brute force attacks by Jacques Gascuel: This article will be updated with any new information on the topic.
Everything You Need to Know About Brute-force Attacks
80% of cyberattacks are brute force attacks. This technique tests all combinations to find a system’s password, key, or URL. These attacks threaten the security of your data. How to protect yourself? What tools and practices should be adopted? This article explains.
2026 Digital Security
February 21, 2026
2026 Digital Security
February 21, 2026
2026 Digital Security
February 18, 2026
2026 Digital Security
January 23, 2026
2026 Digital Security
January 17, 2026
2026 Digital Security
January 8, 2026
2026 Digital Security
January 7, 2026
2025 Digital Security
January 6, 2026
Brute-force Attacks: A Comprehensive Guide to Understand and Prevent Them
Brute Force: danger and protection 80% of cyberattacks are brute force attacks. This technique tests all combinations to find the password, key, URL or hash of a system. These attacks threaten the security of your data. How to protect yourself? What tools and practices to adopt? This article explains:
- Brute force types and methods : they vary according to the hackers’ method, the intrusion level and the application domain.
- Brute force on electronic components : physical or electrical techniques are used to target chips or boards.
- Brute force on passwords, keys, URLs and hashes : software or network techniques are used to access websites, online accounts, encrypted files, etc.
- Brute force on phone systems : code or key techniques are used to hack landlines, mobiles or VoIP services.
- Protection from brute force on devices and domains : encryption, authentication, masking, verification or correction techniques can help you strengthen your security.
- Resistance evaluation of products or services to brute force : a scoring model based on the attack type and severity can help you assess the risk.
Types and Methods of Brute-force Attacks
There are several types and methods of brute force attacks, depending on the hackers’ method, the level of intrusion, and the domain of application.
Hackers’ Method
Hackers can use different methods to perform brute force attacks, depending on the type of data they want to obtain or modify. Here are the most common ones:
- Simple brute force attacks: hackers try to guess the password of a user without using software, based on personal information or common passwords. These attacks work against users who have weak and easy-to-guess passwords, such as “password”, “1234567890”, or “qwerty”.
- Dictionary attacks: hackers use software that tries passwords from a predefined list of common words, such as those from a dictionary or a database. These attacks are faster than simple ones but less effective against complex and random passwords.
- Hybrid brute force attacks: hackers combine the previous two methods by adding variations to the dictionary words, such as numbers, symbols, or capital letters. These attacks are more sophisticated and can crack more robust passwords but they take more time and resources.
- Reverse brute force attacks: hackers target the username rather than the password, assuming that the password is easier to guess or obtain by other means. These attacks are useful to access accounts that use the same username on multiple sites or services.
- Distributed brute force attacks: hackers use multiple computers or devices connected to the Internet to perform brute force attacks simultaneously on the same target. These attacks are more powerful and harder to detect because they distribute the load and avoid security measures such as attempt limits or IP blocks.
- Non-invasive faster than brute force attacks: hackers exploit weaknesses in the design or implementation of a system to reduce the number of combinations to test to find a secret information. For example, they can use a technique called “side-channel cube attack” to break AES encryption in less than 10 minutes with a laptop.
- Analogous attacks: hackers use methods similar to brute force attacks but that do not test all possible combinations. For example, they can use a technique called “binary search attack” to guess a PIN code in less than 20 tries by exploiting the system’s response (correct/incorrect).
Level of Intrusion
Brute force attacks can also be classified according to the level of intrusion they involve:
- Invasive attacks: hackers access physically the system or device they want to hack, using for example a keyboard, a USB stick, or a cable. These attacks are more dangerous because they can bypass software or network protections but they require proximity with the target and a risk of being caught.
- Non-invasive attacks: hackers do not need to access physically the system or device they want to hack; they do it remotely via Internet or wireless network. These attacks are more discreet and easier to perform but they can be blocked by firewalls, antivirus software or secure protocols.
