Vulnérabilité WhatsApp zero-click (CVE-2025-55177) chaînée avec Apple CVE-2025-43300 permet l’exécution de code à distance via des images DNG spécialement conçues en abusant de la synchronisation des appareils liés et du traitement automatique des médias — mettez à jour WhatsApp et votre OS immédiatement.
Résumé express — Vulnérabilité WhatsApp zero-click
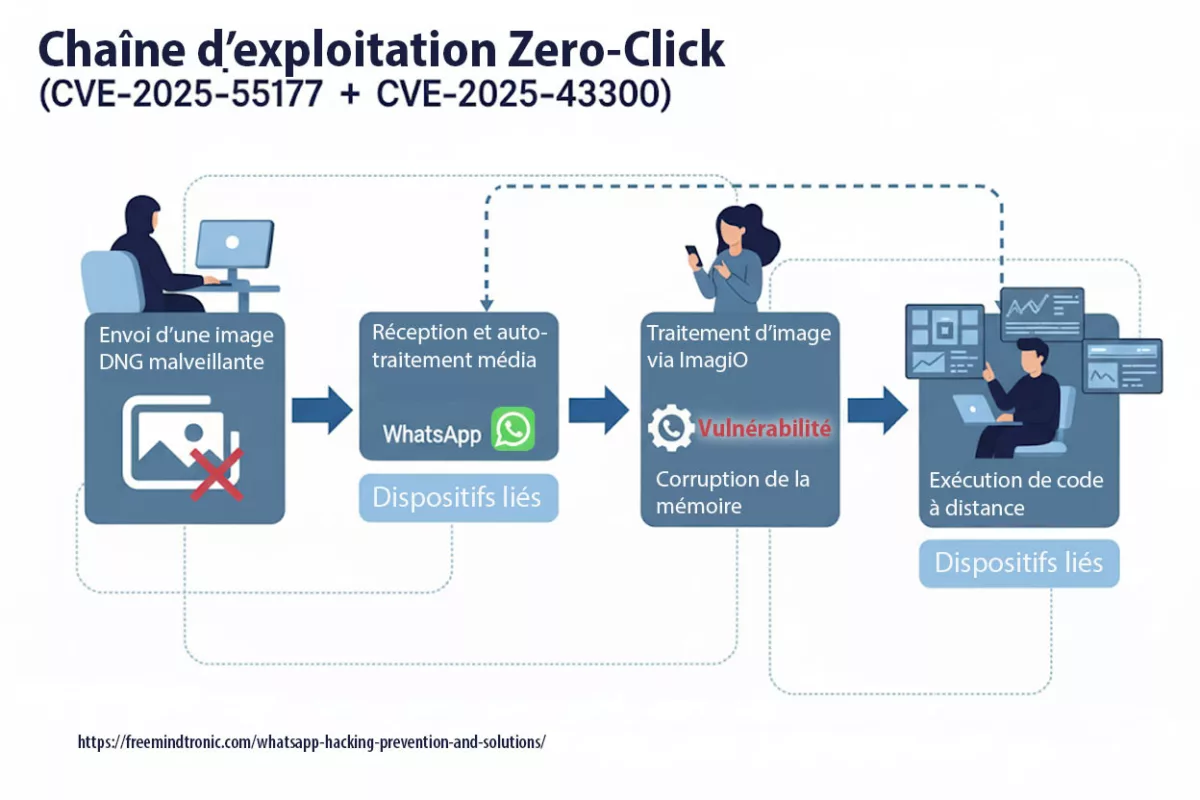
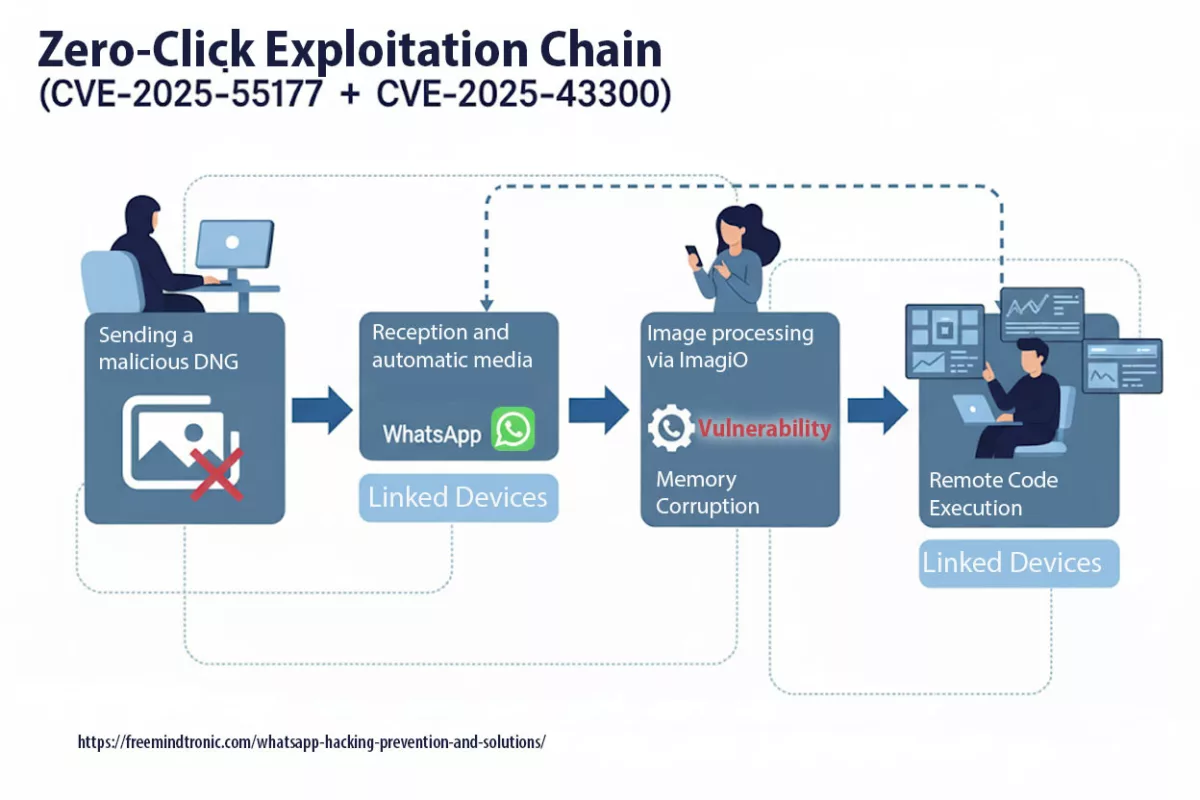
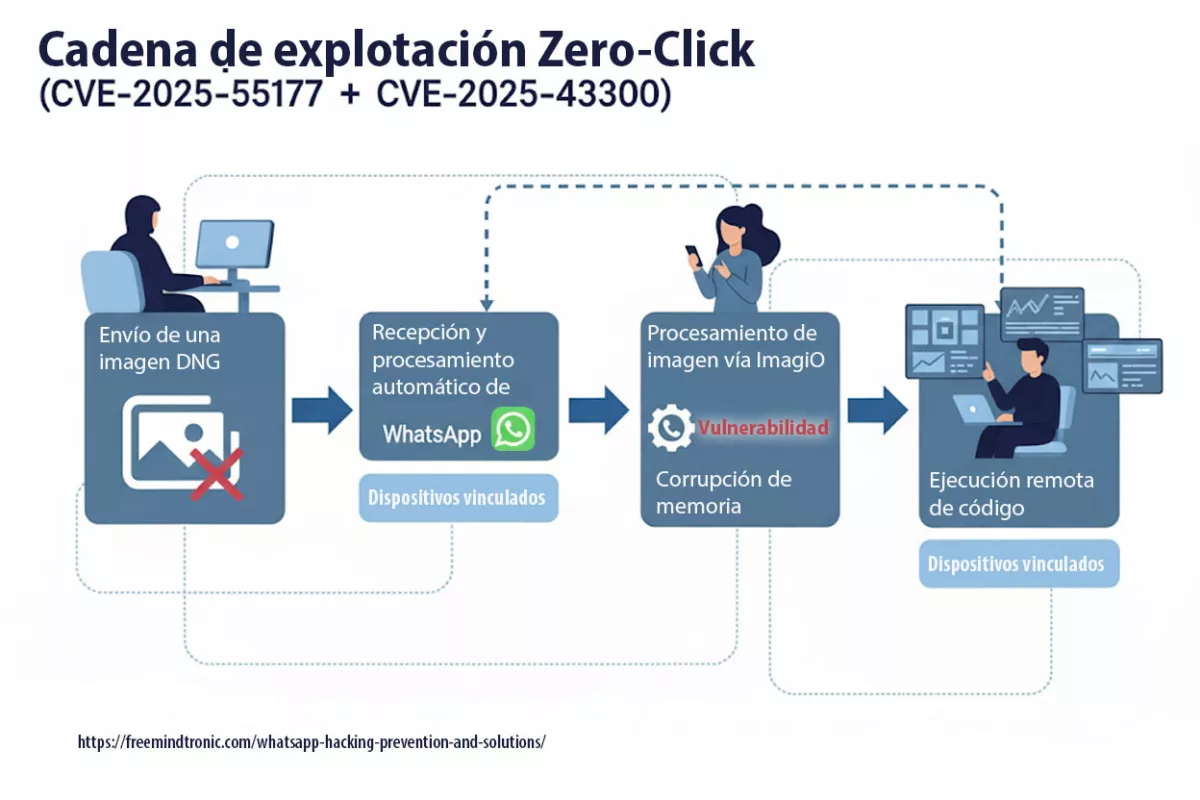
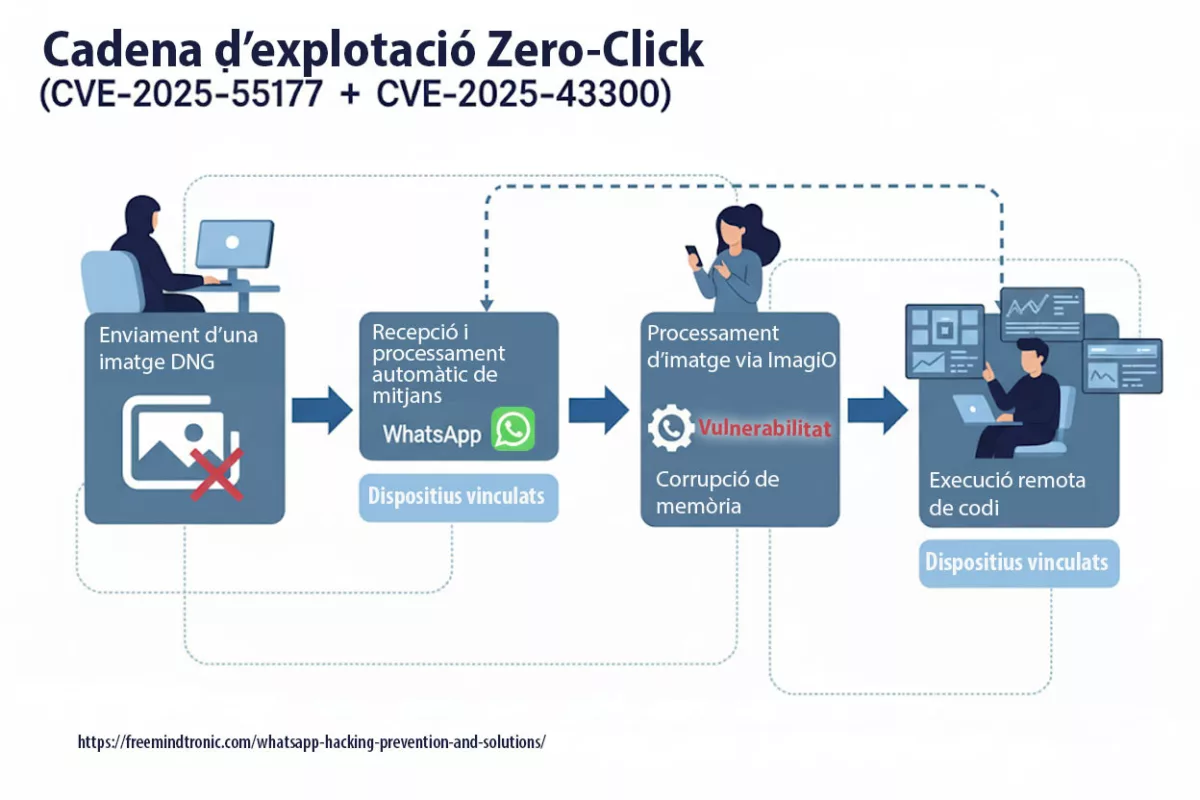
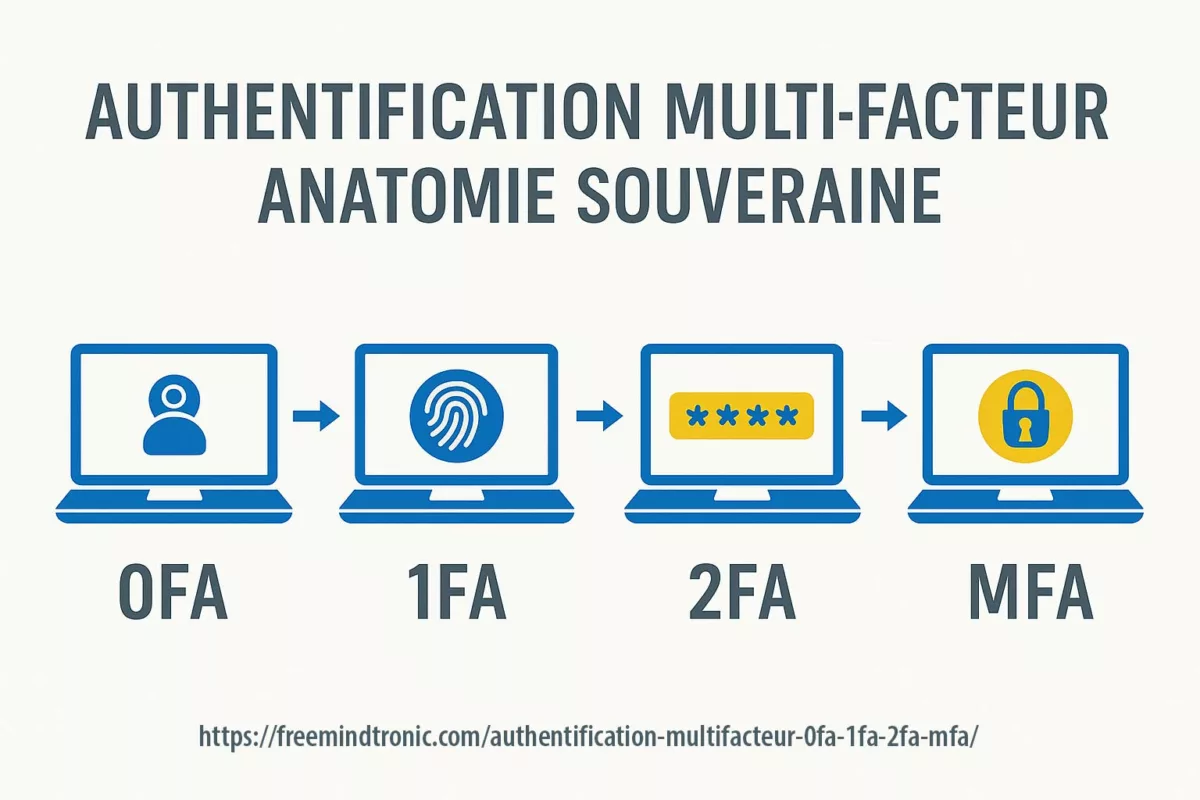
La faille zero-click de WhatsApp (CVE-2025-55177, chaînée avec Apple CVE-2025-43300) permet l’exécution de code arbitraire à partir d’une image DNG fabriquée — aucun clic requis. La synchronisation des appareils liés, combinée au traitement automatique des médias, a ouvert la porte : une URL cachée est récupérée, le parseur d’images corrompt la mémoire et un payload s’exécute. Meta rapporte des exploitations ciblées en conditions réelles contre des profils à haut risque. Des correctifs sont disponibles : iOS ≥ 2.25.21.73, Business iOS ≥ 2.25.21.78, Mac ≥ 2.25.21.78.
