Fingerprint Systems Really Secure by Jacques Gascuel: This article will be updated with any new information on the topic.
Fingerprint Security
You will surely be amazed by our discoveries! These systems verify your identity on smartphones and other devices by using the unique patterns of your finger. But is their security level? In this study, we explore the weaknesses of these systems and how various actors, from cybercriminals to sovereign entities, can exploit them. We looked at 25 techniques for corrupting fingerprint authentication systems. We will also introduce an effective dual-use defense solution: DataShielder HSM solutions to protect your secrets and sensitive data even if this biometric authentication system becomes compromised.
2026 Digital Security
January 23, 2026
2026 Digital Security
January 17, 2026
2026 Digital Security
January 8, 2026
2026 Digital Security
January 7, 2026
2025 Digital Security
January 6, 2026
2026 Digital Security
January 5, 2026
2025 Digital Security
January 5, 2026
2025 Digital Security
December 21, 2025
Acoustic analysis attack. Chemical fingerprint attack. Phishing attacks. Session hijacking attack. Privilege escalation attack. Attack by electronic devices. Spyware attack. False acceptance attack. False rejection attack. Substitution attack. Modification attack. Spoofing attack. Attack by opponent generation. Acoustic analysis attack. Partial fingerprint attack. Adversarial Generation Attack, Impersonation Attack, Code Injection Attack, Residual Fingerprint Attack.BrutePrint. PrintListener
Fingerprint Biometrics: An In-Depth Exploration of Security Mechanisms and Vulnerabilities
It is a widely recognized biometric authentication system for identity verification. In this overview of fingerprint authentication systems, we will explore comprehensively to understand the complex world of fingerprint biometrics. Our goal is to provide a detailed exploration of these systems, their inner workings, vulnerabilities, and countermeasures.
Demystifying Fingerprint Systems: A Thorough Examination
Two fundamental components make up these systems: the fingerprint sensor and the comparison algorithm.:
The Fingerprint Sensor: Where Biometric Data Begins
These systems rely on an essential component: the fingerprint sensor. It captures the finger image and converts it into a digital format. Different types of sensors exist, each with their advantages and disadvantages:
- Optical sensors: They use light and a camera to create a high-resolution image.
- Capacitive sensors: They use an array of small capacitors to measure the differences in electrical charge between the ridges and valleys.
- Ultrasonic sensors: They use sound waves to create a three-dimensional image.
- Thermal sensors: They detect the heat emitted by the finger to generate an image.
The Comparison Algorithm: The Gatekeeper of Access
The comparison algorithm is a critical software component that analyzes the captured fingerprint image. Its role is vital:
- Image Analysis: The algorithm scrutinizes the fingerprint image, extracting its unique features.
- Template Comparison: It then compares these features to one or more stored templates, serving as reference fingerprints for authorized users.
- Threshold Criteria: Access is granted if the algorithm determines a significant similarity between the captured image and a stored template, surpassing a predefined threshold. If not, the system considers the fingerprint invalid and denies access.
Fingerprint System Vulnerabilities and Attack Techniques
First, before evaluating attack techniques against fingerprinting systems, let’s explore different attack types, techniques, motivations, and strategies. In our thorough analysis of fingerprint system vulnerabilities, we must acknowledge numerous attack techniques employed by various actors. These techniques, driven by diverse motivations ranging from personal gain to malicious intent, illuminate the complexities of fingerprint system security. We’ve identified a total of twenty-five (25) distinct attack types, categorized into five groups in this study: “Electronic Devices for Biometric Attacks,” “Additional Fingerprint Attacks,” “Advanced Attacks,” “Attacks on Lock Patterns,” and “Attacks on Fingerprint Sensors.”
