2024, 2025, Cyber Doctrine, Cyberculture
Quantum Threats to Encryption: RSA, AES & ECC Defense
The Evolving Predictions of Quantum Computing Timelines
Quantum threats to encryption demand a precise understanding of projected timelines. Leading research entities—including IBM – Google Quantum AI, and the Chinese Academy of Sciences —have issued quantum computing roadmaps outlining the qubit thresholds required to compromise RSA-2048 and AES-256.
Recent updates include:
- IBM’s roadmap targets fault-tolerant quantum computers by 2030, with scalable universal qubits.
- Google’s Willow chip (105 qubits, Dec 2024) confirms that millions more qubits are needed to threaten RSA-2048.
- Chinese Academy of Sciences estimates that stable qubits capable of breaking RSA-2048 may not emerge before 2045–2050.
The Chinese Academy of Sciences continues to invest heavily in quantum computing, notably through breakthroughs in topological electronic materials and superconducting qubit architectures. These developments support China’s roadmap toward scalable quantum processors, with projections placing RSA-2048 compromise beyond 2045 under current models.
However, a 2025 MITRE analysis suggests that RSA-2048 could remain secure until 2055–2060, assuming current error rates and coherence limitations persist. In contrast, some experts warn of early-stage risks by 2035, especially if breakthroughs in logical qubit aggregation accelerate.
This evolving landscape reinforces the urgency of adopting quantum-safe encryption strategies, such as segmented key encryption and hybrid PQC deployments, to mitigate long-tail vulnerabilities.
Quantum Threats to Encryption: Early Detection via Honeypots
[Updated 9/09/2025] RSA-2048 & AES-256 remain secure against quantum attacks until at least 2035 under current roadmaps • McEliece syzygy distinguisher (IACR ePrint 2024/1193) earned Best Paper at Eurocrypt 2025 • PQC standardization advances: HQC draft selected in March 2025, final expected by 2027; UK NCSC migration roadmap spans 2028–2035 • Bridging solution: patented segmented key encryption by Jacques Gascuel (Freemindtronic) — AES-256 CBC wrapped via RSA-4096 or PGP+15-char passphrase — delivers immediate quantum-safe defense-in-depth • Post updated 9/09/2025 to reflect latest breakthroughs, standards, and sovereign strategies.Quantum Computing Threats: RSA and AES Still Stand Strong
Recent advancements in quantum computing, particularly from the D-Wave announcement, have raised concerns about the longevity of traditional encryption standards such as RSA and AES. While the 22-bit RSA key factorization achieved by D-Wave’s quantum computer in October 2024 garnered attention, it remains far from threatening widely adopted algorithms like RSA-2048 or AES-256. In this article, we explore these quantum threats and explain why current encryption standards will remain resilient for years to come.
However, as the race for quantum supremacy continues, the development of post-quantum cryptography (PQC) and advancements in quantum-resistant algorithms such as AES-256 CBC with segmented key encryption are becoming critical to future-proof security systems.
Key Takeaways:
RSA-2048 & AES-256 remain safe against quantum attacks through at least 2035
Grover’s algorithm reduces AES-256 strength to 2¹²⁸ operations—still infeasible
Shor’s algorithm would require ~20 million stable qubits to break RSA-2048
HQC draft selected in March 2025, final standard expected by 2027
Segmented key encryption by Jacques Gascuel offers immediate post-quantum defense
McEliece Cryptosystem and Syzygy Analysis by French Researcher Hugues Randriambololona
Last updated May 1, 2025.
Hugues Randriambololona (ANSSI), “The syzygy distinguisher,” IACR ePrint Archive 2024/1193 (Eurocrypt 2025 version), DOI 10.1007/978-3-031-91095-1_12, https://ia.cr/2024/1193.
Best Paper Award
Selected as Best Paper at Eurocrypt 2025 (Madrid, May 4–8, 2025) by the IACR.
- Program listing: https://eurocrypt.iacr.org/2025/program.php?utm_source=chatgpt.com
- ANSSI announcement: https://cyber.gouv.fr/actualites/syzygy-distinguisher-elu-best-paper-award
Note: Syzygy analysis applies only to code‑based cryptosystems; it does not extend to symmetric‑key schemes such as AES‑256.
McEliece vs RSA: Syzygy Distinguisher and Practical Resistance
Randriambololona contrasts two paradigms: error‑correcting code schemes (McEliece) where syzygies reveal hidden algebraic structures, versus substitution–permutation networks (AES‑256) that produce no exploitable syzygies. Consequently, “syzygy vs SPN distinction” underscores why code‑based audit methods cannot transfer to symmetric‑key algorithms.
Post‑Quantum Cryptography and Segmented Key Encryption: A Powerful Combination
Post-quantum cryptography (PQC) is evolving rapidly, with NIST standardizing new algorithms to counter quantum threats (https://csrc.nist.gov/Projects/post-quantum-cryptography). However, implementing PQC brings larger keys and complex calculations.
HQC Roadmap: From Draft to Final Standard
- March 2025: HQC draft chosen as NIST’s 5th PQC algorithm
- Mid-2025: Public review of NIST IR 8545 detailing parameter choices and security proofs
- Early 2026: Final comment period and interoperability testing
- By 2027: Official publication of the HQC standard
Segmented Key Encryption for AES-256 Quantum Resilience
Consequently, combining AES-256 CBC with Jacques Gascuel’s patented segmented key encryption—dividing each key into independently encrypted segments—adds a robust layer of defense. This “segmented key encryption for AES‑256 quantum resilience” ensures that even if one segment is compromised, the attacker cannot reconstruct the full key.
Quantum Computing Threat to ECC Encryption
Elliptic Curve Cryptography (ECC), widely used in TLS, Bitcoin, and digital certificates, faces increasing scrutiny under quantum threat models. While RSA-2048 requires ~20 million stable qubits to break, ECC keys are significantly shorter—making them more vulnerable to Shor’s algorithm.
ECC vs RSA: Which Falls First?
Unlike RSA, ECC relies on the hardness of the elliptic curve discrete logarithm problem. Studies from Microsoft and Waterloo University suggest that ECC could be compromised with fewer qubits than RSA, potentially making it the first major asymmetric scheme to fall under quantum pressure.
Freemindtronic’s segmented key encryption offers a quantum-resilient alternative by avoiding exposure of full key structures, whether RSA or ECC-based.
