2025, Digital Security
eSIM Sovereignty Failure: Certified Mobile Identity at Risk
eSIM Sovereignty Failure: Strategic Breach of Certified Mobile Identity
This Chronicle investigates the first public compromise of a GSMA-certified eSIM platform. The Kigen eUICC exploit reveals a systemic failure in runtime security, certification integrity, and sovereign oversight. This case exemplifies a broader eSIM sovereignty failure that reveals strategic gaps in certified mobile identity governance. While the technical flaw traces back to a Java Card vulnerability known since 2019, the real breach lies in the blind trust placed in certification layers without independent verification or revocation protocols. The implications reach beyond telecom security — directly into the sovereignty of digital identities.
In Digital Security ↑ Correlate this Chronicle with other sovereign threat analyses in the same editorial rubric.
Strategic Navigation Index
- Executive Summary / TL;DR
- Genesis of the Exploit: Java Card, GSMA, and Forgotten Warnings
- Technical Breakdown — Sovereign Readout of the Runtime Breach
- Geostrategic Exposure Mapping — eSIMs Across Sectors & Infrastructures
- Accountability Matrix: Researchers, Vendors, Certifiers, Regulators
- Strategic Fallout: Trust Collapse and Sovereignty at Risk
- Simjacker Revisited: Lessons from 2019 and the Road to eUICC Compromise
- Regulatory Landscape: Where NIS2, CRA and GSMA TS.48 Collide
- Industry Blind Spots: Strategic Failures to Anticipate Side-Channel Exploits
- Threat Intelligence Perspective: APT Groups & Espionage Tradecraft with eSIMs
- Runtime Threats in Certified eSIMs: Four Strategic Blind Spots
- Cryptographic Fragility in eSIM Implementations
- Sovereignty Scorecard: Evaluation Framework for National eSIM Policy
- Zero Trust eSIM: Blueprint for Post-Certification Architectures
- Weak Signals Identified
- eSIM on External Storage?
- Misconceptions & Design Constraints
- Countermeasures Against Certified eSIM Sovereignty Threats
- Rethinking eSIM Governance with Sovereign NFC HSM
- Use Case: From EviCall to EviSIM – Resilience via DataShielder NFC HSM Defense
- Infographic: Anatomy of SM-DP+/SM-DS Flow and Attack Vectors
- What We Didn’t Cover
- Certification alone cannot ensure runtime integrity — post-certification attacks exploit logic and memory states invisible to audits.
- Java Card runtime remains unaudited post-deployment — making every certified eSIM a potential time-bomb under stress or glitching conditions.
- Sovereign HSMs externalize trust and isolate secrets — offering a runtime enclave immune to provisioning tampering and OTA subversion.
- Mobile identity governance must embrace revocability and field attestation — static certification chains are insufficient to counter dynamic threat models.
- SM-DP+ infrastructures are inherently opaque — attackers can exploit provisioning without triggering compliance violations.
- Runtime verification is the new perimeter — only sovereign architectures with live integrity checks can enforce trust beyond installation time.
- DataShielder NFC HSM Defense exemplifies this shift — enabling secure messaging (SMS, MMS, RCS) through EviCall, with runtime asymmetric encryption enforced outside the eSIM trust perimeter.
About the Author – Jacques Gascuel, inventor of internationally patented encryption technologies and founder of Freemindtronic Andorra, is a pioneer in sovereign cybersecurity. In this Digital Security Chronicle, he deciphers the strategic breach in certified eSIMs and outlines a sovereign resilience framework based on NFC HSMs and off-host credential governance.
Genesis of the Exploit: Java Card, GSMA, and Forgotten Warnings
The breach of the Kigen eSIM platform did not occur in a vacuum. It stems from a critical vulnerability in Java Card technology—an issue first flagged by independent researchers as early as 2019. The flaw, related to runtime memory leaks and side-channel leakage vectors, remained dormant in certified environments due to insufficient post-certification scrutiny. Despite multiple advisories, the lack of a mandatory patching protocol or revocation mechanism allowed this vulnerability to persist across millions of devices.
Moreover, the GSMA certification process—intended as a guarantee of cryptographic integrity—failed to account for the nuanced runtime behavior of Java Card applets. The systemic gap lay in the absence of a sovereign certification follow-up system, especially after the issuance of eUICC certificates. This blind spot rendered the entire certification stack vulnerable to exploitation once attackers identified how to manipulate instruction flow during remote profile installation. This oversight directly contributed to a certified eSIM sovereignty failure, where legacy vulnerabilities persisted unchecked within supposedly trusted systems.
Far from being a one-off incident, this exploit exemplifies a broader systemic weakness: reliance on opaque certification pipelines without dynamic runtime assurance. Sovereign cybersecurity demands continuous attestation and verifiability—not static compliance artifacts.
Technical Breakdown — Sovereign Readout of the Runtime Breach
The attack against Kigen’s certified eUICC exploited a well-documented weakness in the Java Card runtime — specifically, the handling of memory and instruction flow during the loading of remote applets. By leveraging a side-channel attack chain, the adversary extracted sensitive keys and operational data without triggering standard telemetry or fault logs.
The exploit unfolded in three phases: reconnaissance, fault injection, and controlled memory leakage. During the reconnaissance phase, the attacker mapped the card’s internal logic by issuing benign APDU commands and analyzing response times. In the second phase, glitching techniques—specifically voltage and clock manipulation—were used to bypass secure channel initialization, exploiting fault conditions to manipulate control flow. Finally, the attacker used crafted APDUs with offset variations to read residual data from the heap, effectively exfiltrating cryptographic material and provisioning metadata.
Notably, this breach occurred without violating the certified applet interface, highlighting that even formally verified interfaces are insufficient if the runtime layer remains exposed. Furthermore, the absence of post-deployment attestation mechanisms meant that the rogue behavior remained invisible to MNOs and SM-DP+/SM-DS operators. This scenario encapsulates a textbook case of eSIM sovereignty failure rooted in runtime opacity and post-certification blindness.
Independent formal verification efforts — notably using the 5GReasoner framework — have exposed critical vulnerabilities in the M2M Remote SIM Provisioning (RSP) protocol. These include race conditions, identity binding flaws, and session takeover possibilities within GSMA-compliant SM-DP+/SM-DS architectures. These weaknesses, documented since 2020, remain unaddressed in current certification enforcement, further confirming the runtime sovereignty failure at the core of eUICC design.

This runtime breach demonstrates how a certified, production-grade eSIM platform can be reduced to an opaque black box — exploitable at the lowest level unless sovereignty-driven safeguards like hardware-isolated HSMs and field attestation protocols are enforced.
Geostrategic Exposure Mapping — eSIMs Across Sectors & Infrastructures
The eSIM ecosystem is deeply embedded in global supply chains, spanning sectors from critical infrastructure and defense to consumer electronics. The vulnerability exploited in the Kigen platform potentially affects any system that relies on remote provisioning and over-the-air profile updates. This includes government-issued IDs, mobile banking tokens, connected vehicles, and secure IoT modules.