Attacks on Fingerprint Sensors
Fingerprint sensors, a common biometric authentication method, are vulnerable to several attack types and techniques update 23 february 2024:
| ATTACK TYPE |
TECHNIQUE |
MOTIVATIONS |
STRATEGIES |
| Residual Fingerprint Attack |
Recovers the smartphone owner’s fingerprint left on surfaces, reproducing it. |
Identity theft, unauthorized access, or malicious purposes. |
Exploits traces of fingerprints on surfaces using materials like gelatin, silicone. |
| Code Injection Attack |
Injects malicious code to bypass fingerprint sensor security. |
Compromises device security for data theft or illicit activities. |
Exploits software vulnerabilities for unauthorized access to biometric data. |
| False Acceptance Attack |
The system accepts a fingerprint that doesn’t belong to the authorized user. |
Identity theft, unauthorized access, or malicious intentions. |
Can occur due to poor sensor quality, a high tolerance threshold, or similarity between different individuals’ fingerprints. |
| False Rejection Attack |
The system rejects a fingerprint that belongs to the authorized user. |
Identity theft, unauthorized access. |
Can occur due to poor sensor quality, a low tolerance threshold, environmental changes, or alterations to the user’s fingerprint. |
| Substitution Attack |
Tricks the system with an artificial fingerprint. |
Identity theft or unauthorized access. |
Can be done using materials like gelatin, silicone, latex, or wax. |
| Modification Attack |
Tricks the system with a modified fingerprint. |
Identity theft or to conceal the user’s identity. |
Can be done using techniques like gluing, cutting, scraping, or burning. |
| Impersonation Attack |
Tricks the system with another user’s fingerprint, either with their consent or by force. |
Identity theft using force, threats, bribery, or seduction. |
Uses the fingerprint of another user who has given consent or has been coerced into doing so. |
| Adversarial Generation Attack |
Tricks the system with images of fingerprints generated by an adversarial generative adversarial network (GAN). |
Bypasses liveness detection methods based on deep learning. |
Mimics the appearance of real fingerprints. |
| Acoustic Analysis Attack |
Tricks the system by listening to the sounds emitted by the fingerprint sensor during fingerprint capture. |
Can reconstruct the fingerprint image from acoustic signals. |
Use noise cancellation techniques, encrypt acoustic signals, or use liveness detection methods |
| Partial Print Attack |
Tricks the system with a partial fingerprint from the registered fingerprint. |
Increases the false acceptance rate by exploiting the similarity between partial prints of different users. |
Can use a portion of the registered fingerprint. |
| Privilege Escalation Attack |
Exploits vulnerabilities in the operating system or application to obtain higher privileges than those granted by fingerprint authentication |
Can access sensitive data, manipulate system files, perform unauthorized actions, or bypass security measures |
Use strong passwords, enforce multi-factor authentication, limit user privileges, patch system vulnerabilities, monitor user activities, and audit logs |
| Spoofing Attack |
Imitates a legitimate fingerprint or identity to deceive the system or the user |
Can gain access, steal information, spread malware, or impersonate someone. |
Use liveness detection methods, verify the authenticity, avoid trusting unknown sources, and report spoofing attempts |
| PrintListener: Side-channel Attack |
Utilizes acoustic signals from finger friction on touchscreens to replicate fingerprints |
Gain unauthorized access to devices and services protected by fingerprint authentication |
Implement noise interference, use advanced fingerprint sensors resistant to acoustic analysis, enable multifactor authentication, regularly update security protocols |
For more information on new attack type “PrintListener” (a specific acoustic analysis attack), readers are encouraged to explore the detailed article at https://freemindtronic.com/printlistener-technology-fingerprints/.
These attacks expose vulnerabilities in fingerprint sensor technology and underline the need for robust security measures.
Attacks on Lock Patterns (For Lock Screen Authentication)
Lock patterns, often used on mobile devices for screen unlocking, are susceptible to various attack techniques:
| ATTACK TYPE |
TECHNIQUE |
MOTIVATIONS |
STRATEGIES |
| Brute Force Attack |
Attempts all possible lock pattern combinations. |
Gains unauthorized device access. |
Systematically tests different pattern combinations. |
| Replica Fingerprint Attack |
Uses a 3D printer to create a replica fingerprint. |
Unauthorized access or identity theft. |
Produces a replica for sensor authentication. |
| Sensor Vulnerabilities |
Exploits sensor technology vulnerabilities. |
Compromises device security for malicious purposes. |
Identifies and exploits sensor technology weaknesses. |
| BrutePrint Attack |
Intercepts messages, emulating the fingerprint sensor. |
Gains unauthorized access, often with hardware components. |
Exploits communication protocol vulnerabilities. |
These attacks target the vulnerabilities in lock pattern authentication and underscore the importance of strong security practices.
