2025, Digital Security
Atomic Stealer AMOS: The Mac Malware That Redefined Cyber Infiltration
Atomic Stealer AMOS: Redefining Mac Cyber Threats Featured in Freemindtronic’s Digital Security section, this analysis by Jacques Gascuel explores one of the most sophisticated and resilient macOS malware strains to date. Atomic Stealer Amos merges cybercriminal tactics with espionage-grade operations, forming a hybrid threat that challenges traditional defenses. Gascuel dissects its architecture and presents actionable strategies to protect national systems and corporate infrastructures in an increasingly volatile digital landscape.
Explore More in Digital Security
Stay ahead of advanced cyber threats with in-depth articles from Freemindtronic’s Digital Security section. From zero-day exploits to hardware-based countermeasures, discover expert insights and field-tested strategies to protect your data, systems, and infrastructure.
Executive Summary
Atomic Stealer (AMOS) redefined how macOS threats operate. Silent, precise, and persistent, it bypassed traditional Apple defenses and exploited routine user behavior to exfiltrate critical data. This article offers a strategic analysis of AMOS’s evolution, infection techniques, threat infrastructure, and its geopolitical and organizational impact. It also provides concrete defense recommendations, real-world case examples, and a cultural reassessment of how we approach Apple endpoint security.
Atomic Stealer AMOS: The Mac Malware That Redefined Cyber Infiltration
Last Updated: 08 july 2025
Version: 1.0
Source: Freemindtronic Andorra
Atomic Stealer – Navigation Guide
- Macs Were Safe. Until They Weren’t.
- Updated Threat Capabilities July 2025
- A Threat Engineered for Human Habits
- Adaptation as a Service
- Two Clicks Away from a Breach
- Institutional Blind Spots
- Detecting the Undetectable
- Malware-as-a-Service, Industrial Grade
- Strategic Exposure: Who’s at Risk
- What Defenders Fear Next
- Threat Actor Attribution: Who’s Really Behind AMOS?
- Indicators of Compromise (IOCs)
- Defenders’ Playbook: Active Protection
- Freemindtronic Solutions to Secure macOS
- What About Passkeys and Private Keys?
- DataShielder: Hardware Immunity Against macOS Infostealers
- PassCypher Protection Against AMOS
- Atomic Stealer Amos and the Future of macOS Security Culture
- Verified Sources
Macs Were Safe. Until They Weren’t.
For more than a decade, macOS held a reputation as a bastion of digital safety. Many believed its architecture inherently protected users from the kind of sophisticated malware seen on Windows. This belief was widespread, deeply rooted—and dangerously wrong.
In April 2023, that myth cracked open.
Security researchers from Malwarebytes and Moonlock spotted a new macOS malware circulating on Telegram. It wasn’t loud. It wasn’t chaotic. It didn’t encrypt files or display ransom notes. Instead, it crept in silently, exfiltrating passwords, session tokens, and cryptocurrency wallets before anyone noticed. They called it Atomic Stealer AMOS for short.
It doesn’t log keystrokes. It doesn’t need to. AMOS exploits macOS-native trust zones like Keychain and iCloud Keychain. Only air-gapped hybrid HSM solutions — like NFC HSM and PGP HSM — fully isolate your secrets from such attacks.

✪ Illustration showing Apple’s ecosystem under scrutiny, symbolizing the covert infiltration methods used by Atomic Stealer AMOS.
By mid-2025, Atomic had breached targets in over 120 countries. It wasn’t a side-story in the malware landscape anymore—it had become a central threat vector, especially for those who had mistakenly assumed their Macs were beyond reach.
In April 2023, that myth cracked open…
They called it Atomic Stealer AMOS for short.
It doesn’t encrypt or disrupt. It quietly exfiltrates credentials, tokens, and crypto wallets—without triggering alerts.
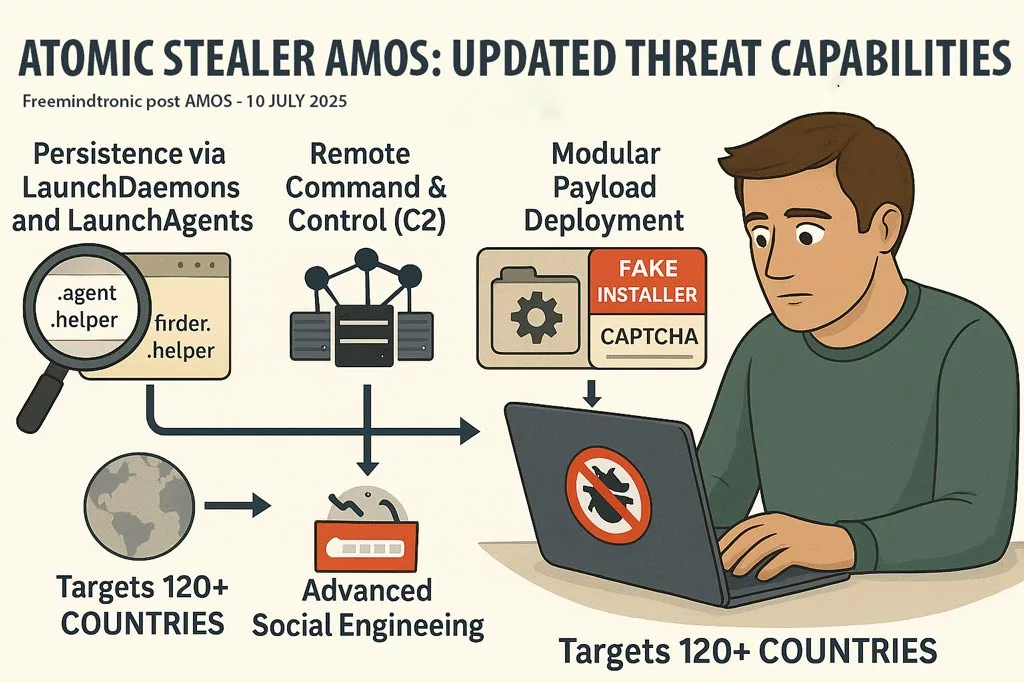
Updated Threat Capabilities July 2025
Since its initial discovery, Atomic Stealer AMOS has evolved dramatically, with a much more aggressive and stealthy feature set now observed in the wild.
