Browser Fingerprinting Tracking today represents one of the true cores of metadata intelligence. Far beyond the content of communications, it is the behavioral correlations — relationships, timelines, locations, regularities — that structure modern digital surveillance, whether civil or state-driven, economic or advertising. Exploited by digital platforms, AdTech, intelligence services, and cybercrime, this logic enables anticipation, profiling, and influence without ever reading a single message. Encryption protects the content, but not the technical fingerprints nor the relational graphs. This article analyzes the strategic stakes of browser fingerprinting, its lawful, unlawful, and hybrid uses, and the conditions for genuine metadata sovereignty.
Stop Browser Fingerprinting: What You Need to Know in 2026
Since 16 February 2025, Google’s Ads platform policies no longer prohibit fingerprinting, which increases pressure on users and IT providers to adopt layered, script-aware defenses.
Express: 3–4 min ·
Advanced: 5–6 min
Chronicle: 30–40 min
Stop Browser Fingerprinting: Jacques Gascuel examines how device and browser signals enable persistent tracking, why policy shifts matter, and which countermeasures remain realistic under real-world constraints.
Stop Browser Fingerprinting: Google’s New Tracking Strategy & Privacy Risks (2025)
From Condemnation to Enforcement
Google initially condemned fingerprinting, stating in 2019 that it “subverts user choice and is incorrect.” However, in December 2024, the company reversed its stance, announcing that advertisers can now use fingerprinting for tracking as Chrome phases out third-party cookies.
Why Google’s Shift to Fingerprinting Endangers Privacy
- Cookieless Tracking: As users block cookies, Google seeks persistent alternatives.
- Ad Revenue Protection: Advertisers need reliable tracking methods.
- Privacy Illusion: While Google claims to enhance privacy, fingerprinting is far more invasive than cookies.
Regulatory Pushback: The UK’s Information Commissioner’s Office (ICO) has criticized this decision as “irresponsible,” arguing it removes user control over their personal data.
Google’s Contradiction: From Condemnation to Approval
In 2019, Google condemned browser fingerprinting as a violation of user choice, calling it a method that “subverts user choice and is incorrect.”
🔗 Official Sources:
- Google Blog: Building a More Private Web
- Google Support: What is Fingerprinting?
- TechCrunch: Google Proposes New Privacy & Anti-Fingerprinting Controls
However, in December 2024, Google reversed its position, announcing that starting February 16, 2025, it will officially allow advertisers to use fingerprinting-based tracking, replacing cookies as the primary method of user identification.
This shift has sparked strong criticism from privacy advocates and regulators. The UK’s Information Commissioner’s Office (ICO) condemned this decision as “irresponsible,” stating that it “removes user choice and control over personal data collection.”
Why Has Google Changed Its Position on Fingerprinting?
The shift towards fingerprinting-based tracking is driven by:
- The Death of Cookies – With Chrome phasing out third-party cookies, advertisers need new tracking methods.
- Fingerprinting’s Persistence – Unlike cookies, fingerprinting cannot be deleted or blocked, making it perfect for tracking users across devices.
- Mass Surveillance & Data Monetization – Fingerprinting enables governments and corporations to build detailed behavioral profiles, bypassing traditional privacy protections.
By officially approving fingerprinting, Google presents itself as a leader in privacy while simultaneously endorsing an even more invasive tracking method.
Stop Browser Fingerprinting Now: How It Affects You & What to Do
Browser fingerprinting is more than a privacy risk—it directly impacts security, fairness, and even personal safety:
- Algorithmic Discrimination – Websites dynamically adjust prices based on your device. Studies show that Mac users often see higher travel fares than Windows users.
- Mass Surveillance – Governments and corporations use fingerprinting for predictive policing, targeted advertising, and even social credit scoring, removing user consent from the equation.
- Threats to Journalists & Activists – Unique browser fingerprints allow regimes to track dissidents despite their use of VPNs or private browsing.
- Inescapable Tracking – Even if you clear cookies or change IPs, fingerprinting allows advertisers to track you across multiple devices.
How PassCypher HSM PGP Helps Stop Browser Fingerprinting
PassCypher HSM PGP disrupts indirect fingerprinting by blocking iFrame-based tracking scripts before they execute—a common method used by advertisers and trackers.
