2025, Digital Security
Signal Clone Breached: Critical Flaws in TeleMessage
Signal Clone Breach: The TeleMessage Scandal That Exposed a Foreign Messaging App Inside U.S. Government
TeleMessage, an Israeli-developed clone of Signal used by U.S. federal agencies, was breached by a hacker in just 20 minutes. This incident compromised diplomatic and government communications, triggered a Senate inquiry, and sparked a national debate about digital sovereignty, encryption trust chains, and FedRAMP reform. As the breach unfolded, it revealed deeper concerns about using foreign-developed, unaudited messaging apps at the highest levels of U.S. government operations.
Key Takeaways
- A “secure” app breached in under 20 minutes
- No independent security audit conducted
- Breach with diplomatic and legal ramifications
- Impacts U.S. cybersecurity debates ahead of 2028 elections
- FedRAMP reform now inevitable
TeleMessage: A Breach That Exposed Cloud Trust and National Security Risks
TeleMessage, marketed as a secure alternative to Signal, became a vector for national compromise after the Signal Clone Breach, which exposed vulnerabilities in sensitive U.S. government environments—including FEMA and White House staff—without proper vetting. In this analysis, Jacques Gascuel reveals how this proprietary messaging platform, breached in just 20 minutes, shattered assumptions about cloud trust, code sovereignty, and foreign influence. Drawing on investigative sources and Senate reactions, this article dissects the TeleMessage breach timeline, identifies key architectural failures, and offers actionable recommendations for U.S. agencies, NATO allies, and cybersecurity policymakers as they prepare for the 2028 elections and a probable FedRAMP overhaul.
Signal Clone Breach in 20 Minutes: The TeleMessage Vulnerability
TeleMessage, pitched as a secure Signal clone for government communications, The app contained critical vulnerabilities. It A hacker compromised it in under twenty minutes by an independent hacker, exposing sensitive conversations from Trump 2 administration officials. This breach raises serious concerns about digital sovereignty, software trust chains, and foreign access to U.S. government data.
Behind the façade of “secure messaging,” TeleMessage offered only a cryptographic veneer with no operational cybersecurity rigor. In an era where trust in communication tools is vital, this case illustrates how a single technical flaw can turn into a diplomatic nightmare.
Context and History of TeleMessage
TeleMessage, founded in 1999, is an Israeli-based company that markets secure messaging solutions for enterprise use. Although widely used in sectors like healthcare and finance for compliance reasons, the app’s use by U.S. federal agencies, including FEMA and White House staff, raises questions about the vetting process for foreign-made software in high-security environments.
Signal Clone Breach Triggered by Trivial Vulnerability
In March 2024, a hacker known as “nat” discovered that TM SGNL—a custom Signal fork built by TeleMessage—exposed an unprotected endpoint: `/heapdump`. This leaked a full memory dump from the server, including credentials, passwords, and message logs.
Unlike Signal, which stores no communication history, TM SGNL logged everything: messages, metadata, phone numbers. Worse, passwords were hashed in MD5, a cryptographic function long considered broken.
The hacker used only open-source tools and a basic methodology: scanning ports, identifying weak endpoints, and downloading the memory dump. This access, which led to the Signal Clone Breach, could have also allowed malicious code injection.
Immediate Response to the Signal Clone Breach and Actions Taken
In response to the breach, TeleMessage quickly suspended its services for government users, and a Department of Justice investigation was launched. Additionally, some government agencies began reevaluating their use of non-U.S. developed platforms, considering alternatives with more robust security audits and controlled code environments. This incident has accelerated discussions around the adoption of sovereign encryption solutions within government agencies.
Comparison with Other Major Breaches
This breach is reminiscent of previous high-profile incidents such as the Pegasus spyware attack and the SolarWinds hack, where foreign-developed software led to massive exposure of sensitive information. Like these cases, the breach of TeleMessage underscores the vulnerabilities of relying on third-party, foreign-made solutions for secure communications in critical government operations.
