Cyberattack Cyberattacks Exploiting Hidden Vulnerabilities: What You Need to Know
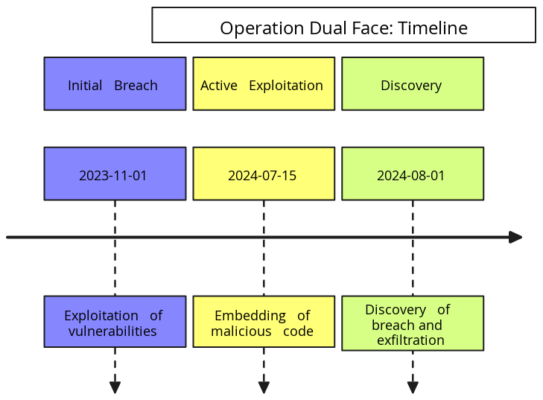
Cyberattacks Exploiting Hidden Vulnerabilities: In October 2024, a cyberattack exploited backdoors in major U.S. telecom providers. Salt Typhoon exposed serious vulnerabilities in legal backdoors. Salt Typhoon, a Chinese hacker group, exploited these backdoors. Consequently, they accessed sensitive data intercepted through wiretaps. This cyberattack exploits backdoors, highlighting the risks associated with legal surveillance tools that hackers can manipulate. This incident highlights the risks associated with backdoors. Designed for legal surveillance, malicious actors can exploit these backdoors. Learn how to protect yourself effectively.
2024 Digital Security
Salt Typhoon: Protecting Government Communications from Cyber Threats
2024 Digital Security Spying Technical News
Side-Channel Attacks via HDMI and AI: An Emerging Threat
2024 Digital Security
Google Workspace Vulnerability Exposes User Accounts to Hackers
Cyberattack Exploits Backdoors: What You Need to Know
In October 2024, a cyberattack exploited backdoors within U.S. telecom systems, revealing critical vulnerabilities. Salt Typhoon, a Chinese hacker group, leveraged legal backdoors designed for lawful surveillance to access sensitive data intercepted through wiretaps. This incident highlights the growing global risk of backdoor exploitation, where tools intended for government use can be weaponized by malicious actors.
What Are Legal Backdoors?
Legal backdoors are deliberate entry points built into software systems, designed to give government agencies access to encrypted data for lawful surveillance. They enable agencies to intercept communications or obtain data based on legal orders such as warrants. This type of backdoor is intended to support law enforcement in protecting national security and public safety.
However, the presence of these backdoors creates significant security concerns. While they are built for lawful purposes, they can introduce vulnerabilities. Cybercriminals often exploit these weaknesses. For example, Salt Typhoon, a Chinese hacker group, leveraged these legal backdoors to bypass security protocols and access sensitive wiretapped communications. By exploiting these vulnerabilities, hackers turn a system intended for lawful use into a weapon for unauthorized access.
The concept of legal backdoors contrasts with illegal backdoors, which are created by attackers without the knowledge or consent of the system owners. Although law enforcement intends legal backdoors for surveillance, they weaken overall system security and pose significant risks. Once organizations implement these backdoors, cyber attackers often discover and exploit them, as seen in the October 2024 cyberattack. The lesson is clear: even systems designed with legal purposes can expose critical data to malicious actors when backdoors are present.
In summary, legal backdoors serve a government function but introduce significant cybersecurity risks. This reality demands robust encryption technologies, like those offered by Freemindtronic, which protect data even in systems compromised by backdoors.
How Cyberattack Exploits Backdoors and Key Insights
Hackers from Salt Typhoon successfully launched a cyberattack exploiting backdoors within telecom systems against telecom providers like Verizon, AT&T, and Lumen Technologies. By exploiting the backdoors legally built into these systems, Salt Typhoon gained unauthorized access to wiretapped communications. Salt Typhoon transformed the vulnerabilities in these backdoors, originally designed for legal surveillance, into entry points for a sophisticated cyberespionage operation, posing a significant threat to national security.
When developers design backdoors for law enforcement access, they often create unintended weaknesses. Salt Typhoon’s use of these backdoors demonstrates the inherent dangers of embedding vulnerabilities into systems, even when for lawful purposes.
