Coinbase blockchain hack by Jacques Gascuel: This article will be updated with any new information on the topic.
The Crypto Nightmare
Imagine waking up one day and finding out that your hard-earned cryptocurrencies have been stolen by hackers who exploited a flaw in the blockchain platform you trusted. That’s what happened to thousands of users of Coinbase, one of the largest and most popular crypto platforms in the world, in August 2023. In this article, we will explain how this hack occurred, what were its consequences.
2026 Digital Security
January 23, 2026
2026 Digital Security
January 17, 2026
2026 Digital Security
January 8, 2026
2026 Digital Security
January 7, 2026
2025 Digital Security
January 6, 2026
2026 Digital Security
January 5, 2026
2025 Digital Security
January 5, 2026
2025 Digital Security
December 21, 2025
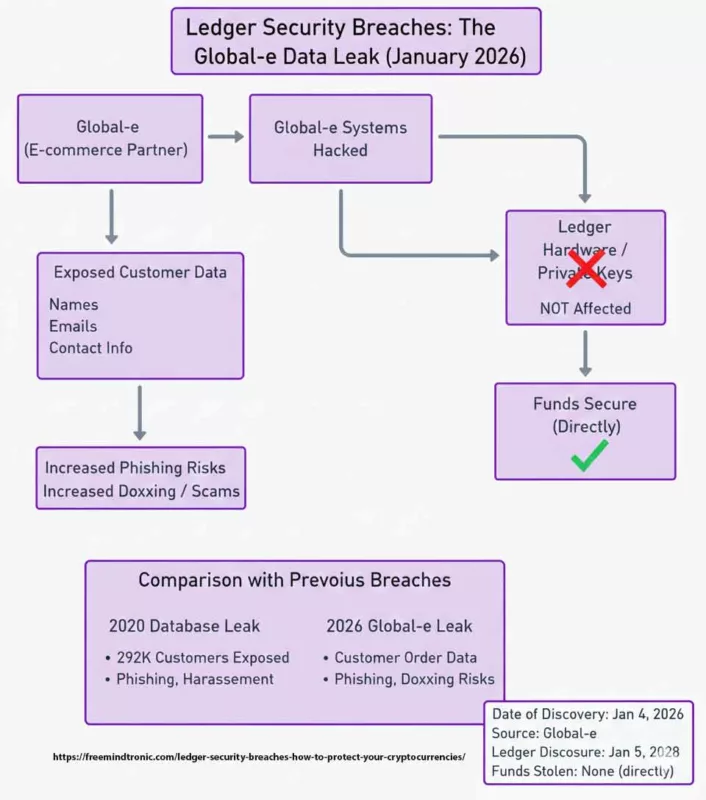
How to Prevent Coinbase Blockchain Hack with EviVault NFC HSM Technology
What happened to Coinbase Chain?
The hack and its consequences
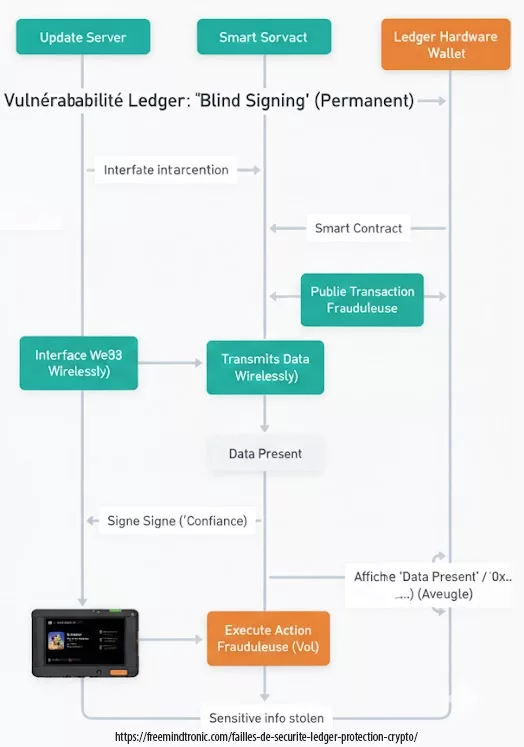
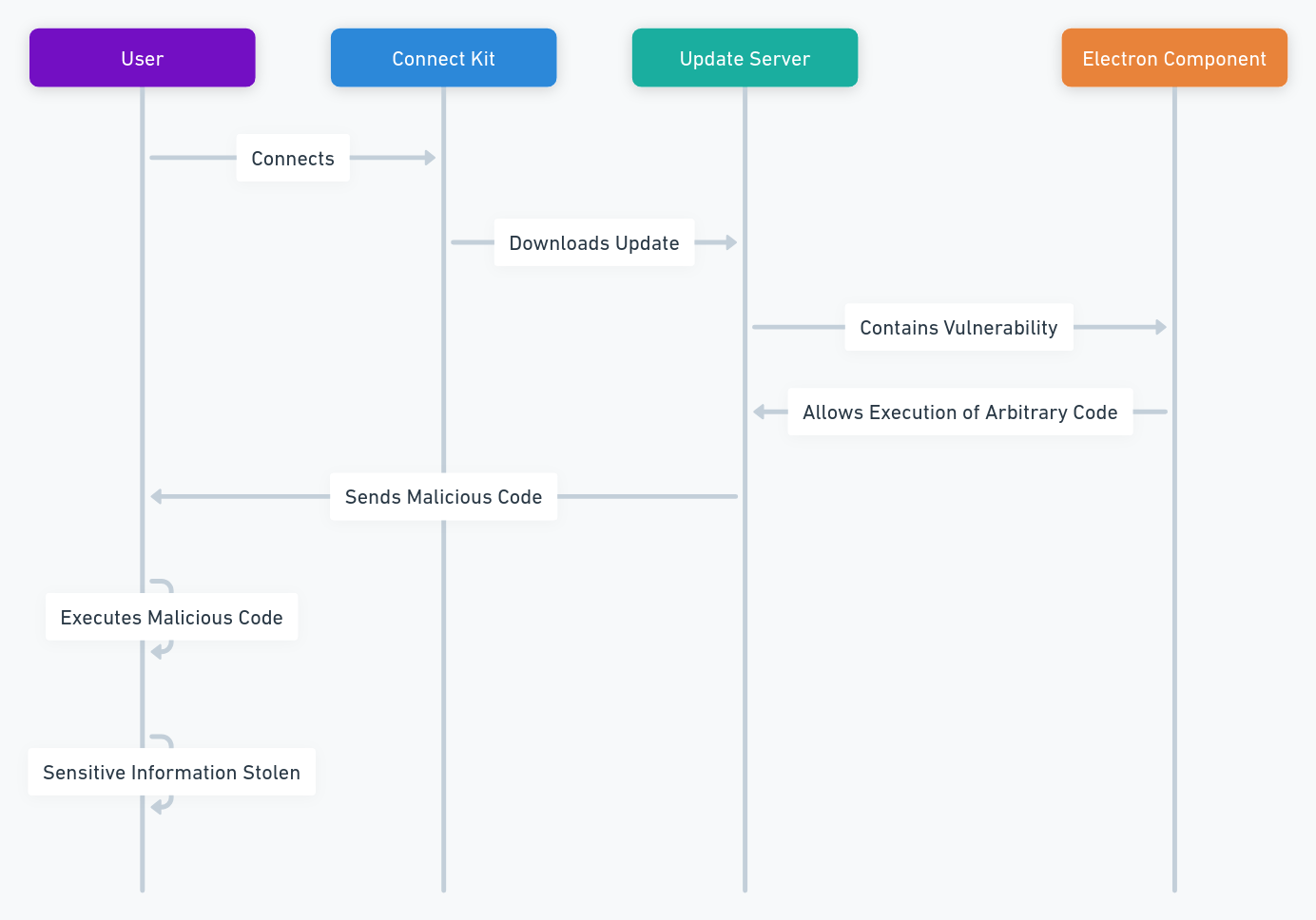
On August 5, 2023, Coinbase announced that it had been the victim of a massive hack that compromised its decentralized blockchain, resulting in the loss of more than $200 million worth of cryptocurrencies. The hackers exploited a flaw in the consensus protocol of the chain, which used a proof-of-stake (PoS) mechanism. By creating fake proofs of stake, the hackers controlled more than 51% of the computing power of the network. This allowed them to alter the transaction history and steal the funds from the users.
