Executive Summary
Strategic Navigation Index
- Executive Summary
- EviKeyboard BLE Overview
- InputStick Protocol Implementation
- Zero Trust Real-Time Transfer
- Zero-Copy Injection Mechanism
- Sovereign Integration with NFC HSM
- Technical Datasheet
- Energy Efficiency & Runtime Design
- Secure Typing Experience
- Real-World Use Cases with EviKeyboard BLE
- Advanced Use Cases
- Regulatory & Standards Alignment
- Related Sovereign Links
- EviPass NFC HSM Integration
- InputStick BLE Integration Strategy
- Security by Design
- Secure Pre-boot or Login Unlock for BitLocker and TPM 2.0 Drives
- Further Key Cyber Safety & Security Use Cases
- Industrial Compliance Use Cases
- Secure HID Comparison Table
- Multi-HSM Orchestration
- Unalterable Flow Integrity
- Beyond This Chronicle
- Technical FAQ
Key insights
- Zero-copy Bluetooth keyboard injection from NFC HSM
- Zero storage, AES-128 encryption, 10m BLE range
- Integration with sovereign air-gapped operations
- Hidden HID mode for maximum discretion and zero persistence
- Offline operation without drivers or host installation
- Secure ephemeral injection for critical infrastructure
- Native support for NFC HSM families like PassCypher and DataShielder
- Support for >30 HID keyboard layouts including FR, EN, DE, RU, etc.
Strategic Positioning in the Global Market
EviKeyboard BLE distinctly offers a sovereign, air-gapped, and non-persistent hardware input injection solution, thereby filling critical security gaps that traditional solutions simply cannot address.
Fundamentally, EviKeyboard BLE does not position itself as a mere password manager or a generic security key. Instead, it represents a cutting-edge technology specifically engineered for environments demanding the utmost in security, sovereignty, and isolation. Crucially, EviKeyboard BLE fills a vital void in the global market by providing a distinct method for injecting data and commands:
- Completely Non-Persistent: Importantly, secrets never reside on the phone, dongle, or host device. Consequently, this guarantees “zero-copy injection” and robust protection against data leaks.
- Native Air-Gap Operations: Furthermore, EviKeyboard BLE functions entirely offline, without any network or cloud dependency. As a result, it stands as an ideal solution for critical infrastructure and isolated systems.
- Data Sovereignty: Moreover, secrets reside exclusively within the physical NFC HSM module, remaining under user control without involving any third-party intermediaries.
- Universal HID Compatibility: Additionally, this Bluetooth Keyboard Emulator enables precise control over any USB-HID compatible system. This ranges from desktop PCs to SCADA systems, BIOS, or embedded devices, all without requiring specific drivers.
Ultimately, EviKeyboard BLE clearly stands apart from existing solutions:
- Versus Software/Cloud Password Managers: While these tools store information (even if encrypted) online or on disks, EviKeyboard BLE ensures physical and ephemeral injection. Consequently, it eliminates risks associated with software exploits, cloud breaches, or phishing. Significantly, it acts not as a management tool, but specifically as a secure injection mechanism.
- Versus Hardware Security Keys (FIDO/OTP): Although these keys offer hardware-backed security, many rely on specific protocols or host connectivity. Conversely, EviKeyboard BLE provides deterministic HID injection of any command, independent of the operating system or network, there where the OTP or FIDO solutions might face limitations.
- Versus Software HID Emulators / Remote Solutions: Inherently vulnerable to operating systems and networks, these solutions are undeniably surpassed by EviKeyboard BLE. This Bluetooth Keyboard Emulator is hardware-based, air-gapped, cryptographically fortified, and leaves no residual traces. Consequently, it stands as the secure antithesis to attacks like BadUSB.
- Versus Privileged Access Management (PAM/IAM) Solutions: Rather than a substitute, EviKeyboard BLE serves as a critical complement. It provides “last mile” security for privileged access to the most isolated systems, especially where PAM/IAM solutions typically operate over existing networks.
- Versus Proprietary Industrial Control Solutions: EviKeyboard BLE offers a standardized (HID), flexible, and highly secure input method for industrial environments (SCADA/ICS). Thus, it simplifies secure access where customized solutions might prove rigid or cryptographically less robust.
Shaping the Future of Secure Operations
Evidently, EviKeyboard BLE emerges as the unquestionable choice for organizations and sectors (including defense, energy, and critical infrastructure) that demand maximum cyber-resilience and unwavering operational sovereignty. This EviKeyboard BLE technology protects human-machine interaction by effectively eliminating all classic attack vectors related to data persistence and network dependency.
Looking ahead, the inherent design principles of EviKeyboard BLE — centered on zero-trust, air-gap integrity, and hardware-rooted sovereignty — lay the groundwork for a new paradigm in digital security. As cyber threats continue to evolve in sophistication, the ability to control and interact with critical systems without leaving a digital footprint or relying on vulnerable network layers becomes paramount. Therefore, EviKeyboard BLE not only solves today’s most pressing security challenges but also empowers a future where critical operations can proceed with unprecedented levels of trust and cryptographic assurance, fostering true digital autonomy for its users.