Advanced Attacks
Advanced attacks employ sophisticated techniques and technologies to compromise fingerprint systems:
| ATTACK TYPE |
TECHNIQUE |
MOTIVATIONS |
STRATEGIES |
| Presentation Attack |
Presents manipulated images or counterfeit fingerprints. |
Espionage, identity theft, or malicious purposes. |
Crafts counterfeit fingerprints or images to deceive sensors. |
| Rapid Identification Attack |
Uses advanced algorithms to swiftly identify fingerprints. |
Corporate espionage, financial gain, or enhanced security. |
Quickly identifies fingerprints from extensive datasets. |
| Digital Footprint Attack |
Collects and analyzes the online data and activity of the target, using open source intelligence tools or data brokers |
Can obtain personal information, preferences, habits, or vulnerabilities of the target. |
Use privacy settings, delete unwanted data, avoid oversharing, and monitor online reputation |
These advanced attacks leverage technology and data to compromise fingerprint-based security.
Network-Based Attacks
Network-based attacks are those that target the communication or data transmission between the device and the fingerprint authentication system. These attacks can compromise the integrity, confidentiality, or availability of the biometric data or the user session. In this section, we will discuss four types of network-based attacks: phishing, session hijacking, privilege escalation, and spyware.
| ATTACK TYPE |
TECHNIQUE |
MOTIVATIONS |
STRATEGIES |
| Phishing Attack |
Technique: Phishing attacks involve sending fraudulent messages to victims, enticing them to click on a link or download an attachment. These malicious payloads may contain code designed to steal their fingerprints or redirect them to a fake website requesting authentication. |
Motivations: Phishing attacks are motivated by the desire to deceive and manipulate users into revealing their fingerprint data or login credentials. |
Strategies: Phishing attackers employ various tactics, such as crafting convincing emails, spoofing legitimate websites, and using social engineering to trick users. |
| Session Hijacking Attack |
Technique: Session hijacking attacks aim to intercept or impersonate an authenticated user’s session, exploiting communication protocol vulnerabilities or using spyware. |
Motivations: Session hijacking is typically carried out to gain unauthorized access to sensitive information or systems, often for financial gain or espionage. |
Strategies: Attackers employ packet sniffing, session token theft, or malware like spyware to compromise and take control of active user sessions. |
| Spyware Attack |
Technique: Spyware attacks infect the device with spyware to capture fingerprint data. |
Motivations: Spyware attacks are driven by the objective of illicitly obtaining biometric data for malicious purposes, such as identity theft or unauthorized access. |
Strategies: Attackers use spyware to secretly record and transmit fingerprint information, often through backdoors or covert channels, without the victim’s knowledge. |
| Predator Files |
Infects Android phones with a spyware application that can access their data, including fingerprint information. |
Sold to multiple governments for targeting political opponents, journalists, activists, and human rights defenders in over 50 countries. |
Use spyware detection and removal tools, update system software, avoid downloading untrusted applications, and scan devices regularly |
As we can see from the table above, network-based attacks pose a serious threat to fingerprint authentication systems and users’ privacy and security. Therefore, it is essential to implement effective countermeasures and best practices to prevent or mitigate these attacks. In the next section, we will explore another category of attacks: physical attacks.