Basique — mettez à jour maintenant. Traitez WhatsApp comme un runtime hostile : appliquez patchs app + OS, désactivez temporairement les appareils liés et l’auto-traitement des médias, et isolez les échanges sensibles via une posture Zero-DOM (HSM/NFC).
Paramètres de lecture
Temps de lecture résumé : 4 minutes
Lecture complète estimée : 29 minutes
Dernière mise à jour : 2025-09-30
Complexité : Niveau expert
Note linguistique : Lexique souverain — densité technique élevée
Densité technique : ≈70 %
Langues : FR · EN · ES · CAT
Accessibilité : Optimisé lecteur d’écran — ancres sémantiques incluses
Type éditorial : Chronique stratégique (analytique / technique)
À propos de l’auteur : Jacques Gascuel, inventeur et fondateur de Freemindtronic®, spécialiste des architectures de cybersécurité souveraines et créateur des technologies NFC & PGP HSM pour la protection Zero-DOM des secrets.
Points clés
- RCE zero-click via DNG façonné livré par la synchronisation des appareils liés.
- Chaînage avec un bug ImageIO d’Apple (CVE-2025-43300) provoquant corruption mémoire.
- Exploitation active, ciblée, confirmée pour des profils à haut risque.
- Builds corrigées : iOS ≥2.25.21.73 · Business iOS ≥2.25.21.78 · Mac ≥2.25.21.78.
