2025, Digital Security
APT36 SpearPhishing India: Targeted Cyberespionage | Security
APT36 SpearPhishing India is one of the most persistent cyberespionage threats targeting India. This article by Jacques Gascuel investigates its methods and how to protect against them.
APT36 SpearPhishing India: Inside Pakistan’s Persistent Cyberespionage Campaigns
APT36 SpearPhishing India represents a serious and persistent cyber threat targeting Indian entities. This article explores their spear-phishing techniques, malware arsenal, and defensive responses.
Understanding Targeted Attacks of APT36 SpearPhishing India
APT36 cyberespionage campaigns against India represent a focused and enduring threat. Actors likely linked to Pakistan orchestrate these attacks. This group, also known as Transparent Unit, ProjectM, Mythic Leopard, and Earth Karkaddan, has been active since at least 2013. Throughout its operations, APT36 has consistently targeted Indian government entities, military personnel, defense organizations, research institutions, diplomats, and critical infrastructure.
Unlike threat actors with broader targets, APT36’s operations primarily focus on gathering intelligence relevant to Pakistani strategic interests, especially concerning its relationship with India. This article analyzes APT36’s attack methods, its specific targeting of Indian entities, technical indicators, and proactive security measures for defense. Understanding their evolving tactics allows cybersecurity professionals to develop tailored countermeasures and strengthen resilience against persistent threats.
Purpose of this Brief: This report aims to provide a detailed understanding of APT36’s tactics, their priority targets in India, and their evolving malware arsenal (e.g., Crimson RAT, Poseidon, ElizaRAT, CapraRAT). It also covers recent techniques such as ClickFix attacks and the abuse of legitimate cloud services, offering insights into how Indian organizations can strengthen their cyber defense against this persistent cyberespionage threat.
The Espionage Model of APT36 SpearPhishing India: Focused Infiltration
The operational model of APT36 features a specific focus on Indian targets, persistence, and adaptability. Their main goal isn’t widespread disruption. Instead, they aim for sustained infiltration of Indian networks to exfiltrate sensitive information over time. Their campaigns often last a significant duration, showing a commitment to long-term access. While they may not always use the most advanced zero-day exploits, their consistent refinement of social engineering and malware deployment proves effective against Indian organizations.
Furthermore, APT36 frequently uses publicly available or slightly modified tools. Alongside these, they also deploy custom-developed malware. This malware is specifically tailored to evade common detection mechanisms within Indian organizations.
Main Targets of APT36 SpearPhishing India
APT36 primarily focuses its attacks on a range of Indian entities, including:
- Indian government ministries, with a particular emphasis on the Ministry of Defence and the Ministry of External Affairs.
- The Indian armed forces and organizations within the defense industrial sector.
- Educational institutions and students.
- Users of government services, such as those utilizing the Kavach authentication application.
These targets align with recent warnings, such as the May 2025 advisory from the Chandigarh Police citing government institutions, defense personnel, research centers, diplomats, and critical infrastructure as primary targets.
The group frequently employs social engineering techniques, including the use of lure documents and the creation of fake websites mimicking legitimate portals, to trick victims into downloading and executing their malware.