Electronic Devices for Biometric Attacks
Some electronic devices are designed to target and compromise fingerprint authentication systems. Here are some notable examples:
| Device |
Description |
Usage |
STRATEGIES |
| Cellebrite UFED |
A portable device capable of extracting, decrypting, and analyzing data from mobile phones, including fingerprint data. Used by law enforcement agencies worldwide. |
Used by law enforcement agencies to access digital evidence on mobile phones. |
Applies substances to damage or obscure sensor surfaces. |
| GrayKey |
A black box device designed to unlock iPhones protected by passcodes or fingerprints using a “brute force” technique. Sold to law enforcement and government agencies for investigative purposes. |
Sold to law enforcement and government agencies for investigative purposes to unlock iPhones. |
Use strong passwords, enable encryption, disable USB access, and update system software. |
| Chemical Attacks |
Alters or erases fingerprints on sensors. |
Prevents identification or creates false identities. |
Use fingerprint enhancement techniques, verify the authenticity, and use liveness detection methods |
These devices pose a high risk to biometric systems because they can allow malicious actors to access sensitive information or bypass security measures. They are moderate to high in ease of execution because they require physical access to the target devices and the use of costly or scarce devices. Their historical success is variable because it depends on the quality of the devices and the security of the biometric systems. They are currently relevant because they are used by various actors, such as government agencies, law enforcement, or hackers, to access biometric data stored on mobile phones or other devices. This comprehensive overview of attack types, techniques, motivations, and strategies is crucial for improving biometric authentication system security.
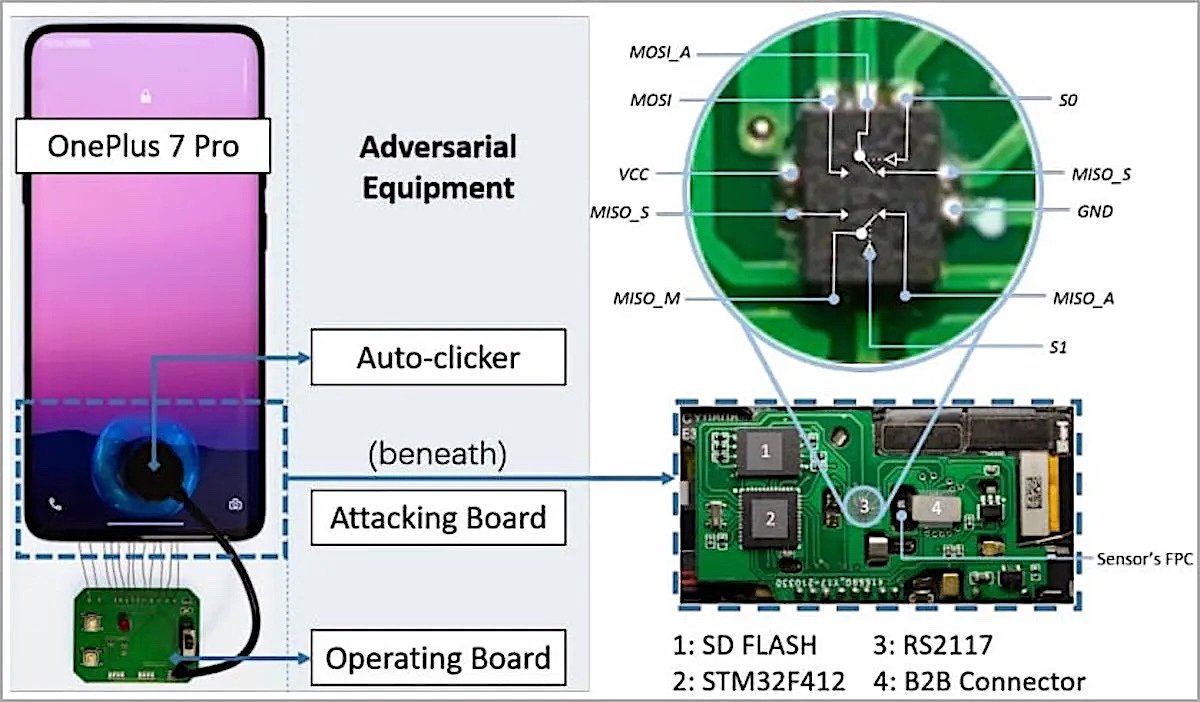
BrutePrint: A Novel Attack on Fingerprint Systems on Phones
Fingerprint systems on phones are not only vulnerable to spoofing or data breach attacks; they are also exposed to a novel attack called BrutePrint. This attack exploits two zero-day vulnerabilities in the smartphone fingerprint authentication (SFA) framework. BrutePrint allows attackers to bypass the attempt limit and liveness detection mechanisms of fingerprint systems on phones. It also enables them to perform unlimited brute force attacks until finding a matching fingerprint.
