Hackers exploit OAuth2 flaw to bypass 2FA on Google accounts
Hackers exploit the Google OAuth2 security flaw to bypass 2FA and access your online services with persistent cookies. They exploit an undocumented OAuth2 endpoint to generate these cookies. PassCypher protects you by verifying the URL of connection to Google, alerting you of password corruption, and blocking redirection iframes attacks.
2026 Digital Security
January 23, 2026
2026 Digital Security
January 17, 2026
2026 Digital Security
January 8, 2026
2026 Digital Security
January 7, 2026
2025 Digital Security
January 6, 2026
2026 Digital Security
January 5, 2026
2025 Digital Security
January 5, 2026
2025 Digital Security
December 21, 2025
Google OAuth2 security flaw articles for in-depth analyses of threats and solutions. Stay updated by clicking on our scrolling topics.
Google OAuth2 security flaw written by Jacques Gascuel, inventor of sensitive data safety and security systems, for Freemindtronic. This article may be updated on this subject.
Google OAuth2 security flaw: Strategies Against Persistent Cookie Threats in Online Services
Google OAuth2 security flaw poses a serious threat that affects millions of users worldwide. However, hackers can exploit an undocumented OAuth2 endpoint to generate persistent cookies that allow them to access your online services, such as Gmail, Google Drive, YouTube, etc., without needing your password or 2FA code. Hackers can compromise your privacy, data, and identity using this flaw. How can you protect yourself from this attack? In this article, we will explain how this flaw works, how it has impacted many countries and organizations, and how you can use PassCypher, an innovative solution that verifies the URL of connection to Google, alerts you of password corruption, and blocks redirection iframes attacks.
Google OAuth2 Protocol: Ensuring Account Security and Comparing Different Methods
OAuth2 is an authorization protocol that facilitates user access to services like YouTube, Gmail, and Google Drive, allowing login with a Google account while avoiding password sharing. Specifically designed for ease and adaptability, this protocol comprehensively supports various applications, ranging from web and desktop platforms to mobile and living room devices. Consequently, when users engage with OAuth2, they authorize Google to share selective information, such as names and email addresses, with the connected service. Following this, Google issues an authentication token, effectively confirming the user’s identity to these services.
However, this protocol also has a security flaw, which was revealed by a hacker in October 2023. This flaw, known as the Google OAuth2 security flaw, allows hackers to create persistent cookies for Google accounts, which give them continuous access to Google services, even after the user resets their password. They exploit an undocumented Google Oauth endpoint named “MultiLogin”.
To protect themselves from this flaw, users can choose between different security methods, which require them to provide two pieces of evidence to log in to their account: their password and another factor. However, these methods have differences, advantages and disadvantages.
Google OAuth2 Multilogin Endpoint two-step verification (2SV)
This method uses the “MultiLogin” endpoint, which allows the user to log in to multiple Google services with a single authentication token. When the user logs in to their Google account, they receive a notification on their phone or computer, which they have to approve to validate their identity. This method is simple and fast, but it has a security risk. Indeed, it is vulnerable to the Google OAuth2 security flaw, which can compromise the user’s account.
One-time password two-factor authentication (2FA)
This method uses a one-time password based on time (TOTP) or on a counter (HOTP). This password is generated by an app or a physical device, which uses an algorithm and a secret shared with the Google account. When the user logs in to their Google account, they have to enter the one-time password displayed by the app or the device, in addition to their usual password. This method is more secure, because it does not depend on the Google Oauth endpoint. It resists phishing, replay or interception attacks. However, it requires access to the app or device, such as PassCypher NFC HSM1, that generates the one-time password. This can be inconvenient or impossible if you lose, damage or forget the app or device. Unless, of course, the app or device, like PassCypher, has an externalized OTP secret key backup system.
In conclusion, 2SV Google OAuth2 Multilogin Endpoint and 2FA one-time password are two security methods that offer different levels of protection. 2SV is simpler and faster, but it is vulnerable to the Google OAuth2 security flaw. 2FA is more secure, but it is more complex and dependent on an external factor. It is up to each user to choose the method that suits them best, depending on their needs and preferences.
