2024, Cyberculture, Digital Security
Russian Cyberattack Microsoft: An Unprecedented Threat
Russian cyberattack on Microsoft by Midnight Blizzard (APT29) highlights the strategic risks to digital sovereignty. Discover how the group exploited password spraying, malicious OAuth applications, and legacy exposure — and the sovereign countermeasures offered by DataShielder and PassCypher.
Executive Summary — Midnight Blizzard (APT29) vs Microsoft
⚡ Objective
Understand how Midnight Blizzard (aka APT29, Cozy Bear) leveraged password spraying, malicious OAuth apps, and legacy exposure to access Microsoft’s internal email and escalate risks across tenants — and how sovereign HSM controls would have contained impact.
💥 Scope
Microsoft corporate mailboxes, executive communications, and internal collaboration workflows; spillover risk to customers and partners via token reuse and app-consent abuse.
🔑 Doctrine
APT29 favors low-noise, cloud-adjacent persistence without obvious malware. Defenders must harden identity (conditional access), monitor OAuth consent creation, rate-limit auth anomalies, and treat encrypted-egress analytics as first-class telemetry.
🌍 Strategic differentiator
Unlike cloud-only defenses, DataShielder & PassCypher adopt a zero cloud, zero disk, zero DOM posture with segmented-key HSM custody (NFC/PGP). Result ⮞ encrypted content remains unreadable even under mailbox compromise; credentials/OTP remain offline and non-replayable.
Technical Note
Reading time (summary): ≈ 3 minutes
Reading time (full): ≈ 15 minutes
Level: Cyberculture / Digital Security
Posture: Identity-first hardening, sovereign encryption (HSM)
Section: Digital Security
Language: FR · EN · CAT · ES
Editorial type: Chronicle
About the author: Jacques Gascuel — Inventor of Freemindtronic®, expert in sovereign HSM architectures, segmented keys (NFC/PGP), and offline, resilient communications.
TL;DR —
Midnight Blizzard (APT29) combined password spraying with malicious OAuth to access Microsoft internal mail. Even with rapid containment (SFI), token-based lateralization and app-consent persistence raised downstream risk. DataShielder keeps content end-to-end encrypted with volatile-memory decryption only; PassCypher stores credentials/OTP offline in HSM, defeating replay and loginless phishing sequences.
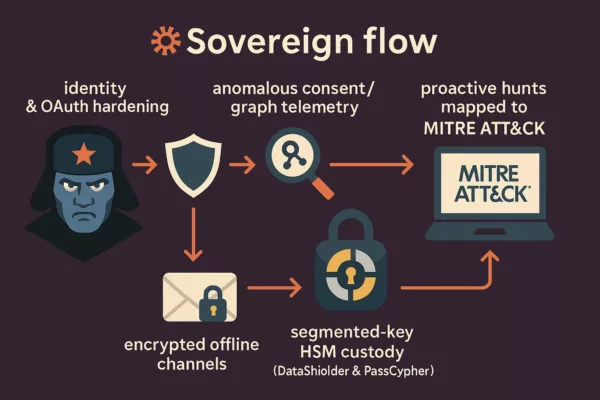
- Executive Summary — Midnight Blizzard vs Microsoft
- Microsoft Admits Russian Cyberattack Was Worse Than Expected
- Background & Technical Details
- Immediate Response from Microsoft
- Impact of Compromised Emails
- Statistical Consequences of the Cyberattack
- Ongoing escalation & data reuse
- October 2024 RDP spear-phishing campaign
- Midnight Blizzard Threat Timeline (HC3)
- Advanced Encryption & Sovereign HSM Solutions
- Global Reactions & Security Measures
- Best Practices to Prevent Russian Cyberattacks
- Comparison with Other Cyberattacks
- Strategic Aftermath — Outlook beyond Midnight Blizzard
- Related links — Russian APT actors
- Weak Signals — Trends to watch
Microsoft Admits Russian Cyberattack Was Worse Than Expected
What changed vs. initial reports
- Discovery of legacy account exposure used as the initial foothold, then pivot to internal email.
