Email metadata privacy sits at the core of Europe’s digital sovereignty: understand the risks, the EU legal framework (GDPR/ePrivacy), and DataShielder countermeasures.
Column summary — email metadata privacy
⚡ Goal
Grasp what email metadata actually reveals (IP addresses, timestamps, recipients, intermediate servers), why it stays visible even when content is encrypted, and how the European Union regulates its use (GDPR, ePrivacy, CNIL and Garante decisions).
💥 Scope
This article targets organisations and individuals concerned with communications privacy: journalists, NGOs, companies, public bodies.
It covers email (SMTP, IMAP, POP), end‑to‑end encrypted messengers, telephony, video conferencing, the web, social networks, IoT, cloud, DNS and even blockchains.
🔑 Doctrine
Metadata is a structural invariant: you can’t remove it from the protocol, but you can neutralise and compartmentalise it.
Conventional solutions (VPN, PGP, SPF/DKIM/DMARC, MTA‑STS) provide partial protection, but digital sovereignty requires going further with DataShielder HSM (NFC and PGP HSM), which encapsulates content, reduces telemetry, and segments usage.
🌍 Strategic differentiator
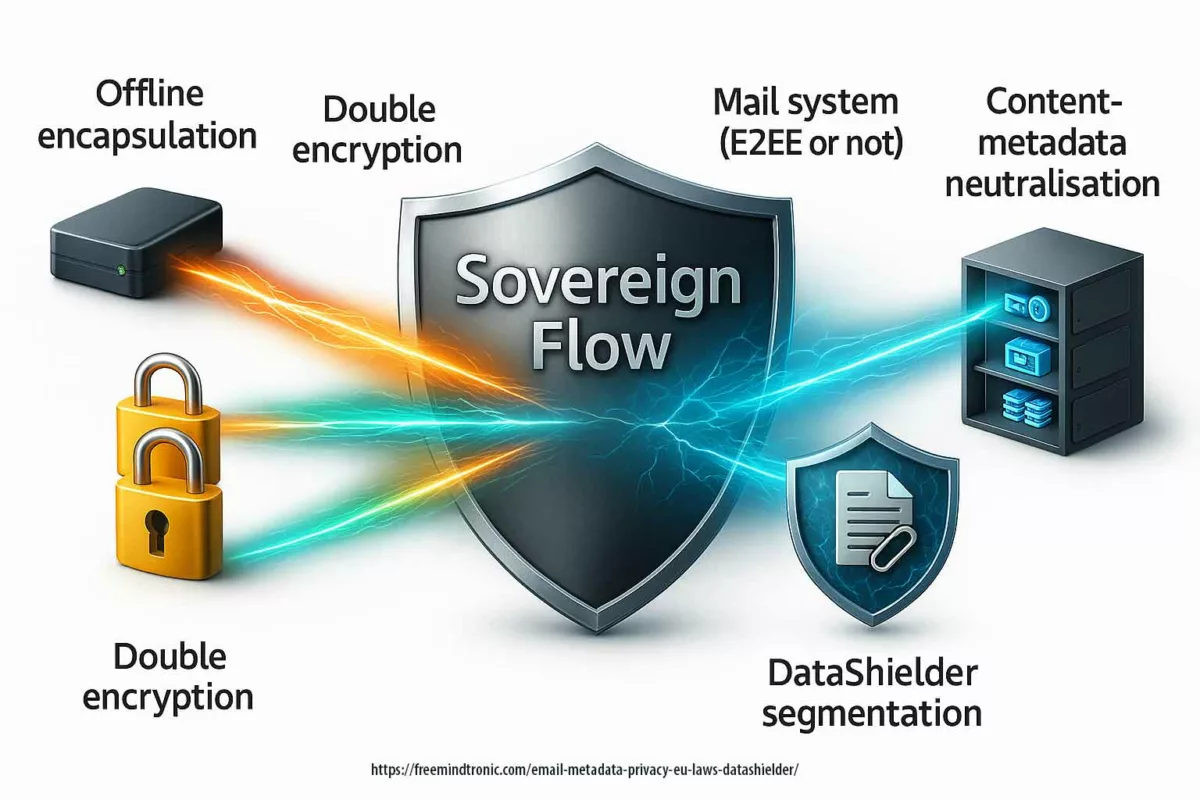
Unlike software‑only or cloud‑centric approaches, DataShielder adopts a zero cloud, zero disk, zero DOM posture. It encrypts upfront (offline), encapsulates the message, then lets your mail system (encrypted or not) apply its own encryption.
Result ⮞ double encryption, neutralisation of content metadata (subject line, attachments, MIME structure) and stronger opacity against traffic analysis. A strategic edge for sensitive communications in Europe and beyond.
Technical note
Reading time (summary): ≈ 4 minutes
Reading time (full): ~35 minutes
Level: Security / Cyberculture / Digital Security
Posture: Sovereign encapsulation, defence‑in‑depth
Sections: Digital Security
Languages available: FR · EN · CAT · ES
Editorial type: Column
About the author: Jacques Gascuel, Freemindtronic® inventor — sovereign HSM architectures, key segmentation, offline resilience, sovereign communications protection.
TL;DR —
Email metadata reveals more than message content. It traces who talks to whom, when, and through which servers. Conventional tools (VPN, TLS, PGP) don’t hide it.
