2025, Tech Fixes Security Solutions
NFC HSM SSL Cert IP: Trigger HTTPS Certificate Issuance Without DNS
Executive Summary
This method of issuing a “NFC HSM SSL Cert IP” enhances sovereign cryptographic automation.This strategic chronique unveils a sovereign method to issue HTTPS certificates without DNS, leveraging the patented PassCypher NFC HSM and DataShielder NFC HSM. These Freemindtronic devices, designed for air-gapped environments, embed full ACME commands within an encrypted Bluetooth USB keyboard emulator. As a result, the issuance of IP SSL certificates from Let’s Encrypt can be securely triggered on Linux or Windows terminals, without relying on domains or manual input. This implementation marks a significant advancement in cyber defense, DevSecOps automation, and critical infrastructure resilience.
Strategic Navigation Index
-
- Executive Summary
- Why Trigger HTTPS via NFC HSM?
- Sovereign Certificate Deployment
- ACME Command Injection
- Threat Modeling & Attack Surface Reduction
- Use Cases
- Advantages Over Conventional Certificate Deployment
- Real-World Implementation Scenario
- Keyboard Emulation Security
- Web Interface Variant
- Step-by-Step Windows 11 Tutorial
- Linux Implementation Notes
- Beyond SSL: Generalized Command Triggering
- Visual Workflow
- FAQ
Key Insights
Bluetooth Security & HID Injection Logic
Let’s Encrypt now actively provides free SSL/TLS certificates for public IP addresses, thereby eliminating any reliance on domain names. This evolution directly supports ACME automation and is valid for 6 days—making it ideal for sovereign DevOps workflows, air-gapped devices, and containerized staging setups.
Freemindtronic’s architecture reinforces this capability by introducing a critical layer of physical trust. Through the NFC HSM, each certificate issuance command becomes encrypted, deterministic, and physically validated before execution.
To secure this pathway, the integration of Bluetooth HID emulators based on InputStick, operating under AES-128 CBC, mitigates known vulnerabilities like CVE‑2023‑45866. These dongles neutralize spoofing and injection attempts that typically compromise HID interfaces.
While HID emulation minimizes exposure to keyloggers—particularly those relying on software vectors—it does not ensure universal protection. Since the command never appears on-screen or uses the clipboard, conventional surveillance tools often miss it. Still, firmware-based interception remains a realistic concern in sensitive contexts.
Another layer of protection stems from the consistent rhythm of injected keystrokes. This predictability inherently circumvents profiling methods like keystroke dynamics, which attackers use for behavioral fingerprinting.
Beyond SSL — Triggering Sovereign Automation
Most critically, this method extends well beyond HTTPS provisioning. The architecture permits any shell-level action to be securely triggered—whether toggling firewalls, initiating VPN connections, or unlocking OTP-based workflows.
Such command injection remains deterministic, reproducible, and physically scoped to authorized personnel. It aligns with zero-trust architectures and supports sovereign automation in environments where human error, remote compromise, or credential leakage must be structurally eliminated.
Why Trigger HTTPS via NFC HSM?
⮞ Summary
Triggering a NFC HSM SSL Cert IP from an NFC HSM enhances sovereignty, reduces exposure, and removes dependency on DNS infrastructure. It is especially relevant in constrained environments where trust, reproducibility, and minimal attack surface are paramount.
In conventional PKI workflows, HTTPS certificates are issued via domain-validated mechanisms. These involve online DNS challenges, public exposure of metadata, and centralized trust anchors. While suitable for general web hosting, such methods are problematic for air-gapped systems, sovereign networks, and critical infrastructures.
An NFC HSM—especially one like DataShielder or PassCypher—bypasses these limitations by embedding a pre-configured ACME command within a secure, tamper-resistant module. Upon physical NFC validation, it injects this command into a terminal using encrypted Bluetooth HID emulation, triggering immediate certificate issuance for a public IP address, without DNS resolution or manual typing.
