Zero-knowledge vulnérable : les attaques par downgrade contre Bitwarden, LastPass et Dashlane révèlent comment la rétrocompatibilité cryptographique peut fragiliser une architecture zero-knowledge. Lorsque les paramètres KDF peuvent être influencés côté serveur, le modèle zero-knowledge devient potentiellement vulnérable sous hypothèse de compromission active. Ce dossier analyse pourquoi un système zero-knowledge vulnérable ne remet pas en cause le chiffrement lui-même, mais interroge la gouvernance des paramètres, la discipline des versions et la souveraineté cryptographique au-delà des arguments marketing. Cette analyse distingue ainsi un zero-knowledge théoriquement solide d’un zero-knowledge vulnérable en raison de choix d’implémentation. Elle explore les contre-mesures envisageables et précise pourquoi les architectures reposant sur une absence totale de négociation serveur, ainsi que sur un mécanisme breveté d’authentification à clés segmentées hors ligne développé par Freemindtronic en Andorre, ne peuvent, par construction architecturale, entrer dans le périmètre étudié.
Résumé exécutif
Contexte
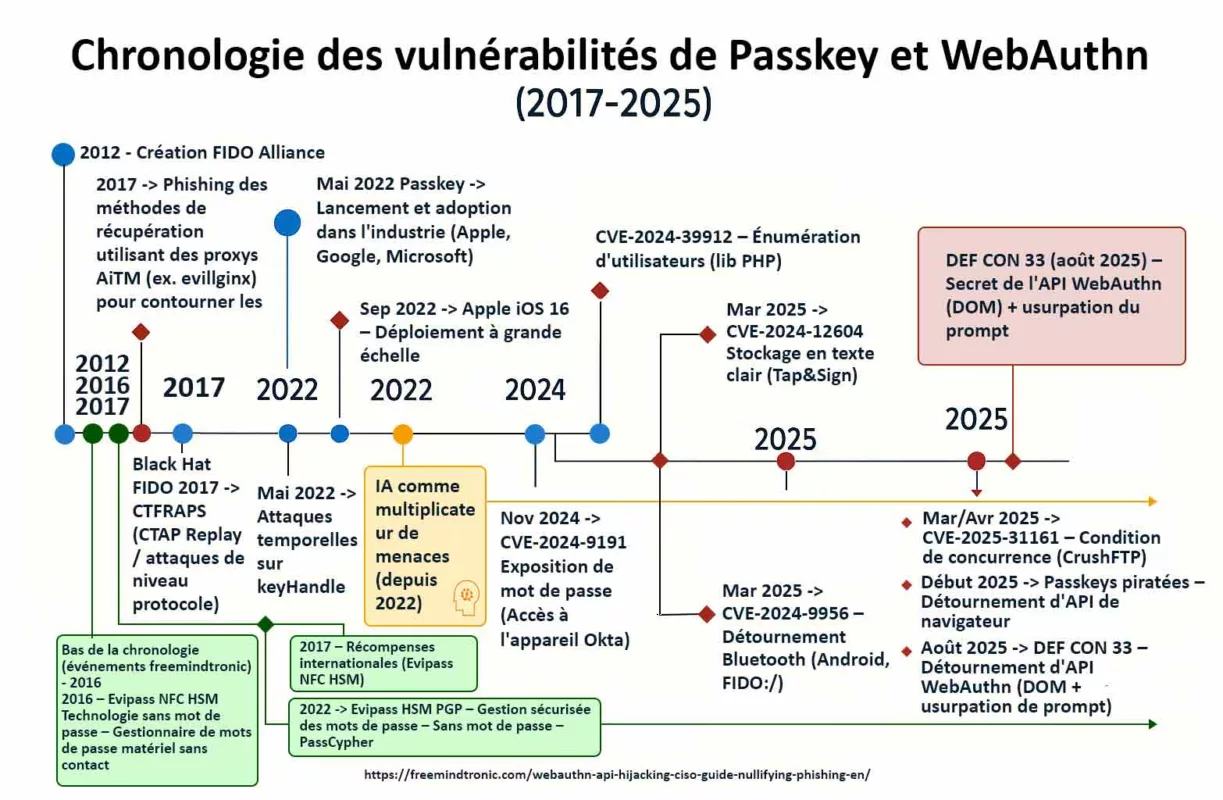
Des chercheurs académiques affiliés à l’ETH Zurich et à l’USI ont analysé la robustesse du modèle zero-knowledge implémenté dans plusieurs gestionnaires de mots de passe majeurs. L’objectif n’était pas de casser les primitives cryptographiques, mais d’examiner comment des attaques par downgrade peuvent exploiter des couches de compatibilité historique.
Constat principal
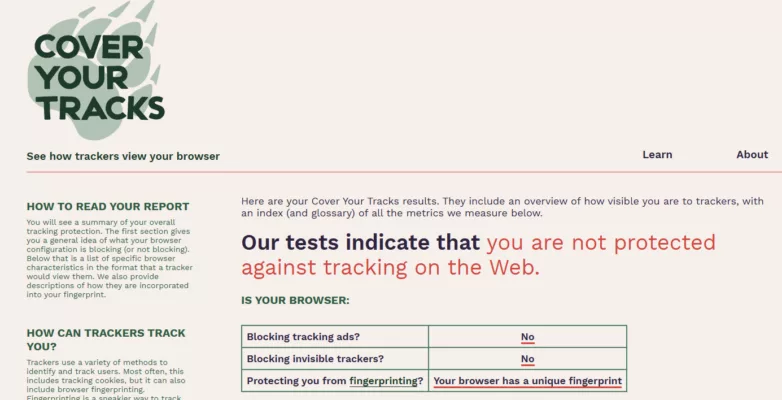
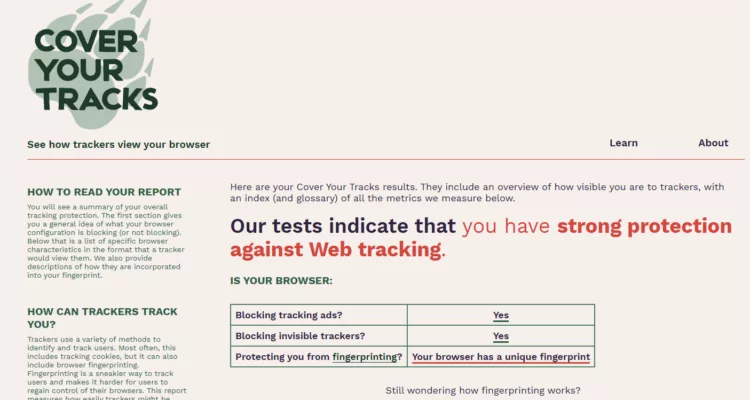
Le principe zero-knowledge reste valide sur le plan cryptographique. Toutefois, sa résilience effective dépend d’une gouvernance stricte des paramètres et de l’impossibilité pour un serveur compromis d’imposer une négociation dégradée.
Périmètre
L’étude porte sur Bitwarden, LastPass et Dashlane. Elle met en évidence comment certaines configurations historiques de PBKDF2 et la rétrocompatibilité peuvent réduire la résistance au brute force sous hypothèse de compromission serveur.
Implication doctrinale
Le zero-knowledge protège contre une compromission passive. Il ne protège pas intrinsèquement contre une manipulation active du protocole si le client accepte des paramètres affaiblis.
Différenciateur stratégique
La maturité sécuritaire ne se mesure plus uniquement à la force du chiffrement. Elle repose sur la gouvernance des paramètres, la discipline des versions et l’élimination des chemins de négociation descendante. Le débat se déplace ainsi de « est-ce chiffré ? » vers « qui contrôle le plancher cryptographique ? ».
Point essentiel
Le modèle zero-knowledge n’est pas cassé.
Il devient structurellement fragile lorsque la rétrocompatibilité permet à un serveur d’imposer des paramètres KDF affaiblis.
La résilience réelle exige une validation stricte côté client, un plancher d’itérations minimum et l’élimination de toute négociation descendante.
Note technique
Temps de lecture (résumé) : ~3 minutes
Temps de lecture complet : ~28–32 minutes
Date de publication : 2026-02-18
Niveau : Cryptographie / Audit / Architecture de sécurité
Posture : Gouvernance zero-knowledge & résilience au downgrade
Catégorie : Digital Security
Langues disponibles : · FR · EN
Niveau d’impact : 9.1 / 10 — modèle de confiance & gouvernance cryptographique
En cybersécurité et architecture numérique, cette analyse appartient à la catégorie Digital Security directement accessible dans le slider ci-dessus ↑ Elle s’inscrit dans la continuité des travaux de Freemindtronic sur la souveraineté cryptographique, le contrôle utilisateur et les architectures résilientes.
