Multi-factor Authentication by Jacques Gascuel: This article will be updated with any new information on the topic.
Why use multi-factor authentication?
Passwords are not enough to protect your online accounts from cybercriminals. You need to use a more robust authentication method: multi-factor authentication. It combines several factors to verify your identity, such as passwordless MFA. In this article, you will discover what it is, how it works and how to choose it.
2024 Digital Security
November 14, 2024
2024 Digital Security
October 15, 2024
2024 Digital Security
September 3, 2024
2024 Articles Digital Security News
August 31, 2024
2024 Digital Security Spying Technical News
August 20, 2024
2024 Digital Security
August 12, 2024
2024 Digital Security
August 1, 2024
2024 Digital Security
July 25, 2024
Everything you need to know about multi-factor authentication and its variants
Have you ever wondered how to protect your online accounts and data from hackers and cybercriminals? If so, you need to know about multi-factor authentication and its variants. Authentication is the process that verifies the identity of a user who wants to access a website, an application or a system. Authentication is essential to protect the security and privacy of data and online transactions. Without proper authentication, hackers and malicious actors can access sensitive information, steal identities, compromise accounts or commit fraud.
There are different authentication methods that can offer different levels of security and convenience for users. Some methods use only one factor, such as a password, to verify a user’s identity. This is called single-factor authentication (SFA). SFA is simple, fast and convenient, but also very insecure and unreliable. Other methods use two or more factors, such as a password and a code, to verify a user’s identity. This is called multi-factor authentication (MFA). MFA offers a high level of security because it makes it harder for attackers to obtain all the factors needed to access an account.
In this article, we will explain the main differences between six popular methods of authentication: single-factor authentication (SFA), multi-factor authentication (MFA), two-factor authentication (2FA), two-step verification (2SV), one-time passwords (OTP) and passwordless multi-factor authentication (Passwordless MFA). We will also introduce you to a new product that offers an innovative and eco-friendly solution for contactless multi-factor authentication: PassCypher NFC HSM. We will also discuss another method of authentication that allows users to access multiple applications or services with one login. This is called single sign-on (SSO). SSO can use different protocols, such as SAML, OAuth, or OpenID Connect, to verify the user’s identity and grant access.
According to a report by Microsoft, 99.9% of account compromise attacks can be blocked by using multi-factor authentication. Therefore, it is important to choose the best authentication method for your online security. In this article, we will help you understand the pros and cons of each method and how to choose the best one for your needs and preferences.
Why use multi-factor authentication?
You use passwords for your online accounts; but are they secure enough? Cybercriminals can steal, guess or hack them easily; you hear many news about it. You want to improve their protection and usage; you need to know more. You need to know the different methods of multi-factor authentication; up to the most robust one, like passwordless MFA. In this article, you will get answers and learn more.
How to evaluate the level of resistance to cyberattacks?
We use several criteria to evaluate the level of resistance to cyberattacks of an authentication method, such as:
- The number and diversity of factors used: An attacker has a harder time getting all the factors if there are more of them. It is also better to combine factors of different natures (what you know, what you have, what you are); they are less vulnerable to the same types of attacks.
- The complexity and variability of factors used: An attacker has a harder time guessing or reproducing the factors if they are more complex and variable. For example, a long and random password is more resistant than a short and simple one. Likewise, a one-time code is more resistant than a fixed one.
- The security and reliability of communication channels used: An attacker has a harder time intercepting or altering the channels if they are more secure and reliable. For example, an encrypted connection is more secure than an unencrypted one. Likewise, a push notification is more reliable than an SMS.
- The ease and speed of use for the user: Users are more likely to adopt the methods if they are easier and faster. A too complex or slow method can discourage users or make them bypass security. For example, facial recognition is easier and faster than a USB key.
We give a score out of 10 to each authentication method based on these criteria; we consider the pros and cons of each factor and channel. This score reflects the level of resistance to cyberattacks of the method; its ability to prevent or reduce the impact of an attack.
What are the differences between MFA, 2FA, 2SV, SFA, SSO, OTP and Passwordless MFA?