How BrutePrint Works

BrutePrint works by hijacking the fingerprint images captured by the sensor. It applies neural style transfer (NST) to generate valid brute-forcing inputs from arbitrary fingerprint images. BrutePrint also exploits two vulnerabilities in the SFA framework:
- Cancel-After-Match-Fail (CAMF): this vulnerability allows attackers to cancel the authentication process after a failed attempt. It prevents the system from counting the failed attempts and locking the device.
- Match-After-Lock (MAL): this vulnerability allows attackers to infer the authentication results even when the device is in “lock mode”. It guides the brute force attack.To perform a BrutePrint attack, attackers need physical access to the phone, a database of fingerprints, and a custom-made circuit board that costs about 15 dollars. The circuit board acts as a middleman between the sensor and the application. It intercepts and manipulates the fingerprint images.
How to Prevent BrutePrint
BrutePrint is a serious threat to phone users who rely on fingerprint systems to protect their devices and data. It shows that fingerprint systems on phones are not as secure as they seem. They need more robust protection mechanisms against brute force attacks. Some of the possible ways to prevent BrutePrint are:
- Updating the phone’s software: this can help fix the vulnerabilities exploited by BrutePrint and improve the security of the SFA framework.
- Using multifactor authentication: this can increase the level of security and reduce the risks of spoofing or brute force attacks. It combines fingerprint authentication with another factor, such as a password, a PIN code, a pattern lock screen ,or other trust criteria that allows patented segmented key authentication technology developed by Freemindtronic in Andorra .
- Use of DataShielder HSM solutions: these are solutions developed by Freemindtronic in Andorra that allow you to create HSM (Hardware Security Module) on any device, without a server or database, to encrypt any type of data. DataShielder HSM solutions also include EviSign technology, which enables advanced electronic signing of documents. DataShielder HSM solutions are notably available in Defense versions, which offer a high level of protection for civil and/or military applications.
Assessing Attack Techniques: Ease of Execution and Current Relevance
In our pursuit of understanding fingerprint system vulnerabilities, it is crucial to assess not only the types and forms of attacks but also their practicality and current relevance. This section provides an in-depth evaluation of each attack technique, considering factors such as the ease of execution, historical success rates, and their present-day applicability.
Attack Techniques Overview
Let’s analyze the spectrum of attack techniques, considering their potential danger, execution simplicity, historical performance, and present-day relevance.
| Attack Type |
Level of Danger |
Ease of Execution |
Historical Success |
Current Relevance |
| Residual Fingerprint Attack |
Medium |
Moderate |
Variable |
Ongoing |
| Code Injection Attack |
High |
Moderate |
Variable |
Still Relevant |
| Acoustic Analysis Attack |
Medium |
Low |
Fluctuating |
Ongoing Concerns |
| Brute Force Attack |
High |
Low |
Variable |
Contemporary |
| Replica Fingerprint Attack |
Medium |
Moderate |
Fluctuating |
Still Relevant |
| Sensor Vulnerabilities |
High |
Moderate |
Variable |
Ongoing Significance |
| BrutePrint Attack |
High |
High |
Variable |
Continues to Pose Concerns |
| Presentation Attack |
High |
Moderate |
Diverse |
Still Pertinent |
| Rapid Identification Attack |
High |
Low |
Variable |
Ongoing Relevance |
| Digital Footprint Attack |
High |
Low |
Fluctuating |
Currently Pertinent |
| Chemical Attacks |
High |
Low |
Variable |
Ongoing Relevance |
| Phishing Attack |
High |
Moderate |
Variable |
Modern Threat |
| Session Hijacking Attack |
High |
Low |
Variable |
Ongoing Relevance |
| Privilege Escalation Attack |
High |
Low |
Variable |
Remains Significant |
| Adversarial Generation Attack |
High |
Moderate |
Variable |
Still in Use |
| Acoustic Analysis Attack (Revisited) |
Medium |
Low |
Fluctuating |
Ongoing Concerns |
| Partial Print Attack |
Medium |
Low |
Variable |
Currently Relevant |
| Electronic Devices for Biometric Attacks |
High |
Moderate to High |
Variable |
Currently Relevant |
| PrintListener (Specific Acoustic Analysis Attack) |
High |
Moderate |
Emerging |
Highly Relevant |
Understanding the Evaluation:
- Level of Danger categorizes potential harm as Low, Moderate, or High.