Unveiling the Perils of PRISMA: A Deep Dive into Google OAuth2 Security Flaws
Google OAuth2 Security Flaw: A Critical Threat Exploiting Persistent Cookies
In October 2023, a critical Google OAuth2 security flaw was discovered in the Google OAuth2 protocol. This flaw, dubbed PRISMA, was a serious threat to the security of Google accounts. It allowed hackers to steal a wealth of sensitive data, including personal, financial, and professional information, as well as passwords and cookies.
Malware groups used the exploit widely. who integrated it into their infostealing tools. These tools were used to target millions of users worldwide, including government institutions, media organizations, NGOs, and businesses.
How the PRISMA Exploit Works: Exploiting an Undocumented Endpoint
Hackers took advantage of the PRISMA exploit, using an undocumented Google OAuth2 endpoint. This endpoint is typically used for legitimate purposes, such as providing limited access to Google accounts. However, the PRISMA exploit cleverly repurposed this endpoint to generate persistent cookies that remained valid even after a user changed their password or IP address.
To further understand how the PRISMA exploit worked, a security researcher from CloudSEK, Pavan Karthick M, analyzed it in depth in a report dated December 29, 2023. His findings revealed that the exploit worked by first obtaining the user’s Google account ID and refresh token. These credentials could be obtained through phishing attacks, malware infections, or other means.
Once the user’s credentials were obtained, the exploit used the undocumented endpoint to generate persistent cookies. Hackers then used these cookies to access the user’s Google account without needing 2FA.
The Impact of the PRISMA Exploit: Stealing Sensitive Data from Millions
The PRISMA exploit impacted a wide range of users. It was used to steal sensitive data from millions of users worldwide.
Government institutions, media organizations, NGOs, and businesses were all targeted by the exploit. Hackers stole sensitive data, such as personal information, financial records, and intellectual property, from these organizations.
The PRISMA exploit highlighted the ever-evolving nature of cyber threats. It showed that even the most secure protocols can be vulnerable to exploitation by determined hackers.
Securing Your Google Account from the PRISMA Exploit
The PRISMA exploit is a critical threat to Google account security. This exploit allows hackers to generate persistent Google cookies through token manipulation, enabling them to access Google services even after a user’s password is reset.
How to Protect Yourself from the PRISMA Exploit
Here are some key steps you can take to protect your Google account from the PRISMA exploit:
-
Enable two-factor authentication (2FA): 2FA is the most effective way to protect your Google account. It requires you to enter a code from your phone or other device, such as a hardware password manager, in addition to your password when you sign in.
-
Use a strong and unique password: Never reuse the same password for multiple accounts. If one account is compromised, all of your accounts are at risk. Choose a password that is long, complex, and difficult to guess. You can use a password generator or password manager to help you generate strong passwords.
-
Be cautious about clicking on links: Hackers often send phishing emails that contain links that will take you to malicious websites disguised as legitimate Google pages. Never click on links in emails or on websites unless you are sure they are from a trusted source.
-
Use a hardware password manager: PassCypher is an advanced hardware password manager that can help you protect your Google account from the PRISMA exploit. It is a versatile tool that can be used to manage your passwords on any storage device, including hard drives, SSDs, SD cards, USB drives, cloud storage, NAS devices, NFC devices, and mobile devices.