MFA, 2FA, 2SV, Passwordless MFA, OTP and SFA are all types of authentication methods that require users to provide one or more pieces of evidence (or factors) to prove their identity. However, they have distinct differences in terms of how they work and how secure they are. Here is a summary of each one:
Multi-Factor Authentication (MFA)
MFA is a security enhancement that requires users to submit two or more pieces of evidence (factors) to access a system. These factors can belong to different categories, such as:
- Knowledge: something that the user knows, such as a password, a PIN or an answer to a secret question.
- Possession: something that the user has, such as a smartphone, a smart card or a hardware token.
- Inherence: something that the user is, such as a fingerprint, a retina scan or a facial recognition.
MFA offers a high level of security because it makes it harder for attackers to obtain all the factors needed to access an account. Even if one factor is compromised, such as a password, the other factors can still prevent unauthorized access.
Level of resistance to cyber attacks: 8/10
Two-Factor Authentication (2FA)
2FA is a type of MFA; it uses two distinct factors of authentication. These factors must belong to two different categories; such as knowledge and possession. For example, you can log in to an account; with your username and password (knowledge). Then you receive a notification on your smartphone (possession); to approve the login.
2FA offers an intermediate level of security between single-factor authentication by password only and MFA by adding an extra layer of protection against unauthorized access attempts. However, it can be less secure than 2FA; if it uses factors that belong to the same category; such as knowledge.
Indeed, if an attacker manages to obtain the password and the additional code; they can access the account without any problem.
Level of resistance to cyber attacks: 6/10
Two-Step Verification (2SV)
2SV is a type of MFA that requires two sequential steps of verification using authentication factors. These steps can belong to the same category, such as knowledge. For example, Google uses 2SV for its accounts. To log in, the user enters their username and password (knowledge), then they enter an additional code that they receive by SMS or email (knowledge).
2SV offers an intermediate level of security between single-factor authentication by password only and 2FA by adding an extra layer of protection against unauthorized access attempts. However, it can be less secure than 2FA if it uses factors that belong to the same category, such as knowledge.
Indeed, if an attacker manages to obtain the password and the additional code, they can access the account without any problem.
Level of resistance to cyber attacks: 4/10
Single-Factor Authentication (SFA)
Single-Factor Authentication (SFA) is a security method that uses only one factor to verify a user’s identity. A factor is something that the user knows, has, or is. For example:
- One piece of evidence (factor) verifies a user’s identity with SFA.
- The factor can be something the user knows (password, PIN, secret question), has (smartphone, smart card, hardware token), or is (fingerprint, retina scan, facial recognition).
- SFA has some benefits but also many drawbacks. It is simple, fast and convenient, but also insecure, unreliable and non-compliant.
- Many cyberattacks expose users to SFA, such as phishing, keylogging, brute force or credential stuffing.
- Attackers can easily obtain the factor and access the account without the user’s consent.
- If the factor is compromised (e.g., password), the account is vulnerable to unauthorized access.
- SFA does not meet the security standards or regulations of some industries or organizations (e.g., banks, government agencies).
SFA offers a low level of security because it makes it easy for attackers to obtain the factor needed to access an account. If the factor is compromised, such as a password, the user’s account is vulnerable to unauthorized access.
Level of resistance to cyber attacks: 2/10
Single Sign-On (SSO) and Multi-Factor Authentication (MFA)
Single Sign-On (SSO) is a security method that allows users to access multiple applications or services with one login. The user only needs to enter their username and password once, and the SSO service authenticates them for all the connected applications. SSO can use different protocols, such as SAML, OAuth, or OpenID Connect, to verify the user’s identity and grant access. SSO has some advantages and disadvantages that you should consider before choosing it as your authentication method.
- Pros of SSO
- Reduced password fatigue: Users only need to remember one password instead of many. This makes it easier to create strong and unique passwords for each application.
- Simplified user and password management: IT admins can control the access rights of users from a central place. They can also revoke or change the passwords of users who leave the organization or lose their devices.
