raises critical questions about the impact on individual freedoms and the urgent need for enhanced regulatory oversight.
Surveillance Trends: Key Figures at a Glance
The CNCTR’s latest findings underscore the significant expansion of surveillance practices in France. For instance:
“15% increase in surveillance activities in 2023 compared to 2022.”
“24,209 individuals were surveilled in France last year—raising critical questions about privacy and oversight.”
These statistics highlight the urgency of addressing the balance between national security and individual freedoms. As surveillance trends evolve, these figures serve as a stark reminder of the potential implications for democratic safeguards and personal privacy.
Targeting Vulnerable Groups: A Hidden Cost of Surveillance
While surveillance aims to ensure societal security, its impact on vulnerable groups—especially journalists, activists, and marginalized communities—raises critical ethical and human rights concerns. These groups are disproportionately subjected to invasive monitoring, exposing them to significant risks.
Journalists Under Threat
Investigative reporters often face unwarranted surveillance, threatening press freedom and undermining their ability to hold power accountable. The Pegasus Project, spearheaded by Amnesty International, revealed how governments misuse spyware like Pegasus to monitor human rights defenders, political leaders, journalists, and lawyers unlawfully. Such practices jeopardize not only individual safety but also the broader democratic fabric. (Source: Amnesty International)
Activists and Human Rights Defenders
Surveillance tools are frequently deployed to suppress dissent and intimidate human rights advocates. Authoritarian regimes exploit advanced technologies and restrictive laws to silence civic movements and criminalize activism. The Internews Civic Defenders Program highlights the increasing use of digital repression against activists, aiming to counteract these oppressive practices. (Source: Internews)
Marginalized Communities and Algorithmic Bias
Certain demographics, including individuals from diverse ethnic or religious backgrounds and those identifying as LGBTQ+, are often disproportionately affected by profiling and algorithmic bias. Surveillance disproportionately targets these groups, exacerbating existing inequalities. A report from The Century Foundation underscores how marginalized communities are subjected to coercive monitoring that is rarely applied in affluent areas, further entrenching systemic disparities. (Source: The Century Foundation)
Advocacy for Equitable Surveillance Practices
Organizations like Amnesty International continue to expose the human rights violations perpetrated through covert cyber surveillance. Their research emphasizes the urgent need for regulatory reforms to address the global spyware crisis and ensure equitable surveillance practices. (Source: Amnesty International)
The Role of Advocacy in Amplifying Awareness
NGOs like Amnesty International and La Quadrature du Net consistently expose the societal impacts of surveillance, urging the adoption of privacy-first policies through public reports and awareness campaigns.
The Call for Change
The disproportionate targeting of these vulnerable groups highlights the critical need for ethical oversight and accountability in surveillance practices. Balancing security needs with respect for privacy and human rights is not just a legal obligation but a moral imperative.
Public Perception of French Digital Surveillance
A recent survey highlights public concerns:
| Survey Question | Response | Percentage |
|---|---|---|
| Do you believe surveillance protects privacy? | Yes | 28% |
| Do you support stricter oversight? | Yes | 72% |
| Are you aware of GDPR protections? | No | 65% |
These findings underscore the necessity of raising awareness and ensuring transparency in how surveillance operations align with citizens’ rights.
Chronology of French Surveillance Developments
French digital surveillance has evolved significantly over time. Here’s a timeline of key events:
| Year | Event | Significance |
|---|---|---|
| 2001 | U.S. Patriot Act introduced | Established mass digital surveillance; influenced global approaches to intelligence. |
| 2015 | France expanded surveillance powers after terror attacks. | Allowed broader interception of digital communications. |
| 2018 | Introduction of GDPR in the European Union | Strengthened personal data protections but revealed gaps in intelligence operations compliance. |
| 2024 | CNCTR report highlighted illegal practices in French surveillance. | Exposed excessive retention and transcription of intercepted data. |
These cases illustrate how unchecked surveillance can lead to societal and legal challenges, particularly when boundaries are not clearly defined.
Technological Aspects of French Digital Surveillance
Technology plays a pivotal role in shaping the scope and efficiency of French digital surveillance.
Tools Utilized in French Digital Surveillance
French intelligence employs a variety of advanced tools to enhance its surveillance capabilities, including:
- Facial Recognition:
Widely deployed in public spaces to identify individuals of interest, facial recognition technology remains a cornerstone of surveillance efforts. However, its use raises concerns about potential misuse. Reports by Privacy International emphasize the need for clear legal frameworks to govern its application. In France, a 2024 draft law sought to reinforce restrictions, underscoring ongoing debates over ethical implications and accountability. - Data Interception Software (e.g., Pegasus, Predator):
Advanced spyware like Pegasus and Predator exemplify powerful yet controversial surveillance tools. Predator, developed by the Greek firm Cytrox, has been linked to European surveillance campaigns, including potential use in France. Its capabilities, such as unauthorized access to encrypted communications, device microphones, and cameras, parallel those of Pegasus, raising concerns about privacy violations and ethical misuse. Advocacy groups, including Amnesty International, continue to push for stricter international regulation of such invasive technologies. Learn more about Predator in this analysis of the Predator Files. - Open-Source Intelligence (OSINT):
French intelligence leverages OSINT to analyze publicly available data from social media platforms, online forums, and public records. This approach complements traditional methods and offers valuable insights without direct access to private communications. However, it also raises concerns about privacy erosion and the ethical boundaries of data collection.
Future Trends in Digital Surveillance
Emerging technologies like AI and machine learning are expected to transform surveillance practices further by:
- Enhancing predictive analytics: These tools can identify potential threats but also raise concerns about bias and accuracy.
- Automating large-scale data collection: This significantly increases monitoring capabilities while amplifying privacy risks.
While these advancements improve efficiency, they also underscore the need for ethical governance to address privacy and oversight challenges. The ongoing debates surrounding AI-driven surveillance reflect the delicate balance between technological progress and the protection of fundamental rights.
French Digital Surveillance vs. Global Practices
| Country | Practices | Legal Framework |
|---|---|---|
| United States | Despite the massive surveillance authorized by the Patriot Act, the United States introduced mechanisms like the Freedom Act in 2015, limiting some practices after public criticism. | Well-defined but broad. |
| China | Unlike France, China openly embraces its intentions of total surveillance. Millions of cameras equipped with facial recognition specifically target political dissidents. | State-controlled; no limits. |
| Germany | Germany has adopted a more transparent approach with parliamentary committees overseeing intelligence services while remaining GDPR-compliant. | GDPR-compliant, transparent. |
These comparisons have sparked international reactions to French surveillance policies, with many global actors urging stricter regulations.
France, with its vague and poorly enforced legal boundaries, stands out as a country where surveillance practices escape effective regulation. The addition of international data-sharing with the NSA and state-sponsored hacking further differentiates its practices. The European Data Protection Supervisor (EDPS) calls for harmonized regulations that balance national security with individual freedoms, setting a model for ethical surveillance.
These global examples underscore the urgent need for France to harmonize its surveillance practices with international norms, balancing security with civil liberties.
GDPR Challenges and Legal Implications: Exploring the Impact of GDPR on Surveillance Practices
| GDPR Principle | Challenge for French Intelligence | Implication |
|---|---|---|
| Data Minimization | Intelligence agencies retain excessive data without clear justification. | These conflicts often lead to legal challenges to government data retention, as individuals and advocacy groups push back against excessive surveillance practices. |
| Purpose Limitation | Surveillance often lacks specific, legitimate purposes. | Risk of surveillance being contested in court. |
| Accountability | Intelligence operations bypass GDPR rules under “national security” claims. | Undermines public trust and legal protections for individuals. |
By refining GDPR to explicitly address intelligence activities, the EU can establish a robust framework that safeguards privacy without compromising security.