- Persistence via macOS LaunchDaemons and LaunchAgents
AMOS now installs hidden.agentand.helperfiles, such ascom.finder.helper.plist, to maintain persistence even after reboot. - Remote Command & Control (C2)
AMOS communicates silently with attacker servers, enabling remote command execution and lateral network movement. - Modular Payload Deployment
Attackers can now inject new components post-infection, adapting the malware’s behavior in real time. - Advanced Social Engineering
Distributed via fake installers, trojanized Homebrew packages, and spoofed CAPTCHA prompts. Even digitally signed apps can be weaponized. - Global Spread
Targets across 120+ countries including the United States, France, Italy, UK, and Canada. Attribution links it to a MaaS operation known as “Poseidon.”
Recommended Defense Enhancements
To defend against this rapidly evolving macOS threat, experts recommend:
- Monitoring for unauthorized
.plistfiles and LaunchAgents - Blocking unexpected outbound traffic to unknown C2 servers
- Avoiding installation of apps from non-official sources—even if signed
- Strengthening your Zero Trust posture with air-gapped tools like SeedNFC HSM and Bluetooth Keyboard Emulator to eliminate clipboard, keychain, and RAM-based exfiltration vectors
Risk Scoring Update for Atomic Stealer AMOS
| Capability | Previous Score | July 2025 Score |
|---|---|---|
| Stealth & Evasion | 8/10 | 9/10 |
| Credential & Crypto Theft | 9/10 | 10/10 |
| Persistent Backdoor | 0/10 | 10/10 |
| Remote Access / C2 | 2/10 | 10/10 |
| Global Reach & Target Scope | 9/10 | 9/10 |
| Overall Threat Level | 7.6 / 10 | 9.6 / 10 |
✪ Illustration showing Atomic Stealer AMOS breaching Apple’s ecosystem, using stealthy exfiltration methods across macOS environments.
New Backdoor: Persistent and Programmable
In early July 2025, Moonlock – MacPaw’s cybersecurity arm – confirmed a significant upgrade: AMOS now installs a hidden backdoor (via .helper/.agent + LaunchDaemon), which survives reboots and enables remote command execution or additional payload delivery — elevating its threat level dramatically
A Threat Engineered for Human Habits
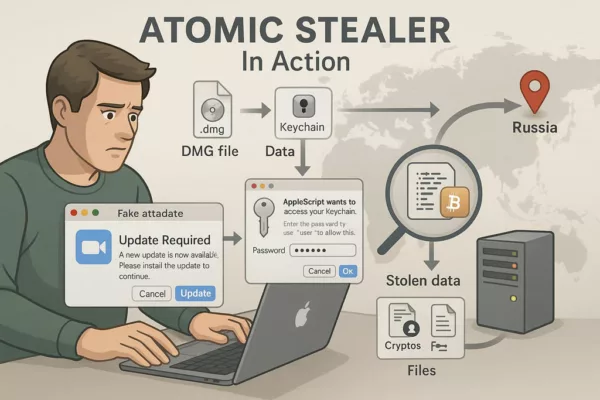
Atomic Stealer AMOS didn’t rely on zero-days or brute force. It exploited something far more predictable: human behavior.
Freelancers seeking cracked design plugins. Employees clicking “update” on fake Zoom prompts. Developers installing browser extensions without scrutiny. These seemingly minor actions triggered full system compromise.
Once deployed, AMOS used AppleScript prompts to request credentials and XOR-encrypted payloads to evade detection. It embedded itself via LaunchAgents and LaunchDaemons, securing persistence across reboots.
✪ A visual breakdown of Atomic Stealer’s infection method on macOS, from fake update to credential theft and data exfiltration.
Its targets were no less subtle:
- Passwords saved in Chrome, Safari, Brave
- Data from over 50 crypto wallets (Ledger, Coinomi, Exodus…)
- Clipboard content—often cryptocurrency transactions
- Browser session tokens, including cloud accounts
SpyCloud Labs – Reverse Engineering AMOS
Atomic didn’t crash systems or encrypt drives. It simply harvested. Quietly. Efficiently. Fatally.
Adaptation as a Service
What makes AMOS so dangerous isn’t just its code—it’s the mindset behind it. This is malware designed to evolve, sold as a service, maintained like a product.
| Date | Evolution Milestone |
|---|---|
| Apr 2023 | First sightings in Telegram forums |
| Sep 2023 | ClearFake phishing campaigns weaponize delivery |
| Dec 2023 | Encrypted payloads bypass antivirus detection |
| Jan 2024 | Fake Google Ads launch massive malvertising wave |
| Jul 2025 | Persistent remote backdoor integrated |

✪ This infographic charts the infection stages of Atomic Stealer AMOS, highlighting key milestones from its emergence via cracked macOS apps to sophisticated phishing and remote access techniques.