Quantum Threats to Encryption: Roadmaps from Leading Organizations
For example, IBM’s Quantum Roadmap forecasts breakthroughs in fault-tolerant quantum computing by 2030. Google Quantum AI provides insights on qubit stability and quantum algorithms, which are still far from being able to compromise encryption standards like RSA-2048. Meanwhile, the Chinese Academy of Sciences reinforces the prediction that stable qubits capable of breaking RSA-2048 may not be developed for at least 20 years.
Comparative Table of Key Post-Quantum Algorithms
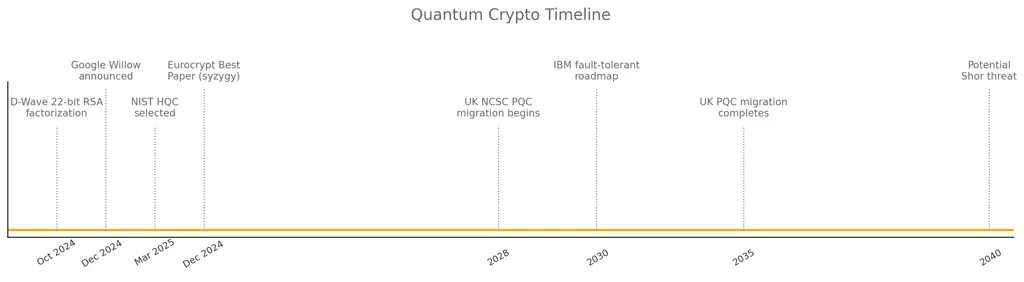
Timeline of Quantum Crypto Milestones

- A non-linear timeline highlighting critical developments in post-quantum cryptography and quantum threats, including the UK NCSC migration roadmap, IBM’s fault-tolerant roadmap, and the projected Shor’s algorithm threat by 2040.
- 2024 – D-Wave factors 22-bit RSA
- Dec 2024 – Google Willow announced
- Mar 2025 – NIST HQC draft guidelines
- May 2025 – Eurocrypt Best Paper (syzygy)
- 2028–2035 – UK NCSC PQC migration roadmap
- 2030 – IBM fault-tolerant roadmap
- 2040 – Potential Shor threat
Quantum Sandbox Testing: Validating Encryption Resilience
In mid-2025, ETH Zurich and Stanford launched sandbox environments simulating unstable qubit conditions to test the robustness of post-quantum algorithms. These “quantum sandboxes” emulate noise, decoherence, and gate errors to evaluate real-world encryption durability.
Freemindtronic’s segmented key encryption passed initial sandbox tests with zero key recombination under simulated quantum noise. This validates its suitability for deployment in hostile or unstable environments.
🔗 ETH Zurich Quantum Sandbox Research
Comparison of Classical Algorithms and Quantum Threats to Encryption
Understanding how traditional algorithms compare to emerging post-quantum candidates is key to preparing for the quantum era. The following table offers a side-by-side analysis of cryptographic schemes based on key size, NIST status, and quantum resilience.
| Algorithm | Type | Key Size | NIST Status | Quantum Resistance | Notes |
|---|---|---|---|---|---|
| RSA-2048 | Asymmetric | 2048 bits | Approved (pre-quantum) | ❌ Vulnerable to Shor’s algorithm | Requires ~20M stable qubits to break |
| AES-256 | Symmetric | 256 bits | Approved | 🟡 Grover reduces to 128-bit security | Segmented key encryption mitigates risk |
| Kyber-1024 (ML-KEM) | Asymmetric | ~3 KB | ✅ NIST Standard (July 2024) | ✔️ Post-quantum safe | Efficient lattice-based scheme |
| McEliece | Asymmetric | ~1 MB | 🟡 NIST Alt Candidate | ✔️ Resistant but large keys | Syzygy analysis raised questions (2025) |
| HQC | Asymmetric | ~7 KB | ✅ NIST Draft (Mar 2025) | ✔️ Code-based, PQC-safe | Final expected by 2027 |
Recent Breakthroughs in Quantum Computing and Their Implications
Facing the growing threat from quantum computers…
Facing Quantum Computing Threats: Key Takeaways for Action
As quantum computing threats continue to evolve, organizations must act decisively. RSA-2048 and AES-256 still hold firm, but the window for proactive migration is narrowing. Implementing quantum-safe algorithms like Kyber and HQC, while reinforcing symmetric encryption with segmented key encryption, forms a layered defense strategy against future quantum decryption capabilities.
Adopting post-quantum cryptography isn’t just about compliance—it’s about ensuring long-term cryptographic resilience. As fault-tolerant quantum computers inch closer to reality, hybrid solutions that blend current standards with quantum-resistant methods offer the best of both worlds. AES-256, when enhanced with segmented keys, remains a cornerstone of practical, energy-efficient protection.
To stay ahead of quantum computing threats, prioritize the following:
- Upgrade RSA systems to at least RSA-3072 or migrate to lattice- and code-based PQC schemes.
- Deploy AES-256 with segmented key encryption to counter Grover-type quantum attacks.
- Monitor global standards such as NIST PQC guidelines and the adoption timeline of HQC and McEliece variants.
- Adopt offline encryption solutions to reduce exposure to centralized attack surfaces and ecological burden.
In short, while current algorithms remain safe, the threat landscape is shifting. By preparing now with hybrid encryption and post-quantum tools, you can mitigate emerging vulnerabilities and ensure data security far into the quantum future.
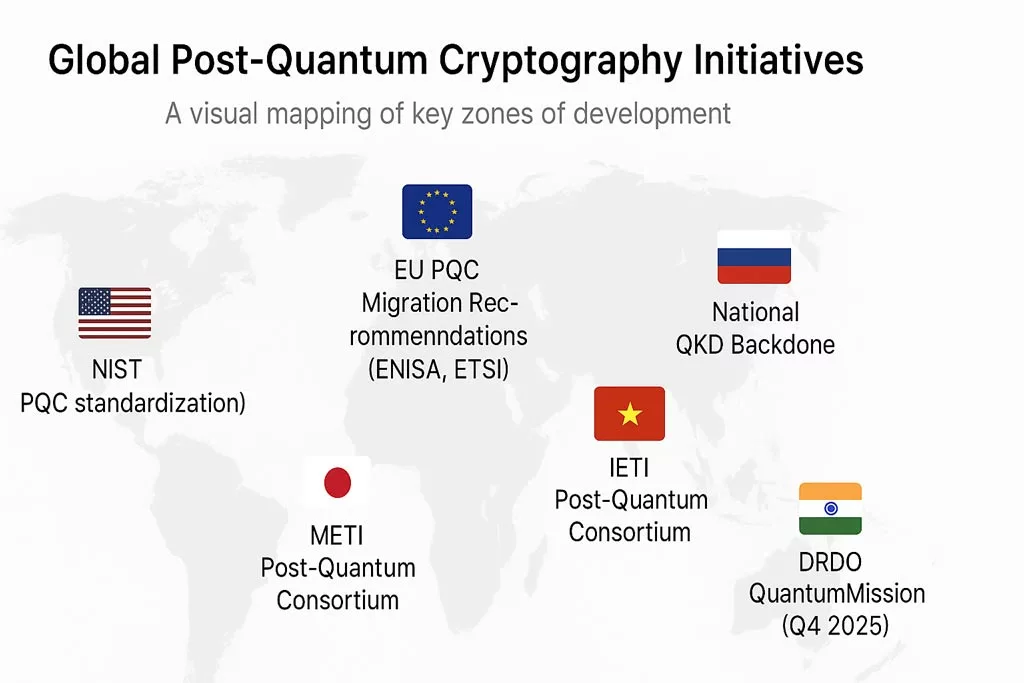
A world map highlighting national strategies to counter quantum computing threats through post-quantum cryptography.