Primary Source:
Wired, May 20, 2025: How the Signal Knock-Off App Got Hacked in 20 Minutes
Leaked TeleMessage Data Reveals Scope of the Signal Clone Breach Impact
The breach, a direct result of the Signal Clone Breach, exposed names, phone numbers, and logs of over 60 users, including FEMA personnel, U.S. diplomats, White House staff, and U.S. Secret Service members:
- FEMA personnel
- U.S. diplomats abroad
- White House staff
- U.S. Secret Service members
Logs contained details about high-level travel, diplomatic event coordination, and crisis response communications. Some metadata even exposed GPS locations of senders.
Although Mike Waltz, a senior Trump 2 official, wasn’t listed directly in the compromised logs, his staffers used the app. This breach jeopardized the confidentiality of state-level communications.
Impact on Government Agencies
The breach affected more than 60 users, including FEMA personnel, U.S. diplomats, White House staff, and U.S. Secret Service members. Exposed messages contained details about diplomatic event coordination and high-level travel logistics, further compromising national security communications.
Long-Term Impact on U.S. Security Policies
This breach has long-lasting implications for U.S. cybersecurity policy, especially in the context of government procurement practices. As foreign-made solutions increasingly enter high-security environments, the call for **greater scrutiny** and **mandatory independent audits** will become louder. This incident could lead to sweeping reforms that demand **full code transparency** for all communication platforms used by the government.
Long-Term Solutions for Securing Government Communications Post Signal Clone Breach
While the breach exposed critical vulnerabilities in TeleMessage, it also emphasizes the need for sovereign encryption solutions that assume breach resilience by design. Platforms like DataShielder offer offline encryption and segmented key architecture, ensuring that even in the event of a server or app breach, data remains cryptographically protected and inaccessible to unauthorized parties.
Authorities’ Response: CISA and CVE Inclusion
The Cybersecurity and Infrastructure Security Agency (CISA) has added TeleMessage’s vulnerability, discovered during the Signal Clone Breach, to its list of Known Exploited Vulnerabilities (KEV), under CVE-2025-47729. This inclusion mandates that federal agencies take corrective actions within three weeks, underscoring the urgency of addressing the breach and securing communications platforms used by government officials.
Call to Action: Strengthening Cybersecurity Measures
As the 2028 U.S. elections approach, it’s crucial that digital sovereignty becomes a central part of national security policies. The breach of TeleMessage serves as a stark reminder that reliance on foreign-made, unaudited platforms jeopardizes the security of government communications. It is time for policymakers to take decisive action and prioritize secure, sovereign encryption solutions to safeguard the future of national security.
Signal Clone Breached: A Deep Dive into the Data Exfiltration and the Attackers Behind the Incident
The breach of TeleMessage revealed alarming details about the extent of the data exfiltrated and the attacker responsible. Here’s a closer look at what was stolen and who was behind the attack:
Types and Volume of Data Exfiltrated
The hacker was able to extract a vast amount of sensitive data from TeleMessage, compromising not only personal information but also highly confidential government communications:
- User Personal Information: Over 60 individuals’ names, phone numbers, and other personal identifiers were exposed, including senior U.S. officials and diplomats.
- Communication Logs: Sensitive logs containing high-level communications about diplomatic events, travel coordination, and crisis response were compromised.
- Metadata: Metadata revealed GPS locations of senders, potentially endangering individuals’ safety and security.
- Credentials and Passwords: The breach exposed passwords stored in MD5 hashes, a cryptographic function known to be vulnerable to attacks.
Who Was Behind the Attack?
The hacker known as “nat” is believed to be the one behind the breach. Using basic open-source tools, nat discovered a critical vulnerability in TeleMessage’s system. The vulnerability was an unprotected endpoint, , which allowed access to the server’s full memory dump. This dump included sensitive data, such as passwords, message logs, and credentials./heapdump
With a simple scanning technique, nat was able to download the full memory dump, bypassing the security measures in place. This attack underscores the need for robust penetration testing, regular audits, and a more resilient approach to securing sensitive communications in government environments.
