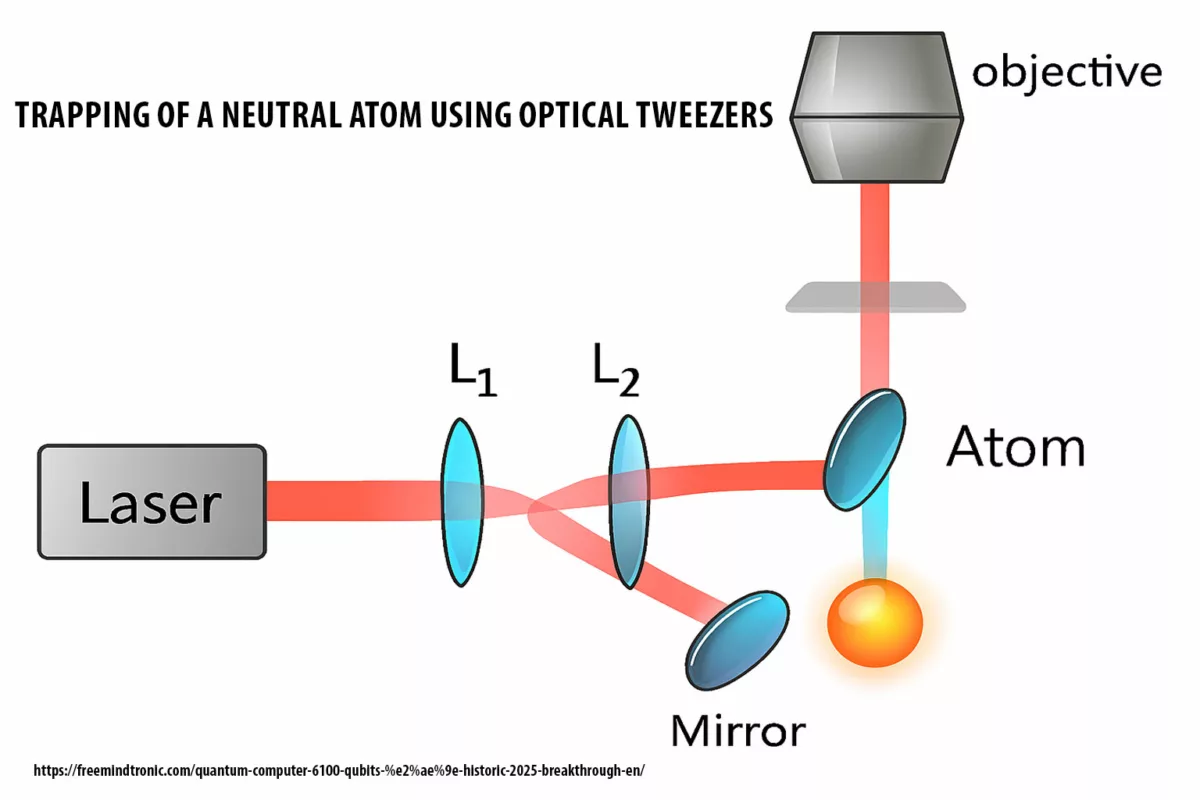
Android Spyware Threat: ClayRat illustrates the new face of cyber-espionage — no exploits needed, just human reflexes. This chronicle explores the doctrinal rupture introduced by DataShielder NFC HSM Defence, where plaintext messages simply cease to exist in Android.
Executive Summary — Android spyware threat ClayRat disguised as WhatsApp
⮞ Quick take
Reading time ≈ 4 minutes.
ClayRat Android is a polymorphic spyware that disguises itself as popular apps (WhatsApp, Google Photos, TikTok, YouTube) to infiltrate Android devices. It silently takes control of SMS, calls, camera and microphone — without any alert.
It bypasses Android 13+, abuses the default SMS role, intercepts notifications, and spreads through social trust between infected contacts.
Its innovation? It relies not on a technical flaw, but on fake familiarity.
Facing this threat, DataShielder NFC HSM Defence eliminates plaintext vulnerability: messages are hardware-encrypted before Android ever sees them.
