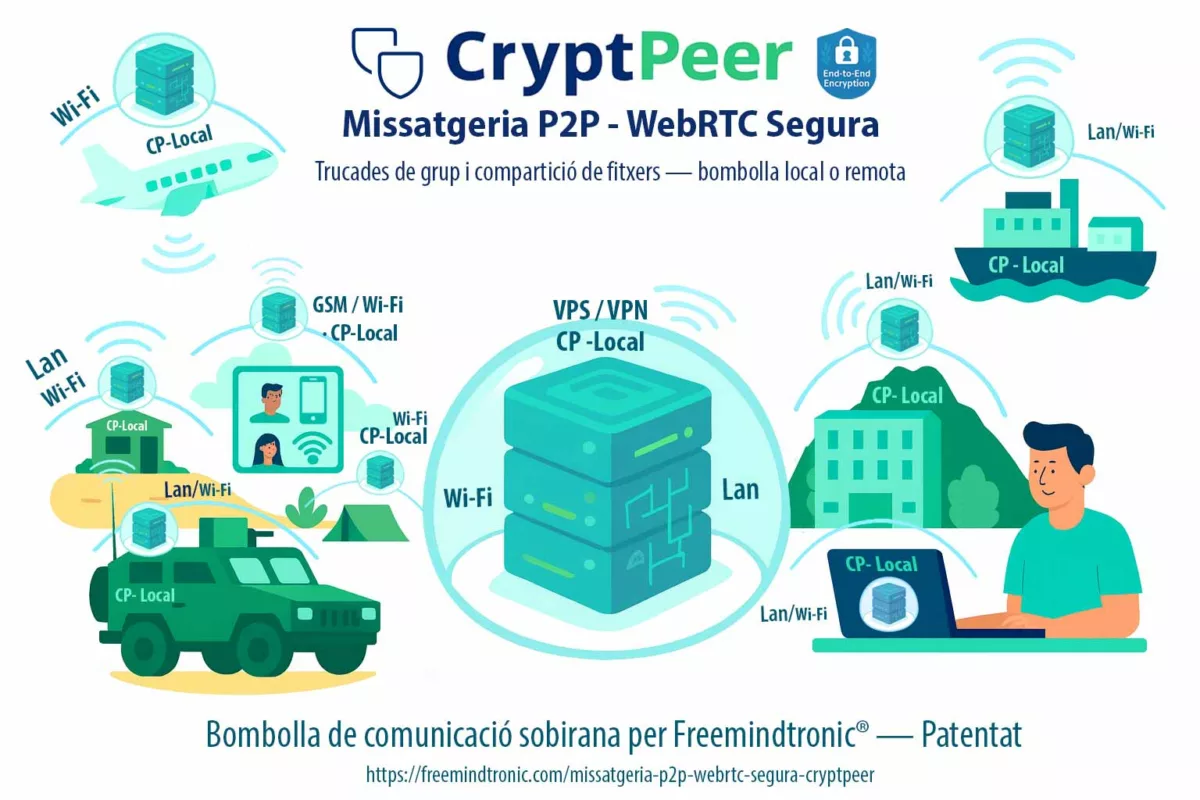
Missatgeria P2P WebRTC segura al navegador és l’esquelet tècnic i sobirà de la comunicació directa xifrada de cap a cap amb CryptPeer. Aquesta crònica explica com aquesta missatgeria P2P segura, 100 % basada en navegador, crea canals WebRTC P2P sense servidor central ni núvol públic, amb control local de claus, flux i metadades. El model peer-to-peer, reforçat per un node de relé local autoallotjat que només encaminada trànsit xifrat, redueix la superfície d’atac i protegeix la sobirania digital. Les tecnologies P2P i WebRTC converteixen cada usuari en únic titular del secret, del canal i de la seva exposició criptogràfica: provar la sobirania mitjançant el disseny.
Resum ràpid — Missatgeria P2P WebRTC segura, què cal retenir
Lectura ràpida ≈ 2 min — WebRTC i el model peer-to-peer són l’eix central de la Missatgeria P2P WebRTC segura: comunicació directa i xifrada independent de qualsevol servidor de núvol de tercers. CryptPeer es recolza en aquesta arquitectura per establir un canal sobirà entre navegadors, on cada usuari conserva el control local del flux, de les claus i de la seva pròpia superfície d’exposició.
Principi — Connexió directa P2P sense servidor central
La connexió direct-to-direct substitueix l’esquema centralitzat clàssic. El flux ja no passa per una plataforma de tercers: es negocia, s’encripta i es manté exclusivament entre els parells, amb com a màxim un node de relé local controlat per l’usuari que només reexpedeix trànsit xifrat. Aquest enfocament redueix la superfície d’atac, limita la recopilació involuntària de dades i neutralitza la dependència estructural de les infraestructures de núvol.
Fonament — WebRTC, ICE/STUN/TURN i xifratge DTLS-SRTP
WebRTC construeix la comunicació en temps real sobre un tríptic: negociació SDP, traversada de NAT via ICE/STUN/TURN i xifratge DTLS-SRTP. El DataChannel completa el dispositiu amb un canal P2P robust per a missatges, metadades i transferències binàries.
Observació — Connexió directa majoritària amb relé local opcional
En el 85–90 % dels casos, la connexió directa s’estableix sense cap relé, assegurant una latència mínima i un control total. En la resta de casos, un node de relé opcional, autoallotjat i portàtil pot reexpedir només trànsit xifrat de cap a cap. El servidor de senyalització s’utilitza només abans de la connexió i no conserva cap estat; un cop establert l’enllaç, el camí de comunicació resta íntegrament sota control dels usuaris.
En joc — Sobirania digital i control local del flux
Aquesta arquitectura no és només una tria tècnica. Desplaça el centre de gravetat de la confiança — del núvol cap a l’usuari — i recorda que la sobirania s’exerceix mitjançant el control local: xifratge de cap a cap, absència d’emmagatzematge en clar als servidors i autonomia de xarxa.
⮞ En resum — Missatgeria P2P WebRTC segura com a nou estàndard sobirà
CryptPeer demostra que la Missatgeria P2P WebRTC segura no és una solució de recés, sinó un nou estàndard de comunicació directa, xifrada i independent del núvol, on la confiança es prova pel disseny i no per delegació.
Paràmetres de lectura
Resum ràpid: ≈ 2 min
Resum ampliat: ≈ 7 min
Crònica completa: ≈ 32 min
Data de publicació: 2025-11-14
Darrera actualització: 2025-11-14
Nivell de complexitat: Sobirana & Tècnica
Densitat tècnica: ≈ 78 %
Idiomes disponibles: FR · EN · ES · CAT · AR
Focal temàtic: P2P, WebRTC, xifratge, comunicació directa
Tipus editorial: Crònica — Freemindtronic Cyberculture Ser
ies
Nivell d’impacte: 8,4 / 10 — tècnic i sobirà
FM-AI-2025-11-SMD5.