This process ensures:
- Full autonomy: No user interaction beyond NFC scan
- Domainless provisioning: Perfect for IP-only infrastructure
- Operational secrecy: No domain names to query or monitor
- Cryptographic trust: Execution only via validated hardware
Unlike browser-integrated certificate requests, this method is scriptable, repeatable, and isolated. It supports compliance with sovereign architecture principles, where infrastructure must operate without internet reliance, telemetry, or cloud-based identity.
– Eliminate DNS metadata exposure for sensitive endpoints
– Enforce HTTPS issuance via local NFC physical validation
– Minimize human input to reduce injection risks and keystroke profiling
Sovereign Certificate Deployment
Deploying HTTPS certificates through an NFC HSM enables a sovereign infrastructure free from DNS, browser, or cloud dependencies. This method ensures deterministic and auditable certificate generation, fully compliant with air-gapped or classified operational models.This guarantees reproducible NFC HSM SSL Cert IP issuance even in air-gapped infrastructure.
Traditional HTTPS deployment relies on central authorities, DNS records, and domain validation—all of which introduce third-party dependencies and potential metadata leaks. In contrast, Freemindtronic’s architecture leverages a hardware-controlled trigger (the NFC HSM) to initiate certificate issuance via a secure command injection mechanism. This reduces the trust surface to a physical, user-held device.
The key innovation lies in the out-of-band orchestration: The ACME client resides on the target host, while the initiation command is stored encrypted on the HSM. No intermediate server, cloud API, or domain registry is needed. The device injects the issuance command via Bluetooth HID over AES-128 CBC, ensuring both authenticity and confidentiality.
Such deployments are ideal for:
- Defense or classified networks under COMSEC restrictions
- Offline DevSecOps environments with no external exposure
- Critical systems requiring deterministic, reproducible PKI actions
The process supports issuance for public IP addresses using Let’s Encrypt’s new IP SSL policy (valid 6 days). Renewal can be re-triggered via the same HSM, ensuring cryptographic continuity under operator control.
– Host the ACME client in a hardened, offline container
– Store issuance commands in sealed HSM compartments
– Trigger issuance only upon physical presence (NFC + HID)
ACME Injection for NFC HSM SSL Cert IP
The NFC HSM securely injects a complete ACME command into the terminal, automating IP-based certificate issuance without keyboard input. This mechanism merges cryptographic determinism with physical-layer control.
The NFC HSM SSL Cert IP architecture ensures every issuance is deterministic and hardware-bound. At the heart of this architecture lies a simple yet powerful mechanism: the injection of an acme.sh command into a terminal session using an emulated keyboard interface. The command itself is stored as a secure “password” inside the NFC HSM, encrypted with AES-128 CBC and transmitted via Bluetooth HID only upon NFC validation.
Typical payload format:
~/.acme.sh/acme.sh --issue --standalone -d 198.51.100.12This command initiates the certificate issuance for a specific public IP, using the standalone HTTP challenge method. The NFC HSM handles the timing and structure of input, including the final “Enter” keystroke, ensuring that no user interaction is needed once the terminal is focused and ready.
Because the device behaves as a hardware keyboard, there is no software stack to compromise, and no plaintext command ever resides on disk or in clipboard memory. This prevents logging, injection, or interception from conventional malware or keyloggers.
The injected command can also include renewal or deployment flags, depending on operational needs:
~/.acme.sh/acme.sh --renew -d 198.51.100.12 --deploy-hook "systemctl reload nginx"This physical injection model aligns with sovereign DevSecOps practices: zero trust, physical validation, no telemetry.
– Avoid clipboard usage and on-screen input
– Limit exposure by using ephemeral ACME sessions
– Control terminal focus strictly to prevent accidental command leaks
ACME Command Injection
The NFC HSM securely injects a complete ACME command into the terminal, automating IP-based certificate issuance without keyboard input. This mechanism merges cryptographic determinism with physical-layer control.
