2015, Cyberculture
Technology Readiness Levels: TRL10 Framework
Technology Readiness Levels (TRL) provide a structured framework to measure the maturity of innovations, from basic research to mission-proven systems. This Chronicle offers a sovereign perspective on how the TRL 1–9 scale shapes strategic adoption in defense, critical infrastructure, and digital security.
Executive Summary — Technology Readiness Levels
⮞ Reading Note
If you only want the essentials, this Executive Summary (≈4 minutes) explains how the TRL framework (1–9) maps the maturity of technologies. For the full Chronicle (≈25 minutes), continue below.
⚡ Key Idea
The TRL framework provides a common language to evaluate innovation — from scientific principles (TRL1) to proven mission operations (TRL9). Each step marks a critical threshold for sovereign technology adoption.
✦ Why it Matters
- Ensures consistency in R&D funding and evaluation.
- Reduces risk in defense, aerospace, and critical infrastructure projects.
- Supports sovereign decision-making in supply chains and digital security.
✓ Sovereign Countermeasure
Using TRL milestones, sovereign actors can validate innovations without relying on external certification chains. This reinforces trust in critical systems and prevents strategic dependency.
• TRL 1–9: a universal framework for innovation maturity
• Each stage defines exit criteria, reducing ambiguity in sovereign procurement
• Prevents premature deployment of immature systems in critical domains
• Strategic relevance for AI, quantum computing, and sovereign cybersecurity adoption
Chronicle to Read
Introductory Reading Time: ≈ 4 minutes
Full Reading Time: ~25 minutes
Complexity: Advanced — R&D, defense, sovereign IT
Languages: EN, FR, ES, CAT
Editorial type: Cyberculture – Strategic Chronicle
About the Author: Jacques Gascuel is the inventor and founder of Freemindtronic®. His work focuses on sovereign hardware-based security, including NFC encryption devices, zero-trust architectures, and counter-espionage resilience systems.
In Cyberculture ↑ Correlate this Chronicle with other sovereign threat analyses in the same editorial rubric.
Strategic Navigation
- Executive Summary
- Historical Genesis
- Understanding TRL 1–9
- Beyond TRL
- Weak Signals
- Standards & Governance
- Research Frontiers
- All About — The Future of Technology Readiness Level (TRL) 10
- Sovereign Implications
- Strategic Outlook
- Sectoral Use Cases
- Case Study — From TRL 5 to TRL 8
- Freemindtronic-and-trl-10
- TRL 10 in Practice — Freemindtronic Sovereign Proof
- What About Your TRL?
- FAQ
Historical Genesis (NASA → DoD → EU)
Initially developed by NASA to assess the maturity of space technologies and reduce mission risk, the Technology Readiness Levels (TRL) scale quickly proved its strategic value. It was subsequently adopted and adapted by defense organizations such as the U.S. Department of Defense (DoD) to standardize acquisition milestones. Over time, it became a reference framework for European research and innovation programs, aligning pre-industrial validation with deployment strategies.
As a result, the TRL framework is now embedded in sovereign programs where reliability, auditability, and interoperability are non-negotiable.
⮞ Summary
The TRL scale evolved from NASA’s internal assurance tool into a globally recognized decision-making framework. It now structures funding, testing, and certification across sovereign ecosystems — from space systems to cybersecurity.
For formal reference, see the international standard ISO 16290:2013 – Space systems — Definition of Technology Readiness Levels (TRLs).