Legal challenges, such as lawsuits citing GDPR violations, have led to partial reforms in intelligence data processing. In 2022, an NGO filed a lawsuit against the Ministry of the Interior for excessive retention of personal data, violating the GDPR’s data minimization principles. This case led to a temporary reduction in surveillance capabilities until compliance with GDPR was ensured. This case led to a temporary reduction in surveillance capabilities until compliance with GDPR was ensured.However, compliance remains inconsistent.
While systemic reforms are essential, individuals can also adopt tools to safeguard their privacy and mitigate the risks of unchecked surveillance. Here are practical solutions designed to empower users in the digital age.
The Road Ahead: Potential Legislative Changes
As digital technologies evolve, so too must the laws governing their use. In France, ongoing debates focus on:
- Expanding GDPR Protections: Advocacy groups propose including surveillance-specific amendments to address gaps in oversight.
- Increased Transparency: Legislators are exploring requirements for annual public reports on intelligence operations.
At the European level, new directives could harmonize surveillance practices across member states, ensuring that privacy remains a core principle of digital governance.
Empowering Individuals Against Surveillance: A Practical Solution
While government surveillance raises legitimate concerns about privacy and security, individuals can take proactive steps to safeguard their communications and data. Tools like DataShielder NFC HSM and DataShielder HSM PGP provide robust encryption solutions, ensuring that sensitive information remains confidential and inaccessible to unauthorized parties.
- DataShielder NFC HSM: This device encrypts communications using AES-256 and RSA 4096 protocols, offering end-to-end protection for messages across various platforms. It operates offline, ensuring no data passes through third-party servers, a critical advantage in the era of mass surveillance.
- DataShielder HSM PGP: Designed for secure email and document exchanges, this tool leverages advanced PGP encryption to keep sensitive data private. Its compatibility with platforms like EviCypher Webmail further enhances its utility for users seeking anonymity and data integrity.
“This device helps individuals take proactive steps in protecting communications with encryption tools, ensuring that no third-party servers access their data” Peut être raccourcie ainsi : “This device ensures secure communications, keeping data away from third-party servers.”
Real-world applications of tools like DataShielder demonstrate their importance:
- Protecting professional communications: Lawyers and journalists use encrypted devices to safeguard sensitive exchanges.
- Securing personal data: Activists and whistleblowers rely on tools like DataShielder NFC HSM to prevent unauthorized access to their data.
These examples underscore the necessity of integrating robust encryption into everyday practices to combat digital overreach effectively.
How Other Countries Handle Digital Surveillance Oversight
Different nations employ diverse strategies to balance surveillance and privacy. For instance:
- Germany: The BND (Federal Intelligence Service) operates under strict oversight by a parliamentary committee, ensuring transparency and accountability.
- United States: The NSA’s activities are supervised by the Foreign Intelligence Surveillance Court (FISC), although criticized for limited transparency.
These examples highlight the need for robust mechanisms like France’s CNCTR to ensure checks and balances in intelligence operations.
Legal Challenges
Cases have emerged where GDPR was cited to challenge excessive data retention by intelligence agencies. For example:
- Case X: A journalist successfully sued an agency for retaining personal data without proper justification, leading to partial reforms in data processing rules.
Survey Data: Public Perception of Surveillance
Recent surveys reveal increasing public concern, providing valuable insights into public opinion on government monitoring:
- 56% of respondents believe current practices infringe on privacy rights.
- 72% support stronger oversight mechanisms to ensure accountability.
This data underscores the growing demand for transparency and legal reforms.
A Call for Reflection: French Digital Surveillance and Democracy
French digital surveillance raises pressing questions about the balance between security and privacy. While safeguarding national security is essential, these measures must respect democratic values.
Joseph A. Cannataci, UN Special Rapporteur on Privacy, aptly states:
“Privacy is not something that people can give up; it is a fundamental human right that underpins other freedoms.”
(Source: OHCHR)
Beyond legal and technical considerations, digital surveillance raises profound ethical questions. How do we reconcile collective security with individual freedoms? What is the psychological toll on citizens who feel constantly monitored?
As Benjamin Franklin once remarked, “Those who would give up essential liberty to purchase a little temporary safety, deserve neither liberty nor safety.” This statement remains relevant in discussions about modern surveillance systems and democratic values.
Citizens play a crucial role in shaping the future of surveillance policies. By:
- Following CNCTR reports to stay informed about intelligence practices.
- Using encryption tools like DataShielder to protect their communications.
- Supporting advocacy groups such as La Quadrature du Net, which campaign for greater accountability and transparency.
Together, these actions can create a safer, more transparent digital landscape that respects both security and individual freedoms.
As artificial intelligence and machine learning reshape surveillance, Ethical governance is essential for aligning national security with democratic values. Reforming French digital surveillance policies offers an opportunity to align security practices with transparency and accountability. As a citizen, you can protect your digital privacy by adopting tools like DataShielder. Advocate for stronger oversight by engaging with reports from the CNCTR and supporting initiatives for ethical governance to ensure privacy and security coexist harmoniously in a digital age. Such measures can redefine trust in democratic institutions and set a global benchmark for ethical digital governance.
Salt Typhoon and Flax Typhoon: Security Solutions for Government Agencies Against Cyber Espionage
Salt Typhoon and Flax Typhoon are two related state-sponsored cyber espionage campaigns that pose significant threats to government agencies worldwide. These campaigns, targeting critical infrastructure, highlight the need for effective solutions to protect government communications from cyber espionage. Solutions like DataShielder NFC HSM offer secure encryption to safeguard mobile communications from state-sponsored cyber threats.
Salt Typhoon – The Cyber Threat Targeting Government Agencies
Salt Typhoon and Flax Typhoon represent two related state-sponsored cyber espionage campaigns that have significantly impacted government agencies. These sophisticated attacks utilize advanced phishing, spyware, and zero-day vulnerabilities to infiltrate government systems and steal sensitive data. The growing sophistication of these campaigns highlights the critical need for secure communication solutions like DataShielder NFC HSM.
But what exactly does Salt Typhoon entail, and how did it come to light?
What is Salt Typhoon? A Rising Cybersecurity Threat
This operation poses a serious cyber threat, with advanced espionage tactics aimed directly at government institutions. This operation, linked to state-sponsored actors, has raised significant concerns within U.S. agencies. Recently, officials warned employees to limit mobile phone use due to potential cyber vulnerabilities associated with this attack. For more on this advisory, you can refer to the original Wall Street Journal report, which outlines the severity and implications of Salt Typhoon.
Expanded Scope of Salt Typhoon Attacks
Recent updates confirm that Salt Typhoon has expanded its reach to nine major U.S. telecommunications companies. These include Verizon, AT&T, T-Mobile, and Spectrum. This expansion emphasizes the growing complexity of cyber threats against government communications. It further underscores the need to implement advanced encryption methods to prevent cyber espionage in government communications. This includes private conversations involving political figures, such as staff from the Kamala Harris 2024 presidential campaign and individuals linked to Donald Trump and JD Vance. The targeted information is invaluable. It exposes vulnerabilities at the highest levels of government and politics.