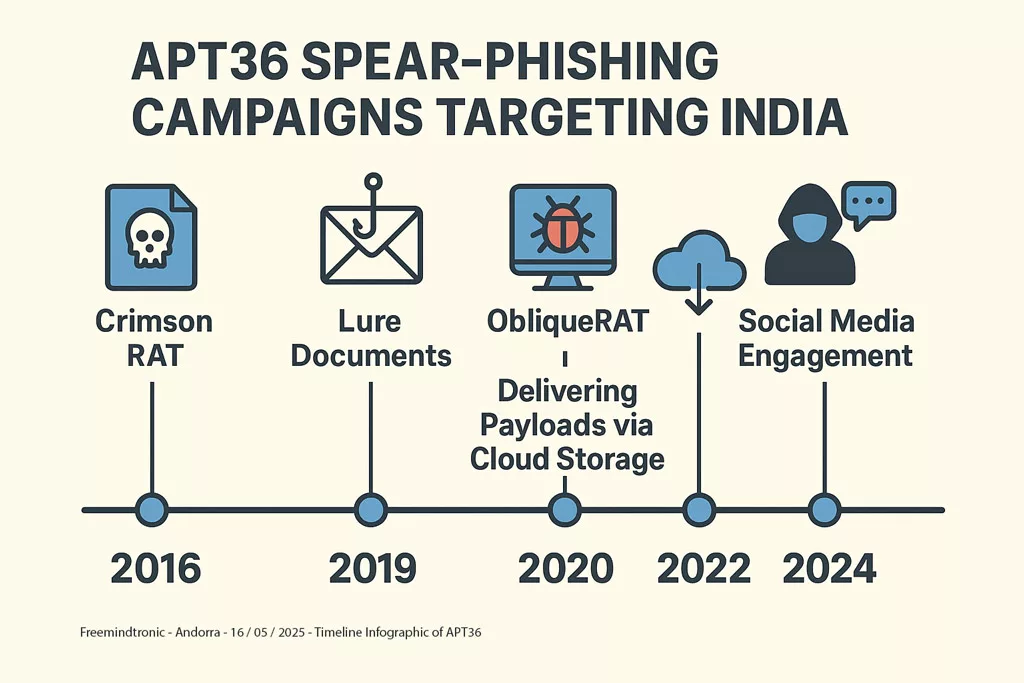
APT36’s Malware Arsenal: Types and Evolution (2013–2025)
APT36 relies on a diverse and evolving malware arsenal tailored to espionage operations against Indian entities. Their tools include widely-used Remote Access Trojans (RATs) and more recent, customized malware. ElizaRAT malware analysis highlights its evolution into a stealthy .NET-based trojan leveraging Telegram for covert C2, as seen in multiple campaigns since late 2023.
- Crimson RAT: In use since 2013 for data exfiltration and surveillance.
- ElizaRAT: A .NET-based RAT communicating via Telegram, with enhanced C2 capabilities.
- Poseidon: Targets Linux via fake Kavach app installations.
- CapraRAT: Android malware for mobile surveillance.
- ApolloStealer: Data harvester targeting government systems.
ClickFix: APT36’s Deceptive New Attack Technique
APT36 has adopted “ClickFix”-style campaigns to trick users into copying malicious commands from websites that impersonate legitimate Indian portals. This bypasses email filters and endpoint protections by relying on user interaction via terminal or shell.
Exploitation of Cloud Services for C2: A Detection Challenge
APT36 leverages popular platforms like Telegram, Google Drive, and Slack for Command & Control. These services allow attackers to blend in with normal encrypted traffic and evade firewall detection.
Why India is APT36’s Primary Target
The cyber activities of APT36 are deeply intertwined with the complex geopolitical dynamics between Pakistan and India. Their consistent focus on targeting Indian government, military, and strategic assets strongly suggests their role in directly supporting Pakistan’s intelligence-gathering efforts.
Furthermore, APT36’s operations often show increased activity during periods of heightened tension or significant political events between the two nations. Their primary objectives appear to center on acquiring sensitive information. This includes data related to India’s defense capabilities, its foreign policy decisions, and its internal security measures.
To illustrate, notable examples of their activity include:
- Sustained campaigns specifically target Indian military personnel. These campaigns often involve sophisticated social engineering combined with malware-laden documents.
- Attacks directed against Indian government organizations involved in policy making and national security. The aim is likely to gain insights into strategic decision-making and sensitive communications.
- Targeting of research institutions and defense contractors. This suggests an interest in acquiring knowledge about India’s technological advancements in defense.
- The strategic use of topical lures in their phishing campaigns. These lures often relate to current events, such as cross-border incidents or diplomatic discussions, to make their malicious emails more relevant.
In essence, APT36 functions as a significant cyber arm within the broader geopolitical context. The intelligence they successfully gather can be leveraged for strategic planning, diplomatic maneuvering, and potentially to gain an advantage in the intricate relationship between India and Pakistan. Therefore, a thorough understanding of this geopolitical context is crucial for developing effective cyber defense strategies within India.