This hack is one of the largest and most sophisticated in the history of cryptocurrencies. It exposes the risks and challenges associated with the security of decentralized blockchains, which rely on the trust of the users and the verification of the transactions by the nodes of the network. Some experts say the hack of Coinbase Chain could damage the reputation and credibility of Coinbase, as well as the confidence of the investors and regulators in cryptocurrencies in general.
The response and the apology
Coinbase reacted quickly and took steps to stop the hack, identify the culprits, reimburse the victims and improve the security of its blockchain. Coinbase promised to reimburse all the users affected by the hack within 30 days and to strengthen the security of its decentralized blockchain. The company also apologized to its customers and to the crypto community for this incident.
Coinbase also announced that it would launch a bug bounty program to reward anyone who finds and reports vulnerabilities in its systems or products. The company said that it would pay up to $1 million for critical bugs that could compromise its platform or users’ funds. Coinbase also encouraged its users to enable two-factor authentication (2FA) and use hardware wallets or cold storage devices to protect their cryptocurrencies.
What is proof-of-stake (PoS) and how was it hacked?
The concept of PoS
Proof-of-stake (PoS) is a type of consensus mechanism or protocol that uses the amount of stake (or value) held in the system to determine consensus. In essence, a consensus protocol is what controls the laws and parameters governing the behavior of blockchains. Think of consensus as a ruleset that each network participant adheres to.
In PoS, the nodes of the network commit “stakes” of tokens for a set period of time in exchange for a chance at being selected to produce the next block of transactions. The selection process is usually random, but weighted by the size of the stake. The more tokens a node stakes, the higher its probability of being chosen as a block producer. The block producer then validates the transactions and broadcasts them to the rest of the network. The other nodes check the validity of the block and vote on whether to accept it or not. If a majority of nodes agree on the block, it is added to the blockchain and the block producer receives a reward in the form of transaction fees or newly minted tokens.
The advantages of PoS
PoS is designed to be more secure, efficient, and scalable than proof-of-work (PoW), which is another type of consensus mechanism that requires nodes to solve complex mathematical problems to produce blocks. PoW consumes a lot of energy and computing power, which makes it vulnerable to attacks and environmental issues. PoS, on the other hand, relies on economic incentives rather than computational resources, which makes it more eco-friendly and resistant to attacks.
The vulnerability of PoS
However, PoS is not immune to hacking, as demonstrated by the recent incident involving Coinbase Chain, a decentralized blockchain project launched by Coinbase, one of the largest and most popular cryptocurrency platforms in the world. According to a report published by Coinbase, hackers exploited a flaw in the consensus protocol of Coinbase Chain, which used a PoS mechanism. By creating fake proofs of stake, they controlled more than 51% of the computing power of the network. This allowed them to alter the transaction history and steal funds from users.
The flaw in Coinbase Chain’s consensus protocol was related to how it handled forks, which are splits in the blockchain caused by conflicting versions of blocks. Normally, when a fork occurs, the network follows the longest chain, which is assumed to be the most valid one. However, in Coinbase Chain’s case, the hackers created a longer chain by generating fake proofs of stake and tricking the network into accepting their version of blocks. This way, they reversed or modified previous transactions and double-spent their coins.
This hack shows that PoS is not foolproof and that it requires careful design and implementation to ensure its security and reliability. It also highlights the importance of using trusted and tested platforms and protocols for building decentralized applications and smart contracts on blockchains.
What are the statistics of crypto hacks?
The trends: DeFi frauds rise while overall crime drops
Coinbase blockchain hack is not an isolated case. Crypto hacks have been happening since the inception of cryptocurrencies, and they have caused significant losses for investors, traders, and platforms. According to a report by CipherTrace, a blockchain analytics firm, crypto-related crime dropped by 57% in 2020 compared to 2019, but still amounted to $1.9 billion in losses.
However, while overall crime decreased, one sector saw a surge in frauds: decentralized finance (DeFi). DeFi is a term that refers to various financial applications that run on blockchains without intermediaries or central authorities. DeFi platforms offer services such as lending, borrowing, trading, investing, and staking cryptocurrencies. DeFi has grown rapidly in popularity and value in recent years, reaching over $100 billion in total value locked (TVL) as of August 2021.