Domain of Application
Hackers’ objectives and motivations determine the domains where they apply brute force attacks. Here are some examples:
- The civil domain: Hackers use brute force attacks to access personal or professional accounts such as emails, social networks, online banks or cloud services. They can steal sensitive information, impersonate identities, extort money or harm the reputation of the victims.
- The defense domain: Hackers compromise national or international security by targeting military, governmental or diplomatic systems with brute force attacks. They can spy, sabotage, destabilize or provoke conflicts between countries.
- The ethical hacking domain: Hackers test the security of systems or devices with brute force attacks by putting themselves in the attackers’ shoes. They can identify and report flaws, improve protections or train users.
- The research domain: Hackers advance science and technology by exploring the limits of systems or devices with brute force attacks. They can discover new possibilities, innovate or create new products.
Brute-force Attacks on Electronic Components
Brute force attacks are not limited to passwords or encryption keys. They can also target electronic components that store or process data such as chips or integrated circuit boards. These attacks aim to access encrypted or protected information that is in the hardware using physical or electrical techniques.
Invasive Attacks
Invasive attacks are attacks that require direct access to the hardware and that involve modifying or destroying it. These attacks are often used to reverse engineer or extract data from chips or smart cards. Here are some examples:
- Decapsulation: this technique consists of removing the outer layer of protection of a chip to expose the silicon and the internal layers. This can be done mechanically or chemically for example with nitric acid.
- Deprocessing: this technique consists of removing progressively the internal layers of a chip to access the transistors and the connections. This can be done with chemicals lasers or focused ion beams (FIB).
- Removal of the passivation layer: this technique consists of removing the insulating layer that covers the surface of a chip to allow electrical contact with the bonding wires (the thin connections between the chip and the package).
- Reverse engineering: this technique consists of analyzing the structure and the functioning of a chip or an integrated circuit board to extract the source code the algorithms or the vulnerabilities.
- Micro-probing: this technique consists of using micro-probes (metal needles) to connect directly to the internal components of a chip or an integrated circuit board and interfere with the signals or extract data.
- Instantaneous memory attack: this technique consists of freezing a chip or an integrated circuit board to preserve the data that is in the volatile memory (RAM) after cutting off the power supply. This technique allows bypassing the mechanisms of automatic erasure of sensitive data in case of intrusion attempt.
- Securing pairing algorithms against physical attacks: this technique consists of protecting pairing algorithms which are used for identity-based encryption against physical attacks that aim to modify the behavior of the hardware. This technique uses mathematical methods to detect and correct errors induced by physical disturbances.
Non-invasive Attacks
Non-invasive attacks are attacks that do not need direct access to the hardware but that use auxiliary or hidden channels to obtain or modify data on chips or integrated circuit boards. These attacks exploit the physical characteristics of the hardware such as power consumption electromagnetic field acoustic noise or temperature. Here are some examples:
- Side-channel attack: this technique consists of measuring a physical parameter related to the functioning of a chip or an integrated circuit board to deduce information about the operations it performs or the data it processes. For example it is possible to guess an encryption key by analyzing the power consumption of a chip while it encrypts or decrypts a message.
- Fault injection attack: this technique consists of provoking an error in the functioning of a chip or an integrated circuit board by sending it an abnormal signal such as an electric pulse a light wave or ionizing radiation. This technique allows modifying the behavior of the hardware revealing hidden information or bypassing protections.
- Software flaw attack: this technique consists of exploiting a vulnerability in the software that controls the functioning of a chip or an integrated circuit board to access or modify sensitive data. For example it is possible to take control of a router by using a flaw in its firmware (the internal software that controls the functioning of the hardware).
- Hidden channel attack: this technique consists of exploiting information that is not directly related to the functioning of the targeted system such as noise temperature or time. For example it is possible to guess the PIN code of a phone by listening to the sound produced by the keys when entering it.