Picus Security – MITRE ATT&CK mapping
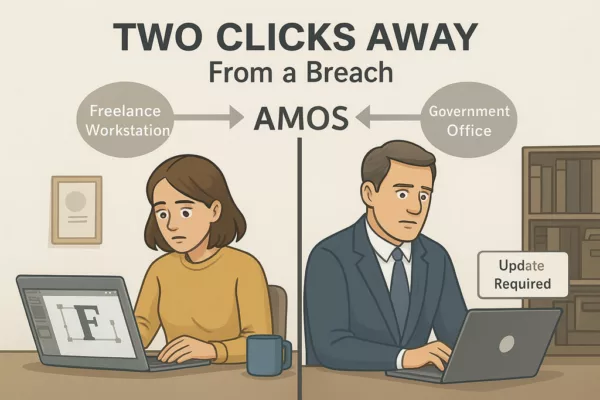
Two Clicks Away from a Breach
To understand AMOS, you don’t need to reverse-engineer its binaries. You just need to watch how people behave.
In a real-world example, a freelance designer downloaded a cracked font plugin to meet a deadline. Within hours, AMOS drained her wallet, accessed her saved credentials, and uploaded client documents to a remote server.
In a separate case, a government office reported unusual login activity. Investigators found a spoofed Slack update triggered the breach. It wasn’t Slack. It was AMOS.
✪ Illustration depicting the dual nature of Atomic Stealer (AMOS) attacks: a freelancer installing a cracked plugin and a government employee clicking a fake Slack update, both leading to data theft and wallet drain.
Institutional Blind Spots
In 2024, Red Canary flagged Atomic Stealer among the top 10 macOS threats five times. A year later, it had infected over 2,800 websites, distributing its payload via fake CAPTCHA overlays—undetectable by most antivirus suites.
Cybersecurity News – 2,800+ infected websites
AMOS breached:
- Judicial systems (document leaks)
- Defense ministries (backdoor surveillance)
- Health agencies (citizen data exfiltration)
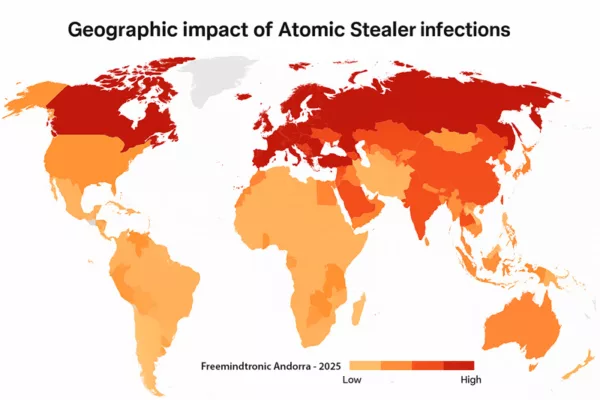
✪ A choropleth heatmap visualizing the global spread of Atomic Stealer AMOS malware, highlighting red zones of high infection (USA, Europe, Russia) and a legend indicating severity levels.
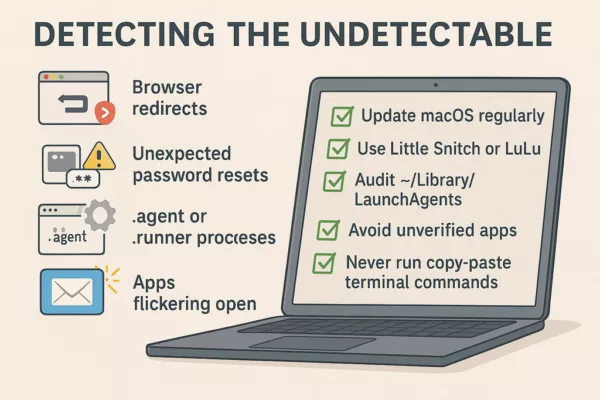
Detecting the Undetectable
AMOS leaves subtle traces:
- Browser redirects
- Unexpected password resets
- .agent or .runner processes
- Apps flickering open
To mitigate:
- Update macOS regularly
- Use Little Snitch or LuLu
- Audit ~/Library/LaunchAgents
- Avoid unverified apps
- Never run copy-paste terminal commands
✪ This infographic checklist outlines 5 key reflexes to detect and neutralize Atomic Stealer (AMOS) infections on macOS systems.
Threat Actor Profile: Who’s Behind AMOS?
While AMOS has not been officially attributed to a specific APT group, indicators suggest it was developed by Russian-speaking actors, based on:
- Forum discussions on Russian-language Telegram groups
- Code strings and comments in Cyrillic
- Infrastructure overlaps with known Eastern European malware groups
These threat actors are not simply financially motivated. The precision, modularity, and persistence of AMOS suggests potential use in state-adjacent cyber operations or intelligence-linked campaigns.
Its evolution also parallels other known cybercrime ecosystems operating in Russia and Belarus, often protected by a “hands-off” doctrine as long as they avoid targeting domestic networks.