⚙ Key concept — defeating Android spyware threats like ClayRat through sovereign encryption
How do you neutralize behavioral spyware?
Freemindtronic answers with a sovereign approach: hardware-based message encryption editing within an interface independent of Android.
Each keystroke is encrypted inside the NFC HSM before injection — no readable text is ever stored in cache or RAM.
This makes any spyware structurally blind, even with full access to phone memory.
Interoperability
Compatible with Android 10 to 14 — all messaging systems (SMS, MMS, RCS, Signal, Telegram, WhatsApp, Gmail, etc.).
Integrated technologies: EviCore · EviPass · EviOTP · EviCall — all derived from the sovereign core DataShielder NFC HSM Defence.
Reading Parameters
- Express summary: ≈ 4 min
- Advanced summary: ≈ 6 min
- Full chronicle: ≈ 35 min
- Last update: 2025-10-15
- Complexity level: Advanced / Expert
- Technical density: ≈ 71%
- Languages: EN FR
- Lexical regime: Sovereign cryptographic terminology
- Reading path: Summary → Mechanics → Impact → Sovereign Defence → Doctrine → Sources
- Accessibility: Optimized for screen readers — editorial anchors included
- Editorial type: Strategic Chronicle —Digital Security
- Author: Jacques Gascuel, inventor and founder of Freemindtronic Andorra, expert in NFC HSM security architectures and designer of digital sovereignty solutions (EviCore, DataShielder, PassCypher).
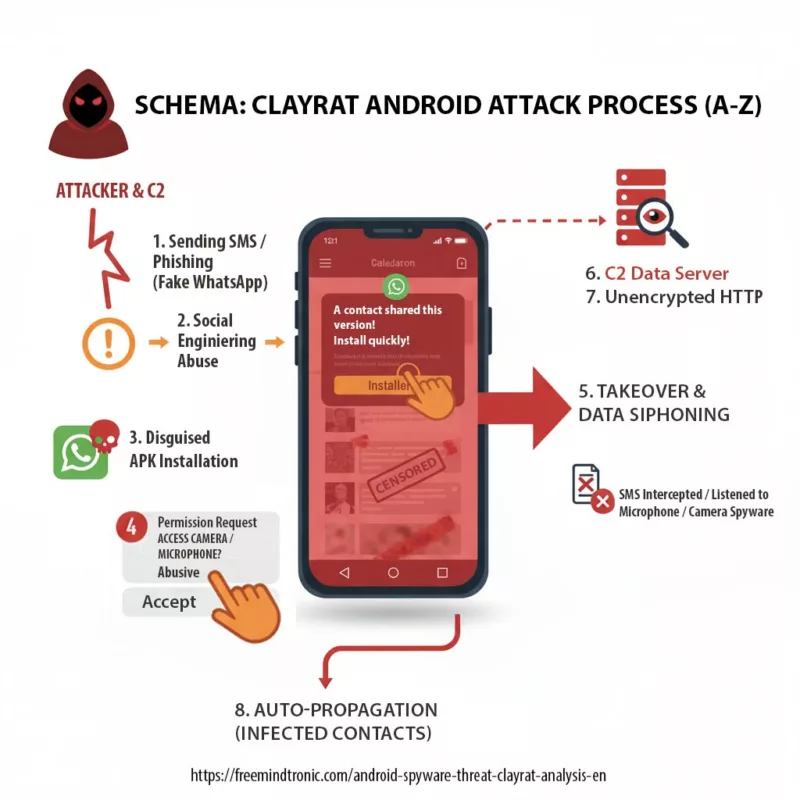
The ClayRat spyware does not rely on a technical flaw, but exploits the user reflex of installing a fake app to gain abusive permissions (camera, mic, SMS) and siphon data to its C2 server.
Advanced Summary — Android spyware threat ClayRat and the end of plaintext
⮞ In detail
ClayRat Android inaugurates a new generation of spyware based on social mimicry. Instead of exploiting software bugs, it abuses human behavior: installing familiar APKs, accepting camera/SMS permissions, and trusting known contacts.