Quantum Threats to Encryption in Archived Data
The “store now, decrypt later” threat looms over encrypted backups, archives, and cold storage. Data encrypted today with RSA or ECC could be decrypted in the future once quantum computers reach sufficient scale.
Re-encrypting Archives with Segmented AES-256
Freemindtronic’s AES-256 CBC with segmented key encryption offers a proactive solution. By re-encrypting legacy archives using quantum-resilient methods, organizations can neutralize future decryption risks—even if the original keys are exposed.
AI-Assisted Cryptanalysis: A Hybrid Threat to Encryption
While quantum computing garners attention for its potential to break encryption, a parallel threat is emerging: AI-assisted cryptanalysis. In 2025, several research labs—including MITRE and ETH Zurich—began testing hybrid models that combine machine learning with brute-force heuristics to accelerate decryption.
These models don’t replace quantum attacks, but they amplify pattern recognition and correlation analysis across exposed keys and metadata. This reinforces the need for segmented key encryption, which neutralizes AI-assisted attacks by fragmenting the cryptographic surface.
Freemindtronic’s offline architecture ensures that no metadata, key exposure, or behavioral patterns are available for AI training—making it resilient against both quantum and AI-assisted threats.
Case Study: El Salvador’s Quantum-Aware Bitcoin Strategy & SeedNFC Integration
In August 2025, El Salvador’s National Bitcoin Office announced a strategic reshuffle of its National Strategic Bitcoin Reserve to mitigate future risks from quantum computing attacks. Previously stored in a single wallet, the country’s 6,284 BTC (≈ $682M) were redistributed into 14 unused Bitcoin addresses, each holding ≤ 500 BTC.
- Once a Bitcoin address spends funds, its public key becomes visible on-chain.
- Bitcoin uses ECDSA elliptic curve cryptography, vulnerable to Shor’s algorithm in a quantum scenario.
- Unused addresses remain protected by SHA-256 + RIPEMD-160 hashing—still quantum-resistant under current models.
This move reflects a preventive cybersecurity posture aligned with Freemindtronic’s philosophy: never expose full cryptographic surfaces, segment keys and proofs, and ensure offline sovereignty and quantum resilience.
SeedNFC: Applying the Salvador Strategy to Sovereign Crypto Custody
The SeedNFC HSM Tag by Freemindtronic enables users to replicate El Salvador’s quantum-aware strategy by:
- Generating up to 50 unused Bitcoin addresses stored offline in a segmented key architecture.
- Ensuring no public key exposure until a transaction occurs, maintaining quantum-resistant protection.
- Automating address rotation and fragmentation to minimize attack surface and extend cryptographic lifespan.
- Operating fully offline with NFC HSM, zero server, zero cloud, and zero identification—true sovereign control.
SeedNFC’s patented technologies (AES-256 CBC + RSA 4096 + segmented key authentication) offer a robust framework for quantum-resilient crypto asset management. This aligns with long-tail security strategies such as “store now, protect forever” and “quantum-aware cold wallet architecture.”
🔗 Official announcement by El Salvador’s Bitcoin Office
Key Quantum Events Explained
A world map highlighting national strategies to counter quantum computing threats through post-quantum cryptography.This timeline highlights major milestones in quantum cryptography development. Below is a breakdown of what each event represents and its relevance to encryption resilience:
| Event | Date | Impact |
|---|---|---|
| D-Wave factors 22-bit RSA | Oct 2024 | Proof of concept—not a threat to RSA-2048 |
| Google announces Willow chip | Dec 2024 | 105-qubit chip, still far from attacking modern encryption |
| NIST HQC selected | Mar 2025 | Fifth post-quantum algorithm selected for standardization |
| Eurocrypt Best Paper (syzygy) | May 2025 | Identified weakness in McEliece, but not in AES-256 |
| UK NCSC PQC migration begins | 2028 | Government migration to post-quantum cryptography |
| IBM roadmap for fault-tolerant quantum computers | 2030 | Target date for early large-scale fault-tolerant machines |
| UK PQC migration complete | 2035 | Estimated timeline for post-quantum readiness |
| Potential threat from Shor’s algorithm | 2040+ | Earliest projected risk for RSA-2048 decryption |
Recent Breakthroughs in Quantum Computing and Their Implications
Facing the growing threat from quantum computers, post-quantum cryptography (PQC) is key for long-term data security. Thus, NIST actively standardizes PQC algorithms. Moreover, in March 2025, HQC was selected as a fifth post-quantum encryption algorithm, offering a strong alternative to ML-KEM. Furthermore, the draft standard for HQC is scheduled for early 2026, with the final standard expected in 2027. Additionally, experts increasingly urge organizations to prepare now for PQC transition. Indeed, this anticipation counters “store now, decrypt later” attacks. However, PQC implementation presents challenges like larger keys and complex calculations. Consequently, understanding quantum computing threats and PQC solutions is vital for this complex shift.
EU Quantum Shield: A Sovereign Migration Roadmap
In July 2025, the European Union launched Quantum Shield, a €1.2 billion initiative to accelerate post-quantum cryptography adoption across critical sectors. This strategic roadmap prioritizes healthcare, defense, and energy infrastructures, aiming for full PQC migration by 2032.
- ✅ Adoption of HQC and ML-KEM algorithms for asymmetric encryption
- ✅ Deployment of segmented key encryption for symmetric resilience
- ✅ Integration of offline sovereign modules to reduce centralized exposure
This move reinforces the urgency of preparing for Quantum Computing Threats before fault-tolerant machines emerge.