For maximum protection:
- PassCypher HSM PGP Free with EviBITB
- Mullvad Browser or Tor for standardizing fingerprints
- uBlock Origin + CanvasBlocker to block tracking scripts
Stop Browser Fingerprinting: Regulations and Privacy Protection Laws You Need to Know
Regulators and privacy organizations have raised concerns over browser fingerprinting due to its impact on digital rights, online privacy, and mass surveillance. While some laws attempt to regulate fingerprinting, enforcement remains weak.
General Data Protection Regulation (GDPR – Europe)
- Fingerprinting is considered personally identifiable information (PII) under GDPR.
- Websites must obtain explicit consent before collecting fingerprinting data.
- Fines for non-compliance can reach up to €20 million or 4% of global annual revenue.
Privacy and Electronic Communications Regulations (PECR – UK)
- Works alongside GDPR to regulate electronic communications tracking.
- Covers cookies, tracking pixels, link decoration, web storage, and fingerprinting.
- Requires transparent disclosure & user consent.
🔗 ICO Guidance on Fingerprinting
The Role of the ICO & EDPB
The UK Information Commissioner’s Office (ICO) has strongly opposed fingerprinting, calling Google’s 2025 update “irresponsible” due to its removal of user control.
Meanwhile, the European Data Protection Board (EDPB) has issued guidelines reinforcing that all tracking technologies, including fingerprinting, require consent under the ePrivacy Directive.
🔗 ICO’s Statement on Google’s Fingerprinting Policy
🔗 EDPB Guidelines on Fingerprinting & Consent
Takeaway
While regulations exist, enforcement is weak, and companies continue fingerprinting without user consent. Users must adopt proactive privacy tools to protect themselves.
Google’s New Privacy Strategy: Why Stop Browser Fingerprinting is Essential
Google claims to prioritize privacy, yet fingerprinting offers deeper tracking than cookies ever did. This move benefits advertisers, ensuring that:
- Users remain identifiable despite privacy tools.
- Ad targeting remains profitable.
- Companies can bypass traditional data protection regulations.
It’s about profits, not privacy.
- Safari, Firefox, and Brave block third-party cookies.
- More users rely on VPNs and ad blockers.
- Google seeks a more persistent tracking alternative that cannot be blocked.
The Privacy Illusion
Google presents third-party cookie removal as a privacy enhancement. However, by replacing cookie-based tracking with fingerprinting, it introduces an even more invasive method. This shift aligns with the transition to a cookieless web, where advertisers must adapt by using alternatives like cookieless tracking.
Google, Cookieless Tracking, and Fingerprinting
Google justifies this transition as necessary to sustain web monetization while respecting user privacy. However, unlike cookies, which users can delete or block, fingerprinting is persistent and much harder to evade.
Stop Browser Fingerprinting: Essential Actions to Protect Your Privacy in 2025
To mitigate the risks posed by Google’s new policy:
- Use privacy-focused browsers (Mullvad, Brave, or Tor)
- Install fingerprinting-blocking extensions (PassCypher HSM PGP Free, uBlock Origin, CanvasBlocker)
- Employ anti-fingerprinting authentication solutions like PassCypher HSM PGP Free with EviBITB protection
💡 As the internet moves toward a cookieless future, new tracking methods like fingerprinting will dominate digital advertising. Users must adopt privacy-enhancing tools to regain control over their online footprint.
How to Stop Browser Fingerprinting and Why It’s Dangerous for Your Privacy
What is Browser Fingerprinting and How to Stop It?
Fingerprinting collects hardware and software details to create a unique ID. Unlike cookies, it cannot be deleted or blocked easily.
What Data Is Collected?
Browser fingerprinting collects many different attributes simultaneously — that’s why it’s so hard to defeat. Modern fingerprinting engines analyze dozens of static and dynamic values from your browser and system, including:
- HTTP headers (User‑Agent, Accept, Content Language, Cache Control, Do Not Track)
- Navigator properties (platform, vendor, hardwareConcurrency, memory)
- Screen metrics (resolution, color depth, effective screen size)
- Canvas & WebGL rendering patterns and GPU shading profiles
- Audio context outputs and frequency analysis
- Installed fonts & plugins
- Time zone & locale settings
- Storage APIs behavior (IndexedDB, LocalStorage)
- Battery status APIs (charging state, level)
Even if you modify a few values, the combination of these attributes creates a highly unique profile that identifies your device across websites.
