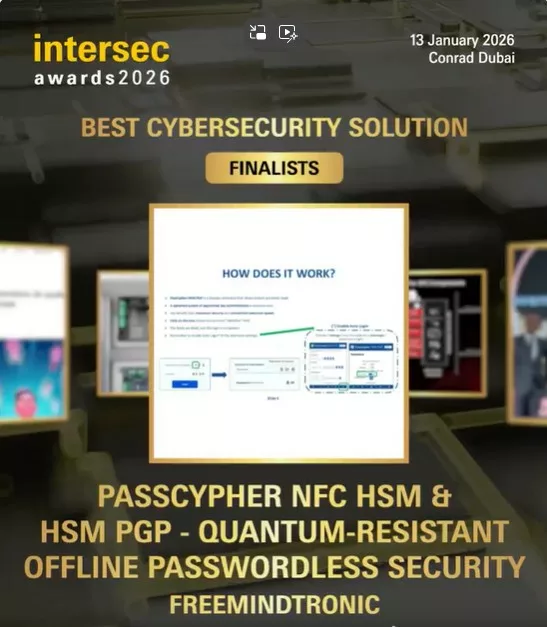
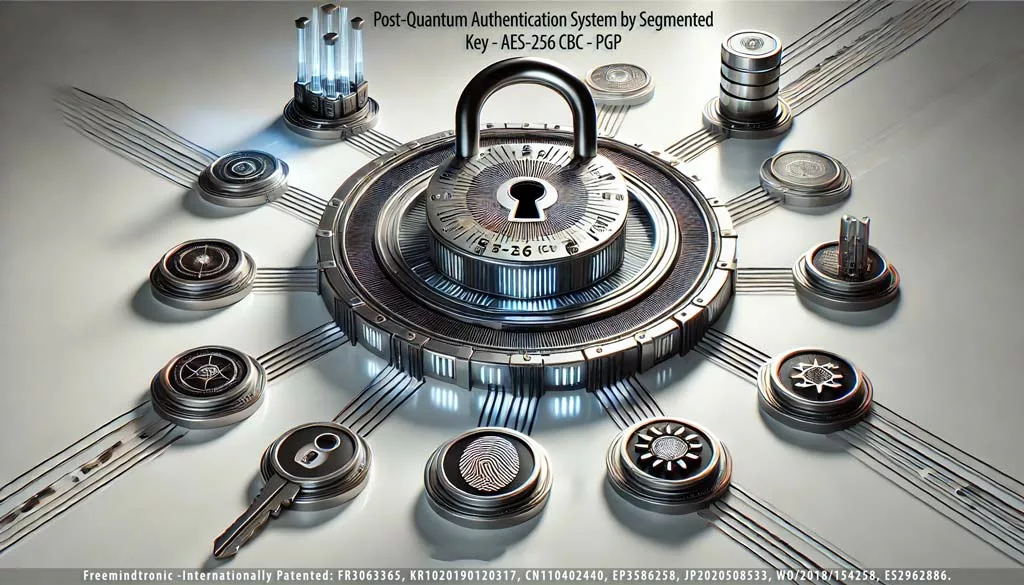
PassCypher finalista Intersec Awards 2026 — Gestor sense contrasenya resistent a l’impacte quàntic (QRPM) a la categoria de Millor Solució de Ciberseguretat fixa un nou referent en seguretat sobirana fora de línia. Finalista a l’Intersec Dubai, funciona íntegrament en memòria volàtil —sense núvol ni servidors— i protegeix identitats i secrets per disseny. Com a gestor de contrasenyes fora de línia, PassCypher ofereix criptologia local amb claus PGP segmentades i AES-256-CBC per a operacions robustes en entorns aïllats (air-gapped). A diferència d’un gestor de contrasenyes tradicional, habilita la prova de possessió sense contrasenya a través de navegadors i sistemes amb interoperabilitat universal. El reconeixement internacional queda confirmat al web oficial: llista de finalistes dels Intersec Awards 2026. Freemindtronic Andorra agraeix cordialment a l’equip d’Intersec Dubai i al seu jurat internacional pel seu reconeixement. PassCypher finalista Intersec Awards 2026.
Resum ràpid — Ecosistema sobirà fora de línia i sense contrasenya (QRPM)
Lectura ràpida (≈ 4 min): La nominació de Freemindtronic Andorra PassCypher finalista Intersec Awards 2026 — valida un ecosistema sobirà complet entre els finalistes dels Intersec Awards 2026 a la Millor Solució de Ciberseguretat al voltant de PassCypher HSM PGP i PassCypher NFC HSM. Dissenyat a partir de patents d’origen francès i pensat per executar-se íntegrament en memòria volàtil (només RAM), permet autenticació sense contrasenya sense FIDO — sense transferència, sense sincronització i sense persistència. Com a gestor sobirà fora de línia, PassCypher aplica PGP segmentat + AES-256-CBC per a seguretat sense contrasenya resistent a l’impacte quàntic, amb traduccions integrades (14 idiomes) per a ús air-gapped. Explora l’arquitectura completa al nostre resum d’gestor de contrasenyes sobirà fora de línia.
⚙ Un model sobirà en acció
PassCypher HSM PGP i PassCypher NFC HSM operen com a veritables mòduls físics de confiança. Executen totes les operacions crítiques localment — xifratge PGP, signatura, desxifratge i autenticació — sense servidor, sense núvol i sense tercers. Aquest model fora de línia i sense contrasenya es basa en la prova de possessió física i en criptologia embeguda, trencant amb enfocaments FIDO o SaaS centralitzats.
Per què PassCypher és un gestor de contrasenyes sobirà fora de línia
PassCypher HSM PGP i PassCypher NFC HSM actuen com a mòduls físics de confiança: tota la criptografia (xifratge, signatura, desxifratge i autenticació PGP) s’executa localment, sense servidor ni núvol. Aquest model sense FIDO es basa en la prova de possessió física i en criptologia embeguda, no pas en intermediaris d’identitat centralitzats.