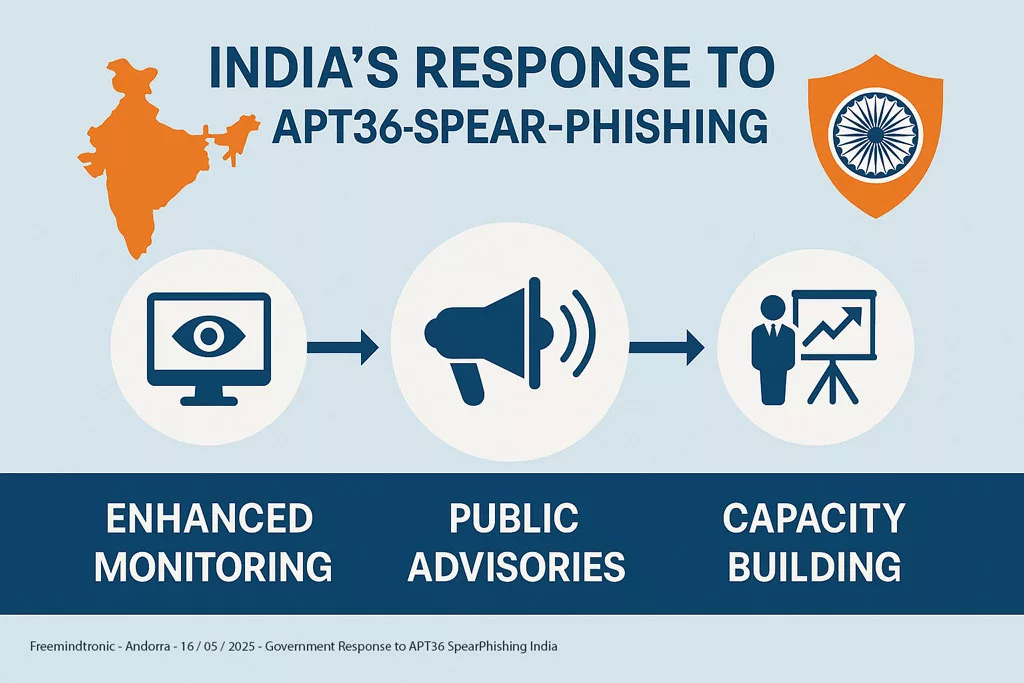
Indian Government and Security Responses to APT36 Cyberespionage

- India’s layered response to APT36 SpearPhishing campaigns — from real-time monitoring to public cybersecurity advisories and professional capacity building.
The Indian government and its security agencies have increasingly focused on detecting, attributing, and mitigating the persistent threats posed by APT36 cyberespionage. Indian government phishing alerts, such as those issued by CERT-In and regional cyber cells, underscore the urgency of countering targeted APT36 spearphishing attacks.
Responses often include:
- Issuing public advisories and alerts regarding APT36’s tactics and indicators of compromise (IOCs).
- Enhancing monitoring and detection capabilities within government and critical infrastructure networks.
- Conducting forensic analysis of attacks to understand APT36’s evolving TTPs and develop better defenses.
- Collaboration between different security agencies and sharing of threat intelligence.
- Efforts to raise cybersecurity awareness among potential targets, particularly within government and military sectors.
- Capacity building initiatives to train cybersecurity professionals within India to better defend against sophisticated threats like APT36.
While direct legal or retaliatory actions are less publicly discussed, the focus remains on strengthening India’s cyber resilience and deterring future attacks through enhanced detection and response.
Potential Impact of Undetected APT36 Cyberespionage
The prolonged and undetected operations of APT36 cyberespionage could have significant ramifications for India’s national security and strategic interests:
- Loss of Sensitive Information: Unfettered access could lead to the exfiltration of classified military plans, diplomatic communications, and sensitive government policies.
- Compromise of Critical Infrastructure: Persistent access to critical infrastructure networks could potentially be exploited for disruptive purposes in the future.