- Ease of Execution is categorized as Low, Medium, or High.
- Historical Success highlights fluctuating effectiveness.
- Current Relevance signifies ongoing concerns in contemporary security landscapes.
By assessing these attack techniques meticulously, we can gauge their practicality, historical significance, and continued relevance.
The type of attack by electronic devices for biometric systems is very dangerous because it can allow malicious actors to access sensitive information or bypass the protections of biometric systems. Its ease of execution is moderate to high, as it requires physical access to target devices and the use of expensive or difficult-to-obtain devices. Its historical success is variable because it depends on the quality of the devices used and the security measures implemented by the biometric systems. It is currently relevant because it is used by government agencies, law enforcement or hackers to access biometric data stored on mobile phones or other devices.
Statistical Insights into Fingerprint Systems
Fingerprint systems have found wide-ranging applications, from law enforcement and border control to banking, healthcare, and education. They are equally popular among consumers who use them to unlock devices or access online services. However, questions linger regarding their reliability and security. Let’s delve into some pertinent statistics:
According to Acuity Market Intelligence, 2018 saw more than 1.5 billion smartphones equipped with fingerprint sensors, constituting 60% of the global market.
The IAFIS Annual Report of 2020 revealed that more than 1.3 billion fingerprint records were stored in national and international databases in 2019.
According to the National Institute of Standards and Technology (NIST), the average false acceptance rate of fingerprint systems in 2018 was 0.08%, marking an 86% decrease compared to 2013.
These statistics shed light on the widespread adoption of fingerprint systems and their improved accuracy over time. Nevertheless, they also underline that these systems, while valuable, are not without their imperfections and can still be susceptible to errors or manipulation.
Real-World Cases of Fingerprint System Corruption: Phone Cases
Fingerprint system corruption can also affect phone users, who rely on fingerprint sensors to unlock their devices or access online services. However, these sensors are not foolproof and can be bypassed or exploited by skilled adversaries. These attacks can result in device theft, data breaches, or other security issues.
Here are some examples of fingerprint system corruption that involve phones:
- German hacker Jan Krissler, alias Starbug, remarkably unlocked the smartphone of the German Defense Minister Ursula von der Leyen in 2014 using a high-resolution photo of her thumb taken during a press conference. He employed image processing software to enhance the photo’s quality and created a counterfeit fingerprint printed on paper.
- A terrorist attack at the Istanbul airport killed 45 people and injured more than 200 in 2016. The investigators found that the three suicide bombers used fake fingerprints to enter Turkey and avoid security checks. They copied the fingerprints of other people from stolen or forged documents.
- Researchers from Tencent Labs and Zhejiang University discovered in 2020 that they could bypass a fingerprint lock on Android smartphones using a brute force attack, that is when a large number of attempts are made to discover a password, code or any other form of security protection.
- Experts from Cisco Talos created fake fingerprints capable of fooling the sensors of smartphones, tablets and laptops as well as smart locks in 2020, but it took them a lot of effort.
- A case of identity theft was discovered in France in 2021, involving the use of fake fingerprints to obtain identity cards and driving licenses. The suspects used silicone molds to reproduce the fingerprints of real people, and then glued them on their fingers to fool the biometric sensors.
- Researchers from the University of Buffalo developed a method in 2021 to create artificial fingerprints from images of fingers. These fingerprints can fool the sensors of smartphones, but also more advanced biometric systems, such as those used by police or airports.
- A report by Kaspersky revealed in 2021 that banking apps on smartphones are vulnerable to attacks by falsified fingerprints. Attackers can use malware to intercept biometric data from users and use them to access their accounts.