Malware-as-a-Service: Industrial Grade
- Custom builds with payload encryption
- Support and distribution via Telegram
- Spread via ClickFix and malvertising
- Blockchain-based hosting using EtherHiding
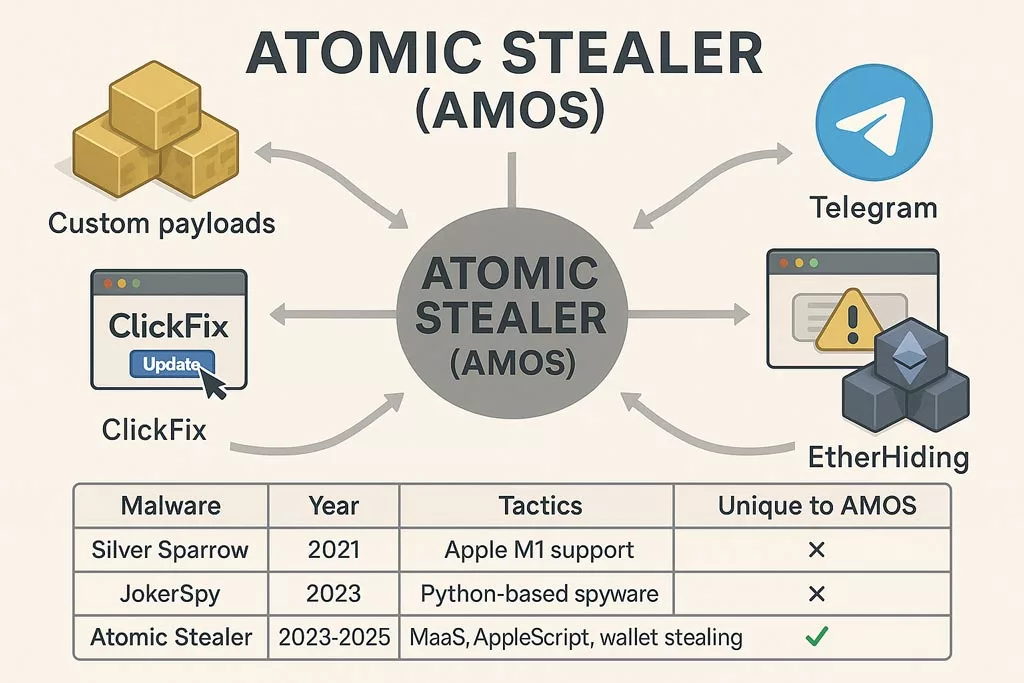
✪ Écosystème MaaS d’Atomic Stealer comparé à Silver Sparrow et JokerSpy, illustrant ses tactiques uniques : chiffrement XOR, exfiltration crypto, AppleScript et diffusion via Telegram.
| Malware Name | Year | Tactics | Unique to AMOS |
|---|---|---|---|
| Silver Sparrow | 2021 | Early Apple M1 compatibility | ✗ |
| JokerSpy | 2023 | Spyware in Python, used C2 servers | ✗ |
| Atomic Stealer | 2023–2025 | MaaS, XOR encryption, AppleScript, wallet exfiltration | ✅ |
AMOS combines multiple threat vectors—social engineering, native scripting abuse, and crypto-focused data harvesting—previously scattered across different strains.
Strategic Exposure: Who’s at Risk
| Group | Severity | Vector |
|---|---|---|
| Casual Users | High | Browser extensions |
| Crypto Traders | Critical | Clipboard/wallet interception |
| Startups | Severe | Slack/Teams compromise |
| Governments | Extreme | Persistent surveillance backdoors |
What Defenders Fear Next
The evolution isn’t over. AMOS may soon integrate:
- Biometric spoofing (macOS Touch ID)
- Lateral movement in creative agencies
- Steganography-based payloads in image files
Security must not follow. It must anticipate.
Strategic Outlook Atomic Stealer AMOS
- GDPR breaches from exfiltrated citizen data (health, justice)
- Legal risks for companies not securing macOS endpoints
- Cross-border incident response complexities due to MaaS
- Urgent need to update risk models to treat Apple devices as critical infrastructure
Threat Actor Attribution: Who’s Really Behind AMOS?
While Atomic Stealer (AMOS) has not been officially attributed to any known APT group, its evolution and operational model suggest the involvement of a Russian-speaking cybercriminal network, possibly APT-adjacent.
The malware’s early presence on Russian-language Telegram groups, combined with:
- Infrastructure linked to Eastern Europe,
- XOR obfuscation and macOS persistence techniques,
- and a sophisticated Malware-as-a-Service support network
…indicate a semi-professionalized developer team with deep technical access.
Whether this actor operates independently or under informal “state-blind tolerance” remains unclear. But the outcome is strategic: AMOS creates viable access for both criminal monetization and state-aligned espionage.
Related reading: APT28’s Campaign in Europe
Indicators of Compromise (IOCs)
Here are notable Indicators of Compromise for Atomic Stealer AMOS:
File Hashes
- fa34b1e87d9bb2f244c349e69f6211f3 – Encrypted loader sample (SHA256)
- 9d52a194e39de66b80ff77f0f8e3fbc4 – macOS .dmg payload (SHA1)
Process Names / Artifacts
- .atomic_agent or .launch_daemon
- /Library/LaunchAgents/com.apple.atomic.*
- /private/tmp/atomic/tmp.log
C2 IPs / Domains (as of Q2 2025)
- 185.112.156.87
- atomicsec[.]ru
- zoom-securecdn[.]net
Behavioral
- Prompt for keychain credentials using AppleScript
- Sudden redirection to fake update screens
- Unusual clipboard content activity (crypto strings)
These IOCs are dynamic. Correlate with updated threat intel feeds.