- Erosion of Trust: Successful and undetected breaches could undermine trust in the security of government and defense systems.
- Strategic Disadvantage: The intelligence gathered could provide Pakistan with a strategic advantage in diplomatic negotiations or during times of conflict.
- Impact on International Relations: Compromise of diplomatic communications could strain relationships with other nations.
This underscores the critical importance of robust cybersecurity measures and proactive threat hunting to detect and neutralize APT36’s activities before they can cause significant harm through their cyberespionage.
Notable APT36 Cyberespionage Incidents Targeting India
| Date (Approximate) | Campaign/Malware | Target | Observed Tactics |
|---|---|---|---|
| 2013 onwards | Crimson RAT | Indian Government, Military | Spearphishing with malicious attachments. |
| 2018-2019 | Transparent Group Campaigns | Defense Personnel, Government Officials | Social engineering, weaponized documents. |
| 2020-2021 | Abuse of Cloud Services | Various Indian Entities | C2 via Telegram, Google Drive. |
| 2022-2023 | ElizaRAT | Government, Research Institutions | Evolved RAT with enhanced evasion techniques. |
| 2024-2025 | ClickFix Campaigns | Government Portals | Tricking users into executing malicious commands. |
Timeline Sources & Attribution of APT36 SpearPhishing India Attacks

- APT36 SpearPhishing India: Visual timeline of APT36 cyberespionage campaigns and malware used against Indian entities from 2013 to 2025.
This infographic is based on analysis and reports from various cybersecurity firms, threat intelligence sources, and official advisories, including:
- Ampcus Cyber on APT36 Insights: Ampcus Cyber.
- Athenian Tech Analysis on APT-36: Athenian Tech.
- Brandefense Analysis on APT-36 Poseidon Malware: Brandefense.
- CERT-In Security Advisories: CERT-In.
- Chandigarh Police Advisory (May 2025) on APT36 Threats (via Indian Express): Indian Express.
- Check Point Research on the Evolution of the Transparent Group: Check Point.
- CloudSEK Threat Intelligence: CloudSEK.
- CYFIRMA Research on APT36 Targeting via Youth Laptop Scheme: CYFIRMA.
- Reco AI Analysis of ElizaRAT: Reco AI.
- SentinelOne Labs on APT36 Targeting Indian Education: SentinelOne.
- The Hacker News on APT36 Spoofing India Post: The Hacker News.
- Zscaler ThreatLabz Analysis of APT36’s Updated Arsenal: Zscaler ThreatLabz.
- Kaspersky Cybermap (General Threat Landscape): Kaspersky.
These sources collectively indicate that APT36 remains a persistent and adaptive threat actor with a clear focus on espionage against Indian interests through cyber means.
APT36 vs. APT29, APT41, APT33: Strategic Comparison of Cyberespionage Groups
| Tactic/Group | APT36 (also known as ProjectM, Mythic Leopard, Earth Karkaddan, “Transparent Tribe” — researcher-assigned alias) | Other APT Groups (e.g., APT29, APT41, APT33) |
| Primary Target | Predominantly focuses on entities within India. | Employs a broader targeting strategy, often including Europe, the United States, and various other regions depending on the group’s objectives. |
| Suspected Affiliation | Believed to have strong links to Pakistan. | Attributed to various state-sponsored actors, including Russia (e.g., APT29), China (e.g., APT41), and Iran (e.g., APT33). |
| Main Objective | Primarily cyberespionage with a specific focus on gathering intelligence relevant to Indian affairs. | Objectives can vary widely, including espionage, disruptive attacks, and financially motivated cybercrime, depending on the specific group. |
| Favored Techniques | Relies heavily on spearphishing attacks, the use of commodity Remote Access Trojans (RATs) such as Crimson and ElizaRAT, social engineering tactics, abuse of cloud services, malicious Office documents, fake websites, and “ClickFix” campaign techniques. | Often employs more sophisticated and custom-developed malware, and in some cases, utilizes zero-day exploits to gain initial access. The level of sophistication varies significantly between different APT groups. |
| Stealth and Sophistication | While their social engineering tactics can be quite effective, their malware development is generally considered less sophisticated compared to some other advanced persistent threat groups. However, they continuously adapt their existing tools for their cyberespionage efforts. | Varies significantly. Some groups utilize highly advanced and stealthy custom malware with sophisticated command and control infrastructure, while others may rely on more readily available tools. |
| Resource Allocation | Likely operates with fewer resources compared to state-sponsored groups from larger nations. | Variable, with some groups having significant state backing and extensive resources, enabling more complex and persistent campaigns. |
| Geopolitical Context | Primarily driven by the geopolitical relationship and tensions between India and Pakistan. | Driven by broader national interests and complex geopolitical strategies that extend beyond a single bilateral relationship. |
Key Indicators and Detection of APT36 Cyberespionage
Security teams targeting APT36 should be vigilant for the following indicators:
- Spearphishing emails with themes relevant to the Indian government, military, or current affairs.