Even if you block some tracking methods, fingerprinting combines multiple data points to reconstruct your identity.
Cover Your Tracks – Browser Fingerprinting Protection Test
Cover Your Tracks (EFF) → Analyzes your fingerprint uniqueness.
Am I Unique? → Provides detailed fingerprinting insights.
If your browser has a unique fingerprint, tracking remains possible despite privacy tools.
Best Anti-Fingerprinting Tools in 2025 – Full Comparison
| Solution | Blocks iFrame Tracking? | Fingerprinting Protection | Static Fingerprinting Protection | BITB Protection? | Blocks Script Execution? | Ease of Use ✅ | Cost 💰 |
|---|---|---|---|---|---|---|---|
| PassCypher HSM PGP Free + Mullvad Browser | ✅ Yes | ✅ High | ✅ Deep-level (user-agent, audio, canvas) | ✅ Yes | ✅ Yes | ✅ Easy | Free |
| Tor Browser | ❌ No | ✅ High | ✅ Deep-level (user-agent, canvas) | ❌ No | ❌ No | ❌ Complex | Free |
| Mullvad Browser (Standalone) | ❌ No | ✅ High | ✅ Deep-level (standardized fingerprint) | ❌ No | ❌ No | ✅ Easy | Free |
| Brave (Aggressive Mode) | ❌ No | 🔸 Moderate | 🔸 Partial (canvas & WebGL randomization) | ❌ No | ❌ No | ✅ Easy | Free |
| Disabling JavaScript | ✅ Yes | ✅ High | ✅ By elimination | ❌ No | ✅ Yes | ❌ Complex | Free |
| VPN + Proxy Chains | ❌ No | 🔸 Moderate | ❌ None | ❌ No | ❌ No | ❌ Complex | Paid |
| uBlock Origin + CanvasBlocker Extension | ❌ No | 🔸 Low | 🔸 Canvas only | ❌ No | ❌ No | ✅ Easy | Free |
| Changing User-Agent Regularly | ❌ No | 🔸 Low | 🔸 User-agent only | ❌ No | ❌ No | ❌ Technical | Free |
| Incognito Mode + Multiple Browsers | ❌ No | 🔸 Very Low | ❌ None | ❌ No | ❌ No | ✅ Easy | Free |
Cover Your Tracks (EFF) analyzes 3 fingerprinting vectors:
- Tracking ads — detection of known tracking ad networks
- Invisible trackers — background scripts collecting data
- Fingerprint uniqueness — comparison with global browser signatures
A “unique” result = your browser is highly identifiable and trackable across sessions and websites.
Optimal Security Setup
PassCypher HSM PGP Free + EviBITB → Bloque les scripts de fingerprinting avant leur exécution
Mullvad Browser → Standardise l’empreinte digitale pour réduire l’unicité
uBlock Origin + CanvasBlocker → Ajoute une protection supplémentaire contre le fingerprinting passif
Test Results: PassCypher HSM PGP BITB Protection
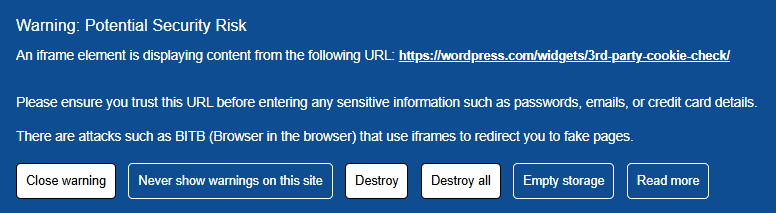
PassCypher HSM PGP Free with EviBITB is the only solution that prevents fingerprinting scripts from executing inside iFrames before they can collect any data.
Test 1: Without EviBITB (PassCypher HSM PGP Disabled)
Problems detected:
- Tracking ads are not blocked ❌
- Invisible trackers remain active ❌
- Fingerprinting scripts fully execute, allowing websites to recognize the browser ❌
🔎 Result: Without EviBITB, the browser fails to block fingerprinting attempts, allowing trackers to profile users across sessions and devices.