However, DeFi also poses significant risks and challenges for users and regulators. DeFi platforms are often unregulated, unaudited, and vulnerable to hacking, exploitation, or manipulation. According to CipherTrace, DeFi-related hacks accounted for 45% of all crypto thefts in 2020, totaling $129 million. In 2021, this trend has continued, with DeFi hacks reaching $361 million in the first half of the year. Some of the most common types of DeFi hacks are:
- Flash loan attacks: A flash loan is a type of loan that allows users to borrow large amounts of crypto without collateral for a very short period of time (usually one transaction). Hackers can use flash loans to manipulate prices or liquidity on DeFi platforms and profit from arbitrage or liquidation opportunities.
- Reentrancy attacks: A reentrancy attack is a type of attack that exploits a vulnerability in a smart contract that allows an attacker to repeatedly call a function before it finishes executing. This can result in multiple withdrawals or transfers of funds from the contract without proper checks or balances.
- Oracle attacks: An oracle is a service that provides external data to smart contracts on blockchains. For example, an oracle can provide price information for different assets or currencies. Hackers can manipulate or compromise oracles to feed false or inaccurate data to smart contracts and cause them to execute malicious actions or transactions.
The examples: some of the biggest crypto hacks in history
Coinbase blockchain hack is one of the largest and most sophisticated crypto hacks in history, but it is not the only one. Here are some other examples of notorious crypto hacks that have occurred over the years:
The following table shows some of the biggest crypto hacks in history, based on the amount stolen and the date of occurrence:
| Platform |
Date |
Amount stolen |
Type of hack |
| Mt.Gox |
2014 |
850,000 Bitcoins ($450 million) |
Unknown |
| DAO |
2016 |
3.6 million Ether ($60 million) |
Reentrancy attack |
| Bitfinex |
2016 |
120,000 Bitcoins ($72 million) |
Security breach |
| Coincheck |
2018 |
523 million NEM ($530 million) |
Security breach |
| Binance |
2019 |
7,000 Bitcoins ($40 million) |
Security breach |
| KuCoin |
2020 |
$281 million |
Security breach |
| Poly Network |
2021 |
$610 million |
Exploit |
The latest news on the Coinbase blockchain hack
Since the announcement of the hack, there have been some developments and updates on the situation. Here are some of the latest news on the Coinbase blockchain hack:
- Hackers return some of the stolen funds: Hours after the hack, the attackers started returning some of the funds – first in small amounts and then in millions. They started sending back small transfers totalling a few dollars to the online wallets controlled by Poly – but then began making much larger deposits, totalling hundreds of millions. The reason for this is unclear, but some speculate that it could be due to pressure from law enforcement, remorse, or fear of being tracked.
- Coinbase identifies the perpetrators: Coinbase claimed that it had identified the perpetrators of the hack, whom it called “brigands” and that it intended to sue them. The company did not disclose their identities or locations, but said that it was working with authorities to bring them to justice. Coinbase also said that it had evidence that the hackers were not affiliated with any state or organization.
- Coinbase launches a bug bounty program: Coinbase announced that it would launch a bug bounty program to reward anyone who finds and reports vulnerabilities in its systems or products. The company said that it would pay up to $1 million for critical bugs that could compromise its platform or users’ funds. Coinbase also encouraged its users to enable two-factor authentication (2FA) and use hardware wallets or cold storage devices to protect their cryptocurrencies.
These are some of the latest news on the Coinbase blockchain hack. We will keep you updated on any further developments as they happen.
How could this hack have been prevented?