The DataShielder NFC HSM Defence response is systemic: encryption becomes a hardware function, no longer a software process.
The message never exists in plaintext within Android. Even if ClayRat accesses memory, it only reads ciphered flows.
Sovereign Defence Principles
- Complete hardware isolation (autonomous NFC HSM, not addressable by Android)
- Auto-erasure of plaintext after hardware encryption
- Universal compatibility across Android messaging systems
- Sovereign call and contact management via EviCall NFC HSM
- Auto-purge of SMS/MMS/RCS history linked to HSM-stored numbers
Key Insights
- ClayRat replaces technical vectors with behavioral levers.
- Android 13+ protections fail against session-based installs.
- Resilience no longer lies in post-exposure encryption, but in the total absence of plaintext.
- DataShielder NFC HSM Defence turns messaging into a hardware editor, making spyware structurally blind.

Origin of the Android spyware threat ClayRat — a social façade with no attribution
Early analyses show that ClayRat primarily targets Russian-speaking Android users, spreading first through Telegram channels, phishing websites, and APK packages hosted outside Google Play. Attribution remains open — no public evidence currently links ClayRat to any state-sponsored or known APT operation.
- C2 Infrastructure : command-and-control servers hosted outside the EU, often in low-cooperation jurisdictions.
- Reconfiguration capability : dynamic domains, rotating DNS and ephemeral hosting to evade blocking lists.
- Main leverage : abuse of social trust between peers to bypass technical vigilance mechanisms.
- No initial exploit vector : ClayRat relies on behavioral vulnerabilities, not software flaws.
This social façade makes ClayRat particularly difficult to detect during its pre-infection phase. It triggers no system alert, requires no root privileges, and installs through legitimate user sessions. It is a mimicry attack — a familiar interface hiding a surveillance logic.
Attribution analysis (evidential, non-speculative)
To date, public reporting (Zimperium, ThreatFox, abuse.ch) provides no definitive APT attribution. However, cross-referenced indicators allow a cautious analytic hypothesis:
- Targeting & language : focus on Russian-speaking users—consistent with an intra-regional espionage campaign rather than a broad geopolitical operation.
- Infrastructure patterns : ephemeral C2s (e.g.
clayrat.top), rotating DNS and low-cost hosting—typical of opportunistic operators or cyber brokers seeking resilience. - Tooling & TTPs : polymorphic APKs, social-engineering delivery and behavioural mimicry resemble techniques used by mid-spectrum actors (mercenary groups or small APT-like teams) rather than high-tier nation-state frameworks.
Analytic hypothesis (confidence: moderate→low) — ClayRat most likely originates from a semi-structured, opportunistic operator or commercial cyber-service borrowing toolsets and TTPs from known APT ecosystems, rather than a directly state-run offensive. This remains a hypothesis and should be treated as such until further forensic attribution is published.
ClayRat’s Rapid Evolution
⮞ Context update
As of mid-October 2025, new telemetry confirms that ClayRat Android spyware continues to expand beyond its initial Russian-speaking target base. Security labs (Zimperium, CSO Online, CyberScoop) report over 600 unique APK samples and more than 50 distribution variants leveraging Telegram and SMS channels.
Evolution timeline
- Q1 2025 — Initial discovery: first campaigns detected in Russian Telegram groups; social-trust infection pattern.
- Q2 2025 — Infrastructure mutation: dynamic DNS & ephemeral C2 domains (
clayrat.topand derivatives). - Q3 2025 — Self-propagation upgrade: infected phones begin auto-spreading malicious SMS links to contact lists.
- Q4 2025 — Session-based installation: ClayRat bypasses Android 13+ restrictions via fake “system update” overlays.
New capabilities of the Android spyware threat ClayRat
- Silent control of camera and microphone even in Doze mode.
- Credential theft from browser autofill and accessibility services.
- Dynamic command list allowing on-the-fly payload replacement.
- Use of plain HTTP exfiltration to remote C2 — data remains unencrypted in transit.