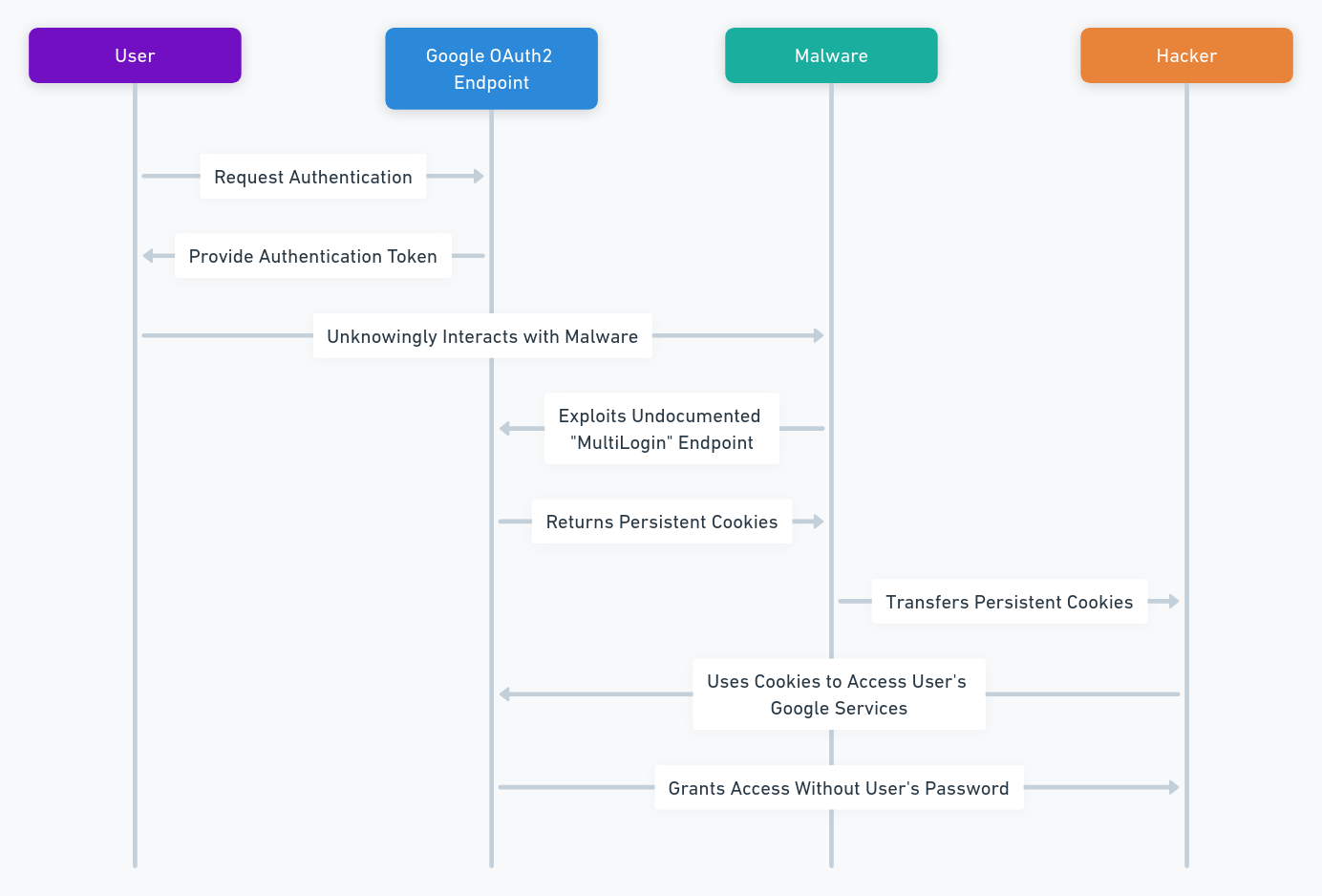
How the flaw works
Firstly, the flaw exploits an undocumented endpoint called the “multilogin” endpoint. Specifically, Google uses this endpoint to enable users to sign in to multiple Google accounts simultaneously. To exploit this flaw, attackers actively use the multilogin endpoint. They do this by generating persistent cookies for a victim’s Google account. Remarkably, the process involves using the victim’s email address and session ID.
Subsequently, the malware stores these cookies on the victim’s computer. Consequently, this action allows the attacker to access the victim’s Google account. Importantly, this access occurs without the need for the victim’s password. Moreover, this approach highlights a significant vulnerability in the account security process.
