2025, Digital Security, Technical News
Quantum computer 6100 qubits ⮞ Historic 2025 breakthrough
A 6,100-qubit quantum computer marks a turning point in the history of computing, raising unprecedented challenges for encryption, cybersecurity, and digital sovereignty.
Executive Summary — Quantum Computer 6,100 Qubits
⮞ Reading Note
This express summary takes ≈ 4 minutes to read. It delivers the essentials: discovery, immediate impact, strategic message, and sovereign levers.
⚡ The Discovery
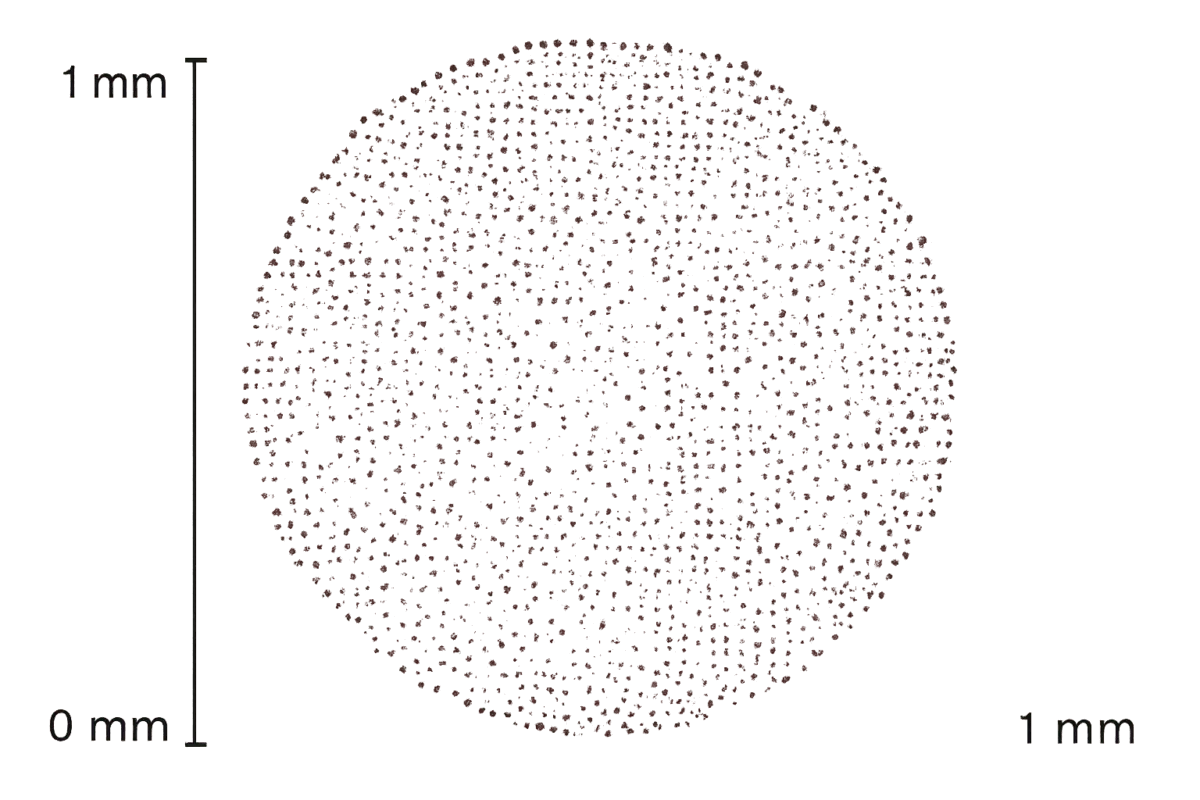
In September 2025, a team from Caltech (United States) set a world record by creating a 6,100-qubit atomic array using neutral atoms in optical tweezers. The breakthrough was published in Nature (UK) and detailed in an arXiv e-print, which highlights key metrics: ~12.6 seconds of coherence, 99.98952% imaging survival, and a zone-based scaling strategy.