Abast global
Aquesta distinció situa Freemindtronic Andorra entre les millors solucions de ciberseguretat del món — PassCypher finalista Intersec Awards 2026.
Aquesta distinció situa Freemindtronic Andorra entre les millors solucions de ciberseguretat del món. Reforça el seu paper pioner en protecció sobirana fora de línia i confirma la rellevància d’un model neutral, independent i interoperable — que combina enginyeria francesa, innovació andorrana i reconeixement emiratí a la fira mundial més gran de seguretat i resiliència digital.
Autenticació sense contrasenya sense FIDO — model sobirà fora de línia (QRPM)
PassCypher ofereix accés sense contrasenya sense FIDO/WebAuthn ni federació d’identitat. La validació es fa localment (prova de possessió física), completament fora de línia, sense servidors, sense núvol i sense magatzems persistents — pilar central de la doctrina Quantum-Resistant Passwordless Manager 2026.
- Prova de possessió — NFC/HID o context local; sense validadors tercers.
- Criptologia local — PGP segmentat + AES-256-CBC només en RAM (efímer).
- Interoperabilitat universal — funciona entre navegadors/sistemes sense passkeys ni sincronització.
Paràmetres de lectura
Temps de lectura del resum ràpid: ≈ 4 minuts
Temps de lectura del resum avançat: ≈ 6 minuts
Temps de lectura de la crònica completa: ≈ 35 minuts
Data de publicació: 2025-10-30
Darrera actualització: 2025-10-31
Nivell de complexitat: Expert — Criptologia i sobirania
Densitat tècnica: ≈ 79%
Idiomes disponibles: FR· CAT· EN· ES ·AR
Enfocament específic: Anàlisi sobirana — Freemindtronic Andorra, Intersec Dubai, ciberseguretat fora de línia
Ordre de lectura: Resum → Doctrina → Arquitectura → Impactes → Abast internacional
Accessibilitat: Optimitzat per a lectors de pantalla — àncores i etiquetes estructurades
Tipologia editorial: reportatge especial de premis — PassCypher finalista Intersec Awards 2026 (Millor Solució de Ciberseguretat)
Nivell d’enjoc: 8,1 / 10 — internacional, criptològic, estratègic
Sobre l’autor: Jacques Gascuel, inventor i fundador de Freemindtronic Andorra, expert en arquitectures HSM, sobirania criptogràfica i seguretat fora de línia.
Referències oficials i mitjans
Localització sobirana (fora de línia)
Tant el PassCypher HSM PGP com el PassCypher NFC HSM estan traduïts de manera nativa a més de 13 idiomes, inclòs l’àrab. Les traduccions estan embegudes en el dispositiu (sense crides a serveis de traducció en línia), garantint la confidencialitat i la disponibilitat en entorns aïllats.
☰ Navegació ràpida
- 🔝 Tornar a dalt
- Resum ràpid — Ecosistema sobirà fora de línia i sense contrasenya (QRPM)
- Resum avançat — Doctrina i abast estratègic
PassCypher finalista Intersec Awards 2026 — Millor Solució de Ciberseguretat
- Crònica — Sobirania validada a Dubai
- Context oficial — Intersec Awards 2026
- La innovació PassCypher — Sobirania, seguretat, independència
- Innovació andorrana amb arrels europees
- Primera fita històrica — Finalista “passwordless” als EAU
- Sobirania validada — Cap a un model independent
- Abast internacional — Model sobirà global
- Sobirania consolidada — Cap a un estàndard internacional
- Preguntes freqüents
Les publicacions mostrades a dalt ↑ pertanyen a la mateixa secció editorial Distincions i Premis — Seguretat Digital. Amplien l’anàlisi sobre sobirania, neutralitat andorrana i gestió de secrets fora de línia, directament connectada amb el reconeixement de PassCypher a l’Intersec Dubai.
⮞ Preàmbul — Reconeixement internacional i institucional
Freemindtronic Andorra expressa el seu agraïment sincer al jurat internacional i a Messe Frankfurt Middle East, organitzador dels Intersec Awards, per la qualitat, el rigor i l’abast global d’aquest certamen dedicat a la seguretat, la sobirania i la innovació. Atorgada a Dubai — al cor dels Emirats Àrabs Units —, aquesta distinció confirma el reconeixement d’una innovació andorrana amb arrels europees que constitueix un model d’autenticació sobirana, resistent a l’impacte quàntic i sense contrasenya fora de línia. També il·lustra el compromís compartit entre Europa i el món àrab per promoure arquitectures digitals basades en la confiança, la neutralitat i la resiliència tecnològica.
Resum avançat — Doctrina i abast estratègic de l’ecosistema sobirà fora de línia
Intersec 2026 — PassCypher finalista Intersec Awards 2026 (Millor Solució de Ciberseguretat)
L’estatus de finalista als Intersec Awards 2026 en la categoria de Millor Solució de Ciberseguretat diferencia PassCypher no només com a avenç tecnològic, sinó com una doctrina sobirana completa per a seguretat sense contrasenya resistent a l’impacte quàntic.Aquesta nominació marca una doble fita — a la nostra coneixença: (1) primera presència andorrana entre els finalistes dels Intersec Awards, i (2) primer gestor de contrasenyes “passwordless” i fora de línia seleccionat a la categoria «Best Cybersecurity Solution». Segons la llista oficial, PassCypher és un dels cinc finalistes d’aquesta categoria..
↪ Abast geopolític i doctrinal
Aquest reconeixement atorga a Andorra un nou paper: laboratori de neutralitat digital dins l’espai europeu. Freemindtronic impulsa un model d’innovació sobirana — andorrà per neutralitat, francès per herència, europeu per visió. En entrar a Millor Solució de Ciberseguretat, PassCypher simbolitza un equilibri estratègic entre independència criptològica i interoperabilitat normativa.