Regions with centralized eID frameworks—such as the EU’s eIDAS or India’s Aadhaar-linked telecom systems—face compounded risks. Once a certified eSIM stack is compromised, attackers can clone, redirect, or exfiltrate digital identities at scale. In NATO and Five Eyes countries, the concern escalates as eSIM modules are increasingly integrated into secure communications for field units, diplomatic missions, and critical infrastructure.
What emerges is a geostrategic mosaic of exposure, where technical supply chains intersect with geopolitical fault lines. Sovereign actors must now assume that hostile powers could exploit trusted certification systems to stage covert identity subversion or persistent access operations.
eSIMs are no longer neutral components — they represent a geostrategic vector of exposure, linking runtime compromise to sovereign identity manipulation across sectors and jurisdictions.
Accountability Matrix in the Certified eSIM Compromise
The Kigen eSIM compromise is emblematic of a wider eSIM sovereignty failure, where no actor assumes full responsibility for runtime trust. While independent researchers were first to identify the Java Card side-channel risk, their findings remained largely unheeded by certification bodies and runtime vendors. The vulnerability was flagged, published, but never operationally integrated into GSMA risk models.
Vendors such as Java Card implementers and eUICC manufacturers bear the technical burden, yet they operate within a certification-driven market that disincentivizes structural transparency. Once certified, platforms are considered immutable and secure—despite lacking mechanisms for sovereign runtime inspection or patch propagation.
Certification authorities like GSMA and EMVCo facilitated compliance at the interface level but failed to mandate continuous runtime monitoring or exploit simulation testing post-certification. National regulators, for their part, lacked either the mandate or the visibility to detect deviations from expected behavior within certified stacks.
This fragmented landscape enables plausible deniability and responsibility deferral—a dangerous precedent in sovereign digital infrastructure.
A sovereign accountability matrix demands unified oversight from research disclosure to runtime attestation—bridging the gap between technical detection, certification governance, and regulatory enforcement.
Strategic Fallout of the eSIM Sovereignty Failure
The breach of a certified eUICC signals not merely a technical failure but a collapse of the trust architecture that underpins sovereign digital identity. In delegating assurance to private certification consortia without enforceable runtime verifiability, states have inadvertently created blind zones in their own critical infrastructure.
Sovereignty risk arises when the integrity of mobile credentials—used in eID, eHealth, fintech, and defense—is no longer auditable nor revokeable in real time. The absence of field attestation protocols and HSM-enforced compartmentalization means that cloned or tampered identities can propagate undetected within systems presumed secure.
For nations operating under NIS2 or with national cryptographic governance frameworks, the Kigen incident necessitates a strategic re-evaluation: Are certification schemes serving national interests, or introducing dependencies on opaque, offshore processes? The breach demonstrates that eSIMs, while micro-scale in hardware, represent macro-scale vectors for influence, surveillance, and destabilization.
⮞ Summary
Sovereignty in the digital era hinges on runtime verifiability and trusted compartmentalization—qualities absent from current eSIM governance models relying solely on certification status.
Regulatory Landscape: Where NIS2, CRA and GSMA TS.48 Collide
The breach of Kigen’s certified eSIM platform exposes a legal grey zone where sovereignty, industry self-regulation, and supranational cybersecurity policies intersect — and often diverge. At the heart of the conflict lies GSMA TS.48, the industry-led eUICC certification standard, which lacks post-certification enforcement, runtime telemetry mandates, or revocation procedures for compromised components.
In contrast, the European Union’s NIS2 Directive and the Cyber Resilience Act (CRA) introduce legal obligations for continuous risk management, vulnerability disclosure, and secure-by-design principles. These frameworks implicitly contradict the current GSMA model by requiring runtime assurance and traceability across critical infrastructures and ICT supply chains. NIS2 classifies telecom as a key sector, requiring incident notification and risk mitigation, yet most MNOs remain blind to eSIM runtime behavior due to opaque OEM integrations.
Moreover, the CRA will enforce mandatory vulnerability management at the firmware and software levels — which includes eSIM middleware and applets. This raises the question: can GSMA continue to certify eUICC stacks under TS.48 without runtime transparency, in jurisdictions bound by NIS2 and CRA?
The disconnect becomes critical when state actors deploy certified eSIMs in sensitive roles — such as in border security, defense-grade communication, or government-issued mobile ID tokens. Sovereign nations adopting EU regulations must reconcile the legal obligations of NIS2/CRA with their technical reliance on private certification frameworks from entities like the GSMA — a non-state body.
For full reference:
– [NIS2 Directive overview – europa.eu](https://digital-strategy.ec.europa.eu/en/policies/nis2-directive)
– [Cyber Resilience Act proposal – europa.eu](https://digital-strategy.ec.europa.eu/en/library/cyber-resilience-act)
⮞ Summary
Sovereign cybersecurity is now a regulatory imperative. The disconnect between GSMA TS.48 certification and the mandatory compliance regimes under NIS2 and CRA exposes states to unmanaged legal and operational risks.
Industry Blind Spots: Strategic Failures to Anticipate Side-Channel Exploits
This strategic neglect forms a recurring pattern of eSIM sovereignty failure, where runtime threats are underestimated across certified ecosystems.
The Kigen eSIM breach illustrates a critical blind spot in the mobile security industry: the persistent underestimation of physical-layer and side-channel threats in certified environments. While certification schemes such as GSMA’s TS.48 emphasize interface compliance and cryptographic validation, they omit runtime behavioral assurance, particularly under fault or stress conditions — the exact domain exploited in the attack.
Despite the public disclosure of Java Card side-channel vulnerabilities by researchers since 2017 — including multiple presentations at events like CHES, Black Hat, and the TCG’s cybersecurity forums — the mobile industry maintained an implicit assumption that certified eUICCs were impervious to practical exploitation. This assumption neglected adversary models capable of leveraging voltage glitching, electromagnetic fault injection (EMFI), or response time correlation — all proven viable in prior smartcard-class attacks. Such assumptions are emblematic of a systemic eSIM sovereignty failure — not merely of vendors, but of governance models.
Furthermore, vendors often treat Secure Element and Trusted Execution Environment vulnerabilities as theoretical or “out-of-scope” for telecom threat modeling, assuming the remote nature of provisioning offers sufficient insulation. This assumption collapses in scenarios involving pre-deployment tampering, rogue MNOs, or insider threats in SM-DP+/SM-DS infrastructure.
The most alarming aspect lies in the lack of mandatory runtime telemetry and attestation mechanisms. Even after a successful breach, neither MNOs nor regulators can independently detect anomalies in eSIM behavior unless external post-mortem forensics are conducted — often too late.