The solution: EviVault NFC HSM
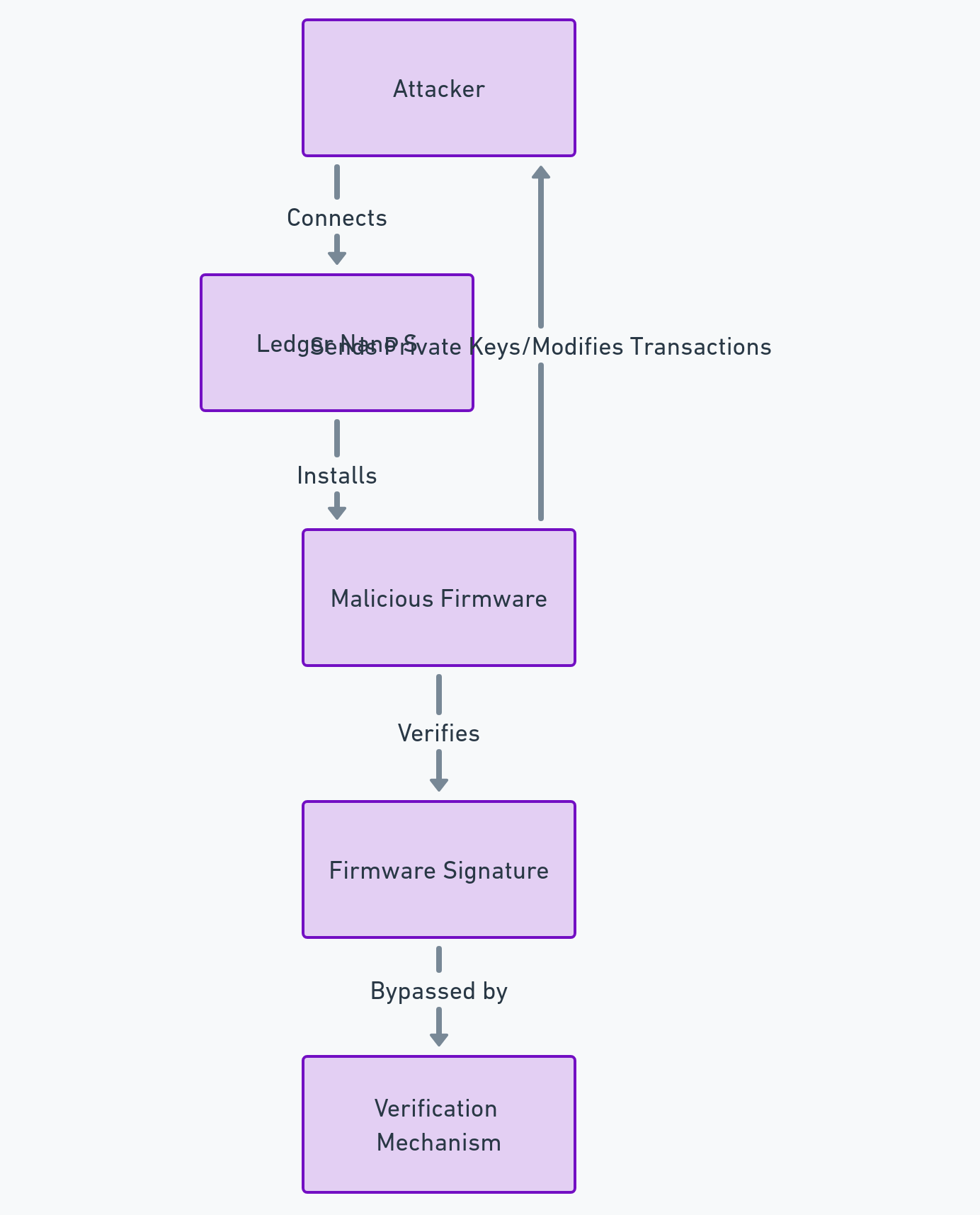
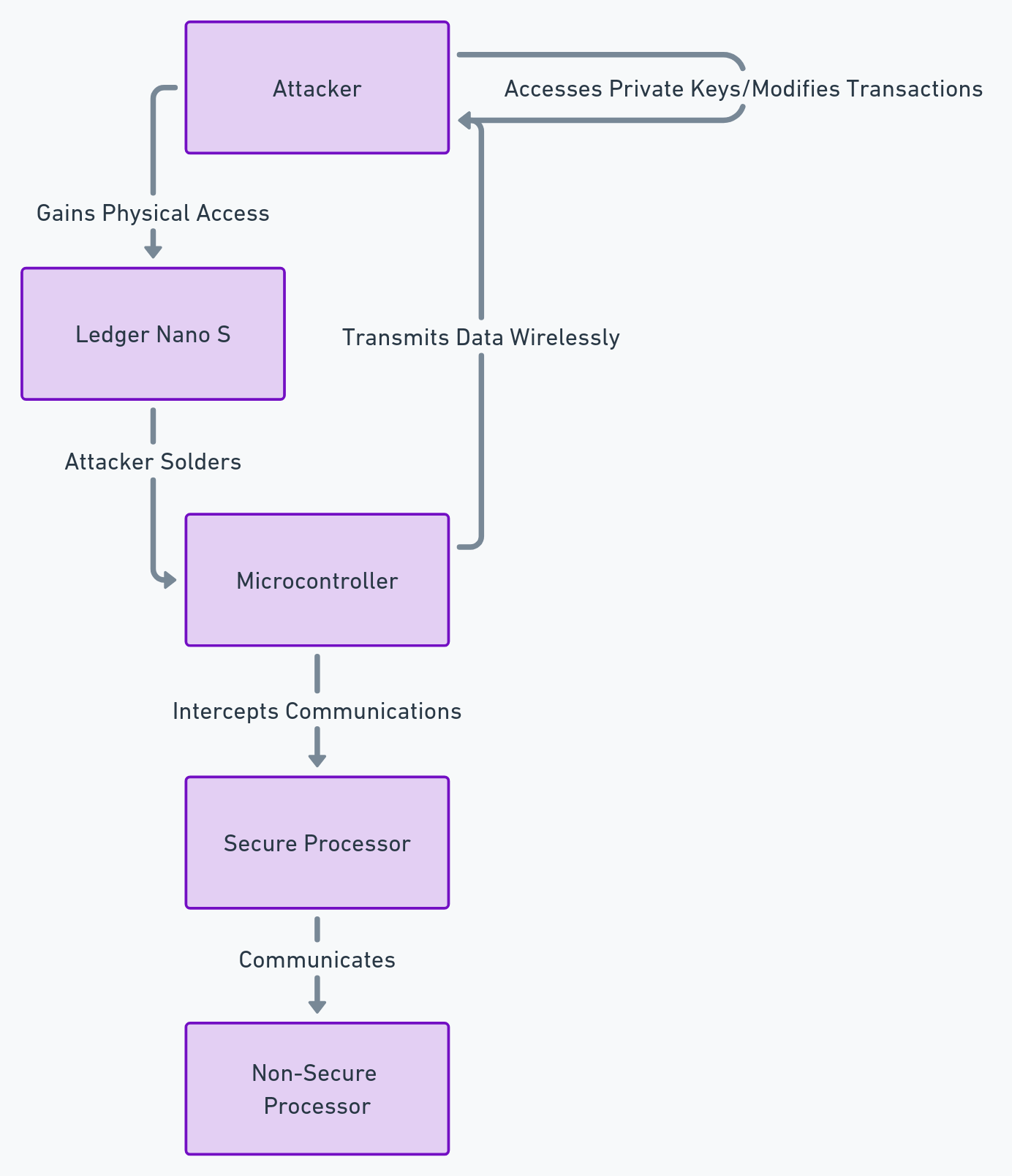
One of the possible ways to prevent this type of hack is to use a technology developed by Freemindtronic, an Andorran company specialized in NFC security solutions. This technology is called EviVault NFC HSM, and it allows for physical offline secure storage of blockchain private keys, cryptocurrencies, wallets, Bitcoin, Ethereum, NFTs, Smart Contracts.
EviVault NFC HSM uses NFC (Near Field Communication) technology to communicate with an Android smartphone and allows access to cryptographic assets with a simple gesture. EviVault NFC HSM is protected by two patents by Jacques Gascuel: wireless access control and segmented key authentication. It integrates EviCore HFC HSM technology developed by Freemindtronic and compatible with EviCore HSM technology.
EviVault NFC HSM comes in different shapes and formats, such as EviTag NFC keychain, EviCard PVC or PCB card, EviPins or EviCard 2 Gen card with two NFC chips on PCB. The latter can store up to 200 blockchain private keys with automatic public address generator. It supports all private keys and derived blockchain keys. And it allows managing with public addresses Bitcoin BTC Ethereum Cash ECASH Namecoin NMC Bitcoin cash BCH Ethereum Classic ETC ReddCoin RDD Bitcoin Gold BTG Ethereum Gold ETG Ripple XRP Dash DASH Ethereum lite ELITE Solar Coin SLR Digibyte DGB Feather Coin FTC Stellar XLM Dogecoin DOGE IOTA Verge XVG Ethereum ETH Litecoin LTC TRON TRX Cardano ADA Polkadot DOT Binance Coin BNB.