- Réflexe souverain : désactiver la synchro liée, conserver les traces, adopter des flux Zero-DOM (HSM/NFC) pour isoler les secrets.
Dans la cybersécurité souveraine ↑ Cette chronique appartient à la section Digital Security, centrée sur les exploits, vulnérabilités systémiques et contre-mesures matérielles pour environnements zero-trust.
- Résumé rapide
- Urgence — zero-click CVE-2025-55177
- Risques du hacking WhatsApp
- Techniques employées par les attaquants
- Outils légitimes & mésusages
- Contremesures souveraines Freemindtronic
- Vulnérabilités récentes
- Campagnes de phishing avancées
- Renforcer la sécurité WhatsApp (HSM)
- Mesures préventives
- Bonnes pratiques pour la sécurité des messageries
- FAQ — zero-click WhatsApp
- Perspectives stratégiques
Résumé étendu
Comment sécuriser WhatsApp contre le hacking : conseils clés pour 2025
Le hacking de WhatsApp reste une préoccupation majeure : l’application subit des menaces sophistiquées telles que le phishing, les spywares et les détournements de compte. Protéger vos données exige de comprendre les vulnérabilités récentes de 2025 et d’adopter des solutions matérielles d’isolation. Comment se protéger et que faire en cas d’incident ? Cet article présente des mesures opérationnelles et des technologies d’encryption avancées de Freemindtronic pour renforcer la sécurité.
Principaux enseignements :
- RCE zero-click via DNG construit, chaîné avec ImageIO d’Apple.
- La synchronisation des appareils liés peut agir comme fetcher involontaire.
- Exploits observés sur cibles limitées — agir comme si exposé.
- Posture Zero-DOM (HSM/NFC) réduit le rayon d’impact post-compromission.
⧉ Depuis quand cette faille existe-t-elle ?
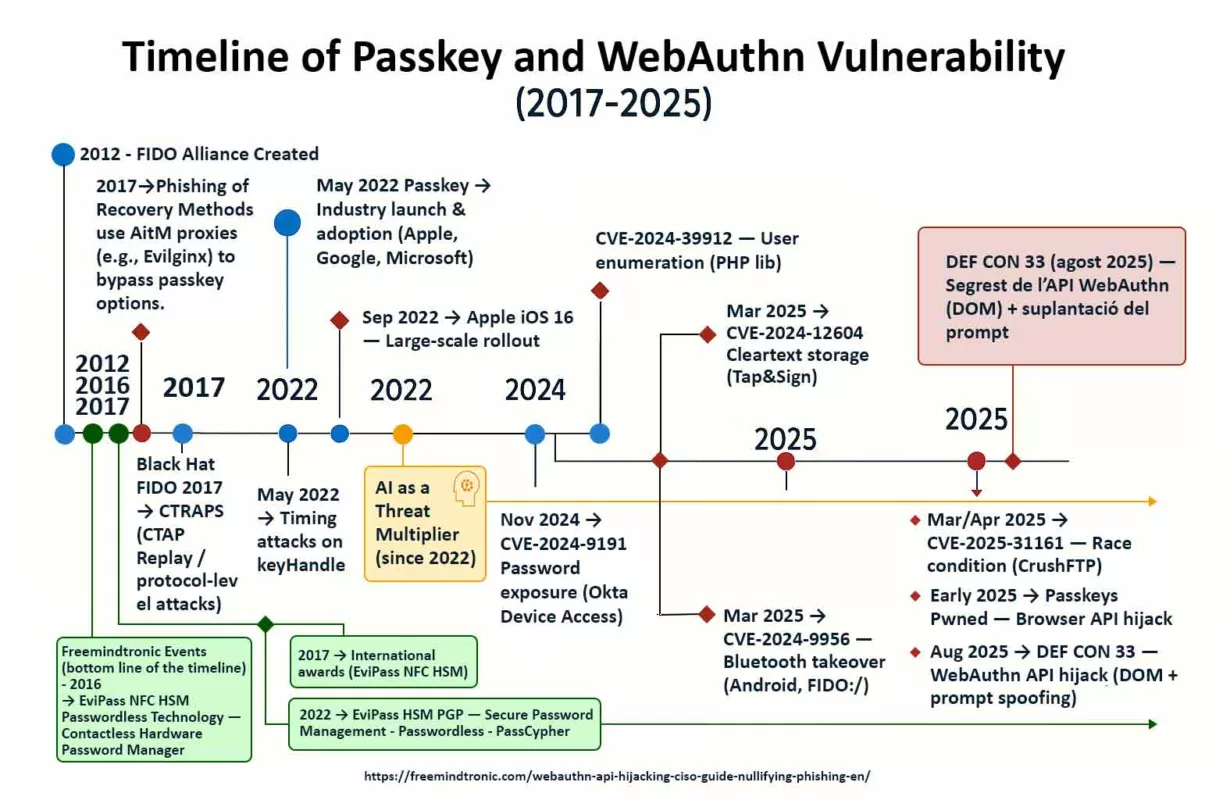
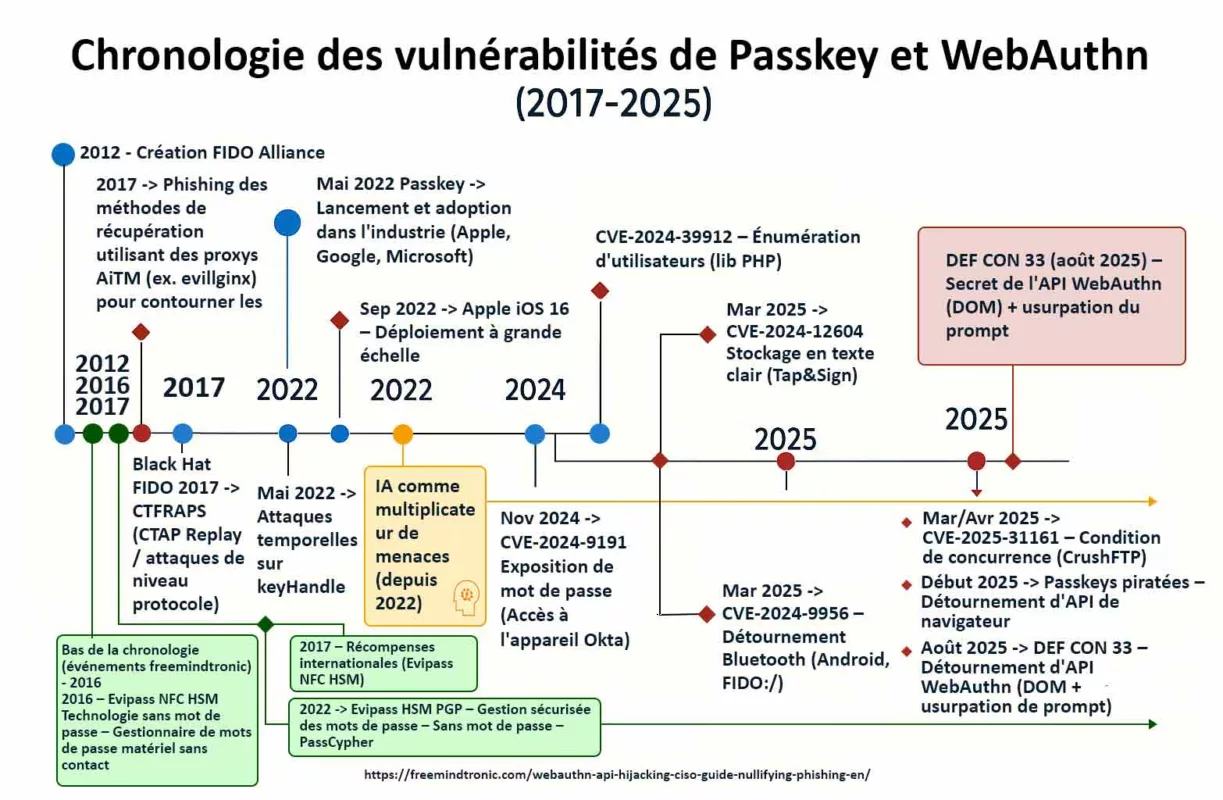
Les premières alertes remontent à mai 2025, mais la vulnérabilité CVE-2025-55177 est restée exploitable plusieurs mois, faute de correctif public. Selon les experts, elle aurait pu être utilisée bien avant sa reconnaissance institutionnelle, dans des campagnes d’espionnage ciblées — souvent sans que les victimes ne s’en rendent compte, et potentiellement depuis plusieurs années.