The Federal Communications Commission (FCC) has addressed the expanded scope of these attacks in its official FACT SHEET on the implications of the Salt Typhoon attack and FCC response (FCC Fact Sheet).
Growing Threats to Government Cybersecurity
To understand the scope of Salt Typhoon, it’s crucial to examine what makes it a significant cybersecurity risk. Salt Typhoon represents an organized campaign specifically engineered to penetrate mobile and computer systems within government networks. This threat has been carefully crafted to bypass standard security measures, allowing it to access highly sensitive information. With state-sponsored cyber threats like Salt Typhoon and Flax Typhoon increasing in sophistication, security solutions for government agencies against Salt Typhoon are more critical than ever.
Impact on National Security
The consequences of Salt Typhoon and Flax Typhoon are far-reaching and impact national security at multiple levels. Both cyber espionage campaigns exploit vulnerabilities in government networks, causing substantial damage to critical operations and sensitive data. If sensitive data—such as classified government communications—were exposed, the effects would be devastating. These attacks highlight the urgent need for solutions to protect mobile communications from cyber attacks espionage, especially in critical sectors like telecommunications and government. Furthermore, these operations have demonstrated how attackers can infiltrate secure channels, gaining strategic insights and potentially sabotaging critical diplomatic or security operations.
The Congressional Research Service (CRS) released a report detailing the Salt Typhoon hacks of telecommunications companies and federal response implications, reinforcing the need for stronger protective measures within government networks (CRS Report).
Consequently, the threat posed by Salt Typhoon and Flax Typhoon is immense, as both campaigns target critical infrastructure and government communications. These attacks highlight the need for secure communication methods, especially for mobile communication. Implementing encryption for SMS can prevent interception and protect sensitive data. For more on this, explore our related article on The Critical Need for SMS Encryption here.
Discovery and Origins of Salt Typhoon
Salt Typhoon was uncovered when analysts noticed an unusual surge in phishing attacks targeting high-ranking officials. These attacks targeted high-ranking officials within government agencies, raising red flags across the cybersecurity community. Working together, researchers from top cybersecurity firms and intelligence agencies traced these attacks back to a group suspected to have links with Chinese state operations. The subsequent analysis revealed that Salt Typhoon used a complex mix of tactics—such as zero-day exploits and spyware—to infiltrate systems without detection. But how exactly does Salt Typhoon operate, and what methods does it employ?
Flax Typhoon: A Parallel Threat to Salt Typhoon
In addition to the ongoing Salt Typhoon campaign, Flax Typhoon, a parallel cyber espionage operation, has emerged, targeting U.S. government agencies. Similar to Salt Typhoon, Flax Typhoon also employs advanced phishing techniques, spyware, and zero-day vulnerabilities. While Salt Typhoon targets government agencies directly, Flax Typhoon has extended its reach into telecom networks, adding another layer of complexity to the attack. Moreover, Flax Typhoon extends its reach into telecom companies, amplifying its potential for widespread disruption. According to the U.S. Department of the Treasury, Flax Typhoon is linked to state-sponsored hacking groups and presents a growing threat to national security. Learn more about Flax Typhoon from the official Treasury release here.
How This Threat Operates
Just as Salt Typhoon uses advanced phishing techniques and zero-day exploits, Flax Typhoon has been noted for its exploitation of telecom network vulnerabilities, which significantly increases its scope and potential damage. Here are some of the core techniques behind this attack:
- Advanced Phishing and Smishing: By sending deceptive links through email and SMS, attackers use realistic, spyware-laden messages to deceive officials into clicking harmful links.
- Spyware and Malware Injection: After gaining access, the attack covertly monitors calls, messages, and even device locations, using sophisticated spyware. It even hijacks cameras and microphones to provide real-time surveillance.
- Exploitation of Zero-Day Vulnerabilities: Salt Typhoon leverages unknown system vulnerabilities to access networks secretly, making it nearly impossible for traditional security protocols to detect.
- IMSI Catchers and Network Interception: Using IMSI catchers, Salt Typhoon intercepts mobile communications, allowing attackers to eavesdrop and capture critical data.
Both Salt Typhoon and Flax Typhoon use techniques such as IMSI catchers to intercept mobile communications. These sophisticated attacks emphasize the importance of implementing strong encryption for sensitive data to prevent unauthorized interception by cyber adversaries. To better understand why SMS encryption is critical, read our comprehensive guide on The Critical Need for SMS Encryption here.
Each of these methods showcases the advanced nature of Salt Typhoon, but why are government agencies the primary targets?
Why Government Agencies Are Prime Targets
To counter these growing threats, it’s essential for government agencies to adopt advanced encryption methods for preventing cyber espionage in government communications. The focus on government agencies underscores the sensitive and strategic nature of the data they hold. Attackers aim to capture:
- Confidential Credentials: Stolen login information provides attackers with access to restricted databases and sensitive operational details.
- Real-Time Location Data: Tracking officials’ movements gives attackers critical insights into strategic activities and plans.
- Sensitive Communication Channels: Communications between government officials often contain details on operations and intelligence, making unauthorized access a serious national security risk.
Given the sensitivity of this information, the repercussions of Salt Typhoon on national security are severe. But what could these repercussions look like in practice?
National Security Implications of Salt Typhoon
This cyber campaign doesn’t merely threaten privacy; it impacts national security at multiple levels. Here’s a look at the potential consequences:
Potential Repercussions of a Security Breach
- Exposure of Classified Information: A breach within a government agency could lead to sensitive data leaks, risking public safety and affecting diplomatic relations.
- Interruption of Critical Operations: If attackers gain control over secure communication channels, they could disrupt essential operations, impacting intelligence and diplomacy.
- Loss of Public Confidence: Breaches like Salt Typhoon can erode public trust in the government’s ability to protect information, creating long-term reputational damage.
U.S. Government Response and Sanctions
In response to Salt Typhoon, the U.S. government has sanctioned Integrity Technology Group, a Beijing-based cybersecurity firm allegedly supporting Flax Typhoon and other state-sponsored cyber operations. These sanctions aim to prevent further infiltration into U.S. systems and disrupt the cyber espionage activities linked to Flax Typhoon and Salt Typhoon. These sanctions target entities directly supporting state-sponsored cyber groups engaged in Salt Typhoon and similar attacks. The sanctions aim to disrupt operations and prevent further infiltration into U.S. systems.
However, sanctions alone are insufficient. Government agencies must prioritize securing mobile communications with encryption to better mitigate the risks posed by these state-sponsored cyber attacks. The U.S. Department of the Treasury issued an official statement regarding the sanctions against Integrity Technology Group, emphasizing its role in supporting malicious cyber activities linked to Salt Typhoon (Treasury Sanctions Press Release).
Recognizing these threats, government agencies must adopt robust defense strategies to safeguard against Salt Typhoon. But what solutions are most effective?
Recommended Defense Strategies Against Salt Typhoon
Countering Salt Typhoon demands advanced cybersecurity measures designed to protect against sophisticated threats. This includes implementing solutions for secure communication for government agencies such as DataShielder NFC HSM to combat advanced phishing attacks, spyware, and unauthorized data access. Below are some key strategies for enhancing security within government agencies.
DataShielder NFC HSM – A Key Solution for Secure Communications
One of the most effective solutions is DataShielder NFC HSM, which provides robust encryption for SMS, MMS, RCS, emails, and chat without the need for servers or databases. By utilizing DataShielder NFC HSM Master for advanced encryption or DataShielder NFC HSM Lite for essential encryption, agencies can ensure their data remains secure and anonymous at the source.