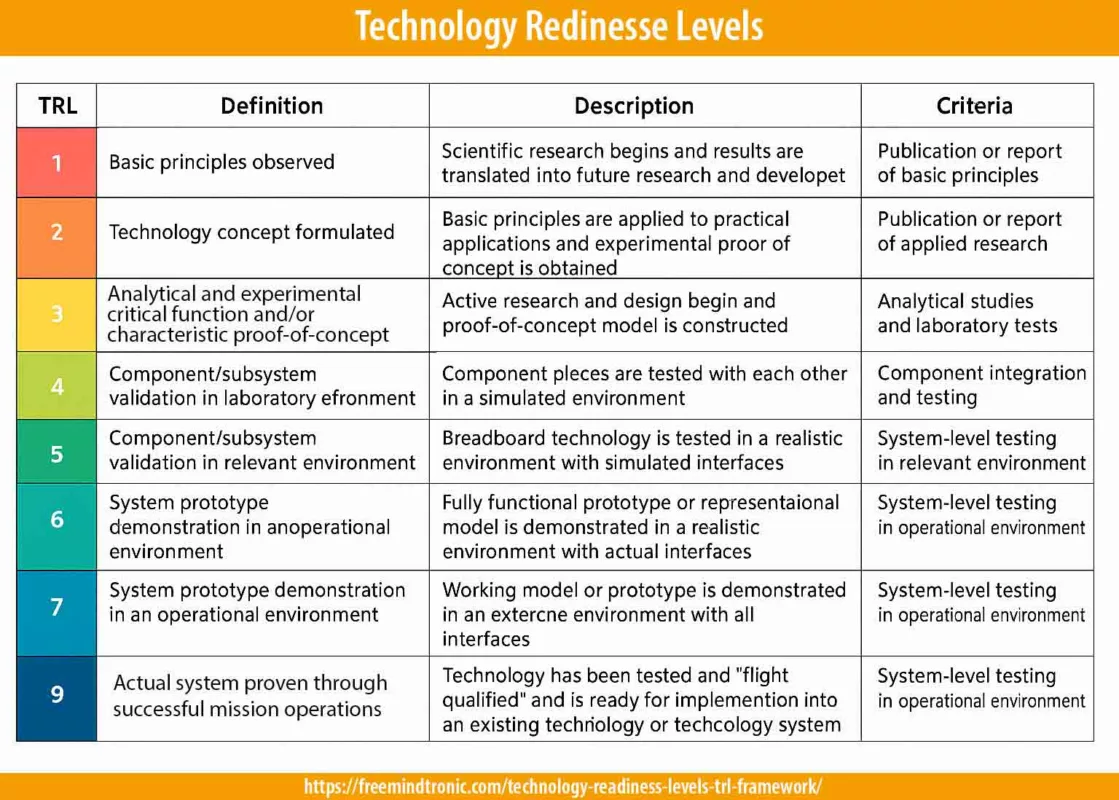
Understanding TRL 1-9 – Technology Readiness Scale in Depth
The Technology Readiness Level (TRL) framework, standardized by NASA and adopted in EU research & innovation policy (e.g. Horizon 2020, Horizon Europe), gives a rigorous scale from TRL 1 (basic principles) to TRL 9 (mission-proven systems). It enables innovation maturity assessment in defense supply chains and supports prototype validation in relevant operational environments.
| TRL | Definition | Detailed Description | Criteria / Exit Conditions |
|---|---|---|---|
| 1 | Basic principles observed | Scientific research begins; underlying scientific truths are documented. Hypotheses, mathematical models, basic research. | Peer-reviewed publication or formal report of basic scientific principles. No prototype. |
| 2 | Technology concept formulated | Conceptualization of practical application. Speculative, analytical work; no experimental proof yet. | Documented concept study; feasibility analysis; early software/hardware mockups. |
| 3 | Proof-of-concept (analytical & experimental) | Active R&D; small scale models or experiments validate critical functions in lab settings. | Laboratory tests; modeling; limited scale demonstrators. |
| 4 | Component / Subsystem validation in laboratory environment | Integration of components; validation of subsystems under controlled conditions; no full environment yet. | Subsystem test benches; performance metrics measured; validation under simulated loads. |
| 5 | Component / Subsystem validation in relevant environment | Breadboard or subsystem tested in conditions representative of actual use (interfaces, perturbations). | Environmental stress tests; compatibility verification with system interfaces. |
| 6 | Prototype demonstration in relevant environment | Fully functional prototype or system/model demonstrated in a relevant (realistic) operational environment with actual interfaces. | System-level testing; integration; performance under representative environmental and operational conditions. |
| 7 | System prototype demonstration in operational environment | Prototype works under operational stresses; system demonstrator in the field, with all relevant interfaces, perhaps non-flight but live use. | Field trials, near-mission deployment; reliability metrics collected; safety/risk testing. |
| 8 | Actual system completed & qualified | The system has been fully built, qualified through test and demonstration under operational conditions; ready for commissioning or deployment. | Full qualification; certification if relevant; readiness for integration/deployment. |
| 9 | Actual system proven through successful mission operations | System has been operated in live mission context; meets performance, reliability, and safety requirements. | Mission success; feedback loops; maintenance/readiness assurance; audit & post-operation evaluation. |
⮞ Practical Summary
Use this table as the definitive guide when assessing technology readiness: each level has clearly defined exit criteria. Avoid ambiguity by demanding full documentation at each TRL checkpoint.