Brute-force Attacks on Passwords Encryption Keys Hidden URLs and Hashes
Passwords encryption keys hidden URLs and hashes are data that serve to protect access or confidentiality of information on Internet. Hackers can try to guess them using brute force attacks which consist in testing all possible combinations until they find the right one. These attacks can have serious consequences such as identity theft account hijacking message decryption or website hacking.
Attacks on Passwords
Passwords are secret codes that users enter to authenticate on a website or an online service. Hackers can try to guess them using brute force attacks simple dictionary hybrid reverse or distributed as we have seen previously. These attacks can allow hackers to access users’ accounts and steal their personal financial or
professional information. To protect themselves from these attacks, users should choose strong and unique passwords, use a password manager, enable two-factor authentication, and avoid phishing emails.
Attacks on Encryption Keys
Encryption keys are data that are used to encrypt or decrypt messages or files. They can be symmetric (the same key is used for encryption and decryption) or asymmetric (two different keys are used: a public key for encryption and a private key for decryption). Hackers can try to guess them using brute force attacks simple or distributed, by testing all possible combinations until they find the right one. These attacks can allow hackers to read or modify confidential messages or files.
To protect themselves from these attacks, users should choose long and random encryption keys, use secure encryption algorithms, do not disclose or store their encryption keys in insecure places, and use secure protocols to exchange their encryption keys with their correspondents, such as the Diffie-Hellman protocol or the SSL/TLS protocol.
Another type of brute force attack targets the data stored in the volatile memory of devices, such as computers and phones. Volatile memory is a type of memory that loses its content when the power supply is cut off. This makes it vulnerable to brute force attacks that aim to extract sensitive data from it, using physical or software techniques. In this section, we will explain what are brute force attacks on volatile memory, how they work, what are the risks and how to prevent them.
Tools for brute force attacks
There are many tools available for brute force attacks on different protocols or services. Some are used for malicious purposes, others for penetration testing or security audit. Here is a non-exhaustive list of tools for brute force attacks:
- Hashcat: Hashcat claims to be the world’s fastest and most advanced password recovery tool based on CPU. It supports five unique modes of attack for over 300 optimized hashing algorithms.
- Flipper Zero: a multifunctional device that allows you to perform brute force attacks on RFID, NFC, Bluetooth systems, etc.
- Gobuster: a tool written in Go that allows you to perform brute force attacks on web directories, DNS subdomains, S3 buckets or virtual hosts.
- BruteX: a shell-based tool that allows you to perform brute force attacks on different services such as FTP, SSH, Telnet, RDP, VNC, etc.
- Dirsearch: a tool written in Python that allows you to perform brute force attacks on web directories and files.
- Callow: a tool written in C# that allows you to perform brute force attacks on web forms.
- SSB: a tool written in Perl that allows you to perform brute force attacks on SMTP servers.
- THC-Hydra: a popular tool that allows you to perform brute force attacks on more than 50 protocols such as HTTP, HTTPS, FTP, SSH, Telnet, SMB, etc.
- Burp Suite: a suite of tools that allows you to perform penetration testing on web applications, including brute force attacks on web forms or HTTP parameters.
- Patator: a tool written in Python that allows you to perform modular brute force attacks on different services such as HTTP, FTP, SSH, SMTP, etc.
- Pydictor: a tool written in Python that allows you to generate custom lists for brute force or dictionary attacks.
- Ncrack: a tool that allows you to perform fast and flexible brute force attacks on different services such as RDP, SSH, Telnet, HTTP(S), POP3(S), etc.
Brute force attacks on volatile memory: a data security risk
Volatile memory is a type of memory that loses its content when the power supply is cut off. This is the case for the random access memory (RAM) of computers and phones, which temporarily stores data and programs that are running. Volatile memory has an advantage: it erases the traces of computer activity in case of power outage or system shutdown. But it also has a drawback: it can be targeted by brute force attacks aiming to recover the sensitive data it contains.
A brute force attack is a method that consists of testing all possible combinations of a password, an encryption key or an access code, until finding the right one. Brute force attacks can be performed using specialized software, which exploits the computing power of computers or networks of machines. Brute force attacks can take a lot of time, depending on the complexity and length of the password, key or code to guess.