- Improved identity protection: SSO can use additional security measures, such as multi-factor authentication (MFA), to enhance the verification process. MFA is a type of authentication that requires two or more factors to verify a user’s identity. These factors can be something that the user knows, has, or is, such as a password, a smartphone, or a fingerprint. MFA offers a higher level of security than single-factor authentication (SFA), which only requires one factor, such as a password.
- Cons of SSO
- Limited user control: Users cannot choose which applications are included in the SSO service. They may also have difficulty logging out of all the applications at once.
- Incompatible apps: Some applications may not support the SSO protocols or require additional configuration to work with the SSO service. This may limit the number of applications that users can access with one login.
- Unpredictable costs and time: Implementing and maintaining an SSO service may be costly or complex for some organizations. They may need to buy or develop software, pay for subscription fees, train users or staff, or comply with regulations.
SSO has some benefits but also some drawbacks that you should consider before choosing it as your authentication method. You should weigh the pros and cons of SSO and compare them with your security goals and resources.
Level of resistance to cyber attacks: 7/10
Passwordless Multi-Factor Authentication (Passwordless MFA)
Passwordless MFA is a term used to describe an authentication method; that does not require a password; and that uses multiple factors. For example, you can log in to an account; using your fingerprint (inherence) and a code generated by your smartphone (possession); without having to enter your username or password.
Passwordless MFA offers the highest level of security; when implemented correctly; because it eliminates the risk of password theft or leakage. It also improves convenience and user experience; because it does not require memorization or input of passwords.
Level of resistance to cyber attacks: 10/10
One-Time Passwords (OTP)
OTP are random and temporary codes; that are used as additional factors of authentication. There are two main types of OTP: Time-based One-Time Password (TOTP) and HMAC-based One-Time Password (HOTP).
Time-based One-Time Password (TOTP)
TOTP is a type of OTP that is generated based on time; it uses a secret key shared between the server and the client; as well as a counter based on the client’s clock. The server and the client calculate the same code; using the same key and the same counter. The code is valid for a short period, usually 30 seconds.
TOTP offers a high level of security because it prevents the reuse of codes. Even if an attacker intercepts a code, they will not be able to use it after its expiration.
Level of resistance to cyber attacks: 7/10
HMAC-based One-Time Password (HOTP)
HOTP is a type of OTP that is generated based on an incremental counter. It uses a secret key shared between the server and the client, as well as a counter that increments every time a code is generated or validated. The server and the client calculate the same code using the same key and the same counter. The code does not have a fixed validity period, but it must be used in order.
HOTP offers an intermediate level of security because it requires synchronization between the server and the client. If the client’s counter is offset from the server’s counter, there may be authentication errors. Moreover, if an attacker manages to obtain the secret key or the counter, they can generate valid codes.
Level of resistance to cyber attacks: 5/10
Statistics on MFA, 2FA, 2SV, SFA, OTP (TOTP and HOTP), Passwordless MFA and SSO
To illustrate the importance and popularity of multi-factor authentication methods, here are some statistics from various sources:
- According to the 2021 Duo Trusted Access Report, the total number of MFA authentications increased by 39% over the past year, while biometric authentications saw an even faster growth, with a 48% increase.
- The report also indicates that Duo Push is the most popular authentication method, accounting for 30% of the total authentications, followed by SMS (25%) and phone calls (19%).
- Among customers using location policies, 74% block Russia and China, which are the most frequently blocked countries in authentication apps.
- In 2020, Duo Security conducted a survey of over 4,000 people in the US and UK on their experience and perception of 2FA. The survey revealed that 79% of respondents had used 2FA in 2020, up from 53% in 2019 and 28% in 2017.
- The survey also showed that SMS (85%) continues to be the second most common factor that respondents with 2FA experience have used, slightly up from 2019 (72%). Email is the second most common factor (74%), with a notable increase from 2019 (57%).
- According to a report by Okta, an identity and access management company, SSO adoption increased by 68% between February and April 2020, as more organizations shifted to remote work due to the COVID-19 pandemic.
- The report also found that SSO usage was highest among education (60%), technology (58%), and non-profit (49%) sectors. The most popular SSO protocols were SAML (54%), OAuth (24%), and OpenID Connect (22%).