For organizations focusing on secure authentication to prevent identity theft, DataShielder NFC HSM Auth offers a reliable solution against AI-assisted identity fraud in workplace settings. Additionally, DataShielder NFC HSM M-Auth is ideal for protecting identity in mobile environments, even when users are on unsecured networks.
For desktop or laptop applications, DataShielder PGP HSM enhances security with strong encryption and secure data transmission when paired with a DataShielder NFC HSM device.
While defensive measures are essential, the global implications of Salt Typhoon also require international collaboration and diplomacy.
Additional Security Measures for Government Agencies
In addition to solutions like DataShielder, agencies can implement further protective practices:
- Limiting Public Wireless Connections: The NSA recommends disabling Wi-Fi, Bluetooth, and GPS services when they are not necessary, to reduce interception risks.
- Regular Security Updates: With Salt Typhoon exploiting zero-day vulnerabilities, frequent updates help close known gaps and protect against attacks.
- Implementing VPNs and Multi-Factor Authentication: Additional layers of security protect devices connected to government networks.
- Cybersecurity Training Programs: Training employees to recognize phishing and smishing attacks reduces the likelihood of human error leading to a breach.
How to Safeguard Against Salt Typhoon
Given the evolving nature of Salt Typhoon, government agencies must adopt more advanced cybersecurity measures to prevent further breaches. Solutions like DataShielder NFC HSM offer essential protection by providing robust encryption for communications, without relying on servers, databases, or user identification. This ensures that government communications remain secure and anonymous.
The National Institute of Standards and Technology (NIST) has provided updated guidelines on securing mobile and network communications, emphasizing the importance of encryption in mitigating risks posed by threats like Salt Typhoon (NIST Cybersecurity Framework).
As Salt Typhoon and Flax Typhoon demonstrate, the importance of adopting advanced cybersecurity measures cannot be overstated. In response to evolving threats, CISA (Cybersecurity and Infrastructure Security Agency) has released comprehensive guidance. This guidance emphasizes key areas such as end-to-end encryption, phishing-resistant multi-factor authentication, and offline functionality. Moreover, these best practices directly align with the secure communication features of DataShielder NFC HSM Defense. This makes it a robust choice for agencies seeking to mitigate such threats.
To enhance your organization’s defense against these cyber espionage campaigns, DataShielder NFC HSM Defense provides critical features aligned with the latest CISA recommendations. Below is a quick overview of how our products match CISA’s guidelines for securing mobile communications.
How CISA Cybersecurity Guidance Supports Secure Messaging Platforms in the Context of Salt Typhoon and Flax Typhoon
As the Salt Typhoon and Flax Typhoon campaigns demonstrate, securing mobile communication systems is essential to defending against state-sponsored cyber threats. In response, the Cybersecurity and Infrastructure Security Agency (CISA) has released comprehensive guidelines. These guidelines emphasize the importance of end-to-end encryption, phishing-resistant multi-factor authentication (MFA), and offline functionality.
These recommendations are especially crucial for organizations in the crosshairs of espionage attacks. This includes government agencies targeted by the Salt Typhoon and Flax Typhoon campaigns. For government agencies under constant threat from cyber espionage campaigns, protecting mobile communications from cyber espionage has never been more important.
| CISA Recommendation | How DataShielder NFC HSM Defense Aligns |
|---|---|
| End-to-End Encryption | Implements AES-256 CBC encryption to secure communications locally before transmission, ensuring they cannot be intercepted. |
| Phishing-Resistant MFA | Replaces vulnerable SMS-based MFA with Zero Trust architecture, offering secure offline authentication. |
| Offline Functionality | Operates fully offline, eliminating vulnerabilities to network-based attacks and phishing. |
| Platform-Specific Compatibility | Fully compatible with Android NFC devices, supporting encrypted DNS and meeting CISA’s security criteria. |
| Sovereign Manufacturing | Designed and manufactured in Europe with STMicroelectronics components, ensuring reliability and trust. |
By incorporating DataShielder NFC HSM Defense into their cybersecurity frameworks, government agencies can enhance their defenses against Salt Typhoon, Flax Typhoon, and similar cyber espionage threats, while adhering to CISA’s recommended security practices.
Explore Official Reports and Recommendations
For further details on CISA’s guidelines and how they address evolving threats like Salt Typhoon, download the official reports:
- CISA Mobile Communications Best Practices Guidance
- FBI-CISA Joint Statement on PRC Cyberespionage
- FCC Fact Sheet on Salt Typhoon
- Salt Typhoon Cyber Threats
DataShielder NFC HSM: Tailored for Strategic and Corporate Needs in the Face of Cyber Espionage
The DataShielder NFC HSM and HSM PGP product line is specifically designed to protect against cyber threats like Salt Typhoon and Flax Typhoon, offering solutions for both civilian and military applications. Whether for government agencies or sovereign institutions, DataShielder provides unmatched security for communications and data.
Explore our Solutions:
- DataShielder NFC HSM Master: Tailored for sovereign institutions and strategic enterprises with AES-256 CBC encryption and offline functionality.
- DataShielder NFC HSM Lite: Perfect for SMEs and businesses needing robust security with easy integration.
- DataShielder NFC HSM Auth & M-Auth: Ideal for secure authentication, including dynamic encryption key management.
Enhanced Security for Sovereign Communications: DataShielder NFC HSM Defense
For highly confidential communications, the DataShielder NFC HSM Defense version provides additional layers of protection. It enables secure phone calls where contacts are stored solely within the NFC HSM, ensuring that call logs, SMS, MMS, and RCS are automatically removed from the device after each call. This level of security is essential for agencies handling classified information, as it leaves no digital trace.
Enhanced Security for Sovereign Communications
For highly confidential communications, the DataShielder NFC HSM Defense version offers additional layers of protection. It enables secure phone calls where contact information is stored exclusively within the NFC HSM, erasing all traces from the device after each call. This feature is crucial for agencies handling classified information, ensuring that no digital footprint remains on mobile devices. The U.S. National Security Agency (NSA) emphasizes the need for such tools to protect national security in the age of cyber espionage (NSA Mobile Security Guidelines).
The Role of Cyberdiplomacy in Countering State-Sponsored Cyber Threats
The attribution of this campaign to a specific nation raises the stakes in global cybersecurity. State-sponsored cyberattacks not only strain diplomatic relations but also create broader geopolitical challenges. As a result, governments must explore cyberdiplomacy to establish boundaries and maintain stability in international relations.
- Cyberdiplomacy’s Role: As cyberattacks like Salt Typhoon increase, governments must negotiate and set international norms to prevent further escalation. Diplomacy plays a vital role in setting boundaries for state-sponsored cyber activities and in addressing breaches collectively.
- Potential Retaliatory Actions: In response to Salt Typhoon and similar attacks, the U.S. may consider diplomatic actions, sanctions, or enhanced security protocols with allied nations. Strengthening cybersecurity collaboration between nations can create a united front against state-backed threats.
The Role of Cyberdiplomacy in Countering State-Sponsored Cyber Threats
As Salt Typhoon exemplifies, the attribution of cyber-attacks to specific nation-states has far-reaching geopolitical consequences. Consequently, this situation has prompted the need for cyberdiplomacy—the negotiation of international norms and responses to state-sponsored cyber threats. Countries, including the U.S., must work together to prevent further escalation of cyber espionage and protect critical infrastructure from foreign interference.
