Apple M-Chip Vulnerability: Critical Risk
Learn about the critical Apple M-chip flaw, a micro-architectural vulnerability that threatens data security. This article reveals the attack process exploiting data prefetching and encryption key extraction, highlighting the major security impact. Essential reading to understand and anticipate the risks linked to this alarming discovery.
Apple M chip vulnerability: uncover the critical security breach highlighted by MIT (CSAIL). Stay updated with our latest insights.
Apple M chip vulnerability: uncovering a breach in data security
Researchers at the Massachusetts Institute of Technology’s (MIT) Computer Science and Artificial Intelligence Laboratory (CSAIL) have unveiled a critical hardware flaw within Apple’s M-series chips, dubbed the “Apple M chip vulnerability,” marking a significant breach in data security. This vulnerability, referred to as ‘GoFetch,’ highlights a concerning issue in the chips’ microarchitecture, potentially compromising the integrity of sensitive information stored on millions of devices. Unlike previous security flaws, this unpatchable vulnerability allows for the unauthorized extraction of cryptographic keys through a secondary channel during the execution of cryptographic protocols, posing a serious threat to data security across a broad spectrum of devices. The discovery underscores the vulnerability’s profound implications, as it affects not only the security of Apple devices but also the broader ecosystem relying on these cryptographic protocols.
Exploiting the Apple M Chip Vulnerability Without Elevated Privileges
A notable aspect of this vulnerability is its exploitation without the need for elevated privileges. Academic researchers have devised an application capable of retrieving cryptographic keys from other applications running the affected algorithms. This exploitation leverages the Data Memory-Dependent Prefetcher (DMP) within the chips, which can mistakenly interpret data as memory addresses, thereby enabling attackers to reconstruct secret keys.
The Risk to Users’ Sensitive Data
The implications of this vulnerability are far-reaching, affecting all common cryptographic algorithms, including those designed to be quantum-resistant. Researchers have demonstrated the successful extraction of RSA, DHKE, Kyber, and Dilithium keys, with extraction times varying from 49 minutes to 15 hours, depending on the algorithm. This vulnerability endangers the integrity of encrypted data, including sensitive personal and financial information.
The Mechanics Behind the Attack
The vulnerability arises from the architectural design of Apple’s M1, M2, and M3 chips, which, similar to Intel’s latest Raptor Lake processors, utilize caches to enhance performance. These caches can inadvertently mix up data with memory addresses, leading to potential data leakage. A well-designed cryptographic code should operate uniformly in time to prevent such vulnerabilities.
La Vulnérabilité des Puces M d’Apple: A Risk to Cryptocurrency Wallets
The discovery of this vulnerability also casts a shadow over the security of cryptocurrency wallets. Given the flaw’s capacity for cryptographic key extraction through side-channel attacks, users of cold wallets or hardware wallets connected to computers with vulnerable chips for transactions may face heightened risks. These vulnerabilities underscore the importance of assessing the security measures of cold wallets and hardware wallets against such exploits.
Impact on Cold Wallets and Hardware Wallets
Private key extraction poses a serious threat, especially when devices are connected to vulnerable computers for transactions. This vulnerability could compromise the very foundation of cryptocurrency security, affecting both local and remote attack scenarios.
Security Recommendations
Manufacturers of cold and hardware wallets must promptly assess and address their vulnerability to ensure user security. Users are advised to adhere to best security practices, such as regular updates and minimizing the connection of cold wallets to computers. An effective alternative is the utilization of Cold Wallet NFC HSM technology, such as Freemindtronic’s EviVault NFC HSM or EviSeed NFC HSM, embedded in Keepser and SeedNFC HSM products, offering robust protection against such vulnerabilities.
Apple M Chip Vulnerability: Unveiling the Unpatchable Flaw
This flaw, inherent to the microarchitecture of the chips, allows the extraction of cryptographic keys via a secondary channel during the execution of the cryptographic protocol.
This discovery of an “irreparable flaw” in Apple’s M-series chips could seriously compromise data security by allowing unauthorized extraction of encryption keys. This vulnerability constitutes a significant security flaw, posing a substantial risk to user data across various devices.