These statistics show that multi-factor authentication methods are more effective and popular than single-factor authentication methods. They provide higher levels of security and reliability for users and organizations. However, they also reveal that there is still room for improvement and awareness in terms of online security. Many users and companies do not use multi-factor authentication or use weak factors that can be compromised. Therefore, it is important to educate and encourage users and companies to adopt multi-factor authentication methods that suit their needs and preferences.
Discover PassCypher NFC HSM: an innovative solution for contactless multi-factor authentication
You now have a better understanding of the different methods of multi-factor authentication and their pros and cons. You may have noticed that some methods have weaknesses, such as vulnerability to cyber attacks, dependency on network or battery availability, or complexity of managing passwords.
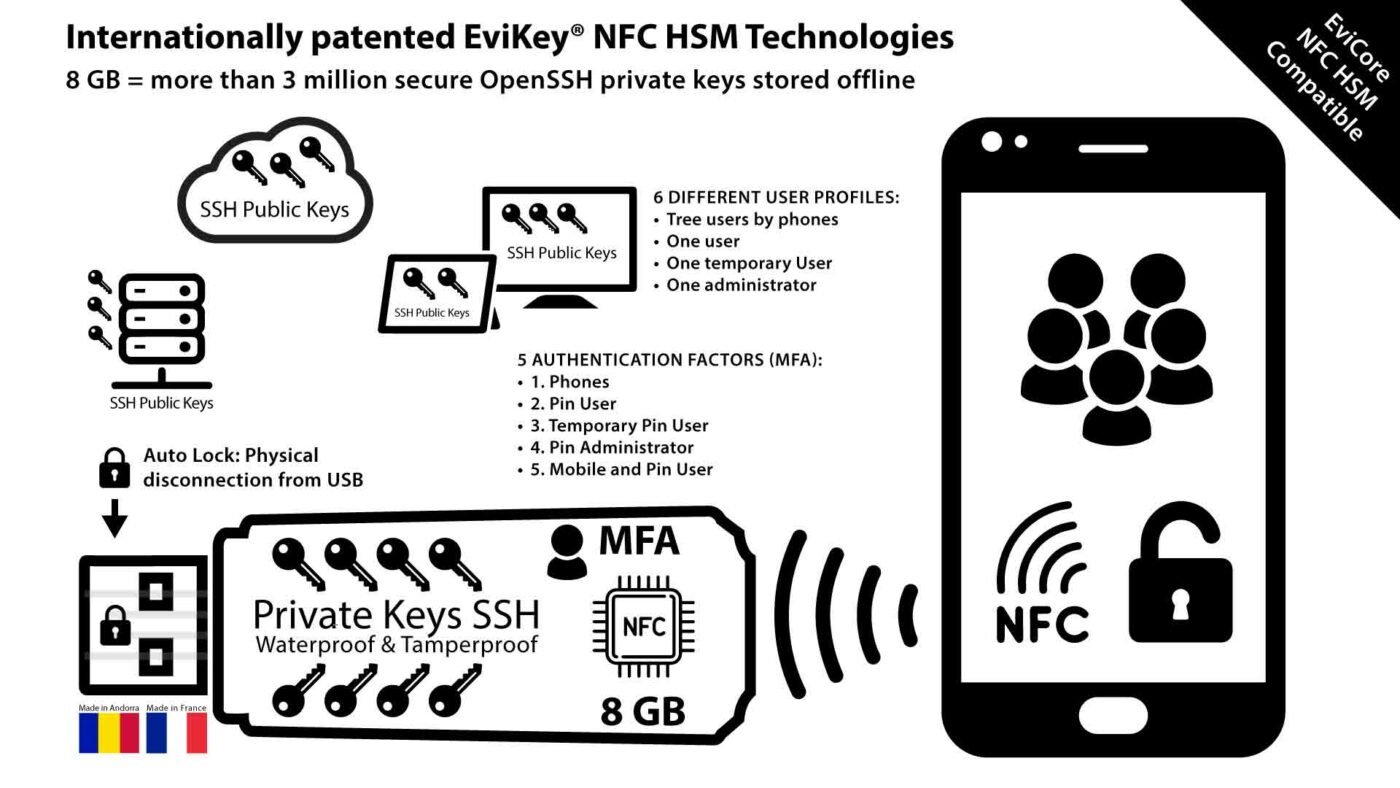
Fortunately, there is a solution that combines security, convenience and ecology to protect your data and online transactions. We introduce you to PassCypher NFC HSM, a product developed by Freemindtronic that allows you to store and manage passwords, one-time passwords (OTP) and HMAC-based passwords (HOTP) in a wireless and battery-free device. It uses EviOTP technology, which is a patented solution by Freemindtronic to generate OTP without internet connection or power supply. It works with NFC-compatible Android smartphones and computers equipped with a Chromium or Firefox web browser.