Strategic negligence toward known side-channel vectors within the eSIM certification ecosystem leaves billions of devices exposed to sovereign-grade adversaries. Runtime threats are no longer theoretical — they are operational realities requiring structural reform.
Threat Intelligence Perspective: APT Groups & Espionage Tradecraft with eSIMs
The eSIM runtime compromise represents a significant shift in the threat landscape observed by national cyber agencies and private threat intelligence units. Advanced Persistent Threat (APT) groups, particularly those linked to state-sponsored cyber espionage, have long sought covert vectors for persistent access and identity subversion. The Kigen breach effectively introduces a new toolset into their arsenal: certified cryptographic devices that can be remotely manipulated without detection.
Historically, APT campaigns targeting telecom infrastructures — such as APT10’s exploitation of managed service providers or APT41’s targeting of mobile operators — prioritized control of metadata and SMS interception. With eSIM runtime attacks, the target expands to full identity extraction and cloning at the cryptographic layer. This enables operations such as device impersonation, interception of secure apps (banking, authentication), and insertion of backdoored profiles via compromised SM-DP+ servers.
Indicators of compromise remain elusive, as current telecom threat monitoring systems do not inspect profile integrity post-installation. Moreover, the GSMA Security Accreditation Scheme (SAS) for SM-DP+/SM-DS actors does not mandate field-level telemetry capable of detecting side-channel-derived manipulations.
Official source reference: [https://www.enisa.europa.eu/topics/csirt-cert-services/national-csirt-network](https://www.enisa.europa.eu/topics/csirt-cert-services/national-csirt-network)
As geopolitical tensions rise, threat actors with intelligence mandates are increasingly incentivized to exploit such blind spots — not merely for data theft, but for strategic impersonation and operational misdirection. eSIMs thus shift from neutral identity containers to offensive espionage tools — a hallmark of systemic eSIM sovereignty failure exploited by nation-state actors.
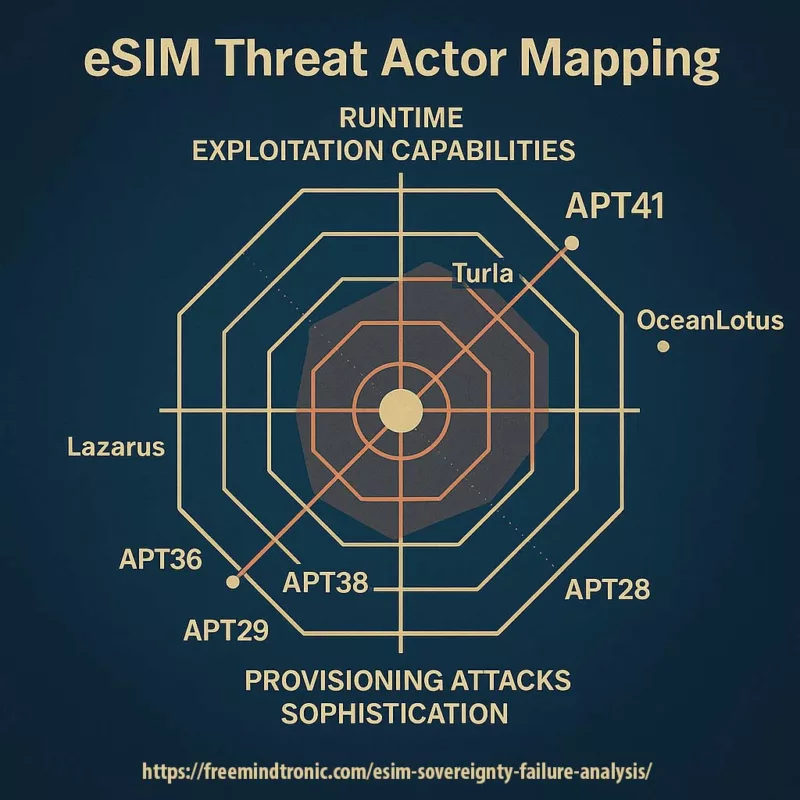
APT Groups Actively Targeting eSIM Runtime and Provisioning Flows
This table summarizes state-linked threat actors whose past campaigns show both interest and capability to exploit mobile identity infrastructure, particularly through eSIM runtime and SM-DP+ provisioning chains.
| APT Group | Origin | Known Targets | eSIM Relevance |
|---|---|---|---|
| APT10 (Stone Panda) | China | MSPs, telecom, cloud | Management infra compromise ideal for SM-DP+ |
| APT41 (Double Dragon) | China | Telecom, IoT, eSIM | Hybrid espionage/cybercrime — runtime abuse observed |
| APT29 (Cozy Bear) | Russia | Govs, think tanks | Stealth ops, focus on digital ID compromise |
| APT28 (Fancy Bear) | Russia | Defense, NATO, Europe | Critical infrastructure targeting, eSIM plausible vector |
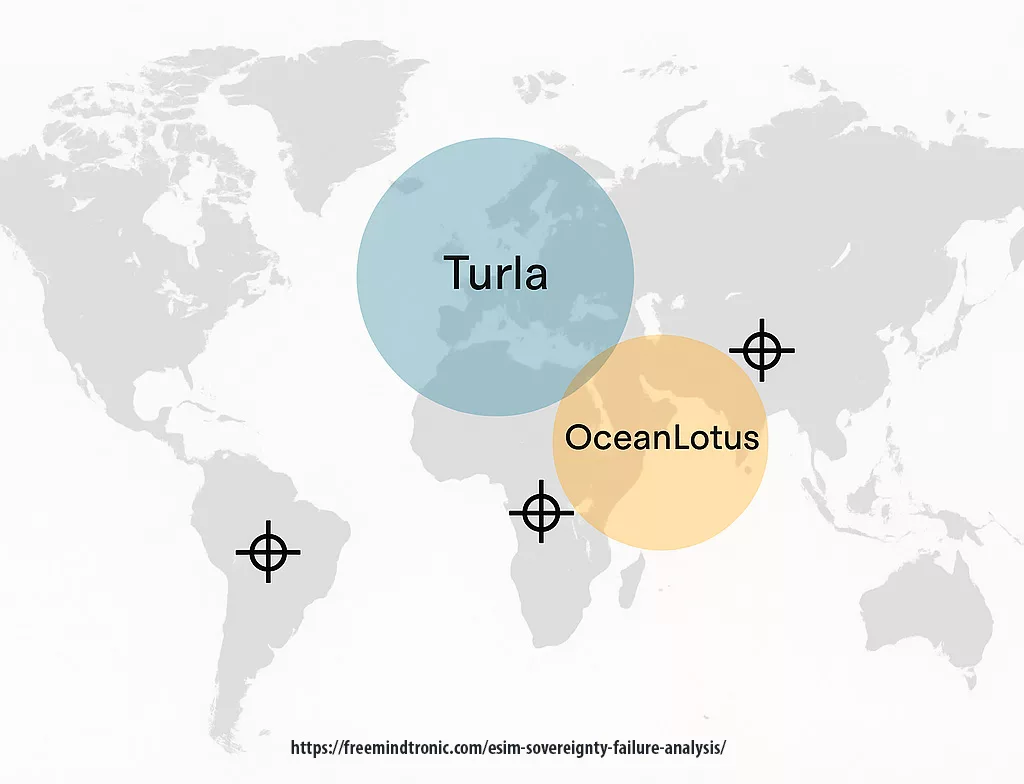
| OceanLotus (APT32) | Vietnam | Journalists, dissidents, telecom | Mobile surveillance, eSIM backdoor usage |
| Turla (Venomous Bear) | Russia | Embassies, gov networks | Satellite C2 usage — ideal for stealthy eSIM pivot |
| APT36 (also known as Transparent T., per official threat intelligence nomenclature) / APT36 Spear Phishing |
Pakistan | Indian military, mobile users | Android malware, known SIM/eSIM targeting |
| Lazarus Group (APT38) | North Korea | Finance, crypto, mobile | Certificate & mobile identity attacks observed |
These APT groups are technically capable and geopolitically incentivized to exploit the runtime opacity and provisioning blind spots inherent in GSMA-certified eSIM infrastructures. Their known operations intersect directly with critical layers of mobile identity management — from certificate chain manipulation to RSP flow infiltration.