- Evidence of token-based lateralization (OAuth consent misuse) across tenants and partners.
- Tenfold increase in password-spray attempts in the weeks that followed, expanding downstream risk.
Why it matters
Midnight Blizzard is a state-sponsored actor assessed as part of Russia’s foreign-intelligence ecosystem, historically targeting governments, NGOs, and IT/service providers in the US and Europe. The campaign underscores how cloud-adjacent identity abuse (OAuth, tokens, legacy accounts) can bypass classical malware-centric defenses and compromise digital sovereignty at scale.
Authoritative references
See Microsoft’s Secure Future Initiative (SFI), Microsoft’s incident communications on Midnight Blizzard (MSRC/On the Issues), and the U.S. CISA Emergency Directive ED-24-02 for official guidance and required mitigations.
This section is part of our in-depth coverage of the Russian Cyberattack Microsoft incident involving Midnight Blizzard.
Background & Technical Details — Russian Cyberattack Microsoft
The Russian Cyberattack Microsoft incident, orchestrated by Midnight Blizzard (APT29/Cozy Bear), revealed a sophisticated combination of password spraying at scale (CISA ED-24-02) and the abuse of malicious OAuth applications. By exploiting a legacy non-production account, attackers gained foothold into Microsoft’s corporate mailboxes, including executive and legal teams.
This operation mirrors past campaigns such as SolarWinds supply-chain compromise, but with a focus on cloud tokens and stealth persistence. The breach emphasized weaknesses in tenant isolation, consent governance, and token refresh lifecycles.
Technical analysis shows how Midnight Blizzard avoided traditional endpoint detections by staying cloud-adjacent: no heavy malware, only abused credentials and trusted OAuth flows. This approach drastically reduced IOC visibility and prolonged dwell time inside Microsoft systems.
Microsoft responded with its Secure Future Initiative (SFI), which prioritizes identity hardening, OAuth monitoring, and sovereign-aligned mitigations. Still, the attack highlights a systemic risk: when cloud identity is compromised, mailbox confidentiality collapses unless sovereign HSM solutions (DataShielder, PassCypher) are enforced.
Immediate Response from Microsoft
On January 12, 2024, Microsoft detected unauthorized access to its internal systems. The security team immediately activated a response process to investigate and mitigate the attack. Midnight Blizzard compromised a legacy non-production test account, gaining access to several internal email accounts, including those of senior executives and critical teams like cybersecurity and legal.
Impact of Compromised Emails from the Russian Cyberattack
Midnight Blizzard managed to exfiltrate internal Microsoft emails, including sensitive information shared between the company and its clients. The attackers used this information to attempt access to other systems and increased the volume of password spray attacks by tenfold in February 2024. This led to an increased risk of compromise for Microsoft’s clients.
Statistical Consequences of the Russian Cyberattack on Microsoft
- Increase in Attacks: In February 2024, the volume of password spray attacks was ten times higher than in January 2024.
- Multiple Targets: The compromised emails allowed Midnight Blizzard to target not only Microsoft but also its clients, thereby increasing the risk of compromise across various organizations.
- Access to Internal Repositories: The attackers were able to access some source code repositories and internal systems, although no customer-facing systems were compromised.
Statistical Consequences of the Russian Cyberattack on Microsoft
Analysis of the Midnight Blizzard (APT29) incident highlights the statistical footprint left on Microsoft and its ecosystem. According to CISA Emergency Directive ED-24-02, downstream exposure went far beyond initial intrusion:
- 10× increase in password-spray attacks during February 2024 compared to January, escalating brute-force telemetry.
- Multiple targets compromised: from Microsoft executive teams to strategic partners, amplifying the risk of supply-chain lateralization.
- Internal repositories accessed: some source code and mailbox content exfiltrated — while Microsoft stressed that no customer-facing systems were breached.
- Regulatory alert: U.S. federal agencies were ordered by CISA to reset credentials and secure Entra ID/Azure privileged authentication tools.