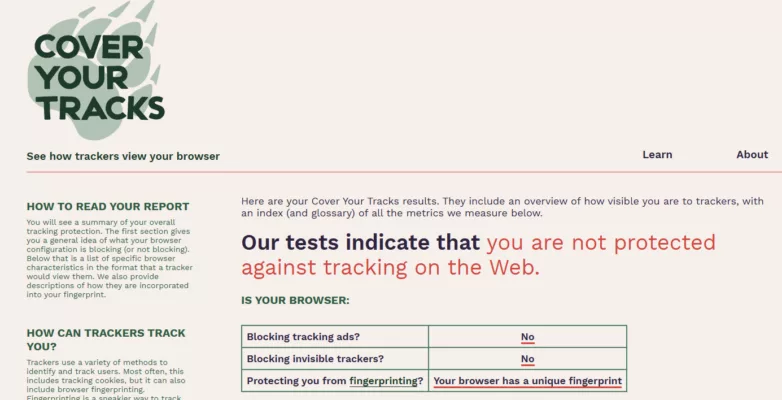
🔎 Without EviBITB, the browser fails to block tracking ads, invisible trackers, and remains fully identifiable through fingerprinting.Beyond theoretical solutions, let’s examine real-world testing of browser fingerprinting protection using Cover Your Tracks.
Test 2: With EviBITB Activated (PassCypher HSM PGP Enabled)
Protection enabled:
- BITB Protection blocks tracking ads and prevents phishing attempts✅
- iFrame-based fingerprinting scripts are blocked before execution✅
- However, static fingerprinting elements (Canvas, WebGL, fonts, etc.) remain detectable⚠️
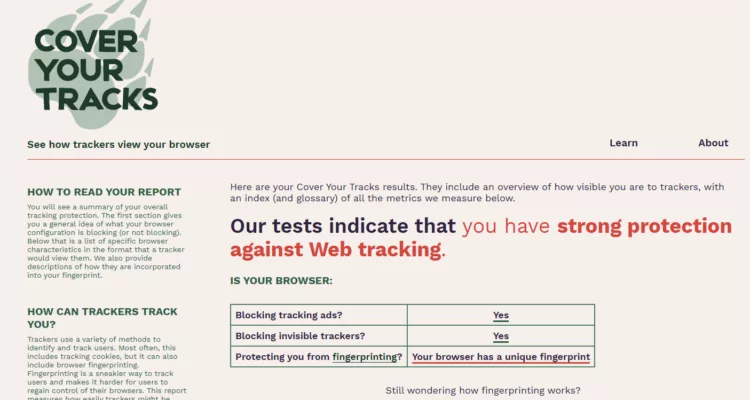
Key Findings:
EviBITB effectively blocks iFrame-based fingerprinting, preventing indirect tracking.
However, it does not alter static browser characteristics used for direct fingerprinting (Canvas, WebGL, user-agent, etc.).
For full protection, users should combine EviBITB with a dedicated anti-fingerprinting browser like Mullvad or Tor.
Comparison of Anti-Fingerprinting Solutions
| Solution | Blocks iFrame Tracking? | Fingerprinting Protection |
|---|---|---|
| PassCypher HSM PGP Free with EviBITB | ✅ Yes | ✅ High |
| Mullvad Browser | ❌ No | ✅ High |
| Tor Browser | ❌ No | ✅ High |
| Brave (Aggressive Mode) | ❌ No | 🔸 Moderate |
For optimal security, combine PassCypher HSM PGP Free with Mullvad Browser for full anti-fingerprinting protection.
Final Thoughts: Stop Browser Fingerprinting and Take Back Your Privacy
Even with BITB Protection, fingerprinting remains a challenge. To achieve maximum privacy:
- Use a dedicated anti-fingerprinting browser like Mullvad or Tor ✅
- Install CanvasBlocker to disrupt common fingerprinting techniques ✅
- Combine BITB Protection with other privacy tools like uBlock Origin ✅
By implementing these measures, users can significantly reduce their online footprint and stay ahead of evolving tracking techniques.
The Fingerprinting Paradox: Why It Can’t Be Fully Eliminated
Despite advancements in privacy protection, browser fingerprinting remains an unavoidable tracking method. Unlike cookies, which users can delete, fingerprinting collects multiple device-specific attributes to create a persistent identifier.