At the heart of this architecture lies a simple yet powerful mechanism: the injection of an acme.sh command into a terminal session using an emulated keyboard interface. The command itself is stored as a secure “password” inside the NFC HSM, encrypted with AES-128 CBC and transmitted via Bluetooth HID only upon NFC validation.
Typical payload format:
~/.acme.sh/acme.sh --issue --standalone -d 198.51.100.12This command initiates the certificate issuance for a specific public IP, using the standalone HTTP challenge method. The NFC HSM handles the timing and structure of input, including the final “Enter” keystroke, ensuring that no user interaction is needed once the terminal is focused and ready.
Because the device behaves as a hardware keyboard, there is no software stack to compromise, and no plaintext command ever resides on disk or in clipboard memory. This prevents logging, injection, or interception from conventional malware or keyloggers.
The injected command can also include renewal or deployment flags, depending on operational needs:
~/.acme.sh/acme.sh --renew -d 198.51.100.12 --deploy-hook "systemctl reload nginx"This physical injection model aligns with sovereign DevSecOps practices: zero trust, physical validation, no telemetry.
– Avoid clipboard usage and on-screen input
– Limit exposure by using ephemeral ACME sessions
– Control terminal focus strictly to prevent accidental command leaks
Threat Modeling & Attack Surface Reduction
Injecting HTTPS issuance commands via NFC HSM significantly reduces exposure to credential theft, remote compromise, and biometric profiling. However, physical layer risks, firmware compromise, and misconfigured terminals remain key vectors.
In a typical PKI deployment, multiple layers expose the certificate lifecycle to threats: DNS hijacking, clipboard interception, keystroke logging, and man-in-the-browser attacks. By shifting the trigger mechanism to a sealed NFC HSM, most software vectors are eliminated.
Remaining risks include:
- Terminal pre-infection: If malware is already resident, it may capture the injected command output or intercept post-issuance files.
- HID spoofing attacks: Emulated keyboards can be impersonated unless verified through MAC binding or secure pairing protocols.
- Compromised firmware: If the InputStick or equivalent dongle is tampered with, it could alter the command or inject additional payloads.
Nonetheless, the attack surface is drastically narrowed by limiting interaction to a physical device performing a single-purpose task with no writable memory exposed to the host.
Further hardening strategies include:
- USB port control and filtering (e.g.,
usbguard) - Privilege isolation of ACME clients
- Separation between issuance terminal and production services
This model aligns with threat-aware infrastructure design, promoting predictability, reproducibility, and low-residue command execution.
– Bind InputStick to a single MAC address with secure pairing
– Use read-only terminals or ephemeral VMs for injection
– Monitor for unexpected keystroke patterns or USB device signatures
Use Cases
NFC-triggered HTTPS certificate deployment unlocks secure automation in domains where DNS is unavailable, interaction must be minimized, and reproducibility is critical. From DevSecOps to defense-grade SCADA, this architecture serves environments requiring absolute trust control.
The following scenarios illustrate how the NFC HSM method enables trusted and repeatable HTTPS certificate issuance workflows in constrained, regulated, or sensitive networks:
- Offline DevSecOps Pipelines
Teams managing infrastructure-as-code or staging environments without internet access can preconfigure NFC HSM SSL Cert IP workflows for staging environments to issue IP-based certificates, ensuring that test environments are reproducible and consistent without any external dependency. - SCADA / OT Infrastructure
Industrial systems often avoid DNS integration for security reasons. Using an NFC HSM allows localized HTTPS activation without exposing endpoints to domain-based resolution or remote management layers. - IoT / Embedded Systems
Devices in disconnected or partially isolated networks can still receive TLS credentials via NFC-triggered issuance, avoiding factory default certs or static keys, and ensuring field-level provisioning control. - Field Operations in Defense or Law Enforcement
Operators in sovereign or tactical contexts can generate valid HTTPS credentials on-site, without contacting centralized authorities, by physically carrying a validated HSM token with embedded commands. - Certificate Renewal for Local Services
NFC HSMs can be configured to perform periodic injections of--renewcommands, allowing HTTPS continuity in local-only networks or maintenance windows without login credentials.