The breach transforms eSIMs into offensive espionage platforms — enabling cryptographic-level impersonation, persistent access, and sovereign identity hijacking by state-grade actors.
✦ Weak Signals — Emerging Risks in eSIM Threat Intelligence
- Academic warnings unaddressed: Security Explorations has published detailed technical reports since 2021 highlighting runtime vulnerabilities in certified eSIM stacks — including memory disclosure flaws and invalid certificate acceptance.
- Zero adaptation by GSMA: Despite side-channel research such as the 2025 Kigen incident, GSMA certification flows (SGP.23-3 v3.1) remain focused on pre-deployment validation, omitting any runtime telemetry or post-certification threat model adaptation.
- Toolkits enabling telecom-layer APTs: MITRE’s Mobile ATT&CK matrix and Google Cloud’s APT dashboards both reflect increased use of provisioning subversion and SIM lifecycle manipulation — tactics consistent with state-driven campaigns but still untracked by telecom operators’ detection ecosystems.
- Blind compliance perimeter: The GSMA SAS does not require anomaly detection during SM-DP+/eUICC interaction sessions — a major blind spot that persists despite known vectorization paths exploited by actors like OceanLotus and Turla.
Strategic foresight: These signals collectively indicate a shift from purely technical vulnerabilities to systemic governance lapses. Sovereign runtime verification and on-device anomaly tracing are likely to become baseline requirements in future compliance frameworks, possibly triggered by regulatory pressure under CRA and NIS2 domains.
Runtime Threats in Certified eSIMs: Four Strategic Blind Spots
While geopolitical campaigns exploit the larger telecom attack surface, the technical fragility lies within the certified eSIMs themselves. This infographic categorizes the four strategic runtime threats exposed during the breach of the Kigen platform: injection threats, integrity bypass, platform subversion, and post-certification vulnerabilities.
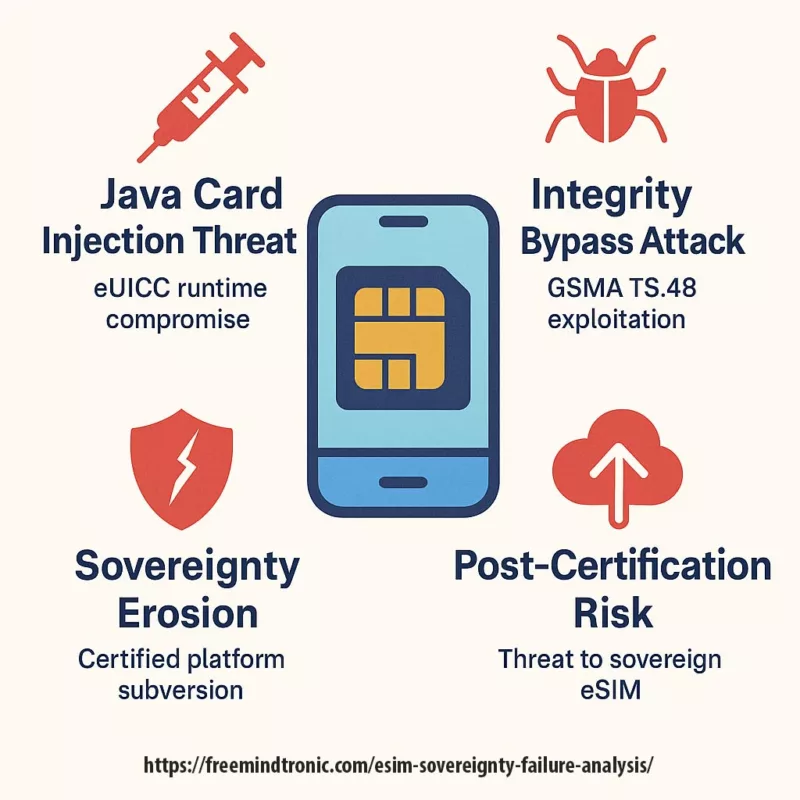
These threats bypass formal certification layers and exploit dynamic gaps in memory isolation, applet injection logic, and insufficient field telemetry — vulnerabilities that persist across certified stacks lacking sovereign runtime attestation.
Certified eSIMs face four critical runtime threats that remain invisible to traditional certification: injection, bypass, subversion, and post-deployment exposure. Without sovereign runtime attestation and hardware-resilient execution, these vectors reduce certified trust to a symbolic shield.
✦ Normative Blind Spots — Regulatory Gaps in eSIM Security Frameworks
Several critical attack surfaces remain unaddressed in regulatory frameworks like CRA, NIS2, and GSMA TS.48. These include runtime behavior validation, post-certification re-attestation, and sovereign auditability of cryptographic execution environments. The absence of mandatory entropy quality tests and secure lifecycle attestation mechanisms leaves certified stacks vulnerable to dormant threats exploitable post-deployment.
Examples of blind spots include:
- TS.48 lacks runtime memory protection enforcement.
- CRA does not cover volatile entropy regeneration failures.
- NIS2 omits sovereign runtime visibility mandates for mobile identity devices.
Cryptographic Fragility in eSIM Implementations
While eSIMs are often marketed as cryptographically secure by design, the Kigen incident exposes critical weaknesses at the implementation level. The core issue lies in the mismatch between theoretical algorithm strength and practical execution within constrained, embedded environments — particularly in Java Card-based secure elements.