Seguretat només RAM per a sobirania sense contrasenya (QRPM)
↪ Una arquitectura fora de línia basada en memòria volàtil
L’ecosistema PassCypher es basa en un principi singular: totes les operacions crítiques — emmagatzematge, derivació, autenticació, gestió de claus — es fan exclusivament en memòria volàtil. No s’escriu ni es sincronitza cap dada en emmagatzematge persistent. Per disseny, aquest enfocament elimina vectors d’intercepció, espionatge i compromís postexecució, també sota amenaces quàntiques.
PGP segmentat + AES-256-CBC impulsant operacions sense contrasenya
↪ Segmentació i sobirania dels secrets
El sistema aplica segmentació dinàmica de claus que desacobla cada secret del seu context d’ús. Cada instància PassCypher actua com un micro-HSM autònom: aïlla identitats, verifica drets localment i destrueix instantàniament qualsevol dada després de l’ús. Aquest model d’esborrat per disseny contrasta amb paradigmes FIDO i SaaS, on la persistència i la delegació generen vulnerabilitats estructurals.
↪ Un reconeixement simbòlic per a la doctrina sobirana
Incloure Freemindtronic Andorra entre els finalistes 2026 eleva la sobirania tecnològica com a motor d’innovació internacional. En un panorama dominat per solucions centrades en el núvol, PassCypher demostra que la desconnexió controlada pot convertir-se en un actiu estratègic, assegurant independència regulatòria, alineació amb GDPR/NIS2 i resiliència davant interdependències industrials.
⮞ Reconeixement internacional ampliat
L’abast global de PassCypher s’estén també al domini de la seguretat de defensa. La solució serà presentada per AMG PRO a MILIPOL 2025 — estand 5T158 — com a soci oficial francès de Freemindtronic Andorra per a tecnologies de doble ús civil i militar. Aquesta presència confirma PassCypher com a solució de referència per a ciberseguretat sobirana adaptada a defensa, resiliència i indústries crítiques.
⮞ En síntesi
- Arquitectura: seguretat només RAM amb claus PGP segmentades + AES-256-CBC.
- Model: autenticació sense contrasenya sense FIDO, sense servidor, sense núvol, air-gapped.
- Posicionament: gestor de contrasenyes sobirà fora de línia per a contextos regulats, desconnectats i crítics.
- Reconeixement: finalista Intersec 2026 a la Millor Solució de Ciberseguretat — seguretat sense contrasenya resistent a l’impacte quàntic per disseny.
PassCypher finalista Intersec Awards 2026 — Crònica: sobirania validada a Dubai (passwordless fora de línia)
La selecció oficial de Freemindtronic Andorra com a PassCypher finalista Intersec 2026 a la Millor Solució de Ciberseguretat marca un punt d’inflexió. Aquesta selecció oficial marca una doble fita — a la nostra coneixença: (1) primera presència andorrana entre els finalistes dels Intersec Awards, i (2) primer gestor de contrasenyes “passwordless” i fora de línia seleccionat a la categoria «Best Cybersecurity Solution». Segons la llista oficial, PassCypher és un dels cinc finalistes d’aquesta categoria gestor de contrasenyes sobirà.
↪ Resiliència algorísmica sobirana (resistent a l’impacte quàntic per disseny)
En lloc de confiar en esquemes post-quàntics experimentals, PassCypher aporta resiliència estructural: segmentació dinàmica de claus PGP combinada amb AES-256-CBC, executada íntegrament en memòria volàtil (només RAM). Les claus es divideixen en segments independents i efímers que trenquen rutes d’explotació — incloses les alineades amb Grover o Shor. No és PQC; és un model operatiu resistent a l’impacte quàntic per disseny.
↪ Innovació i independència
La nominació valida una doctrina de resiliència mitjançant la desconnexió: protegir secrets digitals sense servidor, sense núvol, sense rastre. L’autenticació i la gestió de secrets romanen totalment autònomes — autenticació sense contrasenya sense FIDO, sense WebAuthn i sense intermediaris d’identitat — perquè cada usuari conservi el control físic de les seves claus, identitats i perímetre de confiança.
↪ Intersec Awards 2026 — l’ecosistema al focus
Curat per Messe Frankfurt Middle East, Intersec posa en relleu innovacions que equilibren rendiment, compliment i independència. La presència de Freemindtronic Andorra subratlla l’abast internacional d’una doctrina de ciberseguretat sobirana fora de línia desenvolupada en un país neutral i posicionada com a alternativa creïble als estàndards globals.
⮞ Destaquem Intersec 2026
Presència a la gala: Freemindtronic Andorra serà present a Dubai per a l’entrega dels trofeus, representada per Thomas MEUNIER.
- Esdeveniment: Intersec Awards 2026 — Conrad Dubai
- Etiqueta oficial: PassCypher finalista Intersec Awards 2026
- Categoria: Millor Solució de Ciberseguretat
- Finalista: Freemindtronic Andorra — ecosistema PassCypher
- Innovació: Gestió sobirana de secrets digitals fora de línia (només RAM, air-gapped)
- Origen: Patents d’invenció franceses amb concessions internacionals
- Arquitectura: Memòria volàtil · Segmentació de claus · Sense dependència del núvol
- Valor doctrinal: Sobirania tecnològica, neutralitat geopolítica, independència criptològica
- Validació oficial: Llista oficial de finalistes Intersec 2026
Aquesta peça examina la doctrina, els fonaments tècnics i l’abast estratègic d’aquest reconeixement — una validació institucional que demostra que les identitats digitals es poden salvaguardar sense connectivitat.
Punts clau:
- “Passwordless” sobirà amb 0 núvol / 0 servidor: prova de possessió física.
- Interoperabilitat universal (web/sistemes) sense dependència de protocols.
- Resiliència estructural via segmentació de claus + memòria volàtil (només RAM).