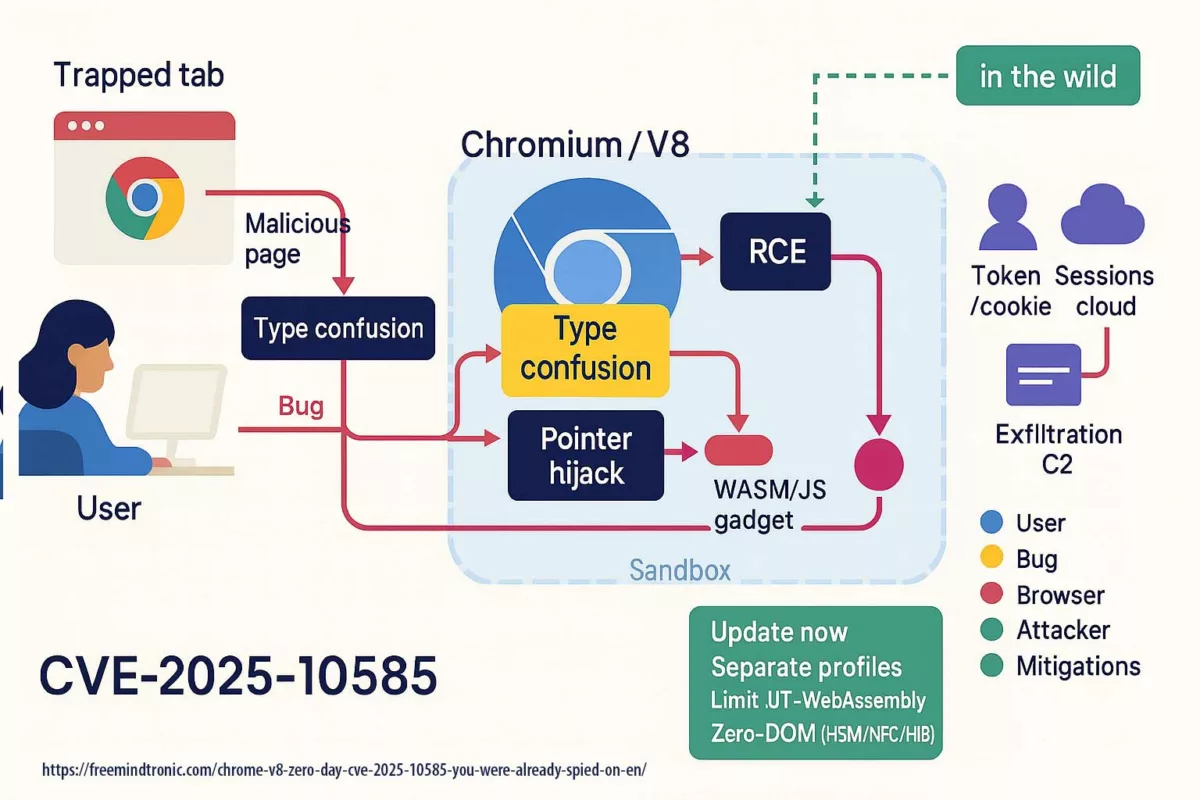
La vulnérabilité CVE-2025-55177 a permis des exécutions de code à distance sans interaction (zero-click) sur iOS et macOS. Son couplage avec CVE-2025-43300 dans ImageIO a prolongé la fenêtre d’exploitation, notamment via la synchronisation automatique des médias.
Ce contexte souligne l’intérêt d’une architecture préventive — où les secrets ne sont jamais exposés au runtime applicatif, ni concaténés sans preuve matérielle souveraine.
⧉ A-t-elle déjà été exploitée ?
Oui — des attaques ciblées ont été confirmées par Meta, et la faille figure dans le catalogue CISA KEV.
Des exploitations ont visé des profils sensibles (journalistes, ONG, diplomates), sans déclenchement visible. L’inscription dans le CISA KEV atteste d’un usage réel en contexte opérationnel.
Cette reconnaissance institutionnelle renforce la pertinence des technologies Zero-DOM / HSM : elles empêchent toute reconstruction de secret sans validation matérielle, même en cas d’exfiltration ou de compromission du DOM.
Vulnérabilité WhatsApp zero-click CVE-2025-55177 : mise à jour urgente
Urgence : vulnérabilité zero-click WhatsApp (CVE-2025-55177)
Versions affectées
- WhatsApp pour iOS : versions antérieures à 2.25.21.73
- WhatsApp Business pour iOS : versions antérieures à 2.25.21.78
- WhatsApp pour Mac : versions antérieures à 2.25.21.78
Actions immédiates recommandées
- Mettez à jour WhatsApp (iOS ≥ 2.25.21.73 · Mac ≥ 2.25.21.78) et appliquez les correctifs iOS/iPadOS/macOS corrigeant CVE-2025-43300.
- Désactivez temporairement Linked Devices et l’auto-traitement des médias si possible.
- Cas sensibles : forensique — conservez les logs (horodatages, noms de fichiers, URLs) et procédez à la rotation des secrets depuis un appareil sain.
Forensics & gestion d’incident (SOC)
- Préserver les artefacts : horodatages des messages, noms de fichiers, URLs, journaux système des appareils.
- Capturer les traces réseau (pcap) sur la fenêtre affectée ; noter les résolutions DNS vers hôtes inconnus.
- Révoquer toutes les sessions WhatsApp Web ; faire tourner les tokens / identifiants Apple depuis un appareil propre.
- Réinstaller / reimager uniquement après acquisition des images (sauvegardes mobiles, snapshots Time Machine).
Notes techniques (niveau opérateur)
- Cause racine : autorisation incomplète côté linked-device sync → déclenchement de traitements à partir d’URL arbitraires.
- Zero-click : aucune interaction requise ; chaîne observée avec CVE-2025-43300 (Image/DNG → corruption mémoire).
- Périmètre : ciblage limité (profils à haut risque) ; pas de PoC public confirmé à ce stade.
Comment prévenir et résoudre les problèmes de hacking WhatsApp
WhatsApp, qui compte plus de 2 milliards d’utilisateurs, reste une cible privilégiée. Malgré ses mécanismes, l’application n’est pas immune : phishing, vulnérabilités de parsing média et accès non autorisés peuvent compromettre la confidentialité. Protéger votre compte exige l’usage d’hygiène basique et de solutions matérielles pour isoler les secrets. Quelles mesures appliquer si vous êtes ciblé ? Ci-dessous : hygiène et isolation matérielle.
Risques liés à la Vulnérabilité WhatsApp zero-click
Le hacking de WhatsApp peut avoir des conséquences lourdes : accès non autorisé aux conversations, médias et contacts. Les attaquants peuvent usurper l’identité d’une victime, envoyer des messages frauduleux sollicitant de l’argent ou des clics malveillants, ou diffuser de la désinformation. Pour les usages professionnels, l’accès non autorisé peut exposer contrats, devis et documents sensibles — d’où la nécessité de protections renforcées.
Techniques d’attaque liées à la Vulnérabilité WhatsApp zero-click
Les attaquants emploient divers moyens : phishing avancé, exploitation de vulnérabilités (QR, parsing), contournement de la 2SV. Parmi les techniques observées :
- Phishing : messages trompeurs incitant la victime à cliquer ou fournir des données via pages factices.
- Exploitation de messagerie vocale : récupération de codes de vérification si la messagerie vocale est accessible.
- Ingénierie sociale / détournement : usurpation de confiance pour obtenir les codes de vérification.
- Scan de code QR : obtention d’un accès via WhatsApp Web en scannant un QR compromis.
Outils de surveillance légitimes et mésusages
Certains outils destinés au contrôle parental ou à la supervision peuvent être détournés. Exemples : KidsGuard, FoneMonitor, mSpy, Spyera, Hoverwatch, FlexiSPY — ces produits ont des usages légitimes mais peuvent porter atteinte à la vie privée s’ils sont mal employés.
Outils légitimes de surveillance
- KidsGuard for WhatsApp — suivi des messages, appels et médias.
- FoneMonitor — surveillance d’activité WhatsApp.
- mSpy — contrôle parental et récolte de journaux d’activité.
- Spyera — outil avancé de monitoring mobile.
- Hoverwatch — suivi de conversations et géolocalisation.
- FlexiSPY — fonctionnalités avancées (enregistrement d’appels, tracking).
Avertissement : ces outils doivent être utilisés conformément à la loi et avec le consentement des parties concernées.
Réponse souveraine à la Vulnérabilité WhatsApp zero-click
Alors que certains outils surveillants manquent de garde-fous, Freemindtronic propose des mesures matérielles pour contenir l’accès et protéger les données personnelles et professionnelles.