Comparative landscape of Android spyware threats: ClayRat vs Pegasus vs Predator
| Spyware | Primary Vector | Distinctive Feature |
|---|---|---|
| Pegasus | Zero-click exploits | State-grade surveillance targeting diplomats and journalists |
| Predator | Zero-day exploits | Government-level espionage through software vulnerabilities |
| FluBot | SMS phishing | Banking credential theft via fake updates |
| ClayRat | Social mimicry | Behavioral infiltration – no exploit, pure trust abuse |
This transition illustrates the strategic move from “technical breach” to “human reflex hijacking” — the new frontier of Android spyware.
Impact & emerging risks
- Transformation of infected phones into distribution hubs via automatic SMS propagation.
- Possible spill-over to corporate devices through BYOD environments.
- Rising interest on darknet forums for ClayRat-derived builder kits.
Recommendations (technical hardening)
- Disable Install unknown apps permissions globally.
- Filter SMS links through secure gateways or EMM policy enforcement.
- Deploy DNS-based blocking for known
*.clayrat.toppatterns. - Use hardware-level editors like DataShielder NFC HSM Defence to eliminate plaintext exposure entirely.
Geographical Mapping & Verified Cyber Victims
Cartography & Heatmap
The global heatmap below illustrates the geographic distribution of the spyware ClayRat Android campaigns detected between late 2024 and 2025. Based on telemetry from Zimperium and cross-referenced open-source indicators, the epicenter remains within Russia and neighboring regions, with propagation vectors extending toward Eastern Europe, Turkey, and monitored exposure in North America and Asia-Pacific.
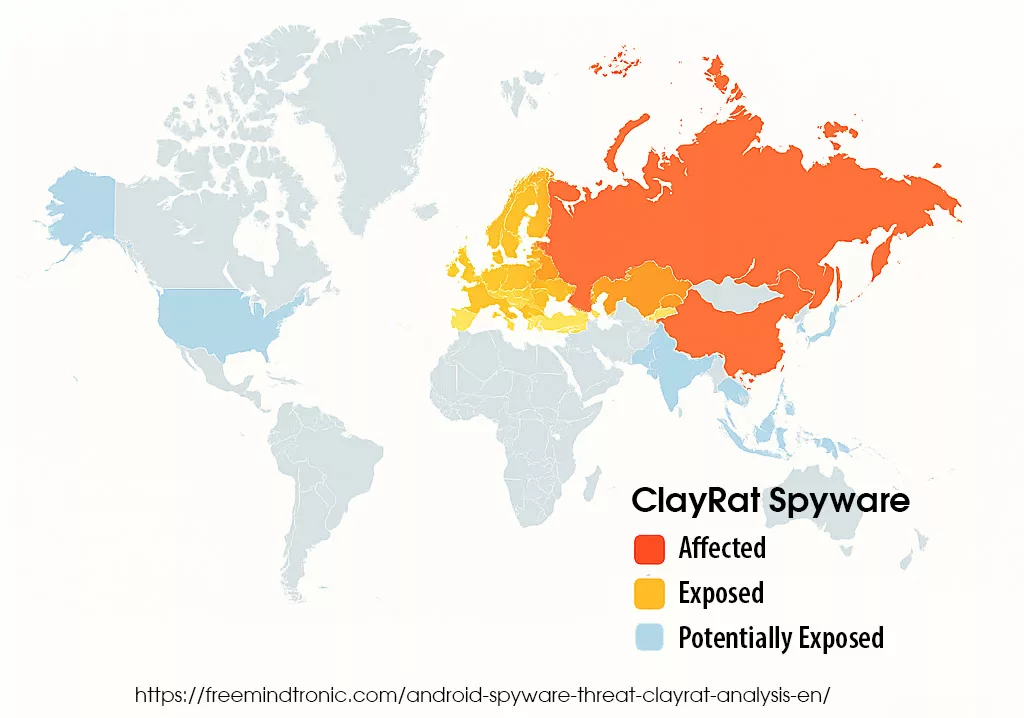
Red and orange indicate confirmed infection areas (Russia, Ukraine, Belarus, Kazakhstan), yellow shows exposure zones (Eastern Europe, Turkey), and blue marks monitored or at-risk regions (US, EU, Asia-Pacific).