- Résumé exécutif
- Pourquoi un zero-knowledge peut devenir vulnérable
- Attaques par downgrade : principe technique
- Analyse par produit
- Lecture systémique d’un zero-knowledge vulnérable
- Modèle de menace d’un zero-knowledge vulnérable
- Synthèse du modèle de menace
- Signaux stratégiques d’un zero-knowledge vulnérable
- Signal fort
- Signal moyen
- Signal faible
- Limites et clarifications
- Impact utilisateur
- Ce que cela ne signifie pas
- Contre-mesures structurelles
- Durcissement logiciel
- Validation côté client
- Architecture souveraine
- Comparaison architecturale
- Alternative à un zero-knowledge vulnérable
- Principe cryptographique
- Génération et protection des segments
- Chiffrement en RAM uniquement
- Authentification segmentée brevetée
- Références officielles
- Évolution doctrinale du modèle zero-knowledge
- Perspective stratégique
- FAQ — Zero-knowledge vulnérable
- Glossaire
Pourquoi un zero-knowledge peut devenir vulnérable
Définition synthétique : Un modèle zero-knowledge devient vulnérable lorsqu’un serveur peut influencer ou dégrader les paramètres cryptographiques acceptés par le client. La faille ne concerne pas l’algorithme de chiffrement lui-même, mais la possibilité structurelle d’une négociation descendante affaiblissant la robustesse effective.
Un zero-knowledge devient vulnérable lorsqu’un serveur peut influencer ou dégrader les paramètres cryptographiques utilisés par le client.
La vulnérabilité ne provient pas du chiffrement lui-même, mais de la négociation descendante autorisée par l’architecture.
Le modèle zero-knowledge repose sur un principe simple : le serveur ne possède jamais la clé de déchiffrement.
Dans sa version idéale :
- La clé est dérivée du mot de passe maître via PBKDF2 / Argon2
- Le serveur stocke uniquement des données chiffrées
- Le déchiffrement s’effectue côté client
Ce modèle protège contre :
- Employé malveillant
- Compromission serveur passive
Il ne protège pas contre :
- Manipulation active du protocole
- Downgrade vers un schéma affaibli
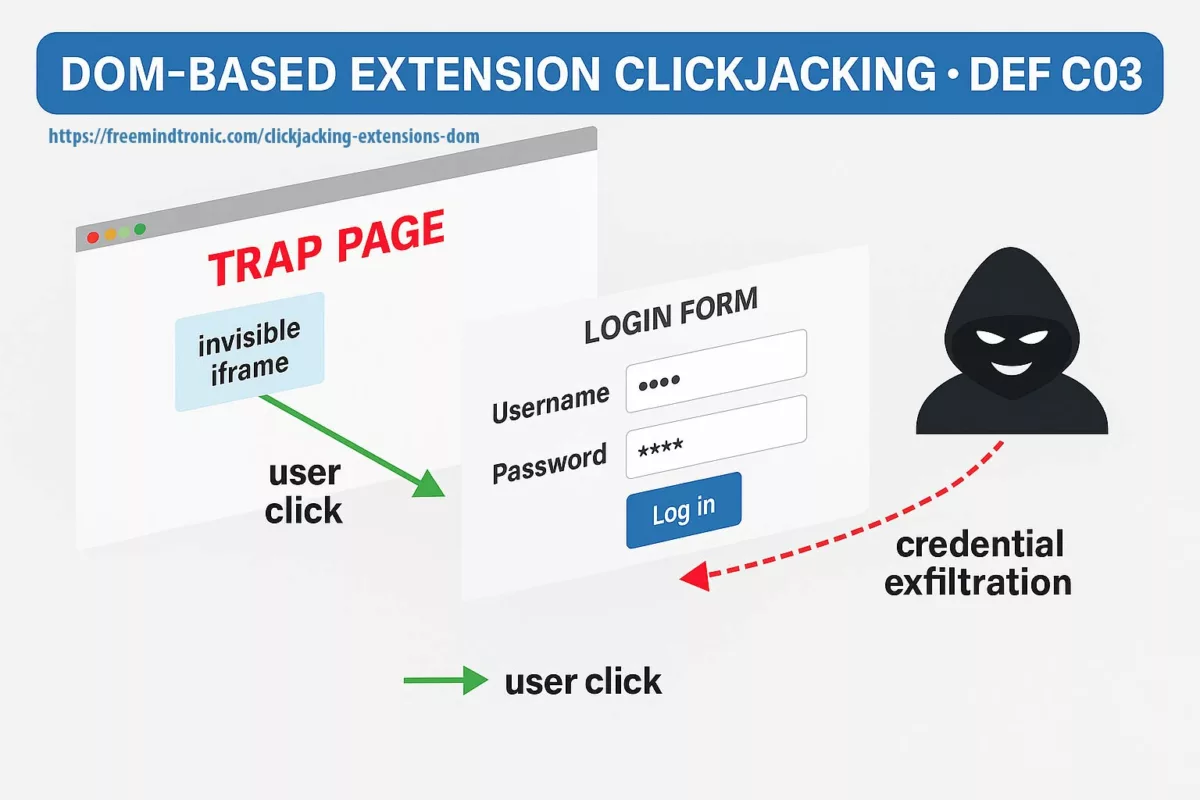
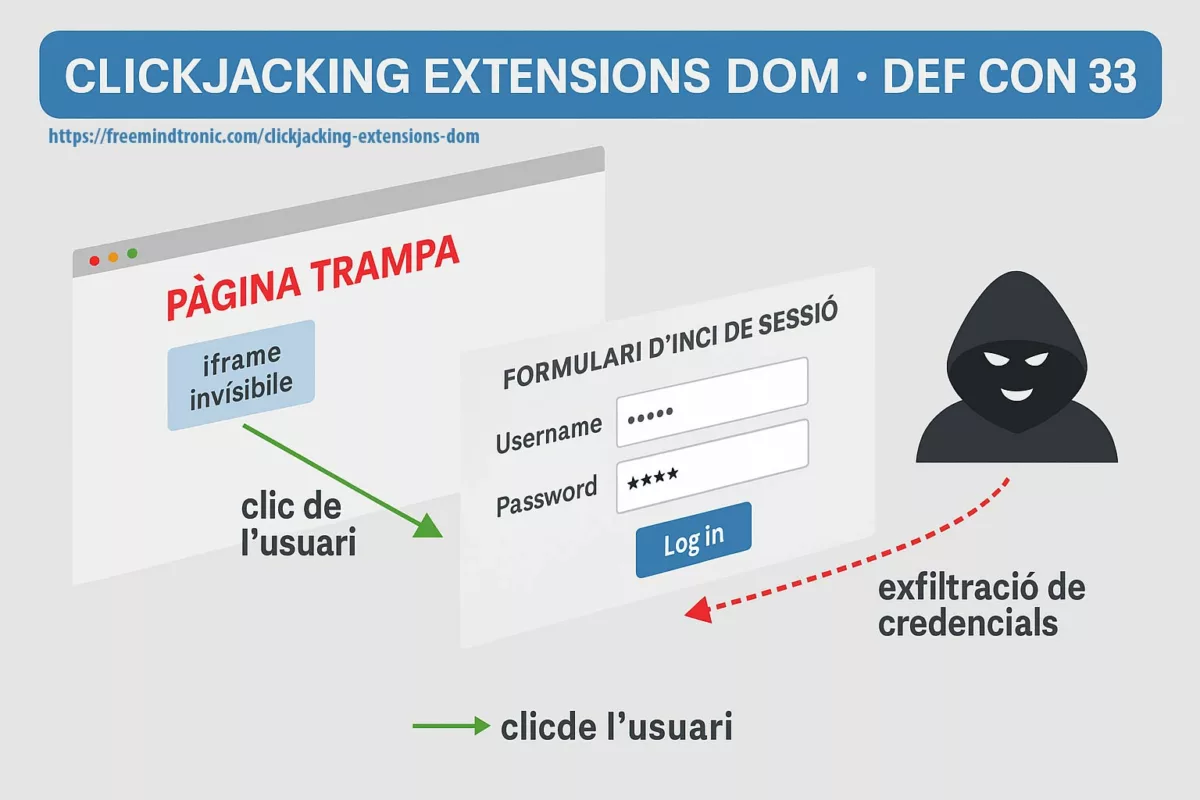
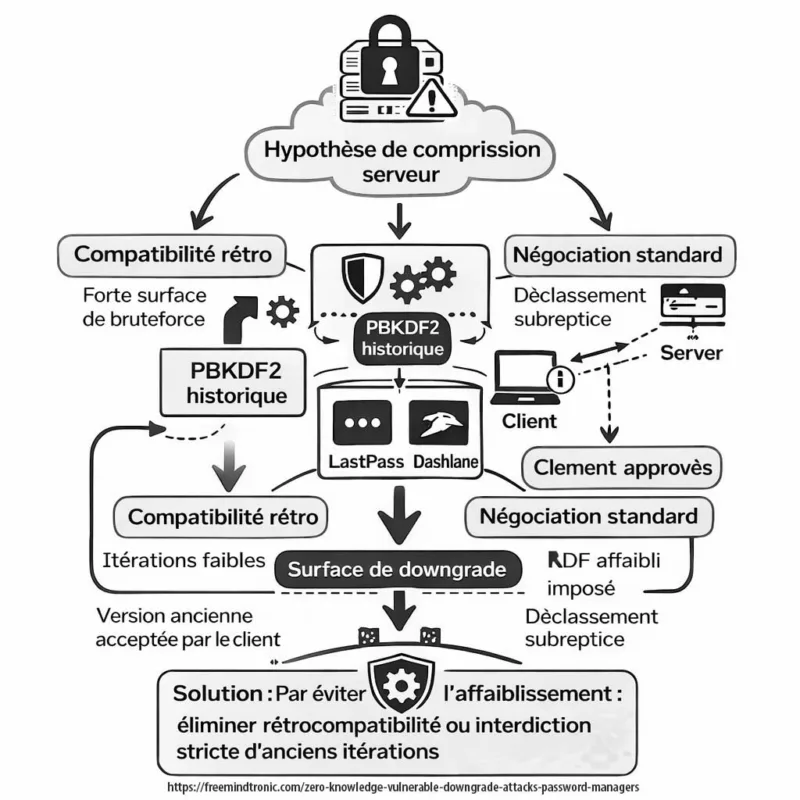
Attaques par downgrade : principe technique
Une downgrade attack consiste à forcer une application à utiliser une version antérieure et moins robuste d’un protocole cryptographique.