Can You Stop Browser Fingerprinting Completely? Myths vs Reality
Fingerprinting relies on multiple static and dynamic factors, making it difficult to block entirely:
- IP address & Network Data → Even with a VPN, passive fingerprinting methods analyze connection patterns.
- Browser Type & Version → Each browser has unique configurations, including default settings and rendering quirks.
- Screen Resolution & Device Specs → Screen size, refresh rate, and hardware combinations create a distinct profile.
- Installed Plugins & Fonts → Specific browser extensions, fonts, and system configurations contribute to uniqueness.
- WebGL & Canvas Rendering → Websites extract graphic processing details to differentiate devices.
Even if users restrict or modify certain attributes, fingerprinting algorithms adapt, refining their tracking models to maintain accuracy.
How PassCypher HSM PGP Free Disrupts Fingerprinting at Its Core
PassCypher HSM PGP Free with EviBITB is a game-changer. Unlike traditional fingerprinting blockers that only randomize or standardize user data, EviBITB prevents fingerprinting scripts from executing inside iFrames before they collect data.
- Blocks tracking scripts before execution✅
- Prevents iFrame-based fingerprinting & Browser-in-the-Browser (BITB) phishing✅
- Works across multiple privacy-focused browsers✅
Key Takeaway
While completely eliminating fingerprinting is impossible, combining EviBITB with anti-fingerprinting browsers like Mullvad or Tor, and tools like uBlock Origin and CanvasBlocker, significantly reduces tracking risks. Stop Browser Fingerprinting before it starts—neutralize it before it executes.
PassCypher HSM PGP Free: The Ultimate Defense Against Fingerprinting & BITB Attacks
Understanding Browser-in-the-Browser (BITB) Attacks
BITB attacks exploit iframe vulnerabilities to create fake login pop-ups, tricking users into submitting their credentials on seemingly legitimate pages. These phishing techniques bypass traditional security measures, making them a growing cybersecurity threat.
How EviBITB Protects Against BITB & Fingerprinting
- ✅ Blocks fingerprinting scripts before execution
- ✅ Eliminates malicious iFrames that simulate login pop-ups
- ✅ Prevents advertisers & trackers from embedding tracking scripts
- ✅ Gives users full control over script execution (Manual, Semi-Auto, Auto)
Why EviBITB is Superior to Traditional Anti-Fingerprinting Tools
While browsers like Mullvad & Tor aim to reduce fingerprinting visibility, they don’t block scripts before execution. EviBITB neutralizes fingerprinting at its core by preventing iFrame-based tracking before data collection begins.
Live Test: How PassCypher HSM PGP Stops Fingerprinting & BITB Attacks
PassCypher Security Suite: Multi-Layered Protection
PassCypher HSM PGP offers multi-layered protection against fingerprinting, BITB attacks, and phishing attempts. Unlike browsers that only standardize fingerprints, PassCypher actively blocks fingerprinting scripts before they execute.
EviBITB – Advanced BITB & Fingerprinting Protection
- ✅ Proactive iframe blocking before execution
- ✅ Neutralization of fake login pop-ups
- ✅ Blocking of hidden fingerprinting scripts
- ✅ Real-time phishing protection
Customizable Security Modes
PassCypher HSM PGP offers three security levels, allowing users to choose their preferred protection mode:
- 🛠️ Manual Mode → Users manually approve or block each iframe.
- ⚠️ Semi-Automatic Mode → Detection + security recommendations.
- 🔥 Automatic Mode → Immediate blocking of suspicious iframes.
Why This Matters?
Unlike browsers that only standardize fingerprints, PassCypher actively blocks scripts before they execute, preventing any tracking or phishing attempts.
🔑 PassCypher NFC HSM – Enhanced Security with Hardware Protection
For even stronger security, pair PassCypher HSM PGP with a PassCypher NFC HSM device.
- ✅ Passwordless Authentication → Secure logins without typing credentials.
- ✅ Offline Encryption Key Storage → Keys remain fully isolated from cyber threats.
- ✅ Automatic Decryption & Login → Credentials decrypt only in volatile memory, leaving no traces.
- ✅ 100% Offline Operation → No servers, no databases, no cloud exposure.
Why Choose PassCypher?
PassCypher Security Suite is the only solution that stops fingerprinting before it even begins.