Taula de continguts
- Resum ràpid — Punts clau
- Resum ampliat — P2P, WebRTC i sobirania tècnica
- Arquitectura P2P, protocol WebRTC i sobirania comunicacional
- Model P2P — Funcionament, fortaleses i límits
- WebRTC — Negociació, xifratge i fluxos directes
- ICE, STUN, TURN — Traversada NAT i resiliència
- DataChannel — Intercanvis sobirans fora de mitjans
- Aplicació CryptPeer — Comunicació directa provada
- Seguretat — DTLS, SRTP i model de confiança local
- Rendiment — Latència, optimització i estabilitat
- Reptes contemporanis — P2P vs polítiques de xarxa
- Sobirania tècnica — Prova local i no-conservació
- Perspectives — Cap a un Internet descentralitzat
- FAQ P2P & WebRTC
- Què no hem tractat
- Casos d’ús sobirans — Freemindtronic
Resum ampliat — Arquitectures P2P i WebRTC per a Missatgeria P2P WebRTC segura
Segons l’IETF (RFC 8825, 8826), WebRTC defineix un conjunt de mecanismes que permeten que dos dispositius negociïn, xifrin i mantinguin una connexió directa. Aquesta arquitectura va molt més enllà d’una simple optimització de xarxa: imposa un paradigma on cada usuari conserva el control operacional del canal, sense delegar-lo a un servidor de tercers. La sobirania comunicacional, aquí, depèn de la capacitat d’establir, mantenir i assegurar una connexió de cap a cap sense dependència estructural.
Definició tècnica — IETF WebRTC Framework (RFC 8825)
“WebRTC és un conjunt de protocols que permeten establir sessions multimèdia interactives entre navegadors o aplicacions utilitzant un model de comunicació peer-to-peer segur.”
Implica:
- Negociació SDP: descripció de capacitats d’àudio/vídeo, còdecs i paràmetres criptogràfics;
- Transports segurs: DTLS per a l’intercanvi de claus, SRTP per protegir els fluxos multimèdia;
- Resolució de connectivitat: ICE, STUN i TURN per trobar un camí directe a través dels NAT;
- Canals de dades P2P: DataChannel per a intercanvis ràpids i sobirans fora de mitjans.
En una lectura sistèmica, Rescorla (autor del model de seguretat WebRTC) recorda que la confidencialitat real en les comunicacions depèn abans de res de la capacitat d’evitar intermediaris. El xifratge només és pertinent si el canal es manté sobirà, és a dir, establert i controlat pels mateixos parells.
Per a Hardy i els treballs del W3C, l’ascens de les arquitectures centralitzades obliga a donar prioritat als protocols que permeten interaccions directes. L’autonomia tècnica es converteix en una condició prèvia per protegir identitats i metadades.
Marcs normatius contemporanis — Cap a una comunicació provada i sobirana
Els estàndards moderns de ciberseguretat convergeixen en la mateixa conclusió:
- NIST SP 800-207 (Zero Trust) — imposa una verificació contínua i rebutja tota confiança implícita en els servidors;
- ENISA 2024 — Secure communications — valora les arquitectures de local trust on la prova tècnica la té l’usuari;
- IETF ICE Working Group — confirma que la resiliència de la comunicació depèn de la capacitat d’establir camins directes;
- Reglament (UE) 2023/1543 e-Evidence — subratlla que la no-conservació de fluxos i metadades aporta una “conformitat per absència”.
Aquests marcs reforcen la doctrina Freemindtronic: la confiança s’ha de provar pel disseny, no delegar-se.
El repte contemporani consisteix, doncs, a distingir entre una “comunicació xifrada” (dependent d’un servidor que relayi el flux) i una “comunicació sobirana” (sense tercers, sense emissió de metadades més enllà dels parells).
Escenari d’amenaces — La batalla s’ha traslladat a la missatgeria
Des que la interceptació massiva és menys rendible (generalització del xifratge, TLS, DoH), el camp de batalla s’ha desplaçat al cor mateix de les aplicacions de missatgeria. És aquí on convergeixen intencions, grafs socials i decisions operatives: un sol implant pot, en teoria, donar accés a “tota una vida”. Les mateixes cadenes d’explotació 0-click i les mateixes famílies de spyware apunten avui a Signal, WhatsApp, Telegram i els seus clons, ja siguin operats per serveis estatals o per venedors comercials de spyware. La frontera entre operacions d’Estat i ofertes privades es difumina: en la pràctica, tothom ataca els mateixos maons (parsing d’imatge/àudio, superfícies 0-click, clients oficials o llurs rèpliques), cosa que industrialitza la compromissió de les missatgeries xifrades.
Taula de correspondència — Marcs P2P & WebRTC
| Marc tècnic | Concepte clau | Modalitat d’aplicació | Tipus de dependència | Font |
|---|---|---|---|---|
| IETF WebRTC 8825–8826 | Comunicació directa segura | Negociació local · DTLS/SRTP | Xarxa (NAT) | IETF |
| ICE/STUN/TURN | Descobriment i traversada NAT | Resolució d’adreces · camins directes | Operadors de xarxa | RFC 8445 |
| W3C WebRTC API | Autonomia del costat usuari | Gestió local · DataChannel | Aplicacions client | W3C |
| NIST SP 800-207 | Zero Trust interactiu | Prova local · validació contínua | Servidors de tercers | NIST |
1️⃣ Transport (trobar un camí directe),
2️⃣ Xifratge (DTLS/SRTP local),
3️⃣ Autonomia (DataChannel, cap servidor de tercers al bucle).
Aquesta convergència fonamenta una comunicació realment sobirana, on cada parell posseeix la prova completa de la confidencialitat.
Així, la comunicació esdevé una extensió de l’autonomia tècnica: controlar el teu canal és autogovernar-te a l’espai digital.
Les cròniques mostrades més amunt ↑ formen part de la mateixa Cyberculture secció editorial Cyberculture. Amplien l’anàlisi sobre les arquitectures sobiranes, la criptografia local i els models distribuïts, aportant llum sobre la tensió entre dependència de xarxa i autonomia tècnica. Aquesta selecció complementa la present crònica dedicada a la comunicació directa amb Missatgeria P2P WebRTC segura, pedra angular de la doctrina Freemindtronic.