The compromise demonstrated that cryptographic keys — including ECDSA and AES session material — could be exfiltrated through side-channel differentials amplified by improper memory sanitation and volatile buffer reuse. These weaknesses were neither mitigated by the applet’s formal validation nor by the certification authorities, which focus on static compliance rather than dynamic entropy or leakage resilience.
Additionally, entropy generation in some Kigen implementations relied on pseudo-random generators insufficiently seeded under certain power-reset conditions — a factor attackers exploited to reduce keyspace guessing during runtime.
Furthermore, the compromise highlights the limitations of relying solely on the GlobalPlatform SCP03 protocol for secure channel establishment. Although SCP03 ensures channel integrity, it does not defend against memory residue exploitation once the session concludes. As a result, sensitive values may remain in unprotected RAM zones accessible via glitching or crafted APDU logic.
Official reference for cryptographic side-channel standards: [https://csrc.nist.gov/publications/detail/sp/800-90b/final](https://csrc.nist.gov/publications/detail/sp/800-90b/final)
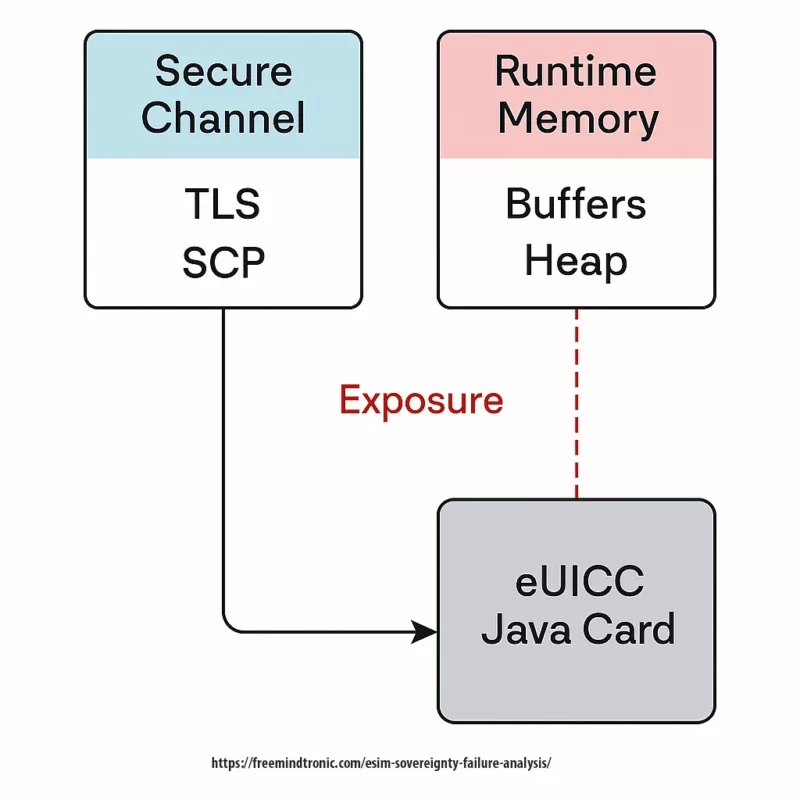
The fragility lies not in the cryptographic primitives themselves, but in the unverified assumptions about their deployment environment. Without sovereign runtime verification and hardware-hardened containers, certified eSIMs remain susceptible to low-level exfiltration despite high-level assurances.
Certified algorithms offer no immunity against weak runtime environments. Sovereign security demands continuous verification beyond algorithm compliance. This type of implementation gap directly reinforces the reality of an eSIM sovereignty failure even in certified stacks.
Sovereignty Scorecard: Evaluation Framework for National eSIM Policy
To assess the sovereign resilience of eSIM infrastructures, Freemindtronic introduces the Sovereignty Scorecard — a strategic evaluation framework that ranks national deployments across five critical dimensions: runtime integrity, credential isolation, certification independence, regulatory agility, and field attestation capabilities.
Each dimension is graded based on measurable criteria:
- Runtime Integrity — Presence of post-deployment attestation mechanisms and resistance to fault injection attacks.
- Credential Isolation — Use of off-host hardware modules (e.g., NFC HSM) to externalize secrets and eliminate on-card exposure.
- Certification Independence — Ability to validate eSIM security independently from GSMA or vendor-issued assertions.
- Regulatory Agility — Alignment with evolving frameworks like NIS2, CRA, and capacity to enforce breach-driven revocation.
- Field Attestation — Ability to confirm device compliance and integrity dynamically in operational conditions.
Based on current data, sovereign readiness varies widely. For instance, Estonia and France exhibit strong regulatory integration but diverge in credential isolation strategies. Meanwhile, federated nations such as the U.S. face internal inconsistency across state-level MNOs and eSIM issuers.
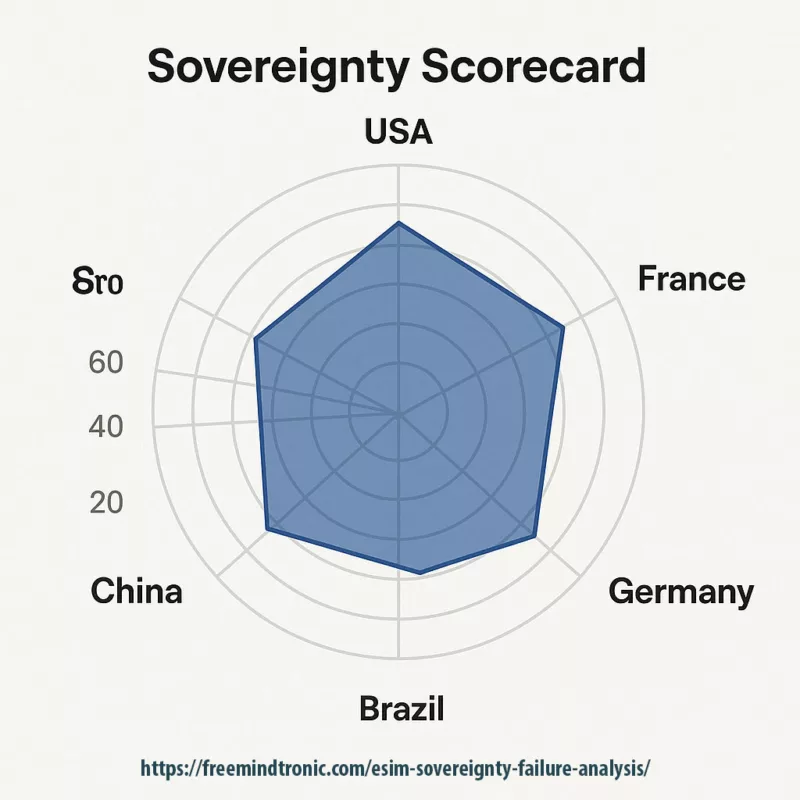
What is 𝒮ro?