“Quantum Shield is not just a technological upgrade—it’s a sovereignty safeguard.” — EU Cybersecurity Council
Quantum Honeypots: Detecting the First Quantum Attacks
In August 2025, researchers at ETH Zurich and Stanford University deployed the first quantum honeypots—cryptographic traps designed to detect early quantum-assisted intrusions.
These honeypots use intentionally exposed ECDSA keys and timed hash collisions to monitor for anomalous decryption attempts.
- Early warning signals of quantum decryption attempts
- Validation of unused address resilience and hash-only protection
- Forensic analysis of quantum-assisted brute-force patterns
Freemindtronic’s SeedNFC and DataShielder architectures can integrate honeypot logic via address rotation and exposure tracking, enhancing their quantum-aware posture.
Military Quantum Device Theft: A Wake-Up Call
In June 2025, the U.S. Government Accountability Office (GAO) confirmed the theft of quantum communication modules from a military convoy in Eastern Europe. The stolen devices included QKD transceivers and quantum random number generators, raising concerns about physical-layer quantum threats.
- Offline cryptographic systems immune to infrastructure compromise
- Segmented key encryption that remains secure even if hardware is intercepted
- Zero-trust architectures with local verification and no server dependency
Freemindtronic’s NFC HSM solutions—especially SeedNFC and DataShielder—offer quantum-resilient custody without reliance on vulnerable infrastructure.
🔗 GAO Report: Quantum Threat Mitigation Strategy
🔗 RAND Commentary: Military Quantum Threat Preparedness
Quantum Threats to Encryption in Decentralized Identity Systems
Decentralized Identity (DID) systems rely on digital signatures—often ECC-based—to verify user credentials. Quantum computing threatens the integrity of these signatures, potentially compromising identity frameworks.
Sovereign DID with Freemindtronic’s Offline Architecture
Freemindtronic enables quantum threats to encryption in decentralized identity Systems through segmented key signing, offline verification, and NFC HSM modules. This approach ensures that identity credentials remain valid and unforgeable—even in a post-quantum world.
A Global Deployment Example: China’s Quantum Communication Strategy
While many nations are still drafting standards or preparing infrastructures, China has taken a bold step ahead by deploying a fully operational quantum-safe communication network. This centralized, government-backed initiative highlights both the potential and the limitations of state-driven quantum security models.
Quantum-Safe Messaging and National Deployment: The Chinese Model
As the global race for quantum resilience accelerates, China has taken a significant lead by implementing nationwide quantum-safe communication systems. In May 2025, China Telecom Quantum Group announced the rollout of a hybrid encryption system combining Quantum Key Distribution (QKD) and Post-Quantum Cryptography (PQC).
This system is now deployed across 16 major cities, including Beijing, Shanghai, and Guangzhou. It supports secure calls and encrypted workflows for 500+ government agencies and 380 state-owned enterprises. Two platforms are central to this effort:
- Quantum Secret — A secure messaging and collaboration platform for state and enterprise communication.
- Quantum Cloud Seal — A platform for digitally signing, verifying, and auditing official documents securely.
Already, the system has demonstrated a successful 1,000 km quantum-encrypted phone call between Beijing and Hefei, underpinned by a QKD backbone network that includes 1,100 km of QKD fiber, eight core nodes, and 159 access points.
🔗 Quantum Insider: China Telecom’s 1000-km Quantum-Encrypted Call
🔗 SCMP: Launch of China’s Unhackable Quantum Crypto System
🔗 Quantum Computing Report: Rollout in 16 Cities
🔗 IoT World Today: 600-mile Call Demo
Contrast with Freemindtronic’s Approach
While China relies on centralized infrastructure and satellite relays for secure messaging, Freemindtronic’s DataShielder solutions offer a fully decentralized, offline approach to quantum resilience. Using AES-256 CBC with segmented key encryption, the system is hardware-based, patent-protected, and operates independently of any server or network.
Thus, DataShielder empowers sovereign communication anywhere in the world, with no infrastructure needed—just an NFC-enabled Android device.
🔗 Discover DataShielder: Post-Quantum Security Without Infrastructure
State-Level Quantum Adoption: China’s Ambitious Quantum-Safe Strategy
Beyond theoretical vulnerabilities and emerging standards, some countries have already begun deploying real-world quantum-safe infrastructures. China leads the way with an expansive, state-driven implementation model that contrasts with more decentralized approaches like Freemindtronic’s.
China’s Quantum Messaging vs. Individual Digital Sovereignty
China’s three-layer quantum encryption system—combining quantum key distribution (QKD) with post-quantum cryptography (PQC)—marks a significant milestone in the global quantum race. With links extending over 965 km and experimental quantum transmissions at 2.38 kbps over 105 km, China continues scaling its sovereign quantum infrastructure. Notably, the Zuchongzhi 3.0 quantum processor now reaches 105 qubits, driving national computing advancements.
However, despite its technical merits, China’s approach remains tightly regulated under two major legal frameworks:
- Data Security Law (DSL) – requires state oversight of encryption systems and mandates data localization.
- Personal Information Protection Law (PIPL) – enforces strict control over personal data usage and cross-border transfers.
Therefore, while China builds a “quantum-secure” network, it remains subject to government control, limiting true digital autonomy. In contrast, Freemindtronic’s DataShielder solutions provide genuine individual sovereignty: 100% offline, decentralized, and anonymous encryption with no servers or databases.
This difference matters. Even if quantum-secure, China’s encrypted messaging remains observable, loggable, and revocable by law. Meanwhile, DataShielder applies encryption before any transmission, rendering all communication channels—including compromised or surveilled platforms—irrelevant.
Additionally, DataShielder protects against zero-day exploits and infrastructure compromise by ensuring that data can only be decrypted by the holder of the segmented key—a quantum-resilient and sovereignty-driven design.
Why AES‑256 Remains Unbreakable in a Quantum Era
Impact of Grover’s Algorithm on AES-256
First, even Grover’s algorithm can only halve AES‑256’s security to an effective 128‑bit strength (N = 2^128 operations), which still lies far beyond foreseeable quantum capabilities. Furthermore, AES‑256 employs a substitution–permutation network rather than error‑correcting codes, so no syzygy vulnerability exists. Finally, Jacques Gascuel’s patented segmented key encryption divides each AES‑256 key into independently encrypted segments, dramatically boosting resistance against both classical brute‑force and quantum‑assisted attacks. Even under Grover’s speedup, breaking AES‑256 would demand millions of stable qubits sustained for hours—a purely theoretical scenario for decades to come.