⧉ Beyond TRL — Comparative Readiness Scales
| Scale | Purpose | Domain |
|---|---|---|
| TRL (Technology Readiness Levels) | Measures innovation maturity from principles (TRL 1) to mission-proven systems (TRL 9). | Defense, aerospace, cybersecurity, R&D policy. |
| MRL (Manufacturing Readiness Level) | Evaluates readiness of industrial processes, supply chain, and production scalability. | Industry, automotive, defense acquisition. |
| SRL (System Readiness Level) | Assesses integration maturity of multi-subsystem architectures. | Complex systems (space, telecom, defense). |
| CRL (Commercial Readiness Level) | Measures market adoption, economic sustainability, and business viability. | Energy, infrastructure, green tech. |
Weak Signals — Early Indicators
– TRL increasingly referenced in EU cyber regulations (NIS2, CRA)
– Ethical and environmental compliance as hidden readiness layer
– Risk of dependency on non-sovereign testbeds for validation
Standards & Governance
- ISO 16290:2013 — Defines TRL scale for space systems, internationally recognized.
- European Commission (Horizon Europe) — Projects must indicate initial and targeted TRL levels.
- NATO STANAG — Aligns TRL with defense procurement standards.
- EARTO (2014 Report) — Recommends TRL as R&I policy tool for EU innovation strategy.
Research Frontiers — Beyond TRL 9?
Some research forums suggest extending the TRL concept toward sustainability and resilience readiness. Proposals include:
- TRL 10 — Long-term resilience, lifecycle maintenance, and sustainability assurance.
- Ethical TRL — Incorporating ethical and regulatory compliance in readiness assessment.
- Digital TRL — Adaptations for AI, quantum computing, and zero-trust cybersecurity environments.
All About — The Future of Technology Readiness Level (TRL) 10
While the official TRL framework ends at level 9, some research communities and defense innovation bodies have begun exploring the concept of a TRL 10. This extension aims to address domains beyond operational proof, emphasizing resilience, lifecycle assurance, and sovereign trust.
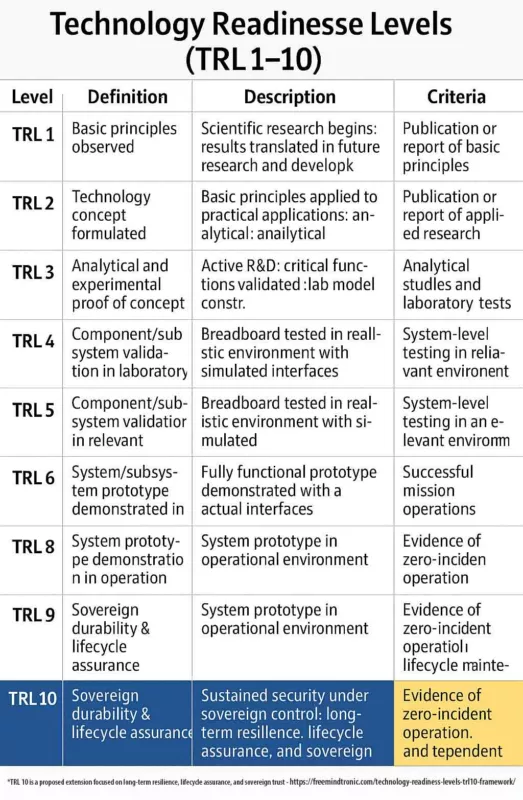
- Long-Term Resilience: Ensures that technology can withstand decades of use, evolving threats, and environmental pressures without critical failure.
- Lifecycle Security: Covers supply chain integrity, maintenance assurance, and update reliability throughout the entire operational life of the system.
- Ethical & Regulatory Alignment: Integrates compliance with cybersecurity acts such as the EU NIS2 Directive and the EU Cyber Resilience Act.
- Sovereign Trust Layer: Adds validation that systems remain independent of foreign certification monopolies, ensuring autonomy in defense and critical infrastructure.
⮞ Key Takeaway
TRL 10 represents the next frontier of technology readiness — moving from systems that are mission-proven (TRL 9) to systems that are sovereignly trusted, resilient, and future-proof. It is not yet an official standard, but it is already being debated in policy circles, think-tanks, and sovereign R&D programs.
For context, see the internationally recognized ISO 16290:2013 — Space systems — Definition of Technology Readiness Levels (TRLs), which remains the reference for TRL 1–9, and evolving EU policy frameworks such as Horizon Europe Calls where TRL milestones are mandatory for project funding.
Sovereign Implications
Adopting TRL frameworks ensures that states and organizations can independently evaluate maturity without depending on external certification monopolies.
- Defense & Aerospace: Prevents premature deployment of immature tech.
- Critical Infrastructure: Ensures resilience before rollout.
- Sovereign Autonomy: Reinforces national independence in R&D chains.