Crònica — Arquitectura P2P WebRTC i sobirania en la Missatgeria P2P segura
La Missatgeria P2P WebRTC segura representa un dels canvis més significatius en l’arquitectura de xarxa des de l’ascens d’Internet modern. A diferència de les infraestructures centralitzades, on un servidor governa l’accés, les metadades i la persistència, el model peer-to-peer distribueix aquestes funcions entre els mateixos usuaris. Quan aquesta lògica es combina amb WebRTC, el resultat és un canal sobirà, xifrat de cap a cap i gairebé instantani, el control tècnic del qual pertany exclusivament als dos participants — l’essència de la missatgeria segura P2P WebRTC.
En aquesta crònica analitzem com WebRTC permet una comunicació realment directa i sense servidor, combinant SDP (senyalització i negociació), ICE/STUN/TURN (connectivitat), DTLS/SRTP (xifratge de cap a cap) i el DataChannel (transport de dades). També examinem el paper central de CryptPeer, que transforma aquests principis en una aplicació de missatgeria segura, sobirana i sense núvol, amb cap retenció en clar al servidor, cap relé extern de tercers i cap recopilació explotable de dades.
Model P2P — Funcionament, punts forts i límits en la Missatgeria P2P WebRTC segura
El model peer-to-peer descriu una arquitectura en què cada entitat actua alhora com a emissor, receptor i node operacional. En eliminar les funcions centralitzades, el P2P desplaça la confiança cap a les vores de la xarxa — els parells. Aquest disseny distribuït millora de manera natural la resiliència, però també exigeix un control més estricte sobre la connectivitat, l’autenticació i la gestió del trànsit.
Key insights — El model P2P es basa en tres característiques estructurals:
- Autonomia: cap entitat central supervisa, filtra o valida els intercanvis.
- Resiliència: fins i tot amb xarxes fragmentades, els parells poden comunicar-se mentre existeixi un camí.
- Confidencialitat estructural: l’absència d’intermediaris redueix automàticament la superfície d’atac i l’exposició.
Arquitectura distribuïda: control local del flux
En una arquitectura P2P, cada parell conserva el context complet de sessió. Això significa que la descripció del flux, la negociació, el xifratge i la transferència de dades no es descarreguen en un servidor central, sinó que es gestionen localment als extrems. Aquesta autonomia tècnica reescriu el model de confiança: l’usuari ja no depèn d’un tercer per intercanviar missatges, mitjans o fitxers mitjançant una Missatgeria P2P WebRTC segura.
Límits estructurals del model P2P
Com que els parells solen estar darrere de routers NAT o tallafocs restrictius, el descobriment d’adreces i l’establiment de camins requereixen estratègies més complexes que en un model centralitzat. Justament és això el que WebRTC automatitza, preservant alhora la sobirania operacional de la comunicació xifrada de cap a cap entre parells.
WebRTC — El nucli de la comunicació directa
WebRTC és un conjunt estructurat de protocols, especificat per l’IETF i el W3C, que permet que dos dispositius es comuniquin directament sense recórrer a un servidor de relé central operat per un tercer. A diferència de les tecnologies tradicionals (VoIP basat en SIP, WebSocket, túnels RTP), WebRTC encapsula tot el procés — negociació, xifratge, descobriment de xarxa i transport de mitjans/dades — en una arquitectura coherent i moderna dissenyada per a una comunicació segura, sobirana i en temps real.
Key insights — WebRTC es recolza en quatre pilars:
- SDP: descriu i negocia les capacitats dels parells.
- ICE/STUN/TURN: troba el millor camí de xarxa per a la connectivitat directa.
- DTLS/SRTP: xifratge de cap a cap establert localment per als fluxos multimèdia.
- DataChannel: una capa de transport de dades P2P sobirana per a missatges i fitxers.
SDP — El llenguatge comú dels parells
El Session Description Protocol descriu totes les capacitats de cada parell: còdecs, claus, ports i opcions de xarxa. Aquesta descripció mai no s’emmagatzema al servidor de senyalització, que només la transmet. En conseqüència, només els dispositius dels usuaris conserven l’estat real de la sessió, la qual cosa és essencial per a un model de Missatgeria P2P WebRTC segura sense servidor i de coneixement zero.
DTLS i SRTP — Xifratge negociat localment
A diferència de les plataformes de missatgeria clàssiques, on el servidor sovint orquestra la gestió de claus, WebRTC negocia les claus localment entre parells mitjançant DTLS. El xifratge SRTP, derivat de DTLS, protegeix després els fluxos multimèdia. El resultat és que fins i tot un servidor de relé TURN no pot desxifrar els paquets que reexpedeix dins d’una sessió de Missatgeria P2P WebRTC segura.
ICE, STUN, TURN — Traversada NAT i resiliència
ICE (Interactive Connectivity Establishment</strong>) coordina el descobriment de camins de xarxa. STUN ajuda a determinar l’adreça pública d’un parell. TURN s’utilitza com a últim recurs quan no es pot establir cap camí directe. En conjunt, aquests components permeten establir comunicacions directes en aproximadament el 85 % de les configuracions de xarxa reals, fins i tot amb NAT a nivell d’operador o tallafocs estrictes.
DataChannel — Intercanvis sobirans fora de mitjans
El WebRTC DataChannel permet enviar text, dades binàries, fitxers i metadades directament d’un navegador a un altre. Funciona sobre SCTP encapsulat en DTLS, oferint alta fiabilitat i confidencialitat sobirana. Cap servidor d’aplicació de tercers té visibilitat sobre aquests fluxos de dades; com a màxim, un node de relé controlat per l’usuari reexpedeix xifratge opac, quelcom crucial per al compartiment segur de fitxers, el xat P2P segur i la col·laboració amb mínima exposició de metadades.
CryptPeer — Implementació sobirana del model P2P WebRTC
CryptPeer implementa el paradigma “direct-to-direct” de forma estricta. Cap contingut en clar
ni material criptogràfic s’emmagatzema mai en cap servidor; només certes dades tècniques xifrades de cap a cap poden existir de manera transitòria en un node de relé controlat per l’usuari. L’aplicació utilitza un servidor únicament per a la fase inicial de senyalització i, quan cal, un relé local autoallotjat per a la connectivitat; un cop establerta, la sessió WebRTC roman completament peer-to-peer i xifrada de cap a cap. Com que CryptPeer funciona íntegrament en un navegador estàndard, sense aplicació ni connector, aquest model sobirà és compatible amb estacions de treball bloquejades, terminals reforçats i entorns BYOD.
Aquest enfocament s’alinea plenament amb la doctrina Freemindtronic: la sobirania es demostra mitjançant el control local de la criptografia, del can
al i de l’exposició — un model de Missatgeria P2P WebRTC segura on els usuaris conserven la propietat dels seus secrets, del seu trànsit i de la seva superfície de comunicació.