The Micro Architectural Rift and its Implications: Unveiling the Apple M Chip Vulnerability
Critical Flaw Discovered in Apple’s M-Chips
Moreover, the recent discovery of the ‘Apple M chip vulnerability’ in Apple’s M-series chips has raised major IT security concerns. This vulnerability, inherent in the silicon design, enables extraction of cryptographic keys through a side channel during the execution of standard cryptographic protocols. Furthermore, manufacturers cannot rectify this flaw with a simple software or firmware update, as it is embedded in the physical structure of processors.
Implications for Previous Generations
Additionally, the implications of the ‘Apple M chip vulnerability’ are particularly severe for earlier generations of the M-series, such as M1 and M2. Furthermore, addressing this flaw would necessitate integrating defenses into third-party cryptographic software, potentially resulting in noticeable performance degradation when performing cryptographic operations.
Hardware optimizations: a double-edged sword
Moreover, modern processors, including Apple’s M-series and Intel’s 13th Gen Raptor Lake microarchitecture, utilize hardware optimizations such as memory-dependent prefetching (DMP). Additionally, these optimizations, while enhancing performance, introduce security risks.
New DMP Research
Moreover, recent research breakthroughs have unveiled unexpected behavior of DMPs in Apple silicon. Additionally, DMPs sometimes confuse memory contents, such as cryptographic keys, with pointer values, resulting in data “dereference” and thus violating the principle of constant-time programming.
Additionally, we can conclude that the micro-architectural flaw and the unforeseen behaviors of hardware optimizations emphasize the need for increased vigilance in designing cryptographic chips and protocols. Therefore, addressing these vulnerabilities necessitates ongoing collaboration between security researchers and hardware designers to ensure the protection of sensitive data.
Everything you need to know about Apple’s M chip “GoFetch” flaw
Origin of the fault
The flaw, dubbed “GoFetch,” was discovered by researchers at the Computer Science and Artificial Intelligence Laboratory (CSAIL) at the Massachusetts Institute of Technology (MIT). It affects Apple’s M1, M2 and M3 chips and allows for the extraction of encryption keys, compromising data security1.
Level of hazardousness
The vulnerability is considered severe because it cannot be fixed by a simple software patch. Furthermore, it is due to a specific hardware optimization in the architecture of the chips, making it difficult to correct without significantly impacting the performance of the devices.
Apple’s response and actions taken
Moreover, to date, Apple has not yet officially communicated about this flaw. Security experts recommend the use of software solutions to mitigate risk, although this may reduce the performance of affected devices.
Source of the vulnerability report
The detailed report on this vulnerability has been published by CSAIL. For an in-depth understanding of the flaw and its implications, it is advisable to consult the full research paper provided by the researchers.
Understanding the ‘Apple M chip vulnerability’ and its ‘GoFetch’ flaw
Vulnerability Description
- Data Memory-Dependent Prefetcher (DMP): Moreover, this function in Apple’s M chips is designed to improve performance by predicting and loading data that the CPU might need next. However, it has a vulnerability that can be exploited through a side-channel attack.
- Side-Channel Attack: Additionally, the flaw allows attackers to observe the effects of the DMP’s operation, such as timing information, to infer sensitive data.
- Encryption Key Extraction: Furthermore, by exploiting the DMP’s behavior, attackers can extract encryption keys that are used to secure data on the device. This includes keys from widely-used cryptographic protocols like OpenSSL Diffie-Hellman, Go RSA, CRYSTALS Kyber, and Dilithium.
Level of Hazardousness
Additionally, the “GoFetch” flaw is considered very dangerous because it is a hardware-level vulnerability. It cannot be fixed with a software update without potentially reducing chip performance.
The diagram illustrating the level of hazardousness of the micro-architectural flaw in the Apple M-Chip, specifically the “GoFetch” flaw, has been successfully created. Moreover, this visual representation captures the flaw’s inception at the Data Prefetching (DMP) function, its exploitation through the attack process, the subsequent extraction of encryption keys, and the final security impact, including compromised data privacy and security breaches.
