- Hero
- Executive Summary
- Quantum-resistant passwordless manager
- Key pillars
- Proof: core architecture
- Segmented containers (security boundary)
- RAM-only decryption
- Embedded URL verification
- Patented technology
- How it works
- Threat model and invariants
- Threats addressed
- Security invariants
- Explicit non-goals
- Unique added values
- Real-World Use Cases
- Comparative table
- Legal and regulatory alignment
- GDPR principles
- Standards references
- Scope note
- FAQ
- FAQ 1 — Standalone?
- FAQ 2 — Standards?
- FAQ 3 — Storage?
- FAQ 4 — Master password?
- FAQ 5 — Offline?
- FAQ 6 — Stolen container?
- FAQ 7 — RAM-only?
- FAQ 8 — Phishing?
- FAQ 9 — Sharing?
- FAQ 10 — Duplication?
- FAQ 11 — Untrusted host?
- FAQ 12 — Linux?
- Glossary
- Sovereign operational use case
Executive Summary
EviOTP HSM PGP is a desktop OTP key manager embedded in PassCypher HSM PGP. It supports TOTP (RFC 6238) and HOTP (RFC 4226) while keeping each OTP secret inside a small PGP AES-256 CBC encrypted container (about 1 KB). As a result, the system avoids centralized storage, accounts, telemetry, and cloud dependencies.
Instead of trusting the host, the design splits decryption material across two segments: one segment resides in local storage (application sandbox), whereas the other segment stays on an external medium that the operator controls (USB key, SD card, encrypted folder, or equivalent). Consequently, the secret remains unusable when either segment is missing.
During use, the application decrypts only in RAM, auto-fills and injects the OTP, and then destroys decrypted material immediately. Moreover, the container can embed the original login URL; therefore, the system can validate domain integrity before injection to reduce typosquatting and phishing exposure.
This architecture targets desktop multi-factor authentication continuity under hostile endpoint conditions, including infostealers, credential theft, and typosquatting-driven OTP interception.
Scope: desktop TOTP and HOTP key management using OpenPGP-encrypted containers, segmented key custody, RAM-only decryption, and domain-bound OTP injection for offline and air-gapped operations.
Integration context: EviOTP HSM PGP operates as an embedded capability inside PassCypher HSM PGP; see https://freemindtronic.com/how-passcypher-hsm-pgp-works and https://freemindtronic.com/product/passcypher-hsm-pgp-password-manager.
Component boundary: EviOTP provides the OTP-specific logic (QR import, container format, segmented key enforcement, RAM-only handling, and OTP generation), while PassCypher HSM PGP supplies the secure desktop environment, user interface, and integration with local workflows.
Quantum-resistant passwordless manager (Intersec Awards 2026)
Within PassCypher HSM PGP, EviOTP HSM PGP operates inside a passwordless workflow that emphasizes RAM-only handling of sensitive material during use. For context on the Intersec Awards 2026 finalist announcement, see https://freemindtronic.com/quantum-resistant-passwordless-manager-intersec-awards-2026.
Key pillars
Offline-first OTP lifecycle
Create, import, store, and use TOTP/HOTP secrets without relying on internet connectivity, remote services, or synchronized databases.
Segmented-key enforcement
Require two independent segments—one in browser local storage and one on external media—before any decryption attempt becomes possible.
RAM-only decryption
Decrypt only in volatile memory during the active operation. After injection, erase decrypted material so that no cleartext lands on persistent storage.
Domain integrity before injection
Associate each container with the original login URL, then validate the destination domain before injecting an OTP to limit typosquatting and phishing paths, including BITB-style deception.
Controlled sharing without accounts
Share encrypted containers through operator-defined passphrases using PGP AES-256 CBC, including portable storage or air-gapped transfer methods.
Serverless and database-free
Operate without a central service, without a required cloud backend, and without a required centralized master password.
Proof: core architecture
Segmented containers as the security boundary
Each OTP secret exists as an independent encrypted container. The system splits decryption material into two segments so that no single location holds everything required to unlock the secret. One segment resides in browser local storage, while the other remains on external media under operator control. Therefore, exfiltration of the host alone does not yield immediate OTP secrets.
