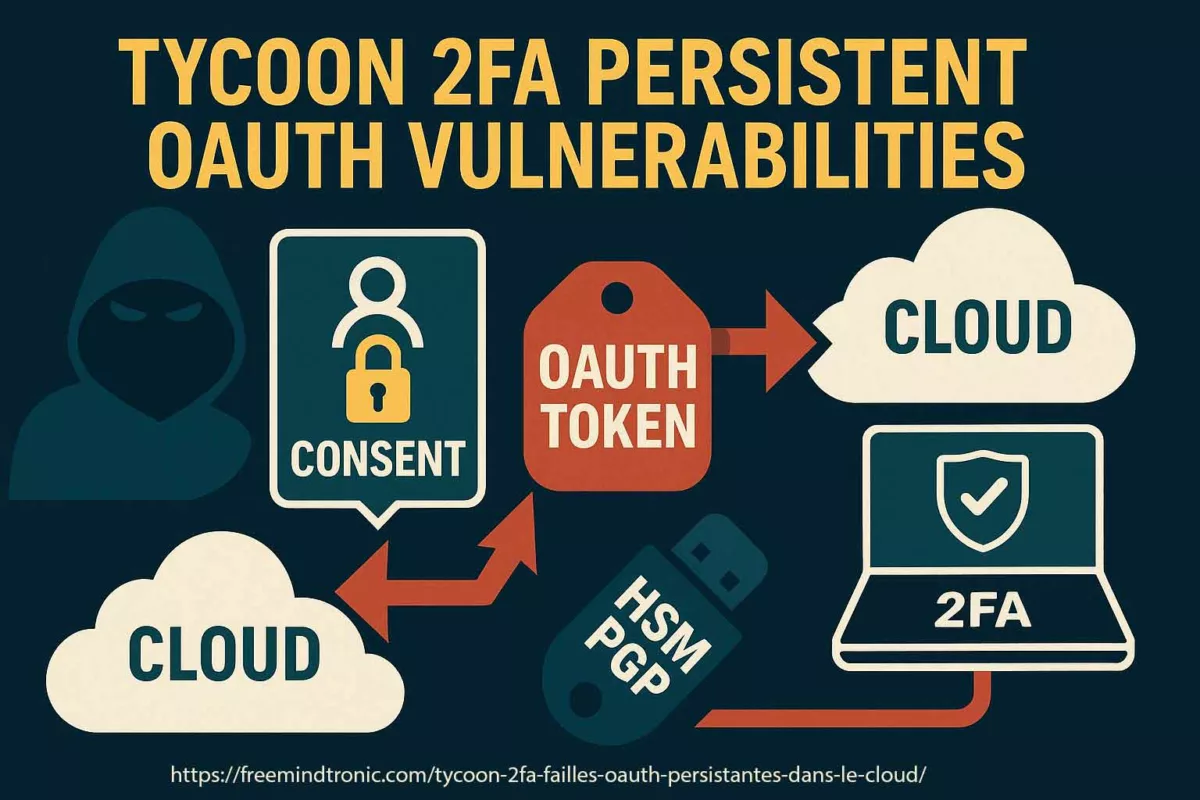
Faille OAuth persistante — Tycoon 2FA exploitée — Quand une simple autorisation devient un accès illimité au cloud. Cette chronique technique analyse comment une faille OAuth persistante permet à des acteurs malveillants de détourner des jetons OAuth légitimes pour contourner la MFA (authentification multifacteur) et maintenir un accès persistant au cloud. Elle expose comment Tycoon 2FA met en œuvre cette forme d’attaque OAuth persistante documentée dans le rapport Proofpoint 2025. Enfin, elle démontre comment la sécurité souveraine et l’architecture Zero-Cloud de PassCypher HSM PGP neutralisent, par conception, cette nouvelle génération de failles OAuth persistantes — un modèle de résilience souveraine contre les abus d’autorisation.
Résumé express — analyse technique Tycoon 2FA et failles OAuth persistantes
Ce premier résumé présente les fondements de la nouvelle menace identifiée par Proofpoint dans son rapport du 21 octobre 2025 : les applications OAuth malveillantes. Elles transforment un simple clic sur « Autoriser » en vecteur d’accès persistant, invisible et légitime, capable de survivre à tout changement de mot de passe ou réinitialisation MFA. Elles transforment un simple clic sur « Autoriser » en vecteur d’accès persistant — une persistance post-consentement invisible, capable de survivre à toute réinitialisation MFA.
⚙ Principe d’exploitation
L’utilisateur clique sur “Autoriser” → le jeton est créé + → une phase dite de *persistance post-consentement* s’installe, → l’accès est enregistré côté fournisseur cloud.
L’attaquant exploite ce jeton pour interagir avec les données (mails, fichiers, calendriers) sans jamais repasser par la MFA. Même après rotation de mot de passe, l’accès reste ouvert car le jeton est considéré comme légitime.
Pourquoi c’est grave
Contrairement à une compromission technique classique, cette attaque repose sur une faille d’intention.
Le cloud ne distingue pas l’autorisation légitime d’une autorisation piégée.
La persistance devient alors comportementale — et donc invisible aux SIEM, aux journaux d’accès et aux outils EDR.
Réponse souveraine
Une architecture conceptuelle Zero Cloud comme PassCypher HSM PGP élimine la persistance OAuth à la racine :
- Pas de jetons ni sessions stockées côté cloud
- TOTP conditionné à l’URL et validé en environnement local
- Suppression automatique des cookies de session après chaque usage
- Authentification par geste physique NFC, hors canal réseau
Le résultat : aucun point d’entrée réutilisable par un jeton OAuth compromis.
Paramètres de lecture
Temps de lecture résumé express : ≈ 4 minutes
Temps de lecture résumé avancé : ≈ 6 minutes
Temps de lecture chronique complète : ≈ 38 minutes
Dernière mise à jour : 2025-10-22
Niveau de complexité : Avancé / Cybersécurité cloud & identités
Densité technique : ≈ 79 %
Langues disponibles : FR · EN
Spécificité : Analyse technique souveraine — OAuth, MFA, jetons d’accès, PassCypher HSM PGP
Ordre de lecture : Résumé → Vecteurs → Défense → Souveraineté
Accessibilité : Optimisé lecteurs d’écran – ancres & résumés inclus
Type éditorial : Chronique technique – Digital Security
Niveau de criticité : ⚠ Critique — 8 / 10 — exploitation active observée sur Microsoft 365 / Google Workspace
Auteur : Jacques Gascuel, inventeur et fondateur de Freemindtronic Andorra.