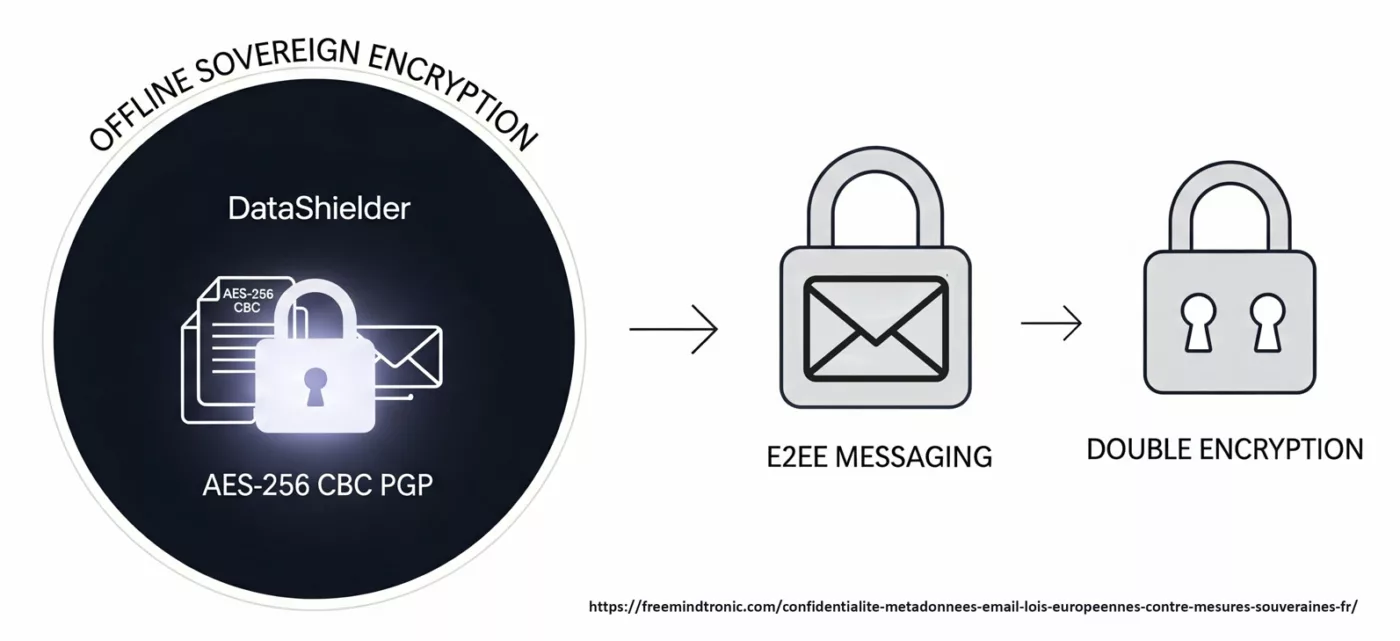
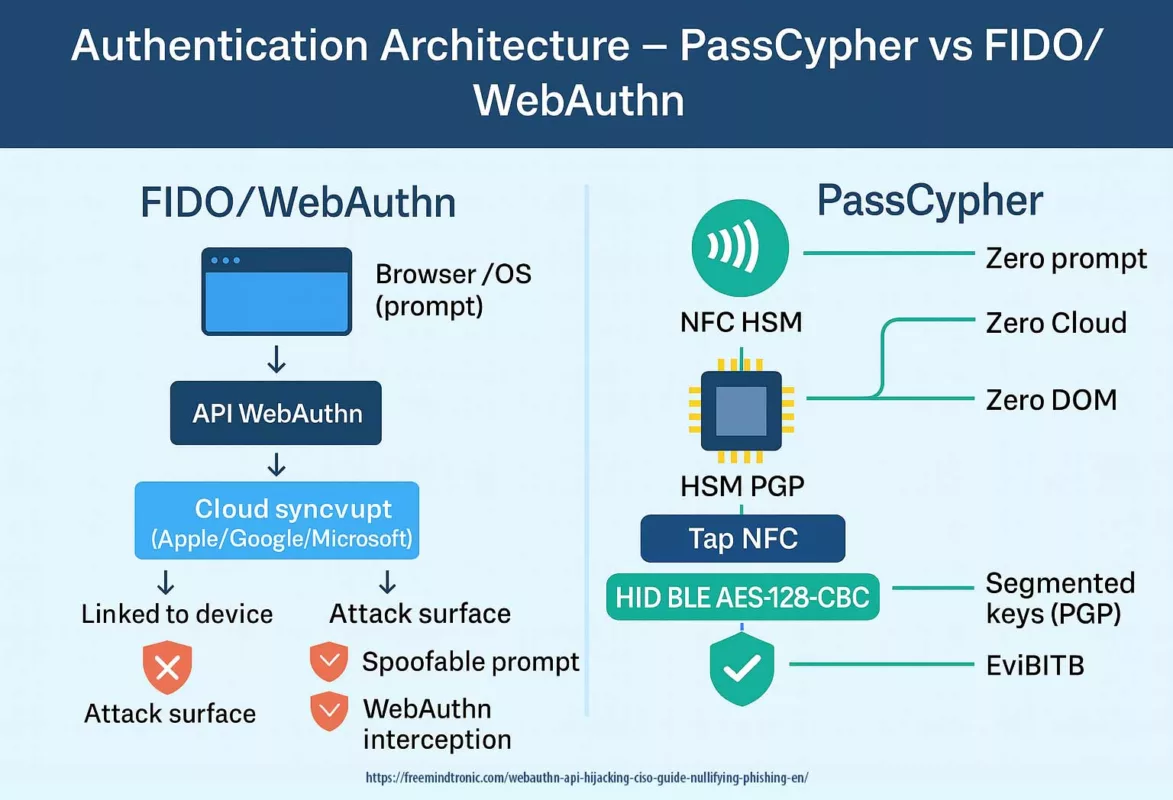
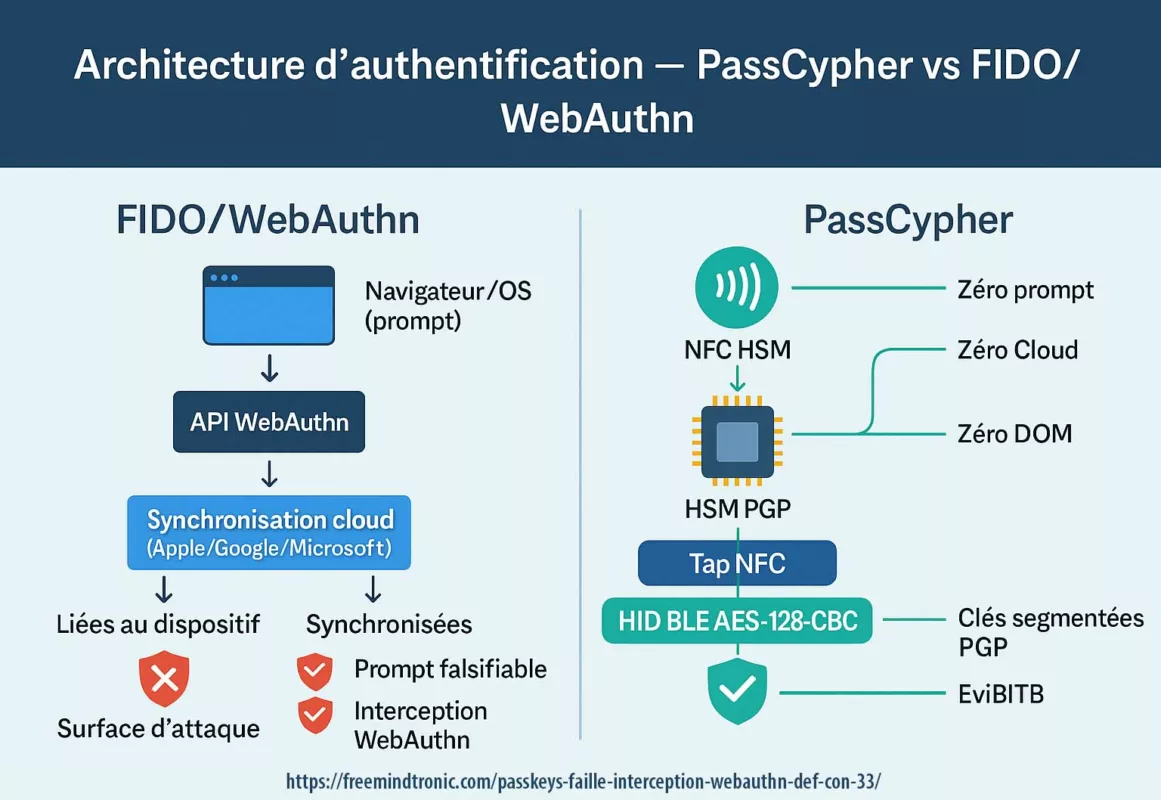
Précision opératoire — PassCypher & DataShielder (HSM PGP)
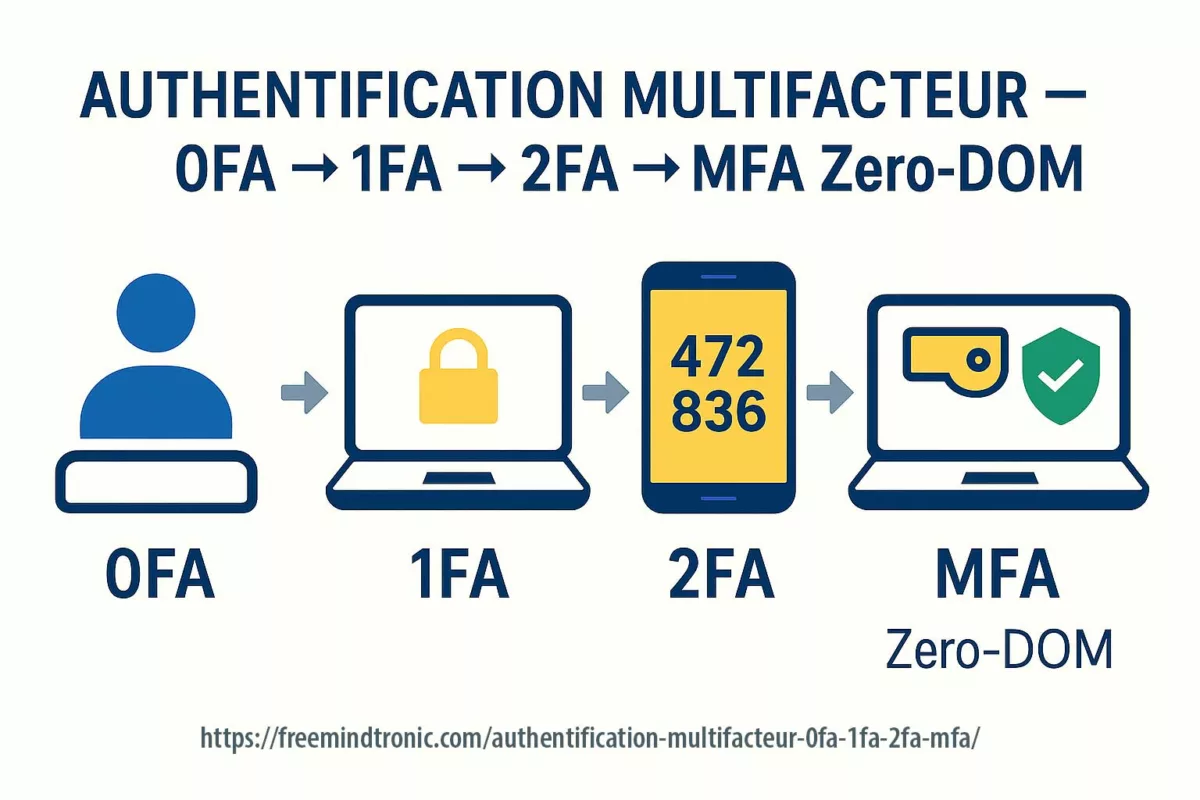
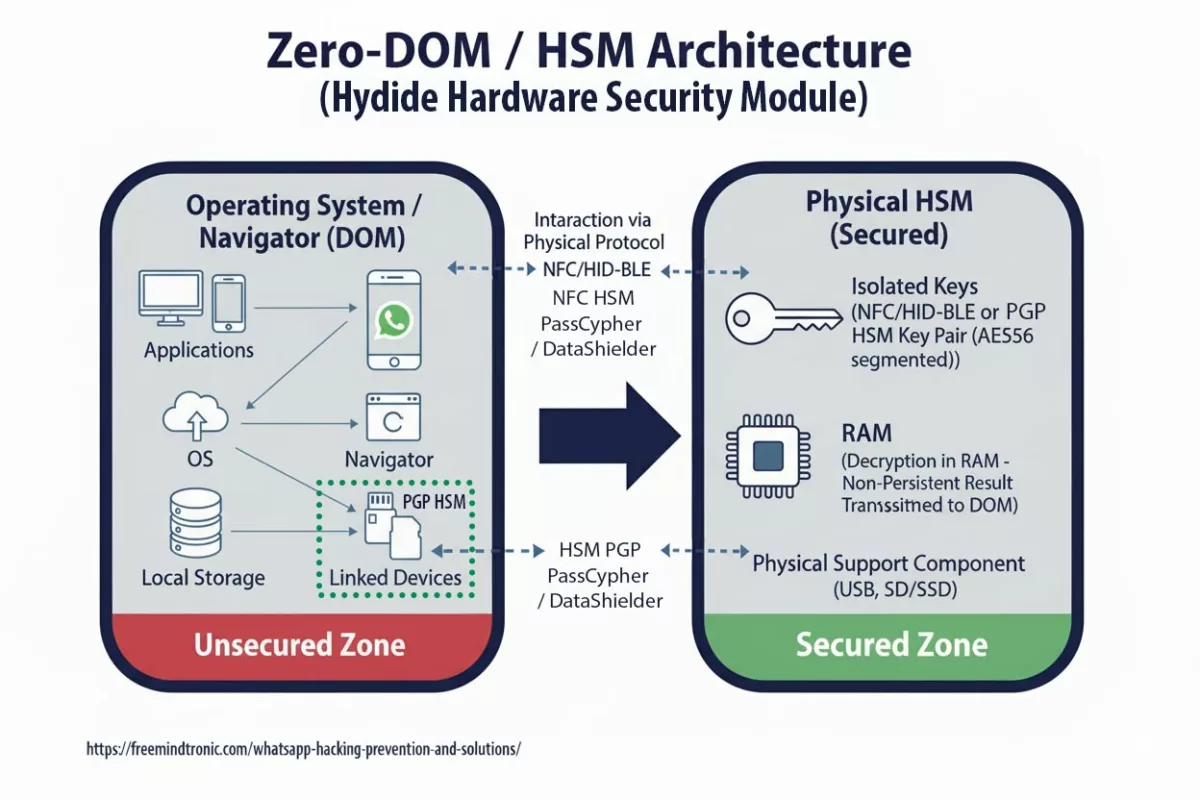
Les architectures PassCypher et DataShielder reposent sur un modèle de clés segmentées autonomes : chaque container chiffré encapsule des segments de 256 bits, et les fragments de clé correspondants demeurent isolés et sécurisés dans le local storage et le support physique HSM, sans jamais transiter ni être persistés côté hôte dans un état exploitable.