- ✅ Neutralizes tracking attempts at the script level
- ✅ Removes malicious iframes before they appear
- ✅ Prevents invisible BITB phishing attacks
🔗 Download PassCypher HSM PGP Free
Best Anti-Fingerprinting Extensions in 2025 – Stop BITB & Online Tracking
⚠️ PassCypher HSM PGP Free detects and blocks BITB phishing attacks before they execute.
How PassCypher HSM PGP Free Protects You
This proactive security tool offers real-time protection against tracking threats:
- ✅ Destroy the iframe → Instantly neutralize any malicious iframe attack.
- ✅ Destroy all iframes → Eliminate all potential threats on the page.
- ✅ Custom Security Settings → Choose whether to allow or block iframes on trusted domains.
Take Control of Your Privacy Now
PassCypher HSM PGP Free ensures complete protection against fingerprinting and BITB phishing—before tracking even starts!
🔗 Download PassCypher HSM PGP Free Now
Stop Browser Fingerprinting: Key Takeaways & Next Steps
Fingerprinting is the future of online tracking, and Google’s 2025 update will make it harder to escape. To fight back:
1️⃣ Install PassCypher HSM PGP Free with EviBITB 🛡️ → Blocks iFrame-based fingerprinting & BITB attacks.
2️⃣ Use a privacy-focused browser 🌍 → Mullvad Browser or Tor for best results.
3️⃣ Block fingerprinting scripts 🔏 → Use CanvasBlocker + uBlock Origin.
4️⃣ Adopt a multi-layered defense
🔄 → Combine browser protections, script blockers, and a VPN for maximum security.
📌 Take Control of Your Privacy Now!
To truly Stop Browser Fingerprinting, users must adopt proactive privacy tools and strategies.
FAQs – Browser Fingerprinting & Privacy Protection
No, private browsing (Incognito mode) does not stop browser fingerprinting. This mode only prevents your browser from storing cookies, history, and cached data after you close the session. However, browser fingerprinting relies on collecting unique characteristics from your device, such as:
- Graphics rendering (Canvas & WebGL)
- Installed fonts and plugins
- Operating system, screen resolution, and hardware details
- Browser version and user-agent string
Since Incognito mode does not alter these attributes, your digital fingerprint remains the same, allowing websites to track you across sessions. For stronger protection, consider using privacy-focused tools like PassCypher HSM PGP Free, Mullvad Browser, or Tor.
Websites collect fingerprinting data to build user profiles and track behavior across multiple sites, even if cookies are blocked. This data is shared with advertisers to deliver highly personalized ads based on browsing history, location, and device information.
Under GDPR, websites must obtain user consent before using fingerprinting techniques, as they collect identifiable personal data. However, enforcement varies, and many companies use workarounds to continue fingerprinting users without explicit permission.
No, fingerprinting is not exclusively used for advertising. It is also utilized for fraud detection, identity theft prevention, and user authentication. However, its use for tracking users without consent raises significant privacy concerns.
Fingerprinting does not directly reveal a user’s identity. However, it creates a unique digital fingerprint that can track a specific device’s activity across multiple websites. If this fingerprint is linked to personal information, it can potentially identify an individual.
Yes, cross-device tracking is possible. While fingerprinting is primarily device-specific, advertisers and trackers use advanced techniques like:
- Correlating browser fingerprints with IP addresses
- Detecting Bluetooth & Wi-Fi network information
- Analyzing behavioral patterns across devices
For example, if you use the same browser settings on your phone and laptop, a tracker may recognize that both belong to you.
- Using different browsers on each device helps, but isn’t foolproof.
- A better option is a privacy-focused browser like Mullvad or Tor.
- PassCypher HSM PGP Free blocks fingerprinting scripts before they execute.
Fingerprinting operates in the background without visible indicators, making it difficult to detect. However, tools like Cover Your Tracks (by the Electronic Frontier Foundation) can analyze your browser and assess its uniqueness and vulnerability to fingerprinting.
Technical & Protection Methods
Yes, some browser extensions can help mitigate fingerprinting. For example, CanvasBlocker prevents websites from accessing canvas data, a common fingerprinting technique. However, adding extensions may alter your digital fingerprint, so it’s essential to choose privacy-focused extensions wisely.
Using different browsers for different online activities can reduce complete tracking. For instance, you could use one browser for sensitive activities and another for general browsing. However, if these browsers are not protected against fingerprinting, websites may still link your activities across them.