✓ Sovereign Countermeasures
- Use sovereign testbeds for TRL validation
- Apply offline HSM with no telemetry for critical assets
- Avoid reliance on foreign certification monopolies
Strategic Outlook
The TRL framework will remain central as emerging fields (AI, quantum computing, edge security) require structured validation before sovereign adoption. Future sovereign strategies should extend TRL frameworks to include ethical and regulatory compliance dimensions.
Sectoral Use Cases — Sovereign Cybersecurity
Avionics systems validated through TRL 7 (prototype demo) → TRL 9 (flight-proven mission).
Zero Trust protocol tested at TRL 5 (lab environment) → TRL 6 (relevant environment) before integration in national infrastructure.
New battery technology progresses from TRL 3 (proof-of-concept) to TRL 7 (field prototype), ensuring viability before market launch.
A national cybersecurity agency applies TRL5→TRL6 to validate a secure communication protocol in a controlled but realistic environment. This ensures resilience against supply chain compromises before large-scale deployment.
Case Study — From TRL 5 to TRL 8 in European Cybersecurity
A concrete example of TRL progression can be found in the European Cybersecurity Competence Centre (ECCC) programs under Horizon Europe. In 2023–2024, the SPARTA Next Generation Intrusion Detection Protocol advanced from TRL 5 (component validation in a relevant environment) to TRL 8 (system completed and qualified in an operational setting).
- TRL 5 (2023): Protocol validated in controlled environments simulating cross-border cyberattacks.
- TRL 6–7 (2024): Field demonstrations across EU research testbeds, including France and Spain.
- TRL 8 (2025): Integration in critical infrastructure pilots (energy and transport), validated under operational cybersecurity stress tests.
Key Takeaway:
This real case illustrates how EU projects enforce progressive TRL checkpoints before large-scale deployment, ensuring that sovereign cybersecurity tools are validated in realistic conditions.
Official references:
– European Cybersecurity Competence Centre (ECCC)
– CORDIS — EU R&D Projects Database
Freemindtronic and TRL 10 — From R&D to Sovereign Solutions
Freemindtronic® applies the Technology Readiness Levels framework in all its R&D activities — from concept and design to manufacturing and deployment.
Unlike most private actors, Freemindtronic extends the model up to TRL 10, validating not only functional maturity but also:
- Cyber safety — ensuring resilience of hardware and critical infrastructures against failures and external stressors.
- Cybersecurity — hardware-based zero-trust architectures, counter-espionage resilience systems, and secure-by-design NFC encryption devices.
- Sovereign trust — independence from foreign certification monopolies and compliance with EU strategic autonomy policies.
📩 To explore Freemindtronic’s sovereign cybersecurity and safety solutions, contact us directly.
TRL 10 in Practice — Freemindtronic Sovereign Proof
A unique and verifiable example of TRL 10 applied in sovereign R&D comes from Freemindtronic®.
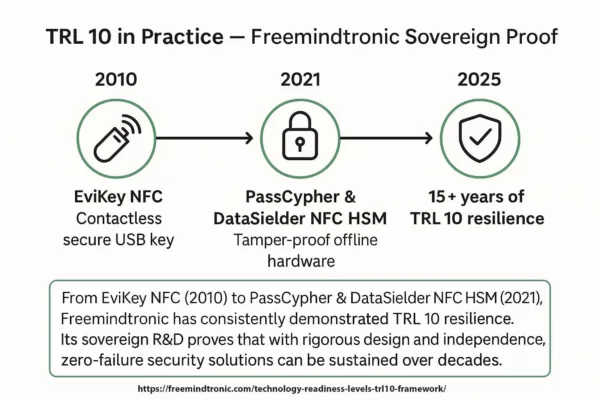
- EviKey NFC (2010) — the world’s first contactless secure USB key, designed to resist cyberattacks and physical tampering.
- PassCypher NFC HSM (2021) — a sovereign offline password and secret manager stored in tamper-proof NFC hardware.
- DataSielder NFC HSM (2021) — an offline hardware encryption/decryption solution ensuring zero cloud or telemetry dependency.
What makes them remarkable:
- 15+ years of operation with zero security incidents (EviKey NFC).
- No failures or returns (zero-SAV) across deployments worldwide.
- No vulnerabilities, no CVEs, no online complaints — a rare achievement in cybersecurity hardware.
- Sovereign lifecycle control: hardware, firmware, and validation without reliance on foreign certification chains.
From EviKey NFC (2010) to PassCypher & DataSielder NFC HSM (2021), Freemindtronic has consistently demonstrated TRL 10 resilience.