Més enllà de les missatgeries segures clàssiques — HSM digital segmentat i claus per missatge
A diferència de les aplicacions de miss
atgeria xifrades de cap a cap tradicionals, que confien en el sistema operatiu del telèfon o del PC per protegir les claus, CryptPeer s’ancora en un HSM digital de claus segmentades. En la versió distribuïda per FullSecure, aquesta capa de seguretat sobirana s’implementa amb la tecnologia EviLink HSM PGP de Freemindtronic. Els secrets criptogràfics es gestionen, doncs, fora del sistema operatiu de l’endpoint, en una capa dedicada inspirada en els HSM, sota control de l’organització. Aquest disseny redueix de manera significativa l’impacte de compromisos de dispositius, anàlisi forense o explots a nivell de sistema operatiu.
Per a cada missatge intercanviat entre parells, CryptPeer deriva una clau efímera específica a partir d’aquest model de claus segmentades. Cada missatg
e queda compartimentat criptogràficament: comprometre’n un no dona accés a la resta, i eliminar un contacte pot desencadenar la destrucció local de les claus de resposta associades al costat de l’emissor. El resultat és un radi d’impacte molt fi, a nivell de missatge, que va molt més enllà dels dissenys clàssics de “una clau per conversa”.
Col·laboració segura 100 % navegador, sense instal·lació
<p>Aquest enfocament de “zero instal·lació al navegador” és crucial per a entorns bloquejats, terminals reforçats, màquines compartides i escenaris BYOD on desplegar clients nadius és impossible o indesitjable.
Malgrat aquest model purament basat en navegador, els usuaris es
beneficien d’un entorn complet de col·laboració sobirana: missatgeria de text xifrada de cap a cap, trucades d’àudio i vídeo, equips i grups centrats en la missió, i transferència de fitxers xifrats de gran volum. En màquines no fiables o compartides, els usuaris poden optar per conservar només còpies xifrades localment i desencriptar-les temporalment en un suport extern de confiança quan calgui. El servidor de relé, en qualsevol cas, només veu xifratge i mai no manipula contingut en clar.
Model d’identitat i compartimentació segons el “need-to-know”
</h4>
A diferència de les missatgeries basades en número de telèfon o correu electrònic, CryptPeer ancora la identitat en claus criptogràfiques, opcionalmen
t representades per avatars en lloc d’identificadors públics. L’adscripció al món real (servei, unitat, missió, organització) es gestiona a través de l’administració i de categories, en lloc de comptes d’usuari globals.
Cada nou contacte s’ha d’assignar a una o més categories, que defineixen la seva bombolla de contacte (unitat, servei, missió, soci, teatre, etc.). No existeix cap directori glob
al que exposi tota l’organització. Aquest model basat en categories imposa un perímetre molt estricte de “need-to-know” i limita els moviments laterals, el social engineering i les oportunitats d’espionatge intern.
Seguretat — DTLS, SRTP i el model de confiança local
La seguretat de les comunicacions WebRTC es basa en una composició metòdica de protocols dissenyats per establir una confiança local. El xifratge no és un afegit; és la columna vertebral mateixa de la capa de transport. Aquest enfocament estructural diferencia la Missatgeria P2P WebRTC segura de les plataformes de xat tradicionals, on el servei actua sovint com a intermediari criptogràfic, generant o emmagatzemant de vegades les claus. Aquí, les claus mai no surten dels parells.
Dels atacs “jackpot” al disseny amb impacte limitat
En la majoria de missatgeries centralitzades, anys d’històric, grafs socials i secrets xifrats conviuen en el mateix siló. Quan un implant té èxit, gaudeix d’un “efecte jackpot”: una sola compromissió pot buidar un enorme arxiu de converses. La doctrina de disseny de CryptPeer parteix de l’angle oposat: acceptar que l’implant pot existir, però reduir allò que obté quan triomfa. Claus segmentades gestionades fora del sistema operatiu, derivacions efímeres a la RAM, bombolles de comunicació compartimentades i la possibilitat de mantenir els missatges emmascarats per defecte limiten allò que un atacant pot veure a un perímetre estret, local i acotat en el temps. L’objectiu no és fer els atacs impossibles, sinó reduir-ne el valor operacional i destruir-ne l’escalabilitat pel disseny.
Key insights — La seguretat WebRTC es basa en tres mecanismes inseparables:
- DTLS: negociació local de claus directament entre parells;
- SRTP: xifratge a nivell d’aplicació dels fluxos d’àudio/vídeo;
- Identity Assertion: validació externa opcional per autenticar els parells.
Aquests tres mecanismes fan que la interceptació sigui tècnicament inútil, fins i tot a través d’un relé TURN.
</div>
HSM de claus segmentades i resiliència pre-quàntica
Més enllà de la seguretat de protocol, l’HSM digital de claus segmentades de CryptPeer imposa un model d’atac molt diferent del de les missatgeries segures clàssiques. Un adversari no pot simplement apuntar un (futur) ordinador quàntic a una clau d’encriptació es
tàtica: per definir tan sols un espai de cerca significatiu hauria primer de comprometre cada segment de clau, comprendre la lògica interna de derivació i capturar el moment precís en què la clau derivada existeix en memòria volàtil.En la pràctica, això significa que l’atacant ha d’aconseguir un compromís profund i multicapal de terminals i de l’HSM
abans que qualsevol esforç criptanalític a gran escala sigui rellevant. Només després de superar la gestió de claus segmentades, la governança local i la derivació efímera a la RAM, es trobaria davant de la robustesa intrínseca d’AES-256. CryptPeer desplaça, així, el problema de “trencar una clau de llarga durada en abstracte” a “controlar múltiples secrets compartimentats i un HSM sobirà en temps real” — un escenari molt més exigent per a qualsevol adversari, clàssic o quàntic.</p>
DTLS — Negociació criptogràfica sense tercer
WebRTC utilitza DTLS per negociar claus criptogràfiques directament entre parells. A
diferència dels protocols centralitzats, cap servidor participa en la negociació. DTLS estableix un canal segur a través de la xarxa, garantint que només els parells autenticats puguin derivar les claus SRTP necessàries per xifrar els fluxos.
SRTP — Xifratge a nivell d’aplicació dels fluxos multimèdia
Un cop les claus s’han inter
canviat via DTLS, WebRTC aplica SRTP per xifrar cada paquet d’àudio i vídeo. Aquesta protecció funciona independentment de la topologia de xarxa, garantint la confidencialitat fins i tot quan s’utilitza un servidor TURN com a relé. Les condicions de transport no degraden mai la seguretat del flux.
Prova local i comunicació sobirana
Com que cap servidor conserva les claus, la confidencialitat del flux dep
èn exclusivament de la capacitat dels parells per assegurar els seus entorns locals. Aquest model inverteix l’economia de confiança tradicional: la seguretat ja no descansa en una entitat central, sinó en una prova local i verificable.
