Geneva International Exhibition of Inventions 2021: Celebrating Inventors’ Achievements
In March 2021, the Geneva International Exhibition of Inventions achieved a historic milestone by transitioning to a virtual format, transcending geographical boundaries and bringing together inventors from 25 countries. This global event served as a platform for groundbreaking solutions across various domains. A significant highlight was Andorra’s exceptional performance at the 2021 Geneva Inventions Expo, marking its inaugural appearance in the competition’s 49-year history.
Andorra’s Historic Triumph at the 2021 Geneva Inventions Expo
In a momentous turn of events, Jacques Gascuel, a French expatriate in Andorra, clinched the prestigious Gold Medal in the C category at the Exposition Internationale des Inventions de Genève, making history for Andorra.
Redefining Data Security: The EviCypher HSM Innovation
Gascuel’s invention, the EviCypher HSM, represents a groundbreaking leap in data security and confidentiality. This innovation facilitates secure data exchange while preserving utmost anonymity. At its core lies a state-of-the-art NFC HSM (Near Field Communication Hardware Security Module) enabling the creation, exchange, and secure utilization of encryption keys.
Andorra’s Historic Win 2021 Geneva Inventions Expo: Why It Matters
Andorra’s participation in the Geneva International Exhibition of Inventions holds immense historical importance, considering it had never taken part in this prestigious event since its inception in 1972. This competition stands as the largest annual gathering dedicated solely to invention, featuring participation from over 45 countries. It enjoys substantial support from the Swiss Federal Government, the State of Geneva, the city of Geneva, the World Intellectual Property Organization (WIPO), and the International Federation of Inventors’ Associations (IFIA).
Invention vs. Innovation: What’s the Difference and Why Does It Matter?
Invention and innovation are two different but complementary concepts in technology. According to the OECD, innovation is the implementation of a new or significantly improved product or process, a new marketing method, or a new organizational method. Innovation can be of product, process, marketing, or organization. Innovation aims to create added value, meet user needs, or solve social problems. According to WIPO, invention is a technical solution to a technical problem. An invention can be a product or a process and must be new, inventive, and industrially applicable to be patentable. Invention aims to make an original contribution to the state of the art, exploit scientific opportunities, or overcome technical limitations.
Therefore, it is essential to distinguish between invention and innovation. While innovation often refers to the improvement or refinement of existing concepts or products, invention involves the creation of entirely new solutions or technologies. To participate in such a prestigious event as the Geneva International Exhibition of Inventions, inventors must generally hold a patent or have a revolutionary concept protected by a patent application.
The Different Categories of Inventions at the Geneva International Exhibition of Inventions 2021
Inventions at the 2021 Geneva International Exhibition are classified into various categories based on their nature and application. Common categories include:
| Class |
Category Description |
| A |
Mechanics, Engines, Machinery, Tools, Industrial Processes, Metallurgy |
| B |
Clocks and Watches, Jewelry, Machinery, Tools |
| C |
Computer Sciences, Software, Electronics, Electricity, Communication Methods |
| D |
Building, Architecture, Civil Engineering, Construction, Materials, Woodwork |
| E |
Sanitation, Ventilation, Heating |
| F |
Security, Rescue, Alarm |
| G |
Ironmongery, Do-It-Yourself |
| H |
Furnishing, Interior Architecture |
| I |
Domestic Science, Restaurant Equipment |
| J |
Commercial, Industrial, and Office Equipment |
| K |
Agriculture, Horticulture, Gardening |
| L |
Clothing, Textiles, Machines, and Accessories |
| M |
Medicine, Surgery, Hygiene, Orthopedics, Material for the Handicapped |
| N |
Optics, Photography, Cinematography |
| O |
Teaching Methods and Materials, Musical Instruments, Art Materials |
| P |
Transport, Motor Vehicles, Ships, Aviation, Accessories |
| Q |
Foodstuffs, Drinks, Cosmetics, Paramedical, Health, Hygiene |
| R |
Sport, Leisure |
| S |
Practical Novelties, Presents |
| T |
Publicity, Printing, Packaging |
| U |
Games, Toys |
| V |
Protection of the Environment, Energy |
These diverse classes encompass a wide spectrum of inventions, from cutting-edge technology to practical everyday solutions. Each class represents a unique field where inventors contribute their creativity and expertise.
