2025, Digital Security
APT29 Exploits App Passwords to Bypass 2FA
A silent cyberweapon undermining digital trust
Two-factor authentication (2FA) was supposed to be the cybersecurity bedrock. Yet, it has a crucial vulnerability: legacy systems that still allow application-specific passwords. Cyber threat actors like UNC6293, tied to the infamous APT29 (Cozy Bear), have seized this flaw to bypass advanced security layers and exfiltrate sensitive data—without triggering alarms.
Understanding How APT29 Exploits App Passwords via Social Engineering
- What makes app passwords a critical weak link.
- How attackers social engineer victims to hand over access.
- Who discovered this exploitation method and its broader geopolitical implications.
This attack vector exemplifies the evolving tactics of Russian state-sponsored actors, echoing campaigns detailed in Freemindtronic’s APT29 spear-phishing analysis.
What Was Discovered—and by Whom?
In May 2024, researchers from Google’s Threat Analysis Group (TAG) and Mandiant jointly published findings revealing that UNC6293, a cluster overlapping with APT29, was leveraging app passwords to gain persistent unauthorized access to Gmail accounts—without defeating 2FA.
Source: https://blog.google/threat-analysis-group/government-backed-attacker-targets-email
Using spear-phishing campaigns impersonating the U.S. State Department, targets—primarily Western academics and think-tank staff—received seemingly legitimate invitations to restricted briefings. The messages included a PDF “technical guide” instructing the recipient to generate and share an application password, presented as a harmless prerequisite to access materials.
Why App Passwords Are a Hidden Threat
App passwords are legacy authentication methods used for third-party email clients (like Thunderbird or Outlook) that do not support modern 2FA. Unfortunately:
- They bypass multi-factor authentication checks entirely.
- Generated passwords can last indefinitely unless manually revoked.
- They create low-visibility, stealth access vectors undetected by most users.
Attackers exploit user unfamiliarity and trust in official-looking procedures to obtain persistent email access, enabling silent observation or data theft over extended periods.
Google strongly advises high-risk users to enroll in the Advanced Protection Program, which disables app passwords entirely.
Mitigation Strategies
Even strong 2FA setups are not enough if legacy methods like app passwords remain active. Here’s how to neutralize this invisible threat:
To protect against such invisible breaches:
- Avoid app passwords—prefer OAuth-based clients or passkeys.
- Never share credentials—even ones labeled as “temporary.”
- Enable account activity monitoring and review app access regularly.
- Opt for physical security keys under Google’s Advanced Protection when handling high-risk communications.
Related Reading from Freemindtronic
This technique directly complements broader tactics used by APT29, including:
- APT29 spear-phishing across Europe
- OAuth token abuse and MFA bypass methods
PassCypher: Hardware-Isolated Sharing for All Credential Types—Without a Backend
In a landscape where attackers exploit trust, identifiers, and server exposure, PassCypher sets a sovereign benchmark in secure credential management. It eliminates traditional weak points—no servers, no databases, no user identifiers—by using patented segmented key containers, enabling fully autonomous and end-to-end secure sharing of any form of identification data.
These containers can encapsulate:
- Login/password pairs (web, VPN, apps)
- 2FA/TOTP secrets
- BitLocker, VeraCrypt, and TrueCrypt recovery keys
- Private SSH keys, OpenPGP identities, or license files
- System secrets or cryptographic material
> All shared containers remain encrypted—even at destination. They are never decrypted or exposed, not even during use.
Browser-Based PassCypher HSM: Segmented Keys for Zero-Trust Distribution
PassCypher HSM creates encrypted containers directly within the browser via JavaScript, using a client-side, patented key segmentation process. Once generated:
- The container can only be accessed using its associated split-key pair;
- Sharing is achieved by exchanging the segmented key pair, not the content;
- The recipient never needs to decrypt the container—usage is performed in-place, fully shielded.
This approach allows compliance with zero-trust governance and offline operational environments, without reliance on cloud infrastructure or middleware.
PassCypher NFC HSM: Air-Gapped, Multi-Mode Secure Sharing
PassCypher’s NFC HSM version adds advanced mobility and decentralized distribution methods, including:
- Secure NFC-to-NFC duplication: total, partial, or unit-based cloning between PassCypher HSMs, each operation protected by cryptographic confirmation;
- Direct QR code export: share encrypted containers instantly via QR, for in-room usage;
- Asymmetric QR transfer (remote): encrypt container delivery using the recipient’s own dedicated RSA 4096 public key, pre-stored in its NFC HSM’s EPROM. No prior connection is needed—authentication and confidentiality are ensured by hardware keys alone.
Each NFC HSM device autonomously generates its own RSA 4096-bit keypair for this purpose, operating entirely offline and without a software agent.