Only a sovereign approach like DataShielder (NFC HSM & PGP HSM) can shrink the attack surface, neutralise content metadata via encapsulation, and thwart abusive correlation. This is strategic given legal duties (GDPR, ePrivacy) and the risks of both lawful and unlawful espionage.
In cybersecurity and digital sovereignty ↑ this column is part of Digital Security and fits the sovereign toolchain by Freemindtronic (HSM, key segmentation, encapsulation, offline resilience).
- Column summary — email metadata privacy
- Definition — What is metadata?
- Which email metadata exist (RFC 5321/5322)?
- What providers can see — visible digital traces
- Francophone & European stats — metadata retention
- Exploitation risks — profiling & surveillance via metadata
- EU legal framework — GDPR, ePrivacy & email privacy
- Classic defences — mail protocols & their limits
- Sovereign countermeasures — DataShielder™
- Sovereign flow — offline encapsulation & double encryption
- End‑to‑end messengers (E2EE) & residual metadata
- Beyond email — metadata across communications
- Other infrastructures — IoT, cloud, blockchain
- Cybersecurity & espionage — legitimate vs abusive
- Real‑world use cases — NGOs, journalists, SMEs
- Practical guide — reduce email‑metadata exposure
- Weak signals 2025→2027 — emerging trends
- FAQ — common questions on email metadata
- Strategic outlook — digital sovereignty & comms
- Weak Signals — Trends to watch
Definition — What is metadata?
The term metadata literally means data about data. It is contextual information that describes, frames, or qualifies a digital asset without being part of it. Metadata is ubiquitous: it accompanies every file, every communication, and every technical record.
- Common examples — A Word document stores the author and last‑modified date. A photo embeds GPS coordinates. An email includes the sender’s IP address and the time sent.
- Primary function — Help sort, search, and manage data across digital systems.
- Side effect — Expose traces exploitable for tracking, surveillance, or correlation, even when content is encrypted.
⮞ Summary
Metadata is context data. It doesn’t say what is communicated, but reveals how, when, where, and by whom. It is essential to digital systems yet represents a strategic exposure surface.
Which email metadata exist (RFC 5321/5322)?
Email metadata privacy rests on a key protocol distinction. The content of a message (body, attachments) is not the same as its metadata. RFC 5321 (SMTP) and RFC 5322 (header format) codify these details. They define what remains visible and what gets hidden. They include: sender address (From), recipient(s) (To, Cc), subject (Subject), timestamp (Date), unique identifier (Message-ID), and the list of SMTP relays traversed (Received headers).
These data do not disappear when the message is encrypted with PGP or S/MIME. They remain exposed to providers, ISPs, and intermediate operators. In practice, they build a true social and technical map of your exchanges.
For journalists, such traces can reveal supposedly confidential contacts.
For NGOs, they expose partner networks, funders, and local relays.
For businesses, they reveal deal flows, decision rhythms, and working hours. This invisible granularity makes metadata extremely powerful — often more useful for surveillance than the content itself.
⮞ Summary
Defined by RFC 5321/5322, email metadata comprises headers and transport traces. They are indispensable for routing and impossible to hide. Result: they reveal identity, chronology, and infrastructure of exchanges, even when content is encrypted.
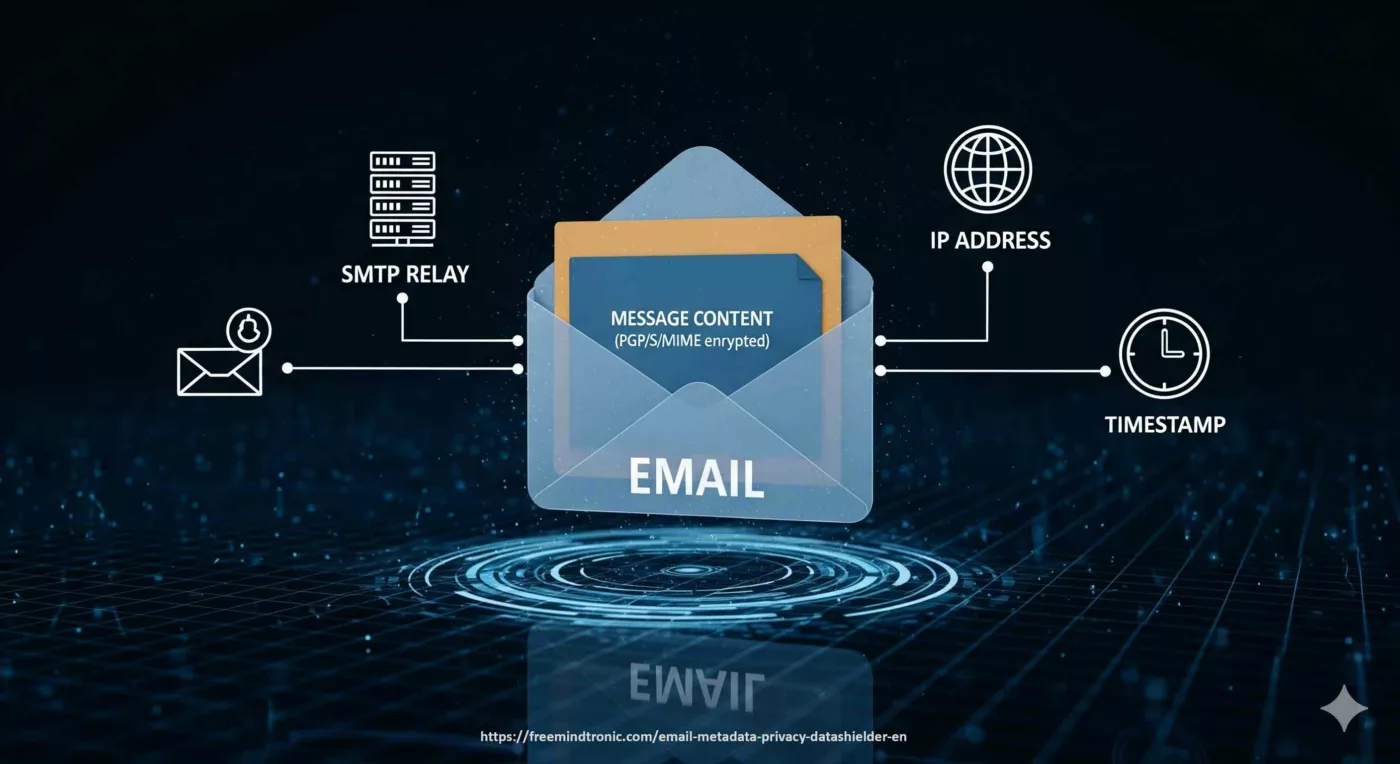
What providers can see