⮞ En résuméPassCypher HSM PGP intègre plusieurs technologies souveraines qui neutralisent les failles OAuth persistantes par conception. Ces briques cryptologiques assurent une gestion locale, segmentée et contextuelle des secrets, sans dépendance cloud ni serveur.
- EviPass HSM PGP — Gestionnaire de mots de passe et secrets segmentés, stockés dans un conteneur chiffré AES-256 CBC, inexportable et hors cloud.
- EviOTP HSM PGP — Générateur local de codes TOTP/HOTP à partir de phrases secrètes inexportables, avec validation sandbox URL avant toute injection.
- EviBITB — Technologie anti-Browser-in-the-Phishing (BitP), qui détruit automatiquement les iframes de redirection malveillante.
- Fonctionnement de PassCypher HSM PGP — Explication détaillée de l’architecture souveraine : segmentation des clés, sandbox URL, chiffrement PGP, purge mémoire, fonctionnement offline.
Résumé avancé — Tycoon 2FA failles oauth persistantes
Ce résumé avancé se lit en ≈ 6 minutes. Il détaille la mécanique d’abus des applications OAuth (consentement → jeton → persistance), le rôle de Tycoon 2FA (AiTM/PhaaS) et la réponse souveraine PassCypher HSM PGP (Zero-Cloud + contrôle comportemental).
⚙ Chaîne d’attaque Tycoon 2FA / OAuth persistante (opérationnelle)
1) Phishing de marque ⟶ invite OAuth falsifiée (SharePoint/DocuSign/Adobe) ↪
2) Clic « Autoriser » ⟶ jeton OAuth valide (scopes API) ⇢
3) Session déjà active ⟶ pas de TOTP redemandé ↦
4) Accès persistant ⟶ exfiltration mails/fichiers/calendriers ↻ (jusqu’à révocation manuelle)
Contournement TOTP dans les attaques OAuth persistantes
| Scénario | TOTP requis | Jeton OAuth | Vecteur actif |
|---|---|---|---|
| Session inactive | ✅ Oui (via AiTM) | ✅ Obtenu | ✅ Oui |
| Session active | ❌ Non | ✅ Obtenu | ✅ Oui |
Exemple terrain — Tycoon 2FA et abus d’autorisations persistantes (AiTM / PhaaS)
Tycoon 2FA orchestre des pages proxifiées (AiTM) ⤴ intercepte les prompts MFA ⤵ et enchaîne vers des autorisations OAuth qui paraissent légitimes. Résultat : jeton valide + persistance + faible détection (activité “autorisée” côté console).
Cartographie synthétique des risques connexes
| Vecteur | Portée | Mitigation prioritaire |
|---|---|---|
| Tycoon 2FA (App OAuth) | M365 / Google Workspace | Admin-consent only · Audit OAuth · HSM local |
| Impersonation OAuth (endpoints) | SaaS / Multi-tenant | Validation redirect_uri · Blocage scopes à risque |
| Vol de jeton (API) | APIs / Intégrations | Révocation proactive · Rotation · HSM |
| BitP / iframe hijack | Navigateurs | Anti-BitP · Iframe-kill · TOTP conditionné |
Doctrinal insight
- Résumé express — analyse technique Tycoon 2FA et failles OAuth persistantes
- ⚙ Principe d’exploitation
- Pourquoi c’est grave
- Réponse souveraine
- Résumé avancé — Tycoon 2FA failles oauth persistantes
- ⚙ Chaîne d’attaque Tycoon 2FA / OAuth persistante
- Contournement TOTP (résumé avancé)
- Exemple terrain — Tycoon 2FA (AiTM / PhaaS)
- Cartographie synthétique des risques connexes
- Doctrinal insight
- Chronique complète — Tycoon 2FA et failles OAuth persistantes
- Fonctionnement de l’attaque Tycoon 2FA — légitimité et persistance OAuth
- Étapes opérationnelles (schéma textuel)
- Contournement du TOTP dans les failles OAuth persistantes Tycoon 2FA
- Exemple d’exploitation Tycoon 2FA : faille OAuth persistante en action
- Vers une immunité souveraine : l’exemple PassCypher HSM PGP
- Tableau comparatif — Tycoon 2FA failles OAuth persistantes et MFA
- Pour aller plus loin : autres articles sur les failles OAuth et MFA
- Implications réglementaires des failles OAuth persistantes (Tycoon 2FA)
- Checklist de résilience pour les DSI et RSSI
- Corrélation comportementale : détecter les failles OAuth persistantes en pratique
- Statistiques d’impact
- Suppression automatique des cookies de session : une stratégie rendue viable par PassCypher
- Pourquoi cette approche protège contre cette faille et bien d’autres
- Signaux faibles
- Ce que nous n’avons pas abordé volontairement
- Vision stratégique
- Cas d’usage souverain — PassCypher HSM PGP (Freemindtronic)
- Architecture (schéma conceptuel)
- Clarification technique — HSM NFC vs HSM PGP
- Ce que nous avons trouvé insuffisant dans les médias
- Bibliothèque technique — Tycoon 2FA & failles OAuth persistantes
- FAQ express — sécurité OAuth et Tycoon 2FA failles OAuth persistantes
- Glossaire technique — Tycoon 2FA failles OAuth persistantes dans le cloud
Les chroniques ci-dessus ↑ appartiennent à la rubrique Digital Security. Elles explorent les failles cloud, les vecteurs d’accès persistants et les contre-mesures souveraines développées par Freemindtronic.