𝒮ro (Sovereignty Runtime Exposure) is an aggregated vulnerability score that quantifies the sovereign risk associated with the runtime execution of eSIM profiles. It serves as a strategic indicator for assessing how exposed a mobile identity infrastructure is to external control, compromise, or unverifiable behavior during live operation.
This scorecard framework is intended not as a final metric but as a dynamic reference model to guide national policy adaptation and resilience strategy against systemic eSIM threats.
𝒮ro Exposure Levels
| 𝒮ro Score | Sovereign Exposure Level | Description |
|---|---|---|
| 20 | Low Exposure | Presence of sovereign runtime defense mechanisms (e.g., autonomous NFC HSM, internally validated countermeasures) |
| 40 | Moderate Exposure | Partial reliance on third-party infrastructures or absence of internal runtime validation |
| 60 | High Exposure | Certified critical infrastructures (e.g., Java Card, SM-DP+/DS) vulnerable at runtime without effective sovereign control |
| 80+ | Critical Exposure (Extrapolated) | Total dependency on certification chain, no sovereign runtime control, opaque execution environment |
Without multi-layer sovereign oversight — from runtime to regulation — national eSIM infrastructures remain structurally exposed. The Scorecard provides a benchmark to close that gap.
Zero Trust Recovery from eSIM Sovereignty Failure
In response to repeated instances of eSIM sovereignty failure, zero trust becomes not just strategic but mandatory.
The collapse of runtime trust in certified eUICC platforms mandates a paradigm shift: from perimeter-based assurance to a zero-trust model tailored for eSIM governance. This model reframes the eSIM not as a static, implicitly trusted object but as a dynamic actor that must continually prove its integrity, provenance, and compliance.
A zero-trust eSIM architecture encompasses:
- Hardware Root of Trust (HRoT) — Use of sovereign HSMs external to the eUICC to store and process critical credentials, mitigating in-situ compromise risks.
- Out-of-Band Attestation — Continuous verification of eSIM state via independent channels, ensuring profile consistency and integrity without relying on vendor telemetry.
- Dynamic Trust Brokering — Integration of policy engines capable of adjusting access privileges based on runtime posture, geopolitical context, or threat intelligence updates.
- Secure Update Chains — Implementation of field-verifiable patching protocols with sovereign signature verification, bypassing dependency on vendor-initiated OTA flows.
The design principle is clear: trust must be earned continuously, not granted via certification artifacts. In practical terms, this means MNOs and state operators must enforce mutual attestation with all eSIM-capable devices, using field-grade diagnostic tools and telemetry relays.
This approach aligns with emerging cybersecurity doctrines, including the European Union’s zero-trust strategic direction within the EU Cybersecurity Strategy, and anticipated provisions under the Cyber Resilience Act.
A post-certification eSIM strategy demands more than patches — it requires an operational posture of distrust, verification, and continuous control. Zero trust is no longer optional.
Weak Signals Identified
Long before the Kigen exploit became public, several early indicators hinted at systemic fragilities in the certified eSIM ecosystem. These weak signals, often dismissed as implementation quirks or vendor-specific limitations, now reveal themselves as precursors to broader architectural vulnerabilities.
- Patch Lag Across Certified Platforms — Multiple vendors delayed integration of Java Card security updates, despite public CVEs and independent advisories.
- Telemetry Blackouts During Remote Provisioning — Field reports noted unexplained telemetry silences during SM-DP+ operations, indicative of instruction hijacking or glitch attacks.
- Inconsistencies in Certification Scope — Certification reports from GSMA TS.48 evaluations showed variable test coverage across applet behaviors and runtime exceptions.
- Proprietary Obfuscation of eUICC Source Chains — OEMs increasingly deployed closed, undocumented applet stacks, frustrating independent auditing and validation.
These signals, while subtle, constituted a strategic early warning. Their disregard stems not from lack of data, but from an institutional overreliance on certification status as a proxy for ongoing security assurance.
Strategic breaches rarely erupt without warning — they ferment in ignored anomalies, silent faults, and governance blind spots. Sovereign vigilance starts with decoding the weak signals.
eSIM on External Storage?
A rising architectural trend in constrained embedded systems involves relocating eSIM data onto external memory modules — typically SPI NOR flash or embedded MultiMediaCard (eMMC). While appealing for hardware flexibility and cost reduction, this design undermines foundational security assumptions of the GSMA eUICC standard.
Externalizing the Secure Element (SE) storage exposes profile data and cryptographic keys to direct bus probing, voltage fault injection, and cold boot extraction. Even when encryption-at-rest is implemented, the integrity of runtime protection collapses once a malicious actor achieves physical access or exploits firmware vulnerabilities to redirect memory calls.
In several observed deployments, OEMs bypassed the GSMA’s certified secure loading protocols by using bootloader-level loading of profiles into external memory-mapped regions — a deviation incompatible with the runtime isolation requirements of eSIM standards.
Authorities such as the [European Union Agency for Cybersecurity (ENISA)](https://www.enisa.europa.eu) and [NIST](https://csrc.nist.gov/) have consistently emphasized that cryptographic material must remain bound to tamper-resistant hardware environments. External memory eSIMs contradict this principle, creating sovereign risk through dilution of trust anchors.
Offloading eSIM data to external storage breaks the hardware root-of-trust. Sovereign-grade identity management requires tamper-resistant, self-contained execution environments.
Misconceptions & Design Constraints
The certified eSIM ecosystem suffers from persistent misconceptions rooted in legacy SIM assumptions and abstracted design abstractions. One key fallacy is the belief that certification implies secure-by-design implementation across all operational contexts. In reality, GSMA certification primarily validates compliance with protocol-level behavior — not resilience to fault injection, physical attacks, or post-certification firmware drift.
Another widespread misconception is that Java Card security models inherently guarantee isolation and non-interference between applets. In practice, vulnerabilities in object reference handling, heap reuse patterns, and predictable class loading sequences allow one applet to indirectly infer or affect the state of another, especially when runtime monitoring is absent.
OEMs and MNOs often operate under the constraint of legacy infrastructure integration — prioritizing backward compatibility with SIM toolkits or OTA provisioning platforms over runtime verifiability. This constraint often leads to the embedding of insecure debug services, deprecated cipher suites, or relaxed access control mechanisms under the guise of “certified flexibility.”
The strategic consequence is a fragmented threat landscape where the weakest implementation in the supply chain compromises the entire trust anchor. Without sovereign control over lifecycle enforcement, firmware lockdown, and remote attestation, certification becomes a checkbox — not a defense.
Certification is not synonymous with sovereignty. Design shortcuts and legacy constraints perpetuate attack surfaces that sovereign architectures must isolate and harden by default.
Countermeasures Against Certified eSIM Sovereignty Threats
These measures directly mitigate the systemic blind spots responsible for the certified eSIM sovereignty failure.
In light of systemic runtime vulnerabilities and certification blind spots, sovereign cybersecurity architectures must prioritize verifiability, hardware isolation, and post-deployment attestation. Traditional eSIM infrastructures relying solely on GSMA certification cannot guarantee runtime integrity against state-level adversaries or advanced persistent threats (APTs).
