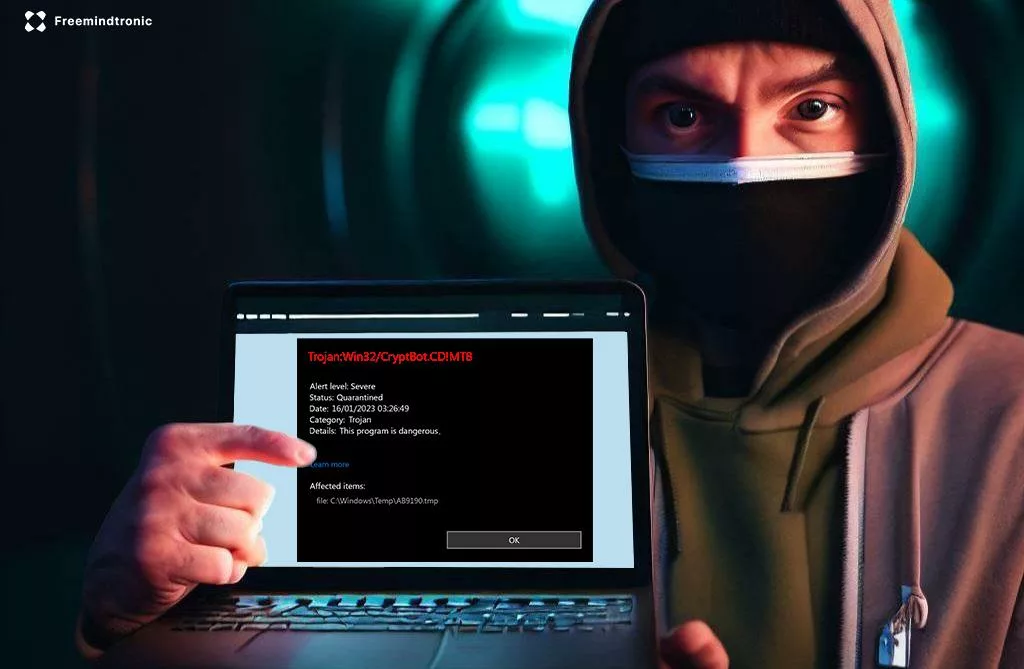
EviSeed and EviVault NFC HSM Technologies could have prevented the $41 million crypto theft by North Korean hackers. Cryptocurrencies have gained immense popularity, but they have also become increasingly vulnerable to theft. Hackers actively search for vulnerabilities in cryptocurrency storage and exchange platforms, leading to them stealing millions of dollars from users. North Korean hackers […]
Stay informed!
Join our community of technology enthusiasts! Subscribe to our newsletter and receive exclusive updates on the latest news, special offers, and tips from Freemindtronic. Stay informed on the latest technology trends, discover new products, and be among the first to take advantage of them. Sign up now by entering your email address below. Don't miss any updates from Freemindtronic!