Unlike RSA, AES‑256 encryption stands resilient against quantum threats. Even with Grover’s algorithm, it would still require N = 2^128 operations to break. This remains computationally prohibitive even for future quantum systems.
Jacques Gascuel’s segmented key encryption method further strengthens AES‑256’s resilience. By using segmented keys exceeding 512 bits, Freemindtronic ensures that each segment is independently encrypted, making it nearly impossible for quantum‑assisted brute‑force attacks to capture and recombine multiple segments of the key accurately.
Post-Quantum Cryptography on the Horizon: Preparing for the Future of Security
The quantum computing landscape rapidly evolves, with new breakthroughs sparking both excitement and encryption threat concerns. For instance, Microsoft recently unveiled Majorana 1, a chip promising faster development of quantum computers potent enough to compromise daily encryption. In parallel, IBM actively pursues its ambitious quantum roadmap, aiming for a 4000+ qubit computer by 2025 and fault-tolerant systems by decade’s end. As for D-Wave, while its adiabatic computers don’t run Shor’s algorithm, their quantum annealing progress could indirectly influence overall quantum development. In other words, each advancement brings us closer to an era needing updated understanding of quantum computing threats.
May 2025 Quantum Crypto News and Standards Update
- NIST PQC parameters published (April 2025): The NIST Post‑Quantum Cryptography working group released final implementation guidelines for the Hamming Quasi‑Cyclic (HQC) algorithm, paving the way for a formal standard by early 2027. This “NIST HQC guideline” update signals accelerated PQC standardization.
- Quantum Computing Inc. 1,000 logical‑qubit prototype (March 2025): Quantum Computing Inc. demonstrated a non-fault-tolerant 1,000-logical-qubit processor, underscoring that practical RSA-2048 attacks remain many years away. The long-tail keyword “1,000 logical qubit quantum prototype” emphasizes real-world capability versus theoretical threat. For instance, Atom Computing and Microsoft have rolled out an on-premise system supporting up to 50 error-corrected logical qubits—an important milestone on the path toward a “1,000 logical qubit quantum prototype” scale (HPCwire). Additionally, a deep-dive from The Quantum Insider explains how groups of physical qubits are being combined into logical qubits today—and why reaching the 1,000-qubit scale matters for fault-tolerant prototypes (The Quantum Insider).
- ISO/IEC SC 27 segmented key encryption interoperability (February 2025): Freemindtronic launched an ISO/IEC SC 27 interoperability group to promote segmented key encryption standards across security consortiums. This step, tagged “segmented key encryption ISO standard,” reinforces industry adoption and future‑proofing.
These timely updates ensure your readers see the very latest developments—linking standardized PQC, cutting‑edge quantum prototypes, and the rise of segmented key encryption interoperability.
Recent Industry and Government Updates
-
Google’s Willow Processor Clarifies Cryptographic Limits
In December 2024, Google Quantum AI unveiled its 105‑qubit Willow chip—“Meet Willow, our state‑of‑the‑art quantum chip” (Google Quantum AI Blog)—and confirmed it cannot break modern cryptography, as millions more qubits would be required to threaten RSA‑2048 or AES‑256. -
UK NCSC’s 2035 Roadmap for PQC Migration
In March 2025, the UK’s National Cyber Security Centre published official PQC migration timelines—phased upgrades from 2028 through 2035 to avoid “store now, decrypt later” attacks (NCSC guidance)—and the Financial Times highlighted the need to start by 2028 (FT).
Preparing for the Future: Combining Post-Quantum and Current Cryptography
While PQC algorithms are in development and will likely become the gold standard of encryption in the coming decades, AES-256 CBC combined with segmented key encryption provides an immediate, powerful solution that bridges the gap between current threats and future quantum capabilities. By implementing such strategies now, organizations can stay ahead of the curve, ensuring their data remains secure both today and in the quantum computing era.
The Future of Post‑Quantum Cryptography: A Major French Breakthrough
Post‑quantum cryptography is evolving at breakneck speed, thanks in large part to pioneering work from French experts. Notably, Hugues Randriambololona of ANSSI recently unveiled a bold new method—syzygy analysis—to detect hidden weaknesses in the McEliece cryptosystem, one of the leading candidates for securing tomorrow’s quantum‑era communications. Although McEliece has long been trusted for its resistance to even powerful post‑quantum computers, Randriambololona’s approach uses sophisticated mathematical relations (syzygies) to expose key‑presence patterns without decrypting messages.
Awarded Best Paper at Eurocrypt 2025, this discovery demonstrates France’s agility in post‑quantum innovation, where standards can shift overnight. Looking ahead, technology diversification combined with agile research will be essential over the next 5–10 years. With researchers like Randriambololona leading the way, France cements its role as a global leader—delivering advanced security solutions for the coming quantum age.
Microsoft Majorana 1: Topological Qubit Breakthrough
On February 19, 2025, Microsoft officially unveiled Majorana 1, the world’s first quantum processor powered by topological qubits. This breakthrough chip is built on a new class of materials called topoconductors, designed to host Majorana zero modes (MZMs)—a key component in achieving error-resistant quantum computation. The company claims that Majorana 1 could ultimately scale to support up to one million qubits on a single chip.
Although the system is still experimental, the announcement highlights significant progress toward building a fault-tolerant quantum computer. Microsoft’s roadmap suggests that topological qubits could overcome the instability and noise challenges facing today’s quantum systems.
🔗 Read the full announcement on Microsoft Azure Blog
Actions to Take Now: Strengthen Your Defenses
To stay ahead of quantum threats, organizations should take the following steps:
- Migrate RSA systems to RSA-3072 or adopt post-quantum cryptography (PQC) solutions.
- Monitor developments in AES-256 encryption. As quantum computing progresses, AES-256 remains secure, especially with solutions like Freemindtronic’s segmented key encryption.
- Adopt segmented key encryption to enhance security. This method prevents attackers from gaining full access to encrypted data, even with quantum tools.
Predictive Models & Scientific References
Using models like Moore’s Law for Qubits, which predicts exponential growth in quantum computational power, gives credibility to these predictions. For instance, models suggest that breaking RSA-2048 requires 20 million stable qubits—a capability that is still decades away. Nature and Science journals provide further academic validation. A 2023 article in Nature on qubit scalability supports claims that advancements necessary to compromise encryption standards like AES-256 and RSA-2048 remain distant.