– Preload HSMs for field deployments without backend dependency
– Enforce HTTPS consistency in LANs without internal CA
– Avoid DNS logging and upstream certificate transparency exposure
Advantages Over Conventional Certificate Deployment
Triggering HTTPS certificates from an NFC HSM provides deterministic provisioning, DNS independence, and air-gapped compatibility—surpassing traditional PKI methods in sovereign, offline, or security-hardened contexts.
Unlike conventional HTTPS deployment—which relies on online DNS validation, interactive browser workflows, or centralized CA integrations—this method centers on physical validation and cryptographic command injection. The result is a sovereign architecture that avoids metadata leaks, limits dependencies, and enhances reproducibility.
Key comparative advantages:
- DNS-free issuance: Certificates can be requested directly for public IP addresses, eliminating exposure to DNS hijacking or telemetry.
- Zero manual typing: The NFC HSM delivers a pre-signed command via Bluetooth HID, reducing human error and eliminating clipboard use.
- Air-gapped operation: No need for internet connectivity during issuance—ideal for SCADA, OT, or classified zones.
- Cross-platform support: Works natively on Linux and Windows terminals with terminal focus, including GUI-less shells.
- Offline reproducibility: The same NFC HSM token can trigger identical issuance workflows across distinct devices or deployments.
– Avoid third-party telemetry via direct IP-based ACME workflows
– Use physical validation to remove keyboard input from trust equation
– Standardize issuance using sealed, immutable NFC HSM command blocks
Market PKI Models vs. NFC HSM SSL Cert IP
⮞ Summary
Commercial PKI models rely on centralized trust architectures, whereas Freemindtronic’s NFC HSM SSL Cert IP model decentralizes certificate control and aligns with offline sovereignty requirements.
Freemindtronic’s NFC HSM SSL Cert IP model contrasts with:
- AWS Certificate Manager (ACM) — automated domain validation and SSL provisioning for AWS workloads, but entirely cloud-tethered.
- Google CA Service — enterprise-focused PKI with global root distribution, but no local control over key injection.
- Entrust or GlobalSign PKIaaS — high-assurance certificate lifecycle services, but designed for regulated environments with consistent network access.
In contrast, the NFC HSM SSL Cert IP model is physically anchored, deterministic, and offline-capable, making it uniquely suited for air-gapped, sovereign, or classified environments where no telemetry or external PKI is permitted.
✓ Sovereign Countermeasures
- Replace centralized CA trust chains with localized issuance
- Avoid reliance on global DNS, root stores, and telemetry
- Use NFC-triggered hardware validation to control all issuance events
| Criteria | Conventional PKI (Cloud HSM) | NFC HSM SSL Cert IP (Freemindtronic) |
|---|---|---|
| Key Storage | HSMs in cloud datacenters (e.g., FIPS-certified Luna HSMs) | On-chip secure memory, per user device |
| Certificate Trigger | API-based orchestration from CA infrastructure | Physical NFC scan and Bluetooth HID injection |
| Metadata Exposure | Public domain names, DNS logs, CA telemetry | None — issues IP certs offline without DNS |
| Operational Model | Centralized, requires internet connectivity | Decentralized, works in air-gapped contexts |
| Sovereign Control | Controlled by Certificate Authority | Fully under user and device holder control |
Strategic Differentiators — NFC HSM SSL Cert IP vs. Cloud HSM
Compared to conventional cloud-based HSM solutions, Freemindtronic’s NFC HSM SSL Cert IP model offers a fully offline, sovereign, and metadata-free method for issuing HTTPS certificates—making it unmatched in security, autonomy, and scalability.