This leap far surpasses earlier prototypes (50–500 qubits) from global leaders in quantum computing.
⚠ Strategic Message
Crossing the threshold of several thousand qubits drastically shortens the cryptographic resilience window. If confirmed, the current equilibrium of global cybersecurity will be challenged much sooner than expected.
⎔ Sovereign Countermeasure
Only sovereign solutions such as, DataShielder, and PassCypher can anticipate the collapse of classical encryption by preventing key exposure in the browser environment.
Reading Parameters
Express summary reading time: ≈ 4 minutes
Advanced summary reading time: ≈ 6 minutes
Full chronicle reading time: ≈ 36 minutes
Last updated: 2025-10-02
Complexity level: Advanced / Expert
Technical density: ≈ 73%
Languages: CAT · EN · ES · FR
Linguistic specificity: Sovereign lexicon — high technical density
Accessibility: Screen-reader optimized — semantic anchors included
Editorial type: Strategic Chronicle — Digital Security · Technical News · Quantum Computing · Cyberculture
About the author: Jacques Gascuel, inventor and founder of Freemindtronic®, embedded cybersecurity and post-quantum cryptography expert. A pioneer of sovereign solutions based on NFC, Zero-DOM, and hardware encryption, his work focuses on system resilience against quantum threats and multi-factor authentication without cloud dependency.
TL;DR —
- Unprecedented scaling leap: with 6,100 qubits, the quantum computer crosses a technological threshold that disrupts classical forecasts.
- Direct cryptographic threat: RSA and ECC become vulnerable, forcing anticipation of post-quantum cryptography.
- Shor and Grover algorithms: closer to real exploitation, they transform quantum computing into a strategic weapon.
- Sovereign response: Zero-DOM isolation, NFC/PGP HSMs, and solutions like DataShielder or PassCypher strengthen digital resilience.
- Accelerated geopolitical race: States and corporations compete for quantum supremacy, with major implications for sovereignty and global cybersecurity.
Advanced Summary — Quantum Computer 6,100 Qubits
⮞ Reading Note
This advanced summary takes ≈ 6 minutes to read. It extends the express summary with historical context, cryptographic threats, and sovereign levers.
Inflection Point: Crossing the 500-Qubit Threshold
Major shift: For the first time, an announcement does not just pass 1,000 qubits but leaps directly to 6,100.
Why systemic: Cryptographic infrastructures (RSA/ECC) relied on the assumption that such thresholds would not be reached for several decades.
| Vector | Scope | Mitigation |
|---|---|---|
| Shor’s Algorithm | Breaks RSA/ECC | Adopt post-quantum cryptography (PQC) |
| Grover’s Algorithm | Halves symmetric strength | Double AES key lengths |
| Quantum Annealing | Optimization & AI acceleration | Isolate sovereign models |
These insights now set the stage for the full Chronicle. It will explore in depth:
- The historic race: IBM, Google, Microsoft, Atos, IonQ, neutral atoms
- Attack scenarios: RSA broken, ECC collapse, degraded symmetric systems
- Geopolitical competition and sovereignty
- Sovereign countermeasures: Zero-DOM, NFC/PGP HSMs, DataShielder
In sovereign cybersecurity ↑ This chronicle belongs to the Digital Security section for its zero-trust countermeasures, and to Technical News for its scientific contribution: segmented architectures, AES-256 CBC, volatile memory, and key self-destruction.