Verified Victim Cases & Sector Targets
As of October 2025, no publicly confirmed victim (government, NGO, or media) has been forensically linked to ClayRat Android spyware. However, open-source intelligence confirms that it targets Russian-speaking Android users via Telegram, phishing sites, and sideloaded APKs outside Google Play.
- Broadcom lists ClayRat Android spyware as an active Android threat but without naming specific victims.
- Zimperium reports infected devices acting as propagation hubs distributing polymorphic variants.
- In comparison, Pegasus and Predator have confirmed cases involving journalists, NGOs, and government officials, underscoring ClayRat’s stealthier behavioral model.
Impact of the Android spyware threat ClayRat — from privacy breach to sovereignty loss
The impact of ClayRat goes far beyond simple data theft. It represents a form of silent compromise where the boundary between personal espionage and systemic intrusion becomes blurred. This Android spyware threat ClayRat unfolds across three distinct layers of impact:
- Violation of privacy : ClayRat intercepts messages, images and call logs, and can activate camera and microphone silently. The user perceives no anomaly while their most private exchanges are siphoned in real time.
- Propagation in professional environments : By exploiting trusted contacts, ClayRat spreads within corporate networks without triggering conventional detection. It bypasses MDM policies and infiltrates internal communication channels, compromising the confidentiality of strategic discussions.
- Systemic risk : Combining espionage, app mimicry and social diffusion, ClayRat leads to a loss of sovereignty over mobile communications. Critical infrastructures, command chains and diplomatic environments become exposed to invisible, unattributed and potentially persistent surveillance.
This triple impact — personal, organisational and systemic — forces a rupture in current mobile-security doctrines. Detection is no longer sufficient : it becomes imperative to eliminate every plaintext zone before it can be exploited.
Typological Risk Score: ClayRat Reaches 8.2 / 10
ClayRat does not exploit a traditional zero-day vulnerability. Instead, it hijacks documented Android mechanisms while abusing social trust and user interface mimicry. For this reason, it deserves a typological risk assessment inspired by the CVSS model.
| Criterion | Rating | Justification |
|---|---|---|
| Attack vector | Network (SMS / phishing) | Propagates without physical contact |
| Attack complexity | Low | Installs via social trust; no root privileges required |
| Required privileges | High (granted by user) | Hijacks SMS role and contact permissions |
| Impact on confidentiality | Critical | Steals messages, photos, calls, and camera feed |
| Impact on integrity | Moderate | Sends malicious SMS without user awareness |
| Impact on availability | Low | Passive espionage, no system disruption |
Estimated typological score : 8.2 / 10 — Critical threat through behavioural mimicry
Doctrinal Shift — Why Android spyware threats like ClayRat bypass legacy defences
With a typological risk score of 8.2 / 10, ClayRat forces a profound re-evaluation of mobile-security approaches. Conventional solutions — antivirus, sandbox systems, MDM policies, and software encryption — fail not because of technical obsolescence, but because they intervene after the plaintext message has already been exposed. A change of paradigm is unavoidable.
In the face of the Android spyware threat ClayRat, legacy defences show structural limits. They protect what is already visible, or act after the message has entered system memory. Yet ClayRat does not attempt to break encryption — it intercepts the message before protection even starts.
- Antivirus: ineffective against disguised APKs and user-session installations.
- Sandboxes: bypassed through delayed activation and interface mimicry.
- MDM/EMM: unable to detect apps behaving like legitimate messengers.
- Software encryption: vulnerable to RAM exposure; plaintext accessible before encryption.
The conclusion is self-evident: as long as the operating system handles plaintext, it can be compromised. Protecting the content is no longer enough — the only viable path is to eliminate the readable state altogether within Android.
Abused Permissions — ClayRat’s System Access Vectors
ClayRat exploits Android’s permission model strategically, not technically. During installation, it requests extensive privileges that users commonly accept, trusting what appears to be a legitimate messaging app.
- Read SMS: intercepts incoming texts, including OTP codes for banking or authentication.
- Access contacts: identifies propagation targets within trusted circles.