Chronique complète — Tycoon 2FA et failles OAuth persistantes
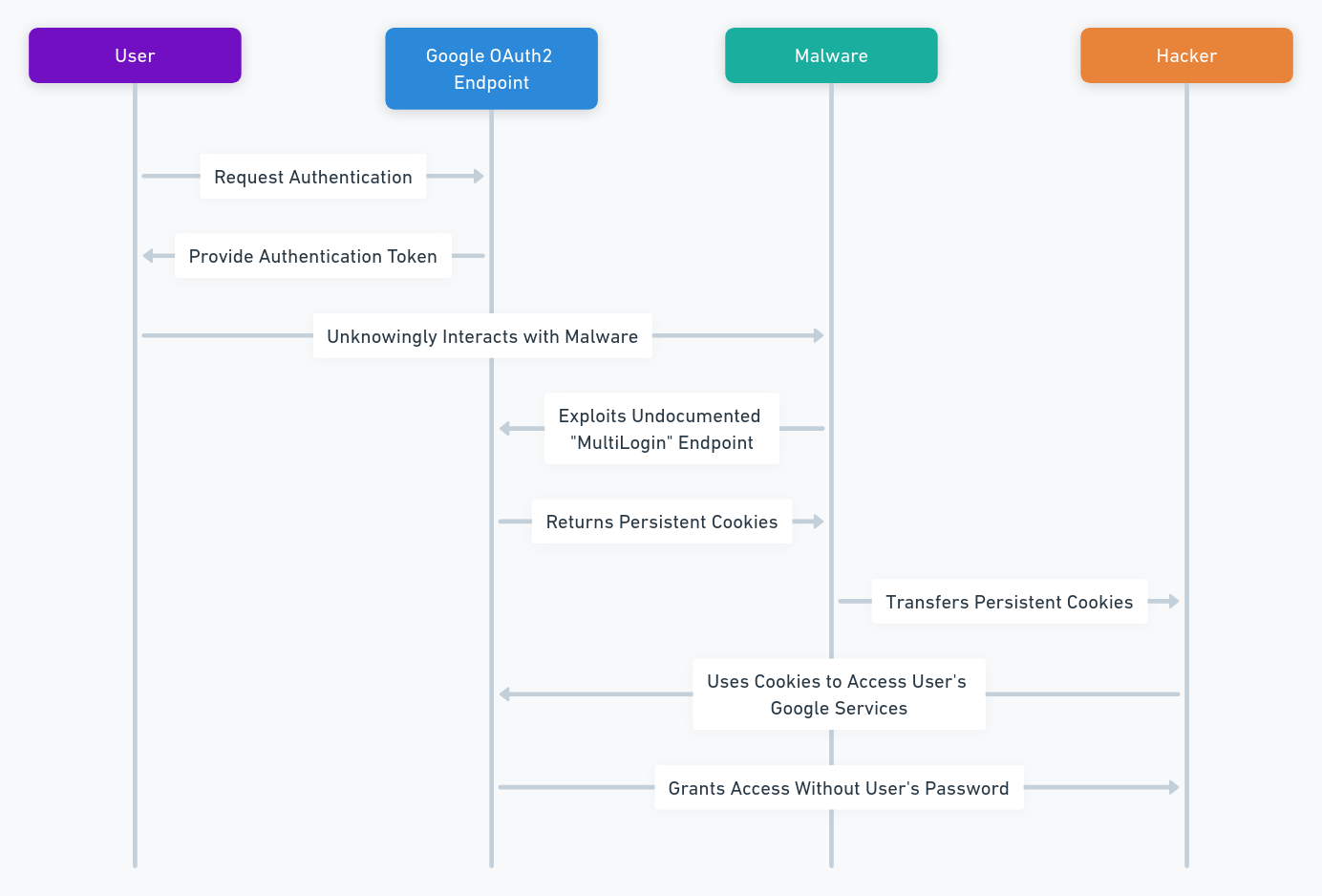
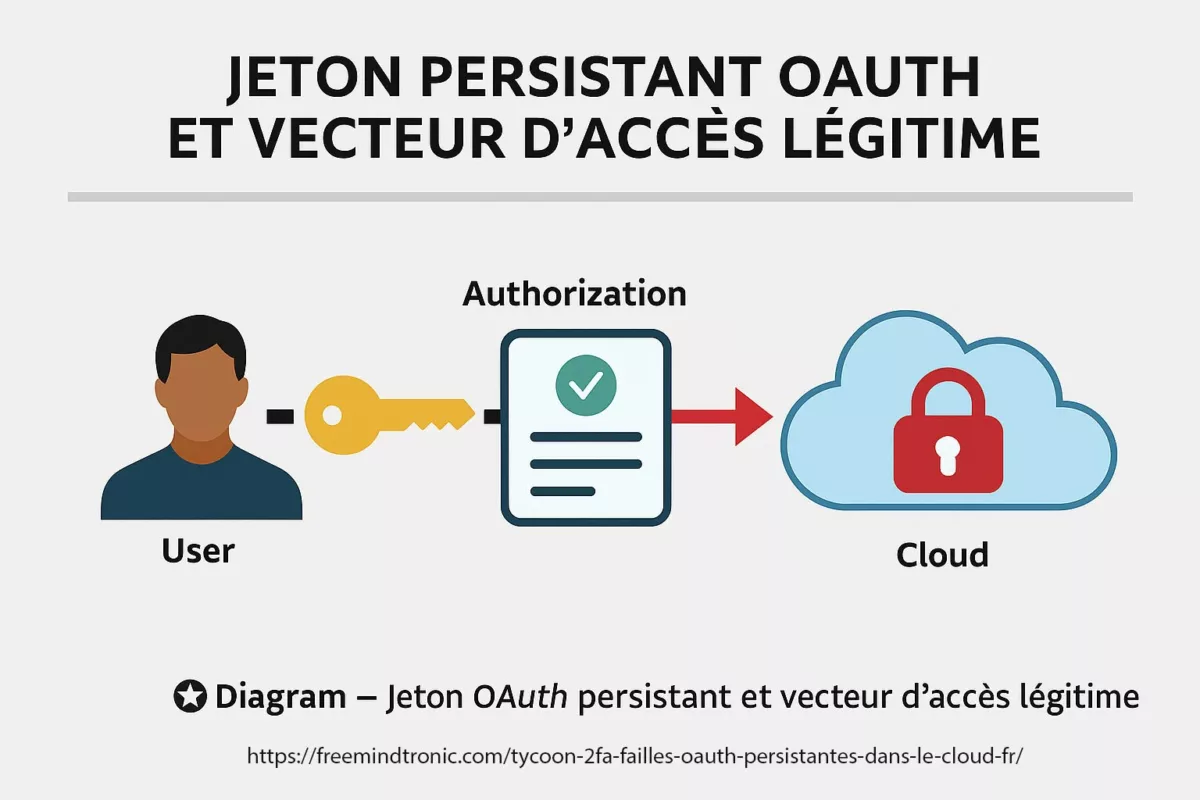
Proofpoint identifie un schéma d’abus centré sur les applications OAuth : légitimes ou imitées, elles obtiennent — via le consentement de l’utilisateur — des jetons d’accès qui permettent un accès persistant aux environnements cloud, sans dépendre des identifiants ni de la MFA. Le vecteur est comportemental : le simple clic sur « Autoriser » devient l’acte d’intrusion.