Consequences of the Data Exfiltration
The exposure of this data has had significant national security implications. Government personnel, including those at FEMA, the U.S. Department of State, and even the White House, were affected. The breach jeopardized not only their personal data but also the confidentiality of state-level communications.
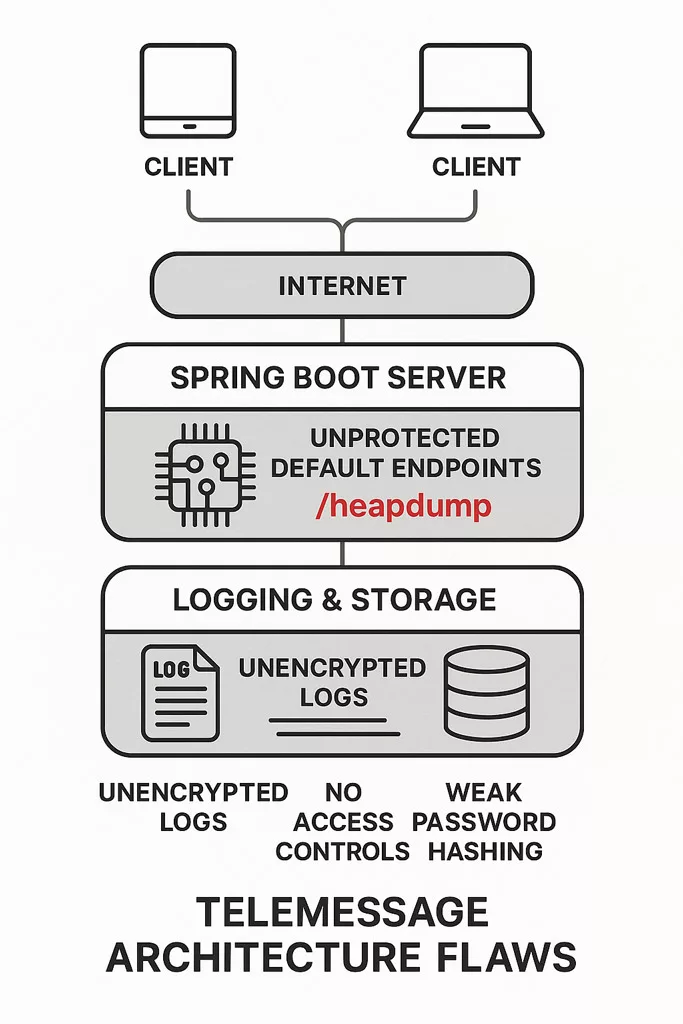
Flawed Architecture Behind the Signal Clone Breach
TeleMessage’s system relied on:
- A Spring Boot server with unprotected default endpoints
- Logs sent in plaintext
- No segmentation or access control for sensitive services
- Poor JWT token management (predictable and insecure)
On the day of the attack, TeleMessage TeleMessage continued to use expired TLS certificates for some subdomains, undermining even HTTPS trust.
The lack of auditing, pentesting, or security reviews was evident. The incident reveals a platform more focused on marketing than technical resilience.
How DataShielder Prevents Damage from a Signal Clone Breach
A Sovereign Encryption Strategy That Assumes Breach — and Renders It Harmless
By contrast, in the context of the Signal clone breached scandal, even the most catastrophic server-level vulnerabilities — such as the exposed endpoint in TeleMessage — would have had zero impact on message confidentiality if users had encrypted their communications using a sovereign encrypted messaging solution using segmented AES-256 CBC like DataShielder NFC HSM or DataShielder HSM PGP./heapdump
With DataShielder NFC HSM, users encrypt messages and files directly on their NFC-enabled Android phones using segmented AES-256 CBC keys stored in a contactless hardware security module (HSM). Messages sent via any messaging app — including Signal, TeleMessage, LinkedIn, or email — remain encrypted end-to-end and are decrypted only locally and temporarily in volatile memory. No server, device, or cloud infrastructure ever handles unencrypted data.