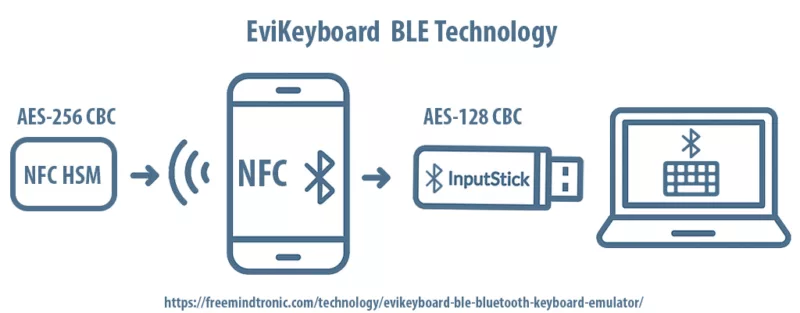
EviKeyboard BLE Overview
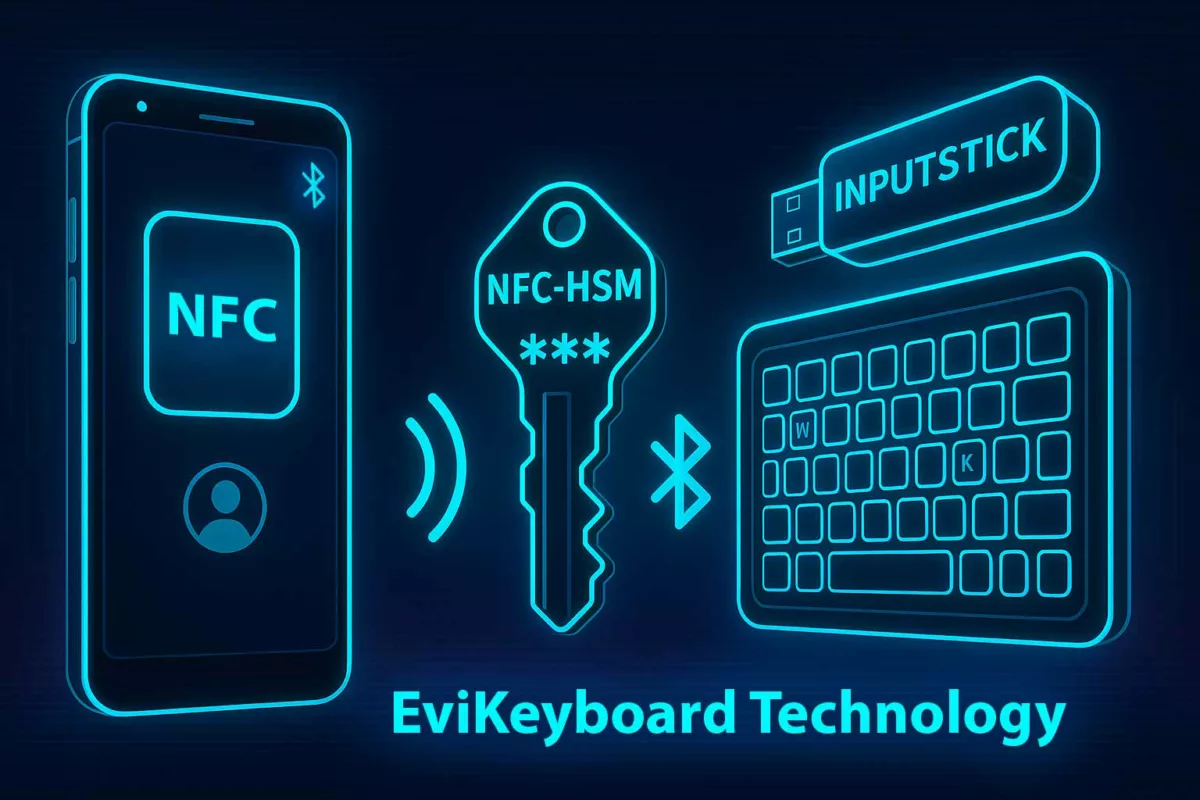
EviKeyboard BLE redefines the use of Android smartphones as secure USB keyboards using Bluetooth Low Energy, without storing or syncing sensitive data.
At its core, EviKeyboard BLE functions as a mobile HID interface. The Android smartphone, equipped with NFC and the Freemindtronic App, decrypts secrets stored in a physical NFC HSM and instantly transmits them via BLE to an InputStick dongle. This dongle emulates a USB keyboard on the host system.
The design supports a range of use cases: from secure password injection and cryptographic access in air-gapped facilities, to administrative logins across untrusted endpoints. Importantly, no credentials or data remain on the phone, the dongle, or the host device—only ephemeral, one-time transmissions aligned with zero-trust protocols.
EviKeyboard BLE enforces strict segregation between the holder of the secret (NFC HSM), the transmission channel (BLE), and the execution environment (host PC), forming a sovereign, attack-resilient data injection chain.
EviKeyboard BLE Overview
EviKeyboard BLE redefines the use of Android smartphones as secure USB keyboards using Bluetooth Low Energy, without storing or syncing sensitive data.
At its core, EviKeyboard BLE functions as a mobile HID interface. The Android smartphone, equipped with NFC and the Freemindtronic App, decrypts secrets stored in a physical NFC HSM and instantly transmits them via BLE to an InputStick dongle. This dongle emulates a USB keyboard on the host system. The design supports a range of use cases: from secure password injection and cryptographic access in air-gapped facilities, to administrative logins across untrusted endpoints. Importantly, no credentials or data remain on the phone, the dongle, or the host device—only ephemeral, one-time transmissions aligned with zero-trust protocols. EviKeyboard BLE enforces strict segregation between the holder of the secret (NFC HSM), the transmission channel (BLE), and the execution environment (host PC), forming a sovereign, attack-resilient data injection chain. This approach eliminates the need for password managers, cloud syncing, or local storage, relying instead on ephemeral, air-gapped communication secured with AES-128 encryption.