Le 21 octobre 2025, Proofpoint publie une analyse détaillée montrant comment ces applications sont instrumentalisées pour pénétrer et maintenir un accès dans Microsoft 365, Google Workspace ou Slack. Les jetons d’accès ainsi obtenus survivent aux rotations de mots de passe et aux politiques MFA, tant qu’ils ne sont pas révoqués manuellement. Le résultat est un accès « légitime » exploitable, qui se traduit par une chaîne d’attaque : persistance ↦ exploitation ↦ exfiltration.
Fonctionnement de l’attaque Tycoon 2FA — légitimité et persistance OAuth
L’attaque combine phishing (ou usurpation d’app), consent exploitation et stockage/usage de jetons. La chaîne : phishing → consentement OAuth → jeton valide → maintien de l’accès. L’ordre d’intervention utilisateur rend la tactique difficile à détecter.
Étapes opérationnelles (schéma textuel)
1. ⇢ L’attaquant prépare une application OAuth ou falsifie une invite d’autorisation (brand spoofing). ↪
2. ⇢ La victime clique sur « Autoriser » — le fournisseur délivre un jeton OAuth valide (scope limité ou étendu). ↪
3. ⇢ L’attaquant stocke et utilise le jeton pour accéder aux API (mail, drive, contacts) sans repasser par MFA. ↪
4. ⇢ Le jeton reste actif jusqu’à révocation manuelle — la fenêtre d’accès peut durer des jours à des mois. ↻
Dans de nombreux cas observés, l’interface d’administration ne signale rien d’anormal : l’activité apparaît comme « autorisée » par l’utilisateur. Par conséquent, les SIEM / EDR traditionnels manquent souvent l’indicateur initial, car la compromission n’est pas une exploitation de vulnérabilité logicielle classique mais un abus du flux d’autorisation.
Contournement du TOTP dans les failles OAuth persistantes Tycoon 2FA
Le TOTP n’est pas « cassé » cryptographiquement. Il est contourné par le contexte de session : si l’utilisateur est déjà authentifié, l’invite OAuth ne déclenche pas un second facteur, permettant l’émission d’un jeton sans TOTP. ➜ Le contournement est donc contextuel et dépend de l’état de session.
⤴ Scénarios clés :
- Session inactive → AitM / interception → TOTP requis → possible mais exploitable. ➜ (moins courant mais possible)
- Session active → aucune réauthentification TOTP → jeton accordé sans MFA → faille effective. ↦
Exemple d’exploitation Tycoon 2FA : faille OAuth persistante en action
Tycoon 2FA est un Phishing-as-a-Service (PhaaS) de type Adversary-in-the-Middle (AiTM), apparu en 2023 et utilisé massivement pour intercepter l’authentification multifacteur (MFA) et inciter les victimes à accorder des applications OAuth malveillantes. Actif depuis août 2023, ce service fournit aux opérateurs des pages et des flux AiTM capables d’arrêter ou de rediriger les invites MFA, d’afficher des fenêtres OAuth falsifiées et d’extraire en temps réel les jetons et sessions. Les analyses publiques documentent ses domaines, ses modèles de phishing et ses techniques d’évasion. Les campagnes récentes révèlent une focalisation sur Microsoft 365 et Gmail, rendant les environnements SaaS particulièrement vulnérables.
Vers une immunité souveraine : l’exemple PassCypher HSM PGP
Principes techniques appliqués (⇒ implémentation PassCypher) :
- ↪ Aucune clé privée ni jeton stocké côté cloud — tout est dans le HSM local (NFC/HSM PGP).
- ↪ TOTP / signature conditionnée à l’URL cible et validée dans un environnement confiné (anti-BitP, detection proxys AiTM).
- ↪ Auto-destruction des iframes de redirection OAuth et filtrage des redirections non vérifiées (↩ iframe kill).
- ↪ Suppression automatique des cookies/session terminaux après usage pour éviter toute résurgence de session (↻ purge session).
Le modèle réduit la surface d’attaque en rendant physiquement impossible l’usage d’un jeton volé hors du terminal HSM. (Cas d’usage & architecture détaillés en fin de chronique.)
Tableau comparatif — Tycoon 2FA failles OAuth persistantes et MFA
| Faille / attaque | Vecteur | MFA contournée | Persistance | Défense efficace |
|---|---|---|---|---|
| Tycoon 2FA | AiTM / App OAuth | ✅ Oui | ✅ Élevée | Audit OAuth, HSM local, blocage consentement utilisateur |
| OAuth App impersonation | Endpoint spoofing | ✅ Oui | ✅ Moyenne–Élevée | Politiques admin consent, revocation proactive |
| Token theft (API) | Jeton exposé | ⚠ Partiel | ✅ Variable | Rotation, revocation, HSM |
| BitP/iframe hijack | Proxy + iframe | ✅ Oui | ✅ Élevée | Anti-BitP, iframe kill, TOTP conditionné |
Pour aller plus loin : autres articles sur les failles OAuth et MFA
- Authentification multifacteur : anatomie, OTP, risques
Analyse typologique des niveaux d’authentification (0FA à MFA), avec un focus sur les failles comportementales OAuth et les vecteurs d’interception liés aux jetons d’accès. Ce dossier fondateur expose la base doctrinale de la souveraineté numérique appliquée à la MFA. - Google OAuth2 security flaw — How to protect yourself from hackers
Étude d’une faille OAuth2 exploitée pour contourner la 2FA sur les comptes Google. L’article met en lumière les protections souveraines intégrées à PassCypher HSM PGP pour neutraliser ces abus par conception hors cloud. - APT29 Exploits App Passwords to Bypass 2FA
Chronique sur les tactiques d’APT29 pour contourner la MFA via des jetons OAuth et des mots de passe d’application. Elle illustre les limites des systèmes cloud face à des attaques étatiques ciblées. - .NET DevExpress Framework UI Security for Web Apps 2025
Article technique sur l’intégration sécurisée d’OAuth2, MFA et Zero Trust dans les interfaces web. Il complète la réflexion sur les architectures souveraines applicables aux environnements cloud. - Rubrique Digital Security
Accédez à l’ensemble des chroniques Freemindtronic sur les menaces cloud, les détournements OAuth, et les innovations cryptologiques souveraines telles que PassCypher et DataShielder.
Implications réglementaires des failles OAuth persistantes (Tycoon 2FA)
Points pratiques RGPD / NIS2 — OAuth persistante & Tycoon 2FA :
- RGPD : accès non autorisé → notification & responsabilité si mesures techniques/organisationnelles insuffisantes.