| Criteria | NFC HSM SSL Cert IP (Freemindtronic) | Cloud HSM (AWS, Google, etc.) |
|---|---|---|
| Offline Capability | Fully functional in air-gapped environments | Impossible — internet connection mandatory |
| Sovereign Control | Full user-side control, no third-party reliance | CA or cloud provider retains authority |
| DNS Independence | Let’s Encrypt IP SSL triggered via NFC | Domain and DNS validation mandatory |
| Command Storage | Encrypted in EEPROM with AES-256 CBC | Cleartext in orchestration scripts or APIs |
| Bluetooth HID Security | AES-128 CBC (BLE), no software installation needed | Not applicable, not physically triggered |
| Telemetry Exposure | Zero telemetry, no cloud or DNS persistence | High — logs, DNS traces, CA activity trails |
| Scalability & Distribution | Up to 100 secure labels per NFC HSM | Requires scripts, APIs, and cloud orchestration |
The NFC HSM SSL Cert IP architecture is ideal for DevSecOps, critical infrastructure, IoT, and tactical IT deployments requiring deterministic control over certificate issuance—with no metadata footprint and no internet trust anchors.
All of these sovereign capabilities are natively included in both DataShielder NFC HSM and PassCypher NFC HSM. In addition to secure NFC-triggered SSL certificate issuance via Bluetooth HID, both devices embed advanced functionalities—offline password management, AES-256 CBC encrypted EEPROM, and air-gapped command injection—at no additional cost, unlike comparable single-feature commercial offerings.
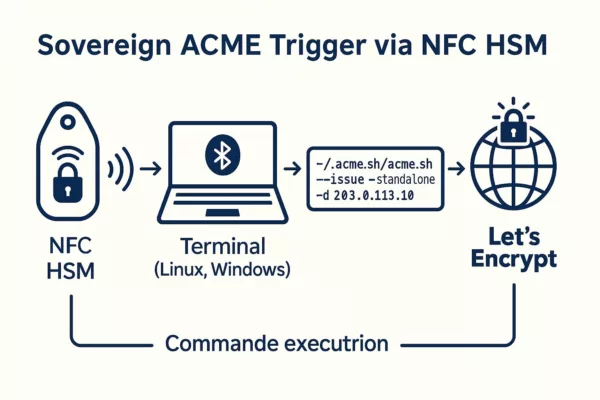
Real-World Implementation Scenario
This scenario illustrates how a DevSecOps team can deploy HTTPS certificates offline, without domain names or keyboard input, using a single NFC HSM device. The workflow minimizes risk while ensuring cryptographic reproducibility across multiple systems.
A sovereign DevSecOps team maintains an internal staging infrastructure composed of multiple servers, each accessible via public IP, but with no domain name assigned. To provision secure HTTPS endpoints, they adopt a physical key approach using a DataShielder NFC HSM.
Each operator receives a token preconfigured with a validated ACME command such as:
~/.acme.sh/acme.sh --issue --standalone -d 203.0.113.10During server provisioning, the operator focuses a terminal session on the target system and activates the NFC HSM over Bluetooth. The secure command is injected in real time via HID emulation, initiating HTTPS certificate issuance locally, without relying on DNS or typing.
The process results in:
- No secret stored on disk
- No manual interaction beyond physical validation
- No DNS contact or metadata exposure
Renewals follow the same offline procedure. Each NFC HSM can be reused cyclically, enforcing consistent operational workflows and reducing the attack surface associated with digital credentials or shared provisioning scripts.
– Delegate issuance authority to hardware tokens only
– Avoid persistent credentials or renewal daemons
– Rotate HSMs per site or per operator to enforce physical trust boundaries
Keyboard Emulation Security
Secure NFC HSM SSL Cert IP provisioning relies on keyboard emulation via NFC-triggered HID injection, delivering encrypted commands without user interaction. While resilient against software-based keyloggers, this method still depends on dongle integrity, terminal focus, and strict physical access control.