- Attachments containing weaponized documents (e.g., malicious DOC, RTF, or executable files).
- Network traffic to known C2 infrastructure associated with APT36.
- Unusual use of cloud services (Telegram, Google Drive, Slack) for data transfer.
- Execution of suspicious commands via command-line interfaces, potentially linked to ClickFix attacks.
- Presence of known APT36 malware like Crimson RAT, ElizaRAT, ApolloStealer, Poseidon (particularly on Linux systems), and CapraRAT (on Android devices).
- Use of domains and URLs mimicking legitimate Indian government or military websites.
- Use of domains and URLs mimicking legitimate Indian government or military websites.
- Suspicious emails with subject lines or content related to recent sensitive events like the April 2025 Pahalgam terror attack.
- Network traffic to or from websites mimicking the India Post portal or other legitimate Indian government services.
◆ Known Indicators of Compromise (IOCs) – APT36
The following Indicators of Compromise have been observed across multiple APT36 campaigns, including those involving Crimson RAT, ElizaRAT, Poseidon, and CapraRAT. Use them to improve detection and defense mechanisms:
- C2 IP addresses (2023–2025): 45.153.241.15, 91.215.85.21, 185.140.53.206 (ElizaRAT / Telegram-based C2)
- File hashes (SHA-256):
3c2cfe5b94214b7fdd832e00e2451a9c3f2aaf58f6e4097f58e8e5a2a7e6fa34 (Poseidon)
bd5602fa41e4e7ad8430fc0c6a4c5d11252c61eac768835fd9d9f4a45726c748 (Crimson RAT) - Malicious domains: kavach-app[.]com, indiapost-gov[.]org, gov-inportal[.]org
- Suspicious file names: Briefing_MoD_April25.docx, Alert_Kavach_Update.exe
◆ Additional IOCs: Linux & Android Malware in APT36 SpearPhishing India
APT36 increasingly targets Linux and Android environments with deceptive filenames and cloud-distributed payloads.
- Linux-specific hashes (MD5):
65167974b397493fce320005916a13e9 (approved_copy.desktop)
98279047a7db080129e5ec84533822ef (pickle-help)
c86f9ef23b6bb200fc3c0d9d45f0eb4d (events-highpri) - Fake .desktop file names: Delegation_Saudi_Arabia.desktop, Meeting_agenda.desktop, approved_copy.desktop
- Linux-focused C2 servers: 108.61.163[.]195:7443, 64.176.40[.]100:7443, 64.227.138[.]127, 134.209.159[.]9
- Android malware package names: com.chatspyingtools.android, com.spyapp.kavachupdate
- Deceptive download URLs:
http://103.2.232[.]82:8081/Tri-Service-Exercise/Delegation_Saudi_Arabia.pdf
https://admin-dept[.]in/approved_copy.pdf
https://email9ov[.]in/VISIT_OF_MEDICAL/
Sources: Brandefense, Zscaler ThreatLabz, Reco AI, CYFIRMA, Check Point Research
◆ Download the Full IOC Report for APT36
To strengthen your spearphishing defense in India and enhance detection capabilities against APT36 cyberespionage, you can download the full list of enriched Indicators of Compromise (IOCs) used by the group.