The United Nations has addressed cyber norms in the context of international peace and security, proposing frameworks for the protection of sensitive national assets (UN Cybersecurity).
To understand the full impact of Salt Typhoon, it’s helpful to compare it to other notorious spyware, such as Pegasus and Predator.
Salt Typhoon Compared to Other Spyware Threats
The techniques used in this cyber operation mirror those of other infamous spyware programs, including Pegasus and Predator. These tools have been used globally for high-stakes espionage and provide insights into the dangers of state-sponsored cyber threats.
Pegasus and Predator – Similar Threats and Their Impacts
Similar to other notorious spyware programs like Pegasus, Flax Typhoon and Salt Typhoon employ advanced techniques to infiltrate devices and networks. These state-sponsored cyber attacks leverage zero-day vulnerabilities and targeted phishing, making them especially difficult to detect.
- Pegasus: This powerful spyware infiltrates devices to monitor calls, messages, and even activate cameras for surveillance. Pegasus has compromised numerous high-profile targets. Learn more about Pegasus’s reach here.
- Predator: Similar to Pegasus, Predator has been linked to espionage campaigns threatening both government and private sectors. Predator’s methods and risks are detailed in our guide here.
These examples underscore the need for advanced encryption solutions like DataShielder NFC HSM, which offers anonymity and security essential for protecting government communications from surveillance threats.
Building a Proactive Defense Against Salt Typhoon
The Salt Typhoon campaign highlights the urgent need for a robust cybersecurity framework. By adopting solutions like DataShielder NFC HSM, government agencies can secure their communications from sophisticated threats. Furthermore, this solution also incorporates CISA’s encryption and MFA guidelines, ensuring compliance with national and international standards.
As state-sponsored cyber espionage campaigns continue to evolve, maintaining proactive defense systems is essential. These systems are crucial for safeguarding critical infrastructure and national security.
For a deeper understanding of mobile cyber threats, explore our full guide on Mobile Cyber Threats in Government Security. It also covers effective measures for enhancing government security practices.
As state-sponsored cyber espionage campaigns like Salt Typhoon and Flax Typhoon continue to evolve, government agencies must prioritize robust cybersecurity frameworks. These frameworks are essential to protect critical infrastructure and national security.
Mobile Cyber Threats in Government Agencies by Jacques Gascuel: This subject will be updated with any new information on mobile cyber threats and secure communication solutions for government agencies. Readers are encouraged to leave comments or contact the author with suggestions or additions.
Protecting Government Mobile Communications Against Cyber Threats like Salt Typhoon
Mobile Cyber Threats like Salt Typhoon are increasingly targeting government agencies, putting sensitive data at risk. This article explores the rising risks for mobile security and explains how DataShielder NFC HSM offers a robust, anonymous encryption solution to protect government communications and combat emerging cyber threats.
US Gov Agency Urges Employees to Limit Mobile Use Amid Growing Cyber Threats
Reports indicate that the U.S. government’s Consumer Financial Protection Bureau (CFPB) has directed its employees to minimize the use of cellphones for work-related activities. This advisory follows recent cyber threats, particularly the “Salt Typhoon” attack, allegedly conducted by Chinese hackers. Although no direct threat to the CFPB has been confirmed, this recommendation highlights vulnerabilities in mobile communication channels and the urgent need for federal agencies to prioritize secure communication methods. For more details, you can refer to the original article from The Wall Street Journal: (wsj.com).
Mobile Cyber Threats: A Growing Risk for Government Institutions
Cyberattacks targeting government employees’ smartphones and tablets are rising, with mobile devices providing a direct gateway to sensitive information. The Salt Typhoon attack serves as a recent example of these risks, but various other espionage campaigns also target mobile vulnerabilities in government settings. Given these threats, the CFPB is now advising employees to limit mobile use and to prioritize more secure platforms for communication.
Focus on Government Employees as Cyberattack Targets
Government employees, especially those with access to confidential data, are prime targets for cybercriminals. These individuals often handle sensitive information, making their devices and accounts particularly appealing. Attacks like Salt Typhoon seek to access:
- Login Credentials: Stolen credentials can provide direct access to restricted databases and communication channels, leading to potentially devastating breaches.
- Location Data: Tracking government employees’ locations in real-time offers strategic information about operations and movements, which is especially valuable for foreign intelligence.
- Sensitive Communications: Intercepting messages between government employees can expose classified information, disrupt operations, or provide insight into internal discussions.
Past cases demonstrate the real-world impact of such cyberattacks. For instance, a 2015 breach targeted the U.S. Office of Personnel Management (OPM), compromising personal information of over 20 million current and former federal employees. This breach revealed details such as employees’ job histories, fingerprints, and social security numbers, underscoring the security risks government personnel face.
Key Cyber Threats Facing Mobile Devices
- Phishing and Mobile Scams: Cybercriminals increasingly use SMS phishing (smishing) and other tactics to lure government employees into revealing sensitive information or unknowingly installing spyware.
- Spyware and Malicious Apps: Tools like Pegasus spyware have demonstrated the capability to access private calls, messages, and even activate cameras and microphones to monitor private communications.
- Exploiting System Flaws and Zero-Day Vulnerabilities: Hackers exploit unpatched vulnerabilities in operating systems to covertly install malware on devices.
- Network Attacks and IMSI Catchers: Fake cell towers (IMSI catchers) allow cybercriminals to intercept calls and messages near the target, compromising sensitive information.
- Bluetooth and Wi-Fi Interception: Public Wi-Fi and Bluetooth connections are particularly vulnerable to interception, especially in public or shared spaces, where attackers can access devices.
Notorious Spyware Threats: Pegasus and Predator
Beyond targeted cyberattacks like Salt Typhoon, sophisticated spyware such as Pegasus and Predator pose severe threats to government agencies and individuals responsible for sensitive information. These advanced spyware tools enable covert surveillance, allowing attackers to intercept valuable data without detection.
- Pegasus: This spyware is one of the most powerful and notorious tools globally, widely known for its capabilities to infiltrate smartphones and monitor high-stakes targets. Pegasus can access calls, messages, and even activate the camera and microphone of infected devices, making it a potent tool in espionage. Learn more about Pegasus’s extensive reach and impact in our in-depth article: Pegasus – The Cost of Spying with One of the Most Powerful Spyware in the World.
- Predator: Like Pegasus, Predator has been employed in covert surveillance campaigns that threaten both governmental and private sector security. This spyware can capture and exfiltrate data, offering attackers a silent but powerful tool for gathering sensitive information. To understand the risks associated with Predator, visit our detailed guide: Predator Files Spyware.
These examples underscore the urgent need for robust encryption solutions. Spyware like Pegasus and Predator make it clear that advanced security tools, such as DataShielder NFC HSM, are essential. DataShielder offers an anonymous, fully encrypted communication platform that protects against sophisticated surveillance, ensuring that sensitive data remains secure and beyond reach.
Impacts on National Security and the Role of Cybersecurity
Cybersecurity failures in government agencies can have serious national security repercussions. The potential consequences underscore the importance of cybersecurity for sensitive government communications.
- Repercussions of a Security Breach: A security breach within a government agency can lead to the disclosure of confidential information, impact diplomatic relations, or even compromise critical negotiations. In some cases, such breaches can disrupt operations or expose weaknesses within government structures. A major breach could also undermine the public’s trust in the government’s ability to safeguard national interests.