- 🔝 Back to top
- Executive Summary
- Advanced Summary
- Caltech’s 6,100-Qubit Breakthrough
- Historic Race
- Quantum Performance by Nation
- Encryption Threats (RSA, AES, ECC, PQC)
- Quantum Attack Vectors
- Sovereign Countermeasures
- Use Cases — DataShielder & PassCypher
- Weak Signals — Quantum Geopolitics
- Strategic Outlook
- What We Didn’t Cover
- Glossary
- FAQ
Caltech’s 6,100-Qubit Breakthrough — Team, Context & Architecture
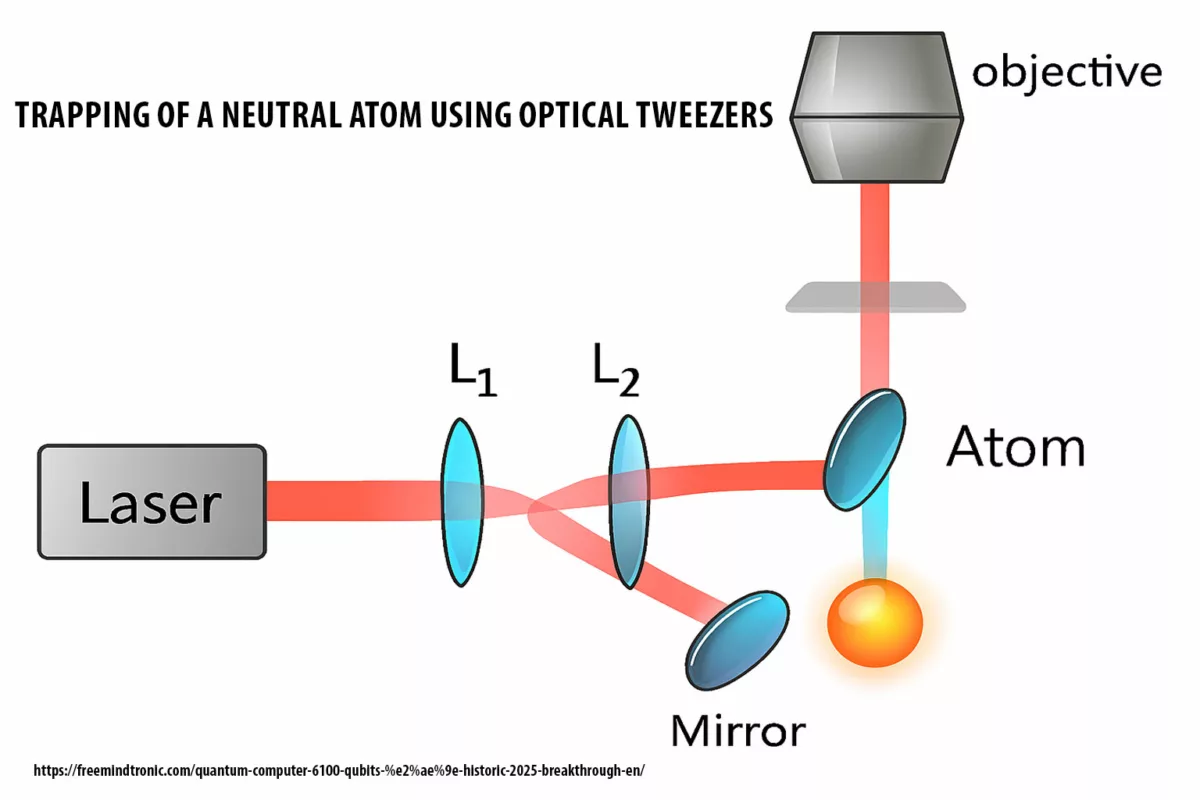
In September 2025, researchers at the California Institute of Technology (Caltech) unveiled the first-ever 6,100-qubit neutral atom array. This achievement, peer-reviewed in Nature and detailed in an arXiv preprint, marks a quantum leap in scale, coherence, and imaging fidelity. The project was led by the Endres Lab and described by Manetsch, Nomura, Bataille, Leung, Lv, and Endres. Their architecture relies on neutral atoms confined by optical tweezers — now considered one of the most scalable pathways toward fault-tolerant quantum computing.
Lead Contributors
- Hannah J. Manetsch — Lead experimentalist in neutral atom physics. Designed and executed the large-scale trapping protocol for cesium atoms, ensuring stability across 12,000 sites. First author of the Nature publication.