Dans le cas étudié :
| Étape | Description | Conséquence |
|---|---|---|
| 1 | Compromission serveur | Contrôle des réponses API |
| 2 | Forçage d’anciens paramètres KDF | Affaiblissement de la dérivation |
| 3 | Attaque brute force optimisée | Extraction d’identifiants |
Le problème central : la rétrocompatibilité conserve des paramètres cryptographiques historiquement plus faibles.
Analyse par produit
Tableau de synthèse :
| Gestionnaire | Modèle KDF | Surface downgrade | Mesures correctives |
|---|---|---|---|
| Bitwarden | PBKDF2 configurable | Paramètres historiques activables | Augmentation itérations & plancher minimum |
| LastPass | PBKDF2 (comptes legacy) | Itérations anciennes sur coffres historiques | Migration forcée & élévation paramètres |
| Dashlane | Architecture propriétaire | Compatibilité génération antérieure | Durcissement progressif des configurations |
Important : Les chercheurs ont informé les éditeurs avant publication. Les vulnérabilités identifiées ont donné lieu à des mesures de durcissement (augmentation des itérations, élévation des paramètres minimum, recommandations de migration). Toutefois, la surface de downgrade liée à la rétrocompatibilité ne peut être totalement supprimée sans rompre la compatibilité avec certains coffres historiques. La contrainte structurelle observée est liée au maintien de la compatibilité avec des coffres historiques, et non à une défaillance de l’algorithme cryptographique lui-même.
L’étude académique porte uniquement sur trois gestionnaires : Bitwarden, LastPass et Dashlane. Ensemble, ces services représentent plusieurs dizaines de millions d’utilisateurs dans le monde. Les conclusions ne peuvent toutefois pas être généralisées à toutes les implémentations zero-knowledge. La recherche démontre un risque structurel sous hypothèse de compromission serveur, et non un scénario d’exploitation massive avéré.
Lecture systémique d’un zero-knowledge vulnérable
Ce cas révèle trois tensions structurelles :
- Innovation vs compatibilité
- Marketing zero-knowledge vs réalité opérationnelle
- Sécurité cloud vs dépendance serveur
Le zero-knowledge n’est pas faux.
Il est dépendant de la gouvernance cryptographique.
Tant qu’un serveur peut imposer des paramètres, il influence la robustesse effective. Cela ne signifie pas que l’ensemble des gestionnaires de mots de passe seraient vulnérables. Cette observation met en lumière une tension architecturale générale entre rétrocompatibilité et enforcement strict du plancher cryptographique dans les systèmes zero-knowledge médiés par le cloud.
Un zero-knowledge vulnérable ne signifie pas que l’algorithme est faible. Cela signifie que l’architecture autorise encore des chemins de négociation descendante exploitables sous certaines conditions.
Modèle de menace d’un zero-knowledge vulnérable
Le scénario étudié ne suppose pas une faille magique dans le chiffrement. Il repose sur une hypothèse structurée : compromission active du serveur ou contrôle partiel de l’infrastructure API.
Dans cette architecture étudiée :
- L’attaquant contrôle les réponses serveur
- Il peut imposer des paramètres KDF historiques
- Le client accepte ces paramètres s’ils restent valides
- Une attaque hors-ligne devient économiquement plus accessible
Il ne s’agit pas d’une attaque opportuniste grand public. Il s’agit d’un scénario ciblé, post-compromission, nécessitant contrôle serveur ou interception active.
Point clé : le risque apparaît uniquement si le client accepte une négociation descendante. Sans acceptation côté client, le downgrade échoue.
Synthèse du modèle de menace
Tableau de synthèse :
| Condition | Nécessaire pour l’attaque | Impact |
|---|---|---|
| Compromission serveur | Oui | Imposition paramètres affaiblis |
| Acceptation client | Oui | Ouverture surface brute force |
| Exploitation massive | Non observée | Scénario ciblé |
Signaux stratégiques d’un zero-knowledge vulnérable
🔴 Signal fort
- La rétrocompatibilité devient une surface d’attaque structurelle.
- La gouvernance des paramètres cryptographiques est désormais un enjeu de sécurité stratégique.
- Le marketing “zero-knowledge absolu” doit intégrer la question des paramètres négociables.
🟠 Signal moyen
- Les comptes anciens ou mal configurés sont plus exposés.
- La migration vers Argon2id devient prioritaire.
- Les politiques de minimum d’itérations doivent être durcies.
🟢 Signal faible
- Aucune exploitation massive observée publiquement.
- Réaction rapide et transparente des éditeurs concernés.
- Les primitives cryptographiques restent solides.
Lecture globale : il ne s’agit pas d’un effondrement du modèle zero-knowledge, mais d’un rappel que la sécurité dépend de la discipline d’implémentation.
Limites et clarifications sur le modèle zero-knowledge vulnérable
Il est essentiel de préciser le périmètre exact de cette analyse.
- Le scénario repose sur une hypothèse de compromission serveur active.
- Aucune exploitation massive publique n’a été documentée.
- Les éditeurs concernés ont réagi et renforcé leurs paramètres.
- Le risque dépend du modèle de menace adopté.
La recherche met en évidence une tension architecturale structurelle, et non une compromission généralisée des gestionnaires de mots de passe zero-knowledge.
Impact concret pour l’utilisateur face à un zero-knowledge vulnérable
Pour un utilisateur final, le risque dépend principalement de la configuration du compte et du niveau de durcissement appliqué.
Recommandations pratiques
- Vérifier le nombre d’itérations PBKDF2 ou l’activation d’Argon2id.
- Augmenter le plancher d’itérations si configurable.
- Utiliser un mot de passe maître long et aléatoire.
- Mettre à jour les comptes anciens configurés avec des paramètres historiques.
Un compte correctement configuré avec des paramètres modernes réduit fortement le risque théorique lié à une attaque par downgrade.