Ces segments peuvent transiter temporairement — mais jamais dans un format directement utilisable. En l’état, ils sont inexploitables sans concaténation typologique validée, laquelle ne s’effectue qu’en RAM, après preuve matérielle contextuelle (NFC HSM, support de stockage HSM PGP, et sandbox-URL).
Processus d’accès légitime :
- Le HSM valide la présence et le contexte (NFC HSM, support de stockage HSM PGP, sandbox-URL, comportement).
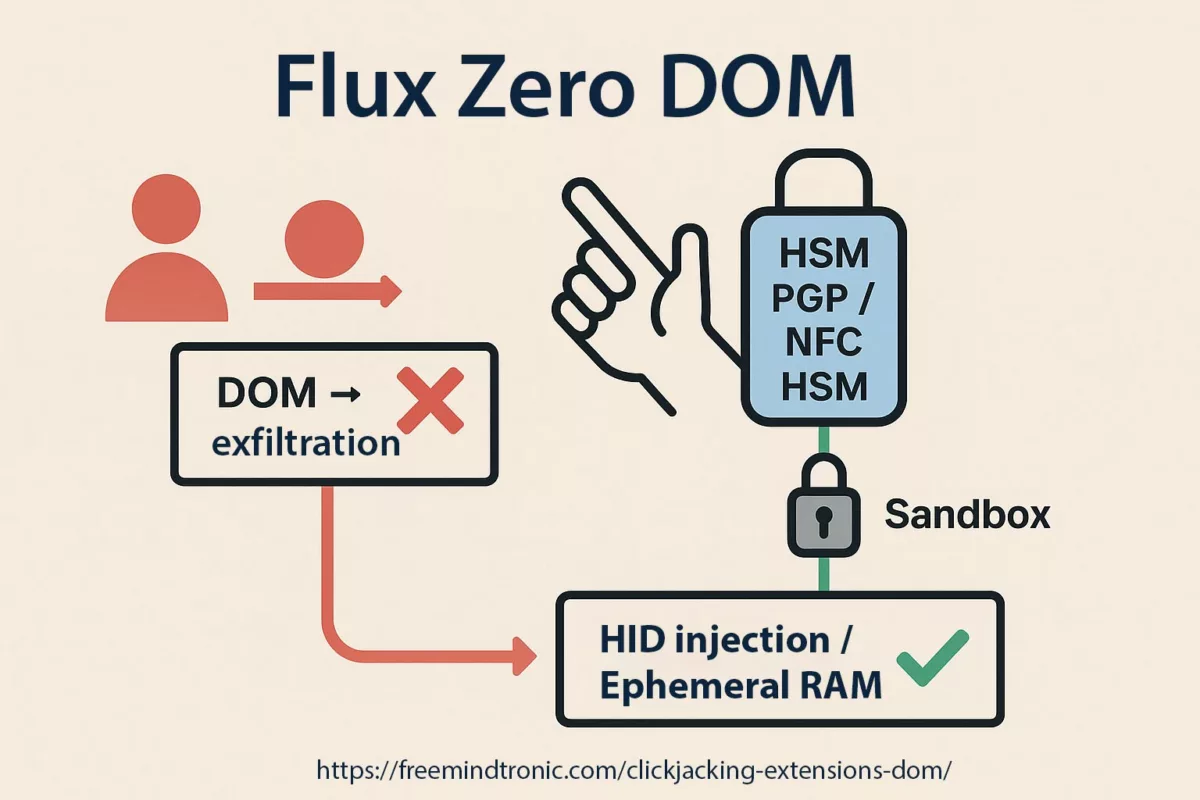
- Les segments requis sont libérés puis concaténés en RAM de l’hôte — uniquement pour la durée strictement nécessaire à l’opération (lecture, auto-fill, chiffrement/déchiffrement, génération de PIN Code ou TOTP).