Defenders’ Playbook: Active Protection
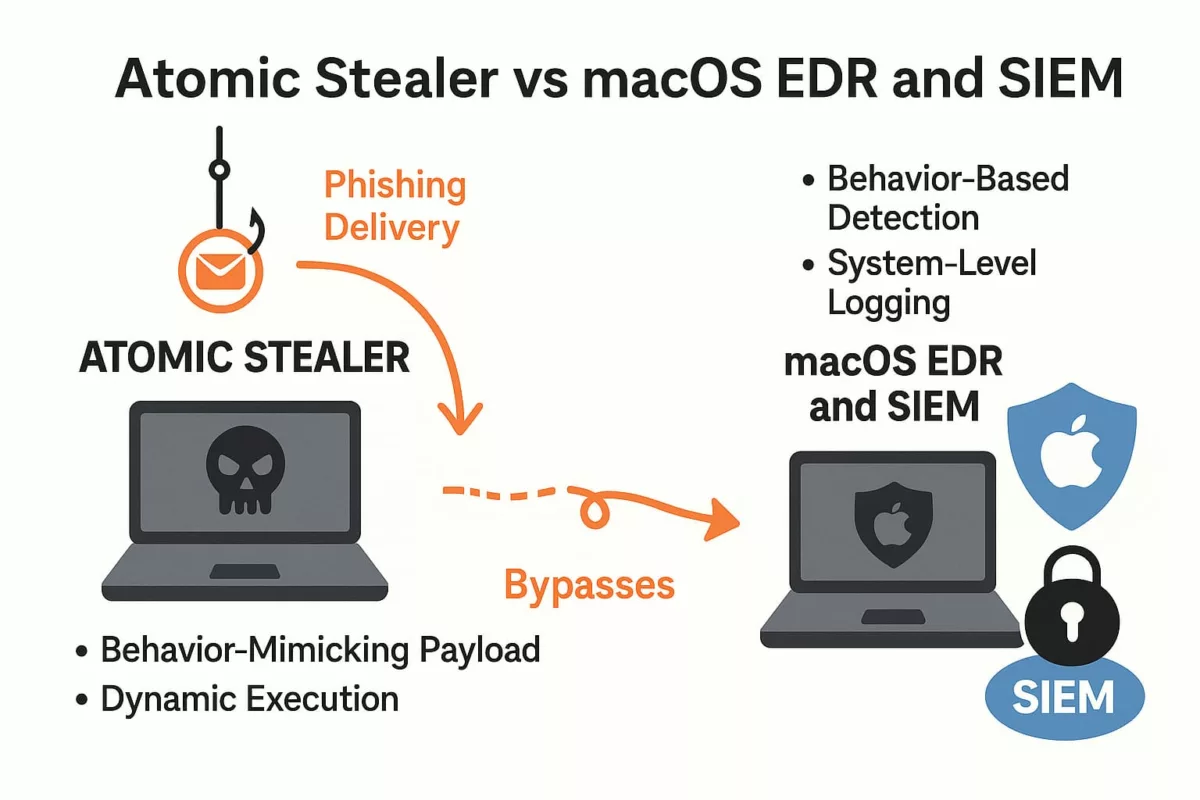
✪ Security teams can proactively counter AMOS using a layered defense model:
SIEM Integration (Ex: Splunk, ELK)
- Monitor execution of osascript and creation of LaunchAgents
- Detect access to ~/Library/Application Support with unknown binaries
- Alert on anomalous clipboard behavior or browser token access
EDR Rules (Ex: CrowdStrike, SentinelOne)
- Block unsigned binaries requesting keychain access
- Alert on XOR-obfuscated payloads in user directories
- Kill child processes of fake Zoom or Slack installers
Sandbox Testing
- Detonate .dmg and .pkg in macOS VM with logging enabled
- Watch for connections to known C2 indicators
- Evaluate memory-only behaviors in unsigned apps
General Hygiene
- Remove unverified extensions and “free” tools
- Train users against fake updates and cracked apps
- Segment Apple devices in network policy to enforce Zero Trust
AMOS is stealthy, but its behaviors are predictable. Behavior-based defenses offer the best chance at containment.
Freemindtronic Solutions to Secure macOS
To counter threats like Atomic Stealer, Freemindtronic provides macOS-compatible hardware and software cybersecurity solutions:
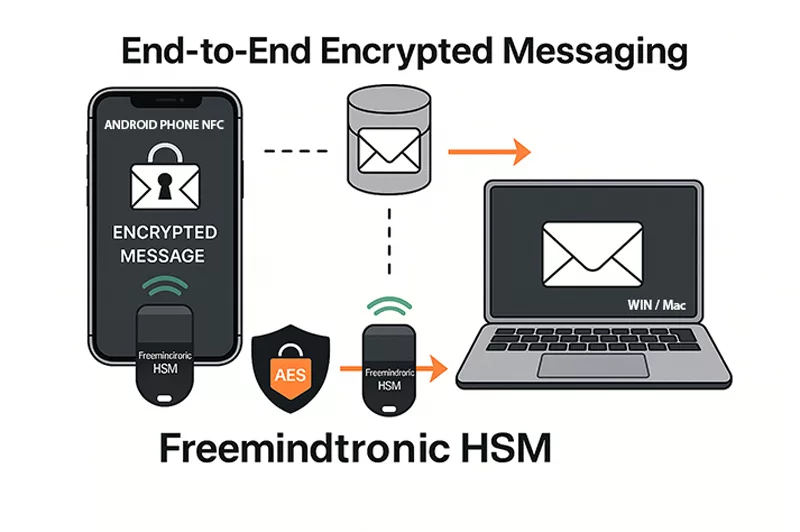
DataShielder: Hardware Immunity Against macOS Infostealers
DataShielder NFC HSM
- Offline AES-256 and RSA 4096 key storage: No exposure to system memory or macOS processes.
- Phishing-resistant authentication: Secure login via NFC, independent from macOS.
- End-to-end encrypted messaging: Works even for email, LinkedIn, and QR-based communications.
- No server, no account, no trace: Total anonymity and data control.
DataShielder HSM PGP
- Hardware-based PGP encryption for files, messages, and emails.
- Zero-trust design: Doesn’t rely on macOS keychain or system libraries.
- Immune to infostealers: Keys never leave the secure hardware environment.
Use Cases for macOS Protection
- Securing Apple Mail, Telegram, Signal messages with AES/PGP
- Protecting crypto assets via encrypted QR exchanges
- Mitigating clipboard attacks with hardware-only storage
- Creating sandboxed key workflows isolated from macOS execution
These tools shift the attack surface away from macOS and into a secure, externalized hardware vault.