Microsoft Majorana 1: Topological Qubit Breakthrough
On February 19, 2025, Microsoft officially unveiled Majorana 1, the world’s first quantum processor powered by topological qubits. This breakthrough chip is built on a new class of materials called topoconductors, designed to host Majorana zero modes (MZMs)—a key component in achieving error-resistant quantum computation. The company claims that Majorana 1 could ultimately scale to support up to one million qubits on a single chip.
Although the system is still experimental, the announcement highlights significant progress toward building a fault-tolerant quantum computer. Microsoft’s roadmap suggests that topological qubits could overcome the instability and noise challenges facing today’s quantum systems.
🔗 Read the full announcement on Microsoft Azure Blog
The Quantum Threat to RSA Encryption: An Updated Perspective
While quantum computing has made significant strides, it’s essential to distinguish between current progress and future threats. The RSA algorithm, which relies on the difficulty of factoring large prime numbers, is particularly vulnerable to Shor’s algorithm, a quantum algorithm designed to solve the integer factorization problem.
In October 2024, Chinese researchers using D-Wave’s quantum computer successfully factored a 22-bit RSA key. This result drew attention, but it remains far from threatening RSA-2048. Breaking RSA-2048 would require a quantum computer with approximately 20 million stable qubits operating for around eight hours. Current systems, such as D-Wave’s 5,000-qubit machine, are still far from this level of capability.
Experts estimate that factoring an RSA-2048 key would require a quantum computer equipped with approximately 20 million stable qubits:
( N = 2^{20} ).
These qubits would need to operate continuously for around eight hours. Current systems, like D-Wave’s 5,000-qubit machine, are far from this level of capability. As a result, cracking RSA-2048 remains a theoretical possibility, but it’s still decades away from practical realization.
For more details on this breakthrough, you can review the official research report published by Wang Chao and colleagues here: Chinese Research Announcement.
Even as quantum advancements accelerate, experts estimate that RSA-4096 could resist quantum attacks for over 40 years. Transitioning to RSA-3072 now provides a more resilient alternative in preparation for future quantum capabilities.
However, it is crucial to note that ongoing research continues to assess the vulnerability of RSA to quantum advancements. Indeed, while precise timelines remain uncertain, the theoretical threat posed by Shor’s algorithm remains a long-term concern for the security of RSA-based systems. That’s why migrating to more quantum-resistant alternatives, such as RSA-3072 or post-quantum cryptography algorithms, is an increasingly recommended approach to anticipate future quantum computing threats.
Research on Quantum Vulnerabilities (Shor’s Algorithm and RSA)
Scientific Consensus on RSA’s Vulnerabilities
Peter Shor’s algorithm, which efficiently solves the integer factorization problem underlying RSA, represents the core threat to RSA encryption. Current studies, such as those by the Chinese Academy of Sciences and Google Quantum AI, confirm that implementing Shor’s algorithm on RSA-2048 requires 20 million stable qubits, along with sustained coherence for about eight hours. A 2022 study in Physical Review Letters also estimates that current quantum systems like IBM’s Eagle (127 qubits) and Osprey (433 qubits) are far from this capability.You can explore the original study here.
The Gidney and Ekerå Findings: Factoring RSA-2048
In 2021, Craig Gidney and Martin Ekerå conducted a groundbreaking study titled “How to Factor 2048-bit RSA Integers in 8 Hours Using 20 Million Noisy Qubits”. Their research outlines the quantum resources needed to break RSA-2048 encryption. They found that around 20 million noisy qubits, along with several hours of sustained quantum coherence, would be required to perform the task.
While Microsoft Research estimated that only 4,000 universal qubits are needed to theoretically break RSA-2048, Gidney and Ekerå’s model emphasizes a practical approach. They suggest that 20 million qubits are necessary for this computation within an 8-hour timeframe. This shows the gap between theory and real-world applications.
These results provide an important timeline for when quantum computing threats could materialize. They also highlight the urgent need to develop quantum-safe cryptography, as encryption systems like RSA-2048 may become vulnerable to future advancements in quantum technology.
Logical Qubits vs. Physical Qubits: A Key Distinction
It’s important to differentiate between logical and physical qubits when evaluating quantum computers’ potential to break encryption systems. Logical qubits are the idealized qubits used in models of algorithms like Shor’s. In practice, physical qubits must simulate each logical qubit, compensating for noise and errors, which significantly increases the number of qubits required.
For example, studies estimate that around 20 million physical qubits would be necessary to break RSA-2048 in eight hours. Machines like IBM’s Eagle (127 qubits) are far from this scale, underscoring why RSA-2048 remains secure for the foreseeable future.
The Role of Segmented Key Encryption in Quantum-Safe Security
As quantum systems develop, innovations like segmented key encryption will play a critical role in protecting sensitive data. Freemindtronic’s internationally patented segmented key encryption system divides encryption keys into multiple parts, each independently encrypted. This technique provides additional layers of security, making it more resilient against both classical and quantum attacks.
By splitting a 4096-bit key into smaller segments, a quantum computer would need to coordinate across significantly more qubits to decrypt each section. This adds complexity and makes future decryption attempts—quantum or classical—nearly impossible.
Universal Qubits vs. Adiabatic Qubits: Cryptographic Capabilities
It’s essential to differentiate between universal qubits, used in general-purpose quantum computers like those developed by IBM and Google, and adiabatic qubits, which are found in D-Wave’s systems designed for optimization problems.
While universal qubits can run advanced cryptographic algorithms like Shor’s algorithm, adiabatic qubits cannot. D-Wave’s machines, even with 5,000 qubits, are not capable of breaking encryption methods such as RSA-2048 or AES-256.
The recent D-Wave breakthrough in factoring a 22-bit RSA key was achieved using quantum annealing, which has limited cryptographic applications. When discussing the potential for breaking encryption, the focus should remain on universal quantum computers, which are necessary to run cryptographic algorithms like Shor’s.
You can explore more about Microsoft’s research here.
Adiabatic Qubits: Solving Optimization Problems
It’s important to note that D-Wave’s systems are not general-purpose quantum computers. Instead, they are quantum annealers, designed specifically to solve optimization problems. Quantum annealers cannot run cryptographic algorithms like Shor’s algorithm. Even with 5,000 qubits, D-Wave’s machines are incapable of breaking encryption keys like RSA-2048 or AES-256. This limitation is due to their design, which focuses on optimization tasks rather than cryptographic challenges.