Meanwhile, DataShielder HSM PGP offers equivalent protection on desktop environments. Operating on Windows and macOS, it enables users to encrypt and decrypt messages and files in one click using AES-256 CBC PGP based on a segmented key pair. Even if an attacker exfiltrated logs or memory snapshots — as occurred with TeleMessage — the content would remain cryptographically inaccessible.
Ultimately, if FEMA staffers, diplomats, or White House personnel had used these offline sovereign encryption tools, the fallout would have been limited to unreadable encrypted blobs. No plaintext messages, credentials, or attachments would have been accessible — regardless of how deep the server compromise went.
✅ Key Benefits of Using DataShielder NFC HSM and HSM PGP:
- AES-256 CBC encryption with segmented key architecture
- Fully offline operation — no servers, no cloud, no identifiers
- One-click encryption/decryption on phone or PC
- Compatible with any messaging system, even those already compromised
- Designed for GDPR, national sovereignty, and defense-grade use cases
👉 Discover how DataShielder protects against any future breach — even those like TeleMessage
Ultimately, the Signal clone breached narrative exposes the need for encryption strategies that assume breach — and neutralize it by design. DataShielder offers precisely that kind of sovereign-by-default resilience.
🔍 Secure Messaging Comparison: Signal vs TeleMessage vs DataShielder
| Feature | Signal | TeleMessage | DataShielder NFC HSM / HSM PGP |
|---|---|---|---|
| AES-256 CBC Encryption (Segmented or Not) | ❌ (uses Curve25519 / X3DH + Double Ratchet) |
❌ (used MD5 and logged messages) |
✅ (AES-256 CBC with segmented keys) |
| Segmented Key Architecture | ❌ | ❌ | ✅ (with RSA 4096 or PGP sharing) |
| Offline Encryption (No server/cloud) | ❌ | ❌ | ✅ |
| Private Keys Stored in Terminal | ✅ | ✅ (and exposed in heap dumps) |
❌ (never stored, only in volatile memory) |
| Survives Server or App Breaches | ⚠️ (depends on OS/hardware) |
❌ | ✅ (designed for breach resilience) |
| Compatible with Any Messaging App | ❌ (limited to Signal protocol) |
❌ | ✅ (works with email, LinkedIn, SMS, RCS, etc.) |
| Open Source / Auditable | ✅ | ❌ | ✅ (uses patented & auditable architecture) |
This side-by-side comparison shows why DataShielder offers unmatched security and operational independence—even in catastrophic breach scenarios like the Signal clone breached incident. Its patented segmented key system, end-to-end AES-256 CBC encryption, and absence of local key storage form a resilient framework that neutralizes even advanced threats.
The segmented key system implemented in all DataShielder solutions is protected by an international patent, including United States patent registration.
This unique approach ensures non-residency of private keys, offline protection, and trust-chain fragmentation — rendering even deep breaches ineffective.
Political Fallout of the Signal Clone Breach: Senate Response
In response to the breach, Senator Ron Wyden immediately called for a Department of Justice investigation. He argued that the app’s use by federal agencies potentially constitutes a violation of the False Claims Act.
Moreover, Wyden raised a serious national security concern by questioning whether the Israeli government could have accessed the compromised data, given that TeleMessage is based in Israel. If proven true, such a breach could escalate into a full-fledged diplomatic crisis.
Crucially, Wyden emphasized a fundamental failure: no U.S. authority ever formally validated the app’s security before its deployment to federal agents—a lapse that may have opened the door to foreign intrusion and legal consequences.
Legal Note: Experts say retaining logs of high-level official communications could violate the Presidential Records Act, and even the Espionage Act, if classified material was exposed.
Source: Washington Post, May 6, 2025: Senator calls for investigation
Closed Messaging Isn’t Secure Messaging
Unlike Signal, whose codebase is open and auditable, TM SGNL TeleMessage created a proprietary fork that lacked transparency. Archiving messages eliminated Signal’s core benefit: ephemeral communication.
Experts stress that a secure messaging app must be publicly verifiable. Closed and unreviewed implementations create critical blind spots in the trust chain.