- NIS2 : obligation de traçabilité et de gestion des accès, politiques de révocation et d’audit.
- Impact contractuel : clauses SOC/ISO/SLAs pouvant imposer révocation et preuve d’investigation.
Checklist de résilience pour les DSI et RSSI
| Action | Objectif | Urgence |
|---|---|---|
| Auditer les applications OAuth autorisées | Identifier accès persistants | 🔴 Immédiat |
| Activer Admin Consent Only | Bloquer consentements utilisateurs | 🔴 Immédiat |
| Déployer alertes SIEM sur grants/consents | Détection précoce | 🟠 Haut |
| Scripts de révocation proactive | Réduire fenêtre d’exposition | 🔴 Haut |
| Former utilisateurs sur « Autoriser = risque » | Réduire clics de phishing | 🟡 Moyen |
| Adopter HSM local / Zero-Cloud pour accès critiques | Éliminer persistance | 🟢 Stratégique |
Corrélation comportementale : détecter les failles OAuth persistantes en pratique
- ↪ Absence de challenge MFA lors de l’octroi d’un jeton OAuth à haut privilège.
- ↪ App OAuth inconnue utilisant des scopes inhabituels (offline_access, Mail.ReadWrite, etc.).
- ↪ Connexion API persistante malgré la rotation du mot de passe.
- ↪ Flux d’activité “autorisée” avec absence de session interactive correspondante.
La doctrine Freemindtronic recommande de relier ces indices comportementaux à une analyse locale Zero-Cloud, ce qui permet une détection souveraine sans dépendance à une télémétrie externe.
Statistiques d’impact
- Tycoon / AiTM : plus de 1 100 domaines observés sur une période d’analyse (2023–2024). :contentReference[oaicite:13]{index=13}
- Campagnes d’usurpation OAuth signalées par Proofpoint durant 2025 (multinationales & secteurs ciblés). :contentReference[oaicite:14]{index=14}
- Durée moyenne de persistance d’un jeton non révoqué : variable (jours → mois) — dépend des politiques de révocation ; observations montrent fenêtres de plusieurs semaines dans des cas réels.
Suppression automatique des cookies de session : une stratégie rendue viable par PassCypher
Technique : configurer les terminaux pour purge automatique + authentification par geste NFC → remise à zéro de l’état de session. Effet : réduction quasi totale de la surface liée aux sessions persistantes OAuth.
Pourquoi cette approche protège contre cette faille et bien d’autres
| Mécanisme | Protection apportée | Failles neutralisées |
|---|---|---|
| TOTP conditionné à l’URL | Empêche génération hors contexte | Tycoon, BitP |
| Anti-BitP / détection proxy | Rejette proxys AiTM | AiTM Kits |
| Auto-destruction iframes | Bloque redirections invisibles | Iframe hijack |
| Purge cookies + HSM reconnection | Élimine sessions dormantes | Jetons dormants |
Signaux faibles
Au fil des derniers mois, plusieurs indices discrets mais révélateurs se sont accumulés. La multiplication des plateformes de Phishing-as-a-Service (PhaaS) en est un premier marqueur : après Tycoon 2FA, Whisper 2FA s’impose désormais parmi les acteurs dominants, confirmant l’industrialisation du modèle. Parallèlement, les kits de phishing intègrent de plus en plus de techniques anti-analyse, rendant leur détection et leur étude par les chercheurs en sécurité toujours plus complexe. Enfin, la diversification des marques usurpées, qui s’étend désormais aux secteurs industriels et non plus seulement aux géants du numérique, traduit une volonté d’élargir le spectre des victimes et d’exploiter de nouvelles verticales. Pris isolément, ces phénomènes pourraient sembler anecdotiques. Mais mis bout à bout, ils dessinent une trajectoire inquiétante : celle d’une escalade qualitative des attaques, où la sophistication technique et la variété des cibles convergent pour accroître l’impact potentiel des campagnes de phishing.
Ce que nous n’avons pas abordé volontairement
Cette chronique se concentre sur le pattern OAuth persistent access. Elle n’aborde pas en détail : exploitations supply-chain, CVE spécifiques aux bibliothèques JWT, ou mitigation réseau avancée (WAF tuning) — sujets prévus pour une note technique dédiée.
Vision stratégique
La trajectoire des menaces et des réponses possibles se dessine par étapes. À court terme, l’essor des kits Adversary-in-the-Middle (AiTM) et des plateformes de Phishing-as-a-Service ciblant les comptes SaaS impose une exigence nouvelle : automatiser la révocation des accès et renforcer la visibilité sur les consentements OAuth. À moyen terme, les organisations amorcent une transition vers des architectures hybrides, combinant HSM locaux et approches zero-cloud pour sécuriser les accès sensibles. À long terme, la maturité du secteur devrait conduire à une normalisation des pratiques : standards d’audit OAuth, journalisation obligatoire des grants, et intégration des HSM directement côté endpoints.
Dans cette perspective, Freemindtronic défend une doctrine claire : conditionner l’accès à un environnement validé localement, afin de réduire la surface d’attaque avant même la détection. Cette approche place la souveraineté et la résilience au cœur de la stratégie, en anticipant les évolutions réglementaires et techniques qui façonneront la cybersécurité de demain.
Cas d’usage souverain — PassCypher HSM PGP (Freemindtronic)
Dans le champ de la souveraineté numérique, PassCypher HSM PGP illustre une mise en œuvre concrète de résilience. Les secrets y sont isolés et chiffrés en AES‑256 CBC, grâce à des clés segmentées conservées sur un support physique sécurisé. Chaque génération de code PIN TOTP est conditionnée à l’URL d’origine, empêchant toute dérive contextuelle. En parallèle, l’outil embarqué anti‑BitP procède à la purge automatique des iframes de redirection sessionnelle, neutralisant les tentatives d’interception furtive.
Ce dispositif supprime de facto la possibilité qu’un jeton OAuth persistant soit exploité côté cloud. Il instaure une immunité comportementale totale face aux failles mises en lumière par Tycoon 2FA et autres campagnes d’abus OAuth. L’approche démontre qu’une architecture souveraine peut réduire la surface d’attaque avant même la détection, en conditionnant l’accès à une validation locale et matérielle.
Architecture (schéma conceptuel)
- Terminal utilisateur ← NFC → HSM PGP local — la clé privée TOTP, les clés segmentées et les secrets sont stockés dans un conteneur chiffré (AES-256 CBC). Ces éléments ne quittent jamais le périmètre matériel NFC du HSM et restent en permanence chiffrés dans le support physique.