Brute force attacks on volatile memory are attacks that aim to extract data stored in the RAM of a computer or a phone, using physical or software techniques. For example, it is possible to cool down the RAM with liquid nitrogen, which allows to preserve its content for a few minutes after the system shutdown. It is then possible to transfer the RAM to another device, and use a brute force software to decrypt the data it contains. It is also possible to use malicious software that infiltrates the system and accesses the RAM, bypassing software or hardware protections.
Brute force attacks on volatile memory pose a risk for data security, because they can allow hackers to access confidential information, such as passwords, encryption keys, personal or professional data, etc. These information can then be used to compromise other systems or services, or to extort the victims. To protect against these attacks, it is recommended to use passwords or keys that are long and complex enough, to encrypt data stored in the RAM, and to update software and hardware to benefit from the latest security measures.
To sum up, brute force attacks on volatile memory are a serious threat for data security, as they can allow hackers to access confidential information, such as passwords, encryption keys, personal or professional data, etc. These information can then be used to compromise other systems or services, or to extort the victims. To protect against these attacks, it is recommended to use passwords or keys that are long and complex enough, to encrypt data stored in the RAM, and to update software and hardware to benefit from the latest security measures.
Attacks on Hidden URLs
Hidden URLs are web addresses that are hidden or modified to avoid being easily accessible or identifiable. They can be used to protect the privacy or security of a website or an online service. For example, a website may use a hidden URL to prevent being indexed by search engines or targeted by hackers. Hackers can try to guess them using brute force attacks simple or distributed, by testing all possible combinations until they find the right one. These attacks can allow hackers to access hidden or forbidden websites, such as illegal, malicious, or sensitive websites.
To protect themselves from these attacks, users should choose long, complex, and random hidden URLs, do not use predictable or easy-to-guess hidden URLs, do not share or publish their hidden URLs with other people or on other websites, and use encryption or authentication techniques to enhance the security of their hidden URLs.
Attacks on Hashes
Hashes are data that result from applying a mathematical function to a message or a file. They are used to verify the integrity or authenticity of a message or a file, by comparing it to the original hash. They can also be used to store passwords securely, by transforming them into irreversible hashes. Hackers can try to guess them using brute force attacks simple, dictionary, or hybrid, by testing all possible combinations until they find the right hash. These attacks can allow hackers to falsify or reveal messages or files.
To protect themselves from these attacks, users should choose secure hashing functions that do not have collisions (two different messages that produce the same hash) or preimages (a message that produces a given hash), use salting (adding a random data to the message before hashing) or peppering (adding a secret data to the message before hashing) techniques to make hashes more resistant to brute force attacks, do not store or transmit their hashes in insecure places, and use secure protocols to exchange their hashes with their correspondents, such as the HMAC protocol or the SSL/TLS protocol.
Brute-force Attacks on Phone Systems
Phone systems are devices that allow communication by voice or text, such as landlines, mobile phones (smartphones), or VoIP services. Hackers can try to hack them using brute-force attacks that consist of guessing codes or keys. These attacks can allow hackers to access data or services of a phone system, such as contacts, messages, calls, payments, or subscriptions.
Attacks on PIN Codes
PIN codes are secret codes of four digits that are used to unlock a mobile phone or a SIM card. Hackers can try to guess them using brute force attacks simple or analogous by testing all possible combinations until they find the right one. These attacks can allow hackers to access data or services of the mobile phone or the SIM card.
To protect themselves from these attacks users should choose random and unpredictable PIN codes that do not contain numerical sequences easy to guess such as “0000” “1234” or “4321”. They should not write or share their PIN codes with other people. They should activate the function of automatic locking of the mobile phone or the SIM card after a certain number of unsuccessful attempts. They should activate the function of automatic reset of the mobile phone or the SIM card after a certain number of unsuccessful attempts.