InputStick Protocol Implementation
InputStick serves as the secure intermediary between Android NFC phones and computers, emulating a USB HID device with Bluetooth Low Energy.
InputStick is a compact USB dongle embedding a microcontroller that interprets BLE signals from an Android device and converts them into HID commands—mimicking a physical keyboard or mouse. This allows the Android phone to act as an input source without a physical connection to the host system. Freemindtronic’s implementation leverages its API to inject real-time keystrokes securely into any USB-compatible host. No drivers or custom OS modules are needed—just plug InputStick into a USB port and initiate the encrypted session from the phone.
This enables precise HID injection over BLE without caching or buffering.
Freemindtronic customizes this protocol by enforcing cryptographic handshake routines: the InputStick interface accepts sessions only when pre-authenticated with a 128-bit password exchanged during a secure NFC app launch. Each interaction is bound to the originating NFC HSM, which provides end-to-end AES-128 encryption without relying on cloud or memory storage. Freemindtronic augments InputStick with sovereign-grade protections: 128-bit password authentication, end-to-end AES-128 encryption, and integration with NFC HSMs. This turns InputStick into a passive, context-aware gateway with zero-retention logic, ideal for zero-trust architectures. InputStick operates as a cryptographically bounded HID emulator. It does not initiate transmissions, store states, or expose itself to the host prior to activation. Once triggered via a secure BLE handshake, it acts solely as a passive receiver of encrypted input—ensuring strict alignment with air-gapped protocols.
Zero Trust Real-Time Transfer
EviKeyboard BLE ensures ephemeral, non-persistent data injection by design—no data is stored or cached at any point in the communication flow.
This zero-trust architecture is enforced by strict local isolation, ensuring all operations remain within trusted boundaries.
Each transmission initiated via EviKeyboard BLE is transient, initiated directly by the user through physical interaction with their NFC HSM. The data decrypted on the Android device is held in memory just long enough to be relayed over BLE to the InputStick dongle, where it is injected as keystrokes into the host machine.
This design inherently prevents any opportunity for replay, interception, or persistence. Even advanced threats on the host, such as USB-level keyloggers or BIOS exploits, are rendered ineffective because no data remains once injected. There is no telemetry, no logging, and no post-session artifact.
This fully transient approach aligns with zero-trust philosophies, especially in critical infrastructure contexts. The operator must be physically present, with their NFC device, to perform a transfer. This adds a layer of physical multi-factor authentication through possession and proximity alone.
Zero-Copy Injection Mechanism
EviKeyboard BLE delivers real-time keyboard emulation using a zero-copy model—eliminating all intermediate storage and enhancing operational determinism.
Injection within EviKeyboard BLE occurs without staging, buffering, or preview. Secrets decrypted by the mobile device are sent directly to the InputStick HID interface in their final keystroke form, bypassing all OS- or app-level intermediaries.
This “zero-copy” model is both technical and philosophical. It reflects the commitment to a stateless, volatile execution pathway: secrets are not retained, not transformed, not reprocessed—merely relayed in one-shot encrypted form to the terminal.
This mode enforces:
- No clipboard use: no copy-paste logic
- No memory duplication: the decrypted secret exists in RAM only momentarily
- No preview layer: the host cannot anticipate, echo, or alter the keystroke stream
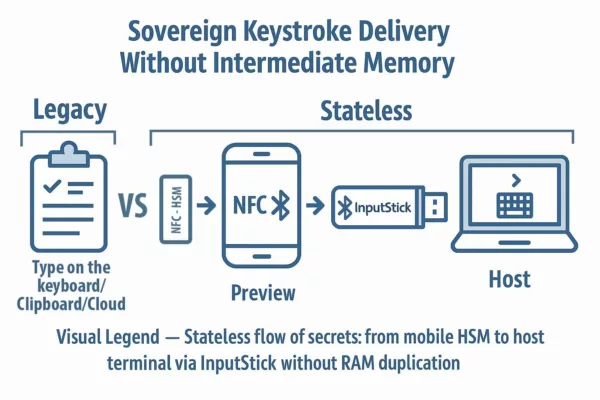
Such directness is crucial in high-assurance environments, where misalignment, delay, or accidental duplication could compromise the system’s integrity. The injection’s atomicity ensures cryptographic sequences, passwords, or commands arrive exactly as expected—at the right time, in the right place, without leaks or residue.
Sovereign Integration with NFC HSM
EviKeyboard BLE enforces sovereignty by design. Credentials are decrypted locally from a physical NFC HSM, held under user control, then injected via BLE HID—never passing through any OS buffer, cloud service, or middleware layer. This unbroken, deterministic trust chain forms the cryptographic backbone of Freemindtronic’s sovereign injection stack.
- Each HSM embeds secure payloads and initiates BLE sessions only when physically tapped by an NFC-enabled Android device.
- All decryption occurs inside the mobile sandbox; only the result is transmitted to InputStick.
- The architecture ensures full sovereignty across the entire lifecycle: key generation, selection, injection—without cloud dependencies.