Security claims and verifiability
Performance note: OTP release and injection are designed to complete within milliseconds, with decrypted material existing only in volatile memory for the shortest necessary time.
- Offline operation: all OTP generation and handling works without network connectivity.
- Encrypted at rest: OTP secrets are stored exclusively inside PGP AES-256 CBC encrypted containers.
- RAM-only decryption: decrypted OTP material exists only in volatile memory during the active operation.
- Segmented key enforcement: decryption requires two independent key segments stored in separate locations.
- URL-bound release: OTP injection occurs only when the active domain matches the reference URL.
These claims can be evaluated through runtime observation, controlled testing, and operational inspection. The architecture intentionally avoids opaque server-side enforcement.
RAM-only decryption and immediate destruction
When the operator requests an OTP, the application reconstructs the required segments and decrypts only in RAM. Next, it auto-fills and injects the OTP into the target login flow. Finally, it destroys decrypted material immediately after use. Consequently, the system avoids writing secrets in cleartext to disk during routine operations.
Embedded URL verification before OTP injection
The container can embed the original login URL. Accordingly, the application can compare the active domain against the stored domain before injection, reducing exposure to typosquatting and look-alike login pages. This control does not replace user awareness; however, it creates a deterministic precondition for OTP release. By binding OTP release to the verified domain, the workflow behaves like an URL sandbox for injection and reduces exposure to modern phishing patterns, including Browser-in-the-Browser (BITB).
Patented technology
The foundation of EviOTP HSM PGP relies on patented innovations that reinforce segmented custody and controlled authentication workflows.
- Segmented key authentication system — enforcing multi-criteria trust conditions before any OTP generation.
Together, these patents formalize a segmented key authentication architecture that strengthens separation of duties and control logic, while keeping OTP secrets unusable unless the defined release conditions hold.
How it works
Canonical OTP lifecycle: offline QR enrollment → encrypted containerization → segmented key custody → RAM-only decryption → URL verification → automatic OTP injection → immediate memory cleanup.
Visual proof (offline): QR import (file or webcam), local TOTP/HOTP detection, and URL-bound OTP autofill inside PassCypher HSM PGP.
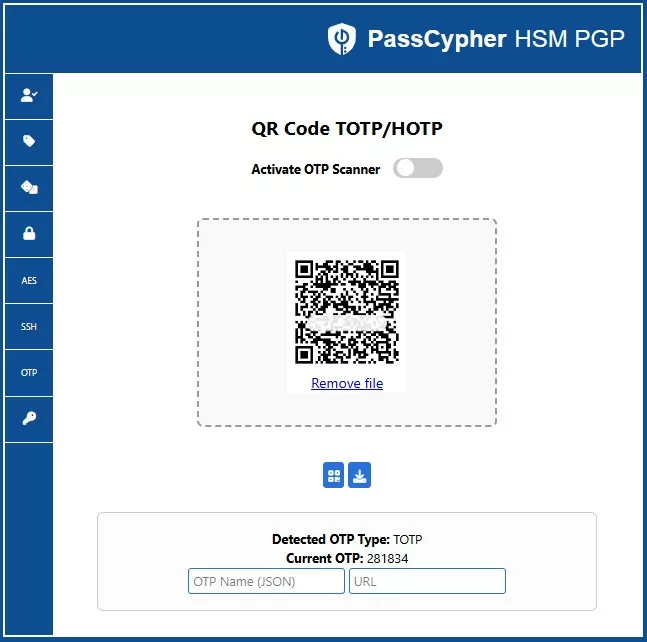
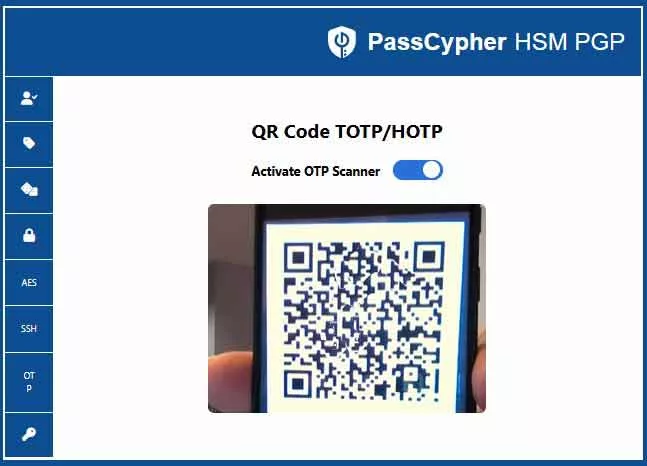
- Define the storage split: Define where the external segment will reside (USB key, SD card, encrypted folder, or equivalent) while the local segment remains in browser local storage.