As we explore the full list of participants, we’ll witness the remarkable impact of human ingenuity across these categories.
The Diversity of Participating Countries at the Geneva International Exhibition of Inventions 2021
A total of 352 inventors from 25 countries participated in this global celebration of innovation and creativity. Here’s a breakdown of participating countries and their contributions:
| Country |
Number of Participants |
| Andorra |
1 |
| Argentina |
1 |
| Canada |
1 |
| China |
97 |
| Egypt |
10 |
| France |
5 |
| Hong Kong |
32 |
| Iran |
18 |
| Malaysia |
15 |
| Peru |
1 |
| Poland |
10 |
| Qatar |
4 |
| Romania |
2 |
| Russia |
5 |
| Saudi Arabia |
27 |
| Senegal |
1 |
| South Korea |
43 |
| Spain |
3 |
| Switzerland |
3 |
| Taipei (Chinese Taipei) |
21 |
| Thailand |
46 |
| Ukraine |
3 |
| United States of America (USA) |
1 |
| Vietnam |
1 |
| Yemen |
1 |
The Best Inventions from the 77 Class C Participants at the Geneva International Exhibition of Inventions 2021
They classify the innovations at the 2021 Geneva Fair into various categories based on their nature and application. Common categories include:
| 1 |
GASCUEL Jacques |
ANDORRA |
C |
| 2 |
BEIJING UNIVERSITY OF POSTS AND TELECOMMUNICATIONS |
CHINA |
C |
| 3 |
CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY |
CHINA |
C, D |
| 4 |
CHINA UNITED NETWORK COMMUNICATIONS GROUP COMPANY LIMITED |
CHINA |
C |
| 5 |
CHONGQING THREE GORGES UNIVERSITY |
CHINA |
C |
| 6 |
CHUNPENG WANG, YIYANG ZHAI, SHENG SU, SITAN JIANG |
CHINA |
C |
| 7 |
COLLEGE OF ELECTRICAL ENGINEERING (ZHEJIANG UNIVERSITY) |
CHINA |
C, P |
| 8 |
DALIAN UNIVERSITY OF TECHNOLOGY |
CHINA |
A, C, D, M, V |
| 9 |
DEPARTMENT OF ELECTRICAL ENGINEERING, TSINGHUA UNIVERSITY |
CHINA |
C |
| 10 |
FUDAN UNIVERSITY |
CHINA |
C, J, M, Q, V |
| 11 |
GREE ELECTRIC APPLIANCES, INC. OF ZHUHAI |
CHINA |
A, C, E, V |
| 12 |
GUODIAN UNITED POWER TECHNOLOGY COMPANY LTD. |
CHINA |
C |
| 13 |
HARBIN ENGINEERING UNIVERSITY |
CHINA |
C |
| 14 |
HUAZHONG UNIVERSITY OF SCIENCE AND TECHNOLOGY |
CHINA |
A, C, J, M, Q, V |
| 15 |
JIUJIANG JUNIOR MIDDLE SCHOOL |
CHINA |
C |
| 16 |
NANJING UNIVERSITY |
CHINA |
A, C, M, P, V |
| 17 |
NORTH CHINA ELECTRIC POWER UNIVERSITY |
CHINA |
C |
| 18 |
NORTH UNIVERSITY OF CHINA |
CHINA |
C |
| 19 |
NORTHEASTERN UNIVERSITY |
CHINA |
C |
| 20 |
QINGDAO HAIER AIR-CONDITIONER GEN. CORP., LTD. |
CHINA |
C, E, V |
| 21 |
SCHOOL OF ELECTRICAL AND INFORMATION ENGINEERING, TIANJIN UNIVERSITY |
CHINA |
C |
| 22 |
SHANGHAI JIAO TONG UNIVERSITY |
CHINA |
C, P |
| 23 |
SICHUAN ENERGY INTERNET RESEARCH INSTITUTE, TSINGHUA UNIVERSITY |
CHINA |
C, F, V |
| 24 |
SOUTHEAST UNIVERSITY |
CHINA |
A, C, D, N, P, V |
| 25 |
STATE GRID CORPORATION OF CHINA |
CHINA |
C |
| 26 |
TSINGHUA UNIVERSITY |
CHINA |
A, C, D, K, P, V |
| 27 |
TSINGHUA UNIVERSITY – JINGBO TAN |
CHINA |
C |
| 28 |
TSINGHUA UNIVERSITY – ZHENG XIAOPING |