Email‑metadata privacy runs into a technical reality. Internet access providers and mail operators have near‑total visibility over headers and flows. At each connection, servers record the sender’s IP address and timestamps. They also log the relays traversed. Even if content is encrypted, this telemetry remains exploitable.
At Google, Gmail infrastructure systematically retains full headers, enabling fine correlation between users and devices.
Microsoft (Outlook/Exchange Online) follows similar policies, integrating these data into anomaly‑detection and compliance systems.
European providers such as Orange or SFR also keep SMTP/IMAP/POP logs, under national and EU retention obligations.
The bare minimum remains visible: the server’s IP address is always exposed. Depending on the client (webmail, mobile app, desktop client), the user’s IP address may also appear in headers. Combined with routing metadata, this exposure is enough to build a technical profile and a **behavioural profile** of correspondents.
Providers (Google, Microsoft, Orange) systematically keep headers and IPs. Even under encryption, these data stay visible and enable profiling. Server IPs are always exposed; depending on the client, the user IP can be exposed too.
Recent news — email (2024→2025)
CNIL — Tracking pixels in emails: the CNIL launched a public consultation to regulate tracking pixels under GDPR consent. Public summaries confirm a push for strict oversight (June–July 2025).
EU — EDPB: reminder that pixels track email opens and are processing subject to GDPR/ePrivacy.
Gmail/Yahoo → Microsoft/Outlook: after Google/Yahoo (02/2024), Microsoft aligned its requirements for bulk senders (SPF, DKIM, DMARC) with reinforced measures from 05/05/2025.
Italy — Garante: tougher stance on retention of employees’ email metadata (reference 7 days, extendable 48h) and first GDPR fine of 2025 for unlawful metadata retention.
⮞ Email synthesis
The ecosystem mandates DMARC/SPF/DKIM for bulk senders and clamps down on tracking pixels. Compliance is now a deliverability prerequisite, while email‑metadata privacy remains a central GDPR issue.
Recent events — Why metadata matters in 2025
The second half of 2025 has seen decisive shifts. Jurisprudence, sanctions, and emerging threats confirm that metadata is no longer a technical footnote — it is now a strategic pillar of digital sovereignty.
Updates — Messengers & E2EE
Debates around end‑to‑end encryption and residual metadata are intensifying. Key developments include:
- Proton: In June and July 2025, Proton updated its privacy policies to clarify how minimal metadata and system-level data are handled. These updates reaffirm Proton’s commitment to privacy-by-design and validate a sovereign, granular approach to metadata control. See Proton privacy policies.
- WhatsApp (Meta): In June 2025, Meta began rolling out targeted ads in WhatsApp’s “Updates” tab, using metadata such as location, language, and channel interactions — while maintaining E2EE for messages. This move reignited debate over the limits of encryption when metadata remains exploitable. Read about WhatsApp Status ads.
Legal & technical events
The legal and technical landscape around email metadata continues to evolve:
- Case law — employee rights: On June 18, 2025, the French Cour de cassation ruled that professional emails and their metadata are personal data under GDPR. Employees retain access rights even after contract termination. This ruling reinforces the need for sovereign tools to manage and neutralise metadata. See the ruling summary.
- Cybersecurity — generative threats: In May 2025, Barracuda Networks reported that 24% of emails</strong are now malicious or unwanted spam. Quishing (QR-code phishing), polymorphic scripts, and AI-generated payloads are rising sharply. Sovereign solutions like DataShielder™ that neutralise metadata and reinforce authentication (DMARC, MTA‑STS) are increasingly critical. Read the Barracuda report.