- Create or import a secret: Create a new TOTP/HOTP secret or import an existing one (including QR-code enrollment workflows, when available in your environment).
- Bind the origin: Define the reference login URL that the container will enforce during OTP injection.
- Encrypt into a container: Generate the small PGP AES-256 CBC encrypted container that encapsulates the secret and its operational metadata.
- Store segments separately: Save the external segment on the chosen medium. Confirm that the local segment remains only in local storage.
- Use the OTP on demand: Navigate to the login page, then click the OTP action in the desktop workflow. The system validates domain integrity, decrypts in RAM, auto-fills and injects the OTP, and destroys decrypted material.
- Share when required: If the operator needs delegated access, encrypt the container with a user-defined passphrase and transfer it via portable storage, QR workflows, or air-gapped channels. Access still requires segment conditions and URL validation.
- Duplicate for resilience: Duplicate encrypted containers across controlled media as needed. Since the containers remain encrypted, duplication supports continuity without exposing cleartext.
For the host workflow context, refer to PassCypher HSM PGP: https://freemindtronic.com/how-passcypher-hsm-pgp-works.
Threat model and invariants
Limitations and assumptions
- The model assumes the operating system is not persistently compromised at kernel level.
- Memory-only handling does not prevent attacks on an actively hijacked user session.
- Swap, crash dumps, or forensic tooling can weaken RAM-only guarantees if misconfigured.
- Segment separation depends on strict operator discipline.
- URL binding reduces phishing risk but does not replace user awareness.
Threats addressed by design
- Host compromise and infostealers: The design reduces value of file system exfiltration because encrypted containers do not reveal secrets without both segments.
- Phishing and typosquatting: The system can block OTP injection when the active domain diverges from the embedded origin URL.
- Offline continuity constraints: Since the workflow can remain offline, it supports scenarios where networks degrade, isolate, or disappear.
- Uncontrolled synchronization: By avoiding cloud sync and centralized databases, the system reduces remote aggregation risk.
- Browser-in-the-Browser (BITB) phishing: URL-bound injection reduces the risk of OTP entry into deceptive in-page login overlays when the active domain does not match the enrolled origin.
Security invariants that must remain true
- Segment separation must persist: The operator must not store both segments together in the same location, otherwise the split-key property collapses.
- Decryption must remain RAM-only: Operational procedures must avoid tools or workflows that dump memory or persist decrypted material outside the intended runtime.
- URL binding must stay authoritative: The operator must bind the correct reference domain during enrollment and must treat domain mismatch alerts as hard stops.
- External media control must remain physical: The operator must maintain custody and integrity of external media. If an adversary controls the external segment and can also coerce the local segment, the barrier weakens.
- Passphrase quality governs shared containers: When the operator shares containers, passphrase strength and handling discipline determine resistance to offline guessing.
Explicit non-goals
- It does not make a compromised user session “safe”: If an attacker controls the browser session and the operator proceeds, the attacker can still exploit authenticated access.
- It does not eliminate endpoint hygiene: The model assumes an untrusted host for storage, yet it still benefits from endpoint hardening for runtime integrity.
Unique added values
- Container-level sovereignty: Treat each OTP secret as a portable cryptographic object rather than an entry inside a centralized vault file.
- Operational duplication without decryption: Duplicate encrypted containers across controlled media to sustain access continuity without expanding cleartext exposure.
- Deterministic release conditions: Release an OTP only when segment presence and domain integrity conditions simultaneously hold.
- Reduced administrative coupling: Avoid mandatory services, accounts, or centralized telemetry paths that expand the attack surface through aggregation.
- Peer transfer without trust escalation: Share encrypted containers over constrained channels (including air gap) while preserving the same segmented enforcement logic at the point of use.
- Desktop-centric injection discipline: Keep the OTP workflow on the workstation that performs authentication, which reduces cross-device exposure paths introduced by mobile-to-desktop relay habits.
