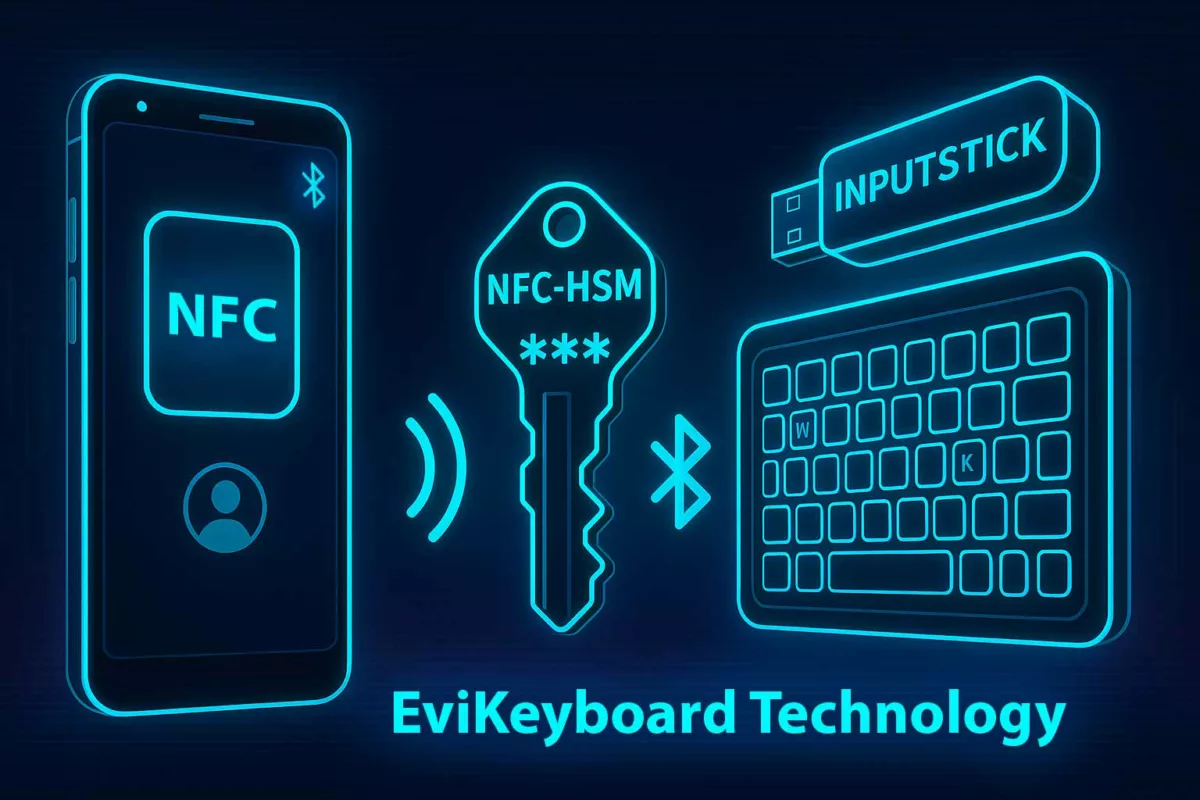
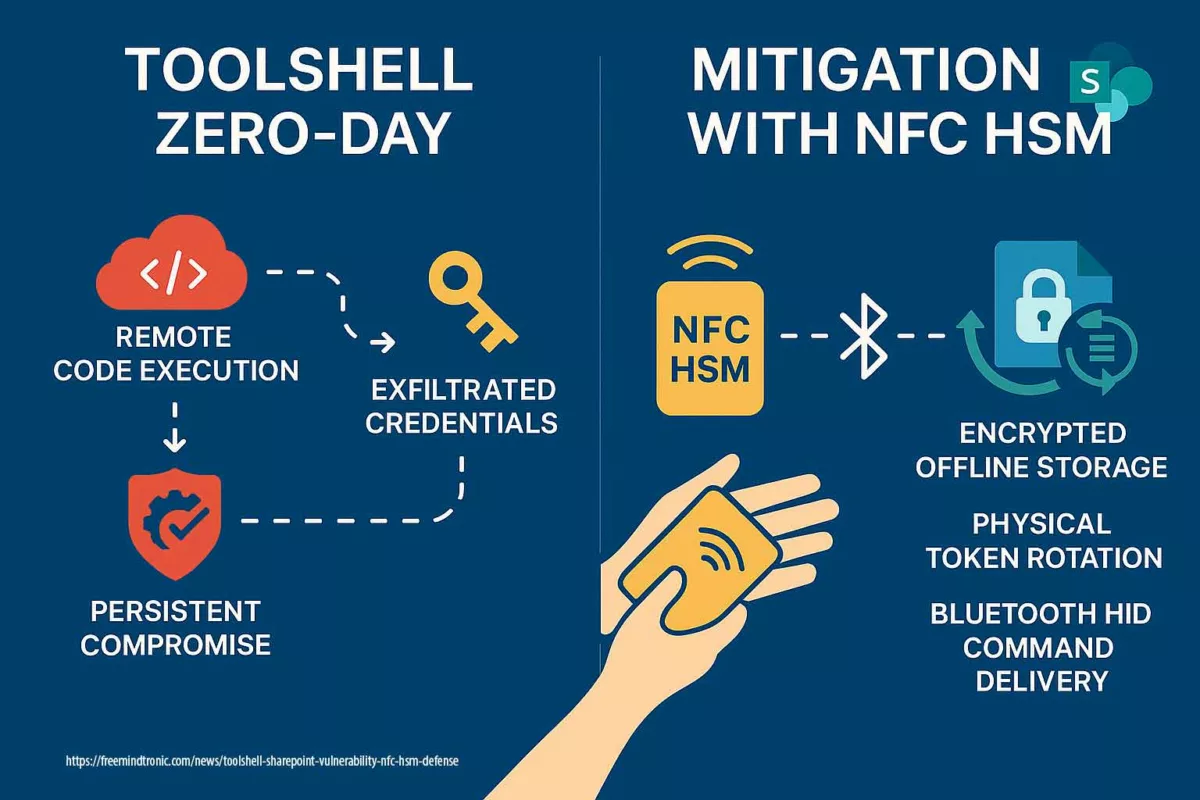
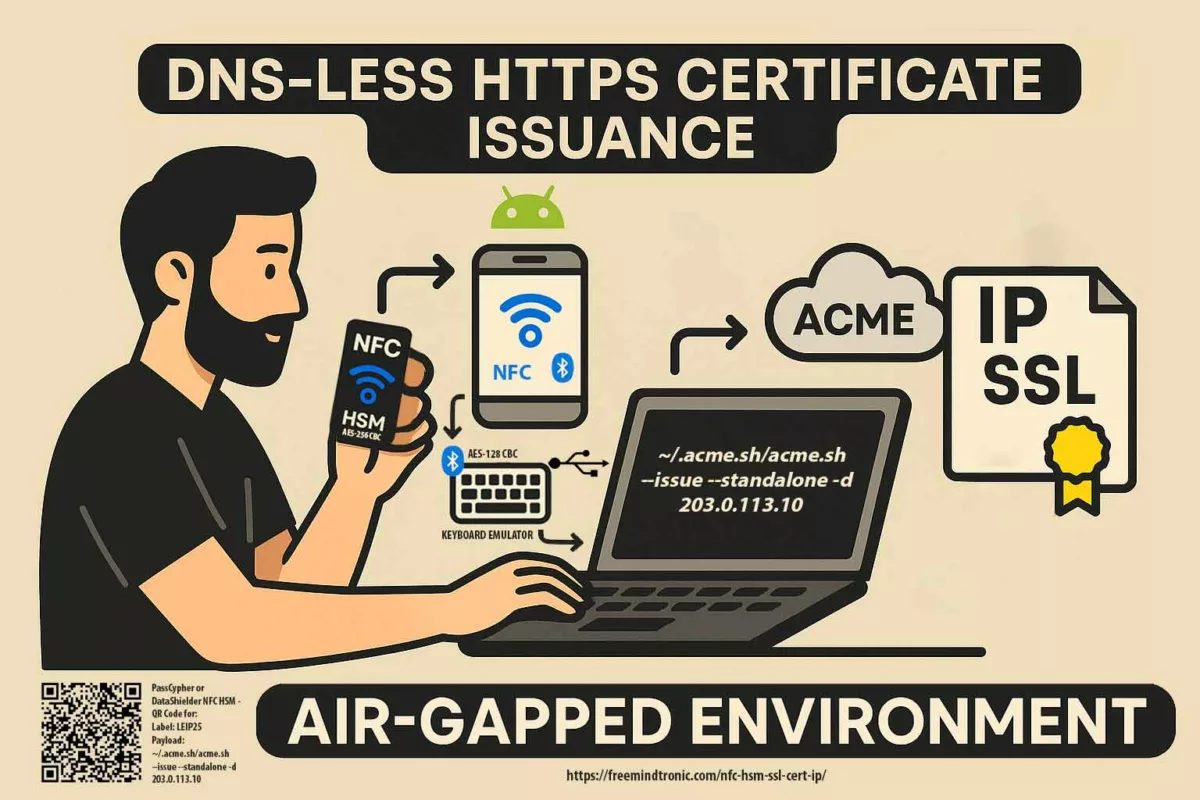
DOM extension clickjacking — a technical chronicle of DEF CON 33 demonstrations, their impact, and Zero-DOM countermeasures. See the Executive Summary below for a 4-minute overview. ☰ Quick navigation Executive Summary History of Clickjacking (2002–2025) What is DOM-Based Extension Clickjacking? Vulnerable Password Managers Technologies of Correction Used Correction Technologies — Technical & Doctrinal Analysis Systemic […]
Search Results for: PassCypher
DOM extension clickjacking — el clickjacking d’extensions basat en DOM, mitjançant iframes invisibles, manipulacions del Shadow DOM i overlays BITB — posa en risc els gestors de contrasenyes; vegeu §Passkeys phishables. Aquesta crònica resumeix les demostracions de DEF CON 33 (DOM-based extension clickjacking i passkeys phishables), el seu impacte i les contramesures Zero-DOM (PassCypher, SeedNFC, […]
Clickjacking d’extensions DOM : DEF CON 33 révèle une faille critique et les contre-mesures Zero-DOM
History of Tchap The origins of Tchap date back to 2017, when the Interministerial Directorate for Digital Affairs (DINUM, formerly DINSIC) launched an initiative to equip French public services with a sovereign instant messaging platform. The goal was clear: to eliminate reliance on foreign platforms such as WhatsApp, Signal, or Telegram, which were deemed non-compliant […]
Synchronized APT leaks erode trust in tech, alliances, and legitimacy through narrative attacks timed with geopolitical milestones.