- CNIL sanctions & infrastructure fragility: In September 2025, the CNIL fined Google (€325M) and Shein (€150M) for illegal tracker deployment and consent violations. Just weeks earlier, a cyberattack on Google exposed Salesforce-linked business data, highlighting the vulnerability of centralised infrastructures. See CNIL decision · Read about the Google breach
⮞ Synthesis
These developments confirm a strategic shift: email‑metadata privacy is now a legal, operational, and geopolitical issue. Sovereign countermeasures — such as offline encapsulation, metadata segmentation, and double encryption — are no longer optional. They are essential.
Global statistics — email‑metadata privacy across jurisdictions
General trends
Email‑metadata privacy is not just theoretical — it’s measurable. Studies and regulatory actions across Europe, the Francophone world, and key English‑speaking jurisdictions confirm the scale of metadata retention and its impact on privacy, cybersecurity, and sovereignty.
🇪🇺 Europe & Francophone space
- France — According to the CNIL, over 72% of privacy complaints in 2024 involved excessive collection of communications data, including email metadata. In 2025, CNIL reinforced its European strategy to regulate cross‑border flows and technical metadata.
- European Union — The EDPB reports that 85% of providers retain IP addresses and SMTP headers for 6 to 24 months. Guidelines issued in January 2025 stress the need for metadata segmentation at collection.
- Italy — In 2025, the Garante limited employee geolocation metadata retention to 24h and professional email metadata to 21 days, unless union-approved or authorized by labor inspection.
- Switzerland — The OFCOM mandates 6‑month retention of messaging metadata, even for secure services.
- Belgium & Luxembourg — Telecom regulators (IBPT, ILR) confirm systematic retention of SMTP logs for judicial access, up to 18 months.
- Monaco — The CCIN enforces CNIL‑aligned retention rules for public services.
English‑speaking jurisdictions
- United States — Under the Federal Rules of Civil Procedure (FRCP), email metadata relevant to litigation must be retained. State‑level laws (e.g., California CPRA, Virginia CDPA) now impose GDPR‑style retention and deletion obligations.
- United Kingdom — Post‑Brexit, the UK Data Protection Act 2018 mirrors GDPR. Metadata retention must be justified, proportionate, and documented. Enforcement has intensified since 2024.
- Australia — The ACMA enforces the Data Retention Act 2015, requiring ISPs to retain metadata (IP, timestamps, routing) for 2 years.
- India — Under the IT Act and CERT-IN guidelines, email and connection metadata must be retained for 180 days. New rules in 2025 extend retention for critical infrastructure providers.
- Canada (outside Québec) — PIPEDA mandates proportional retention. Most providers retain SMTP logs for 6 to 12 months, with stricter rules under provincial laws like Ontario’s Bill 194.
⮞ Summary
Across Europe, the Francophone world, and major English‑speaking jurisdictions, email‑metadata retention is near‑systematic — from 6 months (Switzerland, Canada) to 2 years (France, Australia). Even encrypted services are subject to metadata logging. Sovereign strategies — offline encapsulation, usage segmentation, granular neutralisation — are no longer optional. They are essential.
Regulatory map — retention periods by country
| Country | Retention period | Legal framework |
|---|---|---|
| France | Up to 2 years | CNIL, GDPR |
| European Union | 6 months to 2 years | EDPB, GDPR |
| Italy | 24h (geo), 21 days (email) | Garante, Labor Code |
| Switzerland | 6 months | OFCOM |
| Belgium / Luxembourg | Up to 18 months | IBPT / ILR |
| Canada (Québec) | 6–12 months | CRTC, PIPEDA |
| Canada (other) | 6–12 months | PIPEDA, provincial laws |
| United States | Case‑dependent | FRCP, CPRA, CDPA |
| United Kingdom | Proportional | UK DPA 2018 |
| Australia | 2 years | ACMA, Data Retention Act |
| India | 180 days | IT Act, CERT-IN |
| Morocco | 12 months | ANRT |
| Senegal | 1 year | CDP |
| Monaco | Regulated | CCIN |
This map confirms that metadata retention is regulated — but rarely minimised. Sovereign strategies such as segmentation, encapsulation, and neutralisation are essential to regain control.
Exploitation risks — profiling & surveillance via metadata
Email metadata is a powerful analytical vector. By aggregating IP addresses, SMTP headers, timestamps, and routing data, one can reconstruct a social graph: who exchanges with whom, how often, and in what context. This alone can expose entire networks — journalists, NGOs, companies, or political groups.
In business, the same metadata feeds ad‑profiling, industrial espionage, and competitive intelligence. Platforms correlate technical identifiers with purchase behaviour, geolocation (via IP), and production cycles. In 2025, several advertising networks began integrating email metadata with app telemetry, DNS logs, and biometric signals to refine behavioural targeting.
Public authorities also leverage metadata for lawful surveillance and national security. In Australia, India, and the UK, metadata retention is used to monitor critical infrastructure and encrypted traffic. The boundary between legitimate use and systemic abuse is increasingly blurred — especially with tracking pixels embedded in marketing emails. The EDPB, CNIL, and the UK’s ICO reaffirmed in 2025 that such trackers require explicit consent and must not be deployed covertly.