- New Cybersecurity Standards and Policies: In response to increasing threats, federal agencies may adopt stricter policies. This can include expanded training programs for employees, emphasizing vigilance in detecting phishing attempts and other suspicious activity. Agencies may also implement policies restricting the use of personal devices for work tasks and investing in stronger security frameworks. By enforcing such policies, agencies aim to create a more resilient defense against sophisticated cyber threats.
Statistics: The Rise of Mobile Cyber Threats
Recent data highlights the scale of mobile cyber threats and the importance of robust security measures:
- Increase in Mobile Phishing Attacks: According to the National Institute of Standards and Technology (NIST), mobile phishing attacks rose by 85% between 2020 and 2022, with smishing campaigns increasingly targeting government employees to infiltrate networks. (NIST Source)
- Zero-Day Vulnerabilities: The National Security Agency (NSA) reports a 200% increase in zero-day vulnerability exploitation on mobile devices over the past five years. These flaws enable hackers to infiltrate devices undetected. (NSA Security Guidance)
- Spyware and Surveillance: The use of spyware for surveillance in government settings has tripled since 2019. Tools like Pegasus enable hackers to capture calls and messages, threatening confidentiality. (NIST Mobile Security)
- Centralized Device Management: NIST recommends centralized management of devices within agencies, securing both issued and personal devices. This approach reportedly reduced mobile security incidents by 65% in 2022.
- Financial Impact of Mobile Cyberattacks: According to Cybersecurity Ventures, mobile cyberattacks are expected to cost organizations around $1.5 billion per year by 2025, covering data repair, breach management, and information loss.
Security Guidelines from the NSA and NIST
To address these threats, agencies like the NSA and NIST recommend critical security practices:
- NSA: Disabling Wi-Fi, Bluetooth, and location services when not in use reduces risks from vulnerable wireless connections. (NSA Security Guidance)
- NSA – Securing Wireless Devices in Public Settings: This guide explains how to identify risky public connections and secure devices in public spaces.
- NIST: NIST suggests centralized device management and enforces regular security updates for work and personal devices used in agencies. (NIST Mobile Security Guide)
DataShielder NFC HSM: A Comprehensive Solution for Secure, Anonymous Communication
In response to escalating mobile cyber threats, government agencies are prioritizing more secure communication methods. Traditional security measures often rely on servers or cloud storage, which can be vulnerable to interception or data breaches. DataShielder NFC HSM provides a breakthrough solution tailored specifically to meet the stringent security and privacy needs of sensitive government communications.
DataShielder NFC HSM Products for Android Devices
- DataShielder NFC HSM Master: Provides robust encryption for emails, files, and secure communications on mobile and desktop platforms, protecting against brute force attacks and espionage.
- DataShielder NFC HSM Lite: Offers essential encryption capabilities for secure communications, balancing security and usability.
- DataShielder NFC HSM Auth: Prevents identity theft and AI-assisted fraud, offering secure, anonymous authentication.
- DataShielder NFC HSM M-Auth: Designed for secure authentication in mobile environments, keeping mobile communications protected in less secure networks.
Enhanced Security for Sovereign Communications: DataShielder NFC HSM Defense
The DataShielder NFC HSM Defense version enables secure phone calls where contacts are stored solely within the NFC HSM, ensuring no traces of call logs, SMS, MMS, or RCS remain on the device after use. This feature is invaluable for agencies handling highly confidential information.
How to Shield Your Digital Life from Keystroke Loggers: An Expert’s Guide
Defending Against Keyloggers is essential to protect your sensitive data. Keyloggers are silent tools that record every keystroke, exposing sensitive data to cyber threats. This guide explores high-profile breaches, innovative attack methods, and strategic defenses. It offers a comprehensive strategy to secure your sensitive data against these ubiquitous threats and provides effective solutions for enhanced protection. Stay informed and proactive with our expert advice in the constantly evolving cybersecurity landscape.
FAQ
What’s the Difference Between Software and Hardware Keyloggers?
Software keyloggers
These programs run discreetly in the background of the computer, recording every keystroke. They can be installed through malware or accidentally downloaded together with other applications. These keyloggers can not only capture keystrokes but also record screenshots and monitor internet activity.
Hardware keyloggers
These devices are usually small physical devices that connect between the keyboard and the computer’s USB or PS/2 port. They log keystrokes directly from the keyboard before the information is transmitted to the operating system. Their physical presence makes them detectable by visual inspection, but they are often very discreet and difficult to notice.
Is a keylogger a virus?
No, keyloggers are tools that can be used for both legitimate monitoring and malicious activities.
How do I know if I am infected with a keylogger?
Regular scans with updated antivirus software and monitoring for unusual system behavior are effective detection methods.
Can mobile devices get infected with keyloggers?
Although less common, mobile devices can indeed be compromised by keyloggers, especially through malicious apps or compromised security software.
What is the best way to protect my devices from keyloggers?
Using comprehensive security solutions like PassCypher and maintaining vigilant cybersecurity practices are your best defenses.
What are the best immediate actions to take if a keylogger is detected?
Disconnect from the internet, change all passwords on a secure device, and use a trusted malware removal tool to clean the infected system.
What is the difference between software and hardware keyloggers?
Software keyloggers
These programs run discreetly in the background of the computer, recording every keystroke. They can be installed through malware or accidentally downloaded together with other applications. These keyloggers can not only capture keystrokes but also record screenshots and monitor internet activity.
Hardware keyloggers
These devices are usually small physical devices that connect between the keyboard and the computer’s USB or PS/2 port. They log keystrokes directly from the keyboard before the information is transmitted to the operating system. Their physical presence makes them detectable by visual inspection, but they are often very discreet and difficult to notice.
How can I detect a keylogger on my computer?
Detection of software keyloggers:
- Use of antivirus and anti-malware software: Make sure your security software is up to date and perform regular scans. Many modern security software programs are equipped to detect keyloggers.
- System Process Monitoring: Use the Task Manager to monitor running processes. Unknown or suspicious processes that use high resources can be signs of a keylogger.
- Checking startup programs: Review the programs that launch when your computer starts. Keyloggers can set up an auto-start to stay active.
Hardware Keylogger Detection:
- Physical inspection: Regularly check the connections between your keyboard and your computer. Look for any unusual devices plugged into the USB or PS/2 port where the keyboard connects.
- Check for unknown devices: Monitor your device manager for any unknown or unrecognized hardware that might be connected to your system.
What are the best practices to protect against keyloggers?
Use our password management software
PassCypher HSM PGP in its free or advanced version or hardware version with PassCyppher NFC HSM to secure your NFC Android phone as well
Robust security
Install and maintain trusted antivirus software that includes protection against keyloggers.
Update your operating system and applications
Regular updates often fix security vulnerabilities that could be exploited by keyloggers.
Be careful with downloads
Avoid downloading software from unverified sources. Favor the official websites of the publishers to reduce the risk of downloading malicious applications.
Education and awareness
Learn how to recognize phishing attempts and other techniques used to install keyloggers. Don’t click on suspicious links or attachments in emails or messages.
Use of password managers
Password managers can autofill your login information without you having to hit the keys, reducing the risks associated with software keyloggers.
Multi-factor authentication (MFA)
Use PassCypher NFC HSM also handles 2FA/MFA OTP two-factor authentication keys (TOTP and HOTP) when possible, especially for important accounts like email and bank accounts. This adds an extra layer of security that doesn’t rely solely on passwords.