- Le déchiffrement s’effectue en mémoire vive ; aucune clé n’est écrite sur disque, ni exposée dans le DOM, ni persistée dans les buffers.
- Après usage, les buffers sont effacés, et l’état repasse nativement en « locked » : les segments restent encapsulés en 256 bits dans le HSM et ne peuvent être réutilisés sans nouvelle autorisation matérielle.
Fonctions opérationnelles
- NFC HSM (mobile) : auto-remplissage sécurisé des champs WhatsApp si déconnecté, avec contrôle sandbox-URL et validation comportementale.
- HSM PGP (desktop / extension) : containers isolés contenant credentials et clés privées OTP/TOTP/HOTP ; génération automatique de PIN/TOTP et vérification Pwned Passwords intégrée.
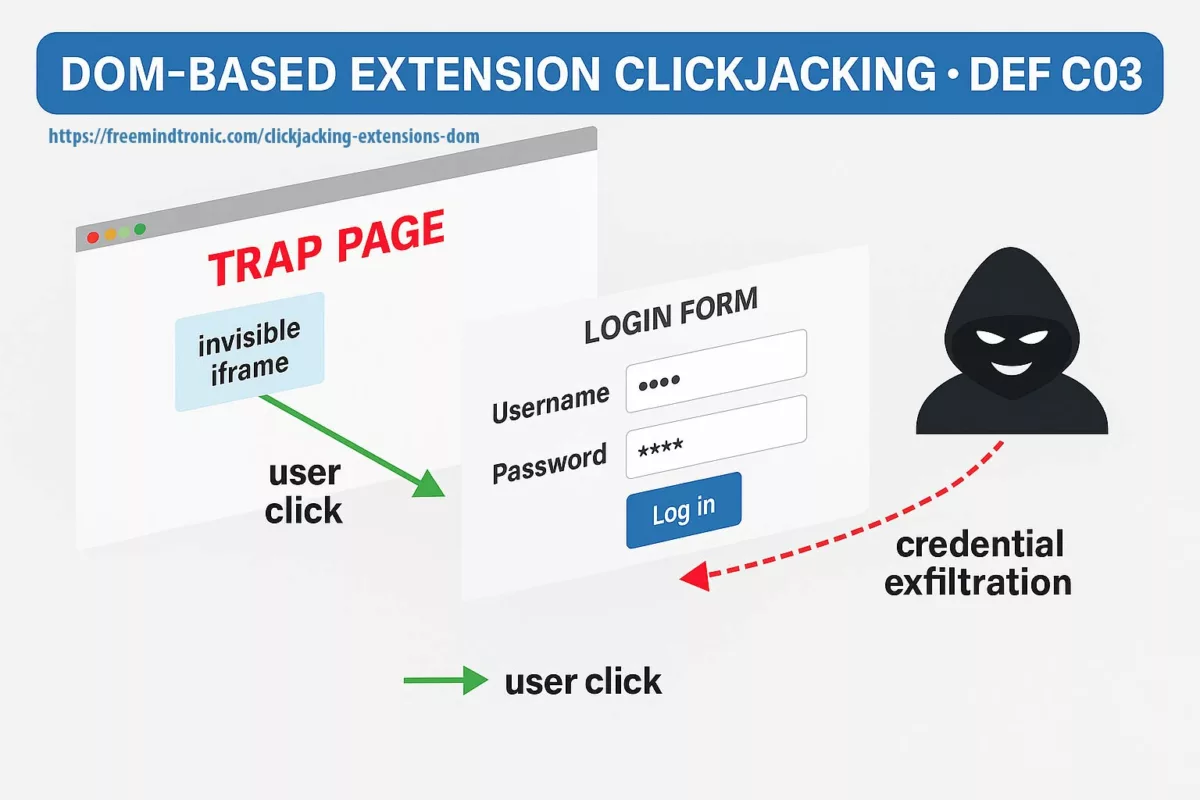
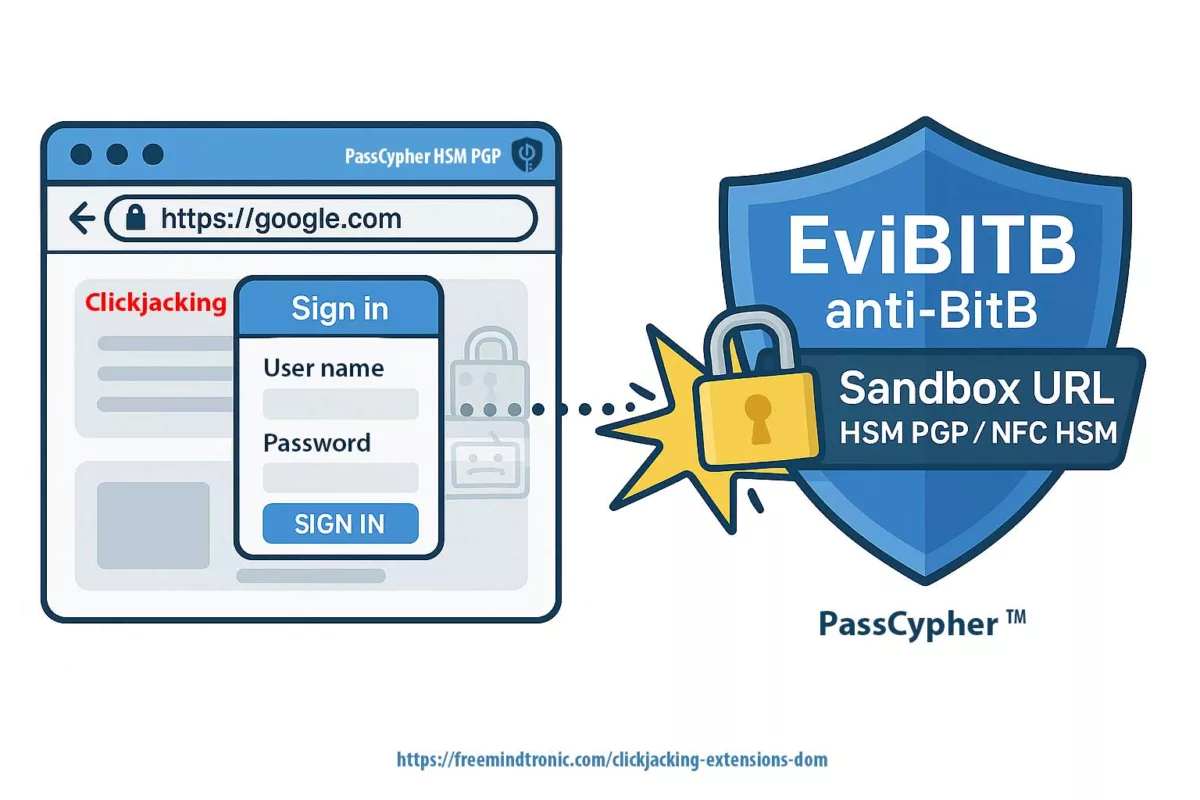
- PassCypher : protection anti-BITB (destruction automatique d’iframes suspectes) et contrôle sandbox avant toute injection de secret.
- Sécurité mémoire : concaténation et déchiffrement en RAM, de manière atomique, éphémère et non exploitable — aucune persistance, aucune écriture disque, aucune exposition DOM.
Conséquence typologique : même en cas d’exécution de code malveillant côté navigateur (zero-click), ou d’exfiltration des blobs chiffrés, l’attaquant ne peut ni reconstruire ni exploiter les secrets sans la preuve matérielle souveraine fournie par le HSM.
Nota : les clés segmentées stockées localement ne sont jamais dans un format directement exploitable. Leur reconstruction nécessite une concaténation validée et une dérivation typologique en contexte sécurisé.
Pourquoi Freemindtronic ?
- PassCypher NFC HSM Lite
- Sécurise l’accès WhatsApp via OTP/TOTP/HOTP générés localement, sans dépendance cloud.
- Neutralise le phishing et le vol d’identifiants grâce à des mots de passe non réutilisables.
- Fonctionne sans contact, sans alimentation, et sans exposition DOM.
- PassCypher HSM PGP
- Gestion avancée des mots de passe et chiffrement PGP avec stockage sécurisé sur HSM.