- Gyohei Nomura — Specialist in optical tweezer instrumentation and control systems. Engineered the laser array configuration and dynamic readdressing logic for atom placement and transport.
- Élie Bataille — Expert in coherence characterization and quantum metrology. Led the measurement of hyperfine qubit lifetimes (~12.6 s) and validated long-duration stability under operational load.
- Kon H. Leung — Architect of the zone-based computing model. Developed benchmarking protocols and error-correction simulations for scalable quantum operations across modular regions.
- Xudong Lv — Imaging and dynamics specialist. Designed high-fidelity imaging systems (>99.99%) and analyzed atom mobility during pick-up/drop-off operations with randomized benchmarking.
- Manuel Endres — Principal Investigator and head of the Endres Lab at Caltech. Directed the overall research strategy, secured funding, and coordinated the integration of experimental and theoretical advances toward fault-tolerant quantum computing.
Technical Milestones
 |
|
Architecture & Technology
The Caltech system uses neutral atoms trapped by optical tweezers — finely focused laser beams that isolate and manipulate atoms with high precision. Thousands of traps can be reconfigured dynamically, enabling modular growth and stability. This supports the zone-based scaling strategy outlined in the technical note.
Primary Sources
Further Reading
Historic Race — Toward the 6,100-Qubit Quantum Computer
The path to 6,100 qubits did not emerge overnight. It is the result of a global technological race spanning more than a decade, with key milestones achieved by major players in quantum science and engineering.
- 2019 — Google claims quantum supremacy with its 53-qubit superconducting processor, Sycamore, solving a task faster than classical computers.
- 2020 — IBM unveils its roadmap toward 1,000 qubits, emphasizing modular superconducting architectures.
- 2021 — IonQ expands trapped-ion systems to beyond 30 qubits, focusing on error correction and commercial applications.
- 2022 — Atos positions itself with quantum simulators, bridging hardware gaps with HPC integration.
- 2023 — Microsoft doubles down on topological qubits research, although practical results remain pending.
- 2024 — IBM demonstrates prototypes approaching 500 qubits, with increasing coherence but mounting error rates.
- 2025 — Caltech leaps far ahead by creating the first 6,100-qubit neutral atom array, eclipsing competitors’ forecasts by decades.
Key inflection: While IBM, Google, and Microsoft pursued superconducting or topological pathways, Caltech’s neutral atom approach bypassed scaling bottlenecks, delivering both magnitude and usability. This breakthrough redefines the pace of quantum progress and accelerates the countdown to post-quantum cryptography.
Quantum Performance by Nation: Sovereign Architectures & Strategic Reach (2025)
Strategic Overview
This section maps the global quantum computing landscape, highlighting each country’s dominant architecture, qubit capacity, and strategic posture. It helps benchmark sovereign capabilities and anticipate cryptographic rupture timelines.