Attacks on IMEI Codes
IMEI codes are unique codes of 15 digits that identify a mobile phone. They are used to block a mobile phone in case of theft or loss. Hackers can try to guess them using brute force attacks simple or distributed by testing all possible combinations until they find the right one. These attacks can allow hackers to unlock a stolen or lost mobile phone and use it for malicious purposes such as making fraudulent calls sending unwanted messages or accessing personal data of the owner.
To protect themselves from these attacks users should note their IMEI codes and keep them in a safe place. They should not disclose their IMEI codes to unknown or suspicious people. They should report the loss or theft of their mobile phone to their operator and request the blocking of their IMEI codes. They should use a service of location or remote locking of their mobile phone in case of loss or theft.
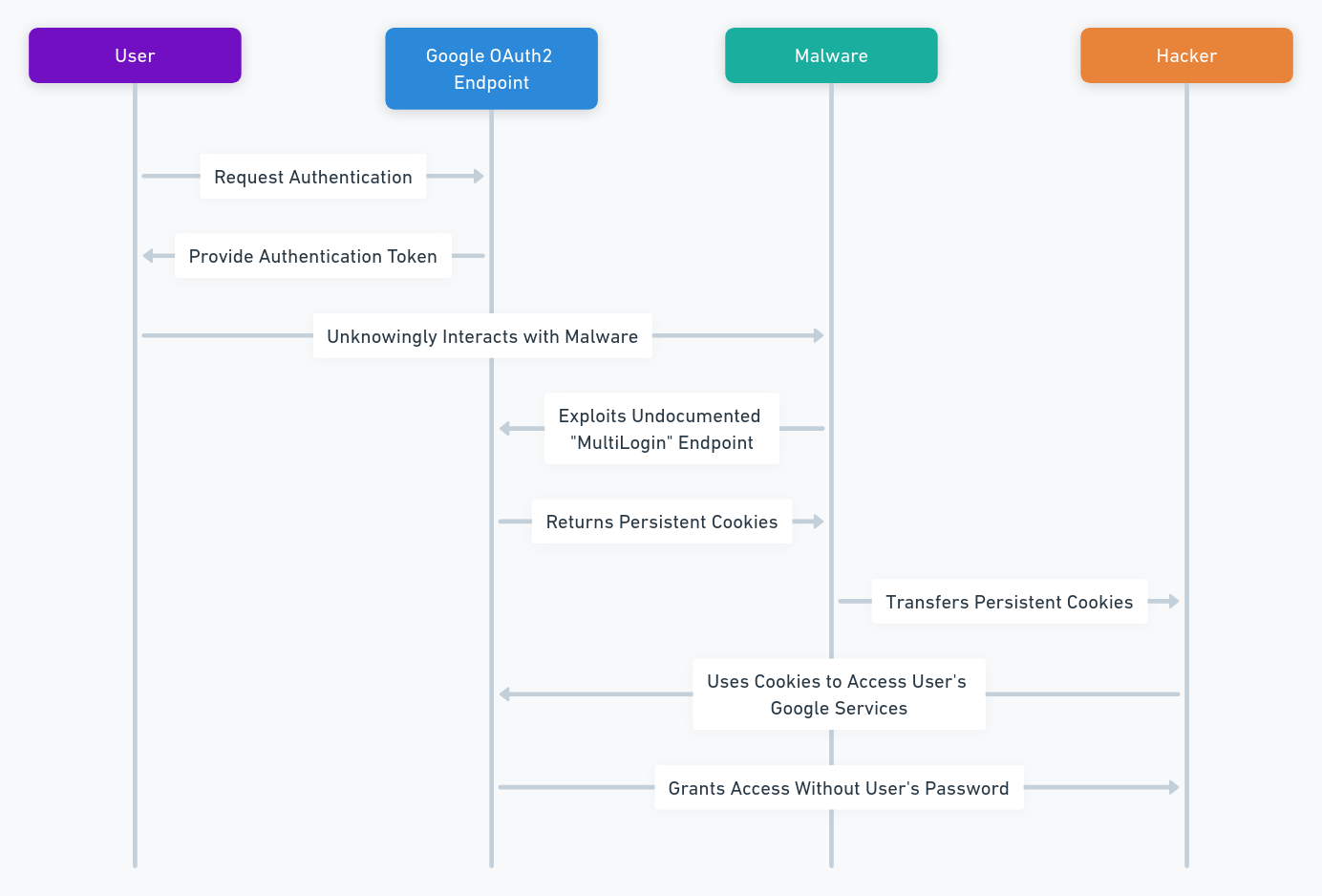
Attacks BrutePrint
You will surely be amazed by our discoveries! These systems verify your identity on smartphones and other devices by using the unique patterns of your finger. But is their security level? In this study, we explore the weaknesses of these systems and how various actors, from cybercriminals to sovereign entities, can exploit them. We looked at 25 techniques for corrupting fingerprint authentication systems. We will also introduce an effective dual-use defense solution: DataShielder HSM solutions to protect your secrets and sensitive data even if this biometric authentication system becomes compromised. Click is here for more information Attacks BrutePrint.