- NFC HSMs are unclonable, untraceable, and fully aligned with air-gapped operational models.
Compatible NFC HSM Modules with Bluetooth Emulator Keyborad
- PassCypher NFC HSM
- DataShielder NFC HSM
- SeedNFC HSM
These modules inject deterministic keystrokes from a fixed cursor anchor—critical for secure logins and automation on constrained systems.
Sovereign Use Cases & Compliance
- Air-gapped system administration
- Emergency decryption of cryptographic seeds
- Passwordless login for SCADA/ICS infrastructures
- Alignment with EU critical infrastructure and digital identity standards
Technical Datasheet
Comprehensive specifications for secure, sovereign deployments of EviKeyboard BLE with InputStick dongle and Freemindtronic NFC HSMs.
- Device: InputStick USB dongle
- Radio Interface: Bluetooth Low Energy (2.4 GHz, BT 4.0)
- Max Range: Up to 10 meters
- Power Supply: USB (5V), Max: 25 mA, Idle: 0.3 mA
- Weight & Dimensions: 6g · 48 × 19 × 8 mm
- Encryption: AES-128 (end-to-end)
- Authentication: 128-bit key, optional password (min. 12 hex chars)
- Data Storage: None — zero-retention, ephemeral session model
- Keyboard Mode: Hidden HID (no input preview, no screen echo)
- Compatibility: Android NFC 4.3+, Windows XP+, Linux 2.6+, macOS 10.5+
- Software Dependencies: Freemindtronic App (Android NFC), InputStick Utility
- Security Integration: Compatible with EviCore NFC HSM, PassCypher, DataShielder, SeedNFC
- Supported HID Interfaces: Keyboard, Mouse, Gamepad, Consumer Control
- Device Type: Plug-and-play (no drivers required)
- Max Dongles Supported: Unlimited — dynamic multi-dongle pairing and sovereign HID injection orchestration
- Environmental Conditions: 0–60°C operating range
- Firmware Update: Updatable via InputStick Utility app
- Use Case Focus: Zero-trust environments, air-gapped systems, SCADA, cyber-resilience, emergency access
- Languages supported:
| Language | Code |
|---|---|
| Czech | cs-CZ |
| Czech (Linux) | cs-CZ-linux |
| Czech (Professional) | cs-CZ-pro |
| German (Switzerland) | de-CH |
| Danish | da-DK |
| German (Mac) | de-DE-mac |
| Greek | el-GR |
| English (Dvorak) | en-DV |
| Spanish (Spain) | es-ES |
| English (UK) | en-GB |
| English (US) | en-US |
| French (Belgium) | fr-BE |
| French (Canada) | fr-CA |
| French (Finland) | fr-FI |
| French (France) | fr-FR |
| French (Linux) | fr-FR-linux |
| Hebrew | he-IL |
| Hungarian | hu-HU |
| Hungarian (Croatia) | hu-HR |
| Italian | it-IT |
| Dutch | nl-NL |
| Norwegian (Bokmål) | nb-NO |
| Portuguese (Brazil) | pt-BR |
| Polish | pl-PL |
| Polish (Linux) | pl-PL-linux |
| Portuguese (Portugal) | pt-PT |
| Russian | ru-RU |
| Swedish | sv-SE |
| Slovak | sk-SK |
https://freemindtronic.com/product/bluetooth-keyboard-emulator/
Energy Efficiency & Runtime Design
The InputStick dongle draws a maximum of 25 mA during active sessions and 0.3 mA while idle. This ensures it can remain permanently inserted in air-gapped systems without draining energy reserves. Meanwhile, Android smartphones benefit from the BLE protocol’s efficient transmission model. The NFC interaction lasts mere milliseconds, while the BLE keystroke injection operates asynchronously, minimizing screen-on time and CPU cycles. This combination of low BLE duty cycles and ephemeral use makes EviKeyboard BLE ideal for battery-constrained deployments or field operations where power availability is limited.
Secure Typing Experience
Unlike traditional software keyboards, EviKeyboard BLE offers a seamless user experience with hardware-level control and sovereign data injection.
In contrast to most BLE-enabled HID solutions, EviKeyboard BLE operates with passive HID activation. The InputStick interface remains entirely dormant—no beacon, no handshake, no negotiation—until a physical NFC event triggers it. This behavior not only supports zero-trust BLE logic but also reinforces the system’s air-gapped architecture: no drivers, no OS interaction, and no ambient discovery. It ensures InputStick remains invisible to host systems and reconnaissance tools until activation, strengthening both operational discretion and physical isolation.
Once triggered, the injected payload follows a logic of HID-only. The BLE transmission between Android and InputStick is designed as a strictly ephemeral, unidirectional channel. Unlike bidirectional HID emulators or buffered virtual keyboards, EviKeyboard BLE never receives input, feedback, or status confirmation from the host. This reflects not only physical isolation but also strict logical disconnection: InputStick behaves as a cryptographic one-way conduit, offering no telemetry, no handshake, and no acknowledgment paths that could be intercepted or reverse-engineered.
The keystroke flow is deterministic, bound to the cursor anchor, and irreproducible—whether intercepted or repeated. InputStick transmits at native 8ms polling, ensuring parity with physical keyboards without visual artifacts or latency. This shielded stream neutralizes threats such as keyloggers, clipboard hijackers, and OS-level echo manipulation.