Use robust security software
Install and maintain trusted antivirus software that includes protection against keyloggers.
Update your operating system and applications
Regular updates often fix security vulnerabilities that could be exploited by keyloggers.
Be careful with downloads
Avoid downloading software from unverified sources. Favor the official websites of the publishers to reduce the risk of downloading malicious applications.
Education and awareness
Learn how to recognize phishing attempts and other techniques used to install keyloggers. Don’t click on suspicious links or attachments in emails or messages.
Use of password managers
Password managers can autofill your login information without you having to hit the keys, reducing the risks associated with software keyloggers.
Software keyloggers
These programs run discreetly in the background of the computer, recording every keystroke. They can be installed through malware or accidentally downloaded together with other applications. These keyloggers can not only capture keystrokes but also record screenshots and monitor internet activity.
Hardware keyloggers
These devices are usually small physical devices that connect between the keyboard and the computer’s USB or PS/2 port. They log keystrokes directly from the keyboard before the information is transmitted to the operating system. Their physical presence makes them detectable by visual inspection, but they are often very discreet and difficult to notice.
No, keyloggers are tools that can be used for both legitimate monitoring and malicious activities.
Regular scans with updated antivirus software and monitoring for unusual system behavior are effective detection methods.
Although less common, mobile devices can indeed be compromised by keyloggers, especially through malicious apps or compromised security software.
Using comprehensive security solutions like PassCypher and maintaining vigilant cybersecurity practices are your best defenses.
Disconnect from the internet, change all passwords on a secure device, and use a trusted malware removal tool to clean the infected system.
Software keyloggers
These programs run discreetly in the background of the computer, recording every keystroke. They can be installed through malware or accidentally downloaded together with other applications. These keyloggers can not only capture keystrokes but also record screenshots and monitor internet activity.
Hardware keyloggers
These devices are usually small physical devices that connect between the keyboard and the computer’s USB or PS/2 port. They log keystrokes directly from the keyboard before the information is transmitted to the operating system. Their physical presence makes them detectable by visual inspection, but they are often very discreet and difficult to notice.
Detection of software keyloggers:
- Use of antivirus and anti-malware software: Make sure your security software is up to date and perform regular scans. Many modern security software programs are equipped to detect keyloggers.
- System Process Monitoring: Use the Task Manager to monitor running processes. Unknown or suspicious processes that use high resources can be signs of a keylogger.
- Checking startup programs: Review the programs that launch when your computer starts. Keyloggers can set up an auto-start to stay active.
Hardware Keylogger Detection:
- Physical inspection: Regularly check the connections between your keyboard and your computer. Look for any unusual devices plugged into the USB or PS/2 port where the keyboard connects.
- Check for unknown devices: Monitor your device manager for any unknown or unrecognized hardware that might be connected to your system.
Use our password management software
PassCypher HSM PGP in its free or advanced version or hardware version with PassCyppher NFC HSM to secure your NFC Android phone as well
Robust security
Install and maintain trusted antivirus software that includes protection against keyloggers.
Update your operating system and applications
Regular updates often fix security vulnerabilities that could be exploited by keyloggers.
Be careful with downloads
Avoid downloading software from unverified sources. Favor the official websites of the publishers to reduce the risk of downloading malicious applications.
Education and awareness
Learn how to recognize phishing attempts and other techniques used to install keyloggers. Don’t click on suspicious links or attachments in emails or messages.
Use of password managers
Password managers can autofill your login information without you having to hit the keys, reducing the risks associated with software keyloggers.
Multi-factor authentication (MFA)
Use PassCypher NFC HSM also handles 2FA/MFA OTP two-factor authentication keys (TOTP and HOTP) when possible, especially for important accounts like email and bank accounts. This adds an extra layer of security that doesn’t rely solely on passwords.
Use robust security software
Install and maintain trusted antivirus software that includes protection against keyloggers.
Update your operating system and applications
Regular updates often fix security vulnerabilities that could be exploited by keyloggers.
Be careful with downloads
Avoid downloading software from unverified sources. Favor the official websites of the publishers to reduce the risk of downloading malicious applications.
Education and awareness
Learn how to recognize phishing attempts and other techniques used to install keyloggers. Don’t click on suspicious links or attachments in emails or messages.
Use of password managers
Password managers can autofill your login information without you having to hit the keys, reducing the risks associated with software keyloggers.
Electronic Warfare in Military Intelligence by Jacques gascuel I will keep this article updated with any new information, so please feel free to leave comments or contact me with suggestions or additions.his article will be updated with any new information on the topic, and readers are encouraged to leave comments or contact the author with any suggestions or additions.
The Often Overlooked Role of Electronic Warfare in Military Intelligence
Electronic Warfare in Military Intelligence has become a crucial component of modern military operations. This discipline discreetly yet vitally protects communications and gathers strategic intelligence, providing armed forces with a significant tactical advantage in an increasingly connected world.
Historical Context: The Evolution of Electronic Warfare in Military Intelligence
From as early as World War II, electronic warfare established itself as a critical strategic lever. The Allies utilized jamming and interception techniques to weaken Axis forces. This approach was notably applied through “Operation Ultra,” which focused on deciphering Enigma messages. During the Cold War, major powers refined these methods. They incorporated intelligence and countermeasures to secure their own networks.
Today, with rapid technological advancements, electronic warfare combines state-of-the-art systems with sophisticated intelligence strategies. It has become a cornerstone of modern military operations.
These historical foundations underscore why electronic warfare has become indispensable. Today, however, even more advanced technologies and strategies are essential to counter new threats.
Interception and Monitoring Techniques in Electronic Warfare for Military Intelligence
In military intelligence, intercepting enemy signals is crucial. France’s 54th Electronic Warfare Regiment (54e RMRT), the only regiment dedicated to electronic warfare, specializes in intercepting adversary radio and satellite communications. By detecting enemy frequencies, they enable the armed forces to collect critical intelligence in real time. This capability enhances their ability to anticipate enemy actions.
DataShielder NFC HSM Master solutions bolster these capabilities by securing the gathered information with Zero Trust and Zero Knowledge architecture. This ensures the confidentiality of sensitive data processed by analysts in the field.
Current technological advancements paired with electronic warfare also spotlight the modern threats that armed forces must address.
Emerging Technologies and Modern Threats
Electronic warfare encompasses interception, jamming, and manipulation of signals to gain a strategic edge. In a context where conflicts occur both on the ground and in the invisible spheres of communications, controlling the electromagnetic space has become essential. Powers such as the United States, Russia, and China invest heavily in these technologies. This investment serves to disrupt enemy communications and safeguard their own networks.
Recent conflicts in Ukraine and Syria have highlighted the importance of these technologies in disrupting adversary forces. Moreover, new threats—such as cyberattacks, drones, and encrypted communications—compel armies to innovate. Integrating artificial intelligence (AI) and 5G accelerates these developments. DataShielder HSM PGP Encryption meets the need for enhanced protection by offering robust, server-free encryption, ideal for high-security missions where discretion is paramount.
While these technological advancements are crucial, they also pose complex challenges for the military and engineers responsible for their implementation and refinement.
Change to: Challenges of Electronic Warfare in Military Intelligence: Adaptation and Innovation
Despite impressive advancements, electronic warfare must continually evolve. The rapid pace of innovation renders cutting-edge equipment quickly obsolete. This reality demands substantial investments in research and development. It also requires continuous training for electronic warfare specialists.