Rendiment — Latència, optimització i estabilitat
El P2P WebRTC es caracteritza per una latència molt baixa, ja que cap plataforma de núvol de tercers relé els paquets i, en la majoria dels casos,
el trànsit circula directament entre parells. Aquesta optimització nativa és essencial per a videoconferències, streaming interactiu, compartició de pantalla i qualsevol escenari de comunicació en temps real sensible al jitter i al retard.
Key insights — El rendiment WebRTC es basa en:
- Control de congestió: algoritmes tipus GCC/TFRC que adapten dinàmicament el bitrate;
- Agilitat de còdecs: selecció automàtica entre VP8, VP9, H.264 segons capacitats;
- Transport adaptatiu: manteniment del flux fins i tot davant degradacions temporals.
Latència mínima i camí directe
Gràcies als seus mecanismes de transport directe, WebRTC elimina el processament al servidor i redueix la latència al mínim indispensable. Això permet trucades segures més naturals, fluides i fiables, fins i tot en condicions de xarxa heterogènies.
Resiliència a la pèrdua de paquets
WebRTC implementa mecanismes de correcció d’errors i retransmissió selectiva. El flux es manté coherent fins i tot en presència de pèrdues ocasionals de paquets — una característica crítica per a entorns inestables com les xarxes mòbils o el Wi-Fi congestionat.
<h3 id=”p2p-challenges-network-policies”>Reptes contemporanis — P2P vs polítiques de xarxaLa multiplicació de dispositius NAT, les restriccions dels operadors i les polítiques de seguretat corporatives redueixen la probabilitat d’establir connexions directes. Tot i que WebRTC està dissenyat per esquivar la majoria d’aquests obstacles, alguns entorns extremadament restrictius segueixen requerint relés TURN.
</p>
Sobirania tècnica en la Missatgeria P2P WebRTC segura — Prova local i no-retenció
La sobirania d’una comunicació en CryptPeer es recolza en dos princip
is verificables: la prova local i la no-conservació en clar al servidor. En la implementació de CryptPeer, un HSM digital de claus segmentades gestiona els secrets fora del sistema operatiu de l’endpoint, i cada missatge utilitza una clau efímera dedicada. Comprometre un dispositiu o un missatge no desbloqueja ni la resta de l’historial ni el directori de l’organització.
Pel que fa al transport, qualsevol node de relé opcional és autoallotjat i només veu xifratge. Pel que fa a l’emmagatzematge, els servidors mai no retenen contingut llegible, metadades o claus utilitzables. Els usuaris poden decidir, per fitxer i per terminal, si volen conservar només còpies xifrades localment o també una versió desencriptada temporal — una funció crítica en màquines compartides o no fiables. Qualsevol rastre residual resta xifrat i sota control de l’usuari o de l’organització.
En la pràctica, CryptPeer — distribuït per FullSecure i basat en la tecnologia EviLink HSM PGP</a> de Freemindtronic — empeny aquesta lògica encara més enllà. Els secrets es tracten fora del sistema operatiu del telèfon, les claus es deriven només a la RAM i es poden combinar amb modes de visualització emmascarada en què els missatges romanen xifrats per defecte i es desencripten sota demanda. Aquesta combinació redueix de manera dràstica la quantitat de material explotable disponible per a un implant en un moment donat.
Aquest enfocament és totalment coherent amb la doctrina Freemindtronic: una arquitectura sobirana es mesura per la seva capacitat d’operar sense perjudicar l’autonomia de l’usuari i sense delegar la governança criptogràfica — una veritable pila de Missatgeria P2P WebRTC segura que pot funcionar localment, fora de línia i íntegrament sota control nacional o organitzatiu.
Perspectives — Cap a un Internet descentralitzat
A mesura que les arquitectures de núvol continuen centralitzant serveis, el model P2P WebRTC restableix l’equilibri retornant el control del flux de comunicació als usuaris. Les tendències actuals — edge computing, sobirania digital, arquitectures Zero Trust i entorns contestats — convergeixen cap a aquest paradigma: la comunicació directa i xifrada de cap a cap com a norma, no com a excepció.
CryptPeer il·lustra aquesta transició de forma molt concreta. El mateix “stack” pot:
- funcionar sobre una Raspberry Pi 5 o micro-node per crear una bombolla de comunicació local i aïllada, sense targetes SIM ni Internet,
- escala fins a centres de dades ministerials o operadors d’infraestructures crítiques utilitzant el mateix model d’HSM de claus segmentades,
- servir múltiples bombolles — cèl·lules de crisi, teatres d’operacions, socis OIV — mitjançant un gestor multi-servidor integrat, sense barrejar directoris ni categories.
Mode regal i de bombolla tàctica — fora de les cadenes d’intercepció clàssiques
Fer funcionar CryptPeer en una bombolla tàctica Wi-Fi autosuficient
En “mode bombolla”, fas funcionar CryptPeer sobre un enllaç Wi-Fi privat amb els telèfons intel·ligents en mode avió, sense targetes SIM i sense cap adhesió 2G/3G/4G/5G ni sistemes de ràdio professionals com TETRA / PMR (~380–430 MHz) i determinades bandes LTE (per exemple LTE banda 20 a 800 MHz). La bombolla de comunicació roman físicament limitada a l’abast del senyal Wi-Fi i no toca mai les infraestructures mòbils públiques ni PMR.
Esquivar les cadenes clàssiques d’intercepció de telecomunicacions
En aquesta configuració, CryptPeer esquiva estructuralment moltes de les cadenes d’intercepció de telecomunicacions habituals — xarxes troncals d’operadors, interfícies d’intercepció legal, monitoratge LTE, captura TETRA / PMR i IMSI-catchers. L’adversari s’ha d’apropar físicament, equipar-se per olorar les bandes Wi-Fi (2,4 / 5 / 6 GHz) i, fins i tot així, només veu xifratge de cap a cap.
Acceptar que la detecció RF continua sent possible, però sense metadades
És clar que una unitat de guerra electrònica a nivell d’Estat que s’acosti deliberadament a la zona pot detectar activitat RF a les bandes Wi-Fi i localitzar aproximadament la zona d’emissió mitjançant tècniques estàndard de radiolocalització. Tanmateix, no obté accés a metadades de la xarxa mòbil ni a contingut en clar, perquè cap operador de telecomunicacions participa en el bucle de comunicació i CryptPeer manté tot el trànsit xifrat peer-to-peer de punta a punta.