EviKeyboard BLE elevates secure typing into a hardened operational vector—initiated by physical presence, executed with cryptographic certainty, and concluded without digital residue.
Real-World Use Cases with EviKeyboard BLE
EviKeyboard BLE supports unlimited InputStick dongles paired with the same Android device. This enables sovereign credential injection across multiple endpoints without host dependency or manual reconfiguration. Each dongle can be dynamically selected and linked to a specific NFC HSM profile, making the system ideal for multi-user deployments, secure facilities, and operational segmentation in zero-trust environments.
Discover sovereign deployments and advanced automation scenarios using EviKeyboard BLE—designed for zero-trust, air-gapped infrastructures and secure workflows without reliance on networked systems or OS trust.
Sovereign Deployment in Critical Infrastructure
- Freemindtronic deployed EviKeyboard BLE across isolated SCADA units operated via NFC-enabled Android smartphones equipped with HSM modules such as PassCypher.
- Session credentials stored in each HSM are decrypted locally within the Android app when scanned, then transmitted through InputStick—connected to USB ports on secure terminals with no network or LAN access.
- Credentials are never reused, stored, or exposed to network interfaces. All data is ephemeral and erased post-injection.
- This model enables IT-free secure access that complies with sovereign infrastructure mandates.
Zero-Trust & Mission-Critical Assurance
- Fully compliant with air-gap mandates—perfect for military, emergency, and SCADA environments.
- True zero-knowledge operations: HSM tokens are wiped after use, InputStick logs nothing, and Android memory is flushed.
- Eliminates reliance on host OS, drivers, or credential caching.
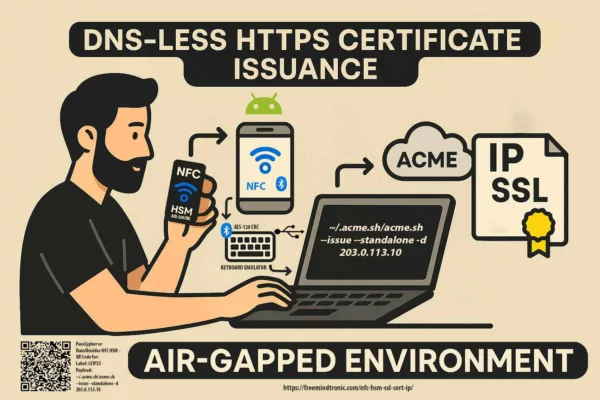
Advanced Automation Use Cases
Issue certificates via Let’s Encrypt over IP without DNS using SeedNFC and ACME protocol in LAN-only setups.
Secure Pre-boot or Login Unlock for BitLocker and TPM 2.0 Drives
EviKeyboard BLE offers a unique capability: direct secure keystroke injection to unlock your BitLocker encrypted and TPM 2.0 protected drives. Whether at pre-boot or login, this functionality is crucial for the security of your workstations, servers, and sensitive environments.
Operating in **HID (Human Interface Device)** mode via a wireless **Air-Gap** channel, EviKeyboard BLE ensures **contactless** secret injection without compromising system isolation. Keys or passphrases never travel over the network and are **never stored** on the device, guaranteeing optimal security even before full OS load.
This method is ideal for environments demanding strict access control and enhanced protection against firmware attacks or unauthorized physical access attempts.
Further Key Cyber Safety & Security Use Cases
Beyond BitLocker and TPM unlock, EviKeyboard BLE’s core technology of secure, air-gapped keystroke injection opens up critical applications across various high-security domains:
- Industrial & OT Security: Securely access PLCs, industrial robots, and SCADA/ICS systems in isolated or critical operational environments, mitigating network-based threats.
- Privileged Access Management (PAM): Safely inject credentials for highly privileged accounts on servers, network devices, and critical IT infrastructure, reducing the attack surface.
- Data Center & Cloud Security (On-Premise): Gain ultra-secure access to VM consoles/KVM, physical servers’ BIOS/UEFI, and network appliance configuration interfaces, even when traditional network access is compromised.
- Emergency & “Break-Glass” Access: Provide an indispensable, ultra-secure, and offline method for critical system access in disaster recovery or compromised network scenarios, ensuring operational continuity.
- Mitigating Zero-Day & Supply Chain Attacks: Its low-level, driverless HID operation significantly reduces the software attack surface, offering robust defense against sophisticated threats targeting firmware or the supply chain.