Celebrats a Dubai, els Intersec Awards s’han convertit, des del 2022, en un referent global en seguretat, ciberseguretat i resiliència tecnològica. La 5a edició, prevista per al 13 de gener de 2026 al Conrad Dubai, distingirà l’excel·lència en 17 categories que cobreixen ciberseguretat, seguretat contra incendis, defensa civil i protecció d’infraestructures crítiques. A la categoria Millor Solució de Ciberseguretat, només cinc finalistes han estat preseleccionats després d’un procés d’avaluació meticulós, liderat per un jurat internacional de 23 experts de cinc països — els Emirats Àrabs Units, Aràbia Saudita, el Regne Unit, Canadà i els Estats Units — que representen les institucions capdavanteres del món en seguretat, defensa civil i ciberseguretat.
Com a context, l’edició anterior — Intersec Awards 2025 — va rebre més de 1.400 propostes internacionals en 15 categories, confirmant l’abast global i la competitivitat de l’esdeveniment. Font oficial: Nota de premsa Intersec 2025 — Messe Frankfurt Middle East.
⮞ Informació oficial
- Esdeveniment: Intersec Awards 2026 — 5a edició
- Lloc: Conrad Dubai, Emirats Àrabs Units
- Data: 13 de gener de 2026
- Categoria: Millor Solució de Ciberseguretat
- Nombre de categories: 17
- Jurat: Panell internacional Intersec 2026 (23 experts)
- Finalistes: Llista oficial de finalistes
↪ Jurat internacional de prestigi
El jurat 2026 reuneix 23 experts de primer nivell de les principals institucions dels EAU, Aràbia Saudita, el Regne Unit, Canadà i els Estats Units — un reflex de la credibilitat global de l’esdeveniment i de l’equilibri entre expertesa de l’Orient Mitjà i d’Occident.
- Dubai Civil Defence — Tinent Coronel Dr. Essa Al Mutawa, Cap del Departament d’Intel·ligència Artificial
- UL Solutions — Gaith Baqer, Enginyer Regulador Sènior
- NFPA — Olga Caldonya, Directora de Desenvolupament Internacional
- IOSH (Regne Unit) — Richard Bate, President electe
- WSP Middle East — Rob Davies i Emmanuel Yetch, Directors Executius
- ASIS International — Hamad Al Mulla i Yassine Benaman, líders de seguretat sènior
↪ Sobirania algorísmica — Resistència quàntica per disseny
En lloc d’algorismes post-quàntics experimentals, PassCypher aconsegueix resistència estructural mitjançant segmentació dinàmica de claus PGP protegida amb AES-256-CBC, executada íntegrament en memòria volàtil (només RAM). Les claus es divideixen en fragments temporals i aïllats que s’autodestrueixen després de l’ús — eliminant vectors d’explotació, inclosos atacs quàntics teòrics com Grover i Shor. No és PQC en sentit acadèmic, sinó una arquitectura sobirana resistent a l’impacte quàntic per disseny.
↪ PassCypher — Primera suite HSM nativament traduïda a l’àrab
PassCypher és el primer gestor de contrasenyes i suite HSM que ofereix una interfície àrab plenament localitzada amb suport RTL (dreta-esquerra), operant completament fora de línia. Aquest disseny vincula l’enginyeria europea amb la identitat lingüística i cultural àrab, i proporciona un model únic de sobirania digital independent del núvol o de sistemes d’autenticació centralitzats.
↪ Doble fita històrica
Aquesta nominació representa una doble fita històrica:
la primera presència andorrana seleccionada com a finalista en una competició tecnològica internacional als EAU,
i — segons el nostre coneixement — el primer gestor de contrasenyes seleccionat com a
finalista als EAU a la categoria Best Cybersecurity Solution.
Aquesta distinció valida les arquitectures desconnectades com a alternatives globals creïbles als models centralitzats en el núvol.
↪ Convergència euro-emiratiana en seguretat sobirana
El reconeixement 2026 posa en relleu l’emergència d’un diàleg euro-emiratià sobre sobirania digital i arquitectures de resiliència per disseny. PassCypher actua com a pont entre la neutralitat andorrana, l’enginyeria francesa, l’expertesa institucional britànica i el reconeixement de patents transatlàntic — amb tecnologies patentades al Regne Unit, als Estats Units i a la Unió Europea. Aquesta convergència exemplifica com interoperabilitat, confiança i innovació sobirana poden coexistir dins una visió internacional compartida de la seguretat. Amb aquest marc institucional i tecnològic establert, la secció següent explora l’arquitectura sobirana i la doctrina criptogràfica que han merescut el reconeixement internacional d’Intersec Dubai.
PassCypher finalista Intersec Awards 2026 — innovació “passwordless” sobirana fora de línia (QRPM)
En un mercat dominat per stacks al núvol i passkeys FIDO, l’ecosistema PassCypher es posiciona com una alternativa sobirana i disruptiva. Desenvolupat per Freemindtronic Andorra sobre patents d’origen francès, se sustenta en una base criptogràfica executada en memòria volàtil (només RAM) amb AES-256-CBC i segmentació de claus PGP — un enfocament alineat amb l’estratègia Quantum-Resistant Passwordless Manager 2026.
↪ Dos pilars d’un sol ecosistema sobirà
- PassCypher HSM PGP: gestor sobirà de secrets i contrasenyes per a escriptori, totalment fora de línia. Tota la criptografia s’executa a RAM per a autenticació sense contrasenya i fluxos air-gapped.
- PassCypher NFC HSM: variant de maquinari portàtil per a Android amb NFC, que converteix qualsevol suport NFC en un mòdul físic de confiança per a autenticació universal sense contrasenya.
Interoperables per disseny, ambdós funcionen sense servidor, sense núvol, sense sincronització i sense confiança en tercers. Secrets, claus i identitats romanen locals, aïllats i temporals — nucli de la ciberseguretat sobirana a Andorra i territoris catalanoparlants.
↪ Localització sobirana — traduccions embegudes (fora de línia)
- Suport nadiu per a més de 13 idiomes, inclòs l’àrab (UI/UX i ajuda).
- Traduccions embegudes: sense crides de xarxa, sense telemetria, sense API externes.