Ce que cela ne signifie pas
- Que le chiffrement AES ou PBKDF2 serait cassé
- Que tous les gestionnaires zero-knowledge sont compromis
- Qu’une exploitation massive est en cours
- Que le modèle zero-knowledge est obsolète
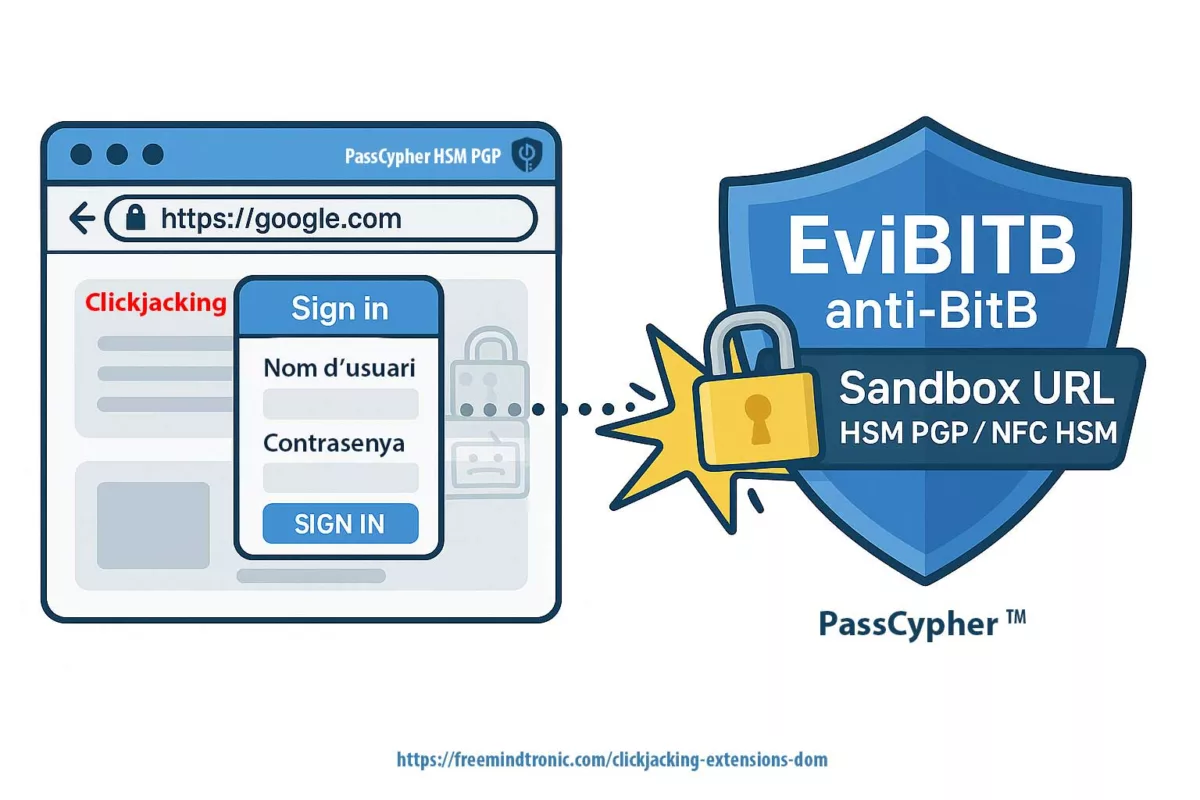
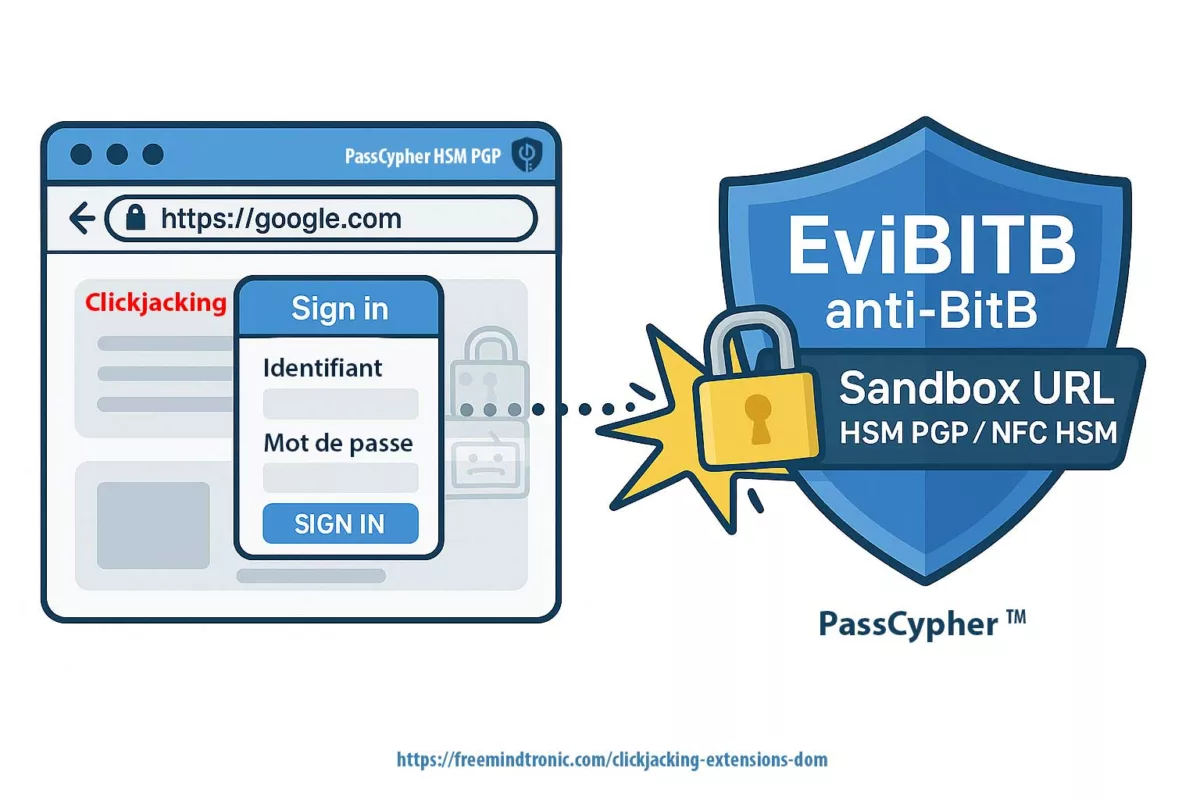
Contre-mesures structurelles
Face à un scénario de zero-knowledge vulnérable, la réponse ne consiste pas uniquement à renforcer les algorithmes, mais à supprimer les surfaces de négociation serveur.