In the workplace, metadata is now recognised as personal data under GDPR and UK DPA. A landmark ruling in Italy confirmed that metadata can infer performance, productivity, and behavioural patterns — triggering the first GDPR fine for unlawful retention. In the US, inferred profiling from metadata is now regulated under CPRA and CDPA.
Combined across vectors — advertising, espionage, state surveillance, workplace monitoring — metadata becomes a strategic lever to anticipate behaviours, select targets, and steer decisions. When exploited abusively, it undermines privacy, distorts agency, and opens the door to systemic drift.
⮞ Summary
Email metadata enables social‑graph mapping, fuels commercial profiling, and powers surveillance. Legitimate uses exist (security, judicial investigations), but abusive exploitation — especially when combined with AI, biometric telemetry, and cross‑protocol inference — poses strategic risks to individuals, organisations, and democratic systems.
EU legal framework — GDPR, ePrivacy & email privacy
Email‑metadata privacy is governed by a layered and increasingly fragmented European legal framework. The GDPR requires data controllers to limit collection to what is strictly necessary — yet communications metadata is often retained far beyond the minimisation principle, especially in enterprise and infrastructure contexts.
The ePrivacy Directive, via Article 5(3), reinforces prior‑consent requirements for tracking technologies, including invisible pixels embedded in emails. In 2025, the CNIL and the EDPB reiterated that such trackers constitute personal data and require explicit, informed user consent.
However, the long‑awaited reform of ePrivacy — intended to modernise and harmonise metadata governance across the EU — was officially withdrawn in February 2025 due to lack of consensus among co‑legislators. The existing directive remains in force, but Member States now diverge in interpretation and enforcement.
At national level:
– 🇮🇹 Italy’s Garante limits employee email metadata retention to 7 days (extendable by 48h), and geolocation metadata to 24h without justification.
– 🇫🇷 France’s CNIL enforces granular consent and transparency obligations for SMTP logs, trackers, and inferred behavioural metadata.
– 🇪🇸 Spain and 🇩🇪 Germany are expected to follow with sector‑specific guidelines for telecoms, finance, and public services.
This legal patchwork illustrates the tension between operational necessity (cybersecurity, compliance, infrastructure monitoring) and privacy protection (minimisation, consent, sovereignty). At EU level, the debate remains unresolved: should large‑scale metadata retention be permitted for cybersecurity and judicial purposes, or should proportionality prevail to avoid systemic surveillance?
⮞ Summary
GDPR and ePrivacy govern email metadata through consent and minimisation. But with the ePrivacy reform officially abandoned in 2025, Member States now diverge in enforcement. Between security, compliance, and sovereignty, Europe continues to seek equilibrium — while metadata remains a strategic and contested asset.
Classic defences — mail protocols & their limits
To mitigate email‑metadata privacy risks, several mechanisms are widely deployed. SPF, DKIM, and DMARC strengthen sender authentication and reduce spoofing. MTA‑STS and TLS‑RPT aim to enforce secure delivery by mandating TLS between mail servers.
These improve flow integrity and authenticity, but leave transport headers and IP addresses intact. In short, they don’t protect metadata itself.
Content encryption solutions like PGP or S/MIME add an important confidentiality layer for message bodies. However, they only hide the body and attachments. Sensitive fields like Subject, To, From, and Received headers remain visible to providers or SMTP relays.
Some users turn to VPN or Tor. These can anonymise the client‑side IP, yet do not stop servers from retaining headers. Defence remains partial.
⮞ Summary
SPF, DKIM, DMARC, MTA‑STS, and TLS‑RPT secure mail transport and authentication — not metadata. PGP/S/MIME encrypt content, not headers. VPN and Tor can mask user IP, but can’t prevent server‑side header retention.
Sovereign countermeasures — DataShielder™ and secure communications
Why go beyond conventional solutions?
Traditional tools (VPN, PGP, SPF/DKIM/DMARC) offer partial protection of email‑metadata privacy. To go further, Freemindtronic deploys sovereign countermeasures through DataShielder™: a hardware‑anchored architecture designed to compartmentalise usage and reduce exposure.
Regulatory compliance and critical use
In October 2024, DataShielder HSM NFC was classified as a dual‑use civil and military product under [EU Regulation 2021/821], and received import authorization from ANSSI. In February 2025, its re-export to EU Member States was approved, confirming its suitability for critical environments.
Segmented encapsulation and double encryption
An advanced segmented encapsulation mode was introduced in DataShielder HSM PGP. It separates MIME metadata (attachments, structure, MIME types) into independently encrypted blocks. The Subject line remains deliberately visible to preserve usability — a strategic choice by the inventor.
Encapsulated data is then injected into communication channels (SMTP, E2EE, cloud), which apply a second layer of encryption. This preemptive double encryption complicates any attempt at abusive correlation.
This architecture is designed for counter‑espionage use cases, where identity segmentation and trace neutralisation are operational imperatives.
Sovereign storage and offline isolation
DataShielder HSM NFC ensures offline storage of keys and digital identities. Its physical isolation prevents leakage to cloud or disk, guaranteeing local, segmented control.
Meanwhile, DataShielder HSM PGP desktop encapsulates the message before sending using AES‑256 CBC PGP with segmented keys. This sovereign lock precedes native encryption by the messaging system (PGP, S/MIME, E2EE), ensuring two-layer protection.