Resilience by Design: No Attack Surface, No Phishing Risk
Because PassCypher avoids:
- Online accounts or identity tracking,
- External database lookups,
- Real-time credential decryption,
…it renders phishing and real-time behavioral override attacks—like those used when APT29 Exploits App Passwords —fundamentally ineffective.
Containers can be shared securely across individuals, air-gapped environments, and even international zones, without exposing content or credentials at any stage. All interactions are governed by asymmetric trust cryptography, offline key exchanges, and quantum-ready encryption algorithms.
> In essence, PassCypher empowers users to delegate access, not vulnerability.
📎 More info:
- PassCypher HSM PGP overview
- PassCypher NFC HSM overview
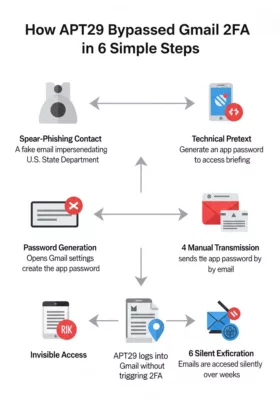
APT29’s attack chain explained in 6 steps — how trust was exploited to bypass Gmail 2FA.
APT29’s attack chain explained in 6 steps — how trust was exploited to bypass Gmail 2FA.
APT29 Attack Flow Using App Passwords
To visualize the manipulation process, here’s a simplified attack chain used by APT29 via UNC6293:
- Reconnaissance Identify high-value targets: academics, journalists, researchers.
- Initial Contact Send authentic-looking spear-phishing emails impersonating government agencies.
- Trust Engineering Engage over several replies, maintain tone of authority and legitimacy.
- Delivery of False Procedure Provide a professional PDF instructing how to generate an app password.
- Credential Submission Convince the target to transmit the app password “for access inclusion.”
- Persistent, Invisible Intrusion Access the mailbox indefinitely without detection.
Threat Evolution Matrix: APT29 Access Techniques
| Campaign | Technique | Target Profile | Access Layer | Visibility | Persistence |
|---|---|---|---|---|---|
| APT29 OAuth Abuse (2023) | OAuth consent hijack (token abuse) | NGOs, diplomats, M365 admins | Microsoft 365 cloud | Medium (IAM logs) | Weeks to months |
| APT29 UNC6293 (2024–2025) | App password social engineering | Russia analysts, cyber experts | Gmail (legacy auth) | Low (no alerts) | Indefinite |
| APT29 credential phishing (historic) | Fake login portals | Broad civilian targets | Multiple | High (browser warning) | Single session |
This table highlights a shift from technical breaches to human-layer manipulations.
Real-World Mitigation Scenarios
Security advice becomes actionable when grounded in context. Here are practical defense strategies, tailored to real-use environments:
- For researchers receiving invitations to conferences or secure briefings: Avoid app passwords altogether. Demand access via federated identity systems only (e.g., SAML, OAuth). If someone asks for a generated credential—even “just once”—treat it as hostile.
- For cybersecurity teams managing high-risk individuals: Implement rules in Workspace or M365 to disable legacy authentication. Mandate FIDO2 physical keys and enforce real-time log correlation monitoring for unusual delegated access.
- For institutions under threat from espionage: Deploy zero-knowledge solutions like PassCypher HSM, which allow secure credential sharing without revealing the data itself. Instruct all staff to treat any unsolicited “technical procedure” as a potential attack vector.
These don’t just mitigate risk—they disrupt the very tactics APT29 depends on.
At the core of PassCypher lies a different security philosophy—one that rejects reliance and instead builds on cryptographic sovereignty. As its inventor Jacques Gascuel puts it:
Inventor’s Perspective
> “Trust isn’t a feature. It’s a surface of attack.”
As creator of PassCypher, I wanted to reimagine how we share secrets—not by trusting people or platforms, but by removing the need for trust altogether.
When you share a PassCypher container, you’re not giving someone access—you’re handing over an undecipherable, mathematically locked object, usable only under predefined cryptographic conditions. No identity required. No server involved. No vulnerability created. Just a sovereign object, sealed against manipulation.
In an age where attackers win by exploiting human belief, sovereignty begins where trust ends.
— Jacques Gascuel
Final Note: Security as Cognitive Discipline
There is no “end” to cybersecurity—only a shift in posture.
APT29 doesn’t breach your walls. It gets you to open the gate, smile, and even carry their suitcase inside. That’s not code—it’s cognition.
This article is a reminder that cybersecurity lives in awareness, not just hardware or protocols. Each message you receive could be a mirror—reflecting either your vigilance or your blind spot. What you do next shapes the threat.
Furthermore, PassCypher’s ability to render attacks where APT29 Exploits App Passwords ineffective is a major security advantage.