CHINA |
C |
| 29 |
XI’AN JIAOTONG UNIVERSITY |
CHINA |
C |
| 30 |
ZHEJIANG UNIVERSITY |
CHINA |
C |
| 31 |
TAIPEI CITY UNIVERSITY OF SCIENCE AND TECHNOLOGY |
CHINESE TAIPEI |
C, D, E, F, J, P, R |
| 32 |
TAIWAN HUIXIN TECHNOLOGY LTD. CO. |
CHINESE TAIPEI |
A, C, D, I, N, Q |
| 33 |
AIVAZAN Inès |
FRANCE |
C |
| 34 |
APPLICATION TECHNOLOGY COMPANY LIMITED |
HONG KONG |
C |
| 35 |
BLUE PIN (HK) LIMITED |
HONG KONG |
C, J |
| 36 |
CITY UNIVERSITY OF HONG KONG |
HONG KONG |
C, D, M |
| 37 |
ELECTRICAL AND MECHANICAL SERVICES DEPARTMENT, THE GOVERNMENT OF THE HKSAR |
HONG KONG |
C, D, E, J, S |
| 38 |
HONG KONG APPLIED SCIENCE AND TECHNOLOGY RESEARCH INSTITUTE (ASTRI) |
HONG KONG |
C, N, V |
| 39 |
HONG KONG BAPTIST UNIVERSITY |
HONG KONG |
B, C, M, Q |
| 40 |
HONG KONG PRODUCTIVITY COUNCIL |
HONG KONG |
A, B, C, D, E, F, M, P, R, V |
| 41 |
INNOSPIRE TECHNOLOGY LIMITED |
HONG KONG |
C |
| 42 |
LOGISTICS AND SUPPLY CHAIN MULTITECH R&D CENTRE (LSCM) |
HONG KONG |
C, P |
| 43 |
THE CHINESE UNIVERSITY OF HONG KONG |
HONG KONG |
A, C, M, V |
| 44 |
MIRKOHI Mohammadamin, MIRKOHI Dorsa |
IRAN |
C |
| 45 |
NIROUMAND Vahid, ABBASZADEH Hamzeh |
IRAN |
C |
| 46 |
SIDHU Manjit Singh |
MALAYSIA |
C |
| 47 |
TIONG Sieh Kiong |
MALAYSIA |
C |
| 48 |
LUBLIN UNIVERSITY OF TECHNOLOGY |
POLAND |
C |
| 49 |
UTP UNIVERSITY OF SCIENCE AND TECHNOLOGY |
POLAND |
C |
| 50 |
AL-RAHIMI Rashed, ZIAD Mohamed |
QATAR |
C |
| 51 |
ABDULLAH Ziyad Ahmed Abdulmatin |
SAUDI ARABIA |
C |
| 52 |
ABORAYA Dalia Refat |
SAUDI ARABIA |
C |
| 53 |
AL-BOGAMI Amjad Salman |
SAUDI ARABIA |
C |
| 54 |
AL-JOHANI Samar Olaythah |
SAUDI ARABIA |
C |
| 55 |
AL-SHEHRI Samia Fayez Mohammed |
SAUDI ARABIA |
C |
| 56 |
ALKHALIFAH Rayan, GHALY Sidi |
SAUDI ARABIA |
C |
| 57 |
ALYAHYA Munirah, ALKHALIFAH Sadeem, ALAYBAN Dalal, ALMUHRIJ Alreem, ALOWISHEQ Areeb |
SAUDI ARABIA |
C |
| 58 |
UNIVERSITY OF TABUK |
SAUDI ARABIA |
C |
| 59 |
ALPHAO CO., LTD. |
SOUTH KOREA |
C |
| 60 |
HWANG Gi Taek |
SOUTH KOREA |
C |
| 61 |
JUNGLEMONSTER |
SOUTH KOREA |
C |
| 62 |
KIM Sung Ryong |
SOUTH KOREA |
C |
| 63 |
LEE Jongho |
SOUTH KOREA |
C |
| 64 |
PARK KiHoon |
SOUTH KOREA |
C |
| 65 |
SEUNGYONG Kim |
SOUTH KOREA |
C |
| 66 |
YOO Cheolyong |
SOUTH KOREA |
C |
| 67 |
ARAMVITH Supavadee, MUHAMMAD Wazir, RUANGSANG Watchara |
THAILAND |
C |
| 68 |
CHUEAMUEANGPHAN Jirachet |
THAILAND |
C |
| 69 |
KETCHAM Mahasak |
THAILAND |
C |
| 70 |
KETCHAM Mahasak |
THAILAND |
C |
| 71 |
KLINHOM Tunchanok, TANGKOCHAREON Thana |
THAILAND |
C |
| 72 |
MANOSNGIAM Ronnakorn |
THAILAND |
C |
| 73 |
PHOTHA Watcharpol |
THAILAND |
C |
| 74 |
SOONTORNPIPIT Pichitpong |
THAILAND |
C, F, Q |
| 75 |
SUDTHONGKHONG Chudanat |
THAILAND |
C |
| 76 |
TUNTISITTHIKORN Oranuch |
THAILAND |
C |
| 77 |
HASSAN Marwan |
UNITED STATES OF AMERICA |
C |
Table: Outstanding Participants in Class C – Insert Table Here
EviCypher’s Breakthrough Invention in Class C