Encryption Solutions to Prevent Cyberattack Exploits Backdoors
Freemindtronic’s encryption technologies offer robust defense mechanisms against cyberattacks exploiting backdoors, securing data even in compromised systems.
DataShielder NFC HSM and PassCypher HSM PGP, for example, ensure that even when systems are compromised, Freemindtronic’s encryption ensures that hackers cannot access the encrypted data. Freemindtronic encrypts data before it passes through any vulnerable system and safely stores encryption keys in NFC HSM modules. This externalization prevents attackers from using backdoors to access or decrypt sensitive information.
Explore these solutions here:
Physical Key Segmentation as a Layer of Protection
Freemindtronic’s physical key segmentation adds an extra layer of defense. This method divides encryption keys into multiple segments, ensuring that access to the full key is virtually impossible without all the physical components. Hackers, even if they manage to breach backdoors, are left without the necessary tools to decrypt the data.
Cyberattack Exploits Backdoors: Global Examples and Risks
The cyberattack exploits backdoors in telecom systems. This has been seen in Verizon, AT&T, and Lumen Technologies. Other instances include several significant cases. These illustrate how backdoors, created for lawful surveillance, have been used for malicious purposes.
Historical Examples of Backdoor Exploits
- Clipper Chip (1993): The U.S. government tried to introduce a backdoor into telecommunications devices to enable lawful surveillance. However, privacy concerns led to the abandonment of this project. This example shows early recognition of the dangers posed by such vulnerabilities.
- EncroChat (2020): European law enforcement successfully exploited backdoors in EncroChat, an encrypted communication platform used by criminals. This led to numerous arrests but sparked privacy concerns and raised ethical questions about how surveillance tools are used.
Recent Exploits Using Backdoors
- Pegasus Spyware (2021): Governments used Pegasus spyware for legitimate surveillance purposes. However, investigators later discovered that Pegasus targeted journalists, activists, and political figures, leading to widespread criticism of its misuse for political gain. The incident highlighted the thin line between security and abuse.
- Microsoft Exchange Server Hack (2021): Chinese hackers exploited vulnerabilities in Microsoft Exchange Server, originally designed for lawful access by governments. The attack compromised data from over 30,000 organizations in the U.S. This case emphasizes the risks of building access points into critical systems.
Why Are Backdoors So Dangerous?
Governments install backdoors to assist with surveillance, but malicious actors often abuse them. The examples above demonstrate how hackers and sometimes even governments can exploit these backdoor vulnerabilities for cyberespionage. This underscores the need for stronger encryption and better security protocols to protect sensitive data.
How Backdoors Become Double-Edged Swords
Backdoors are often justified as essential tools for government surveillance and law enforcement, but their inherent vulnerabilities make them dangerous. In the case of Salt Typhoon, the hackers turned a backdoor meant for lawful use into a vector for cyberespionage. This raises serious concerns about the long-term security of systems that include built-in vulnerabilities, even when used for legitimate purposes.
Solutions to Secure Your Future Against Backdoor Exploits
Why Encryption Is Critical to Combat Backdoor Exploits
As cyberattacks exploiting backdoors continue to rise, it becomes more important than ever to implement robust encryption solutions. These solutions prevent unauthorized access, even when systems are vulnerable to cyberattacks exploiting backdoors. These solutions prevent unauthorized access, even when backdoors exist within systems. Freemindtronic’s encryption technologies, such as the DataShielder NFC HSM and PassCypher NFC HSM, ensure that Freemindtronic stores encryption keys externally. This externalized storage effectively blocks attackers from accessing or decrypting sensitive data, even if they breach the system. Consequently, organizations can maintain security regardless of potential vulnerabilities.
Explore the NFC HSM Encryption Tools
To better protect your systems, explore the following NFC HSM encryption tools:
- DataShielder NFC HSM Lite: This tool is perfect for lightweight encryption and secure password management. It is well-suited for small teams or individual users.
- DataShielder NFC HSM Master: This advanced solution offers full encryption key management, ideal for large-scale operations dealing with sensitive data.
- PassCypher NFC HSM Master: Besides managing passwords, this tool includes OTP secret key management (supporting both TOTP and HOTP) for multi-factor authentication (MFA), which greatly enhances security.