In essence, the attackers’ method of using the multiple sign-in endpoint is alarmingly effective. Notably, the generation and storage of cookies using the victim’s email and session ID underscore the flaw’s criticality. Ultimately, these actions enable attackers to bypass traditional security measures, accessing accounts undetected.
Below is the diagram which illustrates the technical method used to exploit the flaw.

The PRISMA exploit is a reminder that cyber threats are constantly evolving. By staying informed about the latest threats and taking proactive steps to protect your accounts, you can help to keep your data safe.
Analysis of the OAuth2 Flaw Affecting Google Account Security: A Statistical Outlook
The Growing Menace: Malware Exploiting Google Account Security Vulnerability
Significantly, Bitdefender’s study reveals a concerning trend. Between January and April 2023, they detected over 500,000 attempts to exploit the OAuth2 flaw, with a staggering 86% targeting Google Cloud accounts. Hackers have been using these accounts for resource-intensive activities, notably cryptocurrency mining, resulting in considerable costs for victims. This underscores the criticality of the Google account vulnerability, affecting millions worldwide.
The Extent of the Google Account Security Flaw Caused by OAuth2
The OAuth2 flaw exploited by malware has a wide impact. It affects not only individual users, but also major web platforms that use OAuth2 and OpenID for user authentication. Technology giants like Facebook, Google, LinkedIn, and Microsoft are notably impacted. Moreover, various infostealing tools have exploited this vulnerability to siphon off users’ personal, financial, and professional information. These tools include Lumma, Rhadamanthys, Stealc, Meduza, RisePro, and WhiteSnake, as well as Zloader, TrickBot, and Emotet.
Studying the Risks Posed by the Security Flaw
Furthermore, CloudSEK’s study emphasizes the widespread nature of this risk. Alarmingly, over 91% of European Cloud services, which frequently use OAuth2 for Google account connections, are at risk. Notably, a widely-used design application was found to be vulnerable to such attacks.
Disturbingly, Google’s data reveals that by 2024, only around 15% of Google account users had activated two-step verification. Consequently, this leaves a substantial 85% more exposed to the OAuth2 flaw and other security threats. Kaspersky’s survey indicates that 60% of users reuse passwords across multiple online accounts, exacerbating the risks of identity theft and account compromise. Moreover, RiskIQ’s analysis detected over 25,000 malicious applications on the Google Play Store in 2023, many of which contain infostealing tools exploiting the OAuth2 flaw.
Mitigating the Impact: Proactive Strategies Against OAuth2 Security Flaws in Google Accounts
In response to these risks, enabling two-step verification on Google accounts is crucial. Additionally, using reliable password managers is essential for enhanced security. It’s important to regularly monitor account activities, identifying and addressing suspicious behavior swiftly.
Exercising caution with untrusted links or attachments is vital. By taking this step, users can help avoid phishing attempts and other deceptive practices. Moreover, innovative solutions like PassCypher significantly enhance security. PassCypher verifies Google connection URLs and alerts users to password corruption. It effectively blocks iframe redirection attacks, adding an extra defense layer against sophisticated cyber threats.
By adopting these measures, users can significantly reduce vulnerability to the OAuth2 flaw. Staying vigilant and informed about security risks and solutions is key. This approach is essential for maintaining digital identities and assets’ integrity and safety in a connected world.
Recent Victims of Google’s OAuth2 Security Breach: A Global Overview
Malware has affected several countries and organizations, which have seen their Google accounts compromised and their data stolen. Among the victims, we can mention:
- Greece, Moldova and Tunisia, which were targeted by a first hacking campaign in October 2023. Hackers used the exploit to access government institutions, media, NGOs, and businesses in these countries. Hackers stole sensitive information, such as official documents, diplomatic correspondence, financial data, etc.
- Vietnam, which was targeted by a second hacking campaign in November 2023. The hackers used the exploit to access the Google accounts of ministries, press agencies, universities and businesses in this country, and stole strategic data, such as development plans, research reports, trade contracts, etc.
