Understanding Targeted Attacks of APT36 SpearPhishing India APT36 cyberespionage campaigns against India represent a focused and enduring threat. Actors likely linked to Pakistan orchestrate these attacks. This group, also known as Transparent Unit, ProjectM, Mythic Leopard, and Earth Karkaddan, has been active since at least 2013. Throughout its operations, APT36 has consistently targeted Indian government […]
Search Results for: PassCypher
APT29 SpearPhishing Europe: A Stealthy LongTerm Threat APT29 spearphishing Europe campaigns highlight a persistent and highly sophisticated cyberespionage threat orchestrated by Russia’s Foreign Intelligence Service (SVR), known as Cozy Bear. Active since at least 2008, APT29 has become synonymous with stealthy operations targeting European institutions through phishing emails, Microsoft 365 abuse, supply chain compromises, and […]
Russian cyberattack on Microsoft by Midnight Blizzard (APT29) highlights the strategic risks to digital sovereignty. Discover how the group exploited password spraying, malicious OAuth applications, and legacy exposure — and the sovereign countermeasures offered by DataShielder and PassCypher. Sovereign Use Case — Outlook backdoor neutralized Context. A regional authority receives a themed spear-phish. A VBA […]
Password Statistics 2025: Global Trends in Usage and Security Challenges The growing reliance on digital services has made passwords an essential component of online security. Every day, billions of users interact with various platforms and applications requiring authentication, creating a heavy dependency on passwords. This study aims to explore the scope of this phenomenon by […]
BadPilot Cyber Attacks: Sandworm’s New Weaponized Subgroup Understanding the rise of BadPilot and its impact on global cybersecurity. BadPilot, a newly identified subgroup of Russia’s infamous Sandworm unit (APT44), is expanding its cyber-espionage operations, targeting critical infrastructures worldwide. The group’s advanced tactics go beyond typical cyber-espionage, focusing on long-term infiltration and the potential to disrupt […]
Browser Fingerprinting Tracking today represents one of the true cores of metadata intelligence. Far beyond the content of communications, it is the behavioral correlations — relationships, timelines, locations, regularities — that structure modern digital surveillance, whether civil or state-driven, economic or advertising. Exploited by digital platforms, AdTech, intelligence services, and cybercrime, this logic enables anticipation, […]
The Context of the French IT Liability Case The Rennes French Court of Appeal examined case RG n° 23/04627 involving S.A.S. [L] INDUSTRIE, a manufacturing company, and its IT provider, S.A.S. MISMO. Following a ransomware attack in 2020 that paralyzed [L] INDUSTRIE’s operations, the company alleged that MISMO had failed in its contractual obligations to […]
Microsoft: 159 Vulnerabilities Fixed in 2025 Microsoft has released a record-breaking security update in January 2025, addressing 159 vulnerabilities, including 8 actively exploited zero-days. These critical flaws affect major products such as Windows, Office, and Hyper-V, exposing systems to remote code execution, privilege escalation, and denial-of-service attacks. This update underscores the growing complexity of cyber […]
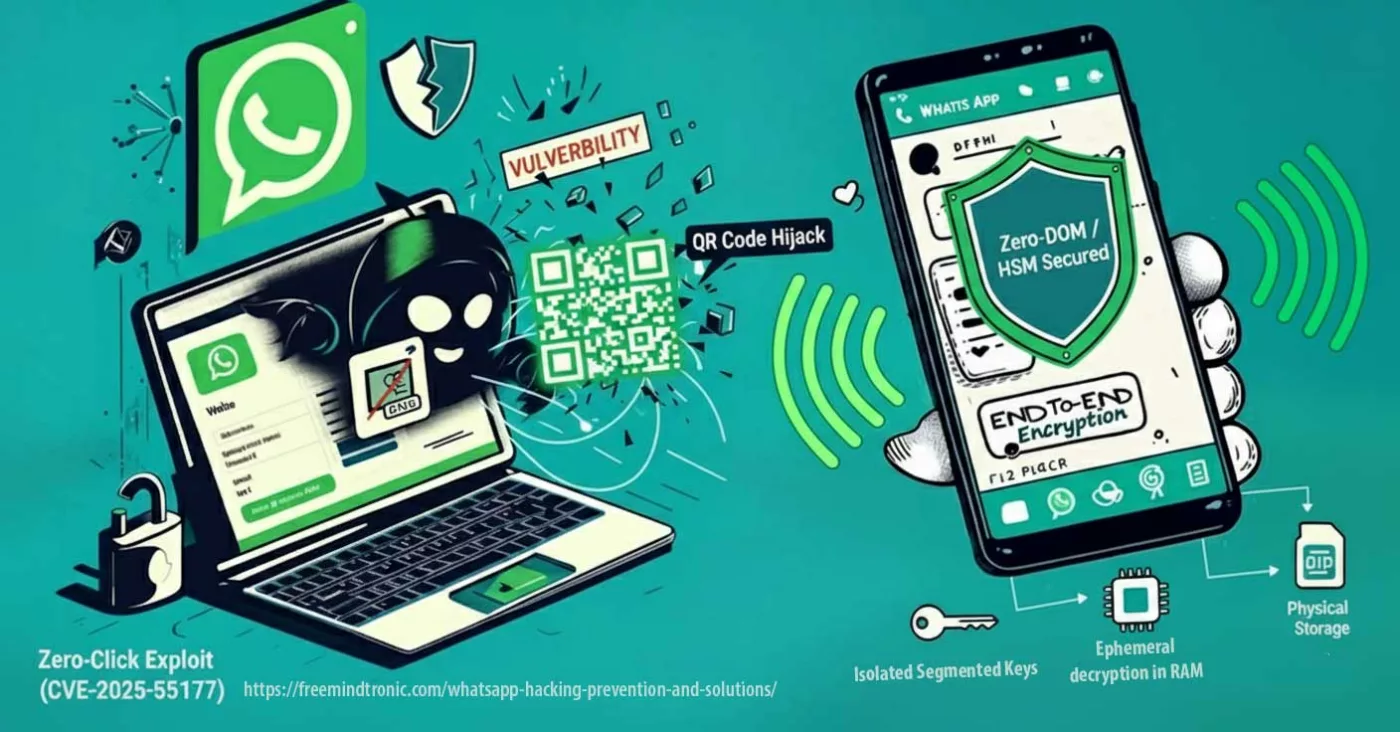
WhatsApp hacking zero-click exploit (CVE-2025-55177) chained with Apple CVE-2025-43300 enables remote code execution via crafted DNG images by abusing linked-device sync and automatic media processing — update WhatsApp and your OS now. ☰ Quick Navigator Quick summary Emergency — zero-click CVE-2025-55177 The Risks of WhatsApp Hacking Techniques used by attackers Legitimate tools & misuse Freemindtronic […]