Its sovereign R&D proves that with rigorous design and independence, zero-failure security solutions can be sustained over decades.
References & External Sources (2023–2025)
FAQ — Technology Readiness Levels (TRL)
TRL (Technology Readiness Levels) measures the maturity of a technology from research principles to mission-proven systems.
MRL (Manufacturing Readiness Levels) evaluates industrial readiness, supply chain resilience, and production scalability.
→ Together, TRL and MRL give a holistic view of both technical and industrial maturity, essential for sovereign R&D projects.
Yes. EU research frameworks such as Horizon Europe allow TRL 1–2 funding for basic and applied research.
However, most applied research calls require TRL ≥ 5 as a target for eligibility.
This ensures projects deliver real-world demonstrators, not just theoretical concepts.
Transitioning from TRL 6 (prototype in relevant environment) to TRL 7 (operational prototype) requires:
- Field testing in live operational conditions
- Reliability and safety metrics collection
- Independent validation or sovereign certification
Example: a cybersecurity protocol tested in a national agency sandbox (TRL6) and then deployed in a live defense infrastructure (TRL7).
Sovereignty ensures that innovation maturity assessments are not dependent on foreign validation chains.
Without sovereign TRL validation:
- Critical infrastructure could be exposed to external control
- Supply chains remain vulnerable to hidden dependencies
- Strategic autonomy in defense and digital security is undermined
→ Sovereign TRL checkpoints reinforce national independence and digital trust.
TRL 10 is a proposed extension focusing on long-term resilience, sustainability, and sovereign digital trust.
While TRL 1–9 evaluate functionality and deployment readiness, TRL 10 integrates:
- Lifecycle maintenance and sustainability metrics
- Ethical & regulatory compliance (AI, quantum, cybersecurity)
- Resilience against supply chain attacks and espionage
→ TRL 10 = beyond deployment, toward sovereign durability.
Yes. The most cited standards include:
Yes. Under the European Cybersecurity Competence Centre (ECCC),
the SPARTA Next-Gen Intrusion Detection Protocol progressed:
- 2023: TRL 5 — validated in controlled lab environments
- 2024: TRL 6–7 — field demonstrations across EU sovereign testbeds
- 2025: TRL 8 — integrated into energy and transport infrastructure pilots
This illustrates how EU projects move step by step toward sovereign deployment.
The official highest TRL is TRL 9, representing mission-proven systems.
Some research communities propose TRL 10 as an extension for resilience, sustainability, and sovereign trust.
TRL 0 is not officially part of the NASA or ISO standard scales.
It is sometimes used in academia to describe the stage *before research begins* — when only an idea or theoretical concept exists.
It helps distinguish between pre-research ideation and TRL 1 (basic principles observed).
The “Valley of Death” describes the gap between TRL 4–6, when technologies have been validated in labs but lack funding or risk tolerance for operational deployment.
Crossing it often requires public investment or sovereign programs to de-risk innovation.
The reference standard is ISO 16290:2013,
which defines Technology Readiness Levels (TRLs) for space systems and is widely used internationally.
In Horizon Europe projects, TRL 6 corresponds to a prototype demonstrated in a relevant environment.
EU calls often require starting at TRL 3–5 and aiming at TRL ≥ 6–7 to secure funding.
– TRL 7: System prototype demonstrated in an operational environment.
– TRL 8: Actual system completed and qualified through operational testing.
→ TRL 8 means the system is ready for deployment or commissioning.
The Technology Readiness Level (TRL) scale is used worldwide by organizations such as NASA, the U.S. Department of Defense (DoD), the European Commission (Horizon Europe), and NATO, as well as national innovation agencies assessing maturity of new technologies.
It is also adopted in the private sector. For example, Freemindtronic® applies the TRL framework in all its sovereign R&D, extending the model up to TRL 10 to validate resilience, counter-espionage security, and sovereign trust in its hardware-based cybersecurity and safety solutions.
→ This demonstrates that TRL is not only a public-sector standard but also a strategic tool for companies innovating in critical infrastructures and digital sovereignty.
🔗 Related Reading
To deepen your understanding of sovereign technology maturity and its strategic implications, we recommend exploring the following reference articles:
⧉ What We Didn’t Cover
This Chronicle focused on TRL as a strategic framework. Future work will address sector-specific adaptations such as AI trustworthiness, cloud zero-trust evaluation, and sustainability-linked readiness levels.

































