- Pakistan, which was victim of a third hacking campaign in December 2023. The hackers used the exploit to access the Google accounts of authorities, media, NGOs and businesses in this country, and stole confidential data, such as military documents, secure communications, personal data, etc.
- Several European countries, including France, Germany, Italy, Spain and the United Kingdom, which were targeted by a fourth hacking campaign in January 2024. The hackers used the exploit to access the Google accounts of European institutions, political parties, media, NGOs and businesses in these countries, and stole critical data, such as bills, investigation reports, electoral data, etc.
Voices of the targeted: Testimonies from Google’s OAuth2 Flaw Victims
The vulnerability severely damaged the victims, exposing their data, blocking their accounts, disrupting their services, and even ruining their finances. Here are some real testimonies of victims, collected by the website 20 Minutes and the website Aleteia:
- Julien, 35, computer engineer, received an email that seemed to come from Google. It asked him to confirm his identity to access a service. He clicked on the link and entered his password. A few minutes later, he received another email from Google. It told him that his account had been hacked and that he had to change his password. But it was too late, he no longer had access to his account. The hackers used his account to send spam to his contacts, to access his photos, his documents, his bank accounts, etc. They even tried to blackmail him by threatening to publish his personal data on the Internet. He filed a complaint, but he did not get a response. He feels helpless and violated.
- Léa, 28, school teacher, uses her Google account to log in to several online services, such as YouTube, Gmail, Google Drive, etc. Malware blocked her account, preventing her access to any of these services. She contacted Google support, who told her that her account had been compromised by malware and that she had to recover it by following a procedure. But Hackers changed her account’s security settings, causing the recovery procedure to fail. She lost all her files, her emails, her videos, etc. She had to create a new account and start over. It’s very frustrating and stressful for her.
- Omar, 42, human rights activist, works for an NGO that defends human rights in the world. He uses his Google account to communicate with his colleagues, his partners, his sources, etc. One morning, he discovered that Hackers hacked his account and stole his data. Hackers sent defamatory messages, accessed confidential information, and compromised the security of his contacts using his account. They even tried to make him look like a spy. He was threatened, harassed, intimidated. He had to change his phone number, email address, pseudonym, etc. He fears for his life and for that of his loved ones.
How to protect yourself from the Google OAuth2 security flaw?
Google OAuth2 security flaw exposes users to this threat. It allows hackers to bypass 2FA and access online services with persistent cookies. They exploit an undocumented OAuth2 endpoint to generate these cookies. To protect yourself, use PassCypher. PassCypher is a hardware password manager that uses NFC technology to securely store and manage passwords. It can also detect and block phishing attacks and iframe redirection attacks. It is an innovative solution that verifies the URL of connection to Google, alerts you of password corruption, and blocks redirection iframes attacks.
Securing Your Google Account: Proactive Measures Against OAuth2 Exploits
Google tried to strengthen its fraud detection measures to counter the exploit, but the hackers adapted their method to bypass them. Therefore, there is no simple solution to protect yourself from the vulnerability. But you can adopt some good practices to secure your Google account:
Use a strong and unique password
Do not reuse the same password for multiple accounts. If one of them is compromised, the others will be too. Choose a long, complex and hard to guess password. You can use a password generator or a password manager to help you.
Enable two-step verification
It is an additional layer of security that asks for a code or a confirmation on your phone when you log in to your Google account. Thus, even if someone knows your password, they will not be able to access your account without your device. You can enable two-step verification in the settings of your Google account.
Check recent activities and connected devices
Google allows you to check the history of connections to your account, as well as the devices that have accessed it. If you notice any suspicious activity or unknown device, you can report it and remove it from your account. You can check recent activities and connected devices in the settings of your Google account.
Be careful of fraudulent emails and websites
Hackers may try to trick you by sending you emails or links that seem to come from Google, but are actually phishing attempts. Phishing is a technique that makes you believe that you need to provide your credentials or personal information to access a service or an offer. Do not click on dubious links or attachments, and always check the website address before entering your data. You can report fraudulent emails and websites to Google.