EviVault NFC HSM is the ultimate solution to protect all cryptographic asset keys from hackers, theft or loss. Its private keys are stored in EviVault’s EPROM memory, encrypted by an AES 256-bit algorithm. EviVault NFC HSM also benefits from a patented contactless access control system that allows defining two distinct access profiles: administrator and users, without allowing them to access each other’s secrets without their authorization. EviVault NFC HSM also has a patented segmented key authentication system that allows defining up to 9 trust criteria for encrypting its secrets, such as geolocation, BSSID, password or fingerprint.
By using EviVault NFC HSM technology, coinbase users could have secured their funds by storing them in an offline NFC device that offers a high level of protection and encryption for their keys and secrets. They could have avoided the risk of hacking, theft or loss of their cryptocurrencies, and have full control over their digital assets without depending on a centralized platform. They could also enjoy ease of use and speed of transaction thanks to NFC technology, which allows communicating with their Android smartphone and accessing their cryptographic assets with a simple gesture. EviVault NFC HSM is therefore a revolutionary technology for the security of coinbase and cryptocurrencies in general.
Click [here] for more information on EviVault NFC HSM Technology
Click [here] for more information on EviCore NFC HSM Technology
The alternative: EviSeed NFC HSM
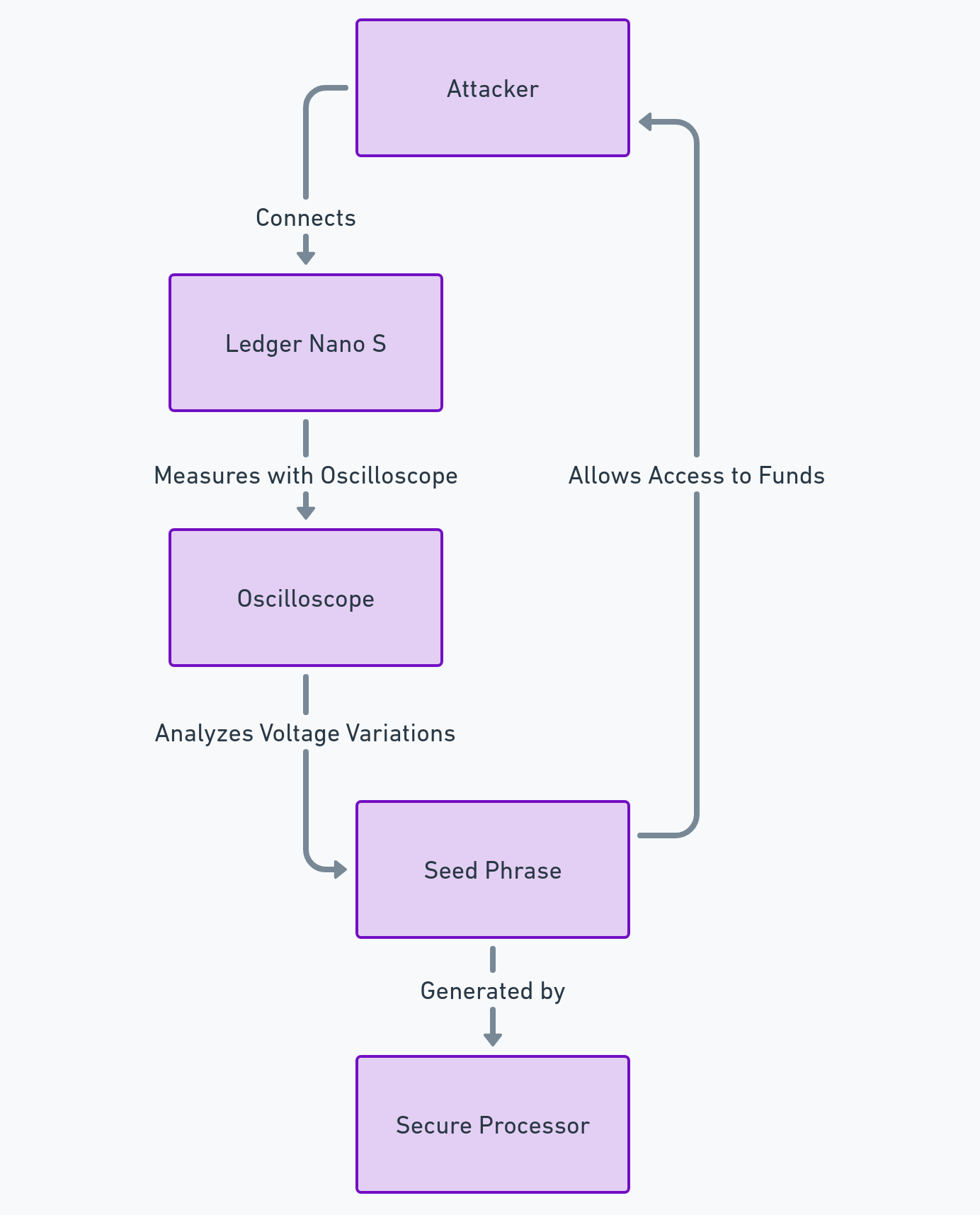
Another technology that can provide security against this hacking of Coinbase is EviSeed NFC HSM, also developed by Freemindtronic. EviSeed NFC HSM is a technology that lets you store your crypto seed phrase in a simple, efficient and durable way. A seed phrase is a sequence of words, usually 12 or 24, that serves as a recovery key for your crypto wallet. If you lose your seed phrase, you lose access to your funds. If someone steals it, they can access your wallet and divert your funds.
EviSeed uses the standards of the BIP (Bitcoin Improvement Proposal) formats, especially the BIP39, to generate, enter or scan seed phrases without error thanks to a checksum control. EviSeed allows you to back up your seed phrases encrypted with your own encryption keys that can be segmented according to an implementation of the invention patent on segmented key authentication. You can use any type of fixed or removable media to store your seed phrases, including Freemindtronic’s NFC HSM devices, which are contactless hardware security modules. EviSeed also generates a QR code containing your encrypted seed phrase, which you can print, share, send or save between NFC HSMs by scanning the QR code encrypted in RSA 4096.