Offline MFA for privileged consoles
Use OTP for administrative web consoles while maintaining offline continuity; the system decrypts in RAM, auto-fills and injects the OTP, and destroys decrypted material immediately.
Air-gapped enrollment and use
Store the external segment on removable media in segmented workflows so that OTP use remains possible in isolated environments without network dependencies.
Delegated access with bounded exposure
Share an encrypted container with a user-defined passphrase while keeping release conditions tied to segment presence and domain binding.
Incident response continuity under isolation
During containment, keep OTP capability available through duplicated encrypted containers, while limiting the risk of secrets being extracted as files.
Regulated access with minimized personal data
Operate without account creation or telemetry paths, thereby reducing the collection footprint in environments where data minimization drives security posture.
Red/black workstation separation support
Use segmented storage to preserve separation intent: keep the external segment under strict custody while limiting what a compromised endpoint can recover from disk.
Desktop-only DevOps workflows
Authenticate to internal tools from a workstation without depending on a mobile authenticator relay; click to generate and inject OTP under enforced conditions.
Third-party audit access under custody rules
Provide time-bounded access by transferring encrypted containers through controlled channels while keeping the external segment under explicit custody procedures.
Comparative table
This table compares EviOTP HSM PGP to common OTP storage and authentication categories. Entries labeled “varies by model” reflect differences in feature sets, deployment modes, and administrative choices.
| Capability | EviOTP HSM PGP | KeePassXC | WinAuth | OTPClient | Nitrokey (OTP USB) | SoloKeys (FIDO2/U2F) | Thales CipherTrust Manager |
|---|---|---|---|---|---|---|---|
| TOTP / HOTP support | Yes | Yes (where configured) | Yes | Yes | Varies by model | No (FIDO2/U2F, not OTP) | Not an OTP manager (key management platform) |
| Offline operation | Yes | Yes | Yes | Yes | Yes (device-generated) | Varies by relying service | Typically no (enterprise service deployment) |
| Serverless by design | Yes | Yes (local vault file) | Yes | Yes | Yes (hardware-bound) | Varies by relying service (authentication is local, account lifecycle is external) | No (platform architecture) |
| Segmented-key storage (two locations) | Yes | No | No | No | Hardware-bound, not split | Hardware-bound, not split | Varies by deployment |
| RAM-only decryption claim | Yes (as described) | Varies by workflow | Varies by workflow | Varies by workflow | Not applicable (device) | Not applicable (device) | Varies by architecture |
| Domain integrity check before OTP injection | Yes (container URL binding) | No (depends on plugins/workflows) | No | No | No | Phishing-resistant auth by design (not OTP injection) | Not applicable (platform) |
| Encrypted container sharing | Yes (PGP AES-256 CBC + passphrase) | Varies by sharing method | Limited / manual | Limited / manual | No (device secret handling differs) | No (credential remains on device) | Varies by policy |
| Account creation and telemetry dependency | None required | None required | None required | None required | None required | None required (service may differ) | Enterprise administration varies |
Interpretation note: some columns represent product families or security platforms rather than pure OTP managers; feature availability therefore varies by deployment model and operational configuration.
Legal and regulatory alignment
GDPR principles applied by architecture
- Data minimization: The workflow does not require account creation or centralized user profiles for OTP storage operations.
- Privacy by design: Containers remain encrypted at rest; decryption occurs only in RAM during use, reducing cleartext persistence risk.
- Purpose limitation: OTP secrets exist to authenticate; the design avoids incidental collection channels such as cloud sync telemetry.
Reference: Regulation (EU) 2016/679 (GDPR): https://eur-lex.europa.eu/eli/reg/2016/679/oj
Standards and technical references
- TOTP: RFC 6238 — https://www.rfc-editor.org/rfc/rfc6238
- HOTP: RFC 4226 — https://www.rfc-editor.org/rfc/rfc4226
- OpenPGP: RFC 4880 — https://www.rfc-editor.org/rfc/rfc4880
- AES: NIST overview — https://www.nist.gov/cryptographic-standards-and-guidelines/aes
Scope note
This section cites public references for protocols and primitives. It does not claim external certification. Instead, it maps the design claims to established technical baselines and to data protection principles.