- Compatibilitat RTL completa per a l’àrab, amb tipografia coherent i maquetació segura fora de línia.
↪ Autenticació sobirana sense contrasenya — sense FIDO, sense núvol
A diferència dels models FIDO vinculats a validadors centralitzats o claus biomètriques, PassCypher opera 100% de forma independent i fora de línia. L’autenticació es basa en la prova de possessió física i comprovacions criptològiques locals — sense serveis externs, sense API de núvol, sense cookies persistents. El resultat: un gestor de contrasenyes sense contrasenya, compatible amb tots els principals sistemes operatius, navegadors i plataformes web, i amb NFC d’Android per a ús sense contacte — interoperabilitat universal sense bloqueig per protocols.
⮞ Etiquetat com a “seguretat fora de línia sense contrasenya resistent a l’impacte quàntic”
En el procés oficial d’Intersec, PassCypher es descriu com a seguretat fora de línia sense contrasenya resistent a l’impacte quàntic. Mitjançant AES-256-CBC i una arquitectura PGP multicapa amb claus segmentades, cada fragment és inútil de manera aïllada — interrompent rutes d’explotació algorísmica (p. ex., Grover, Shor). Això no és un esquema PQC; és resistència estructural via fragmentació lògica i efimeritat controlada. Consulta la crònica de la distinció.
↪ Un model d’independència i confiança digital
La ciberseguretat sense núvol pot superar dissenys centralitzats quan l’autonomia del maquinari, la criptologia local i la no-persistència són primers principis. PassCypher restableix la confiança digital al seu fonament — seguretat per disseny — i ho demostra en contextos civils, industrials i de defensa com a gestor de contrasenyes sobirà fora de línia. Amb la base tècnica establerta, la següent secció aborda els orígens territorials i doctrinals que han modelat aquest finalista a Millor Solució de Ciberseguretat.
Innovació andorrana — Arrels europees d’un gestor sobirà sense contrasenya resistent a l’impacte quàntic
Després d’exposar la base tècnica de l’ecosistema PassCypher, cal cartografiar-ne l’abast institucional i territorial. Més enllà de l’enginyeria, l’estatus de finalista a la Millor Solució de Ciberseguretat 2026 confirma una innovació andorrana — d’herència europea i governança neutral — avui visible a l’escenari mundial de la ciberseguretat sobirana.
↪ Entre arrels franceses i neutralitat andorrana
Nascut a Andorra el 2016 i construït sobre patents d’origen francès concedides internacionalment, PassCypher es dissenya, es desenvolupa i es produeix a Andorra. El seu NFC HSM es fabrica a Andorra i França amb Groupe Syselec, soci industrial de llarga trajectòria. Aquesta identitat dual — llinatge franco-andorrà amb governança sobirana andorrana — ofereix un model concret de cooperació industrial europea. Aquesta posició permet a Freemindtronic actuar com a actor neutral, independent de blocs polítics però alineat amb una visió compartida d’innovació de confiança.
↪ Per què la neutralitat importa en un gestor sobirà
La neutralitat històrica d’Andorra i la seva geografia entre França i Espanya creen condicions idònies per a tecnologies de confiança i sobirania. L’enfocament de gestor de contrasenyes a Andorra — només RAM, sense núvol, sense contrasenya — pot adoptar-se sota marcs reguladors diversos sense dependències d’infraestructures estrangeres.
↪ Reconeixement amb abast simbòlic i estratègic
La selecció als Intersec Awards 2026 assenyala un enfocament europeu independent que triomfa en una arena internacional exigent, els Emirats Àrabs Units — centre global d’innovació en seguretat. Demostra que territoris europeus neutrals com Andorra poden equilibrar blocs tecnològics dominants mentre impulsen seguretat sense contrasenya resistent a l’impacte quàntic.
↪ Un pont entre dues visions de sobirania
Europa promou sobirania digital via GDPR, NIS2 i DORA; els EAU impulsen ciberseguretat d’estat centrada en resiliència i autonomia. El reconeixement a Dubai enllaça aquestes visions i prova que la innovació sobirana neutral pot unir el compliment europeu i les necessitats estratègiques emiratianes amb arquitectures sense núvol i interoperables.
↪ Doctrina andorrana de sobirania digital
Freemindtronic Andorra encarna la sobirania digital neutral: innovació al capdavant, independència reguladora i interoperabilitat universal. Aquesta doctrina sustenta l’adopció de PassCypher en sectors públics i privats com a gestor de contrasenyes sobirà que opera fora de línia per disseny.
⮞ Transició
Aquest reconeixement institucional prepara el següent capítol: la primera fita històrica d’un gestor passwordless preseleccionat en una competició tecnològica dels EAU — ancorant PassCypher en la història dels grans premis internacionals de ciberseguretat.
Primera fita històrica — Finalista “passwordless” als EAU (fora de línia, sobirà)
PassCypher NFC HSM & HSM PGP, desenvolupats per Freemindtronic Andorra, són — segons el nostre coneixement — els primers gestors de contrasenyes (de qualsevol tipus: núvol, SaaS, biomètric, codi obert, sobirà, fora de línia) seleccionats com a finalistes en una competició tecnològica als EAU. Aquesta fita segueix esdeveniments clau com GITEX Technology Week (2005), Dubai Future Accelerators (2015) i els Intersec Awards (des de 2022), cap dels quals havia preseleccionat abans un gestor de contrasenyes fins a PassCypher el 2026. Valida una aproximació de quantum-resistant passwordless manager 2026 arrelada en sobirania i disseny fora de línia.