This statistical aftermath confirms the systemic risks of cloud-identity compromise: once OAuth tokens and mailbox credentials are stolen, propagation extends across tenants and partners. Without sovereign HSM custody (DataShielder & PassCypher), organizations remain exposed to credential replay and stealth exfiltration.
Ongoing Escalation & Data Reuse — Russian Cyberattack Microsoft
After the January 2024 compromise, APT29/Midnight Blizzard did not stop at Microsoft’s initial remediation. Instead, the group weaponized data already stolen to sustain access and broaden espionage reach. According to CISA alerts and Microsoft’s own Secure Future Initiative (SFI), adversaries systematically:
- Replayed OAuth tokens harvested from compromised accounts to bypass fresh credential resets.
- Exfiltrated mail archives used to craft targeted spear-phishing campaigns against partners and governments.
- Leveraged leaked correspondence to execute disinformation and hybrid-conflict narratives.
- Expanded persistence through new malicious OAuth application consents, evading traditional MFA checks.
This escalation phase illustrates that the Russian Cyberattack Microsoft was not a one-time event but an ongoing campaign with iterative exploitation. For defenders, this confirms the need for sovereign cryptographic containment: while cloud identities can be replayed, DataShielder and PassCypher ensure that exfiltrated data remains undecipherable and credentials are non-replayable due to offline segmented-key HSM custody.
October 2024 RDP Spear-Phishing Campaign — Russian Cyberattack Microsoft
.RDP files. These attachments initiated covert remote desktop sessions, bypassing traditional email security and extending persistence.On October 16, 2024, Microsoft confirmed that Midnight Blizzard actors were distributing .RDP attachments in targeted phishing campaigns. When opened, the files automatically launched remote desktop sessions to attacker-controlled infrastructure, effectively granting adversaries direct access to victim environments.
This new tactic leveraged trusted file types and signed components to evade standard email filters and sandboxing. The campaign primarily targeted government entities, NGOs, and IT providers in Europe and North America, aligning with APT29’s long-term espionage doctrine.
According to CISA alerts and ENISA threat bulletins, the malicious RDP sessions allowed attackers to:
- Establish persistent remote control bypassing traditional login prompts.
- Harvest additional credentials through Windows authentication requests inside the RDP session.
- Deploy secondary payloads undetected by endpoint monitoring, as the activity was masked as legitimate remote access.
For defenders, this October 2024 escalation illustrates how Russian APTs adapt quickly, shifting from OAuth abuse to remote desktop weaponization. Without sovereign safeguards, even encrypted mail channels remain insufficient against file-based phishing vectors.
Here, DataShielder and PassCypher deliver layered resilience: offline decryption ensures malicious .RDP payloads cannot auto-open decrypted content, while HSM-segmented key custody prevents credential replay inside remote sessions.
Midnight Blizzard Threat Timeline (HC3) — Russian Cyberattack Microsoft
The U.S. Department of Health and Human Services Health Sector Cybersecurity Coordination Center (HC3) published a June 2024 threat profile detailing APT29’s operational history. Key stages align with the escalation observed in the Russian Cyberattack Microsoft:
- 2018–2020: Initial reliance on spear-phishing and credential harvesting, including campaigns against U.S. and European institutions.
- 2020–2021: SolarWinds supply-chain compromise, marking APT29’s ability to exploit trusted third-party software ecosystems.
- 2022–2023: Transition to cloud identity abuse, including malicious OAuth applications and stealthy persistence.
- 2024: Large-scale escalation with Microsoft corporate mailbox compromise, password spraying at scale, and token replay — culminating in October spear-phishing via
.RDPfiles.
According to CISA and ENISA, APT29 demonstrates a doctrine of hybrid conflict cyber-espionage: combining stealth persistence, identity abuse, and information operations. This timeline confirms the progressive escalation model of Midnight Blizzard campaigns.
Defensive takeaways: only sovereign HSM architectures (e.g., DataShielder, PassCypher) can neutralize token replay and ensure that exfiltrated data remains encrypted and non-exploitable across campaign phases.