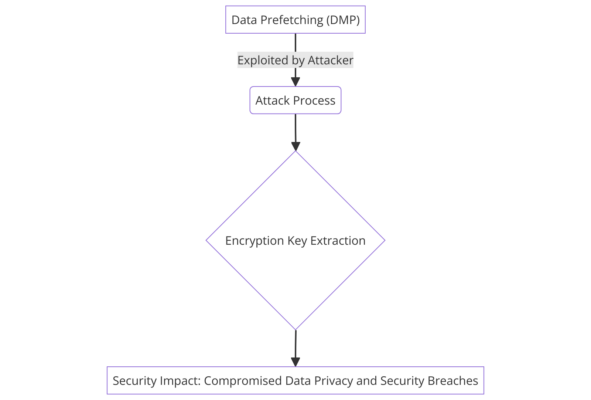
- Data Prefetching (DMP): Furthermore, a diagram component shows the DMP function, which is the initial target for the attack.
- Attack Process: Additionally, a flow demonstrates how the attacker exploits the DMP to initiate a side-channel attack.
- Encryption Key Extraction: Moreover, a depiction of the attacker successfully retrieving the encryption keys through the side-channel.
- Security Impact: Additionally, the final part of the diagram should show the potential risks, such as compromised data privacy and security breaches.
Impact and Timeline of Apple M1, M2, and M3 Chips: Assessing the ‘Apple M chip vulnerability’ Impact and Progression
The ‘Apple M chip vulnerability’ affects all Macs running Apple silicon, including M1, M2, and recent M3 chips. This includes a wide range of Mac and MacBook computers, which are now susceptible to side-channel attacks exploiting this vulnerability.
Apple computer affected by this flaw
The ‘Apple M chip vulnerability’ impacts a wide range of Apple hardware, starting with the launch of the first Mac system-on-chip, the M1, in November 2020. This hardware includes the M1, M1 Pro, M1 Max, M1 Ultra, M2, M2 Pro, M2 Max, M2 Ultra, M3, M3 Pro, and M3 Max chips.
| Date | Model | Description |
| Nov 2020 | M1 | Introducing the M1 to MacBook Air, MacBook Pro, and Mac mini 13″ |
| Apr 2021 | M1 | Launch of the iMac with M1 chip |
| Oct 2021 | M1 Pro and M1 Max | M1 Pro and M1 Max arrive in 14-inch and 16-inch MacBook Pros |
| March 2022 | M1 Ultra | M1 Ultra launches with Mac Studio |
| June 2022 | M2 | Next generation with the M2 chip |
| Jan. 2023 | M2 Pro and M2 Max | M2 Pro and M2 Max launch in 14-inch and 16-inch MacBook Pros, and Mac mini |
| June 2023 | M2 Ultra | M2 Ultra launches on Mac Studio and Mac Pro |
| Oct 2023 | M3 | M3 series with the M3, M3 Pro and M3 Max |
To establish the extent of the problem of Apple’s M chip vulnerability and its consequences on a global scale, we sought to establish the most accurate statistics published on the internet to try to assess as accurately as possible the number of devices affected and the geographical scope of the impact.
The Magnitude of the ‘Apple M chip vulnerability’: Global Consequences and Statistics
The “GoFetch” vulnerability in Apple’s M chips has a potential impact on millions of devices around the world. Since the introduction of the M1 chip in November 2020, Apple has sold tens of millions of Mac computers with the M1, M2, and M3 chips, with a presence in more than 100 countries. This security flaw therefore represents a significant threat to data privacy and security on a global scale.
Potential Consequences:
- Privacy breach: Because encryption keys can be extracted, sensitive user data is at risk.
- Business impact: Organizations that rely on Apple devices for their operations could face costly data breaches.
- Economic repercussions: Confidence in the safety of Apple products could be shaken, potentially affecting future sales.
It is crucial that users are aware of this vulnerability and take steps to secure their devices, pending an official response from Apple and potential solutions to mitigate the risks associated with this critical security breach.
Statistics
In terms of sales, Apple’s A and M chips have seen impressive growth, with a 54% increase in revenue, reaching $2 billion in the first quarter. This positive trend reflects the widespread geographic impact and growing adoption of Apple Silicon technologies.
Based on available data, here is an estimate of the number of Apple computers with the M1, M2, and M3 chips sold, broken down by geographic region:
Statistics Table Detailed Statistics
Based on available data, here is an estimate of the number of Apple computers with the M1, M2, and M3 chips sold, broken down by geographic region:
| Region | Estimated sales |
| Americas | 2 millions |
| Europe | 1.5 million |
| Greater China | 1 million |
| Japan | 500 000 |
| Middle East | 300 000 |
| Africa | 200 000 |
| Asia-Pacific | 300 000 |
| Latin America | 100 000 |
| Eastern Europe | 100 000 |
Estimated total: 6 million units sold.