- Validation de contexte (sandbox / URL d’origine) — avant toute opération, le HSM vérifie localement l’URL d’origine (sandbox URL) pour autoriser la génération du code PIN TOTP et l’auto-remplissage du champ correspondant. Toute requête OAuth ou redirection ne correspondant pas à cette URL validée est automatiquement rejetée.
- Génération locale du PIN TOTP — le HSM dérive et génère le code PIN TOTP à partir d’un seed ou d’une phrase secrète stockée chiffrée via des clés segmentées. Ce secret est inexportable : le calcul du PIN ne peut donc jamais être effectué sans HSM.
- Iframe-kill & filtrage des redirections (anti BITB) — toutes les formes de redirection via iframe sont automatiquement détruites (auto-destruction), empêchant toute capture invisible du flux d’autorisation.
- Sessions éphémères & purge automatique — Configurer le navigateur pour ne conserve aucun jeton persistant. Ainsi la session est strictement éphémère, et tous les cookies ou jetons sont purgés à la fermeture du navigateur web ou après usage explicite, réduisant ainsi la surface d’attaque.
- Confirmation matérielle — l’utilisateur valide physiquement l’opération (geste NFC ou clic sur le champ PIN). La génération du PIN TOTP n’est autorisée que si l’URL d’origine et le contexte ont été validés par le HSM, rendant tout contournement distant impossible.
Effet : le seed, la phrase secrète TOTP et les clés segmentées étant confinés et chiffrés dans le HSM, toute tentative d’exploitation d’un jeton ou d’un code volé hors du terminal échoue systématiquement. La chaîne d’attaque (consentement frauduleux → jeton OAuth → persistance post-consentement) est ainsi brisée à la source, neutralisant les Tycoon 2FA failles OAuth persistantes par conception.
Clarification technique — HSM NFC vs HSM PGP
Il est essentiel de lever une ambiguïté fréquente. Les HSM NFC de PassCypher fonctionnent exclusivement en mode sans contact : dépourvus de port USB, ils valident et exécutent les opérations cryptographiques uniquement en proximité via NFC. Leur logique repose sur une interaction instantanée et locale, garantissant que chaque action est conditionnée par la présence physique du support.
À l’inverse, l’appellation HSM PGP renvoie à des supports de stockage matériels — clés USB, cartes SD, disques durs, SSD ou même CD — qui interagissent avec l’application PassCypher NFC HSM. Ces supports servent de réceptacles pour les clés segmentées et les secrets chiffrés, tout en restant dépendants de la validation NFC pour déclencher les opérations sensibles.
Dans les deux cas, la philosophie reste identique : aucune opération cryptographique n’est autorisée sans validation locale, ce qui réduit drastiquement la surface d’attaque et instaure une barrière matérielle souveraine face aux menaces cloud :
- ↪ Containers chiffrés — les secrets (seed / phrase secrète TOTP, clés segmentées) sont stockés dans des containers chiffrés et restent chiffrés au repos. Ainsi, rien ne circule en clair hors du HSM ou du conteneur chiffré.
- ↪ Déchiffrement en mémoire volatile — le container est déchiffré uniquement en mémoire volatile, et seulement pour la durée d’usage strictement nécessaire ; ensuite, les données sensibles sont immédiatement purgées. Par conséquent, aucune clé persistante en clair n’est écrite sur le poste ou le cloud.
- ↪ Auto-remplissage contrôlé (HSM PGP) — l’auto-remplissage du champ PIN Code TOTP est une fonctionnalité prévue côté HSM PGP : en 2–3 clics l’utilisateur demande la génération du PIN, et le HSM effectue cette action seulement si la sandbox URL (origin / redirect_uri) est validée localement. Cela signifie que l’auto-saisie n’est possible que dans le contexte exact attendu, rendant toute réutilisation par un tiers impossible.
- ↪ Sans port ≠ sans intégration — noter enfin que l’absence de port physique (NFC) n’empêche pas l’intégration avec le poste de travail : la communication se fait via le canal NFC ou via le mécanisme d’interface du HSM PGP; toujours est-il que la surface d’attaque est minimale car les secrets ne quittent jamais le périmètre chiffré.
⮞ En résumé
Les containers restent chiffrés en permanence, ils ne sont déchiffrés qu’en mémoire volatile pour une durée limitée, et l’auto-remplissage TOTP n’est autorisé que si le contexte (sandbox URL) est validé par le HSM — garantissant ainsi une protection opérationnelle contre le détournement de jetons et les Tycoon 2FA failles OAuth persistantes.
Ce que nous avons trouvé insuffisant dans les médias
⮞ Ce qui manque concrètement
- Peu de médias expliquent en détail les mécanismes de persistance OAuth dans les environnements cloud.
- Les témoignages de victimes ou d’administrateurs confrontés à ces failles restent extrêmement rares.
- Absence de vulgarisation claire sur les IoCs et les moyens de détection accessibles au plus grand nombre.
⮞ Ce que nous proposons
- ✔️ Une documentation bilingue, accessible et vérifiable.
- ✔️ Des cas d’usage concrets pour les PME, collectivités et indépendants.
- ✔️ Une typologie claire des risques, des solutions et des responsabilités.
⮞ Objectif
Replacer la victime au centre du discours et offrir des outils concrets pour comprendre, détecter et réagir.
Bibliothèque technique — Tycoon 2FA & failles OAuth persistantes
- Proofpoint (2025) — Beyond Credentials: Weaponizing OAuth Applications for Persistent Cloud Access
Source primaire décrivant la campagne Tycoon 2FA et l’abus des jetons OAuth légitimes. Utilisée ici à titre documentaire. - ENISA — Cloud Security Threat Landscape 2025
Rapport officiel européen sur les menaces cloud émergentes, incluant la persistance OAuth et les risques comportementaux liés aux accès SaaS. - IETF RFC 6749 — The OAuth 2.0 Authorization Framework
Spécification officielle du protocole OAuth 2.0, référence technique sur laquelle reposent toutes les implémentations modernes. - Freemindtronic — Authentification multifacteur : anatomie, OTP, risques
Analyse technique interne sur les failles comportementales liées à l’OAuth, aux OTP et à la MFA, avec démonstration de mitigation via HSM PassCypher. - Freemindtronic — PassCypher HSM PGP
Exemple d’implémentation souveraine supprimant la persistance OAuth par conception Zero-Cloud et gestion locale des jetons.