Log in regularly to your Google account
Starting from December 2023, Google will delete inactive accounts for more than two years. This measure aims to increase security and reduce the risks of compromise of abandoned accounts. To avoid losing your data, remember to log in to your Google account at least once every two years.
By following these tips, you can increase the security of your Google account and protect it from hackers. Do not forget to change your password regularly and keep your phone updated. For more information, visit Google’s security website.
PassCypher: A Leading-Edge Solution for Protecting Against Google OAuth2 Vulnerabilities
A leading-edge solution
The Google OAuth2 vulnerability is a critical security threat to Google accounts. Attackers can use this vulnerability to generate persistent cookies and access your Google account, even after you change your password or IP address.
PassCypher is a hardware password manager that can help protect your Google account from the Google OAuth2 vulnerability. PassCypher seamlessly integrates EviPass, EviOTP, EviCore NFC HSM, EviCore NFC HSM Browser Extension, and EviCore HSM OpenPGP technologies, as well as the NFC HSM devices from Freemindtronic. These technologies form the foundation of PassCypher’s comprehensive security features.
PassCypher uses post-quantum AES-256 robust encryption with segmented keys, which makes it impossible for attackers to decrypt your passwords, even with a quantum computer.
Advanced security features
In addition to its post-quantum encryption, PassCypher also offers a number of other advanced security features that can help protect your Google account.
- Protection against iframe redirection: PassCypher blocks iframe redirection, preventing attackers from redirecting you to malicious websites without your knowledge.
- Sandbox protection: PassCypher uses a sandbox protection mechanism to isolate each encrypted secret, preventing attackers from accessing or modifying your passwords or the original login URL.
- Protection against SQL injection attacks: PassCypher does not store your passwords on a server or database. Instead, each password is encrypted individually and stored freely on one or more local or online or offline storage devices at the user’s choice, in lan and/or wan. This physically prevents attackers from accessing your encrypted passwords via SQL injection attacks.
- Password corruption detection: PassCypher alerts you if it detects that a password has been corrupted, ensuring that your sensitive information remains secure.
- State-of-the-art password generation: PassCypher uses a variety of algorithms to generate truly random and strong passwords greater than 256 bits, making them impossible to guess even to post-quantum attacks.
A versatile solution
PassCypher is a versatile tool that can be used to manage your passwords on any storage device, including:
- Hard drives
- SSDs
- SD cards
- USB drives
- Cloud storage
- NAS devices
- NFC devices
- Mobile devices
How to use PassCypher
To use PassCypher, you can install the free PassCypher HSM PGP extension for your Chromium or Firefox web browser. Once the extension is installed, you can easily access the following features:
- Protection against iframe redirection
- Password corruption detection
- State-of-the-art password generation
- Segmented key AES-256 OpenPGP encrypted password manager
To log in to your Google account using PassCypher, simply click on the PassCypher icon that appears in the Google login field. Once you click on the icon, PassCypher will automatically fill in your login credentials and submit them for you.
PassCypher HSM PGP is a free extension that provides basic password management features. PassCypher Engine, a paid add-on, adds additional features, such as automatic login in one second, password change in five seconds, fully automated secret usage management on multiple devices, and instant, fully automated encryption and decryption.
An effective solution
By using PassCypher, you can significantly improve the protection of your Google account against the Google OAuth2 vulnerability. PassCypher’s robust security features and ease of use make it a valuable tool for protecting your digital assets.
Conclusion: Safeguarding Against Google’s OAuth2 Security Flaws
We have seen how a clever hack allows cybercriminals to access Google accounts without passwords. We have also seen how this hack has affected many countries and organizations, and how he victims have testified about their distress. Finally, we have seen how to protect ourselves from this threat by adopting good security practices, and by using PassCypher, an innovative solution that verifies the URL of connection to Google, alerts in case of password corruption, and protects from redirection iframes attacks. The exploit reveals the complexity and stealthiness of modern cyber threats. The need for continuous monitoring of technical vulnerabilities and human intelligence sources to stay ahead of emerging threats.