Trois niveaux de mitigation :
1 — Durcissement logiciel
- Forcer paramètres minimum
- Désactiver anciens schémas
- Argon2id obligatoire
2 — Validation côté client
- Refus paramètres faibles
- Version locking cryptographique
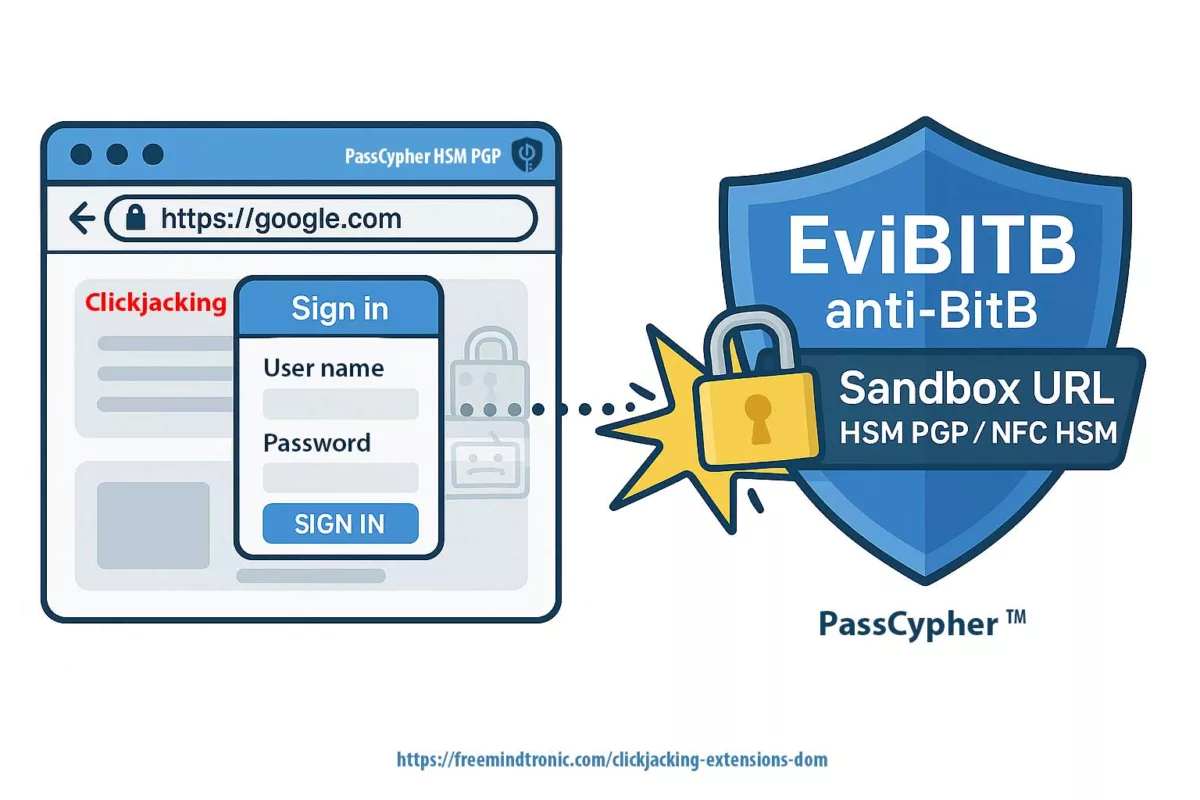
3 — Architecture souveraine
- Secrets hors navigateur
- HSM offline
- Aucune négociation serveur
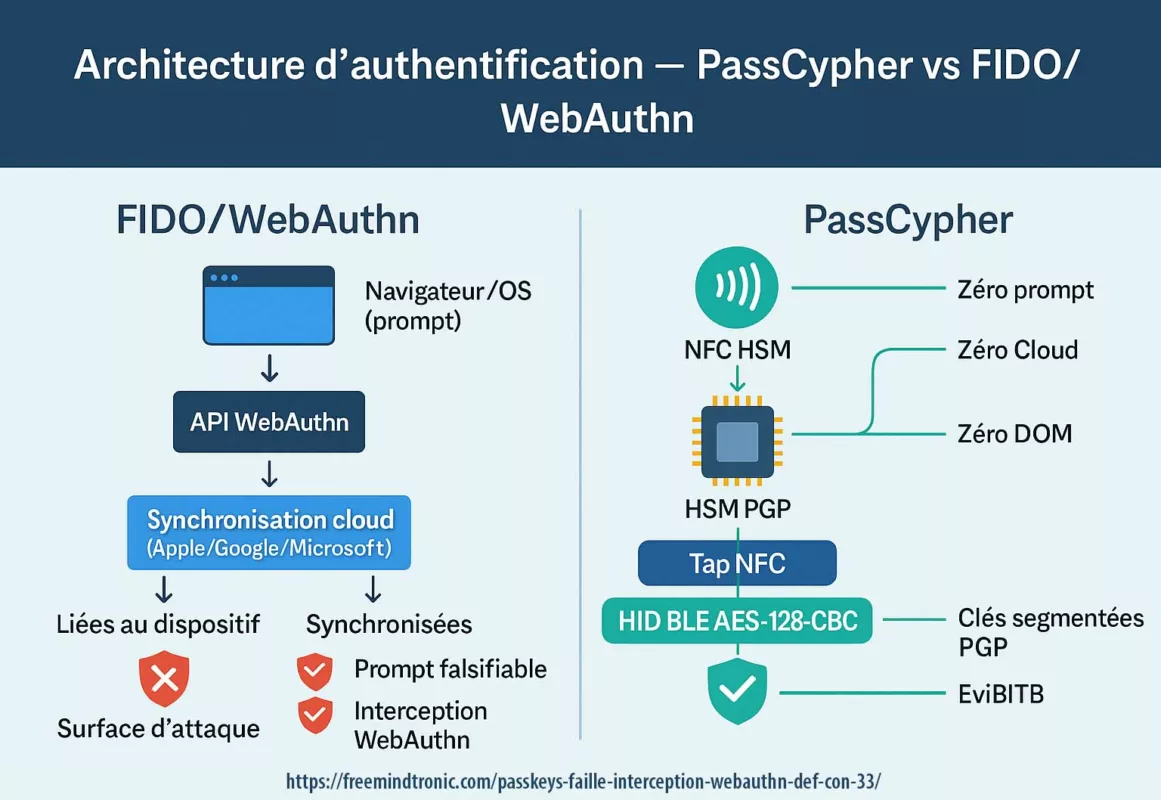
Comparaison architecturale : zero-knowledge vs architecture segmentée
Tableau de synthèse :
| Critère | Modèle zero-knowledge cloud | Architecture PassCypher segmentée |
|---|---|---|
| Clé maîtresse | Oui (mot de passe maître) | Aucune clé maîtresse centrale |
| Dérivation KDF | Négociable selon version | Aucune négociation serveur |
| Dépendance serveur | Oui | Non |
| Surface downgrade | Possible si rétrocompatibilité | Inexistante |
| Persistance en clair | Non prévue mais dépend implémentation | RAM uniquement |
| Point central de défaillance | Serveur / identité | Aucun |
Alternative à un zero-knowledge vulnérable : centralisation sans SSO et clés segmentées
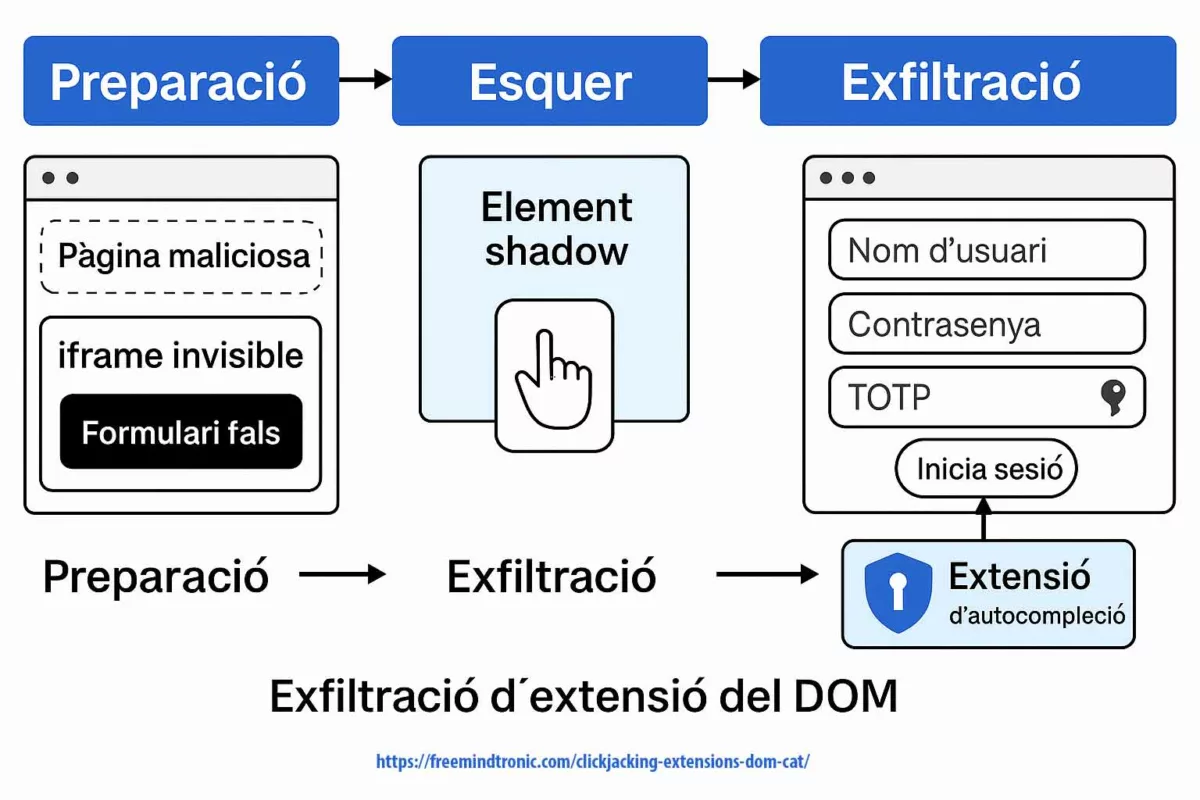
Contrairement aux architectures cloud classiques, PassCypher HSM PGP permet une centralisation volontaire sans serveur d’identité, sans SSO et sans clé maître globale.