Contrast — Històric de competicions tecnològiques als EAU
| Competició | Any de creació | Abast | Gestors de contrasenyes finalistes |
|---|---|---|---|
| GITEX Global / Cybersecurity Awards | 2005 | Tecnologia global, IA, núvol, ciutats intel·ligents | ❌ Cap |
| Dubai Future Accelerators | 2015 | Start-ups disruptives | ❌ Cap |
| UAE Cybersecurity Council Challenges | 2019 | Resiliència nacional | ❌ Cap |
| Dubai Cyber Index | 2020 | Avaluació del sector públic | ❌ Cap |
| Intersec Awards | 2022 | Seguretat, ciberseguretat, innovació | ✅ PassCypher (2026) |
Millor gestor sense contrasenya resistent a l’impacte quàntic 2026 — posicionament i casos d’ús
Reconeixent-se a Intersec Dubai, PassCypher es posiciona com el millor gestor “passwordless” resistent a l’impacte quàntic 2026 per a organitzacions que necessiten operacions sobiranes i sense núvol. L’stack combina validació fora de línia (prova de possessió) amb criptologia només a RAM i claus segmentades. Per a context de mercat, consulta la nostra instantània del millor gestor de contrasenyes 2026.
- Entorns regulats i air-gapped (defensa, energia, salut, finances, diplomàcia).
- Desplegaments sense núvol on la residència i minimització de dades són obligatòries.
- Interoperabilitat entre navegadors/sistemes sense dependències FIDO/WebAuthn.
En resum:
Pel nostre coneixement, cap solució al núvol, SaaS, biomètrica, de codi obert o sobirana en aquesta categoria havia arribat a finalista als EAU abans de PassCypher. Aquest reconeixement reforça la posició d’Andorra a l’ecosistema de ciberseguretat dels EAU i subratlla la rellevància d’un gestor de contrasenyes sense contrasenya pensat per a ús sobirà i fora de línia.
PassCypher finalista Intersec Awards 2026 — tipologia doctrinal: allò que aquest gestor sobirà fora de línia no és
Abans de detallar la sobirania validada, convé situar PassCypher per contrast. La matriu següent clarifica la ruptura doctrinal.
| Model | S’aplica a PassCypher? | Per què |
|---|---|---|
| Gestor al núvol | ❌ | Sense transferència ni sincronització; gestor sobirà fora de línia. |
| FIDO / Passkeys | ❌ | Prova de possessió local; sense federació d’identitat. |
| Codi obert | ❌ | Arquitectura patentada; doctrina sobirana i cadena de qualitat. |
| SaaS / SSO | ❌ | Sense backend ni delegació; sense núvol per disseny. |
| Bòveda local | ❌ | Sense persistència; només RAM efímera. |
| Zero Trust de xarxa | ✔️ Complementari | Doctrina Zero-DOM: fora de xarxa, identitats segmentades. |
Aquest marc destaca PassCypher com a fora de línia, sobirà i universalment interoperable — no és un gestor de contrasenyes convencional lligat al núvol o a FIDO, sinó una arquitectura de quantum-resistant passwordless manager 2026. Consulta la crònica de la distinció.
PassCypher finalista Intersec Awards 2026 — sobirania validada cap a un model independent “passwordless” resistent a l’impacte quàntic
El reconeixement a Freemindtronic Andorra a Intersec confirma més que un èxit de producte: valida una arquitectura sobirana fora de línia dissenyada per a la independència.
↪ Validació institucional de la doctrina sobirana
La preselecció a Millor Solució de Ciberseguretat avala una filosofia de seguretat desconnectada i autònoma: protegir secrets digitals sense núvol, dependències ni delegació, alineant-se amb marcs globals (GDPR/NIS2/ISO-27001).
↪ Resposta a dependències sistèmiques
Mentre moltes solucions assumeixen connectivitat permanent, les operacions en memòria volàtil i la no-persistència de PassCypher eliminen riscos de centralització. La confiança passa de “confiar en un proveïdor” a “no dependre de ningú”.
↪ Cap a un estàndard global
Combinant sobirania, compatibilitat universal i resiliència criptogràfica segmentada, PassCypher marca un camí cap a una norma internacional de seguretat “passwordless” resistent a l’impacte quàntic aplicable a defensa, energia, salut, finances i diplomàcia.
Mitjançant el reconeixement de Dubai, Intersec assenyala un nou paradigma en seguretat digital — on un gestor de contrasenyes sobirà fora de línia pot esdevenir referent de Millor Solució de Ciberseguretat.
⮞ Transició — Cap a la consolidació doctrinal
La secció següent detalla els fonaments criptològics i les arquitectures d’aquest model — memòria volàtil, segmentació dinàmica i disseny resilient a l’impacte quàntic — enllaçant doctrina amb pràctica desplegable.
Abast internacional — cap a un model global de “passwordless” sobirà fora de línia
Allò que va començar com una nominació es converteix ara en la confirmació internacional d’una doctrina europea neutral nascuda a Andorra: una aproximació de quantum-resistant passwordless manager 2026 que redefineix com es pot dissenyar, governar i certificar la seguretat digital com a fora de línia, sobirana i interoperable.
↪ Reconeixement que traspassa fronteres
La distinció als Intersec Awards 2026 a Dubai arriba quan la sobirania digital esdevé prioritat global. Com a finalista de Millor Solució de Ciberseguretat, Freemindtronic Andorra posiciona PassCypher com a referent transcontinental entre Europa i l’Orient Mitjà — un pont entre la tradició europea de confiança i compliment i la resiliència i neutralitat operativa emiratianes. Entre aquests pols, PassCypher actua com a pont d’interoperabilitat segura.
↪ Aparador global per a ciberseguretat desconnectada
Dins el cercle selecte de proveïdors que ofereixen ciberseguretat de confiança fora de línia, Freemindtronic Andorra dona resposta a governs, indústries i defensa que cerquen protecció independent del núvol. El resultat: un camí concret on protecció de dades, neutralitat geopolítica i interoperabilitat tècnica coexisteixen — reforçant la capacitat europea de resiliència digital.
↪ Un pas cap a un estàndard sobirà global
Amb volatilitat de dades (només RAM) i no-centralització com a valors per defecte, PassCypher dibuixa un estàndard sobirà universal per a identitat i gestió de secrets. Organismes transregionals — europeus, àrabs, asiàtics — poden alinear-se al voltant d’un model que reconcilia seguretat tècnica i independència reguladora. El reconeixement d’Intersec actua com un accelerador de convergència normativa entre doctrines nacionals i estàndards emergents.