These cases highlight the significant threats posed by fingerprint system corruption to phone users. Therefore, it is important to protect these systems against external and internal threats while integrating advanced technologies to enhance security and reliability.
DataShielder HSM: A Counter-Espionage Solution for Fingerprint System Security
You have learned in the previous sections that fingerprint systems are not foolproof. They can be corrupted by attacks that expose your secrets and sensitive data. To prevent malicious actors from capturing them, you need an effective and reliable encryption solution, even if your phone is compromised.
Freemindtronic, the leader in NFC HSM technologies, designed, developed, published and manufactured DataShielder HSM in Andorra. It is a range of solutions that you need. You can use either EviCore NFC HSM or EviCore HSM OpenPGP technology with DataShielder HSM. It lets you encrypt your data with segmented keys that you generate randomly yourself. The key segments are securely encrypted and stored in different locations. To access your secrets and your sensitive data encrypted in AES 256 quantum, you need to bring all segments together for authentication.
DataShielder HSM has two versions: DataShielder NFC HSM for civil and military use, and DataShielder NFC HSM Defense for sovereign use. DataShielder NFC HSM Defense integrates two technologies: EviCore NFC HSM and EviCore HSM OpenPGP. They allow you to create a hardware security module (HSM) without contact on any medium, without server, without database, totally anonymous, untraceable and undetectable.
DataShielder HSM is a user-friendly and compatible solution with all types of phone, with or without NFC, Android or Apple. It can be used for various purposes, such as securing messaging services, encrypting files or emails, signing documents or transactions, or generating robust passwords.
DataShielder HSM is a counter-espionage solution that enhances the security of fingerprint systems. It protects your data and secrets from unauthorized access, even if your fingerprint is compromised.
Current Trends and Developments in Fingerprint Biometrics
Fingerprint biometrics is a constantly evolving field. It seeks to improve the performance, reliability and security of existing systems. But it also develops new technologies and applications. Here are some current or expected trends and developments in this field.
- Multimodality: it consists of combining several biometric modalities (fingerprint, face, iris, voice, etc.) to increase the level of security and reduce the risks of error or fraud. For example, some smartphones already offer authentication by fingerprint and facial recognition.
- Contactless biometrics: it consists of capturing fingerprints without the need to touch a sensor. This technique avoids the problems related to the quality or contamination of fingerprints. And it improves the comfort and hygiene of users. For example, some airports already use contactless scanners to verify the identity of travelers.
- Behavioral biometrics: it consists of analyzing the behavior of users when they interact with a biometric system. For instance, the way they place their finger on the sensor or the pressure they exert. This technique adds a dynamic factor to identification. And it detects attempts of impersonation or coercion. For example, some banking systems already use behavioral biometrics to reinforce the security of transactions.
Standards and Regulations for Fingerprint Systems
The use of fingerprint systems is subject to standards and regulations. They aim to ensure the quality, compatibility and security of biometric data. These standards and regulations can be established by international, national or sectoral organizations. Here are some examples of standards and regulations applicable to fingerprint systems.
- The ISO/IEC 19794-2 standard: it defines the format of fingerprint data. It allows to store, exchange and compare fingerprints between different biometric systems. It specifies the technical characteristics, parameters and procedures to be respected to ensure the interoperability of systems.
- The (EU) 2019/1157 regulation: it concerns the strengthening of the security of identity cards and residence permits issued to citizens of the European Union and their relatives. It provides for the mandatory introduction of two fingerprints in a digital medium integrated into the card. It aims to prevent document fraud and identity theft.
- The Data Protection Act: it regulates the collection, processing and storage of personal data, including biometric data. It imposes on data controllers to respect the principles of lawfulness, fairness, proportionality, security and limited duration of data. It guarantees to data subjects a right of access, rectification and opposition to their data.
Examples of Good Practices for Fingerprint System Security
Fingerprint systems offer a convenient and effective way to authenticate people. But they are not without risks. It is important to adopt good practices to strengthen the security of fingerprint systems and protect the rights and freedoms of users. Here are some examples of good practices to follow by end users, businesses and governments.