This includes:
- Command & Control (C2) IP addresses
- SHA-256 hashes of known malware samples (e.g. Crimson RAT, ElizaRAT, Poseidon)
- Fake domains and URLs (Kavach, India Post…)
- Malicious file names and Android package names
- Registry keys, mutexes, user-agents and encoded payload strings
⇩ Download APT36 Cyberespionage IOC & TTP Report by Freemindtronic (PDF – English)
◆ APT36 साइबर जासूसी समूह तकनीकी दस्तावेज़ डाउनलोड करें
भारत में अपने स्पीयरफ़िशिंग बचाव को मजबूत करने और APT36 साइबर जासूसी के खिलाफ पहचान क्षमताओं को बढ़ाने के लिए, आप समूह द्वारा उपयोग किए गए समृद्ध संकेतकों की पूरी सूची डाउनलोड कर सकते हैं।
इसमें शामिल हैं:
- कमांड एंड कंट्रोल (C2) आईपी एड्रेस
- ज्ञात मैलवेयर नमूनों के SHA-256 हैश (जैसे क्रिमसन आरएटी, एलिजारैट, पोसीडॉन)
- फर्जी डोमेन और यूआरएल (कवच, इंडिया पोस्ट…)
- दुर्भावनापूर्ण फ़ाइल नाम और एंड्रॉइड पैकेज नाम
- रजिस्ट्री कुंजियाँ, म्युटेक्स, उपयोगकर्ता-एजेंट और एन्कोडेड पेलोड स्ट्रिंग
⇩ APT36 साइबर जासूसी समूह तकनीकी दस्तावेज़ डाउनलोड करें (PDF – हिंदी)
Compiled from: Brandefense, Zscaler, Check Point, Reco AI, SentinelOne, CYFIRMA, and CERT-In reports
APT36 SpearPhishing India in 2025: Updated Arsenal and Emerging Linux Threats
APT36 continues to evolve its tactics in 2025, expanding its targeting scope beyond Windows environments. Recent reports highlight sophisticated ClickFix-style attacks on Linux systems, where users are tricked into pasting terminal commands disguised as harmless instructions. This represents a critical shift, bypassing traditional endpoint security solutions.
- ClickFix Linux Variant: In 2025, APT36 began testing ClickFix-style social engineering attacks on Linux by embedding dangerous commands inside fake support messages and screenshots. [BleepingComputer Report]
- New Linux-based Payloads: Building on their 2023 campaigns, APT36 now weaponizes .desktop files with inflated size (1MB+), obfuscated base64 commands, and deceptive PDF decoys. These payloads deploy cross-platform backdoors with persistence via cron jobs.
- Advanced C2 Infrastructure: They continue to abuse trusted cloud services like Telegram, Google Drive, and now Indian TLDs (e.g.,
.indomains) to mask origins and evade attribution. These deceptive techniques align with past OPSEC failures such as the “Nand Kishore” Google Drive account.
For a full technical breakdown, we recommend reading the excellent deep-dive analysis by Zscaler ThreatLabz: Peek into APT36’s Updated Arsenal (2023).
Countering APT36 with Sovereign Zero-Trust Solutions
APT36 targets India through spearphishing, remote access malware, and cloud abuse. To counter such advanced persistent threats, Freemindtronic offers patented, sovereign, and fully offline security tools that eliminate traditional attack surfaces.
DataShielder & PassCypher: Zero-Trust Hardware-Based Protection
To further support organizations in India against threats like APT36, the user interfaces and relevant documentation for our DataShielder and PassCypher solutions are also available in Hindi, ensuring ease of use and accessibility.