The benefits of PassCypher NFC HSM
Some of the benefits of PassCypher NFC HSM over traditional multi-factor authentication solutions are:
- Higher resistance to cyber attacks: It uses a NFC HSM device that stores the secrets in an encrypted way. It also verifies the validity of the device used, its pairing key, its unique anti-counterfeiting key, and the validation of the Authenticator Sandbox. It does this with auto verification of fraudulent URLs.
- Greater convenience: It does not require network or battery. You just need to scan the PassCypher NFC HSM device with your smartphone. This will automatically fill in the login fields on your computer or display the OTP code. The OTP code corresponds to the online service.
- Better eco-friendliness: It reduces energy consumption and CO2 emissions. It uses a wireless and battery-free device. It works with EviOTP technology, which generates OTP without network or battery. You can scan them with your smartphone to access your accounts.
- More customization: It allows the user to freely define the authentication factors that they want to use. They can add cumulative factors such as the UID of the NFC Android phone, a BSSID or an authorized geofence. They can also add additional factors that involve their intervention. For example, a biometric criterion or a segmented key via a QR code or a hexadecimal barcode.
The features of PassCypher NFC HSM
PassCypher NFC HSM offers several features that facilitate the management and use of passwords and OTP. Here are some of these features:
- It allows you to automatically fill in the identifiers and passwords of 2SV methods, such as Google or Facebook, using a browser extension. You just need to scan the PassCypher NFC HSM device with your smartphone to automatically fill in the login fields on your computer.
- It manages TOTP, such as those used by GitHub or Dropbox, using a dedicated application on your smartphone. You just need to scan the PassCypher NFC HSM device with your smartphone to display the TOTP code corresponding to the online service. For this, you must have previously saved the OTP codes via the QR Code generated from the site that authorizes 2FA via TOTP or HOTP.
- It has an advanced configurable passwordless MFA function patented using physical origin segmented key authentication defined freely by the user. It can add them cumulatively for each secret stored in the NFC HSM of segments that can be UID of the NFC Android phone, a BSSID or an authorized geofence. It can also add additional factors that involve their intervention, such as a biometric criterion or a segmented key via a QR code or a hexadecimal barcode. You just need to scan the PassCypher NFC HSM device with your smartphone to access your account without entering any username or password.
- It allows you to save and restore contactlessly, in real time in volatile memory of the phone or computer, without needing a server, database, without needing to create an account and anonymously and encrypted end-to-end from the NFC HSM. It works on the NFC Android phone and on computer via an extension only on the local network encrypted end-to-end from the NFC HSM. You just need to pass the PassCypher NFC HSM under your smartphone’s antenna to auto-connect to the cloud service via the passwordless MFA process.
- It allows you to share secrets stored in NFC HSM by various means with other authorized users with trust criteria who also have a PassCypher NFC HSM. Sharing can be done in presence of the recipient who scans a QR Code of the secret shared via coded QR Code. It can share nearby by bluetooth file sharing. It can also share remotely via all means of communication existing in their phone including SMS or RCS using a 4096-bit RSA public key that the recipient has freely generated in their NFC HSM that they regenerate at will. It can also share it contactlessly via Android Beam NFC technology.
Conclusion
In this article, we have discussed how to choose the best multi-factor authentication method for your online security. We have also compared some of the most popular and innovative solutions available in the market. Multi-factor authentication is a vital component of online security that protects your data and transactions from unauthorized access. However, not all methods are suitable for all situations and needs. Therefore, you should consider several factors when choosing an authentication method, such as:
- The type and sensitivity of the data or transactions that you want to protect. Some data or transactions are more valuable or confidential than others. For example, your bank account or medical records require more protection than your social media account or online shopping.
