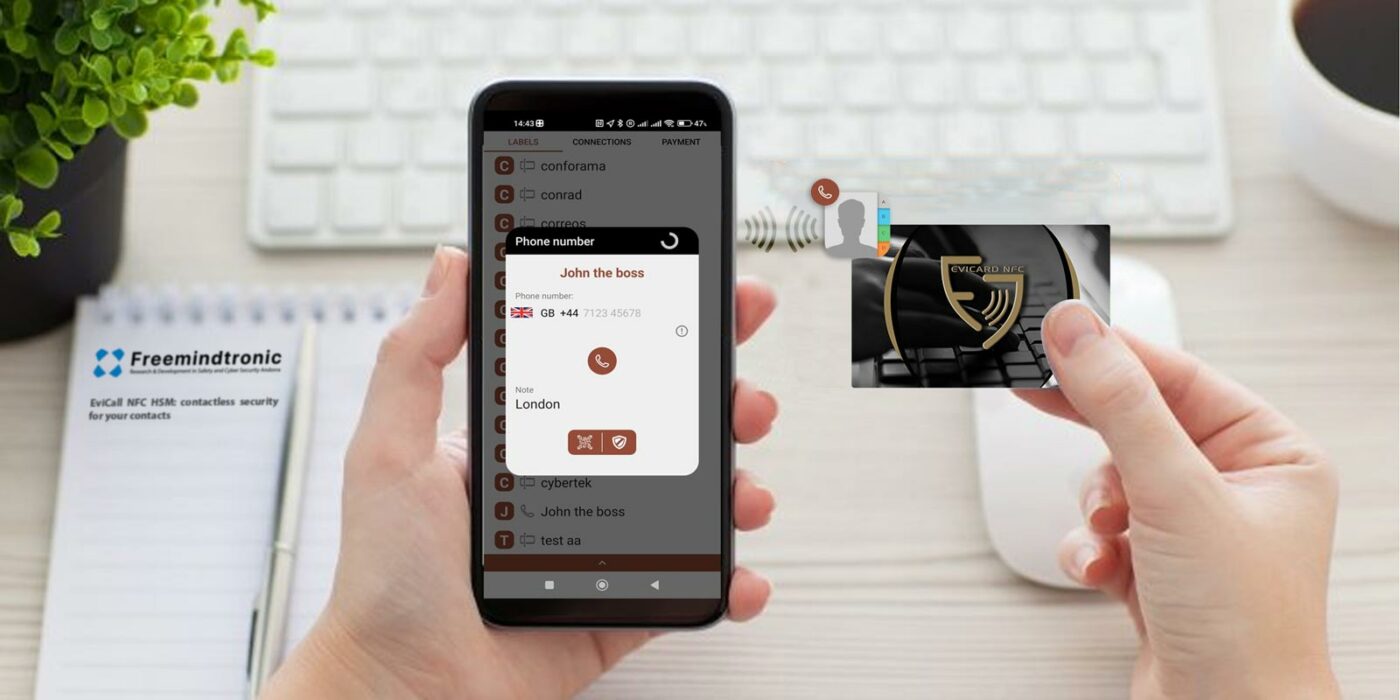
The advantages and disadvantages of EviSCP HSM
EviSCP HSM is a secure communication protocol that has many advantages over existing VPN solutions, such as:
Enhanced security
EviSCP HSM uses patented mechanisms, such as segmented key authentication, salting system, access control, and black box monitoring, to ensure the security and confidentiality of data and devices. EviSCP HSM also uses ZKP to prove the truthfulness of statements without revealing any information beyond the simple fact of the truth. EviSCP HSM protects against various attacks, such as counterfeiting, replay, brute force, or keylogging.
Application flexibility
EviSCP HSM transforms any existing communication protocol into a virtual VPN between portable electronic devices, without requiring a server or a database of secrets. EviSCP HSM is compatible with any type of network or device, and can be used in various contexts, such as payment, health, or IoT. Personalized security control: EviSCP HSM allows the user to define trust criteria adapted to his specific needs. These criteria determine the authentication factors required to access the encrypted data or devices. The user can thus choose the level of security he wants to apply, depending on the context and risk.
However, EviSCP HSM also has some disadvantages that should be considered, such as:
Cost: EviSCP HSM requires the use of NFC HSM or HSM multi-support devices, which are more expensive than standard VPN solutions. The user also needs to purchase a license to use the EviSCP HSM protocol and software. Compatibility: EviSCP HSM may not be compatible with some legacy systems or devices that do not support NFC or HSM technologies. The user may need to upgrade or replace his existing hardware or software to use EviSCP HSM. Transparency: EviSCP HSM relies on patented mechanisms that are not open source or publicly available. The user may not be able to verify the effectiveness or security of the cryptographic algorithms or random number generators used by EviSCP HSM.