FAQ express — sécurité OAuth et Tycoon 2FA failles OAuth persistantes
Pourquoi la MFA ne suffit-elle pas ?
Le contournement comportemental de la MFA
La MFA (Multi-Factor Authentication) protège les identifiants, mais pas les décisions de consentement. Ainsi, lorsqu’un utilisateur autorise une application OAuth malveillante, cette action est considérée comme légitime. Par conséquent, Tycoon 2FA exploite ce vecteur pour créer une faille OAuth persistante sans violer la MFA.
Un flux OAuth indépendant du facteur de vérification
Le flux OAuth ne dépend pas directement de la session MFA : il repose sur le consentement utilisateur. En d’autres termes, un simple clic sur “Autoriser” suffit à générer un jeton actif, même dans un environnement protégé par 2FA.
Comment révoquer un jeton OAuth compromis ?
Procédure de révocation manuelle
Pour supprimer une application suspecte, accédez à : Azure AD → Enterprise Applications → Permissions ou Google Security Center → Applications tierces. Ensuite, cliquez sur “Révoquer”. Cela désactive immédiatement le jeton OAuth compromis.
Vers une révocation proactive
En outre, il est conseillé d’automatiser la révocation périodique via API. Ainsi, vous empêchez la persistance indéfinie de jetons OAuth et réduisez la fenêtre d’exposition face aux Tycoon 2FA failles OAuth persistantes.
Les jetons OAuth expirent-ils automatiquement ?
Une durée de vie bien plus longue qu’attendu
Contrairement à un mot de passe, un jeton OAuth ne possède pas toujours d’expiration automatique. De nombreux fournisseurs laissent les jetons actifs jusqu’à révocation manuelle. Cela crée un risque de persistance.
La persistance comportementale des accès
Cette particularité explique pourquoi les attaques de type Tycoon 2FA sont redoutables. L’attaquant conserve un accès actif tant que l’organisation ne procède pas à une révocation explicite du jeton compromis.
PassCypher HSM PGP empêche-t-il le vol de jeton ?
Protection physique et logique du secret
Oui. PassCypher HSM PGP conserve les clés d’accès dans un HSM NFC local. Aucune donnée sensible n’est stockée ni dans le cloud ni sur le terminal. Le jeton OAuth ne peut donc pas exister hors du périmètre souverain.
Neutralisation des failles OAuth persistantes
Grâce à cette approche Zero-Cloud, les Tycoon 2FA failles OAuth persistantes deviennent inopérantes. L’accès repose sur une action physique — un geste NFC — impossible à automatiser ou détourner à distance.
Quel est le lien entre Tycoon 2FA et les attaques AiTM ?
Le rôle du proxy Attacker-in-the-Middle
Tycoon 2FA s’appuie sur des proxys Attacker-in-the-Middle pour intercepter les flux d’authentification légitimes. L’utilisateur croit se connecter à un service authentique, alors que le proxy intercepte la session et injecte un flux OAuth malveillant.
Une chaîne d’attaque automatisée
Cette automatisation rend les attaques massives. En conséquence, les kits PhaaS comme Tycoon 2FA peuvent transformer un simple clic d’utilisateur en compromission durable du cloud.
Peut-on détecter une faille OAuth persistante dans un SIEM ?
Une détection partielle et souvent trompeuse
Les logs cloud enregistrent les autorisations OAuth, mais les classent comme légitimes. Ainsi, le SIEM ne déclenche pas d’alerte. En revanche, un suivi des créations d’applications OAuth non référencées peut révéler des anomalies.
Corrélation comportementale avancée
Il est donc essentiel d’ajouter des règles de corrélation comportementale : absence de TOTP lors du consentement, permissions inhabituelles, ou activité réseau persistante. Cette approche améliore la détection proactive.
Comment limiter le risque de consentement malveillant ?
Activation du mode Admin Consent Only
Activez la politique Admin Consent Only dans vos environnements Microsoft 365 ou Google Workspace. De cette manière, seules les applications validées par un administrateur peuvent être autorisées, bloquant ainsi la plupart des scénarios Tycoon 2FA.
Renforcement par audit périodique
En complément, un audit régulier des autorisations OAuth et une éducation des utilisateurs permettent de réduire la surface d’exploitation des failles OAuth persistantes.
Qu’est-ce qu’une architecture Zero-Cloud ?
Une infrastructure sans dépendance réseau
Une architecture Zero-Cloud élimine tout stockage ou traitement sensible côté cloud. Par conséquent, un jeton OAuth volé devient inutilisable. Cette philosophie est au cœur des solutions DataShielder NFC HSM et PassCypher HSM PGP.
Une doctrine souveraine appliquée
Ce modèle renforce la souveraineté comportementale : la sécurité découle de la conception même du système, non d’un correctif ultérieur.
Quelle différence entre une faille technique et une faille comportementale ?
Une faille d’intention plutôt que de code
Une faille technique découle d’un bug logiciel. À l’inverse, une faille comportementale repose sur une action humaine légitime exploitée à mauvais escient. Tycoon 2FA illustre cette dérive : l’utilisateur agit en confiance, mais crée une persistance.
La souveraineté comportementale comme réponse
En validant localement chaque action via un HSM, on supprime la possibilité de consentement piégé. Ainsi, aucune autorisation OAuth ne peut être abusée sans validation matérielle explicite.
Comment intégrer la souveraineté comportementale dans un SI ?
La sécurité par condition
Appliquer la doctrine Freemindtronic de sécurité par condition consiste à exiger une validation physique ou locale avant chaque opération critique. Cela bloque les flux OAuth externes par conception.
Un contrôle décentralisé et vérifiable
Chaque autorisation devient un événement mesurable, validé par un dispositif HSM souverain. De plus, cette approche est compatible avec les exigences RGPD, NIS2 et DORA, garantissant ainsi une conformité native.
Comment éviter les failles OAuth persistantes ?
Pour éviter les failles OAuth persistantes, il est essentiel de :
- Ne jamais conserver de jetons OAuth au-delà de leur durée utile
- Purger automatiquement les sessions et cookies après usage
- Valider systématiquement l’URL d’origine avant toute autorisation
- Utiliser un HSM local pour générer les codes TOTP, sans dépendance cloud
- Bloquer les redirections invisibles (iframe-kill) et surveiller les flux d’autorisation
Qu’est-ce qu’un jeton OAuth persistant ?