Comparative Table
| 🇺🇳 Country | Lead Institution / Program | Architecture Type | Qubit Count (2025) | Strategic Notes |
|---|---|---|---|---|
| 🇺🇸 United States | Caltech, IBM, Google, Microsoft, IonQ | Neutral atoms, superconducting, topological, trapped ions | 6,100 (Caltech), 1,121 (IBM), 100+ (Google) | Zone-based scaling, Majorana prototype, supremacy benchmarks |
| 🇫🇷 France | Atos / Eviden | Hybrid HPC, emulated | ~50 simulated | QLM integration, sovereign HPC-quantum convergence |
| 🇨🇳 China | USTC / Zuchongzhi | Superconducting | ~105 qubits | Claims 1M× speed over Sycamore, national roadmap |
| 🇷🇺 Russia | Russian Quantum Center | Superconducting / ion hybrid | ~50 qubits | Focus on secure comms, national sovereignty |
| 🇰🇷 South Korea | Quantum Korea | Superconducting + photonic | ~30 qubits | Photonic emphasis, national R&D strategy |
| 🇯🇵 Japan | RIKEN / NTT / Fujitsu | Superconducting / photonic | ~64 qubits | Hybrid annealing + gate-based systems |
| 🇨🇦 Canada | D-Wave Systems | Quantum annealing | >5,000 qubits | Optimization-focused, not universal gate-based |
| 🇩🇪 Germany | Fraunhofer / IQM | Superconducting / ion | ~30 qubits | EU-funded scaling, industrial integration |
| 🇬🇧 United Kingdom | Oxford Quantum Circuits | Superconducting / photonic | ~32 qubits | Modular cloud-accessible systems |
| 🇮🇳 India | MeitY / IISc | Superconducting (early stage) | <20 qubits | National mission launched, early prototypes |
| 🇮🇱 Israel | Quantum Machines / Bar-Ilan | Control systems / hybrid | Control layer focus | Specializes in orchestration and quantum-classical integration |
Encryption Threats — RSA, AES, ECC, PQC
The arrival of a 6,100-qubit quantum computer poses an existential challenge to today’s cryptography. Algorithms once considered secure for decades may collapse far sooner under Shor’s and Grover’s quantum algorithms.
| Cryptosystem | Current Assumption | Quantum Threat | Timeline |
|---|---|---|---|
| RSA (2048–4096) | Backbone of web & PKI security | Broken by Shor’s algorithm with thousands of qubits | Imminent risk with >6,000 usable qubits |
| ECC (Curve25519, P-256) | Core of TLS, blockchain, mobile security | Broken by Shor’s algorithm, faster than RSA | Critical risk, harvest now / decrypt later |
| AES-128 | Standard symmetric encryption | Halved security under Grover’s algorithm | Still usable if upgraded to AES-256 |
| AES-256 | High-grade symmetric security | Quantum-resistant when key size doubled | Safe for now |
| Post-Quantum Cryptography (PQC) | Lattice-based, hash-based, code-based | Designed to resist Shor & Grover | Migration required before 2030 |
Key point: While symmetric encryption can survive by increasing key sizes, all asymmetric systems (RSA, ECC) become obsolete once thousands of error-tolerant qubits are available. This is no longer a distant scenario — it is unfolding now.
Quantum Attack Vectors
The emergence of a 6,100-qubit quantum computer redefines the landscape of cyber attacks. Threat actors — state-sponsored or criminal — can now exploit new attack vectors that bypass today’s strongest cryptography.
⚡ Shor’s Algorithm
- Target: RSA, ECC, Diffie-Hellman
- Impact: Immediate collapse of asymmetric encryption
- Scenario: TLS sessions, VPNs, blockchain signatures exposed
⚡ Grover’s Algorithm
- Target: Symmetric algorithms (AES, SHA)
- Impact: Security levels halved
- Scenario: AES-128 downgraded, brute-force viable with scaled quantum hardware
⚡ Harvest Now / Decrypt Later (HNDL)
- Target: Encrypted archives, communications, medical & financial data
- Impact: Today’s encrypted traffic may be stored until broken
- Scenario: Nation-states archiving sensitive data for post-quantum decryption
⚡ Hybrid Quantum-Classical Attacks
- Target: Blockchain consensus, authentication protocols
- Impact: Amplified by combining quantum speed-up with classical attack chains
- Scenario: Faster key recovery, bypass of multi-factor authentication
Sovereign Countermeasures Against the Quantum Computer 6,100 Qubits Breakthrough
The historic quantum computer 6100 qubits announcement forces a strategic rethink of digital security. Therefore, organisations cannot rely solely on traditional encryption. Instead, they must adopt a sovereign doctrine that reduces exposure while preparing for post-quantum cryptography. This doctrine rests on three pillars: Zero-DOM isolation, NFC/PGP hardware security modules, and offline secret managers.