The recent breakthroughs involving D-Wave, such as the factorization of a 22-bit RSA key, were achieved using quantum annealing. However, quantum annealing has a narrow application scope. These advancements are unrelated to the type of quantum computers needed for cryptographic attacks, such as factoring RSA-2048 with Shor’s algorithm. When discussing the potential for breaking encryption, the focus should remain on universal quantum computers—such as those developed by IBM and Google—that are capable of running Shor’s algorithm. You can learn more about D-Wave’s quantum optimization focus here.
What Are Quantum Annealers?
Quantum annealers, like those developed by D-Wave, are specialized quantum computing systems designed for solving optimization problems. These machines work by finding the lowest energy state, or the optimal solution, in a complex problem. While quantum annealers leverage aspects of quantum mechanics, they are not universal quantum computers. They cannot execute general-purpose algorithms like Shor’s algorithm, which is essential for cryptographic tasks such as factoring large numbers to break encryption keys like RSA-2048.
Quantum annealers excel in specific applications like optimization and sampling, but they are not designed to tackle cryptographic challenges. This is why, even though D-Wave’s machines have achieved notable results in their field, they do not pose the same level of threat to encryption that universal quantum computers do.
Implications for Quantum Computing Threats
The distinction between universal and adiabatic qubits is critical for assessing real-world quantum computing threats. While both qubit types push the field of quantum computing forward, only universal qubits can realistically pose a threat to cryptographic systems. For instance, Google Quantum AI achieved a milestone in quantum supremacy, demonstrating the increasing potential of universal qubits. However, they remain far from breaking today’s encryption standards. You can read more about Google’s achievement in quantum supremacy here.
IBM’s Quantum Roadmap: The Future of Universal Qubits
Similarly, IBM’s Quantum Roadmap predicts breakthroughs in fault-tolerant quantum computing by 2030. This progress will further enhance the potential of universal qubits to disrupt cryptographic systems. As universal qubits advance, the need for quantum-safe cryptography becomes increasingly urgent. IBM’s roadmap can be reviewed here.
Looking Ahead: The Evolution of Quantum Cryptographic Capabilities
As quantum computing evolves, it’s essential to understand the differences between universal qubits and adiabatic qubits in cryptography. Universal qubits, developed by Microsoft, Google, and IBM, have the potential to run advanced quantum algorithms like Shor’s algorithm, which could theoretically break encryption methods such as RSA-2048. In contrast, adiabatic qubits, used in D-Wave’s systems, are better suited for solving specific optimization problems rather than breaking encryption algorithms like RSA-2048.
Therefore, announcements from companies like Microsoft and D-Wave should not be directly compared in terms of cryptographic capabilities. Each company’s quantum advancements address different computational challenges.
The Need for Segmented Key Encryption
To mitigate the risks posed by quantum computing threats, innovations like segmented key encryption will be crucial. Jacques Gascuel’s internationally patented segmented key encryption system provides extra layers of security by splitting encryption keys into multiple parts. This method makes it significantly more difficult for quantum computers, even those with enhanced capabilities, to decrypt sensitive information. This system is designed to address both classical and quantum attacks, offering robust protection against evolving threats.
Preparing for the Future: Responding to Quantum Threats to Encryption
As quantum systems continue to develop, adopting quantum-safe cryptography and integrating advanced solutions like segmented key encryption will be essential. Even though universal qubits are still far from breaking modern encryption algorithms, the rapid evolution of quantum technologies means that organizations must prepare now. By doing so, they ensure their encryption strategies are resilient against both current and future threats posed by quantum computing threats.
ANSSI’s Guidance on Post-Quantum Migration for Critical Sectors
While no joint statement by the CNIL and ANSSI was issued on May 6, 2025, the ANSSI’s follow-up position paper emphasizes the urgent need for early preparation for quantum-safe cryptography, especially in critical sectors like healthcare and digital identity. This aligns with its official migration roadmap, recommending phased adoption well before 2028 to mitigate the “store now, decrypt later” threat.
🔗 ANSSI’s official views on post-quantum cryptography transition
ISO/IEC 23894: Toward Global Certification of PQC Systems
In February 2025, the ISO/IEC JTC 1/SC 27 committee initiated work on ISO/IEC 23894, a future standard for certifying post-quantum cryptographic systems. This framework will define interoperability, auditability, and resilience benchmarks for PQC implementations.
Freemindtronic actively monitors this development to ensure its segmented key encryption modules meet future certification requirements. This proactive alignment reinforces trust and regulatory readiness across sectors.
Quantum Threats to Encryption in PKI Migration Strategy
Public Key Infrastructure (PKI) underpins digital trust—TLS, S/MIME, code signing, and identity verification. Yet, most PKI systems rely on RSA or ECC, both vulnerable to quantum attacks.
Migrating Certificate Authorities to PQC
To mitigate quantum threats, certificate authorities must adopt post-quantum cryptography (PQC) standards like HQC and ML-KEM. Freemindtronic’s offline HSM modules support PQC-ready key generation and segmented key storage, enabling sovereign PKI migration without cloud dependencies.
AES-256 Resilience Against Quantum Threats to Encryption
AES-256 remains resilient even when factoring Grover’s algorithm, as breaking it would still require:
[N = 2^{256} rightarrow N = 2^{128}
]
operations—an unachievable number for current or near-future quantum systems. Moreover, Freemindtronic’s DataShielder solutions ((DataShielder NFC HSM Lite, Master, ‘Auh’, M-Auth and HSM PGP) integrate segmented key encryption, adding layers of complexity and further enhancing AES-256’s quantum resilience.
However, it is important to emphasize that the scientific community continues to study the resistance of AES-256 to quantum algorithms. Although the estimated time required to break AES-256 with a powerful quantum computer remains prohibitive, research actively explores potential vulnerabilities. Therefore, combining AES-256 with innovative techniques like segmented key encryption, as offered by Freemindtronic with its DataShielder solutions, provides a crucial additional layer of security to strengthen protection against future quantum computing threats.
Current Research and Theses
Recent Theses & Academic Research
Theses and academic papers from institutions such as MIT, Stanford, and ETH Zurich often provide deep insights into post-quantum cryptography and quantum resilience. Specifically, the work of Peter Shor on Shor’s algorithm underpins much of the concern around RSA’s vulnerability to quantum computing. Mentioning Waterloo University’s Quantum-Safe Cryptography Group can also substantiate your argument on AES-256’s continued resilience when combined with techniques like segmented key encryption.