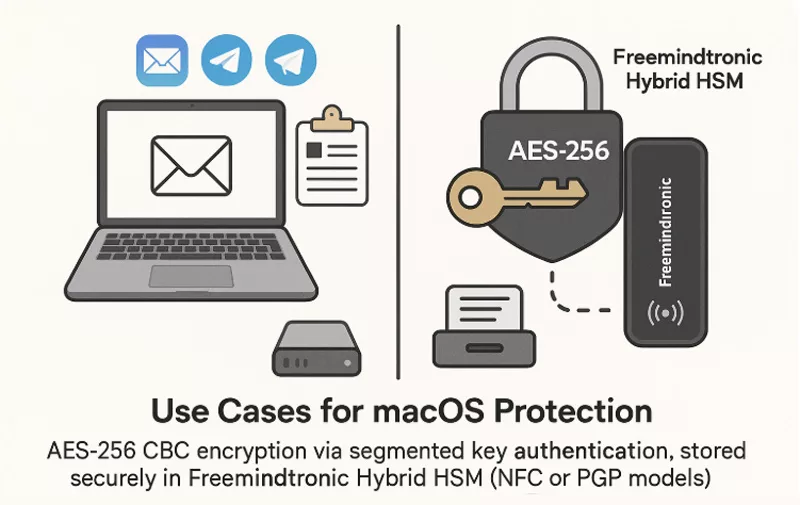
✪ Hybrid HSM from Freemindtronic securely stores AES-256 encryption keys outside macOS, protecting email and messaging apps like Apple Mail, Signal, and Telegram.
SeedNFC HSM Tag
Hardware-Secured Crypto Wallets — Invisible to Atomic Stealer AMOS
Atomic Stealer (AMOS) actively targets cryptocurrency wallets and clipboard content linked to crypto transactions. The SeedNFC HSM 100 Tag, powered by the SeedNFC Android app, offers a 100% externalized and offline vault that supports up to 50 wallets (Bitcoin, Ethereum, and others), created directly on the blockchain.
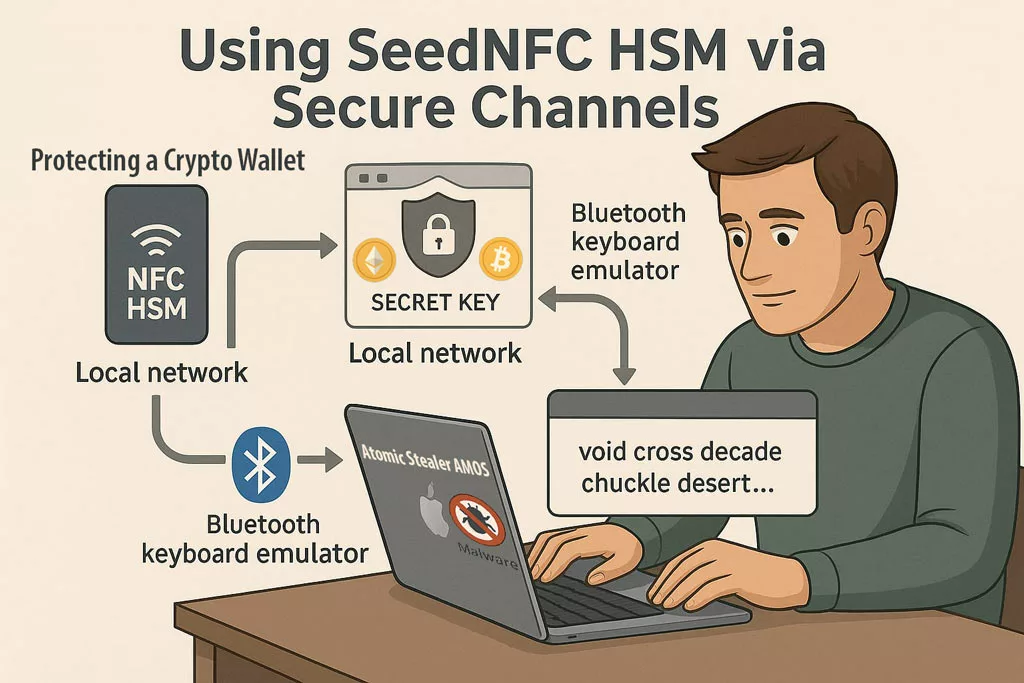
✪ Even if Atomic Stealer compromises the macOS system, SeedNFC HSM keeps crypto secrets unreachable via secure local or Bluetooth emulation channels.
Unlike traditional browser extensions or software wallets:
Private keys are stored fully offline — never touch system memory or the clipboard.
Wallets can be used on macOS and Windows via:
- Web extensions communicating over an encrypted local network,
- Or via Bluetooth keyboard emulation to inject public keys, passwords, or transaction data.
- Wallet sharing is possible via RSA-4096 encrypted QR codes.
-
All functions are triggered via NFC and executed externally to the OS.
This creates a Zero Trust perimeter for digital assets — ideal against crypto-focused malware like AMOS.