The first line of defense is the elimination of in-field runtime secrets through hardware-based enclaves such as NFC HSMs. These devices externalize cryptographic operations and enforce out-of-band identity validation, mitigating the risk of key exposure during applet execution.
Secondly, sovereign architectures must incorporate real-time behavioral monitoring. They should leverage secure telemetry and tamper-evident logs to detect abnormal access patterns and control flow deviations.
In parallel, remote attestation plays a critical role. Ideally anchored in sovereign hardware roots of trust (RoT), it allows MNOs and regulators to verify that deployed eUICC modules remain unaltered since certification.
This process includes checking firmware hashes, assessing secure element states, and confirming the continuity of audit trails. Such mechanisms reinforce operational trust and transparency in high-assurance environments.
Furthermore, regulatory mandates must evolve to require sovereign oversight in the lifecycle management of certified secure elements. This includes revocation procedures, trusted firmware distribution channels, and cryptographic agility standards that support post-quantum migration paths.
Sovereign resilience requires architectures that do not merely comply with certification but enforce runtime integrity, field visibility, and cryptographic independence from third-party vendors.
Rethinking eSIM Governance with Sovereign NFC HSM
The structural failure exposed by the Kigen breach compels a foundational shift in how nations approach eSIM governance. Rather than perpetuating reliance on external certification authorities and embedded runtime platforms, sovereign models must prioritize minimal attack surfaces, externalized key management, and verifiable operational integrity.
NFC-based Hardware Security Modules (HSMs) represent a pivotal architectural response. By isolating secrets from the runtime environment and enabling offline transaction validation, these modules offer resilience against both remote and local attack vectors. Moreover, their user-mediated design supports privacy-preserving identity activation and fine-grained access control—without requiring permanent connectivity to central servers or vendor-controlled key managers.
This paradigm aligns with core sovereignty principles. It ensures jurisdictional control over digital identities, enables revocable credentials without foreign dependency, and supports auditable hardware roots of trust.
Moreover, it directly responds to growing regulatory pressures. Frameworks such as the European Cyber Resilience Act (CRA) and the NIS2 Directive increasingly demand demonstrable security and traceability for critical digital infrastructure.
Sovereign NFC HSM architectures offer a forward-compatible path for eSIM governance—enabling state-controlled identity assurance without runtime exposure or opaque vendor dependencies.
Use Case: From EviCall to EviSIM – Resilience via DataShielder NFC HSM Defense
Freemindtronic’s sovereign cybersecurity suite delivers a tangible countermeasure to runtime eSIM compromise. This is achieved through its NFC HSM-enabled technologies, which underpin platforms like EviCall and EviSIM. Both solutions integrate seamlessly with DataShielder to establish fully air-gapped, hardware-bound identity containers. These containers operate independently from traditional eUICC execution environments.
Externalization through NFC HSM: a runtime safeguard
Thanks to EviSIM, mobile identities and eSIM profiles are stored externally in a contactless NFC HSM. Once activated, the device executes cryptographic operations—such as authentication, signature generation, or key release—in real time. Crucially, these operations occur without exposing secrets to the host device’s operating system or runtime environment. As a result, even if the OS stack or baseband processor is compromised, the credentials remain shielded, immutable, and non-extractable. These safeguards directly counteract the runtime threats that caused the certified eSIM sovereignty failure.
Sovereign control via DataShielder architecture
Beyond this core isolation, the DataShielder framework introduces additional layers of control. These include dynamic self-destruct policies, offline multi-factor unlocking, and sovereign key attestation mechanisms. This architecture fundamentally diverges from remote provisioning models dominated by SM-DP+ infrastructures. Instead, EviSIM enables field-level validation and revocation under direct sovereign supervision.
En déplaçant l’assurance de l’identité mobile loin des ancrages de confiance contrôlés par l’étranger, EviSIM rétablit l’autonomie juridictionnelle. Il s’agit d’un modèle souverain pour sécuriser les identités numériques dans un écosystème de plus en plus compromis.
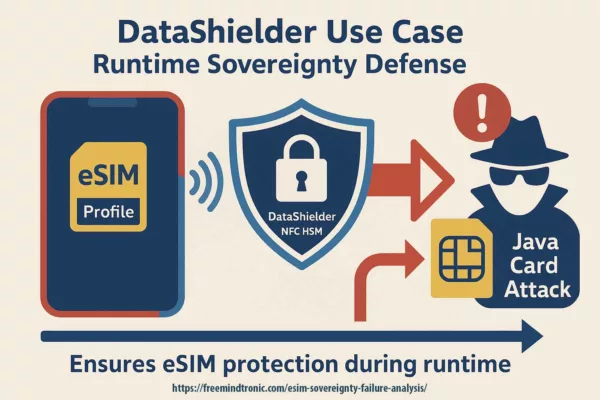
EviSIM powered by NFC HSM and DataShielder demonstrates a sovereign eSIM implementation: isolated from runtime compromise, resilient to side-channel attacks, and verifiably controlled under national jurisdiction.