FAQ
Is EviOTP HSM PGP a standalone product?
No. The OTP manager capability powered by EviOTP HSM PGP is embedded in the PassCypher HSM PGP desktop application.
Which OTP standards does it support?
It supports TOTP and HOTP as defined by RFC 6238 and RFC 4226.
Where does the system store OTP secrets?
It stores each secret inside a small PGP AES-256 CBC encrypted container. The design splits decryption material across browser local storage and operator-controlled external media.
Does it require a master password?
No centralized master password is required by the architecture. However, when the operator shares containers, they can define a passphrase for transfer protection.
Can it work without internet access?
Yes. The workflow targets offline operation and does not require cloud services for OTP generation and use.
What prevents a stolen container from being used immediately?
The split-key condition blocks decryption if the attacker lacks one segment. Additionally, URL binding can block OTP injection on mismatched domains.
What does “decryption only in RAM” mean operationally?
The application decrypts the container only during the active OTP operation and then destroys decrypted material after injection, so routine use avoids writing cleartext secrets to disk.
Does it protect against phishing?
It can reduce OTP release on look-alike pages by validating domain integrity against the original login URL embedded in the container. Nonetheless, the operator must still verify context and intent.
How does sharing work without a server?
The operator can encrypt containers with a user-defined passphrase and move them via portable storage, QR-based transfer workflows, or air-gapped channels.
Can the operator duplicate containers for resilience?
Yes. Because containers remain encrypted, duplication supports continuity while preserving encrypted-at-rest conditions.
Does the design assume the host is untrusted?
Yes. The design avoids persistent decrypted storage on the host and relies on segmented storage to reduce the value of endpoint data theft.
Is Linux supported?
The provided specification states availability for Windows and macOS. If Linux support exists in a specific integration, document it explicitly in that release context.
Glossary
- AES-256 CBC: A symmetric encryption construction using AES with a 256-bit key in Cipher Block Chaining mode.
- Air gap: A transfer or operation method that avoids network connectivity between systems.
- Browser local storage: A browser-provided client-side storage mechanism used here to hold one decryption segment.
- Container: A small encrypted object that encapsulates an OTP secret and related operational metadata.
- Decryption segment: A portion of decryption material required to unlock a container; the design requires at least two segments.
- Domain integrity check: A validation step that compares the active login domain to the reference domain embedded in the container.
- HOTP: HMAC-Based One-Time Password algorithm standardized in RFC 4226.
- Injection: The controlled action of entering an OTP into a login flow after validating release conditions.
- OpenPGP / PGP containerization: Use of OpenPGP-compatible formats and concepts to package and protect encrypted data.
- Passphrase: A user-defined secret used to protect containers during sharing or transfer.
- RAM-only operation: A runtime behavior where decrypted material exists only in volatile memory for the shortest necessary time.
- Segmented-key architecture: A design where required decryption material is split across independent locations to enforce separation.
- Serverless: An operational model that does not require a central server to store or synchronize OTP secrets.
- Telemetry: Automated collection of usage or device data; the stated model does not require it for OTP operations.
- TOTP: Time-Based One-Time Password algorithm standardized in RFC 6238.
- Typosquatting: A phishing tactic using look-alike domains to capture credentials and OTPs.
Sovereign operational use case
An incident responder isolates a workstation after detecting an infostealer. The attacker exfiltrates files, browser data, and screenshots. However, the responder has enforced segment separation: one segment remains in browser local storage on the isolated workstation, while the external segment remains under physical custody on removable media. As a result, the stolen encrypted containers do not yield OTP secrets in isolation.
Next, the responder rebuilds a clean workstation, restores only encrypted containers, and reintroduces the external segment under controlled procedures. Then, they authenticate to recovery portals while the domain integrity check blocks OTP injection into look‑alike pages generated during the breach. Consequently, the responder sustains access for containment and restoration, while limiting the operational blast radius of stolen data to encrypted artifacts that remain unusable without the missing segment and the correct domain context.

Pingback: Tycoon 2FA failles OAuth persistantes dans le cloud | PassCypher HSM PGP
Pingback: Persistent OAuth Flaw: How Tycoon 2FA Hijacks Cloud Access - Freemindtronic