Political Reactions: Senator Ron Wyden’s Call for Investigation
Senator Ron Wyden called for a Department of Justice investigation, raising serious concerns about national security and potential violations of the False Claims Act. Wyden emphasized the need for transparency and accountability regarding the use of foreign-made communication tools in U.S. government operations.
Black Box Encryption in Signal Clone Breaches: A Dangerous Illusion
An app can claim end-to-end encryption and still be utterly vulnerable if it logs messages, exposes traffic, or retains keys. Encryption is only one link in a broader security chain involving architecture and implementation.
This mirrors the lessons of the Pegasus spyware case: secret code is often the enemy of real security.
Geostrategic Fallout from the Signal Clone Breach: A Wake-Up Call
Far beyond a mere technical failure, this breach represents a critical chapter in a broader influence war—one where the ability to intercept or manipulate state communications serves as a strategic advantage. Consequently, adversarial nations such as Russia, China, or Iran may weaponize the TeleMessage affair to highlight and exploit American dependency on foreign-developed technologies.
Furthermore, in a post-Snowden world shaped by heightened surveillance awareness, this case underscores a troubling paradox: a national security strategy that continues to rely on unverified, foreign-controlled vendors to handle sensitive communications. As a result, digital sovereignty emerges not just as a policy option—but as a strategic imperative.
Lessons for NATO and the EU
European and NATO states must learn from this:
- Favor open-source, vetted messaging tools with mandatory audits
- Ban apps where code and data flows aren’t 100% controlled
- Develop sovereign messaging standards via ENISA, ANSSI, or the BSI
This also calls for investing in decentralized, offline encryption platforms—without cloud reliance or commercial capture—like NFC HSM or PGP HSM technologies.
Impact on Government Communication Practices
This breach highlights the risks of using unverified messaging apps for sensitive government communications. It underscores the importance of strengthening security protocols and compliance in the tools used by government agencies to ensure that national security is not compromised by foreign-made, unaudited platforms.
Signal Clone Breach Fallout: Implications for 2028 Elections and FedRAMP Reform
As the 2028 presidential race rapidly approaches, this scandal is poised to profoundly influence the national conversation around cybersecurity. In particular, candidates will face urgent questions: How will they protect U.S. government communications from future breaches?
Simultaneously, FedRAMP (Federal Risk and Authorization Management Program) reform appears imminent. Given recent failures, traditional cloud certifications will no longer suffice. Instead, the next generation of federal security baselines will need to ensure:
- Verified backend sovereignty
- Independent third-party auditability
- Full Zero Trust compliance
In light of these developments, this incident could fast-track federal adoption of open-source, sovereign solutions hosted within tightly controlled environments.
Who Develops TeleMessage?
TeleMessage is developed by TeleMessage Ltd., an Israeli-based software company headquartered in Petah Tikva, Israel. Founded in 1999, the company specializes in enterprise mobile messaging and secure communication solutions. Its core business includes SMS gateways, mobile archiving, and secure messaging services.
Despite offering features tailored to compliance-heavy sectors like healthcare and finance, TeleMessage is not an American company and operates under Israeli jurisdiction. This legal and operational reality introduces potential security and sovereignty concerns when its services are deployed by foreign governments.
Why Is a Foreign-Made Messaging App Used in U.S. Government Agencies?
The fact that a foreign-developed proprietary messaging platform was adopted in sensitive parts of the U.S. government is surprising—and concerning. Several critical risks emerge:
- Sovereignty Risk: U.S. agencies cannot fully verify, audit, or control TeleMessage’s software or data-handling practices.
- Legal Exposure: As an Israeli entity, TeleMessage could be subject to local laws and intelligence cooperation requirements, including secret court orders.
- Backdoor Possibilities: Without full code transparency or U.S.-based auditing, the platform may contain vulnerabilities—intentional or not—that compromise national communications.
🛑 Bottom line: No matter the claims of encryption, a messaging tool built and controlled abroad inherently places U.S. national security at risk—especially if deployed in White House staff or federal emergency agencies.