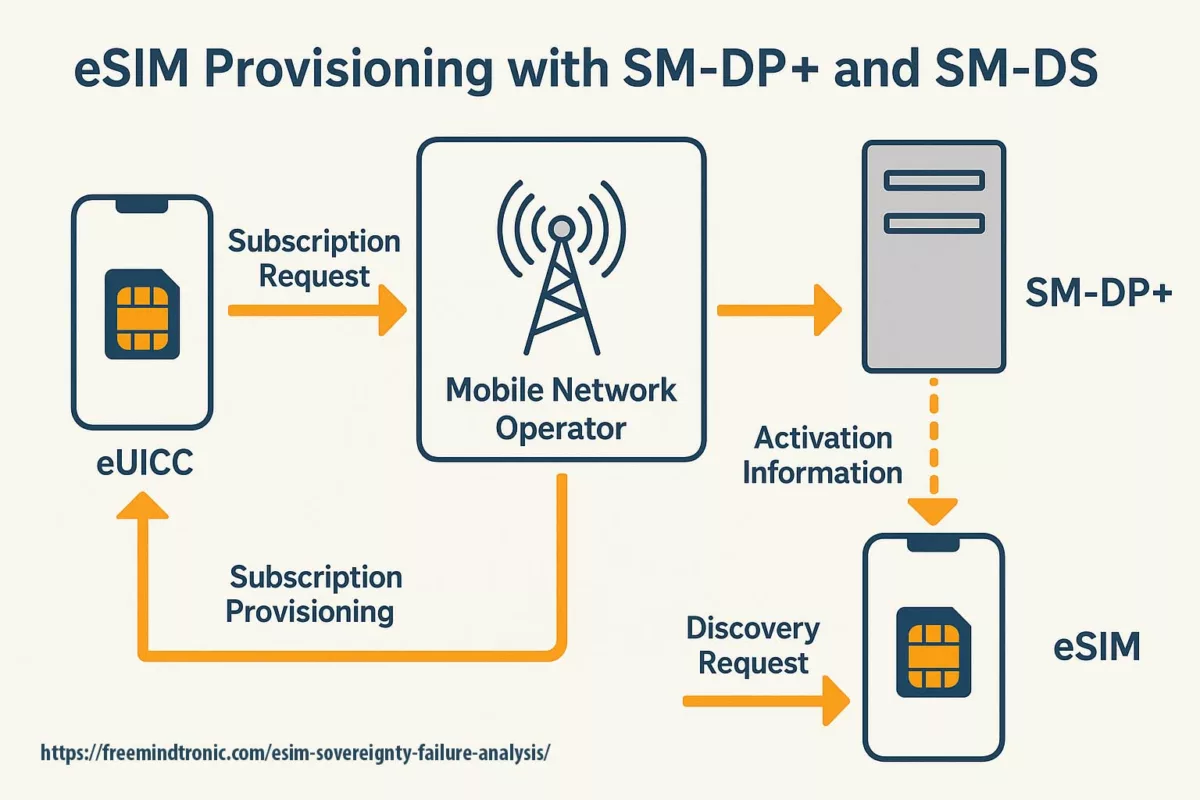
Infographic: Anatomy of SM-DP+/SM-DS Flow and Attack Vectors
To visualize the complexity and vulnerabilities in eSIM provisioning, this infographic maps the full lifecycle of an eSIM profile. It spans the SM-DP+ (Subscription Manager Data Preparation) and SM-DS (Discovery Service) systems, as defined by the GSMA’s Remote SIM Provisioning standard.
Key stages include:
- Initial bootstrap and device registration
- Profile download request and mutual authentication
- Encrypted delivery of the eSIM profile
- Activation and binding to the device’s secure element
Overlaying this flow are potential attack vectors such as:
- Side-channel leakage during profile decryption on the device
- Relay attacks exploiting delays in SM-DP+/SM-DS communication
- Malicious MNO provisioning triggering compromised profiles
- Lack of post-delivery attestation, allowing silent substitution
Each step is annotated to highlight where certified trust anchors can be bypassed through runtime manipulation or credential diversion. This systemic exposure reveals why runtime isolation and sovereign credentialing are no longer optional but foundational to eSIM security governance.
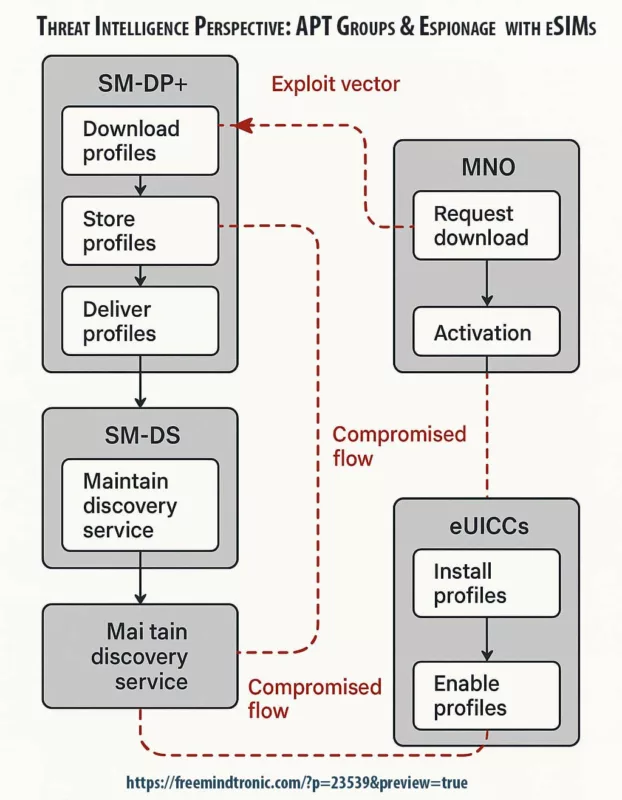
This visual breakdown of eSIM provisioning reveals multiple runtime blind spots exploitable by adversaries. It underscores the strategic necessity of sovereign field attestation and off-host credential storage.
Beyond This Chronicle: Expanding the eSIM Sovereignty Failure Scope
This Chronicle focused on a critical instance of eSIM sovereignty failure, but additional vectors deserve sovereign scrutiny. Yet several strategic dimensions remain outside the scope of this investigation and call for sovereign attention:
Post-quantum readiness of eSIM infrastructures
Currently, most GSMA certification frameworks still rely on elliptic-curve cryptography. This reliance poses vulnerabilities in a future post-quantum context. Moreover, the lack of mandated migration timelines toward post-quantum algorithms reveals enduring gaps in long-term identity resilience.
Private 5G and critical infrastructure deployments
Furthermore, industrial 5G networks using eSIM-based credentials introduce distinct threat vectors. This is particularly evident in autonomous systems, smart energy grids, or battlefield IoT scenarios. Such environments require sovereign attestation pipelines—yet current standards fail to address these needs.
eSIM vulnerabilities in satellite and remote deployments
Additionally, remote provisioning via low-Earth orbit (LEO) satellites presents unique security challenges. Telemetry spoofing and delay injection attacks become feasible, enabling potential bypasses of existing integrity verification methods.
Non-GSMA provisioning implementations
Lastly, certain sovereign entities are experimenting with bespoke eSIM frameworks beyond GSMA control. While these alternatives enhance autonomy, they risk fragmenting the ecosystem in the absence of interoperable verification mechanisms.
Each of these aspects warrants focused analysis and technical experimentation. Only through such sovereign efforts can the next generation of digital identity infrastructure achieve true resilience and autonomy.
Beyond this case study, sovereign cybersecurity strategy must encompass satellite, post-quantum, industrial, and extra-GSMA eSIM use cases. Each of these contexts presents their own attack surfaces and governance blind spots.
In light of ongoing eSIM profile compromises by APT groups, the sovereign solution DataShielder NFC HSM Defense integrating the EviCall module encrypts all messaging channels (SMS, MMS, RCS) independently from the operator profile.Even if the eUICC is infiltrated or cloned, content access remains impossible without the embedded sovereign hardware HSM. Asymmetric runtime encryption is enforced directly within the enclave — fully outside GSMA certification and undetectable by compromised infrastructures.🔐 This solution is available off-catalogue through Fullsecure (Andorra) from Freemindtronic and AMG PRO (France), trusted sovereign deployment partners.



































































