- DataShielder NFC HSM (Lite, Auth, Master, M-Auth)
Offline AES-256 encryption with RSA 4096 key exchange (M-Auth), ideal for fixed (Auth) and mobile (M-Auth) use. No RAM, no OS access, no server. - DataShielder HSM PGP
Browser-integrated, offline PGP encryption/decryption. Compatible with air-gapped systems. Private keys never leave the HSM. - PassCypher NFC HSM
Offline password & OTP manager (TOTP/HOTP) using a contactless HSM. Injects credentials only on verified domains. No clipboard, no RAM exposure. - PassCypher HSM PGP
Secure, passwordless login + PGP + OTP autofill, browser-integrated. 100% offline. No secrets exposed to the system.
📘 Learn more about the DataShielder NFC HSM Starter Kit
APT36 Tactics vs. Freemindtronic Defense Matrix
| APT36 Tactic | Freemindtronic Defense | Compatible Products |
|---|---|---|
| Spearphishing / Fake Portals | Sandboxed URL validation; no credential injection on spoofed sites | PassCypher NFC HSM, PassCypher HSM PGP |
| Credential Theft (ElizaRAT, ApolloStealer) | No copy/paste, no secrets in RAM, no browser storage | All products |
| Remote Access Tools (Crimson RAT, Poseidon) | 100% offline operation, NFC/QR key exchange, no OS exposure | DataShielder NFC HSM Lite, Auth, Master, M-Auth |
| Fake Apps & ClickFix Commands | Credential injection via NFC or container — no terminal input | PassCypher NFC HSM, PassCypher HSM PGP |
| Cloud-based C2 (Telegram, Google Drive) | No connectivity, no browser plug-in, no C2 callbacks possible | All NFC HSM and HSM PGP solutions |
🛡️ Why Choose These Solutions?
- 🛠 No server • No database • No RAM exposure • No clipboard
- ⚖️ GDPR / NIS2 / ISO 27001 compliant
- 🎖️ Built for air-gapped and sovereign systems (civil + defense use)
- 🔐 Licensed HSM PGP on Windows/macOS, NFC HSM works on all OS (via Android NFC)
Comparative Threat Mitigation Table: APT36 vs. Freemindtronic HSM Ecosystem
This table summarizes how each threat vector used by APT36 is mitigated by Freemindtronic’s sovereign tools — whether mobile or desktop, fixed or remote, civilian or defense-grade.
🧩 How does each solution stand against APT36’s arsenal?
The table below compares threat-by-threat how DataShielder and PassCypher mitigate attacks — whether on mobile, desktop, or air-gapped infrastructure.
| APT36 Tactic / Malware | DataShielder NFC HSM (Lite/Auth/M-Auth) |
DataShielder HSM PGP (Win/macOS) |
PassCypher NFC HSM (Android) |
PassCypher HSM PGP (Win/macOS) |
|---|---|---|---|---|
| Spearphishing (India Post, Kavach) | ✔ QR-code encryption + sandbox |
✔ Signature check + offline PGP |
✔ URL sandbox + no injection |
✔ Sandboxed PGP container |
| Crimson RAT | ✔ NFC avoids infected OS |
✔ No system-stored keys |
✔ Secrets off-device |
✔ No memory exposure |
| ElizaRAT | ✔ No cloud or RAM access |
✔ PGP keys isolated in HSM |
✔ No RAM / no clipboard |
✔ OTP only if URL matches |
| ApolloStealer | ✔ Credentials never exposed |
✔ Key never loaded in system |
✔ Immune to clipboard steal |
✔ Phishing-proof login |
| Poseidon (Fake Kavach on Linux) | ✔ NFC-only: bypasses compromised OS |
✘ Not Linux-compatible |
✔ No OS dependency |
✘ Desktop only |
| CapraRAT (Android) | ✘ (Not on Android) |
✘ | ✔ Secrets never stored in app |
✔ With desktop pair only |
| ClickFix (command injection) | ✔ No shell interaction possible |
✔ PGP validation |
✔ No typing / no pasting |
✔ No terminal interaction |
| Telegram / Cloud C2 Abuse | ✔ No cloud usage at all |
✔ Fully offline |
✔ 100% offline |
✔ 100% offline |
| CEO Fraud / BEC | ✔ Auth/M-Auth modules encrypt orders |
✔ Digital signature protection |
✔ No spoofing possible |
✔ Prevents impersonation |
Understanding Targeted Attacks of APT36 SpearPhishing India
APT36 cyberespionage campaigns against India represent a focused and enduring threat. Actors likely linked to Pakistan orchestrate these attacks. This group, also known as Transparent Unit, ProjectM, Mythic Leopard, and Earth Karkaddan, has been active since at least 2013. Throughout its operations, APT36 has consistently targeted Indian government entities, military personnel, defense organizations, research institutions, diplomats, and critical infrastructure.