- Manage calls: intercepts or initiates calls silently.
- Access camera and microphone: captures visual and audio data without user consent.
These permissions — legitimate for genuine messengers — become espionage vectors when granted to disguised malware. They highlight the need for a sovereign, system-independent interface where no plaintext ever transits.
Network Exfiltration — Unencrypted Flows to the C2
Once collected, data is exfiltrated to ClayRat’s command-and-control servers, primarily identified under clayrat.top. Network analysis reveals unencrypted HTTP traffic, exposing both victims and operators to interception.
- Protocol: insecure HTTP (no TLS)
- Method: POST requests carrying JSON payloads of stolen data
- Content: messages, contacts, call logs, device metadata
This clear-text exfiltration confirms that ClayRat implements no end-to-end encryption. It relies entirely on access to unprotected messages. In contrast, a hardware-encrypted messaging architecture renders such exfiltration meaningless — the spyware can only transmit cryptographic noise.
Neutralizing the Android spyware threat ClayRat — Sovereign Defence with DataShielder NFC HSM
This doctrinal rupture paves the way for a new generation of mobile defence — one based on hardware-level message editing that operates independently of the operating system. That is precisely what DataShielder NFC HSM Defence delivers.
Sovereign Isolation with EviPass NFC HSM — contactless security
Unlike conventional apps relying on Android’s sandbox, DataShielder integrates sovereign technology derived from EviCore NFC HSM, embodied here as EviPass NFC HSM. This hybrid hardware–software isolation executes cryptographic operations in a fully autonomous enclave, independent from Android.
- Dedicated sandbox URL: each instance runs in a sealed execution space, inaccessible to other Android processes.
- EviPass NFC HSM: decentralised secret manager, no cloud, no local storage, fully controlled by the sovereign app.
- Defence version: integrates EviOTP NFC HSM, an offline sovereign OTP generator (TOTP/HOTP) — no connectivity required.
This native isolation ensures that neither Android nor spyware such as ClayRat can access credentials, messages, or generated OTPs. It forms an embedded sovereign sandbox — one designed to function even within a compromised system.
Hybrid DataShielder Architecture — the EviCore NFC HSM advantage
DataShielder relies on a patented hybrid architecture built on EviCore NFC HSM, combining:
- A shielded ultra-passive NFC HSM containing segmented keys and hardware-level access control.
- An agile software intelligence layer responsible for orchestration, UI and dynamic cryptographic operations.
This combination enables sovereign hardware editing of messages while maintaining flexible software orchestration. The HSM holds no executable code — it functions as a cryptographic vault, while the software performs controlled operations without ever exposing secrets or plaintext. All sensitive data exists only encrypted within the NFC HSM’s EPROM memory.
Sovereign Encrypted Messaging Interface
Within DataShielder NFC HSM Defence, message drafting occurs in a proprietary cryptographic editor independent of Android. Plaintext exists only briefly in volatile memory within this secure interface. Upon validation, the message is immediately encrypted via the NFC HSM — the only entity holding the keys — and then injected (already encrypted) into the selected messenger (SMS, MMS, RCS, or third-party app). The plaintext is erased instantly and never passes through Android.
| Approach | Message Exposure | Resilience to ClayRat |
|---|---|---|
| Software encryption | Plaintext in Android memory before encryption | Vulnerable |
| Sovereign hybrid editing (DataShielder NFC HSM) | Message never readable by Android | Resilient |
⮞ Cryptographic Mechanism
- AES-256 encryption inside the NFC HSM, no software signing required.
- No plaintext in Android memory — only transient RAM data during input.
- Universal injection: all messengers receive pre-encrypted content.
- Auto-purge: immediate destruction of plaintext after encryption.
- Multi-messenger compatibility: SMS, MMS, RCS, Signal, Telegram, WhatsApp, etc.
The algorithms follow international standards: AES-256 (FIPS 197) and OpenPGP RFC 9580.
Unlike architectures requiring software signatures, DataShielder operates through exclusive encryption/decryption between NFC HSM modules. Any modification attempt renders the message unreadable by design. The HSM acts as a hardware message editor, inherently blinding any spyware attempting inspection.