Bluetooth Keyboard Emulator
Zero-Exposure Credential Delivery — No Typing, No Trace
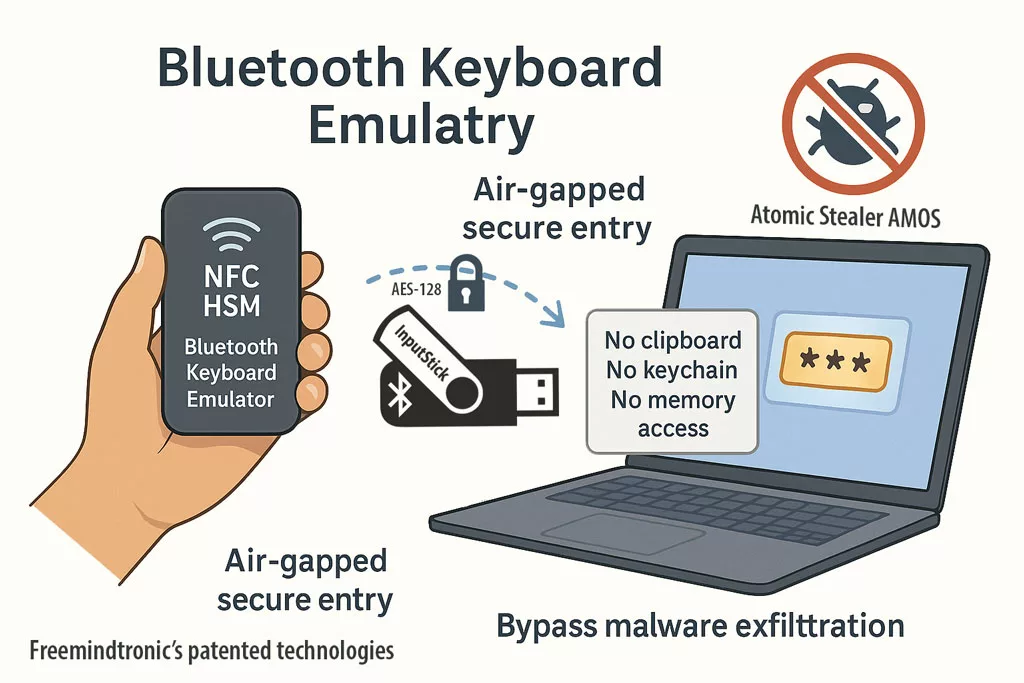
✪ Freemindtronic’s patented NFC HSM delivers secure, air-gapped password entry via Bluetooth keyboard emulation — immune to clipboard sniffers, and memory-based malware like AMOS.
Since AMOS does not embed a keylogger, it relies on clipboard sniffing, browser-stored credentials, and deceptive interface prompts to steal data.
The Bluetooth Keyboard Emulator bypasses these vectors entirely. It allows sensitive information to be typed automatically from a NFC HSM device (such as DataShielder or PassCypher) into virtually any target environment:
- macOS and Windows login screens,
- BIOS, UEFI, and embedded systems,
- Shell terminals or command-line prompts,
- Sandboxed or isolated virtual machines.
This hardware-based method supports the injection of:
- Logins and passwords
- PIN codes and encryption keys (e.g. AES, PGP)
- Seed phrases for crypto wallets
All credentials are delivered via Bluetooth keyboard emulation:
- No clipboard usage
- No typing on the host device
- No exposure to OS memory, browser keychains, or RAM
This creates a physically segmented, air-gapped credential input path — completely outside the malware’s attack surface. Against threats like Atomic Stealer (AMOS), it renders data exfiltration attempts ineffective by design.
Bluetooth keyboard emulation bypasses AMOS exfiltration entirely. Credentials are securely “typed” into systems from NFC HSMs, without touching macOS memory or storage.
What About Passkeys and Private Keys?
While AMOS is not a keylogger, it doesn’t need to be — because it can access your Keychain under the right conditions:
- Use native macOS tools (e.g.,
securityCLI, Keychain API) to extract saved secrets - Retrieve session tokens and autofill credentials
- Exploit unlocked sessions or prompt fatigue to access sensitive data
Passkeys, used for passwordless login via Face ID or Touch ID, are more secure due to Secure Enclave, yet:
- AMOS can hijack authenticated sessions (e.g., cookies, tokens)
- Cached WebAuthn tokens may be abused if the browser remains active
- Keychain-stored credentials may still be exposed in unlocked sessions
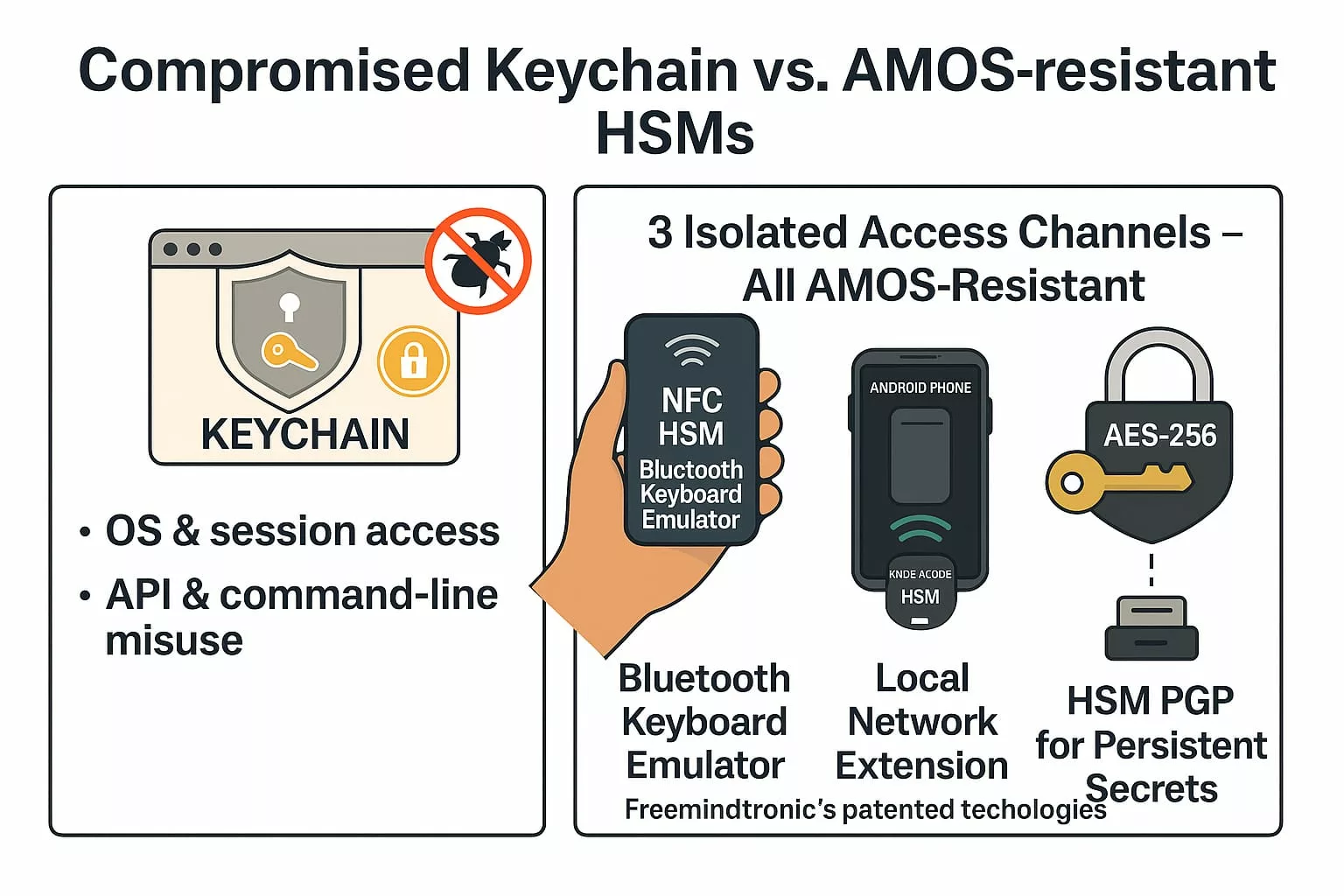
Why External Hardware Security Modules (HSMs) Are Critical
Unlike macOS Keychain, Freemindtronic’s NFC HSM and HSM PGP solutions store secrets completely outside the host system, offering true air-gap security and malware immunity.
Key advantages over macOS Keychain:
- No clipboard or RAM exposure
- No reliance on OS trust or session state
- No biometric prompt abuse
- Not exploitable via API or command-line tools
✪ This infographic compares the vulnerabilities of macOS Keychain with the security of Freemindtronic’s NFC HSM technologies, showing how they resist Atomic Stealer AMOS threats.
Three Isolated Access Channels – All AMOS-Resistant
1. Bluetooth Keyboard Emulator (InputStick)
- Sends secrets directly via AES-128 encrypted Bluetooth HID input
- Works offline — ideal for BIOS, command-line, or sandboxed systems
- Not accessible to the OS at any point