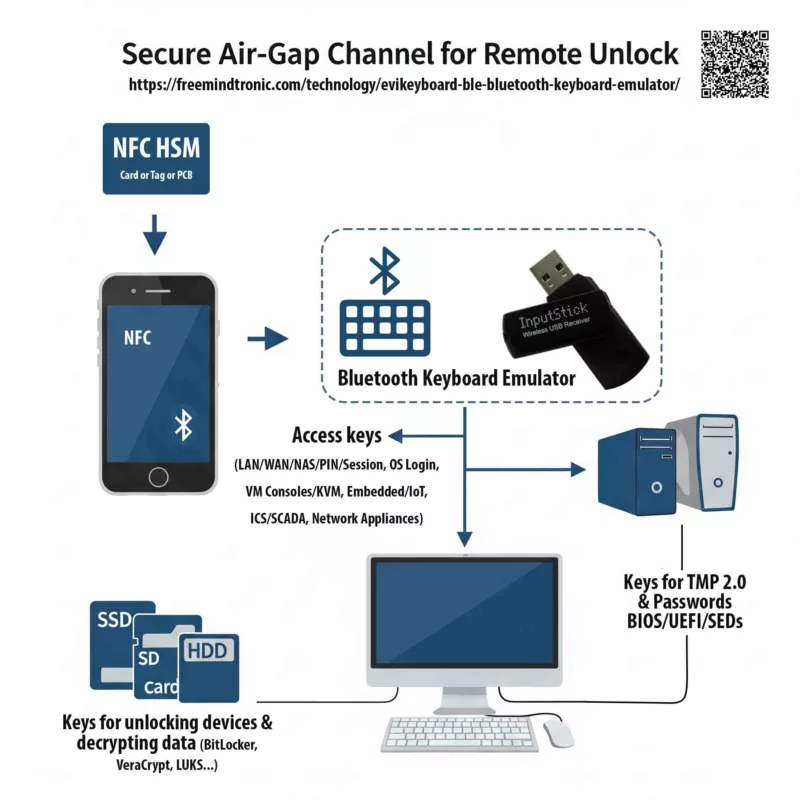
Detailed diagram of the EviKeyboard BLE system, showing secure, contactless secret injection via an Air-Gap channel to unlock systems and access critical environments remotely.
Industrial Compliance Use Cases
Control robotics, embedded systems, and industrial equipment through NFC-triggered deterministic input workflows.
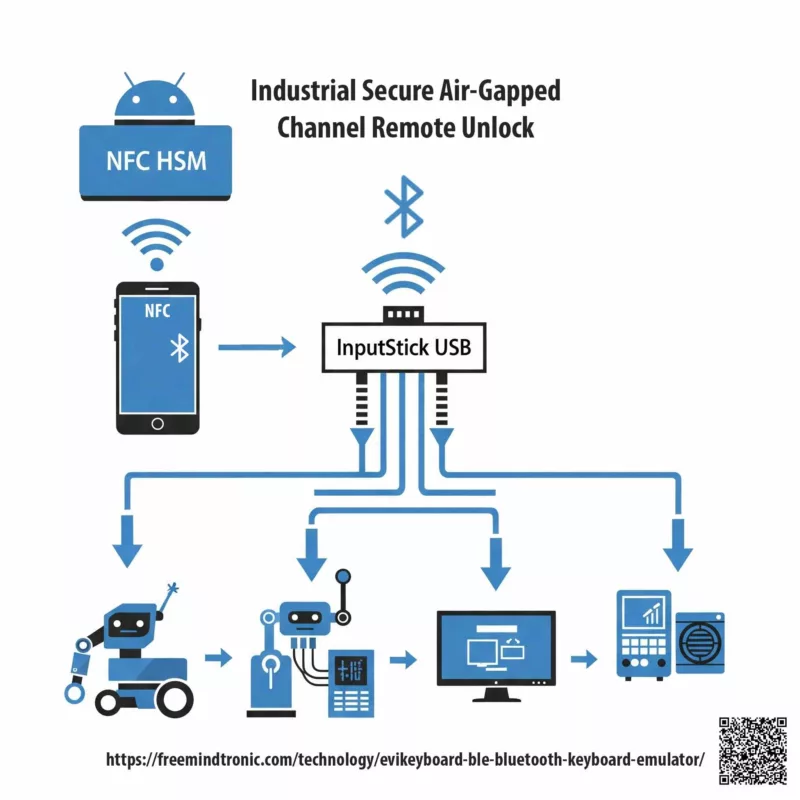
Related Readings & Technical Insights
Regulatory & Standards Alignment
EviKeyboard BLE complies with global cybersecurity frameworks, institutional guidelines, and academic research focused on secure HID emulation, air-gapped operations, and BLE security.
🏛️ Institutional & Regulatory Standards
- ANSSI – IT Hygiene Guide (v3.0): Recommends non-persistent devices for sensitive tasks—aligned with EviKeyboard BLE’s stateless design.
- NIST SP 800-53 Rev.5 – AC-20: Integrates temporary external devices in zero-trust environments.
- NIST SP 800‑121 Rev.1: Details secure Bluetooth pairing for HID devices.
- ISA/IEC 62443: Industrial cybersecurity standard fully compatible with EviKeyboard BLE deployments.
EU & US Cybersecurity Recommendations
- ENISA Threat Landscape: Spotlights HID-related vulnerabilities and sovereign countermeasures.
- CISA – Secure by Design: Reinforces network-independent device trust, mirroring EviKeyboard BLE’s architecture.
BLE HID Technical Security References
- Bluetooth SIG HID‑Lite White Paper: Requires authenticated pairing and AES encryption for BLE keyboards.
- SySS GmbH BLE Keyboard Study: Analysis of BLE keyboard vulnerabilities and defenses.
- BrokenStrokes Inference Attack: Shows RF signal inference risks even with encrypted BLE.
- BLURtooth Vulnerability: Examines downgrade and MITM threats in BLE 4.x HID devices.
- IJARCCE Red Team Methodology: Validates resilience testing of USB HID injectors in ethical hacking environments.
🎓 Academic & Community Endorsements
- ETH Zurich (2021) & DEF CON/CCC Forums: Support sovereign HID emulation strategies as resilient alternatives to networked access—especially in air-gapped operations.