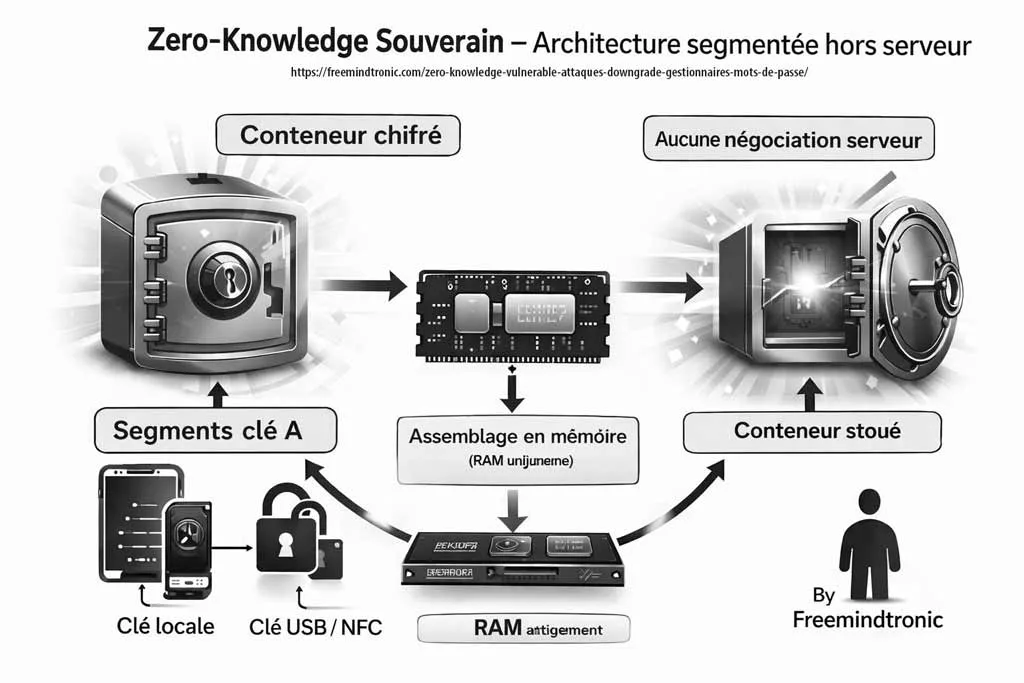
Le principe repose sur des clés segmentées autonomes combinables à la discrétion de l’utilisateur.
Principe cryptographique
Le système peut utiliser, par exemple :
- Deux segments de clé indépendants de 256 bits
- Stockés séparément (ex. stockage local + clé USB)
- Assemblés dynamiquement par concaténation
La concaténation de deux clés de 256 bits produit un espace de combinaison de :
2²⁵⁶ × 2²⁵⁶ = 2⁵¹² combinaisons possibles
Soit environ :
1,34 × 10¹⁵⁴ combinaisons
Ce nombre dépasse largement toute capacité réaliste d’attaque exhaustive.
Génération et protection des segments
Chaque segment de clé est :
- Généré de manière aléatoire par un générateur cryptographiquement sûr
- Indépendant des autres segments
- Chiffré au repos lorsqu’il est stocké
Il ne s’agit donc pas d’un simple découpage d’une clé maîtresse.
Chaque segment possède sa propre entropie complète (256 bits par segment dans l’exemple décrit).
Même isolé, un segment reste mathématiquement impraticable à deviner.
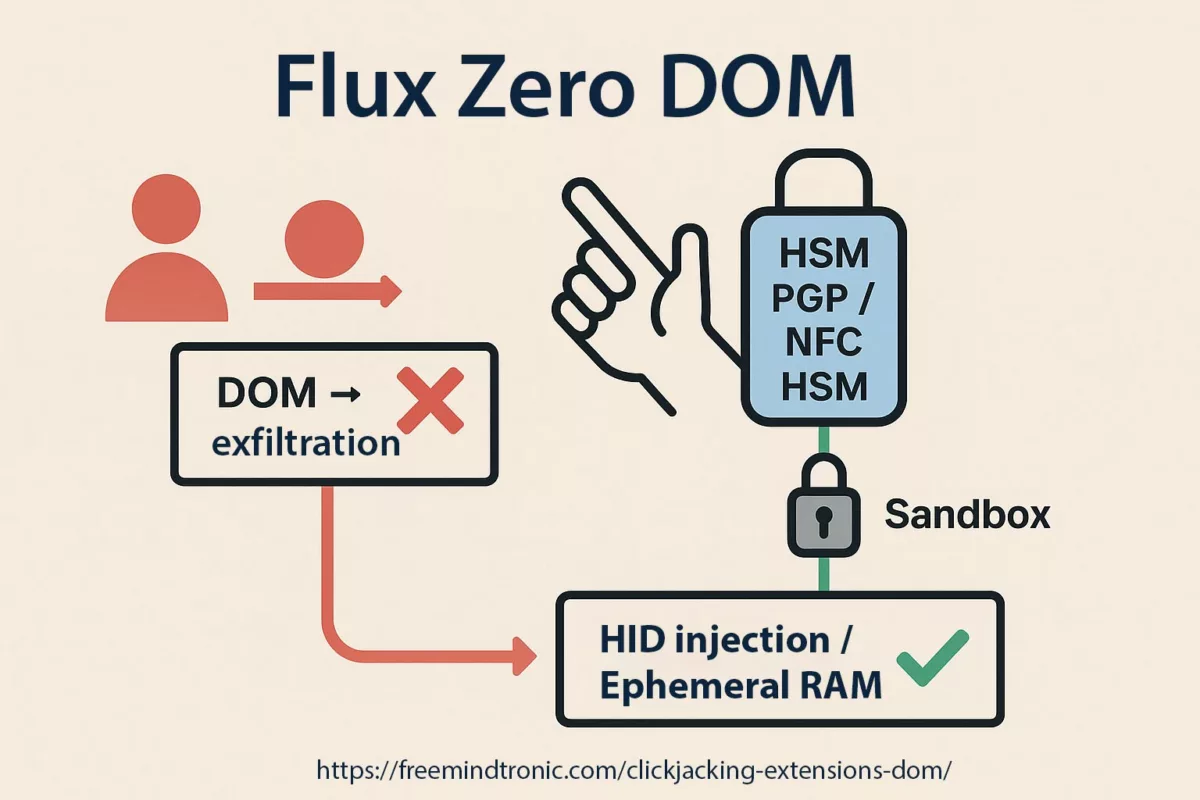
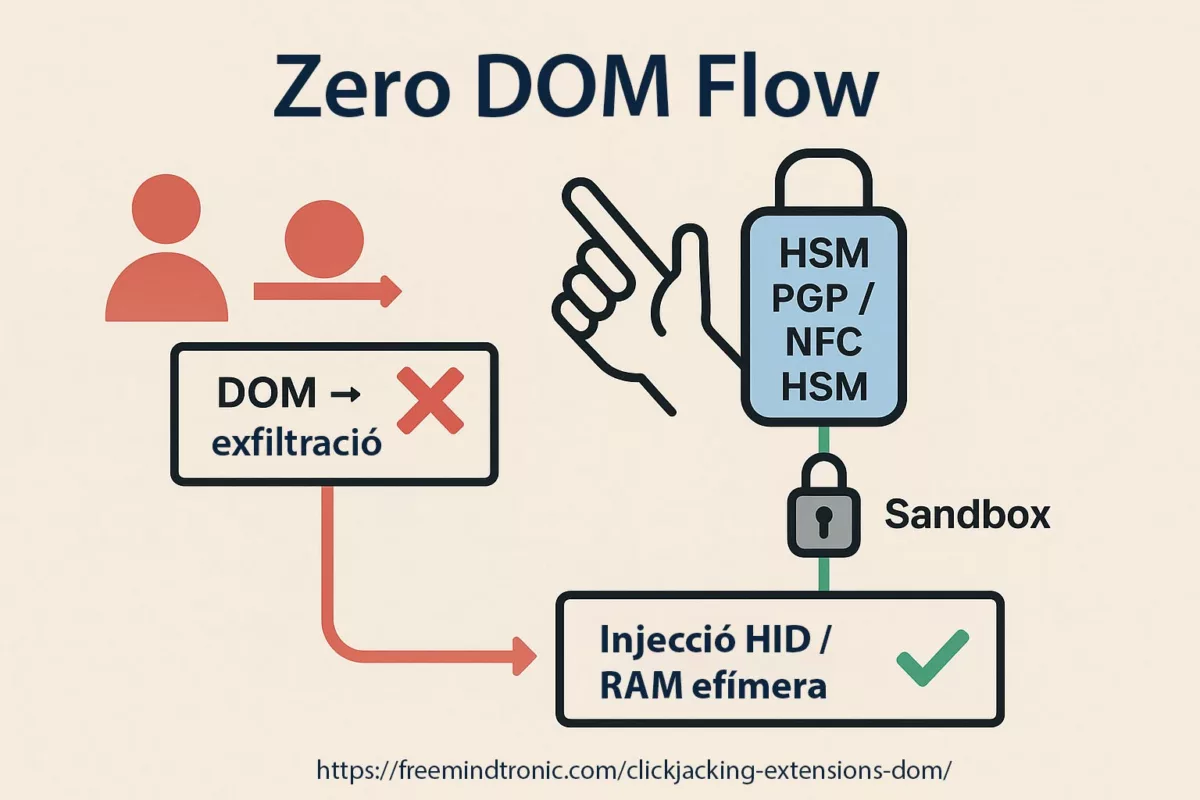
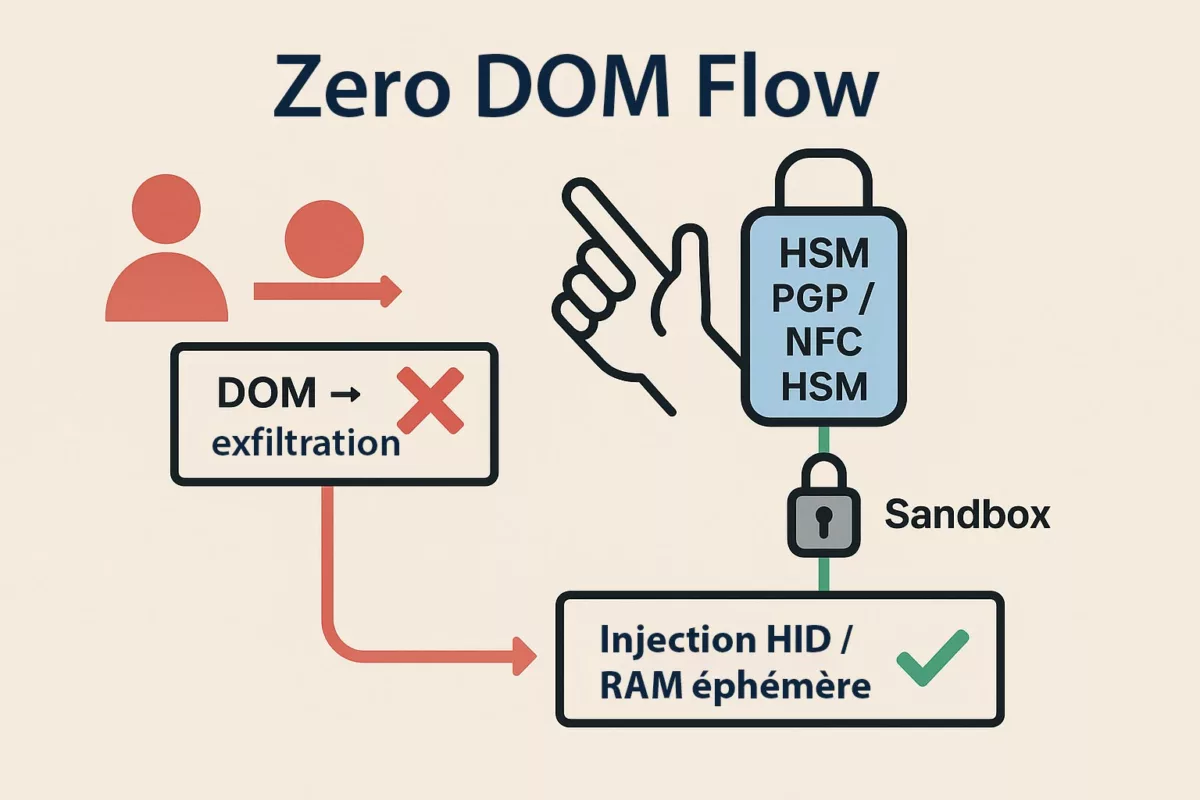
Chiffrement et déchiffrement en RAM uniquement
Dans l’architecture PassCypher, le chiffrement et le déchiffrement s’effectuent exclusivement en mémoire volatile (RAM), et uniquement pendant la durée strictement nécessaire à l’auto-connexion.
Cela signifie :
- Aucun secret en clair n’est écrit sur disque
- Aucune donnée déchiffrée n’est persistée
- Les conteneurs restent chiffrés au repos en permanence
- La clé complète n’existe que temporairement en mémoire
Ce fonctionnement est identique :
- Sur smartphone Android via NFC
- Sur ordinateur Windows
- Sur macOS
Une fois l’opération terminée :
- La mémoire est libérée
- La clé concaténée disparaît
- Le conteneur reste chiffré
Conséquence sécuritaire
Ce modèle réduit considérablement :
- Le risque d’extraction par analyse disque
- Le risque lié aux sauvegardes involontaires
- La persistance accidentelle de secrets
La fenêtre d’exposition est limitée à la durée d’exécution en mémoire.
Dans une architecture cloud classique, des éléments critiques transitent par des couches serveur, stockage distant ou synchronisation.
Dans le modèle PassCypher, le secret n’existe en clair qu’en mémoire volatile et uniquement le temps strictement nécessaire à l’action utilisateur.
Protection par brevet international — authentification à clé segmentée
L’architecture d’authentification à clés segmentées utilisée par PassCypher HSM PGP fait l’objet d’une protection par brevet international.
Ce brevet couvre le principe suivant :
- Segments de clés générés aléatoirement et indépendants
- Segments stockés séparément et protégés
- Assemblage dynamique par concaténation locale
- Absence de clé maîtresse centralisée
- Absence de dépendance serveur ou SSO
Le mécanisme d’authentification ne repose donc pas sur une identité centralisée, mais sur la possession et la combinaison correcte de segments cryptographiques autonomes.
Différence fondamentale
Dans les architectures classiques :