Advanced Encryption and Security Solutions
To resist state-grade threats, organizations should enforce robust encryption with sovereign key custody. Technologies like
DataShielder NFC HSM, DataShielder HSM PGP, and DataShielder Auth NFC HSM encrypt emails and attachments end-to-end while keeping decryption keys offline inside an HSM (NFC/PGP).
If Midnight Blizzard had accessed an executive mailbox protected by DataShielder, message bodies and files would have remained unreadable. Decryption occurs only in volatile memory after physical HSM presence and multi-factor checks. This neutralizes token replay and limits the blast radius of OAuth or identity abuse.
Beyond confidentiality, the sovereign design simplifies incident response: keys are never hosted in the provider’s cloud, and credentials or OTPs managed with segmented keys are not replayable across OAuth/RDP sessions.
Global Reactions and Security Measures
This attack highlights the ongoing risks posed by well-funded state actors. In response, Microsoft launched the Secure Future Initiative (SFI). This initiative aims to strengthen the security of legacy systems and improve internal processes to defend against such cyber threats. The company has also adopted a transparent approach, quickly sharing details of the attack and closely collaborating with government agencies to mitigate risks.
Microsoft’s Secure Future Initiative (SFI) aims to harden legacy infrastructure. In parallel, CISA and ENISA coordinate sectoral resilience guidance for critical operators.
Best Practices in Cybersecurity to Prevent Russian Cyberattacks
To protect against these threats, companies must adopt robust security measures. Multi-factor authentication and continuous system monitoring are crucial. Additionally, implementing regular security updates is essential. The CISA emergency directive ED 24-02 requires affected federal agencies to analyze the content of exfiltrated emails, reset compromised credentials, and secure authentication tools for privileged Azure accounts (CISA).
Beyond classical defenses, sovereign encryption and segmented HSM custody ensure that even if OAuth tokens or mailboxes are compromised, sensitive data remains cryptographically unusable.
Comparison with Other Cyberattacks
This attack is reminiscent of other major incidents, such as those against SolarWinds and Colonial Pipeline. These attacks demonstrate the evolving techniques of attackers and the importance of maintaining constant vigilance. Companies must be ready to respond quickly and communicate transparently with stakeholders to minimize damage and restore trust.
See CISA SolarWinds advisory and Colonial Pipeline cyberattack report for context.
The Sovereign Takeaway — Russian Cyberattack Microsoft
Only a sovereign HSM posture — with DataShielder and PassCypher — ensures that exfiltrated data or stolen tokens remain cryptographically unusable.
This doctrine of zero cloud, zero disk, zero DOM with segmented HSM custody is what transforms a breach into a contained incident rather than a systemic crisis. It marks the line between conventional cloud security and sovereign cryptographic resilience.
Further Reading: For extended analysis, see our chronicle on the Midnight Blizzard cyberattack against Microsoft & HPE, authored by Jacques Gascuel.
Strategic Aftermath — Outlook beyond the Russian Cyberattack Microsoft
A sovereign posture treats cloud identity as ephemeral and sensitive content as persistently encrypted under offline HSM custody.
In the wake of the Russian Cyberattack Microsoft, three shifts are non-negotiable. First, identity becomes telemetry-driven: conditional access, consent creation, and token lifecycles are continuously scored, not merely logged. Second, communications become sovereign by default: message bodies and files remain unreadable without physical HSM presence, even if mailboxes are accessed. Third, credentials and OTPs leave the cloud: segmented-key custody prevents reuse across OAuth, Graph, or RDP flows.
- Containment by design — Enforce zero cloud, zero disk, zero DOM decryption paths; treat tokens as hostile until proven otherwise.
- Operational continuity — Maintain an out-of-band sovereign channel for IR, so investigations never depend on compromised tenants.
- Partner hygiene — Require OAuth consent baselines and cross-tenant anomaly sharing; audit refresh-token lifetimes.
Practically, this outlook translates into DataShielder for end-to-end content encryption with volatile-memory decryption, and PassCypher for offline credential custody and non-replayable OTP. Together, they narrow the blast radius of future APT29-style campaigns while preserving mission continuity.