Related Sovereign Links
Explore complementary technologies and secure modules by Freemindtronic that integrate seamlessly with EviKeyboard BLE for advanced sovereign cybersecurity.
- PassCypher NFC HSM – Sovereign offline password manager supporting EviKeyboard BLE injection.
- DataShielder NFC – Multi-layered encrypted data vault for protecting secrets in air-gapped environments.
- SeedNFC – Offline injector for wallet seed phrases and identity recovery.
EviPass NFC HSM Integration
EviPass NFC HSM is the cornerstone passwordless technology embedded in Freemindtronic’s apps—PassCypher, DataShielder, and SeedNFC—enabling seamless keyboard emulation and credential injection through EviKeyboard BLE.
- EviPass acts as a secure, segmented container for credentials (up to 61 printable ASCII characters) stored directly on the HSM.
- Each record includes a label (used as a selector), a login, and a password—all encrypted with AES-256 CBC using a user-defined key.
- Users can manage multiple EviKeyboard BLE profiles, define favorites, and choose in real time through the Android app interface.
- EviKeyboard BLE becomes an extension of EviPass—injecting credentials directly into any USB HID-compatible device (TV, robot, domotics, ACME clients, BitLocker unlock, etc.).
- No reliance on DNS, network or OS-level clipboard—ensuring full compatibility even in constrained, legacy, or embedded systems.
Explore technical example: EviPass for ACME/DNS-less HTTPS Cert Deployment
📺 Watch tutorial: EviKeyboard BLE Secure Autofill Tutorial by EviVault NCF HSM Technology
📺 Also see: How to Use EviKeyboard BLE in Freemindtronic Apps
Understand the flow:
InputStick BLE Integration Strategy
EviKeyboard is the official InputStick BLE integration layer developed by Freemindtronic to support its entire ecosystem of sovereign NFC HSM products. This strategic implementation ensures real-time HID emulation across all Freemindtronic apps and modules.
- Acts as a universal BLE HID bridge between Freemindtronic apps (Android NFC) and USB host systems via InputStick dongle.
- Enables seamless deployment across all Freemindtronic solutions including PassCypher, DataShielder, SeedNFC, and future sovereign modules.
- Implements an air-gap control model: the HSM unlocks, decrypts, and injects via BLE without exposing secrets to any OS clipboard or buffer.
- Optimized to support deterministic workflows like credential injection, seed recovery, and encrypted command injection for SCADA, OT, and embedded systems.
- Represents the BLE HID cornerstone of Freemindtronic’s sovereign architecture stack—offering continuity, security, and extensibility across solutions.
Security by Design Architecture
EviKeyboard BLE inherits the full security isolation of EviPass NFC HSM, with a zero-OS, air-gapped design that eliminates exposure vectors by design.
- No operating system between secret storage and transmission—decryption is executed locally within a sealed environment.
- No copy-paste mechanisms, no system clipboard, no logging—transfers are ephemeral and fully deterministic.
- Each EviKeyboard profile is encrypted using user-defined AES-256-CBC keys, stored only in the NFC HSM under multi-factor control.
- Architecture resists telemetry injection, unauthorized synchronization, and remote extraction attacks.
- Integrated seamlessly with Freemindtronic’s patented technologies EviCypher and EviToken.
Industrial Compliance Use Cases
EviKeyboard BLE directly supports compliance with stringent industrial cybersecurity regulations and best practices by enabling secure, air-gapped, and auditable access to critical OT systems.
EviKeyboard BLE stands as a strategic asset for organizations actively seeking to strengthen their OT compliance posture within increasingly regulated industrial environments. Its fundamental features directly address the most stringent security requirements:
- IEC 62443 Compliance: By providing a secure, air-gapped command injection channel, EviKeyboard BLE directly aligns with the segmentation and access control principles of the IEC 62443 standard for ICS/SCADA systems. Crucially, it actively minimizes the attack surface by eliminating the need for network connections or secret storage on industrial systems.
- Zero-Day & HID Attack Prevention: Its driverless operation in low-level HID mode, even before OS launch, drastically reduces exposure to software vulnerabilities and BadUSB/HID attacks. Consequently, this serves as a critical advantage for infrastructure resilience and operational continuity.
- Strong Multi-Factor Authentication (MFA) for OT: Integration with NFC HSMs, offering geo-fencing and fingerprint authentication, enables robust multi-factor authentication for accessing PLCs, robots, and embedded systems. This is essential for proving compliance with access control mandates and identity verification protocols.
- Simplified Traceability and Auditability: While the device ensures zero data persistence, its HSM-centric architecture allows centralized management of access and permissions (on the HSMs). Furthermore, this significantly facilitates compliance audits regarding who accessed what, and when, without compromising system isolation.
- Data Sovereignty and Operational Resilience: The physical offloading of keys and payloads to the HSMs ensures secrets remain under the user’s exclusive control. This directly meets data sovereignty requirements and enhances operational resilience against advanced cyber threats.
EviKeyboard BLE offers a concrete solution for sectors demanding rigorous compliance, such as energy, defense, manufacturing, and critical national infrastructure. It delivers a secure, verifiable, and resilient access method for their vital assets.
SCADA & ICS Compliance Use Cases
EviKeyboard BLE satisfies the security, offline capability, and hardware constraints of industrial environments including SCADA, ICS, and TPM-based boot systems.
- Offline secret injection for BitLocker TPM 2.0, BIOS-level login, and emergency decryption workflows.