Un jeton OAuth persistant est un jeton d’accès qui reste valide au-delà de la session initiale. Il permet à un service tiers d’accéder aux ressources d’un utilisateur sans nouvelle authentification. S’il est volé ou mal géré, il peut être utilisé comme vecteur d’attaque pour contourner la MFA et accéder illégitimement à des données sensibles.
Pourquoi PassCypher HSM PGP est-il souverain ?
PassCypher HSM PGP est souverain car :
- Il stocke les clés et secrets localement, dans un conteneur chiffré AES-256 CBC
- Il ne dépend d’aucune infrastructure cloud ou serveur externe
- Il valide le contexte (sandbox URL) avant toute opération sensible
- Il génère les codes TOTP localement, sans exportation du seed
- Il neutralise les redirections invisibles et purge les sessions automatiquement
Cette architecture garantit que l’utilisateur reste maître de ses secrets, sans exposition à des tiers.
Glossaire technique — Tycoon 2FA failles OAuth persistantes dans le cloud
OAuth
Protocole d’autorisation normalisé (RFC 6749) permettant à une application d’accéder à des ressources cloud sans exposer le mot de passe de l’utilisateur. Cependant, lorsqu’il est mal configuré, il devient un vecteur d’attaque favorisant les failles OAuth persistantes, comme celles exploitées par Tycoon 2FA.
Tycoon 2FA
Kit Phishing-as-a-Service (PhaaS) combinant des proxys Attacker-in-the-Middle (AiTM) et des flux OAuth falsifiés. Il permet ainsi de contourner la MFA, d’obtenir des jetons OAuth valides et de créer des accès persistants au cloud. Tycoon 2FA illustre la nouvelle génération d’attaques comportementales OAuth persistantes.
Faille OAuth persistante
Vulnérabilité où un jeton OAuth reste actif même après un changement de mot de passe ou une réinitialisation MFA. En outre, cette faille permet un accès prolongé et invisible. Elle démontre que la compromission peut venir du consentement légitime plutôt que d’un exploit technique.
Jeton OAuth
Jeton d’accès généré par un fournisseur (Microsoft, Google, Slack, etc.). Il accorde temporairement des droits à une application. Néanmoins, en cas d’abus, il devient une backdoor légitime — une des causes principales des Tycoon 2FA failles OAuth persistantes.
AiTM (Attacker-in-the-Middle)
Technique consistant à intercepter les échanges entre un utilisateur et un service. En particulier, Tycoon 2FA s’en sert pour voler cookies et jetons OAuth, contournant la MFA et facilitant les attaques persistantes dans le cloud.
PhaaS (Phishing-as-a-Service)
Modèle d’attaque industrialisé. En effet, il permet à tout acteur malveillant de déployer rapidement des campagnes AiTM ou OAuth persistantes. Des plateformes comme Tycoon 2FA ou EvilProxy en sont des exemples notoires.
MFA (Multi-Factor Authentication)
Méthode d’authentification utilisant plusieurs facteurs. Toutefois, elle peut être contournée lorsque la session est déjà ouverte, rendant inefficace la vérification TOTP. C’est pourquoi les attaques OAuth persistantes représentent une menace même en environnement sécurisé.
TOTP (Time-based One-Time Password)
Code à usage unique fondé sur le temps. Bien qu’il renforce la sécurité, il est vulnérable lorsqu’il est combiné à une session active. Ainsi, dans un scénario Tycoon 2FA, un jeton OAuth peut être obtenu sans que le TOTP soit redemandé.
HSM (Hardware Security Module)
Dispositif matériel protégeant les clés cryptographiques hors ligne. Chez Freemindtronic, il constitue la base d’une architecture Zero-Cloud souveraine, empêchant tout vol de jeton OAuth et neutralisant la persistance par conception.
PGP (Pretty Good Privacy)
Protocole de chiffrement et de signature utilisé dans les solutions Freemindtronic. Par conséquent, l’intégration de PGP dans les HSM NFC permet d’assurer une authentification locale inviolable, sans dépendance au cloud.
PassCypher HSM PGP
Solution souveraine de Freemindtronic qui stocke les secrets sur un HSM NFC. En outre, chaque action est validée physiquement par l’utilisateur. Ainsi, aucun jeton OAuth ne subsiste dans le cloud, éliminant de fait toute persistance.
DataShielder NFC HSM
Technologie complémentaire à PassCypher, conçue pour chiffrer et protéger les données locales. De plus, elle permet de conserver un contrôle total sur les secrets sans transmission ni stockage distant.
Souveraineté comportementale
Doctrine Freemindtronic fondée sur le principe que la sécurité ne doit pas reposer sur la détection a posteriori, mais sur la validation locale des comportements. En d’autres termes, une action non autorisée devient techniquement impossible.
Zero-Cloud Architecture
Approche qui supprime toute dépendance au cloud. Par conséquent, les attaques par jetons OAuth compromis ne peuvent s’y appliquer. Cette conception assure la résilience souveraine contre les failles OAuth persistantes.
BitP (Browser-in-the-Proxy)
Variante d’attaque où un proxy navigateur capture les sessions. Cependant, les dispositifs Freemindtronic incluent un anti-BitP matériel empêchant toute interception du flux OAuth.
Iframe hijack
Technique d’injection silencieuse d’un cadre web dans une page afin de détourner un flux OAuth. Néanmoins, le mécanisme iframe-kill intégré à PassCypher neutralise ce vecteur de manière systématique.
Admin Consent Only
Politique de sécurité Microsoft et Google imposant que seules les applications approuvées par un administrateur puissent obtenir un consentement OAuth. Ainsi, elle réduit considérablement les risques d’abus observés dans les campagnes Tycoon 2FA.
OAuth scopes
Ensemble de permissions demandées par une application OAuth. Un scope trop large augmente la surface d’exposition. Il est donc essentiel d’en limiter la portée et de vérifier leur légitimité.
Révocation proactive
Processus d’invalidation régulière des jetons OAuth afin d’éviter toute persistance. En outre, cette pratique réduit le risque de compromission comportementale et limite la durée d’exploitation d’un jeton compromis.
Zero Trust Behavioral
Extension du modèle Zero Trust appliquée aux comportements. Ainsi, chaque action est validée localement, empêchant tout usage détourné de jetons OAuth persistants ou de sessions volées.
Chronique souveraine
Format éditorial Freemindtronic associant analyse technique, doctrine de cybersécurité et souveraineté numérique. Il vise notamment à documenter des menaces telles que les Tycoon 2FA failles OAuth persistantes dans les environnements cloud modernes.