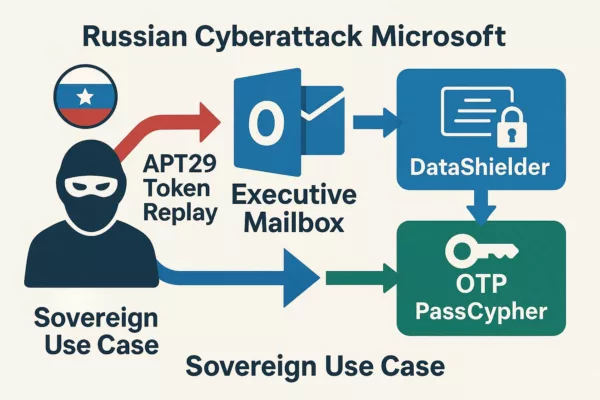
Real-world sovereign use case — Russian Cyberattack Microsoft (executive mailbox compromised)
- During the Russian Cyberattack Microsoft (Midnight Blizzard / APT29), an executive’s mailbox is accessed via token replay.
- Emails & attachments remain unreadable: content is end-to-end encrypted with DataShielder; decryption occurs only in volatile memory after NFC HSM presence.
- Credentials & OTP are never exposed: PassCypher stores them offline with segmented keys, preventing replay inside OAuth/RDP sessions.
- Operations continue seamlessly: an out-of-band sovereign channel maintains secure communications during incident response, with no cloud keys to rotate.
Related links — Russian APT actors
- APT28 — Outlook spear-phishing & NotDoor backdoor in Europe
GRU-linked APT28: Outlook zero-days, mailbox-resident malware (NotDoor), and information ops across EU & France. - APT29 — Spear-phishing in Europe: stealthy Russian espionage
SVR/Cozy Bear: stealth campaigns leveraging cloud relays and low-persistence tactics, complementary to Midnight Blizzard’s methods. - APT29 — Exploitation of app passwords
Bypassing classical credentials via OAuth/app passwords; illustrates why sovereign identity hardening is crucial. - Russian espionage hacking tools revealed
Technical inventory of Russian cyber-espionage arsenals, shedding light on APT29’s evolving toolkit. - Reputation & cyberattacks in hybrid conflicts
Strategic analysis: how Russian APT campaigns (including APT29) fuel hybrid warfare and influence operations. - APT44 — QR-code phishing & blended info-ops
Sandworm/GRU: QR-code phishing, mobile-first vectors, and hybrid information warfare converging with Russian spear-phishing doctrines.
Weak Signals — Trends to Watch Beyond the Russian Cyberattack Microsoft
These evolutions are consistent with the Russian hybrid warfare doctrine, where cyber-espionage (APT29) and influence operations converge to destabilize strategic sectors.
Looking ahead, the aftermath of the Midnight Blizzard (APT29) intrusion offers insights into future trends in Russian cyber-espionage:
- AI-augmented spear-phishing: Generative AI may increase the credibility and linguistic adaptation of phishing lures, complicating detection (ENISA reports).
- Encrypted C2 channels inside cloud apps: Expect wider abuse of collaboration platforms (Teams, SharePoint) with end-to-end encrypted exfiltration masquerading as normal traffic.
- OAuth & token lifecycle attacks: Beyond classic consent abuse, attackers may pivot to refresh token manipulation and multi-cloud federation exploits.
- Hybrid conflict synchronization: Cyber intrusions paired with influence campaigns targeting elections, energy policy, and EU institutional trust.
- Regulatory misalignment: While frameworks such as EU CRA and NIS2 strengthen defenses, uneven adoption leaves OIV/OES with exploitable gaps.
These signals reinforce the necessity of sovereign cryptographic architectures. With DataShielder and PassCypher, organizations can enforce offline key segmentation, volatile-memory decryption, and encrypted egress control, making exfiltrated data strategically useless to adversaries.

Pingback: Russian Espionage Hacking Tools Revealed - Freemindtronic