These estimates underscore the importance of the “GoFetch” vulnerability and the need for Apple to effectively respond to this security flaw on a global scale.
These estimates are based on market shares and sales trends in these regions. They give an idea of the distribution of sales of Macs with the M1, M2, and M3 chips outside of major markets.
These figures are based on overall sales and may vary depending on the sources and methods of calculation. Still, they give an idea of the scale of Apple’s M-chip distribution around the world and highlight the importance of the “GoFetch” vulnerability on a global scale. It’s important to note that these numbers are estimates, and exact sales data by country isn’t always published by Apple or third-party sources.
What are the Safeguards?
The IT security expert community emphasizes the importance of developing software solutions to mitigate risk, even if it could lead to a significant decrease in the performance of affected devices. Solutions like DataShielder Defense NFC HSM, developed by Freemindtronic, offer hardware or hybrid countermeasures to secure encryption keys
DataShielder NFC HSM
DataShielder Defense NFC HSM, developed by Freemindtronic, offers advanced security measures to protect encryption keys against vulnerabilities such as “GoFetch.” Utilizing AES-256 and RSA-4096 encryption through an NFC HSM and/or hybrid hardware and software HSM PGP for data encryption as well as wifi, Lan, Bluetooth, and NFC communication protocols, DataShielder enables externalized encryption for Apple computers, ensuring the confidentiality and integrity of sensitive data. This solution is particularly beneficial for businesses and organizations handling highly sensitive information, providing them with robust cybersecurity and security against potential cyber threats.
DataShielder HSM PGP
DataShielder HSM PGP provides a secure hybrid HSM PGP platform solution for generating, storing, and managing PGP keys, offering end-to-end encryption for email communications via a web browser. By integrating mechanisms for creating secure containers on multiple hardware supports that can be physically externalized from the computer, DataShielder HSM PGP enhances the confidentiality and authenticity of email exchanges by encrypting emails, thus mitigating the risk of interception or tampering by malicious actors. This solution is ideal for all types of businesses, financial institutions, and companies requiring stringent data protection measures without the risk of relying on their computers’ security vulnerabilities.
DataShielder Defense
DataShielder Defense provides comprehensive protection against hardware vulnerabilities and cyber threats by combining hardware and software hybrid encryption compatible with all types of storage media, including NFC HSM. It incorporates the management of various standard symmetric and asymmetric encryption keys, including freely selectable Open PGP encryption algorithms by the user. By protecting sensitive data at the hardware level, without servers, without databases, and in total anonymity, DataShielder Defense ensures a very high level of security considered post-quantum, offering a wide range of applications, including data storage, communication, and processing. This solution is particularly advantageous for governmental entities and organizations dealing with classified information. It serves as a counter-espionage tool suitable for organizations looking to strengthen their cybersecurity posture and mitigate risks associated with very complex emerging threats.
In summary, DataShielder solutions provide effective countermeasures against hardware vulnerabilities like “GoFetch,” offering organizations reliable protection for their sensitive data and critical assets. Through continuous innovation and collaboration with industry partners, DataShielder remains at the forefront of data security, empowering organizations to defend against evolving cyber threats and protect their digital infrastructure.
Let’s summarize
The recent discovery of a vulnerability in Apple M chips, dubbed “GoFetch,” by MIT researchers raises major concerns about data security on devices equipped with these chips. This flaw potentially exposes millions of Mac computers worldwide to side-channel attacks, compromising the privacy of stored information.
In conclusion on the vulnerability of Apple M series chips: Addressing the critical Apple M chip vulnerability
The vulnerability discovered in Apple’s M-series chips, known as “GoFetch,” by researchers at MIT underscores the significant challenges facing hardware manufacturers in terms of security. Effective safeguards, both in software and hardware, are crucial to mitigate risks and uphold the security of sensitive user data. Collaboration among manufacturers, security researchers, and government entities is essential to develop robust solutions and ensure protection against emerging threats.
In conclusion, the prompt identification and resolution of hardware vulnerabilities like “GoFetch” are imperative for maintaining user confidence and safeguarding the integrity of IT systems. Continuous evaluation and implementation of technological advancements and security best practices are necessary to provide adequate protection against potential threats.