Evaluation of Products or Services Resistance to Brute-force Attacks
To evaluate the resistance of products or services to brute force attacks we can use a scoring model based on the type and severity of possible attacks. The scoring model can be as follows:
- For each product or service we identify the possible types of brute force attacks that can target it such as passwords encryption keys hidden URLs hashes PIN codes or IMEI codes.
- For each type of brute force attack we assign a score from 1 to 5 according to the severity of the attack. The score can be based on the following criteria: the complexity of the attack the time required to perform the attack the impact of the attack on the confidentiality integrity or availability of the data or service and the likelihood of the attack to succeed.
- We calculate the average score for each product or service by adding up the scores for each type of brute force attack and dividing by the number of types. The lower the score the more resistant the product or service is to brute force attacks.
For example let’s consider two products: a web application and a smartphone. The possible types of brute force attacks and their scores are as follows:
| Type of brute-force attack |
Web application |
Smartphone |
| Passwords |
3 |
2 |
| Encryption keys |
4 |
3 |
| Hidden URLs |
2 |
N/A |
| Hashes |
3 |
N/A |
| PIN codes |
N/A |
2 |
| IMEI codes |
N/A |
4 |
The average score for the web application is (3 + 4 + 2 + 3) / 4 = 3. The average score for the smartphone is (2 + 3 + 2 + 4) / 4 = 2.75. Therefore, according to this scoring model, the smartphone is more resistant to brute force attacks than the web application.
Statistics on brute force attacks
Brute force attacks are common and effective methods used by hackers to access systems protected by passwords or encryption keys. According to the IBM Cost of a Data Breach 2022 report, stolen or compromised credentials are the leading cause of data breaches and cost an average of $4.35 million to businesses worldwide in 2021. Brute force attacks are also increasing with the health crisis, which has encouraged remote work and online services. According to Cloudflare, the number of brute force attacks on RDP and SSH protocols increased by 400% between March and April 2020.
The duration and difficulty of a brute force attack depend on the length and complexity of the password or key to guess. According to Cloudflare, a seven-character password would take, at a rate of 15 million keystrokes per second, 9 minutes to crack. An eight-character password would take 4 hours, a nine-character password would take 8 days, and a ten-character password would take 463 days. It is therefore essential to use passwords or keys that are long and random enough to resist brute force attacks.
Real Cases of Brute-force Attacks
Brute force attacks are not only theoretical methods, but also real threats that have affected various domains, such as finance, health, politics, etc. In this section, we will present some examples of brute force attacks that have taken place in recent years, and show their consequences and lessons.
Brute force attacks on financial institutions
Financial institutions are often targeted by brute force attacks, as they store sensitive data and money. For instance, in 2019, a group of hackers used brute force attacks to access the online banking systems of several banks in Eastern Europe and Central Asia. They stole over $100 million from more than 40,000 accounts. The hackers used a software called Cobalt Strike, which allowed them to remotely control the infected computers and launch brute force attacks on the banks’ servers. They also used a technique called “ATM cash-out”, which enabled them to withdraw money from ATMs without using cards.