- The availability and reliability of the network or battery for your devices. Some methods depend on the network or battery to work. For example, you cannot use SMS or email if you have no internet connection or phone signal. Likewise, you cannot use a USB key or a smart card if your device has no power or port.
- The ease and frequency of use and management of the authentication factors. Some methods are easier and faster to use and manage than others. For example, facial recognition or fingerprint scanning are more convenient than typing a password or entering a code. However, you may also need to change or update your factors regularly to maintain their security.
- The compatibility and interoperability of the authentication method with your devices and platforms. Some methods work only with specific devices or platforms. For example, you cannot use an Apple Watch or a Google Authenticator app if you have an Android phone or a Windows computer. Likewise, you cannot use a biometric scanner if your device does not have one.
- The cost and benefit of implementing and maintaining the authentication method. Some methods are more expensive or complex to implement and maintain than others. For example, you may need to buy additional hardware or software, pay for subscription fees, train users or staff, or comply with regulations.
These factors can help you decide which authentication method suits your needs and preferences best. You should weigh the pros and cons of each method and compare them with your security goals and resources.
Comparison of popular authentication methods
We have explained the main differences between five popular methods of multi-factor authentication: multi-factor authentication (MFA), two-factor authentication (2FA), two-step verification (2SV), passwordless multi-factor authentication (Passwordless MFA) and one-time passwords (OTP). Each method has its own advantages and disadvantages depending on the context and implementation. We have also introduced you to a new product that offers an innovative and eco-friendly solution for contactless multi-factor authentication: PassCypher NFC HSM.
PassCypher NFC HSM offers several benefits over traditional multi-factor authentication solutions, such as SMS or email
Freemindtronic designed, developed and manufactured PassCypher NFC HSM. This product lets you store and manage passwords, keys, OTP and HOTP. It uses a wireless, battery-free NFC HSM device. It works for life without maintenance. It also incorporates several EviPass technologies. EviCore NFC HSM and EviOTP technology are patented by Freemindtronic. With these technologies, you can manage, store, share, encrypt and generate OTP code securely. You can do this contactlessly from NFC devices. It does not need an Internet connection, a server, a database or a power supply. It works contactless with NFC-compatible Android smartphones.
PassCypher NFC HSM also offers several features that facilitate the management and use of passwords, such as:
Password generator: It can generate strong and random passwords for any website or application.
- Password manager: It can store and retrieve your passwords securely and conveniently.
- OTP generator: It can generate OTP based on time (TOTP) or counter (HOTP) for any website or application that supports them.
- HOTP generator: It can generate HOTP based on HMAC algorithm for any website or application that supports them.
- QR code scanner: It can scan QR codes that contain OTP information and generate the corresponding OTP.
- Web extension: This is a feature that can integrate with your web browser. It can automatically fill in your complicated and complex usernames and passwords in MFA Passwordless. It does this for any website you visit.
One of the features of PassCypher NFC HSM is that it can store and manage SSO credentials and passwords for automatic login in passwordless MFA. This means that you can use PassCypher NFC HSM to access multiple applications or services with one tap, without entering any password. This increases the level of security of the authentication by SSO, as it eliminates the risk of password theft or compromise. Similarly, PassCypher NFC HSM can also store and manage SFA credentials and passwords for automatic login in passwordless MFA. This means that you can use PassCypher NFC HSM to access any website or system with one tap, without entering any password. This increases the level of security of the authentication by SFA, as it reduces the password fatigue and reuse.
PassCypher NFC HSM is a powerful and innovative product that enhances your online security and convenience. It is compatible with any type of authentication method, such as MFA, 2FA, 2SV, Passwordless MFA or SFA. It is also easy to use and eco-friendly.
If you are interested in trying out PassCypher NFC HSM, you can order it from our [website] or download our [web extension] for free. If you have any questions or feedback, please feel free to [contact us]. We would love to hear from you.