Reduir la superfície d’atac local amb un HSM digital de claus segmentades
A més, la criptografia de CryptPeer s’executa a nivell de terminal, en memòria volàtil (RAM), sense clar en el costat servidor i sense emmagatzematge local obligatori en clar al dispositiu. Fins i tot en un telèfon intel·ligent limitat a la xarxa Wi-Fi local i completament fora de línia, aquesta arquitectura redueix dràsticament la superfície d’atac: no hi ha infraestructura de telecomunicacions a comprometre, ni clar persistent a recuperar, i només material criptogràfic transitori governat pel model d’HSM de claus segmentades.
Lectures complementàries — intercepció a les xarxes públiques
A tall de referència — exemples d’intercepció i cadenes d’intercepció legal a les xarxes públiques:
- ETSI – Estàndards d’intercepció legal per a xarxes de telecomunicacions
- Bundesnetzagentur – Guia tècnica sobre intercepció legal (TR TKÜV)
- ENISA – Seguretat 5G i equilibri entre intercepció legal i confidencialitat d’extrem a extrem
- CableLabs – Entendre els IMSI-catchers i la intercepció en xarxes mòbils
- Recerca pública sobre vulnerabilitats TETRA / PMR i riscos d’intercepció
Al mateix temps, la convergència actual entre operacions estatals i spyware comercial — des d’explots 0-click sobre imatge i àudio en missatgeries de gran consum fins a kits de vigilància de “segment mitjà” — reforça aquest escoll arquitectònic. La pregunta ja no és només “puc aturar l’implant?”, sinó “quant pot arribar a robar si té èxit?”. Mentre anys d’historial, grafs socials i claus visquin en un sol siló, la compromissió seguirà sent un jackpot.
Per això, la Missatgeria P2P WebRTC segura és molt més que una tria de protocol; defineix un model de governança. En lloc de confiar en plataformes de núvol públiques i directoris globals, les organitzacions opten per explotar bombolles sobiranes autosuficients, on controlen identitats, claus, fluxos i exposició localment. D’aquesta manera, obren el camí a futurs sistemes de comunicació “trust-by-design” que continuen sent portàtils, compartimentats i resilients, fins i tot quan la infraestructura i els terminals deixen d’oferir plena confiança.
FAQ tècnica — Missatgeria P2P WebRTC segura, P2P, WebRTC i CryptPeer
Punt clau — WebRTC xifra sempre el trànsit P2P pel disseny
Sí, les implementacions modernes de WebRTC xifren el trànsit per defecte. En tots els navegadors actuals, WebRTC protegeix els fluxos d’àudio i vídeo amb SRTP. A més, protegeix els canals de dades amb DTLS/SCTP. En conseqüència, cap paquet WebRTC viatja en clar per la xarxa. Ni tan sols en videotrucades bàsiques o en transferències senzilles de dades.
Gràcies a això, la Missatgeria P2P WebRTC segura parteix ja d’una capa de transport xifrada. CryptPeer va més enllà: afegeix un HSM digital de claus segmentades i claus efímeres per missatge damunt de WebRTC. En la pràctica, WebRTC proporciona el túnel segur. Al seu torn, CryptPeer construeix una capa de missatgeria sobirana, xifrada de cap a cap, dins d’aquest túnel. Aquesta combinació permet aprofitar ambdues coses: xifratge estàndard i àmpliament auditat a nivell de transport. A més, aporta un model E2EE de confiança elevada governat per HSM per a la confidencialitat a llarg termini.
Pregunta d’intercepció — Què veu realment un relé al cable?
No. Un relé TURN no veu mai el contingut llegible d’un flux de Missatgeria P2P WebRTC segura. En lloc d’això, simplement reexpedeix paquets xifrats sense tenir accés a les claus que els protegeixen. Fins i tot en sessions de llarga durada, el relé només manipula xifratge. Per tant, mai no rep prou informació per desxifrar mitjans o missatges.
CryptPeer explota aquesta propietat de manera sobirana. Quan cal un relé, s’executa com un node opcional autoallotjat sota control de l’organització. Normalment s’insereix dins d’una infraestructura local o nacional. En conseqüència, operadors de telecomunicacions, proveïdors de núvol i atacants externs no obtenen un nou punt de vantage sobre els fluxos. Només veuen trànsit xifrat de cap a cap, i el relé es limita a actuar com un component de pas neutral. A més, no disposa de poder de desxifratge ni de retenció de metadades explotables.
Pregunta de sobirania — Qui controla realment el canal i les claus?
CryptPeer ofereix comunicació sobirana perquè permet a l’organització controlar plenament infraestructures, claus i exposició. Ets tu qui opera els servidors — des d’un micro-node Raspberry Pi 5 fins a un centre de dades ministerial. Per tant, mai no cedeixes el poder criptogràfic a un proveïdor de núvol. Els servidors només gestionen la senyalització i, si cal, un relé autoallotjat. En cap cas veuen contingut en clar ni claus mestres.
Al mateix temps, CryptPeer es basa en un HSM digital de claus segmentades i claus efímeres per missatge. Així implementa un xifratge de cap a cap que no depèn del sistema operatiu del telèfon o del PC. Combinat amb la Missatgeria P2P WebRTC segura i la capacitat d’operar en mode “bombolla” completament local, aquest model resulta especialment coherent. En conseqüència, permet als serveis regals i als operadors d’infraestructures crítiques conservar íntegrament la governança criptogràfica, el trànsit i el perímetre d’identitat.
Escenari tàctic — Bombolles P2P sense cap columna vertebral d’Internet
Sí, el P2P WebRTC funciona molt bé en una xarxa local sense cap connexió a Internet. WebRTC pot recolzar-se en ICE i mDNS per descobrir parells exclusivament dins d’un Wi-Fi privat o d’una LAN cablejada. En aquest cas, tot el flux de Missatgeria P2P WebRTC segura roman dins del perímetre de la xarxa local. Per tant, no toca mai Internet pública.
CryptPeer utilitza aquesta capacitat per crear bombolles de comunicació tàctiques. Telèfons intel·ligents i portàtils poden romandre en mode avió, sense targetes SIM i sense adherència 2G/3G/4G/5G. Tot i així, segueixen intercanviant missatges i fent trucades en temps real a través d’un micro-node local. Per exemple, poden utilitzar una Raspberry Pi 5 en mode punt d’accés Wi-Fi. Aquest enfocament és especialment útil a teatres d’operacions sensibles, sales de crisi o entorns aïllats. En aquests contextos, es vol eliminar deliberadament qualsevol dependència de núvols públics i operadors de telecomunicacions.