↪ De la distinció a la difusió
Més enllà de les institucions, l’impuls es tradueix en cooperació industrial i aliances de confiança entre estats, empreses i centres de recerca. La presència en esdeveniments de referència com MILIPOL 2025 i Intersec Dubai reforça el doble focus — civil i militar — i la demanda creixent d’un gestor sobirà fora de línia que és passwordless sense FIDO.
↪ Trajectòria europea d’abast global
El reconeixement d’Andorra a través de Freemindtronic mostra com un microestat neutral pot influir en els equilibris de seguretat globals. A mesura que les aliances es polaritzen, la innovació sobirana neutral ofereix una alternativa d’unitat: una doctrina passwordless resistent a l’impacte quàntic que eleva la independència sense sacrificar la interoperabilitat.
⮞ Transició — cap a la consolidació final
Aquest abast internacional no és honorífic: és la validació global d’un model independent, resilient i sobirà. La secció següent consolida la doctrina de PassCypher i el seu paper en la definició d’un estàndard global de confiança digital.
Sobirania consolidada — cap a un estàndard internacional de confiança “passwordless” sobirana
Per tancar aquest capítol, l’estatus de PassCypher finalista Intersec 2026 és més que honorífic: assenyala la validació global d’un model de ciberseguretat sobirana basat en desconnexió controlada, operacions en memòria volàtil (RAM) i criptologia segmentada. Aquesta trajectòria s’alinea de manera natural amb entorns reguladors diversos — des dels marcs de la UE (GDPR, NIS2, DORA) fins a referències dels EAU (PDPL, DESC, IAS) — i afavoreix la propietat sobirana dels secrets al centre d’una aproximació quantum-resistant passwordless manager 2026.
↪ Compatibilitat reguladora global per disseny
El model de gestor de contrasenyes sobirà fora de línia (sense núvol, sense servidors, prova de possessió) dona suport a objectius de compliment clau en grans jurisdiccions mitjançant minimització de moviment i persistència de dades:
- Regne Unit: UK GDPR, Data Protection Act 2018 i NCSC CAF.
- Estats Units: NIST SP 800-53 / 800-171 i Zero Trust SP 800-207; suport a salvaguardes sectorials (HIPAA/GLBA).
- Xina: principis de CSL, DSL i PIPL.
- Japó: requisits d’APPI (finalitat, minimització, mitigació) afavorits per operació només RAM.
- Corea del Sud: PIPA (consentiment, minimització, mesures tècniques/organitzatives) amb ús air-gapped i validació local.
- Índia: DPDP 2023 (licitud, minimització, seguretat per disseny) amb passwordless sense FIDO i criptologia en dispositiu.
Nota:
PassCypher no reclama certificació automàtica; facilita assolir objectius (segregació de funcions, mínim privilegi, reducció d’impacte) mantenint els secrets locals, aïllats i efímers.
↪ Consolidar una doctrina universal
La doctrina de ciberseguretat sobirana passa del manifest a la pràctica. PassCypher HSM PGP i PassCypher NFC HSM demostren que autonomia criptogràfica, interoperabilitat global i resiliència a amenaces emergents poden coexistir en un gestor sobirà fora de línia. L’interès transregional — Europa, el GCC, el Regne Unit, els EUA i Àsia — confirma una premissa simple: la ciberseguretat fiable exigeix sobirania digital.
↪ Multilingüe per disseny (embegut, fora de línia)
Per donar suport a desplegaments globals i operacions air-gapped, PassCypher incorpora més de 13 idiomes embeguts (inclòs català per a Andorra, Catalunya, Illes Balears, País Valencià i Catalunya Nord). La IU i l’ajuda són totalment fora de línia (sense API externes).
↪ Catalitzador d’estandardització internacional
El reconeixement a Dubai actua com a accelerador d’estandardització i obre el camí a criteris on seguretat desconnectada i protecció d’identitat segmentada siguin propietats certificables.
↪ Sobirania andorrana com a palanca d’equilibri global
La neutralitat i l’agilitat reguladora d’Andorra ofereixen un laboratori d’innovació sobirana que equilibra grans blocs tecnològics.
↪ Un horitzó compartit: confiança, neutralitat, independència
- confiança — verificació local i prova de possessió;
- neutralitat — sense intermediaris ni dependència de proveïdor;
- independència — eliminació de dependències de núvol/servidor.
“PassCypher no és un gestor de contrasenyes. És un estat criptogràfic sobirà, resilient i autònom, reconegut com a finalista dels Intersec Awards 2026.” — Freemindtronic Andorra, Dubai · 13 de gener de 2026
⮞ Senyals febles identificats
- Patró: demanda creixent de passwordless sense núvol en infraestructures crítiques.
- Vector: convergència GDPR/NIS2/DORA amb doctrines sobiranes fora de xarxa; imperatius dels EAU PDPL/DESC/IAS; èmfasi regulador UK/US/Àsia en minimització i zero trust.
- Tendència: fòrums de defensa i sector públic (p. ex., Milipol novembre 2025, esdeveniments GCC) explorant arquitectures només RAM.
⮞ Cas d’ús sobirà | Resiliència amb Freemindtronic
En aquest context, PassCypher HSM PGP i PassCypher NFC HSM neutralitzen:
- Validació local per prova de possessió (NFC/HID), sense servidors ni núvol.
- Desxifratge efímer en memòria volàtil (només RAM), zero persistència.
- Segmentació PGP dinàmica amb aïllament contextual dels secrets.
FAQ — Gestor sense contrasenya resistent a l’impacte quàntic i ciberseguretat sobirana
Resposta breu
Sí. PassCypher valida l’accés per prova de possessió amb cap servidor, cap núvol i cap WebAuthn.