What remains visible — and why
Only transport metadata (IP addresses, traversed servers, timestamps) remains visible, as required by SMTP routing. These elements are technical invariants, but their value is significantly reduced by content opacity.
✓ Sovereign countermeasure summary
- Offline key compartmentalisation with DataShielder HSM NFC
- Offline encapsulation → AES‑256 CBC PGP with segmented keys
- Double encryption: sovereign encapsulation + native mail encryption
- Neutralisation of content metadata (attachments, MIME structure)
- Visible subject line by strategic choice to preserve usability
- Reduced local traces and segmented identity architecture
Official distribution
Fullsecure Andorra is the official distributor of Freemindtronic technologies, including DataShielder™, for the Principality of Andorra. Specialised in sovereign cybersecurity and critical infrastructure protection, Fullsecure ensures traceable deployment, regulatory compliance, and dedicated support for sensitive environments.
In France, AMG PRO is the exclusive distributor of DataShielder™ HSM NFC. Focused on tactical equipment and dual‑use cybersecurity solutions, AMG PRO serves government agencies, law enforcement, and sensitive private‑sector entities. The products are also supported by Bleu Jour, AMG PRO’s technology partner, known for its industrial computing solutions and commitment to French manufacturing.
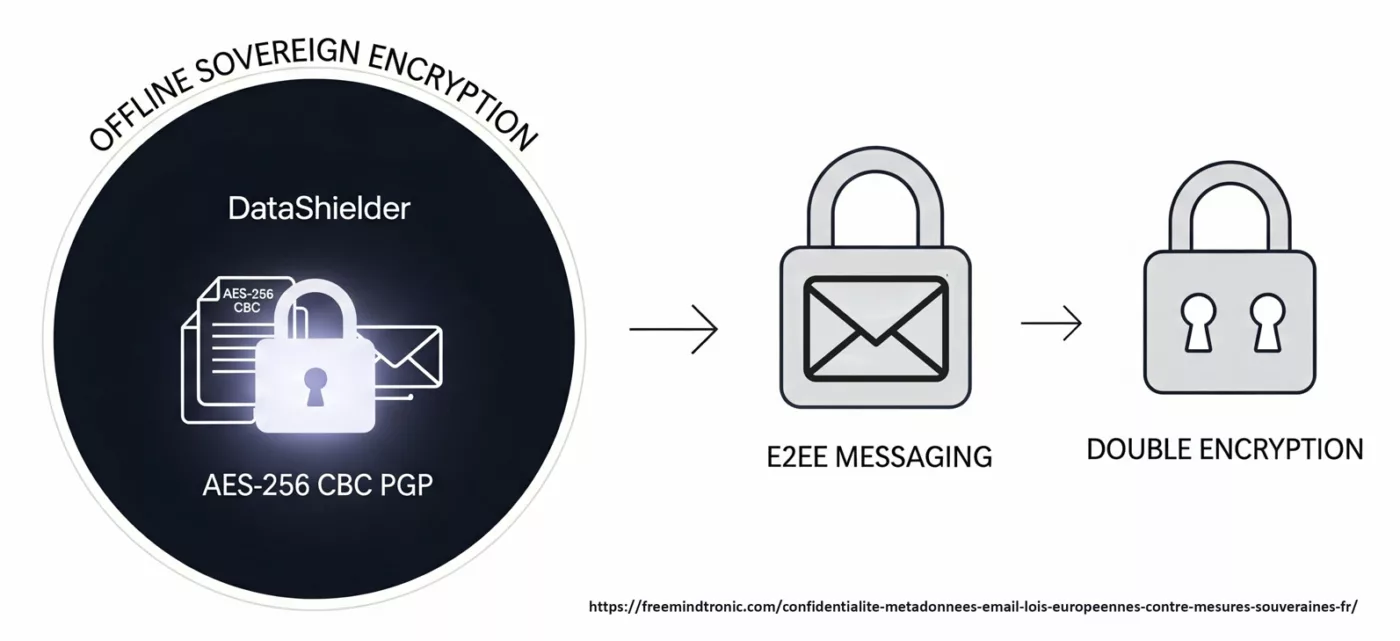
✪ Diagram — Double encryption combines offline encapsulation (DataShielder) with the messenger’s E2EE for maximum resilience.
Sovereign flow — offline encapsulation & double encryption
The sovereign flow implemented by DataShielder™ follows a precise chain designed to neutralise content metadata and compartmentalise usage, reducing what third parties can exploit to the bare minimum.
- Offline encapsulation — The message and its attachments are first encrypted offline with AES‑256 CBC PGP using segmented keys stored in DataShielder HSM NFC or DataShielder HSM PGP desktop. Content (text, attachments, MIME structure) becomes fully opaque.
- Double encryption — Once encapsulated, the message is handed to the mail system, which applies its own encryption (PGP, S/MIME, or E2EE, depending on the service). Outcome: two locks.
- Neutralisation of content metadata — Subject, attachments, and MIME structure are contained within the encrypted payload, preventing provider‑side analysis.
- Persistence of transport metadata — Only IP addresses, relays, and timestamps remain visible, as they are indispensable to SMTP routing.
This architecture introduces analytical friction that exceeds typical automated correlation capabilities, creating cryptographic noise that makes profiling or interception costlier and less certain.