1) Zero-DOM Isolation — Protecting Keys From Quantum Computer Exploits
Firstly, Zero-DOM isolation ensures that cryptographic operations remain outside the browser’s interpretable environment. Consequently, the quantum computer 6100 qubits cannot exploit web vulnerabilities to exfiltrate secrets. By creating a minimal, auditable runtime, this countermeasure blocks XSS, token theft, and other injection attacks.
2) Hardware Anchoring — NFC and PGP HSMs Against 6,100-Qubit Quantum Attacks
Secondly, sovereign defence requires hardware anchoring of keys. With NFC/PGP HSMs, master secrets never leave secure hardware. As a result, even if a quantum computer 6100 qubits compromises the operating system, the keys remain inaccessible. Key segmentation further ensures that no single device contains the entire cryptographic secret.
3) Offline Secret Managers — DataShielder & PassCypher in the Quantum Era
Finally, offline secret managers such as DataShielder and PassCypher eliminate persistent storage of keys. Instead, keys are materialised in volatile memory only during use, then destroyed. Consequently, the threat posed by quantum computers of thousands of qubits is mitigated by denying them access to long-lived archives.
Use Cases — DataShielder & PassCypher Facing the 6,100-Qubit Quantum Computer
After presenting the principles of sovereign countermeasures, it is essential to illustrate their concrete application.
Two solutions developed by Freemindtronic, DataShielder and PassCypher, demonstrate how to anticipate today the threats posed by a quantum computer with 6,100 qubits.
DataShielder: Securing Sensitive Communications
DataShielder relies on a hybrid hardware/software HSM, available in two versions:
- NFC HSM version: the AES-256 key is stored on a physical NFC device, used via a mobile NFC application. It is loaded into volatile memory only during use, then self-destructed. No persistent trace remains in the host environment.
- Browser PGP HSM version: based on a pair of autonomous symmetric segments of 256 bits each:
- The first segment is stored in the browser’s local storage,
- The second segment is kept on a physical NFC device.
These segments are useless in isolation.
The browser extension must know the exact location of both segments to trigger the sovereign concatenation algorithm, dynamically reconstructing a usable AES-256 CBC key.
This key is loaded into volatile memory for the operation, then self-destructed immediately after use.
This mechanism guarantees that the full key never exists in persistent memory, neither in the browser nor in the OS.
PassCypher: Sovereign Secret Manager
PassCypher also implements these two approaches:
- NFC HSM version: allows users to add more than 9 cumulative key segments, each linked to a trust criterion. Reconstructing the AES-256 key requires the simultaneous presence of all segments, ensuring total hardware segmentation.
- Browser PGP HSM version: identical to DataShielder’s, with two autonomous 256-bit segments dynamically concatenated to generate a temporary AES-256 CBC key, loaded into volatile memory then self-destructed after use.
These mechanisms are protected by two complementary international patents:
– 📄 WO2018154258 – Segmented key authentication system
– 📄 WO2017129887 – Embedded electronic security system
Together, they ensure sovereign protection of secrets — off-cloud, off-OS, and resilient against post-quantum cryptographic disruption.
Anticipating Quantum Threats
By combining these two approaches, Freemindtronic illustrates a clear and immediately operational strategy: on one hand, physically isolating secrets to prevent exfiltration; on the other, avoiding their software exposure by eliminating interpretable environments, while ensuring immediate resilience against future threats.
In this technological shift, where the prospect of a quantum computer reaching 6,100 qubits accelerates the urgency of migrating to post-quantum cryptography, these solutions emerge as strategic safeguards — sovereign, modular, and auditable.
This figure exceeds the estimated age of the universe, highlighting the robustness of secrets stored in EviTag NFC HSM or EviCard NFC HSM devices.
This demonstration is detailed in the chronicle 766 trillion years to find a 20-character password, and reinforces the doctrine of segmentation, volatile memory, and key self-destruction.
After exploring these use cases, it is important to focus on the weak signals surrounding the quantum race.