This case shows the importance of using strong passwords and encryption keys for online banking systems, as well as updating the software and hardware to prevent malware infections. It also shows the need for monitoring and alerting mechanisms to detect and stop brute force attacks in real time.
Brute force attacks on health systems
Health systems are also vulnerable to brute force attacks, as they store personal and medical data that can be used for identity theft or blackmail. For example, in 2020, a hacker group called Maze used brute force attacks to breach the network of Fresenius, Europe’s largest private hospital operator. They encrypted the data and demanded a ransom for its release. The attack affected the hospital’s operations and patient care, as well as its subsidiaries that produce dialysis products and blood transfusion devices.
This case illustrates the impact of brute force attacks on human lives and health services. It also highlights the need for securing the network and data of health systems, as well as having backup and recovery plans in case of an attack.
Brute force attacks on political systems
Political systems are not immune to brute force attacks, as they can influence the outcome of elections or policies. For instance, in 2016, a hacker group called Fancy Bear used brute force attacks to access the email accounts of several members of the Democratic National Committee (DNC) in the United States. They leaked the emails to WikiLeaks, which published them online. The leaked emails revealed internal conflicts and controversies within the DNC, and damaged the reputation of Hillary Clinton, who was running for president against Donald Trump.
This case demonstrates the power of brute force attacks to manipulate public opinion and interfere with democratic processes. It also underscores the need for protecting the email accounts and communications of political actors, as well as educating the public about cyber threats and misinformation.
How to Prevent Brute-force Attacks
Brute force attacks are a serious threat to the security and privacy of users, systems, and devices. Therefore, it is important to take preventive measures to avoid or mitigate their impact. Here are some general tips to prevent brute force attacks:
- Use strong and unique passwords, encryption keys, hidden URLs, hashes, PIN codes, and IMEI codes. They should be long, complex, and random, containing letters, numbers, and symbols. They should not be based on personal or predictable information, such as names, dates, or phone numbers.
- Use secure encryption algorithms and hashing functions. They should not have known or exploitable flaws or weaknesses, such as collisions or preimages. They should have enough entropy (degree of unpredictability) to resist brute force attacks.
- Use secure protocols and techniques to exchange and store data. They should provide encryption, authentication, verification, correction, masking, or salting features. They should use secure channels and devices to transmit and store data.
- Use security software and hardware to protect systems and devices. They should include firewalls, antivirus software, sensors, or locks. They should detect and block brute force attacks or trigger self-destruction or data erasure mechanisms.
- Use ethical hacking and research to test and improve the security of systems and devices. They should identify and report vulnerabilities, flaws, or weaknesses. They should provide solutions, innovations, or products to enhance the security of systems and devices.
In conclusion
In this article, we have explored the topic of brute force attacks, also known as trial-and-error or exhaustive attacks. We have seen that brute force attacks are methods used by hackers to access systems protected by passwords or encryption keys, by testing all possible combinations until finding the right one. We have also seen that there are different types and methods of brute force attacks, depending on the hackers’ method, the level of intrusion, the domain of application and the tools used. We have focused on some specific types of brute force attacks, such as those on electronic components, passwords, encryption keys, hidden URLs, hashes and phone systems. We have also evaluated the resistance of products or services to brute force attacks, by presenting some real cases and some criteria to assess the security level. Finally, we have given some tips on how to prevent brute force attacks, by using long and complex passwords or keys, encrypting data, updating software and hardware, and using security tools.
Brute force attacks are a serious threat for data security and privacy, as they can allow hackers to access confidential information, compromise other systems or services, or extort the victims. Therefore, it is essential to be aware of the risks and the solutions to protect yourself from brute force attacks. If you want to learn more about this topic, you can check the sources that we have cited throughout this article.