The Freemindtronic architecture relies on Bluetooth HID keyboard emulation to input a pre-defined ACME command into a terminal. This approach avoids clipboard use, bypasses browser interfaces, and limits the attack surface to physical vectors. Communication is secured using AES-128 CBC encryption, typically via InputStick-compatible dongles.
Advantages:
- Bypasses traditional keystroke logging malware
- Works in both GUI and CLI-only contexts
- Evades behavioral profiling (e.g., typing speed, cadence)
- Injects full command strings deterministically
Limitations:
- Relies on terminal focus: any background app may intercept keystrokes if hijacked
- Cannot distinguish user intent—no dynamic validation layer
- Firmware-level compromise of the HID dongle remains a plausible threat
Despite these considerations, NFC-triggered HID input remains more secure than local typing or shell-based provisioning—especially in air-gapped networks. It minimizes cognitive load and human error while ensuring consistent syntax execution.
– Validate terminal window state before injection.
– Secure HID dongles using hardware-based pairing and trusted device filtering mechanisms.
– Physically isolate trusted input endpoints from internet-connected interfaces.
Web Interface Variant
In controlled environments requiring GUI validation, the NFC HSM can inject commands into a web interface with an autofocused field. This variant enables HTTPS provisioning through privileged backend scripts, maintaining traceability and physical-layer initiation.
While terminal-based workflows are ideal for sovereign and CLI-dominant deployments, some regulatory or enterprise environments require a graphical layer for auditability, accessibility, or operator ergonomics. To meet this need, Freemindtronic supports an alternative mode: NFC-triggered command injection into a local HTTPS web form.
This method involves a locally hosted, air-gapped web interface with an <input autofocus> element. When the NFC HSM is scanned, its command is injected directly into this field via the Bluetooth HID emulator. The browser captures the string and relays it to a local backend daemon (e.g., Python Flask, Node.js) that executes the ACME command securely.
Workflow highlights:
- No need for system-level terminal access
- Improves auditability and UX in regulated environments
- Allows integration with role-based web dashboards
This variant preserves the sovereign principle: no data leaves the machine, and execution still requires physical validation via NFC. It also opens the door to multistep approval flows, graphical logs, or on-screen HSM verification feedback.
– Host the web interface locally on loopback or hardened LAN
– Prevent remote form submission or cross-site injection
– Validate command syntax on server side before execution
Step-by-Step Windows 11 Tutorial
⮞ Summary
This Windows 11 sequence explains how to trigger a NFC HSM SSL Cert IP securely using a Bluetooth keyboard emulator. It ensures deterministic certificate injection in sovereign infrastructures without any DNS dependency.

Scan this QR code with the Freemindtronic NFC HSM app (Android) to auto-generate a secure encrypted container. Label: LEIP25 | Payload: ~/.acme.sh/acme.sh --issue --standalone -d 203.0.113.10
- Install Git for Windows: Ensure Git Bash is available. Download from git-scm.com.
- Install MSYS2: Download and install from msys2.org. Open the MSYS terminal and update it with:
pacman -Syu - Install Socat:
pacman -S socat
Verify withsocat -V - Install acme.sh:
curl https://get.acme.sh | sh
Check with~/.acme.sh/acme.sh --help - Create a secure NFC HSM container: Set a 6-character label (e.g., LEIP25), leave the login field empty, and insert the full ACME command in the password field (≤55 ASCII characters). This forms a secure 61-byte encrypted memory block.
- Command to store:
~/.acme.sh/acme.sh --issue --standalone -d 203.0.113.10 - Trigger via NFC HSM: Enable Bluetooth HID emulation, plug the InputStick, and scan your NFC HSM. It injects the command, initiating the NFC HSM SSL Cert IP issuance process autonomously.