⮞ Summary
The DataShielder sovereign flow combines offline encapsulation (AES‑256 CBC PGP + segmented keys, covering messages and attachments) with mail‑layer encryption (PGP, S/MIME, or E2EE). Result: double encryption, content‑metadata neutralisation, and reduced correlation. Only transport metadata remains visible for routing.
End‑to‑end encrypted messengers (E2EE) & residual metadata
Services like ProtonMail, Tutanota, Signal, Matrix, or WhatsApp ensure that only sender and recipient can read messages. No third party can decrypt the content — even the provider.
However, even with E2EE, some metadata remains exposed. Transport metadata (origin IP, SMTP relays, timestamps) is required for routing and cannot be hidden. Some content metadata such as Subject, file size, or MIME type may also be accessible depending on the protocol and implementation.
In 2025, the EU’s Digital Markets Act (DMA) introduced mandatory interoperability between messaging platforms. While this improves accessibility, it also increases metadata exposure across systems. Meta’s implementation of WhatsApp interoperability confirms that E2EE does not neutralise metadata shared between third-party services.
This is why the DataShielder™ sovereign approach complements E2EE services. By encapsulating messages and files offline using AES‑256 CBC PGP with segmented keys, the content becomes opaque before it ever reaches the server. The E2EE service then applies its own encryption, resulting in double encryption: sovereign offline + native E2EE.
This layered architecture reduces the exploitable surface, neutralises content metadata (subject, attachments, MIME), and ensures that only transport metadata remains — a technical invariant required for delivery.
⮞ Summary
E2EE protects message content, but not all metadata. With DataShielder™, messages and attachments are encapsulated offline, then encrypted again by the E2EE service — a double lock that neutralises content metadata and strengthens privacy across interoperable platforms.
Beyond email — metadata in all communications
The metadata‑privacy problem extends beyond email. Every digital service produces traces, often invisible to users yet highly exploitable by providers, platforms, and authorities.
- Instant messaging — Slack, Teams, Messenger, Telegram log connection times, groups joined, and associated IPs.
- VoIP & video — Zoom, Skype, Jitsi expose call duration, participants, and relays.
- Mobile telephony & SMS — Operators retain call metadata (calling/called numbers, cell‑ID, duration, rough location).
- Web browsing — Even with HTTPS, IP address, DNS resolutions, and TLS SNI reveal destinations.
- Social networks & cloud — Platforms like Facebook, Google Drive, Dropbox exploit access logs, devices used, and file‑sharing histories.
- VPN & Tor — These mask origin IP but don’t erase logs retained by certain nodes or operators.
Alone, these bits seem trivial. Aggregated, they form a behavioural profile capable of revealing work habits, social ties, even political or union leanings.
⮞ Summary
Metadata goes far beyond email: instant messaging, VoIP, SMS, web, social platforms, and cloud generate it continuously. In isolation they look harmless; aggregated they enable broad surveillance.
Other infrastructures — IoT, cloud, blockchain & technical traces
Metadata privacy also covers digital and industrial infrastructure. Each technical interaction leaves an exploitable trace, often more persistent than human communications.
- Connected objects (IoT) — Voice assistants, medical wearables, or home sensors continuously emit activity logs, including usage times and unique identifiers.
- Cloud storage & collaboration — Services like Google Drive, OneDrive, Dropbox keep access timestamps, devices used, and sharing histories, even if files are encrypted.
- DNS & network metadata — Every DNS lookup, every TLS SNI, every firewall log exposes destinations and frequency, independent of content.
- Blockchain & crypto — Transactions are immutable and public; addresses form permanent metadata, traceable at scale via graph analysis.
These stacks show metadata has become a structural invariant of the digital realm. It cannot be removed, but must be neutralised or compartmentalised to limit abusive exploitation.
⮞ Summary
IoT, cloud, DNS, and blockchain generate persistent metadata. They underpin digital infrastructure yet expose exploitable traces, even without readable content.
Cybersecurity & espionage — legitimate vs abusive uses
Metadata has ambivalent value. On one hand it is essential to cybersecurity and justice: connection logs, IPs, and timestamps let SOC teams and investigators detect anomalies, identify attacks, and build evidence.
On the other hand, the same data becomes an espionage instrument when exploited outside legal bounds: state or industrial actors can map relationships, anticipate strategic decisions, or track sensitive organisations in real time. Intrusive ad campaigns also rely on covert correlation mechanisms.
DataShielder™ actively counters abusive exploitation. It encapsulates messages offline, applies double encryption, and segments identities to reduce local traces and disrupt correlation attempts. At the same time, it preserves legitimate use cases—such as security audits or judicial investigations—by maintaining access to transport metadata. Meanwhile, content metadata like subject lines, MIME structure, and attachments is neutralised before transmission, ensuring that sensitive information remains shielded from profiling and surveillance.
⮞ Summary
Metadata is dual‑use: legitimate for security and justice, illegitimate for espionage and abusive profiling. Sovereignty means enabling the former while neutralising the latter.
Real‑world use cases — NGOs, journalists, SMEs
The metadata issue is not theoretical — it translates into concrete risks. Three scenarios where DataShielder™ changes the game:
Journalists — Metadata can reveal a newsroom’s confidential contacts. With DataShielder HSM PGP, messages and attachments are encapsulated offline, then re‑encrypted by an E2EE service (ProtonMail, Signal). Sources gain protection against abusive correlations.