- L’authentification repose sur un mot de passe maître
- Ou sur un serveur d’identité
- Ou sur une fédération SSO
Dans l’architecture brevetée PassCypher :
- L’authentification est purement cryptographique
- Elle est indépendante d’un tiers de confiance
- Elle repose sur la combinaison volontaire de segments aléatoires
La protection par brevet ne porte pas sur l’algorithme AES-256-CBC lui-même, qui est un standard ouvert, mais sur l’architecture d’authentification segmentée et son mode opératoire hors ligne.
Architecture sans clé maîtresse
Le modèle PassCypher ne repose sur :
- Aucune clé maîtresse centrale
- Aucune clé dérivée d’un mot de passe global
- Aucune négociation serveur
- Aucune base de données centrale
La clé effective utilisée pour AES-256-CBC est construite dynamiquement par concaténation locale des segments valides.
Sans l’ensemble correct des segments :
- La clé complète ne peut être reconstituée
- Le conteneur reste chiffré en permanence
- Aucune information partielle exploitable n’est exposée
Conséquence stratégique
Dans une architecture cloud classique :
- La sécurité dépend d’un mot de passe maître
- La dérivation dépend d’un KDF négociable
- Le serveur influence potentiellement les paramètres
Dans l’architecture segmentée :
- Il n’existe pas de secret unique à forcer
- Il n’existe pas de paramètre négociable
- Il n’existe pas de point central de défaillance
La centralisation devient une construction volontaire fondée sur la possession physique ou logique de segments cryptographiques aléatoires, eux-mêmes protégés au repos.
Ce modèle élimine la surface d’attaque par downgrade liée à la négociation serveur.
Fonctionnement opérationnel
- Les conteneurs restent chiffrés en permanence
- Aucune base centrale ne détient les clés
- Aucun serveur ne valide l’accès
- La combinaison correcte des segments permet l’ouverture
PassCypher réalise la concaténation localement en mémoire vive uniquement pour chiffrer et déchiffrer les conteneurs protégés en AES-256-CBC.
Contrôle d’accès par combinaison
Il devient alors possible de :
- Déployer plusieurs conteneurs
- Rendre chaque conteneur accessible à un groupe spécifique
- Définir l’accès uniquement par possession de la bonne combinaison segmentée
Aucun SSO.
Aucune fédération d’identité.
Aucun serveur d’autorisation.
L’accès est purement cryptographique.
Différence stratégique
Dans les modèles cloud :
- La centralisation dépend d’un serveur
- L’identité dépend d’un fournisseur
- La gouvernance dépend d’une infrastructure
Dans le modèle PassCypher :
- La centralisation est optionnelle
- La combinaison est maîtrisée par l’utilisateur
- La surface d’attaque distante est inexistante
La centralisation n’est plus un service. Elle devient une propriété mathématique basée sur la combinaison volontaire de segments cryptographiques. Le débat sur le zero-knowledge vulnérable marque une évolution doctrinale : la sécurité ne se mesure plus uniquement à la force mathématique du chiffrement, mais à l’impossibilité structurelle d’en négocier les paramètres.