Letterboxing is a technique that adds gray margins around browser content when resizing the window. This conceals the exact window size, making it harder for websites to collect precise screen dimensions—a common fingerprinting metric. Firefox implements this method to enhance user privacy.
No, a VPN only hides your IP address, but fingerprinting gathers other device-specific data such as browser type, screen resolution, and hardware details. To enhance privacy, use a combination of anti-fingerprinting tools like PassCypher HSM PGP Free, Tor, or Mullvad Browser.
The best approach is using a multi-layered defense:
- Privacy-focused browsers like Tor or Mullvad.
- Extensions such as PassCypher HSM PGP Free, uBlock Origin, and CanvasBlocker.
- JavaScript blocking tools like NoScript.
- Regularly changing settings like user-agent and browser resolution.
Disabling JavaScript can block many fingerprinting techniques, but it also breaks website functionality. Some tracking methods, such as TLS fingerprinting and IP-based tracking, do not rely on JavaScript and can still be used to identify users.
Not really.
Changing your user-agent (e.g., making your browser appear as Chrome instead of Firefox) or screen resolution may add some randomness, but it does not significantly reduce fingerprintability.
Fingerprinting works by analyzing multiple attributes together, so even if you change one, the combination of hardware, fonts, and other details still makes you unique.
- A better approach is using a browser that standardizes your fingerprint, like Mullvad or Tor.
- PassCypher HSM PGP Free blocks tracking scripts before they collect data.
Some websites use battery APIs to track users based on their **battery percentage, charging status, and estimated time remaining**. Although this technique is less common, it can still contribute to building a unique fingerprint.
To mitigate this risk, consider using:
- A browser that blocks access to battery APIs (e.g., Firefox, Mullvad, Tor)
- Privacy-enhancing tools like PassCypher HSM PGP Free, which block JavaScript-based tracking techniques.
No, but it’s still good practice.
Fingerprinting is a cookieless tracking method, meaning it works even if you block cookies. However, blocking third-party cookies still improves privacy, as it prevents advertisers from combining fingerprinting with cookie-based tracking for more accurate profiling.
For the best protection, use a multi-layered approach:
- Block third-party cookies
- Use anti-fingerprinting browsers (Mullvad, Tor, Brave in Aggressive mode)
- Install extensions like CanvasBlocker & uBlock Origin
- Use PassCypher HSM PGP Free for script-blocking & BITB protection
Letterboxing is a privacy technique used by Firefox and Tor to reduce fingerprinting risks. Instead of revealing your exact window size, letterboxing adds empty space around the browser content, making your screen resolution appear more generic.
This helps prevent fingerprinting based on window dimensions, which is a common tracking method.
To enhance protection, combine letterboxing with other privacy measures, like:
- Using PassCypher HSM PGP Free with EviBITB
- Blocking iFrames with CanvasBlocker
- Using Mullvad or Tor for standardized fingerprints
Future of Online Privacy & Google’s Role
With the elimination of third-party cookies, Google and advertisers need new ways to track users for targeted ads. Fingerprinting allows persistent tracking across devices without requiring user consent, making it an attractive alternative for data collection.
Currently, no mainstream browser completely blocks fingerprinting. However, some browsers provide strong protection:
- Tor Browser: Standardizes fingerprints across users.
- Mullvad Browser: Focuses on reducing fingerprinting techniques.
- Brave: Offers randomized fingerprints.
- Firefox (Strict Mode): Blocks known fingerprinting scripts.
Fingerprinting-based tracking is expected to become more common, making it harder for users to remain anonymous online. This shift may lead to **increased regulatory scrutiny**, but in the meantime, privacy-focused tools will become essential for protecting online identity.
Google’s move to fingerprinting is a business-driven decision. Since third-party cookies are being phased out, Google needs an alternative tracking method to maintain ad revenue. Fingerprinting offers:
- Persistent tracking (harder to delete than cookies)
- Cross-device profiling (better for targeted ads)
- Circumvention of privacy laws (harder to detect and block)
While Google markets this as a “privacy improvement,” it’s actually an even more invasive tracking method.
This is why privacy advocates recommend using browsers and tools that block fingerprinting, like PassCypher HSM PGP Free, Mullvad, and Tor.