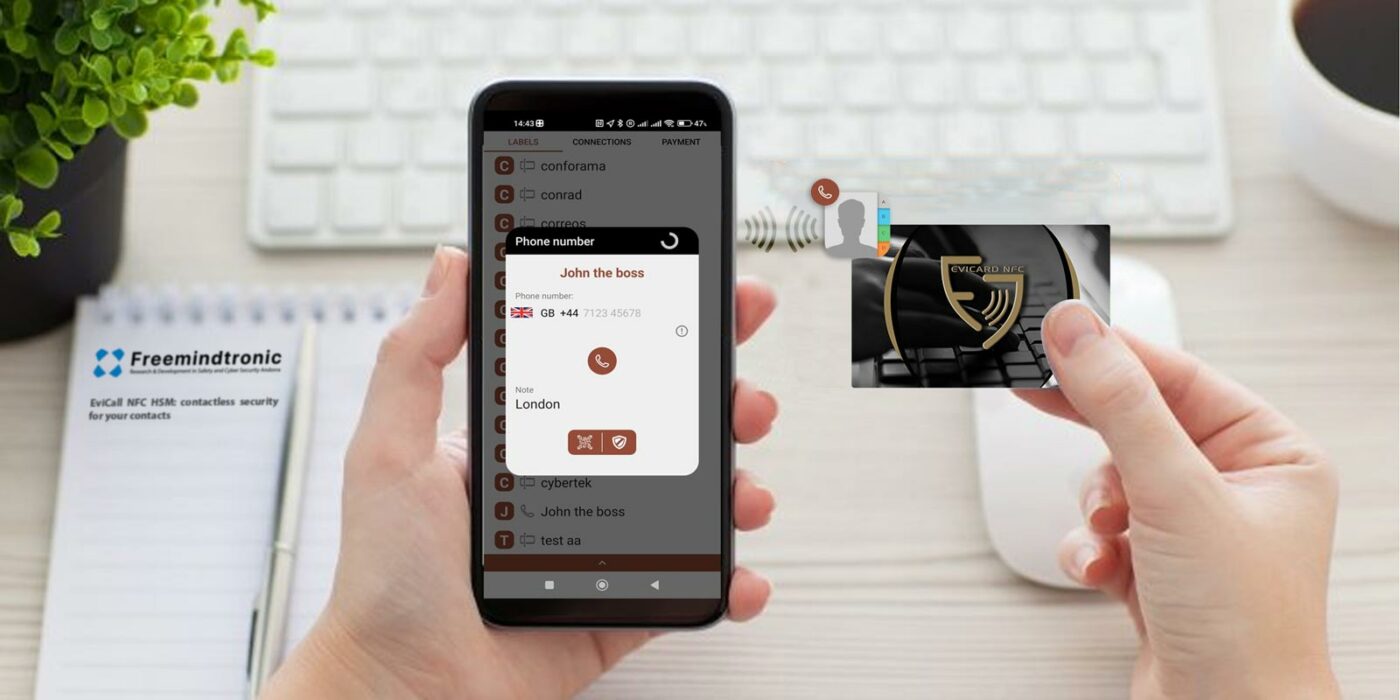
First, phone contacts are securely encrypted and physically externalized in the non-volatile memory of the NFC HSM EviCall. This has the effect of making sensitive telephone contacts not present in the telephone.
This technology secures phone contacts by using NFC HSM (Near Field Communication Hardware Security Module). This device contains a secure element (SE) that can store cryptographic keys and perform cryptographic operations. It communicates with a smartphone via NFC (Near Field Communication) technology, which allows data exchange over short distances.
With this technology, you can store and manage phone numbers in a secure and independent way from the smartphone. The device encrypts the phone numbers with AES 256-bit algorithm and stores them in the SE of the NFC HSM. EviCall, which acts as a physical key and a multi-factor access control system, blocks any unauthorized access to access the SEs. Therefore, your encrypted phone contacts in the HSM NFC cannot be corrupted by a third-party application wishing to access the encrypted data in the SE. No third-party application can access the SE of the NFC HSM.
In addition, you can activate telephone communications from your NFC HSM after you have authenticated yourself via the various trust criteria that you have determined to access your telephone contact. Contacts are decrypted only in the phone’s volatile memory just long enough to activate the call. Once the call has ended, the EviCall NFC HSM technology erases the phone number used from the NFC HSM EviCall from the phone’s call history. Note that the call made via EviCall NFC HSM is made via the SIM or eSIM of your phone.
Therefore, this technology provides physical and logical security for data storage, transmission and deletion.


Comments are closed.