Strategic Misstep: TeleMessage and the Sovereignty Paradox
This case illustrates a paradox in modern cybersecurity: a nation with vast technical capacity outsources secure messaging to foreign-made, unaudited platforms. This paradox becomes especially dangerous when used in political, diplomatic, or military contexts.
- Trust Chains Broken: Without control over source code and hosting infrastructure, U.S. officials place blind trust in a black-box system.
- Supply Chain Vulnerability: Foreign-controlled tech stacks are harder to verify, patch, and secure against insider or state-level threats.
- Diplomatic Fallout: If foreign governments accessed U.S. data via TeleMessage, the breach could escalate into a full diplomatic crisis.
Lessons Learned
- Adopt only auditable, sovereign solutions for national security messaging.
- Enforce Zero Trust by default, assuming breach potential even in “secure” tools.
- Mandate domestic code ownership, cryptographic control, and infrastructure localization for all federal communication systems.
Final Word
The Signal clone breach is not just a cautionary tale of poor technical design—it’s a wake-up call about digital sovereignty. Governments must control the full lifecycle of sensitive communication platforms—from source code to cryptographic keys.
DataShielder, by contrast, embodies this sovereignty-by-design approach with offline, segmented key encryption and patented trust-chain fragmentation. It’s not just a messaging enhancement—it’s an insurance policy against the next breach.
Exclusive Infographic: TeleMessage Breach Timeline
- 2023 — TM SGNL launched by TeleMessage, marketed as a secure alternative to Signal for government use.
- January 2024 — Deployed across FEMA, diplomatic missions, and White House staff without formal cybersecurity audit.
- March 20, 2024 — Independent hacker “nat” discovers an open endpoint leaking full memory contents.
/heapdump - March 22, 2024 — Full dump including messages, credentials, and phone logs is extracted using public tools.
- April 1, 2024 — Leaked data shared anonymously in private cybercrime forums and OSINT channels.
- May 2, 2025 — First major media coverage by CyberScoop and WIRED reveals breach to the public.
- May 6, 2025 — Senator Ron Wyden demands DOJ investigation, citing espionage and FedRAMP violations.
- May 21, 2025 — Reuters confirms breach included classified communications of senior U.S. officials.
This visual timeline highlights the rapid descent from unchecked deployment to full-scale data compromise—with unresolved strategic consequences.
Final Thoughts: A Hard Lesson in Cyber Sovereignty
This case clearly illustrates the dangers of poor implementation in critical tools. Unlike robust platforms like Signal, which is designed to leave no trace, TM SGNL demonstrated the exact opposite behavior, logging sensitive data and exposing communications. Consequently, this breach underscores the urgent need to rely on secure, sovereign, and auditable platforms—not commercial black boxes driven by opacity.
Beyond the technical flaws, this incident also raises a fundamental question: Who really controls the technology securing a nation’s most sensitive data? In an era of escalating digital threats, especially in today’s volatile geopolitical climate, digital sovereignty isn’t optional—it’s an essential pillar of national strategy. The Signal clone breached in this case now serves as a cautionary tale for any government outsourcing secure communications to opaque or foreign-built platforms.
Official Sources:
- Reuters, May 21, 2025: Hacker stole data across US
- CyberScoop, May 20, 2025: TeleMessage suspends services
- Wired, 2025: TM SGNL code analysis and breach timeline
Latest Updates on the TeleMessage Breach
Recent reports confirm the data leak, with Reuters revealing more details about the exposed data. DDoSecrets has published a 410 GB dataset containing messages and metadata from the breach, further fueling the controversy surrounding TeleMessage’s security flaws. TeleMessage has since suspended its services and removed references to the app from its website, signaling the severity of the breach.





















































Pingback: Reputation Cyberattacks in Hybrid Conflicts — Anatomy of an Invisible Cyberwar - Freemindtronic