DataShielder products, such as DataShielder NFC HSM Auth, play a pivotal role in addressing these challenges. For instance, NFC HSM Auth provides secure, anonymous authentication, protecting against identity theft and AI-assisted threats. By combining advanced security with ease of use, these solutions facilitate adaptation to modern threats while ensuring the protection of sensitive information.
These advances pave the way for emerging technologies, constantly reshaping the needs and methods of electronic warfare.
Analyzing Emerging Technologies: The Future of Electronic Warfare
Integrating advanced technologies like AI is vital for optimizing electronic warfare operations. AI automates interception and jamming processes, increasing military system responsiveness. DataShielder NFC HSM Auth fits seamlessly into this technological environment by protecting against identity theft, even when AI is involved. Post-quantum cryptography and other advanced security techniques in the DataShielder range ensure lasting protection against future threats.
To better understand the real-world application of these technologies, insights from field experts are essential.
Case Studies and Operational Implications: The Testimony of Sergeant Jérémy
Insights from the Field: The Realities of Electronic Warfare Operations
In the field of electronic warfare, the testimony of Sergeant Jérémy, a member of the 54th Transmission Regiment (54e RMRT), provides a deeper understanding of the challenges and operational reality of a job that is both technical, discreet, and demanding. Through his accounts of operations in Afghanistan, Jérémy illustrates how electronic warfare can save lives by providing essential support to ground troops.
Real-Time Threat Detection and Protection in Combat Zones
During his mission in Afghanistan, at just 19, Jérémy participated in radiogoniometry operations, identifying the location of electromagnetic emissions. In one convoy escort mission, his equipment detected signals from enemy forces, indicating a potential ambush. Thanks to this detection, he alerted his patrol leader, allowing the convoy to take defensive measures. This type of mission demonstrates how electronic warfare operators combine technical precision and composure to protect deployed units.
Tactical Jamming and Strategic Withdrawals
In another operation, Jérémy and his team helped special forces withdraw from a combat zone by jamming enemy communications. This temporary disruption halted adversary coordination, giving allied troops the necessary time to retreat safely. However, this technique is not without risks: while crucial, jamming also prevents allied forces from communicating, adding complexity and stress for operators. This mission underscores the delicate balance between protecting allies and disorganizing the enemy, a daily challenge for electronic warfare specialists.
The Role of Advanced Equipment in Electronic Warfare Missions
On missions, the 54e RMRT uses advanced interception, localization, and jamming equipment. These modern systems, such as radiogoniometry and jamming devices, have become essential for the French Army in electronic intelligence and neutralizing adversary communications. However, these missions are physically and psychologically demanding, requiring rigorous training and a capacity to work under high pressure. Sergeant Jérémy’s testimony reminds us of the operational reality behind each technology and demonstrates the rigor with which electronic warfare operators must adapt and respond.
To listen to the complete testimony of Sergeant Jérémy and learn more about his journey, you can access the full podcast here.
Examining the methods of other nations also reveals the varied approaches to electronic warfare.
International Military Doctrines in Electronic Warfare for Military Intelligence
Military doctrines in electronic warfare vary from one country to another. For example, the United States integrates electronic warfare and cyber operations under its “multi-domain operations.” Meanwhile, Russia makes electronic warfare a central element of hybrid operations, combining jamming, cyberattacks, and disinformation. This diversity shows how each country adapts these technologies based on its strategic goals and specific threats.
The growing importance of electronic warfare is also reflected in international alliances, where cooperation is essential to address modern threats.
NATO’s Role in Electronic Warfare
Electronic warfare is also crucial for military alliances such as NATO. Multinational exercises allow for testing and perfecting electronic warfare capabilities, ensuring that allied forces can protect their communications and disrupt those of the enemy. This cooperation strengthens the effectiveness of electronic warfare operations. It maximizes the resilience of allied networks against modern threats.
Recent events demonstrate how electronic warfare continues to evolve to meet the demands of modern battlefields.
Recent Developments in Electronic Warfare
In 2024, the U.S. military spent $5 billion on improving electronic warfare capabilities, notably during the Valiant Shield 2024 exercise. During this event, innovative technologies like DiSCO™ (Distributed Spectrum Collaboration and Operations) were tested. This technology enables real-time spectrum data sharing for the rapid reprogramming of electronic warfare systems. These developments highlight the growing importance of spectral superiority in modern conflicts.
In Ukraine, electronic warfare allowed Russian forces to jam communications and simulate signals to disorient opposing units. This capability underscores the need to strengthen GPS systems and critical communications.
In response to these developments, advanced technological solutions like those of DataShielder provide concrete answers.
Integrating DataShielder Solutions
In the face of rising identity theft and AI-assisted cyber espionage threats, innovative solutions like DataShielder NFC HSM Auth and DataShielder HSM PGP Encryption have become indispensable. Each DataShielder device operates without servers, databases, or user accounts, enabling end-to-end anonymity in real time. By encrypting data through a segmented AES-256 CBC, these products ensure that no trace of sensitive information remains on NFC-enabled Android phones or computers.
- DataShielder NFC HSM Master: A robust counter-espionage tool that provides AES-256 CBC encryption with segmented keys, designed to secure communications without leaving any traces.
- DataShielder NFC HSM Auth: A secure authentication module essential for preventing identity theft and AI-assisted fraud in high-risk environments.
- DataShielder NFC HSM Starter Kit: This all-in-one kit offers complete data security with real-time, contactless encryption and authentication, ideal for organizations seeking to implement comprehensive protection from the outset.
- DataShielder NFC HSM M-Auth: A flexible solution for mobile authentication, enabling secure identity verification and encryption without dependence on external networks.
- DataShielder PGP HSM Encryption: Offering advanced PGP encryption, this tool ensures secure communication even in compromised network conditions, making it ideal for sensitive exchanges.
By leveraging these solutions, military intelligence and high-security organizations can securely encrypt and authenticate communications. DataShielder’s technology redefines how modern forces protect themselves against sophisticated cyber threats, making it a crucial component in electronic warfare.
The convergence between cyberwarfare and electronic warfare amplifies these capabilities, offering new opportunities and challenges.
Cyberwarfare and Electronic Warfare in Military Intelligence: A Strategic Convergence
Electronic warfare operations and cyberattacks, though distinct, are increasingly interconnected. While electronic warfare neutralizes enemy communications, cyberattacks target critical infrastructure. Together, they create a paralyzing effect on adversary forces. This technological convergence is now crucial for modern armies. Products like DataShielder NFC HSM Master and DataShielder HSM PGP Encryption guarantee secure communications against combined threats.
This convergence also raises essential ethical and legal questions for states.
Legal and Ethical Perspectives on Electronic Warfare
With its growing impact, electronic warfare raises ethical and legal questions. Should international conventions regulate its use? Should new laws be created to govern the interception and jamming of communications? These questions are becoming more pressing as electronic warfare technologies improve.
In this context, the future of electronic warfare points toward ever more effective technological innovations.
Looking Ahead: New Perspectives for Electronic Warfare in Military Intelligence
The future of electronic warfare will be shaped by AI integration and advanced cryptography—key elements for discreet and secure communications. DataShielder NFC HSM Master and DataShielder HSM PGP Encryption are examples of modern solutions. They ensure sensitive data remains protected against interception, highlighting the importance of innovation to counter emerging threats.