- Zero-network interaction aligns with IEC 62443 recommendations for segregated cyber-physical environments.
- Fully compatible with legacy systems requiring no drivers, updates, or system-level permissions.
- Air-gapped key management prevents remote intrusion or telemetry extraction.
Secure HID Comparison Table
| Feature | EviKeyboard BLE | YubiKey OTP HID | Google Titan BLE | Encrypted USB Keyboard |
|---|---|---|---|---|
| Storage | None | Local OTP | Cloud backup | Flash memory |
| Connectivity | Bluetooth Low Energy | USB | BLE | USB |
| Encryption | AES-256 CBC (HSM) | OTP | Google Auth | AES or proprietary |
| Compatibility | Any USB HID | OS login/screens | Google ecosystem | OS-limited |
| Offline Operation | Yes | Yes | No | Yes |
| Customization | Unlimited profiles | Fixed OTP | Minimal | None |
Multi-HSM Orchestration
Secure orchestration of workflows across multiple sovereign NFC HSMs—without backend synchronization or online exposure.
EviKeyboard BLE establishes a sovereign orchestration model via native support for multi-HSM workflows. Users can seamlessly switch between distinct NFC HSMs and/or EviKeyboard BLE instances—each representing unique roles, credentials, or operational contexts—without restarting the app or triggering reauthentication.
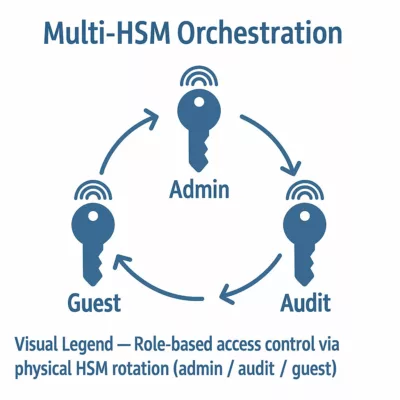
Thus, the orchestration pillar ensures full sovereignty and flexibility in air-gapped or segmented deployments, even during mission-critical operations.
- Profile-level isolation: Each NFC HSM securely stores encrypted EviKeyboard BLE profiles, governed by granular trust criteria and independent access control. Administrators can predefine role-based permissions.
- Deterministic session control: No broadcast pairing, no shared states. EviKeyboard BLE operates as a pure AES-128 CBC encrypted communication channel.
- Operational continuity: Switching between NFC HSMs does not interrupt workflows or injection routines. Users preselect the secret to be used.
Therefore, EviKeyboard BLE empowers teams to operate securely—even remotely within Bluetooth range—by enforcing cryptographically segmented responsibilities and access privileges across both NFC HSM and InputStick BLE encryption keys.
As a result, every role, action, and keystroke stream is strictly controlled and authenticated end-to-end at the hardware level.
In essence, this framework ensures the impermeability of trust boundaries, delivering an execution environment so robust that even minor vulnerabilities risk compromising system-wide integrity.
Finally, Freemindtronic’s orchestration model honors the foundational principles of sovereignty:
- No telemetry
- No online syncing
- Full operational control via physical possession of the NFC HSM
Unalterable Flow Integrity
EviKeyboard BLE guarantees cryptographic and procedural integrity of every keystroke — from source to destination — by preventing interception, delay, or injection manipulation.
The NFC HSM generates each keystroke and transmits it unidirectionally and statelessly to InputStick over BLE. This deterministic flow ensures accurate interpretation and injection with zero deviation.
EviKeyboard BLE bypasses echo, eliminates preview, and denies write-access to the host memory space. It injects exactly what it decrypts — byte for byte.
Here, integrity goes beyond data accuracy — it represents total immutability of execution:
- Hosts cannot alter or reformat keystrokes
- Attackers cannot interfere with or reorder input midstream
- Systems do not cache, buffer, or log any injected data
EviKeyboard BLE delivers high-integrity command injection, even under adversarial conditions involving clipboard hijacking, key remapping, or keyboard interception malware.
It enforces an execution environment where every HSM-driven operation reaches its target undistorted, unmodified, and without leaving a forensic trace.
Beyond This Chronicle
EviKeyboard BLE is not just a solution—it is a strategy for critical sovereignty and future-proof cybersecurity practices.
As attack vectors evolve and regulatory mandates intensify, the demand for autonomous, offline security tools grows. EviKeyboard BLE exemplifies this new paradigm—where control is physical, secrets are transient, and sovereignty is operational.
Future iterations may incorporate biometric triggers, multi-tag HSM orchestration, or enhanced integration with decentralized identity frameworks (DID). With expanding HID compatibility and firmware modularity, EviKeyboard BLE stands at the frontier of operational cybersecurity—ready for adaptation across industries requiring uncompromised integrity.
Technical FAQ
For full technical details, see How EviKeyboard BLE Works.
Functionality & Usage
Compatibility & Integration
Cybersecurity
Operational Safety
While this chronicle focused on InputStick BLE injection and NFC HSM workflows, peripheral aspects such as firmware-level threat modeling, InputStick BLE stack debugging, and compatibility with legacy systems were not addressed. These blind spots warrant future sovereign investigations.




Pingback: Chrome V8 Zero-Day CVE-2025-10585 — Ton navigateur était déjà espionné ? - Freemindtronic
Pingback: Chrome V8 confusion RCE — Your browser was already spying - Freemindtronic