- DataShielder NFC HSM M-Auth: This solution allows for remote key creation via encrypted QR codes, which is crucial for teams needing secure mobile access.
- DataShielder NFC HSM Auth: Specifically focused on authentication, this tool helps prevent unauthorized access by managing user credentials securely.
Managing Passwords and Secret Keys with PassCypher and DataShielder Technologies
PassCypher HSM PGP
PassCypher HSM PGP is a patented password manager that operates server-free, without a database, user identifier, or master password. It leverages AES-256 CBC PGP encryption with segmented keys to create secure encrypted containers for storing login credentials, URLs, and passwords. This solution guarantees complete anonymity and offers 1-click auto-login for rapid and secure access. Furthermore, its anonymized architecture makes it an excellent choice for environments requiring digital signatures and secure communications. This also protects against phishing attacks and minimizes human error.
PassCypher NFC HSM Master
In addition to its advanced password management capabilities, PassCypher NFC HSM Master integrates OTP secret key management. It supports both TOTP (Time-based One-Time Password) and HOTP (HMAC-based One-Time Password), offering multi-factor authentication (MFA). This added layer of security ensures that your systems remain secure with time-sensitive passwords, making it an ideal solution for organizations that require secure user authentication alongside efficient password management.
DataShielder NFC HSM Series
The DataShielder NFC HSM series offers flexible encryption tools designed for different levels of security needs:
- DataShielder NFC HSM Lite: This lightweight solution provides basic encryption and password management. It’s particularly suited for individuals or small teams that require external key storage for enhanced security.
- DataShielder NFC HSM Master: A more comprehensive tool, this solution offers full encryption key management for large-scale, highly sensitive operations. It is ideal for organizations managing multiple encryption keys while needing extensive security features.
- DataShielder NFC HSM Auth: Specifically designed for authentication, this tool focuses on preventing unauthorized access by securely managing credentials. It’s essential for any system where protecting access is paramount.
- DataShielder NFC HSM M-Auth: Perfect for remote access needs, this tool allows for remote key creation via encrypted QR codes. This is especially useful for highly mobile teams or individuals who need secure access on the go.
The Importance of Chiffrement in Protecting Sensitive Data
Chiffrement, or encryption, plays a critical role in protecting sensitive data by transforming it into an unreadable format unless decrypted by the correct key. Freemindtronic’s NFC HSM solutions provide externalized key storage, ensuring that even if a system is breached, attackers cannot access the encrypted data. These solutions cover everything from password management and OTP secret keys to full encryption key management. This guarantees that your organization’s most sensitive information remains safe from cyberattacks and backdoor exploits.
By implementing these advanced NFC HSM encryption solutions, your organization can effectively secure its data, authenticate user access, and stay protected against the increasing threats posed by backdoor vulnerabilities. With external key management, multi-factor authentication, and robust encryption protocols, you ensure that your critical data remains safe, even in the face of sophisticated cyberattacks.
Strengthen Your Cybersecurity Through Proactive Defense
The cyberattack executed by Salt Typhoon on U.S. telecom systems underscores the urgent need for organizations to anticipate vulnerabilities and take proactive steps. To protect your systems effectively, you must implement robust encryption technologies. By adopting Freemindtronic’s encryption solutions, you actively ensure that your data stays secure, even in the presence of backdoors or system breaches.
First, use chiffrement to protect sensitive information. Then, enhance security with external encryption key management and physical key segmentation. These tools offer a strong defense against both current and future cyber threats. In today’s rapidly evolving cyber landscape, cyberattacks exploiting backdoors target every available vulnerability. Implementing these solutions now will safeguard your systems and prevent backdoor exploits from compromising your operations.
For more insights, you can review the detailed analysis provided by The Cybersecurity and Infrastructure Security Agency (CISA). Their resources cover essential cybersecurity best practices that help organizations stay resilient against emerging threats.
Your cybersecurity strategy must continuously adapt to the threats you face. By investing in strong encryption technologies and addressing key vulnerabilities, you actively shield your data from both current and future cyberattacks. Stay ahead of cybercriminals by using the right tools and employing proactive defense strategies.