They reveal less visible but equally decisive issues linked to geopolitics, standardisation, and industrial espionage.
Weak Signals — Quantum Geopolitics
The quantum computer 6100 qubits breakthrough is not only a scientific milestone. It also generates geopolitical ripples that reshape strategic balances. For decades, the United States, China, and Europe have invested in quantum technologies. However, the scale of this announcement forces all actors to reconsider their timelines, alliances, and doctrines of technological sovereignty.
United States: Through Caltech and major industry players (IBM, Google, Microsoft, IonQ), the U.S. maintains technological leadership. Yet, the very fact that an academic institution, rather than a corporate lab, reached 6,100 qubits first reveals a weak signal: innovation does not always follow the expected industrial path. Consequently, Washington will likely amplify funding to ensure that such breakthroughs remain aligned with national security interests.
China: Beijing has long framed quantum computing as part of its Made in China 2025 strategy. A 6,100-qubit quantum computer in the U.S. accelerates the perceived gap, but also legitimises China’s own programs. Therefore, one can expect intensified investments, not only in hardware but also in quantum-safe infrastructures and military applications. In fact, Chinese state media have already begun positioning sovereignty over data as a counterbalance to American advances.
Europe: The European Union, while a pioneer in cryptography, risks strategic dependency if it remains fragmented. Initiatives such as EuroQCI and national PQC roadmaps show awareness, but they remain reactive. As a result, the European sovereignty narrative will need to integrate both quantum R&D and deployment of sovereign countermeasures such as Zero-DOM, DataShielder, and PassCypher.
Strategic Outlook — Quantum Computer 6,100 Qubits
The announcement of a quantum computer with 6,100 qubits redefines more than technology. It resets strategic horizons across security, economy, and sovereignty. Until recently, experts assumed that the cryptographic impact of quantum machines would not materialize until the 2030s or beyond. However, this milestone has forced the clock forward by at least a decade. As a result, decision-makers now face three plausible trajectories.
1) Scenario of Rupture — Sudden Collapse of Cryptography
In this scenario, a 6,100-qubit quantum breakthrough triggers the abrupt fall of RSA and ECC. Entire infrastructures — from banking networks to PKIs and blockchain systems — face systemic failure. Governments impose emergency standards, while adversaries exploit unprotected archives harvested years earlier. Although radical, this scenario illustrates the disruptive potential of quantum acceleration.
2) Scenario of Adaptation — Accelerated Migration to PQC
Here, the immediate shock is contained by swift deployment of post-quantum cryptography (PQC). Organisations prioritise hybrid models, combining classical and PQC algorithms. Consequently, long-lived assets (archives, digital signatures, PKI roots) are migrated first, while symmetric encryption is reinforced with AES-256. This scenario aligns with NIST’s ongoing standardisation and offers a pragmatic path toward resilience.
3) Scenario of Sovereignty — Digital Autonomy as Strategic Priority
Finally, a sovereign perspective emerges: the quantum computer 6100 qubits becomes a catalyst for autonomy. Nations and organisations not only deploy PQC but also invest in sovereign infrastructures — including Zero-DOM, DataShielder, and PassCypher. In this outlook, quantum risk becomes an opportunity to reinforce digital independence and redefine trust architectures at a geopolitical level.
What We Didn’t Cover — Editorial Gaps & Future Updates
Every chronicle has its limits. This one focused on the quantum computer 6100 qubits milestone, its cryptographic impact, and the sovereign countermeasures required. However, there are many dimensions that deserve dedicated analysis and will be addressed in upcoming updates.
- Standardisation processes: NIST PQC algorithms, European ETSI initiatives, and ISO workstreams shaping the global transition.
- Industrial deployment: How banks, telecom operators, and cloud providers are experimenting with hybrid post-quantum infrastructures.
- Ethical and social impacts: From data sovereignty debates to the role of academia in securing open innovation in the quantum era.
- Emerging weak signals: New patents, military investments, and private sector roadmaps beyond Caltech’s 6,100-qubit breakthrough.