Embedded Technologies — the EviCore Family
- EviCore NFC HSM — foundational sovereign encryption core.
- EviPass NFC HSM — decentralised password and secret manager.
- EviOTP NFC HSM — offline sovereign OTP generator.
- EviCypher NFC HSM — dedicated module for message, file, and email encryption.
- EviCall NFC HSM — sovereign contact and call manager exclusive to DataShielder Defence.
Strategic Outlook — Toward Embedded Digital Sovereignty and the End of Plaintext
In essence, ClayRat marks the end of an era for mobile security: protection no longer means monitoring intrusions — it means eliminating every plaintext surface. Temporary message exposure is itself a vulnerability, even without a known exploit.
This is why DataShielder NFC HSM Defence embodies a doctrinal break: a hardware architecture where confidentiality precedes transport, and where sovereign encryption is not a software operation but a material act of edition.
As a result, the operating system no longer protects anything readable — it holds nothing decipherable. The message, identifier, OTP, and contact all exist, operate, and vanish inside an isolated enclave beyond the reach of any Android spyware threat ClayRat.
Ultimately, this approach initiates a new generation of embedded cybersecurity, where sovereignty depends on no cloud, OS, or external provider — only on a controlled cryptographic lifecycle from keystroke to transmission.
Hence, it extends to critical and sensitive domains — defence, diplomacy, infrastructure, investigative journalism — for whom message invisibility becomes the ultimate condition of digital freedom.
Technical and Official Sources
- Primary analysis : Zimperium — ClayRat Android Spyware Targeting Russia
- IoC database : ThreatFox / abuse.ch (
clayrat.topC2 domain) - Sovereign monitoring : Freemindtronic — Digital Security Chronicles
- Solutions : Tech Fixes & Security Solutions
Typological Glossary — Key Concepts in Cybersecurity, Hardware Encryption and Digital Sovereignty
- APK : Android Package — the standard installation file of any Android app. Downloading unofficial APKs remains a key infection vector for the ClayRat spyware.
- APT : Advanced Persistent Threat — a highly organised or state-backed actor capable of long-term espionage campaigns; ClayRat shows hallmarks of that level of sophistication.
- C2 : Command & Control — the remote server used by malware to receive orders or exfiltrate stolen data.
- CVSS : Common Vulnerability Scoring System — the global standard for quantifying security-vulnerability severity.
- DNS : Domain Name System — translates domain names (e.g. the C2 address
clayrat.top) into IP addresses; rotating DNS is a common evasion tactic. - EMM / MDM : Enterprise Mobility / Mobile Device Management — enterprise systems often bypassed by behavioural attacks such as ClayRat.
- HSM : Hardware Security Module — a physical component dedicated to encryption and secure key storage; its isolation surpasses any software solution.
- IoC : Indicators of Compromise — technical artefacts (IP addresses, hashes, domains) used by CERT and SOC teams to identify malicious activity such as connections to ClayRat C2s.
- MMS : Multimedia Messaging Service — legacy protocol for media messages, gradually replaced by RCS.
- NFC HSM : Hybrid Hardware Security Module — the core of DataShielder technology. Operates contactlessly via NFC, ensuring full hardware isolation and encryption independent from Android.
- OTP : One-Time Password — single-use authentication code often intercepted by ClayRat through SMS access.
- RAM : Random Access Memory — the volatile zone where conventional encryption apps temporarily expose plaintext; DataShielder removes this exposure entirely.
- RCS : Rich Communication Services — successor to SMS/MMS, also at risk when plaintext remains visible to the OS.
- Sandbox : Traditionally a software isolation environment; in DataShielder’s context it refers to a sovereign hardware enclave operating independently of Android.
- Sideload : Installing an app outside the official Play Store via an APK file — the primary diffusion method of ClayRat.
- SMS : Short Message Service — one of the oldest yet still-exploited phishing and infection channels for Android spyware.
- TOTP / HOTP : Time-based / HMAC-based One-Time Password — global OTP standards; their hardware generation by DataShielder ensures maximum resilience.