In the Class C category of the 2021 special edition of the Geneva International Exhibition of Inventions, one invention truly shone. EviCypher, an inventor hailing from the small principality of Andorra, achieved a remarkable feat that garnered the attention of the 82 international experts comprising the jury. These experts represented diverse technical, scientific, industrial, and commercial fields, and they hailed from 25 different countries and regions. The countries and regions included Switzerland, France, Spain, Italy, Germany, the United Kingdom, China, Hong Kong, Japan, South Korea, the United States, Canada, Brazil, India, Iran, Thailand, Malaysia, Singapore, Australia, and New Zealand.
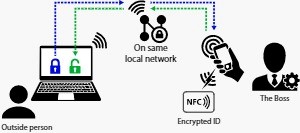
The revolutionary invention of EviCypher HSM, known as EviCypher NFC HSM (Near-Field Communication – Hardware Security Module) based on EviCore NFC HSM technology or EviCypher HSM OpenPGP (Hardware Security Module Open Pretty Good Privacy) based on EviCore HSM OpenPGP technology, won the prestigious gold medal for its revolutionary innovation in the field of highly secure authentication. via segmented keys, without the need for a server or database. What sets EviCypher HSM apart is its unique approach, enabling end-to-end anonymized human-to-human interaction.
EviCypher HSM introduced two remarkable technologies: EviCypher HSM and EviCore HSM, both of which garnered international recognition. These implementations are distinguished by the EviCypher NFC HSM technology, which leverages an individual cryptography NFC HSM device based on NFC. This technology offers a secure means to create, exchange, and utilize encryption keys without the requirement for physical contact.
This exceptional accomplishment not only highlights EviCypher’s ingenuity but also underscores the far-reaching impact and global significance of the inventions showcased at the Geneva International Inventions Fair. EviCypher’s success stands as a testament to the innovative spirit that propels inventors from all corners of the world to participate in this prestigious event—a platform where revolutionary concepts come to life.
The Success Story of Andorra at the Geneva International Exhibition of Inventions 2021
The 2021 Geneva International Exhibition of Inventions also marked a historic moment for Andorra. This tiny European principality made its debut in the competition, a testament to the event’s global appeal. While Andorra is renowned for its picturesque landscapes, it unveiled a new facet—the innovation and creativity of its residents.
Jacques Gascuel, a resident of Andorra, represented his nation on the international stage. His invention, the EviCypher HSM, is a testament to human ingenuity and technological advancement. It introduced the world to cutting-edge data security and authentication solutions, showcasing the transformative power of invention.