- Protection des données sensibles via clés isolées, segmentées et non persistées.
- Compatible avec les environnements desktop et extensions navigateur.
- DataShielder NFC HSM Starter Kit
- Chiffrement en temps réel des messages/fichiers (AES-256 CBC)
- Partage de secrets avec encapsulation typologique via RSA 4096 généré et stocké dans le NFC HSM.
- Clés stockées localement, inaccessibles aux attaquants distants ou aux scripts malveillants.
Fonctions de protection
- Anti-phishing / BITB : atténuation des attaques Browser-in-the-Browser par destruction automatique des iframes de redirection.
- Chiffrement en temps réel : protection même si l’appareil est compromis.
- Sécurité matérielle : clés localisées hors application, hors cloud, et hors portée des vecteurs DOM.
Découvrez comment le DataShielder NFC HSM Starter Kit peut sécuriser vos communications.
Comment se prémunir contre le mésusage
- Restreindre les permissions d’app pour éviter l’accès non justifié.
- Auditer régulièrement les apps installées pour détecter les outils de surveillance cachés.
- Utiliser le chiffrement matériel (NFC HSM) pour chiffrer en amont avant sauvegarde cloud.
Erreur humaine : vecteur persistant
Les arnaques demandant le code de vérification à six chiffres restent efficaces : l’usurpation par contact de confiance est courante. La 2SV limite le risque mais ne l’élimine pas.
Comment DataShielder protège le contenu
- Chiffrement hors-WhatsApp : même si le compte est compromis, le contenu chiffré par DataShielder/HSM PGP reste inaccessible sans la clé matérielle.
- Stockage local des clés : prévention contre l’extraction depuis l’app ou le cloud.
- Intégration Web : HSM PGP permet le chiffrement côté client, utilisable avec WhatsApp Web via flux Zero-DOM (selon intégration).
- Anti-phishing : PassCypher génère OTP dynamiques (TOTP/HOTP) pour réduire le risque de takeover.
En résumé
Les technologies NFC HSM et HSM PGP ne se contentent pas de répondre aux failles : elles définissent une nouvelle typologie de sécurité. Elles sont préventives, non réactives, non simulables et non exploitables sans preuve matérielle. Elles incarnent une architecture de souveraineté numérique dans laquelle chaque opération est conditionnée, traçable et non rejouable.
Bonnes pratiques pour la sécurité des messageries — chiffrement temps réel et solutions matérielles
Suite aux alertes récentes, forcer la vérification en deux étapes reste crucial. Activer 2SV empêche un takeover si un code est compromis. Pour une protection renforcée, combinez bonnes pratiques (2SV, éviter Wi-Fi public) et solutions matérielles (DataShielder, HSM PGP, PassCypher). Ces technologies ajoutent des couches de défense critiques.
Spyware Pegasus & NSO Group
En décembre 2024, une décision fédérale (Northern District of California) a jugé NSO responsable pour l’usage non autorisé de serveurs WhatsApp pour déployer Pegasus. Le cas illustre les risques des frameworks de surveillance commerciale et rappelle l’impératif de maintenir les applications à jour. Voir le document officiel cité pour les détails.
Décision marquante : responsabilité de NSO Group
La juridiction a confirmé que des acteurs commerciaux développant des spywares ne peuvent échapper à la responsabilité lorsqu’ils agissent hors cadre gouvernemental. Pour le texte intégral : document de sauvegarde.
Campagnes de phishing avancées visant WhatsApp : protégez vos données en 2025
En janvier 2025, le groupe « Star Blizzard » a mené des campagnes ciblées contre des responsables via phishing multi-étapes. Ces attaques combinent email trompeur, QR corrompu et usurpation via WhatsApp Web. Elles démontrent que même des profils hautement protégés peuvent être piégés.
Pourquoi ces menaces comptent
Les campagnes montrent l’adaptabilité des attaquants : ils exploitent formats établis (Safe Links, QR) et la confiance. La défense efficace demande des dispositifs matériels et des processus d’authentification rigoureux.
Contre-mesures Freemindtronic
- DataShielder NFC HSM M-Auth : chiffrement en temps réel et critères de confiance d’origine physique.
- DataShielder HSM PGP : chiffrement PGP avec clés isolées sur HSM pour protéger messages et fichiers.
Vulnérabilités WhatsApp récentes
WhatsApp a corrigé plusieurs vulnérabilités critiques : RCEs dans des handlers média en 2023/2024 et d’autres failles illustrent l’importance d’appliquer les mises à jour. Restez à jour.
Renforcer la sécurité WhatsApp
Nouvelles fonctionnalités : Account Protect, Device Verification, Automatic Security Codes — ces mécanismes améliorent la résilience mais ne remplacent pas l’isolation matérielle pour les échanges de haute sensibilité.
Recommandations supplémentaires
Combinez messages éphémères, chiffrement hors-app et politiques MDM pour réduire l’exposition.
Renforcer la sécurité WhatsApp en 2025 : DataShielder NFC HSM et outils de chiffrement avancés
Pour des scénarios où les identifiants peuvent être compromis, intégrer des HSM matériels (DataShielder NFC HSM, DataShielder HSM PGP, PassCypher NFC HSM) renforce la défense.
DataShielder NFC HSM stocke et gère les clés sur matériel ; DataShielder HSM PGP protège les messages via PGP ; PassCypher génère OTP dynamiques (TOTP/HOTP).
Mesures préventives contre le hacking WhatsApp
Activez la vérification en deux étapes, utilisez biométrie, changez régulièrement le code de messagerie vocale, et associez ces pratiques à des solutions matérielles (EviCrypt, DataShielder, PassCypher). Ces mesures réduisent le risque de takeover et limitent l’impact d’attaques sophistiquées.
Bonnes pratiques contre la Vulnérabilité WhatsApp zero-click
- Vérifiez toute demande inhabituelle via un second canal.
- Activez la vérification en deux étapes.
- Si compromis : déconnectez toutes les sessions Web et contactez le support WhatsApp depuis un appareil sain.
Contremesures souveraines avancées
Intégrer PassCypher (OTP), EviCrypt (chiffrement local), et flux Zero-DOM pour réduire la fenêtre d’exposition.
⮞ Cas d’usage souverain | Résilience avec Freemindtronic Avec DataShielder NFC HSM et PassCypher HSM PGP, les secrets ne touchent jamais le DOM : validation physique (NFC/HID-BLE), déchiffrement éphémère en RAM, pas de persistance. Cela limite matériellement l’impact des zero-clicks et des hijacks de session Web.
- Chiffrement hors-navigateur (Zero-DOM) pour messages/fichiers.
- Matériel air-gapped ; pas de télémétrie cloud.
- Flux PGP/OTP résistants au phishing et au takeover par QR.
FAQ — zero-click WhatsApp
Oui. La chaîne abusait de la synchronisation des appareils liés + traitement automatique des médias pour déclencher le parsing d’un DNG construit (zero-click). Patch WhatsApp et iOS/iPadOS/macOS, puis réactivez les fonctions uniquement si nécessaire. Voir Urgence — zero-click CVE-2025-55177.
Builds corrigées : iOS ≥ 2.25.21.73, Business iOS ≥ 2.25.21.78, Mac ≥ 2.25.21.78. Mettez aussi à jour l’OS Apple pour CVE-2025-43300. Voir affected versions.
Pour les profils à haut risque : oui, temporairement — ou utilisez des clés isolées (Zero-DOM / HSM) pour limiter l’exposition.
Considérez-les sensibles : préférez le chiffrement côté client (PGP/HSM) avant la sauvegarde, réduisez la rétention et limitez qui peut restaurer. L’isolation matérielle empêche l’extraction de clés.
Horodatages, noms de fichiers, URLs, journaux système, crash logs (ImageIO) et traces réseau. Révoquez les sessions Web et faites tourner les identifiants depuis un appareil propre.
Perspectives stratégiques
Les zero-clicks ne vont pas disparaître. Les piles de messagerie continueront d’absorber des risques de niveau navigateur via les ponts Web/Desktop et les codecs média. La voie durable repose sur deux axes : raccourcir les fenêtres de patch et retirer les secrets de la mémoire applicative. Les entreprises doivent formaliser une doctrine Zero-DOM pour les échanges à haute valeur, imposer des baselines MDM restreignant WhatsApp Web, et faire tourner les identifiants depuis des appareils propres après tout soupçon d’attaque.
Checklist admin (entreprise / MDM)
- Appliquer et forcer les versions patchées via MDM.
- Désactiver temporairement WhatsApp Web sur postes gérés à risque.
- Durcir le traitement média (macOS/iOS) et restreindre les fetchs d’URL arbitraires.
- Adopter l’isolation matérielle pour VIPs (NFC HSM / PGP) — Zero-DOM pour échanges critiques.
- Effectuer des chasses ciblées : anomalies DNG/RAW, crash ImageIO, WebSockets suspects.