EviSeed offers you several advantages over traditional methods of storing seed phrases, such as paper, metal or digital media. EviSeed is simple: you don’t need to write or engrave your seed phrase, just scan it with the EviSeed app and transfer it to the media of your choice. EviSeed is efficient: you don’t need to memorize or type your seed phrase, just scan it with your smartphone to restore your wallet. EviSeed is durable: the media you choose to store your seed phrase can be resistant to water, fire, shocks and scratches. It does not deteriorate over time.
By using EviSeed NFC HSM technology, coinbase users could have backed up their seed phrases securely and conveniently. They could have restored their wallets easily in case of loss or theft of their devices. They could have also protected their seed phrases from physical or digital attacks thanks to the encryption and segmentation features of EviSeed.
Click [here] for more information on EviSeed NFC HSM
In conclusion
The hack of Coinbase’s decentralized blockchain was a major event that exposed the vulnerabilities and challenges of decentralized platforms. The hackers exploited a flaw in the proof-of-stake consensus protocol of Coinbase Chain and stole more than $200 million worth of cryptocurrencies from the users. Coinbase reacted quickly and took steps to stop the hack, identify the culprits, reimburse the victims and improve the security of its blockchain.
However, this hack could have been prevented by using EviVault NFC HSM technology, which allows for physical offline secure storage of blockchain private keys and cryptocurrencies. EviVault NFC HSM is a patented technology developed by Freemindtronic that offers a high level of protection and encryption for cryptographic asset keys, as well as ease of use and speed of transaction thanks to NFC technology.
This article shows that proof-of-stake is not foolproof and that it requires careful design and implementation to ensure its security and reliability. It also highlights the importance of using trusted and tested platforms and protocols for building decentralized applications and smart contracts on blockchains. Moreover, it demonstrates that EviVault NFC HSM is a revolutionary technology for the security of coinbase and cryptocurrencies in general.
Therefore, we recommend that coinbase users adopt EviVault NFC HSM technology to protect their funds from hacking, theft or loss. We also suggest that coinbase developers review their consensus protocols and implement best practices to prevent future attacks. Finally, we urge coinbase regulators and policymakers to establish clear standards and guidelines for ensuring the safety and integrity of decentralized platforms.