~/.acme.sh/acme.sh --register-account -m your@email.comℹ NFC Container Tip — You can automatically generate this QR code using the PassCypher HSM PGP extension, specifically the Evipass module. A small icon appears next to the password field—tap it to create a secure, scannable QR code without typing.However, for high-assurance environments, Freemindtronic strongly recommends entering the payload manually via the mobile keyboard. This strategy mitigates risks posed by hardware-based keyloggers and enhances end-to-end trust in the container provisioning process.
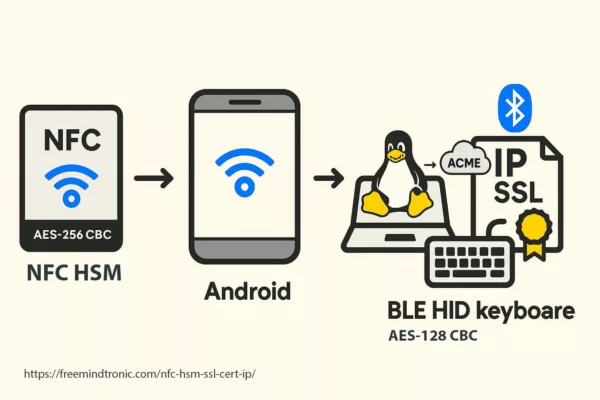
Linux Implementation Notes
⮞ Summary
Although not yet validated under Linux, this sovereign method for domainless HTTPS certificate issuance is inherently compatible with Unix-based systems. Thanks to standard CLI tools and terminal-centric workflows, its adaptation requires minimal adjustments.
The core architecture of this NFC-triggered SSL certificate method is platform-agnostic. It is built on command-line principles, which are foundational in Linux distributions. Tools such as socat and acme.sh are widely available through most package managers, enabling seamless porting.
Bluetooth HID support is also accessible under Linux, via bluez and hidraw interfaces. Furthermore, USB HID emulation through InputStick or compatible AES-128-CBC Bluetooth dongles can be managed using udev rules or manually mounted as trusted devices in headless environments.
Freemindtronic anticipates a CLI-only variant—entirely graphical-interface free—especially valuable in minimal server builds or embedded systems. This reinforces its utility in sovereign deployments and isolated networks.
⚠ Privileged access (root/sudo) will often be required for port binding (443), USB device configuration, and real-time command injection via socat or ACME clients. This underscores the importance of trusted administrative control in production systems.
Although no full test has been completed under native Linux environments as of this writing, technical compatibility is ensured by the universality of the tools involved. From a cyber-sovereignty standpoint, Linux remains a natural host for this methodology—offering deterministic, reproducible certificate issuance workflows without DNS reliance.
✓ Sovereign Countermeasures
– Bind certificate issuance to air-gapped Linux environments
– Use encrypted Bluetooth HID with physical validation
– Automate renewal via preloaded CLI command sets stored in the NFC HSM
– Trend: Expansion of IP-only HTTPS services bypassing DNS exposure
– Pattern: Rise in physical-layer triggers (NFC, QR, USB HID) for digital workflows
– Vector: Exploitation of unattended terminals via rogue HID emulation devices
– Regulatory gap: Absence of standards for command-triggered cryptographic operations without interactive validation
– Operational drift: Shadow issuance procedures escaping central IT visibility in DevSecOps pipelines
Beyond SSL: Generalized Command Triggering
The NFC HSM method is not limited to HTTPS certificate issuance. Its architecture supports secure, offline triggering of any shell-level command—making it a versatile sovereign automation tool for sensitive or disconnected infrastructures.
While originally designed for issuing IP-based SSL certificates via acme.sh, the NFC HSM trigger mechanism is fundamentally command-agnostic. Any shell instruction can be stored in the encrypted memory block and injected securely into a terminal or web input form, provided it respects length and syntax constraints.