In fact, this chronicle is deliberately living. As standards evolve and as new demonstrations emerge, we will enrich this narrative with fresh data, updated insights, and additional case studies. Therefore, readers are invited to revisit this page regularly and follow the dedicated Digital Security and Technical News sections for further developments.
Glossary — Quantum Computer 6,100 Qubits
This glossary explains the key terms used in this chronicle on the quantum computer 6100 qubits breakthrough. Each entry is simplified without losing scientific precision, to make the narrative more accessible.
- Qubit: The quantum equivalent of a classical bit. Unlike bits, which can be 0 or 1, qubits can exist in superposition, enabling parallel computation.
- Neutral Atom Array: A grid of atoms trapped and manipulated using optical tweezers. Caltech’s 6,100-qubit quantum machine is based on this architecture.
- Optical Tweezers: Highly focused laser beams used to trap, move, and arrange individual atoms with extreme precision.
- Coherence Time: The duration during which a qubit maintains its quantum state before decoherence. For Caltech’s array, ≈12.6 seconds.
- Imaging Survival: The probability that an atom remains intact after quantum state measurement. Caltech achieved 99.98952% survival.
- Shor’s Algorithm: A quantum algorithm that factors large numbers efficiently, breaking RSA and ECC encryption once enough qubits are available.
- Grover’s Algorithm: A quantum algorithm that accelerates brute-force search, effectively halving the security of symmetric ciphers such as AES.
- Harvest Now, Decrypt Later (HNDL): A strategy where encrypted data is intercepted and stored today, awaiting future decryption by large-scale quantum computers.
- Zero-DOM Isolation: A sovereign architecture that executes cryptographic operations outside the browser/DOM, preventing key exposure in interpretable environments.
- NFC/PGP HSM: Hardware Security Modules that store cryptographic keys offline, activated via NFC or PGP protocols for secure signing and decryption.
- PQC (Post-Quantum Cryptography): Cryptographic algorithms designed to resist attacks from quantum computers with thousands of qubits.
- Sovereignty: In cybersecurity, the ability of a nation, organisation, or individual to secure digital assets without dependency on foreign infrastructure or cloud services.
FAQ — Quantum Computer 6,100 Qubits
This FAQ compiles common questions raised on expert forums, Reddit, Hacker News, and professional networks after the announcement of the quantum computer 6100 qubits. It addresses technical doubts, strategic implications, and everyday concerns.
2. Upgrade symmetric encryption to AES-256.
3. Deploy hybrid PQC solutions.
4. Anchor keys in hardware (NFC/PGP HSM).
In fact, a 90-day action plan is already recommended.
Annexes & Quantum Computer 6,100 Qubits
The announcement of a quantum computer with 6,100 qubits marks a decisive turning point in digital history. Indeed, it accelerates scientific forecasts, while at the same time disrupting cryptographic assumptions, and consequently forces a rethinking of sovereignty in cyberspace. Therefore, the central message is clear: adaptation cannot wait.
Final Perspective: Sovereign infrastructures — “target=”_blank” rel=”noopener”>Zero-DOM isolation, DataShielder, and PassCypher — illustrate a doctrine where quantum disruption does not lead to collapse but to strategic resilience. In fact, the real milestone is not just 6,100 qubits, but our capacity to transform threat into sovereignty.
References
- Nature (2025) — Caltech 6,100 Qubit Array
- Caltech — Press Release
- arXiv Preprint — Neutral Atom Scaling
- NIST Post-Quantum Cryptography Project
- EU — EuroQCI Initiative




































































































Pingback: Authentification multifacteur : anatomie, OTP, risques - Freemindtronic