Resposta a incidents — Limitar el radi d’impacte d’una compromissió
Si un atacant compromet un terminal o un compte d’usuari, el disseny de CryptPeer limita activament els danys. En primer lloc, l’HSM digital de claus segmentades i les claus efímeres per missatge creen compartiments forts. Gràcies a això, una sola compromissió no pot desbloquejar tot un arxiu de converses. Cada missatge té la seva clau derivada pròpia. Això fa que l’atacant no obtingui automàticament accés a tot l’historial.
En segon lloc, CryptPeer organitza els usuaris en categories i bombolles que segueixen estrictament els principis de “need-to-know”. Una identitat compromesa mai no veu tota l’organització. Només pot accedir al seu perímetre assignat: unitats, missions, serveis o teatres concrets. El radi d’impacte es manté, doncs, limitat tant criptogràficament com organitzativament. Aquest model encaixa amb els escenaris d’amenaça de defensa, d’intel·ligència i d’operadors d’infraestructures crítiques. En aquests entorns, s’assumeix que hi haurà incidents i es dissenya el sistema per contenir-los per defecte.
Precisió — Un transport segur per si sol no garanteix un E2EE real
No, WebRTC no equival a xifratge complet de cap a cap. WebRTC assegura el transport: xifra els fluxos multimèdia i de dades “al cable” mitjançant DTLS, SRTP i SCTP. Aquest disseny protegeix contra molts atacs de nivell xarxa, com l’escolta passiva. A més, dificulta intents senzills d’man-in-the-middle sobre routers intermedis.
Tanmateix, el veritable xifratge d’extrem a extrem depèn de com l’aplicació genera, emmagatzema i intercanvia les claus criptogràfiques. Si un servidor crea o conserva les claus, el sistema no ofereix un E2EE genuí, encara que utilitzi WebRTC. Per això CryptPeer fa servir WebRTC com a base de transport segura. Sobre aquesta base, hi afegeix un HSM digital de claus segmentades amb claus efímeres per missatge. Els servidors mai no reben claus mestres en clar ni les poden reconstruir. D’aquesta manera, CryptPeer converteix un transport WebRTC segur en una capa de missatgeria i col·laboració completament sobirana. Alhora, manté el xifratge de cap a cap en tot moment.
Preocupació de privacitat — Entendre què pot veure realment l’altra banda
En una sessió P2P WebRTC directa, cada parell sol veure les adreces de xarxa que fa servir la connexió. Aquestes adreces poden incloure IP públiques o privades segons la topologia. Aquest comportament és normal en qualsevol comunicació IP en temps real. En efecte, els dos extrems han de saber com arribar l’un a l’altre a nivell de xarxa.
CryptPeer mitiga això de diverses maneres pràctiques. En primer lloc, pots fer funcionar CryptPeer íntegrament dins d’una bombolla Wi-Fi local aïllada. En aquest escenari, els parells només veuen adreces IP locals que no tenen cap significat a Internet pública. En segon lloc, tots els missatges i trucades utilitzen Missatgeria P2P WebRTC segura amb xifratge fort de cap a cap. A més, no hi ha retenció de metadades en clar al servidor. En conseqüència, fins i tot quan els parells veuen informació IP, mai no obtenen accés a contingut llegible ni a claus criptogràfiques. Tampoc poden consultar directoris organitzatius complets. Per a molts escenaris institucionals, aquest equilibri ofereix alhora eficiència operacional i privacitat robusta.
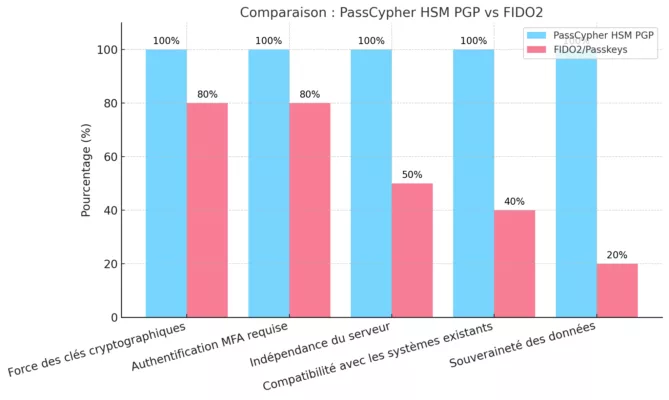
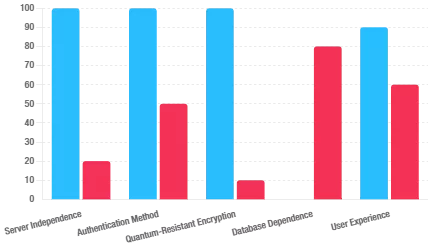
Comparació — Més enllà de les missatgeries xifrades de consum massiu
CryptPeer es diferencia de les aplicacions de missatgeria segura clàssiques en diversos punts estratègics. Primer, funciona al 100 % al navegador i sense instal·lació. Això permet utilitzar-la en estacions de treball bloquejades, terminals compartits i sales de crisi on les aplicacions natives estan prohibides. Només cal obrir un navegador i unir-se a la bombolla de Missatgeria P2P WebRTC segura.
En segon lloc, CryptPeer ancora la seguretat en un HSM digital de claus segmentades i claus efímeres per missatge. Així evita confiar en el sistema operatiu del telèfon o del PC per protegir els secrets. En tercer lloc, funciona com una bombolla de comunicació sobirana i autosuficient, sense Internet ni núvol públic. Per això utilitza únicament infraestructura local o nacional sota control organitzatiu. Finalment, estructura les identitats mitjançant categories i bombolles alineades amb doctrines de “need-to-know”, no pas directoris globals d’usuaris. En resum, CryptPeer s’adreça a serveis regals, ecosistemes de defensa i operadors d’infraestructures crítiques més que no pas al xat de gran consum.
Governança vs vigilància — Els admins gestionen el sistema, no el contingut
No. Els administradors de CryptPeer no llegeixen ni desxifren les converses dels usuaris. Gestionen la infraestructura, les categories, les bombolles, les actualitzacions de servidor i la monitorització de recursos. Tot i això, mai no reben claus de xifratge de cap a cap. El servidor de relé només reexpedeix xifratge i no emmagatzema missatges en clar ni secrets utilitzables.
Paral·lelament, la governança continua sent robusta. Els administradors poden aplicar polítiques d’accés, configurar bombolles per a missions o teatres diferents i definir regles de retenció per a dades tècniques. Tanmateix, tot això es fa sense convertir CryptPeer en una eina de vigilància massiva. Aquesta separació entre poder administratiu i capacitat de desxifratge s’alinea amb les doctrines de “need-to-know” i amb les expectatives de defensa, intel·ligència i infraestructures crítiques. En conseqüència, es garanteix una governança forta sense comprometre la confidencialitat.