NGOs — Partner networks, funders, and local relays leak through timestamps and IPs. Combining DataShielder HSM NFC for identity segmentation with encrypted mail helps compartmentalise exchanges and limit espionage or intrusive surveillance.
SMEs — Decision cycles, deal flows, and working hours can be inferred from SMTP headers alone. Deploying DMARC + MTA‑STS plus DataShielder HSM reduces spoofing attacks and strengthens confidentiality of internal communications.
⮞ Summary
Journalists, NGOs, and SMEs face different exposures yet share metadata vulnerabilities. With DataShielder they gain offline encapsulation, identity segmentation, and reduced abusive correlations.
Practical guide — reduce email‑metadata exposure
Protecting email‑metadata privacy blends standards with sovereign measures. A practical checklist for companies, NGOs, and public bodies:
- Domain authentication — Enable
SPF,DKIM, andDMARC(reject) to curb spoofing and reinforce trust. - Secure transport — Deploy
MTA‑STSandTLS‑RPTto enforce TLS between mail servers. - Tracker neutralisation — Block automatic loading of remote images and use anti‑pixel filters to prevent clandestine collection.
- Retention minimisation — Limit mail‑log retention. Italy, for instance, caps employees’ email retention to a few days.
- Sovereign encapsulation — Use DataShielder HSM NFC or HSM PGP desktop to encrypt offline messages and attachments with AES‑256 CBC PGP and segmented keys before sending.
Together, this combination reduces exposure, strengthens digital sovereignty, and makes abusive metadata exploitation harder.
⮞ Summary
SPF, DKIM, DMARC, MTA‑STS, and TLS‑RPT secure transport and authentication. Anti‑pixels and minimal retention curb collection. DataShielder adds a sovereign layer: offline encapsulation and neutralisation of content metadata.
Weak signals 2025→2027 — emerging trends
Expect intensifying debate around email‑metadata privacy and digital communications. Several weak signals already point to structural shifts:
- Tighter tracker controls — New European guidance will likely restrict invisible pixels and other trackers, with stiffer penalties.
- DMARC & MTA‑STS by default — Adoption could become quasi‑mandatory, enforced by major operators and national regulators.
- Targeted & proportionate retention — Authorities are considering stricter limits on metadata retention to avoid massive, permanent surveillance.
- Mass‑correlation AI — Rising AI tools will cross‑reference logs, DNS, IPs, and public data, accelerating intrusive correlation.
- Sovereign + cloud hybrid — A mixed model combining offline encapsulation (DataShielder) with cloud E2EE may become the standard for sensitive organisations.
Bottom line: mastering metadata will be a strategic priority between 2025 and 2027 for EU sovereignty and cybersecurity.
⮞ Summary
By 2027: tougher tracker rules, default DMARC/MTA‑STS, tighter retention, more powerful AI correlation, and a sovereign‑cloud hybrid. Metadata is becoming a strategic battleground.
FAQ — common questions on email metadata
From, To, Date), Received headers, IP addresses, and timestamps. To reduce exposure of content metadata (subject, MIME structure), you need upstream encapsulation with DataShielder HSM.
Metadata actively exposes a precise social and technical map. It shows who communicates with whom, when, how frequently, and from which location—often via IP geolocation. By aggregating these traces, systems can build a connection graph that reveals relationships, hierarchies, and behavioral patterns. In many cases, this graph proves more powerful for profiling and surveillance than the message content itself. That’s why mastering metadata exposure is just as critical as encrypting the message body.
PGP and MTA‑STS protect content and transport respectively, without hiding routing metadata. DataShielder HSM adds offline encapsulation to reduce exposure of content metadata and improve overall email‑metadata privacy.
Strategic outlook — digital sovereignty & communications
Mastering email metadata and related traces goes beyond technical cybersecurity. It enables a sovereign doctrine that aligns privacy protection, regulatory compliance, and resilience against hybrid threats.
In the coming years, convergence between end‑to‑end encryption, offline encapsulation, and decentralised infrastructure will redefine the balance between security and efficiency. A key perspective will be EU‑level standards on metadata retention — integrating judicial needs with individual protection. As mass‑correlation AI rises, sovereign hardware like DataShielder™ will be vital to restore strategic symmetry between citizens, businesses, and institutions.
Longer term, the goal is hybrid resilience that combines local solutions (offline HSM, segmented compartments) with encrypted cloud services, ensuring continuity even under geopolitical or technological stress.
This column explored email metadata and the sovereign countermeasures designed to neutralise its exploitation. Looking ahead, we will examine how emerging quantum networks reshape encryption paradigms, how dynamic pseudonymisation standards evolve under regulatory pressure, and how algorithmic sovereignty redefines mass‑correlation capabilities. These topics form the next frontier in digital resilience—and will be addressed in upcoming pieces.



































































