Generalized sovereign use cases:
- VPN toggles — trigger
openvpnorwg-quickcommands in air-gapped environments - Firewall configuration — inject
iptablesorufwrules for dynamic security postures - System unlocks — initiate session-specific passwordless login scripts on hardened devices
- Credential rotation — execute PGP key rotation or 2FA OTP sync triggers without exposing tokens
- Audit commands — launch
sha256sum,journalctl, or integrity checkers during physical inspection
This flexibility transforms the NFC HSM into a **sovereign hardware trigger for trusted automation**, particularly in high-assurance zones. Combined with contextual awareness (e.g. operator role, physical presence, device pairing), the method enables deterministic, reproducible and minimal-risk operations.
– Restrict accepted commands to a known safe set on receiving systems
– Use NFC validation only in controlled physical perimeters
– Pair each command with logging or cryptographic attestation to ensure accountability
Visual Workflow
This visual sequence illustrates the complete offline workflow of sovereign certificate issuance triggered by an NFC HSM device, from physical validation to HTTPS activation on a target system.
Understanding the interaction flow between hardware, host OS, and the ACME client is crucial to ensure deterministic outcomes and reproducible deployment in sovereign infrastructures.
The sequence includes:
- NFC validation of the operator’s credential (physical control)
- Bluetooth pairing and HID readiness handshake
- Command injection to the focused shell or input field
- ACME client execution with preconfigured flags
- Key + CSR generation by the ACME engine
- HTTP challenge response via localhost (port 80/443)
- Retrieval of IP SSL cert and optional post-processing
This architecture supports both CLI and GUI variants, and maintains air-gapped integrity by ensuring no secret or domain is ever transmitted or stored online.
While this Chronicle focused on triggering HTTPS certificate issuance via NFC HSM devices in IP-only environments, several adjacent topics remain open for deeper exploration:
- Zero-trust orchestration using chained HSM devices
- Integration with sovereign enclaves and TPM attestation models
- Secure destruction or rotation of command blocks after single use
- Long-term auditability in decentralized PKI contexts
- Legal implications of offline crypto orchestration under international law
These topics will be addressed in future sovereign chronicles.
FAQ
This section clarifies operational and technical concerns about triggering HTTPS certificate issuance without DNS using sovereign NFC HSM devices such as PassCypher or DataShielder.
➤ Can you alter the ACME command stored inside the NFC HSM?
No, you cannot. Once the ACME command is encrypted and securely embedded in the NFC HSM’s sealed memory, it becomes immutable. Modifying it requires complete erasure and full reinitialization. Therefore, this approach ensures deterministic execution and robust tamper resistance.
➤ Does the AES-128 CBC Bluetooth HID channel resist replay attacks?
Yes, it does. Each communication session encrypts and synchronizes independently, using AES-128 CBC. The HSM transmits no data unless the NFC validation occurs again. Furthermore, the HID dongle enforces Bluetooth pairing, and each session expires automatically—greatly minimizing the window for replay exploitation.
➤ What happens if the terminal window lacks focus during injection?
In that case, the injected command could land in an unintended application or background process. To mitigate this, Freemindtronic strongly recommends sandboxed launchers or explicit terminal focus validation. These measures guarantee command redirection doesn’t compromise the system.
➤ Is Linux inherently more secure than Windows for sovereign NFC-triggered issuance?
In most sovereign cybersecurity architectures, yes. Linux offers greater auditability, native CLI environments, and fewer proprietary dependencies. That said, when properly hardened, both Linux and Windows provide comparable integrity for NFC HSM-based HTTPS provisioning.
➤ Can this method operate inside virtual machines, containers, or cloud platforms?
Absolutely. As long as the virtual environment presents a HID-compatible interface and supports direct terminal focus, the NFC HSM injection works seamlessly. This includes ephemeral VMs, containerized services, and CI/CD agents configured with sovereign command workflows.