Per què importa
Com que tot s’executa en memòria volàtil (només RAM), es manté fora de línia, universal i interoperable entre navegadors i sistemes. Dona resposta directa a consultes com autenticació sense FIDO i gestor sobirà fora de línia dins el posicionament PassCypher finalista Intersec 2026.
En una frase
FIDO es basa en WebAuthn i federació d’identitat; PassCypher és sense FIDO, sense servidor i sense núvol, amb PGP segmentat + AES-256-CBC íntegrament a RAM.
Context i recursos
La federació centralitza la confiança i amplia la superfície d’atac. PassCypher la substitueix per criptologia local i material efímer (derivar → usar → destruir). Consulta:
Segrest d’API WebAuthn,
Clickjacking d’extensions DOM (DEF CON 33).
Objectius: seguretat “passwordless” resistent a l’impacte quàntic, gestor sense contrasenya 2026.
Resposta curta
Sí. L’àrab (RTL) i més de 13 idiomes estan embeguts; les traduccions funcionen totalment fora de línia (air-gapped), sense API externes.
Idiomes inclosos
العربية, English, Français, Español, Català, Deutsch, 日本語, 한국어, 简体中文, हिन्दी, Italiano, Português, Română, Русский, Українська — alineats amb el long-tail de gestor sobirà per a desplegaments multiregió (Andorra, Catalunya, Illes Balears, País Valencià, Catalunya Nord, l’Alguer).
Essencials
Sense núvol, sense servidors, sense persistència: els secrets es creen, s’usen i es destrueixen a RAM.
Com funciona
El patró de gestor només RAM i la segmentació de claus eliminen camins d’exfiltració comuns (bases de dades, sincronització, extensions). Nucli de la nostra doctrina gestor sobirà fora de línia.
Ambdós en un sol stack
És un gestor de contrasenyes sobirà fora de línia que també habilita accés sense contrasenya sense FIDO.
Com encaixa
Com a gestor, els secrets només viuen en memòria volàtil. Com a “passwordless”, prova la possessió física entre navegadors i sistemes. Cobreix intencions com millor gestor 2026 fora de línia i gestor sense núvol per a empreses.
Perspectiva operativa
Sí. És sense núvol i sense servidor per disseny, compatible amb escriptori, web i NFC d’Android.
Notes de risc
Sense broker d’identitat, sense tenant SaaS, sense capa d’extensions — coherent amb Zero Trust (verificació local, privilegi mínim). Lectures relacionades:
Debilitats persistents d’OAuth/2FA,
Ús indegut d’App Passwords per APT29.
Què pots esperar
PassCypher no certifica automàticament; facilita resultats (minimització, privilegi mínim, reducció d’impacte) mantenint els secrets locals, aïllats i efímers.
On encaixa
Alineat amb objectius de política a la UE GDPR/NIS2/DORA, EAU PDPL/DESC/IAS, UK (UK GDPR/DPA 2018/NCSC CAF), EUA (NIST SP 800-53/171, SP 800-207 Zero Trust, àmbits HIPAA/GLBA), CN (CSL/DSL/PIPL), JP (APPI), KR (PIPA), IN (DPDP).
Explicació plana
Aquí “resistent a l’impacte quàntic” vol dir resistència estructural — segmentació i efimeritat en RAM —, no pas nous algorismes PQC.
Elecció de disseny
No substituïm primitives; limitem utilitat i vida del material perquè els fragments aïllats no tinguin valor. S’alinea amb el long-tail de seguretat sense contrasenya resistent a l’impacte quàntic.
Instantània
Evita les capes més atacades: sense WebAuthn, sense extensions de navegador, sense persistència OAuth, sense app-passwords guardades.
Per aprofundir
Lectures recomanades:
Segrest d’API WebAuthn,
DOM extension clickjacking,
Vulnerabilitat persistent d’OAuth (2FA),
APT29 i app-passwords.
Motiu en breu
Per demostrar que la seguretat sobirana, fora de línia i sense contrasenya (només RAM + segmentació) escala globalment — sense núvol ni federació.
Intenció dels premis
Respon a cerques com millor solució de ciberseguretat 2026 i millor gestor de contrasenyes 2026 fora de línia, i reforça el posicionament PassCypher finalista Intersec 2026 amb abast multilingüe (incloent àrab) per a audiències de Dubai i del GCC.
⮞ Aprofundeix — Solucions PassCypher arreu del món
Descobreix on avaluar el nostre gestor de contrasenyes sobirà fora de línia i l’autenticació sense contrasenya sense FIDO a l’EMEA. Aquests enllaços cobreixen opcions de maquinari, aplicacions només RAM i accessoris d’interoperabilitat universal.
AMG PRO (París, França)
KUBB Secure de Bleu Jour (Tolosa, França)
- PassCypher HSM PGP — gestor “passwordless” (només RAM, fora de línia)
- Clau USB Crystal PassCypher — suport extraïble segur
- Emulador de teclat Bluetooth — pont universal K/M per a NFC HSM
- KUBB Secure Mini — NFC HSM “fanless” per a “passwordless” sobirà
Fullsecure Andorra
- PassCypher HSM PGP — gestor de secrets fora de línia (memòria volàtil)
- PassCypher NFC HSM Lite — autenticació NFC sense contrasenya
- PassCypher NFC HSM Master — identitat i gestió de secrets avançades
- Emulador de teclat Bluetooth — compatibilitat universal (ús air-gapped)
Consell: per a enllaçat intern i captura d’intenció de cerca, referencia àncores com /passcypher/offline-password-manager/ i /passcypher/best-password-manager-2026/ quan escaigui.
⮞ Visió estratègica
El reconeixement de Freemindtronic Andorra a Intersec 2026 subratlla que la sobirania és un valor tecnològic universal. En habilitar operacions sense núvol i sense servidor amb autenticació sense contrasenya sense FIDO, l’enfocament Quantum-Resistant Passwordless Manager 2026 traça un camí pragmàtic cap a un estàndard global de confiança digital — nascut a Andorra, reconegut a Dubai, rellevant a l’EMEA, les Amèriques i l’Àsia-Pacífic.