Angle jurídic — Compliment sense introduir portes del darrere al xifratge
CryptPeer aborda l’accés legal i les constriccions regulatòries mitjançant arquitectura i governança. En cap cas recorre a portes del darrere criptogràfiques. La plataforma no emmagatzema missatges en clar ni claus mestres al costat servidor. Per tant, no pot desxifrar retroactivament tot l’historial de comunicacions sota demanda. Cada organització continua sent responsable dels seus propis processos legals a nivell d’endpoint i de la manera com gestiona dispositius i identitats.
A nivell d’infraestructura, CryptPeer pot seguir proporcionant informació d’auditoria sobre recursos, disponibilitat, esdeveniments de connexió i estat de salut dels servidors. Tot això es manté sempre sota control de l’organització. Aquest enfocament permet complir polítiques internes i regulacions sectorials. Al mateix temps, preserva la integritat de la Missatgeria P2P WebRTC segura i del xifratge de cap a cap. En altres paraules, CryptPeer separa la governança legal de l’afebliment criptogràfic. Aquesta separació és essencial per a casos d’ús d’alta garantia i regals.
Angle quàntic — Com la Missatgeria P2P WebRTC segura es prepara per a les amenaces post-quàntiques
CryptPeer té en compte les amenaces quàntiques a nivell arquitectònic. Avui es basa en criptografia simètrica consolidada com AES-256-GCM. Aquest esquema es considera robust fins i tot en un context post-quàntic quan s’utilitza amb claus de 256 bits. Un ordinador quàntic a gran escala podria accelerar atacs de brute-force mitjançant l’algoritme de Grover. Tot i així, AES-256 continua oferint un marge de seguretat enorme per a comunicacions xifrades de cap a cap a llarg termini.
A més, CryptPeer no es limita a una única clau de 256 bits. La plataforma utilitza un HSM digital de claus segmentades. Genera diversos segments independents de 256 bits i deriva una clau mestra només en memòria volàtil (RAM). A partir d’aquesta clau mestra, CryptPeer deriva després claus efímeres per missatge per a la Missatgeria P2P WebRTC segura. Un atacant hauria, doncs, de recuperar tots els segments i reconstruir el mètode de concatenació. Després encara hauria d’afrontar un espai de claus enorme, un escenari que va molt més enllà dels models d’atac clàssics.
Al mateix temps, CryptPeer utilitza deliberadament algoritmes estàndard i públicament revisats, en lloc de xifrats propietaris. Aquesta elecció facilita les futures transicions cap a esquemes de clau pública post-quàntics, per exemple per a intercanvi de claus o signatures. Això serà especialment útil quan WebRTC i DTLS evolucionin. En la pràctica, la combinació d’AES-256-GCM, HSM de claus segmentades i claus efímeres per missatge ja ofereix avui un nivell de resiliència molt elevat. Al mateix temps, manté un camí clar de migració cap als estàndards post-quàntics emergents.
Què no hem tractat
- Arquitectures distribuïdes híbrides — com conviuen amb WebRTC en sistemes mixtos (edge computing, xarxes mesh).
- Models avançats de detecció de compromís local — essencials per reforçar la sobirania operacional del costat usuari.
- Estratègies de mitigació de latència en entorns extrems — en particular en xarxes mòbils asimètriques o inestables.
- Impactes geopolítics de les comunicacions descentralitzades — especialment en relació amb regulacions extraterritorials.
- Mecanismes de pseudonimització dinàmica — útils per desacoblar identitat i canal en la comunicació directa.
Aquests temes es basen en els fonaments establerts aquí. Aporten llum sobre dimensions que influeixen directament en la resiliència, la confidencialitat i la portabilitat de les arquitectures sobiranes de Missatgeria P2P WebRTC segura. Es tractaran en altres cròniques tècniques de la sèrie Freemindtronic Cyberculture.
Casos d’ús sobirans — ecosistema de Missatgeria P2P WebRTC segura de Freemindtronic
El model P2P WebRTC desplegat per CryptPeer forma part d’un ecosistema més ampli de dispositius sobirans dissenyats per Freemindtronic. Cada tecnologia segueix un principi comú: la prova local de confiança.
Focus regal i infraestructures crítiques — Més enllà de les missatgeries segures clàssiques
- Zero instal·lació, 100 % navegador: compatible amb estacions de treball bloquejades, terminals reforçats i centres de crisi on desplegar aplicacions no és acceptable.
- Bombolles locals autosuficients: funcionament sobre xarxes Wi-Fi privades o xarxes cablejades sense targetes SIM ni accés a Internet, des d’un micro-node Raspberry Pi 5 fins a centres de dades ministerials.
- HSM digital de claus segmentades</strong>: claus efímeres per missatge i gestió de claus inspirada en maquinari, dissenyada per a models d’amenaça d’alta garantia i nivell defensa.
- Identitat sense número de telèfon ni correu: identitats criptogràfiques, categories i bombolles alineades amb doctrines de “need-to-know” en lloc de directoris globals.
- Sense portes del darrere ni dades explotables al servidor: els servidors mai no conserven contingut en clar ni claus utilitzables, i els nodes de relé opcionals només reexpedeixen xifratge sota control organitzatiu.
Aquest principi garanteix que l’usuari continuï sent l’únic titular de les seves claus, els seus secrets i la seva superfície d’exposició.
DataShielder HSM PGP — Protecció local i xifratge de maquinari
- Emmagatzematge de claus fora de línia, inaccessible per a servidors remots.
- Xifratge PGP realitzat íntegrament dins de l’HSM físic.
- Cap empremta digital fora del perímetre de l’usuari.
PassCypher NFC HSM — Identitats i secrets sobirans
- Gestió local d’identitats, claus, secrets i OTP.
- Derivació criptogràfica sense núvol i sense infraestructura de tercers.
- Autonomia operacional completa, fins i tot fora de línia.
CryptPeer — Comunicació directa P2P WebRTC
- Fluxos d’àudio/vídeo directes entre parells, sense relé de tercers; només un relé local autoallotjat quan els camins directes són impossibles.
- Xifratge DTLS–SRTP negociat localment.
- DataChannel WebRTC sobirà per a missatges i transferència de fitxers.
- En la versió distribuïda per FullSecure, CryptPeer es basa en la tecnologia EviLink HSM PGP de Freemindtronic. D’aquesta manera, proporciona una capa d’HSM digital de claus segmentades que governa claus i secrets.
- Cap metadada llegible conservada després de finalitzar la sessió; qualsevol traça tècnica resta xifrada i sota control de l’usuari.
En combinar aquests dispositius, Freemindtronic construeix una doctrina que unifica sobirania criptogràfica, d’identitat i de comunicació. Així, la promesa és clara: posseir claus, dades i canal en un ecosistema de Missatgeria P2P WebRTC segura.