- For end users: it is recommended not to disclose their fingerprints to third parties, not to use the same finger for different biometric systems, and to check regularly the state of their fingerprints (cuts, burns, etc.) that may affect recognition. It is also advisable to combine fingerprint authentication with another factor, such as a password or a PIN or other trust criteria that allows the patented segmented key authentication technology developed by Freemindtronic in Andorra.
- For businesses: it is necessary to comply with the applicable regulation on the protection of personal data, and to inform employees or customers about the use and purposes of fingerprint systems. It is also essential to secure biometric data against theft, loss or corruption, by using encryption, pseudonymization or anonymization techniques.
- For governments: it is essential to define a clear and consistent legal framework on the use of fingerprint systems, taking into account ethical principles, fundamental rights and national security needs. It is also important to promote international cooperation and information exchange between competent authorities, in compliance with existing standards and conventions.
Responses to Attacks
Fingerprint systems can be victims of attacks aimed at bypassing or compromising their operation. These attacks can have serious consequences on the security of people, property or information. It is essential to know how to react in case of successful attack against a fingerprint system. Here are some recommendations to follow in case of incident.
- Detecting the attack: it consists of identifying the type, origin and extent of the attack, using monitoring, auditing or forensic analysis tools. It is also necessary to assess the potential or actual impact of the attack on the security of the system and users.
- Containing the attack: it consists of isolating the affected system or the source of the attack, by cutting off network access, disabling the biometric sensor or blocking the user account. It is also necessary to preserve any evidence that may facilitate investigation.
- Notifying the attack: it consists of informing competent authorities, partners or users concerned by the attack, in compliance with legal and contractual obligations. It is also necessary to communicate on the nature, causes and consequences of the attack, as well as on the measures taken to remedy it.
- Repairing the attack: it consists of restoring the normal functioning of the fingerprint system, by eliminating the traces of the attack, resetting the settings or replacing the damaged components. It is also necessary to revoke or renew the compromised biometric data, and verify the integrity and security of the system.
- Preventing the attack: it consists of strengthening the security of the fingerprint system, by applying updates, correcting vulnerabilities or adding layers of protection. It is also necessary to train and raise awareness among users about good practices and risks related to fingerprint systems.
Next Steps for Fingerprint Biometrics Industry
Fingerprint biometrics is a booming field, which offers many opportunities and challenges for industry, society and security. Here are some avenues for reflection on the next steps for this field.
- Research and development: it consists of continuing efforts to improve the performance, reliability and security of fingerprint systems, but also to explore new applications and technologies. For example, some researchers are working on artificial fingerprints generated by artificial intelligence, which could be used to protect or test biometric systems.
- Future investments: it consists of supporting the development and deployment of fingerprint systems, by mobilizing financial, human and material resources. For example, according to a market study, the global market for fingerprint systems is expected to reach 8.5 billion dollars in 2025, with an average annual growth rate of 15.66%.
- Expected innovations: it consists of anticipating the needs and expectations of users, customers and regulators, by offering innovative and adapted solutions. For example, some actors in the sector envisage creating fingerprint systems integrated into human skin, which could offer permanent and inviolable identification.
Conclusion
Fingerprint systems are a convenient and fast way to authenticate users, based on their unique fingerprint patterns. They have many applications in device protection and online service access. However, these systems are not immune to attacks by skilled adversaries, who can manipulate and exploit them. These attacks can lead to unauthorized access, data breaches, and other security issues.
To prevent these threats, users need to be vigilant and enhance security with additional factors, such as PINs, passwords, or patterns. Moreover, regular system updates are crucial to fix emerging vulnerabilities.
Fingerprint systems are still a valuable and common form of authentication. But users must understand their weaknesses and take steps to strengthen system integrity and data protection. One of the possible steps is to use DataShielder HSM solutions, developed by Freemindtronic in Andorra. These solutions allow creating HSM (Hardware Security Module) on any device, without server or database, to encrypt and sign any data. DataShielder HSM solutions also include EviSign technology, which allows electronically signing documents with a legally recognized value. DataShielder HSM solutions are available in different versions, including Defense versions, which offer a high level of protection for civil and military applications.