Not only did Jacques Gascuel participate, but he also achieved a milestone by securing the prestigious Gold Medal in the C category. This historic win serves as an inspiration to inventors worldwide, proving that innovation knows no boundaries, and even the smallest nations can make significant contributions to the world of invention.
A Recap of the Inventors Showcase 2021 Geneva
This brief highlights the historic significance of the Geneva International Inventions Fair 2021, where an inventor from Andorra won a gold medal for his groundbreaking invention, the EviCypher HSM. It also explains the difference between invention and innovation and the importance of celebrating both.
A Remarkable Event for Invention and Innovation
The 2021 fair in Geneva was historic for many reasons. It displayed revolutionary inventions from around the world. It also marked a turning point for the event and for Andorra. PALEXPO SA organized this event. It praised the spirit of invention and innovation. These are two different but complementary concepts in technology.
Andorra’s First Participation: A Milestone for Inclusion and Creativity
For the Geneva International Exhibition of Inventions, this edition was truly unprecedented. It saw the inaugural participation of an inventor from Andorra, a country better known for the beauty of its landscapes than for its inventions. This milestone welcomed a new nation into the global fraternity of inventors, highlighting the universal appeal of invention and innovation. The inclusion of Andorra underlined the event’s commitment to inclusion and the promotion of creativity, regardless of a nation’s size or importance on the world stage.
Jacques Gascuel’s Gold Medal: A Breakthrough for Data Security and Privacy
This technology uses segmented key authentication, a disruptive innovation that redefines data security, access, confidentiality and individual sovereignty. This technique creates, exchanges and uses contactless secrets, using physical trust factors (authorized geographical area, local network BSSID, telephone identifier and/or barcode and/or password or original biometric elements (fingerprint , facial recognition, DNA, etc.). If a segment is not validated, the secret is physically and digitally unusable. Thus, sensitive data (such as personal, financial, medical, professional, etc.) is protected against any unauthorized access, modification, disclosure or destruction. Jacques Gascuel has shown the spirit and power of invention and innovation, as defined by WIPO. His invention is already used in the United States, China , in South Korea, Europe, Japan and Algeria.
A Message for Inventors Around the World
This historic achievement sets an inspiring example for inventors around the world. It shows that innovation knows no borders and that even the smallest of nations can have a significant impact on the global stage. The Geneva International Inventions Fair 2021 celebrated not only inventors and their creations, but also the collaborative and inclusive spirit of the inventions community. Innovation is the implementation of a new or significantly improved product or process, a new marketing method or a new organizational method, according to the OECD.
A Reminder of Innovation’s Role in Progress
As we reflect on this exceptional event, we are reminded that innovation drives progress and that inventions like the EviCypher HSM are paving the way for a more secure and connected future. It is a testament to the unwavering human spirit and the limitless potential of inventors to shape a better world through their creations. The 2021 Geneva International Exhibition of Inventions stands as a shining example of how innovation can transcend boundaries, bringing nations together in celebration of human creativity and ingenuity.
Conclusion
We look forward to future editions of this prestigious event, where inventors from around the world will continue to push the boundaries of what is possible and redefine the future. To participate in this event, inventors must hold a patent or have filed a patent application for a patentable concept. Therefore, it is essential to distinguish between invention and innovation and to celebrate both.
In the end, it’s not just about winning medals; it’s about changing the world, one invention at a time. And in this endeavor, inventors like Jacques Gascuel are leading the way.
Downloads and more informations:
More information of golden Medal EviCypher NFC HSM click here
Download list of participants in alphabetical order click here
Download Geneva-Exhibition-Brochure.pdf click hereD
ownload press releases: The following press releases are freely available for download click here
























 Fabrice Crasnier is the director of Research & Development departement of FREEMINDTRONIC. Freemindtronic, Andorran start-up designs and manufactures tailor-made solutions for its customers in the field of safety and cyber security of information systems and computer systems.
Fabrice Crasnier is the director of Research & Development departement of FREEMINDTRONIC. Freemindtronic, Andorran start-up designs and manufactures tailor-made solutions for its customers in the field of safety and cyber security of information systems and computer systems.