2. Local Network Extension (DataShielder / PassCypher)
- Ephemeral symmetric key exchange over LAN
- Segmented key architecture prevents man-in-the-middle injection
- No server, no database, no fingerprint
3. HSM PGP for Persistent Secrets
- Stores secrets encrypted in AES-256 CBC using PGP
- Works with web extensions and desktop apps
- Secrets are decrypted only in volatile memory, never exposed to disk or clipboard
If your credentials live in macOS, they’re fair game. If they live in NFC HSMs or PGP HSMs — with no OS, clipboard, or RAM exposure — they’re not.
PassCypher Protection Against Atomic Stealer AMOS
PassCypher solutions are highly effective in neutralizing AMOS’s data exfiltration techniques:
PassCypher NFC HSM
- Credentials stored offline in an NFC HSM, invisible to macOS and browsers.
- No use of macOS keychain or clipboard, preventing typical AMOS capture vectors.
- One-time password insertion via Bluetooth keyboard emulation, immune to keyloggers.
PassCypher HSM PGP
- Hardware-secured PGP encryption/decryption for emails and messages.
- No token or password exposure to system memory.
- Browser integration with zero data stored locally — mitigates web injection and session hijacking.
Specific Protections
| Attack Vector Used by AMOS | Mitigation via PassCypher |
|---|---|
| Password theft from browsers | No password stored in browser or macOS |
| Clipboard hijacking | No copy-paste use of sensitive info |
| Fake login prompt interception | No interaction with native login systems |
| Keychain compromise | Keychain unused; HSM acts as sole vault |
| Webmail token exfiltration | Tokens injected securely, not stored locally |
These technologies create a zero-trust layer around identity and messaging, nullifying the most common AMOS attack paths.
Atomic Stealer AMOS and the Future of macOS Security Culture

✪ Atomic doesn’t just expose flaws in Apple’s defenses. It dismantles our assumptions.
For years, users relied on brand prestige instead of security awareness. Businesses excluded Apple endpoints from serious defense models. Governments overlooked creative and administrative Macs as threats.
That era is over.
Atomic forces a cultural reset. From now on, macOS security deserves equal investment, equal scrutiny, and equal priority.
It’s not just about antivirus updates. It’s about behavioral change, threat modeling, and zero trust applied consistently—across all platforms.
Atomic Stealer will not be the last macOS malware we face. But if we treat it as a strategic wake-up call, it might be the last we underestimate.
If your credentials live in macOS, they’re fair game. If they live in NFC HSMs with no OS or network dependency, they’re not.
Strategic Note
Atomic Stealer is not a lone threat—it’s a blueprint for hybrid cyber-espionage. Treating it as a one-off incident risks underestimating the evolution of adversarial tooling. Defense today requires proactive anticipation, not reactive response.


















































Pingback: Innovation of rupture: strategic disobedience and technological sovereignty - Freemindtronic