Research Supporting AES-256’s Resilience
AES-256’s Resilience in Current Research: The strength of AES-256 against Grover’s algorithm can be further supported by recent research published in Physical Review Letters and IEEE. These studies emphasize that even if quantum computers reduce the complexity of breaking AES-256 to 2^128 operations, this still remains infeasible for current quantum machines. Citing such studies will validate your claims regarding the security of AES-256 for the next 30 to 40 years, especially when using additional safeguards like segmented key encryption.
Estimating the Time to Crack AES-256 with Quantum Computers
Though AES-256 is secure for the foreseeable future, estimating the time it would take quantum computers to crack it offers valuable insights. Experts predict that a quantum system would need 20 million stable qubits to effectively execute Grover’s algorithm. Even with a reduction in security to AES-128 levels, quantum computers would still need to perform:
[N = 2^{128}
]
operations. This remains computationally infeasible and poses significant challenges for quantum systems.
Currently, machines like D-Wave’s 5,000-qubit computer fall short of the qubit count required to compromise AES-256 encryption. Moreover, these qubits would need to maintain stability over extended periods to complete the necessary operations, further complicating such an attack. Consequently, AES-256 is expected to remain secure for at least the next 30 to 40 years, even with advancements in quantum computing.
Organizations should begin preparing for these future quantum threats by adopting solutions like Freemindtronic’s DataShielder, which utilizes segmented key encryption to add additional layers of protection. These segmented keys provide enhanced security, ensuring that sensitive data remains secure and future-proof against the looming quantum computing threats.
Advanced Techniques to Combat Quantum Computing Threats
To combat the emerging quantum threats, Freemindtronic has developed a patented segmented key encryption system, protected under patents in the USA, China, Europe, Spain, the UK, Japan, South Korea, and Algeria. This technique divides encryption keys into multiple segments, each of which is independently encrypted. To decrypt the data, an attacker would need to obtain and decrypt all segments of the key. Even with current quantum computers, achieving this is impossible.
For example, if you segment a 4096-bit key into four 1024-bit sections, a quantum computer would need to coordinate across significantly more qubits, thereby complicating the decryption process. This method effectively future-proofs encryption systems against quantum advancements and significantly strengthens the security of AES-256 CBC encryption.
Quantum Computing Threats: What’s Next for RSA and AES?
Shor’s Algorithm Timeline for RSA-2048
To safeguard encryption during this period, NIST recommends transitioning to RSA-3072, which offers better quantum resistance than RSA-2048. Additionally, adopting post-quantum cryptography (PQC) solutions, especially for critical infrastructures, will ensure systems remain resilient as quantum technologies advance. For AES-256, it’s estimated that 295 million qubits would be required to crack it, reaffirming its continued security. With innovations like segmented key encryption, AES-256 will likely remain highly resistant to quantum computing for decades.
Freemindtronic Solutions for Enhanced Security
Freemindtronic provides cutting-edge tools to strengthen defenses against both classical and quantum threats. These solutions leverage AES-256 CBC with segmented keys, offering an extra layer of protection against quantum brute-force attacks.
Key solutions include:
- DataShielder NFC HSM Lite: Implements AES-256 with segmented keys, resistant to quantum and classical brute-force attacks.
- DataShielder NFC HSM Master: Provides secure key exchange and uses AES-256 CBC encryption.
- PassCypher NFC HSM Lite: A robust encryption solution that integrates AES-256 and segmented keys for email and file security.
- PassCypher NFC HSM Master: Offers additional security for file communications and authentication, using AES-256 encryption.
- DataShielder HSM Auth: Strengthens authentication through secure key exchange.
- DataShielder HSM M-Auth: Ensures secure key creation and exchange, combining traditional and quantum-resistant methods.
- PassCypher HSM PGP: Protects email and file communications with strong encryption, ensuring security against phishing and MITM attacks.
- PassCypher HSM PGP Free: A free version offering PGP encryption for secure communication.
- SeedNFC HSM: Ensures secure cryptocurrency wallet management with AES-256 encryption, protecting wallets against quantum threats.
- Keepser NFC HSM: Provides a hardware-based solution for secure password and key management, integrating AES-256 encryption.
The Future of Post-Quantum Cryptography
As quantum computing evolves, organizations must prepare for future encryption challenges. While post-quantum cryptography (PQC) solutions are emerging, systems like AES-256 with segmented key encryption will remain secure for the foreseeable future.
Actions to Strengthen Defenses
Organizations should take the following steps to stay ahead of quantum threats:
- Migrate RSA systems to RSA-3072 or adopt PQC solutions.
- Monitor AES-256 developments, as it remains secure, especially with solutions like segmented key encryption.
- Adopt segmented key encryption to enhance security. This method prevents attackers from gaining full access to encrypted data, even with quantum tools.
The Environmental Cost of Quantum Security
While quantum computing promises breakthroughs in encryption and computational power, its environmental impact remains a growing concern. The energy requirements to sustain millions of stable qubits—often under extreme cryogenic conditions—are immense. Operating a fault-tolerant quantum system capable of executing Shor’s algorithm for practical RSA-2048 decryption would demand enormous physical infrastructure and constant cooling near absolute zero.
This high energy footprint raises a critical question: even if quantum decryption becomes technically feasible, would it be sustainable at scale? In contrast, offline encryption solutions like Freemindtronic’s DataShielder, which require no servers, power-hungry data centers, or network connections, offer a low-energy, environmentally resilient alternative—immune to centralized infrastructure vulnerabilities and ecological limitations alike.
🌱 Energy Efficiency: Offline Encryption vs Quantum Infrastructure
Operating a fault-tolerant quantum computer requires cryogenic cooling near absolute zero, energy-intensive error correction, and massive infrastructure. A single quantum decryption session could consume megawatts of power.
In contrast, Freemindtronic’s SeedNFC and DataShielder modules operate fully offline, with near-zero energy consumption. They require no servers, no cloud, and no persistent connectivity—making them ideal for deployment in low-resource environments or critical infrastructure with strict energy budgets.
This ecological advantage complements their cryptographic resilience, offering a future-proof solution that’s both secure and sustainable.
Act Now to Counter Quantum Computing Threats
Quantum computing presents future risks to encryption standards like RSA-2048 and AES-256 CBC, but current advancements are far from threatening widely used systems. Organizations can counter quantum computing threats today by migrating to post-quantum cryptography and adopting segmented key encryption.
Freemindtronic’s patented solutions, such as DataShielder NFC HSM and PassCypher HSM PGP, ensure encryption systems are future-proof against the evolving quantum threat.








Pingback: Tchap Sovereign Messaging — Strategic Analysis France - Freemindtronic
Pingback: Post-Quantum Cryptography: The RSA-2048 Threat Is Now