Références officielles sur le zero-knowledge vulnérable et les KDF
Les analyses techniques s’appuient sur des standards publics et des documentations officielles :
- RFC 8018 — PKCS #5 v2.1 (PBKDF2)
- RFC 9106 — Argon2 Memory-Hard Function
- NIST SP 800-63B — Digital Identity Guidelines
- Bitwarden Security Whitepaper
- LastPass Technical Whitepaper
- Dashlane Security Architecture
- ETH Zurich — Information Security Group
- Università della Svizzera italiana (USI)
Ces documents confirment que le risque ne réside pas dans la rupture des primitives cryptographiques, mais dans la gestion des versions et paramètres.
Évolution doctrinale du modèle zero-knowledge
Le débat sur un zero-knowledge vulnérable marque une transition conceptuelle.
Pendant une décennie, la promesse était simple : le serveur ne possède pas la clé.
Aujourd’hui, la question devient plus exigeante : le serveur peut-il influencer la robustesse effective du chiffrement ?
Ce déplacement du débat est désormais observable dans la littérature académique récente : la question ne se limite plus à savoir si le serveur voit la clé, mais s’il peut influencer les paramètres cryptographiques qui conditionnent la robustesse effective du chiffrement
(RFC 9106 – Argon2 Memory-Hard Function, arXiv:2504.17121 – Evaluating Argon2 Adoption, Springer – Optimal Argon2 Parameters). Cette évolution ne relève pas d’un incident isolé, mais d’un changement progressif de paradigme dans l’évaluation des architectures zero-knowledge médiées par le cloud.
En parallèle, on observe un durcissement généralisé vers Argon2id memory-hard, ainsi qu’un verrouillage croissant des paramètres côté client. Les évolutions récentes tendent vers l’imposition d’un plancher cryptographique non négociable, confirmant que la résilience effective dépend désormais de l’impossibilité structurelle de négocier ou d’abaisser le plancher cryptographique.
Cette évolution déplace le centre de gravité :
- Du chiffrement vers la gouvernance des paramètres
- Du marketing vers la discipline d’implémentation
- De la promesse vers la preuve d’invariance cryptographique
Un modèle zero-knowledge devient réellement souverain lorsque :
- Les paramètres minimum sont non négociables
- La rétrocompatibilité ne permet aucune dégradation
- L’architecture empêche toute influence externe sur la dérivation
Perspective stratégique : au-delà du zero-knowledge vulnérable
Le zero-knowledge n’est pas une garantie absolue. C’est un modèle de confiance conditionnel.
Un zero-knowledge vulnérable n’est pas un échec cryptographique, mais une conséquence de choix d’architecture et de compatibilité.
Tant qu’un serveur peut influencer des paramètres cryptographiques, la résilience dépend de la discipline d’implémentation.
La souveraineté cryptographique commence lorsque :
- La négociation descendante devient impossible.
- Le plancher cryptographique est non négociable.
- Le secret n’existe jamais hors contrôle utilisateur.
Le débat n’oppose pas chiffrement et non chiffrement.
Il oppose gouvernance négociable et architecture souveraine.
À retenir
- Un zero-knowledge vulnérable n’est pas un échec du chiffrement, mais une conséquence de la rétrocompatibilité.
- Le risque apparaît uniquement sous hypothèse de compromission serveur active.
- La gouvernance des paramètres KDF devient un enjeu stratégique majeur.
- La suppression de toute négociation descendante renforce la résilience.
- Une architecture sans dépendance serveur élimine structurellement la surface de downgrade.
Glossaire
Zero-knowledge
Définition fondamentale
Modèle de sécurité dans lequel le fournisseur de service ne détient jamais les clés de déchiffrement des données utilisateur. Les opérations cryptographiques s’effectuent exclusivement côté client.
Zero-knowledge vulnérable
Qualification architecturale
Situation dans laquelle un modèle zero-knowledge reste mathématiquement solide mais devient structurellement exposé en raison d’une rétrocompatibilité ou d’une négociation descendante des paramètres cryptographiques.
Downgrade attack
Mécanisme d’attaque
Attaque consistant à forcer l’usage d’une version antérieure ou d’un paramètre cryptographique plus faible afin de réduire la résistance au brute force ou à l’analyse hors ligne.
KDF (Key Derivation Function)
Fonction de dérivation
Algorithme transformant un mot de passe en clé cryptographique via des paramètres contrôlés (itérations, mémoire, parallélisme). La robustesse dépend directement de ces paramètres.
PBKDF2
Standard historique
Fonction standardisée de dérivation de clé basée sur des itérations répétées. Sa sécurité dépend principalement du nombre d’itérations configuré.
Argon2id
Standard moderne
Fonction moderne de dérivation de clé résistante aux attaques GPU et ASIC grâce à son approche memory-hard.
Rétrocompatibilité cryptographique
Contraintes de version
Maintien de la compatibilité avec des paramètres ou configurations anciennes afin de préserver l’accès aux comptes historiques, pouvant introduire une surface de downgrade.
Négociation descendante
Processus de dégradation
Acceptation par le client de paramètres cryptographiques inférieurs à un plancher moderne, ouvrant potentiellement une surface d’attaque.
Compromission serveur active
Scénario de menace
Situation dans laquelle un attaquant contrôle ou manipule les réponses du serveur afin d’influencer le comportement cryptographique du client.
Architecture souveraine
Principe d’indépendance
Architecture dans laquelle les secrets, les clés et les paramètres cryptographiques restent sous contrôle exclusif de l’utilisateur, sans dépendance serveur négociable.
Clés segmentées
Mécanisme d’authentification
Génération de segments de clés indépendants combinés dynamiquement en mémoire locale afin d’éviter l’existence d’une clé maîtresse centralisée.
FAQ — Zero-knowledge vulnérable
Un modèle zero-knowledge est-il cassé par une attaque par downgrade ?
Non le zero-knowledge n’est pas cassé, pourquoi !
Le chiffrement lui-même n’est pas cassé. En effet, le risque apparaît lorsque la rétrocompatibilité permet à un serveur compromis d’imposer des paramètres KDF historiquement plus faibles acceptés par le client. De fait, le problème relève donc de la gouvernance des paramètres, et non de la rupture des primitives cryptographiques.
Qu’est-ce qu’une attaque par downgrade dans un gestionnaire de mots de passe ?
Comprendre le mécanisme en pratique
Concrètement, une attaque par downgrade consiste à forcer l’utilisation d’anciens paramètres cryptographiques afin de réduire la résistance au brute force. Autrement dit, l’attaquant cherche à faire fonctionner le système avec un niveau de sécurité historiquement plus faible. Toutefois, un tel scénario suppose une compromission active du serveur ou une manipulation des réponses API.
Tous les gestionnaires zero-knowledge sont-ils concernés ?
Remettre le périmètre en perspective
Non, et il est important de le préciser. L’analyse porte sur un périmètre précis et ne permet pas de généraliser à toutes les implémentations zero-knowledge. En réalité, le risque dépend étroitement de l’architecture retenue, du contrôle des paramètres et du modèle de menace considéré.
Pourquoi la rétrocompatibilité peut-elle devenir une surface d’attaque ?
Une conséquence indirecte de la continuité technique
À première vue, la rétrocompatibilité est une bonne pratique puisqu’elle garantit l’accès aux comptes historiques. Cependant, elle conserve parfois des paramètres cryptographiques plus anciens. Dès lors, si ces paramètres restent activables, ils peuvent constituer une surface de downgrade sous certaines conditions de compromission active.
Pourquoi une architecture sans négociation serveur n’entre-t-elle pas dans ce périmètre ?
Une différence structurelle déterminante
Dans une architecture sans négociation serveur, l’assemblage des clés s’effectue localement en mémoire volatile. Par conséquent, aucune influence externe ne peut modifier les paramètres cryptographiques. En supprimant toute négociation descendante, la surface d’attaque par downgrade est éliminée par conception.
Que doit vérifier un utilisateur pour réduire son exposition ?
Des mesures simples mais essentielles
Avant tout, il convient de vérifier le nombre d’itérations PBKDF2 ou l’activation d’Argon2id. Ensuite, si cela est possible, il est recommandé d’augmenter les paramètres minimum et d’utiliser un mot de passe maître long et aléatoire. Ainsi, une configuration moderne réduit fortement le risque théorique lié à une attaque par downgrade.