Unlike threat actors with broader targets, APT36’s operations primarily focus on gathering intelligence relevant to Pakistani strategic interests, especially concerning its relationship with India. This article analyzes APT36’s attack methods, its specific targeting of Indian entities, technical indicators, and proactive security measures for defense. Understanding their evolving tactics allows cybersecurity professionals to develop tailored countermeasures and strengthen resilience against persistent threats.
Purpose of this Brief: This report aims to provide a detailed understanding of APT36’s tactics, their priority targets in India, and their evolving malware arsenal (e.g., Crimson RAT, Poseidon, ElizaRAT, CapraRAT). It also covers recent techniques such as ClickFix attacks and the abuse of legitimate cloud services, offering insights into how Indian organizations can strengthen their cyber defense against this persistent cyberespionage threat.
-
-
- ⇨ Implement comprehensive security awareness training focused on identifying and avoiding sophisticated spearphishing attacks and social engineering tactics.
- ⇨ Deploy robust email security solutions with advanced threat detection capabilities to filter out malicious emails and attachments.
- ⇨ Utilize strong endpoint detection and response (EDR) solutions to detect and block malware execution and suspicious activities.
- ⇨ Enforce strict access controls and the principle of least privilege to limit the impact of compromised accounts.
- ⇨ Ensure regular patching and updating of all systems and software to mitigate known vulnerabilities.
- ⇨ Implement network segmentation to limit lateral movement in case of a breach.
- ⇨ Monitor network traffic for unusual patterns and communication with known malicious infrastructure.
- ⇨ Implement multi-factor authentication (MFA) to protect against credential theft.
- ⇨ Conduct regular security audits and penetration testing to identify and address potential weaknesses.
-
Security Recommendations Against APT36 SpearPhishing India
To enhance protection against APT36 attacks, organizations and individuals in India should implement the following security measures:
-
-
- Regularly update operating systems, applications, and security software to patch known vulnerabilities.
- Deploy robust and up-to-date security solutions, including antivirus, anti-malware, and intrusion detection/prevention systems, capable of identifying and blocking malicious behavior.
- Provide comprehensive security awareness training to employees and users, educating them on how to recognize and avoid phishing attempts, social engineering tactics, and suspicious documents or links.
- Implement multi-factor authentication (MFA) for all sensitive accounts and services to prevent unauthorized access even if credentials are compromised.
- Monitor network traffic for unusual patterns and connections to known command and control (C2) infrastructure associated with APT groups.
-
Sovereign Security Considerations for Cyberespionage Defense
For organizations with stringent security requirements, particularly within the Indian government and defense sectors, considering sovereign security solutions can add an extra layer of protection against advanced persistent threats. While the provided APT29 article highlights specific products, the underlying principles of offline, hardware-based security for critical authentication and data protection can be relevant in the context of defending against APT36 cyberespionage as well.
Toward a National Cyber Defense Posture
APT36’s sustained focus on India highlights the urgent need for a resilient and sovereign cybersecurity posture. Strengthening national cyber defense requires not only advanced technologies but also strategic policy coordination, inter-agency threat intelligence sharing, and continuous capacity-building efforts. As threat actors evolve, so must the institutions that protect democratic, economic, and military integrity. The fight against APT36 is not a technical issue alone — it’s a matter of national sovereignty and strategic foresight.


Pingback: eSIM Sovereignty Failure: Certified Mobile Identity at Risk - Freemindtronic
Pingback: Reputation Cyberattacks in Hybrid Conflicts — Anatomy of an Invisible Cyberwar - Freemindtronic