Executive Summary
Let’s Encrypt IP SSL now enables the issuance of SSL/TLS certificates directly for public IP addresses, without requiring a domain name or DNS configuration. This breakthrough unlocks secure HTTPS access for test labs, DevOps deployments, IoT devices, and local infrastructure. Valid for 6 days, these certificates support automated renewal via ACME clients like Certbot or acme.sh. Compared to self-signed alternatives, Let’s Encrypt IP SSL offers browser trust, automation, and a zero-cost advantage. This article explores practical use cases, technical constraints, WordPress integration, and alternatives for full HTTPS coverage on raw IP addresses.
Strategic Navigation Index
- Executive Summary
- Why Trigger HTTPS via NFC HSM?
- Sovereign Certificate Deployment
- ACME Command Injection
- Threat Modeling & Attack Surface Reduction
- Use Cases
- Keyboard Emulation Security
- Web Interface Variant
- Step-by-Step Windows 11 Tutorial
- Linux Implementation Notes
- Beyond SSL: Generalized Command Triggering
- Visual Workflow
- FAQ
- Image JSON-LD Metadata
About the Author – Jacques Gascuel is the inventor of several patented, hardware-based encryption and authentication technologies, and founder of Freemindtronic Andorra. A specialist in sovereign cybersecurity and offline cryptographic systems, he focuses on privacy-by-design solutions for environments with no internet or server dependency. In this article on Let’s Encrypt IP SSL, he explores the strategic potential of securing raw IP communications without DNS, offering insight into resilient digital architectures compatible with sensitive and constrained infrastructures.
Let’s Encrypt IP SSL: Secure an IP Address with HTTPS Without a Domain Name
Let’s Encrypt, the free and open-source certificate authority, now offers SSL/TLS certificates for IP addresses, without requiring a Fully Qualified Domain Name (FQDN). This innovation enables encrypted HTTPS communication on servers accessible via raw IP addresses, without relying on DNS. It’s ideal for DevOps pipelines, test labs, and local or self-hosted network appliances.
Let’s Encrypt IP SSL vs Domain-Based SSL
Let’s Encrypt primarily issues free SSL certificates for domain names, but it also supports securing public IP addresses directly through the ACME protocol. This article explores how Let’s Encrypt IP SSL differs from traditional domain-based certificates and when this approach makes sense.
Let’s Encrypt IP SSL vs Domain-Based Certificates
Let’s Encrypt is historically known for issuing domain-validated SSL/TLS certificates. However, it now also supports issuing certificates directly for public IP addresses. This removes the dependency on DNS and makes it possible to secure services by IP alone.
Unlike domain-based certificates, which require a Fully Qualified Domain Name (FQDN), IP SSL certificates use the SAN field to declare the IP address (IPv4 or IPv6). This change facilitates secure deployments in contexts like DevOps, IoT, or test environments without needing to register domains.
Official Let’s Encrypt Forum Post · ACME Protocol – RFC 8555
Why Use HTTPS on an IP Without a Domain?
- Test or Staging Environments: No need to register temporary domains—launch secure interfaces instantly.
- Cloud Instances & Containers: Secure dynamic or short-lived cloud workloads with HTTPS without DNS hassle.
- Internal or Local Networks: Access NAS devices, routers, DoH/DoT services, or IoT devices without browser warnings, even without a domain.
- Use in Security-Conscious or Air-Gapped Environments: Combine IP SSL certs with self-hosted ACME setups to create secure enclaves without domain exposure or internet reliance.
Key Use Cases
New use cases include securing DNS‑over‑HTTPS (DoH) endpoints, IoT/home‑lab devices, and ephemeral cloud workloads.
-
- NAS Admin Interfaces: Secure your NAS control panel accessed via public IP.
- Fast HTTPS for VMs or Bare Metal: Deploy secure servers on AWS, Azure, or OVHcloud with public IPs in seconds.
- CI/CD & DevOps Pipelines: Spin up HTTPS-enabled test servers with no DNS propagation.
- Self-Hosted DoH/DoT: Serve encrypted DNS traffic using a valid IP SSL cert.
- Internet-Facing Cameras: Protect IP-streamed video feeds without needing a domain.
- Industrial & SCADA Systems: Encrypt communication between web dashboards and IP-based industrial devices.
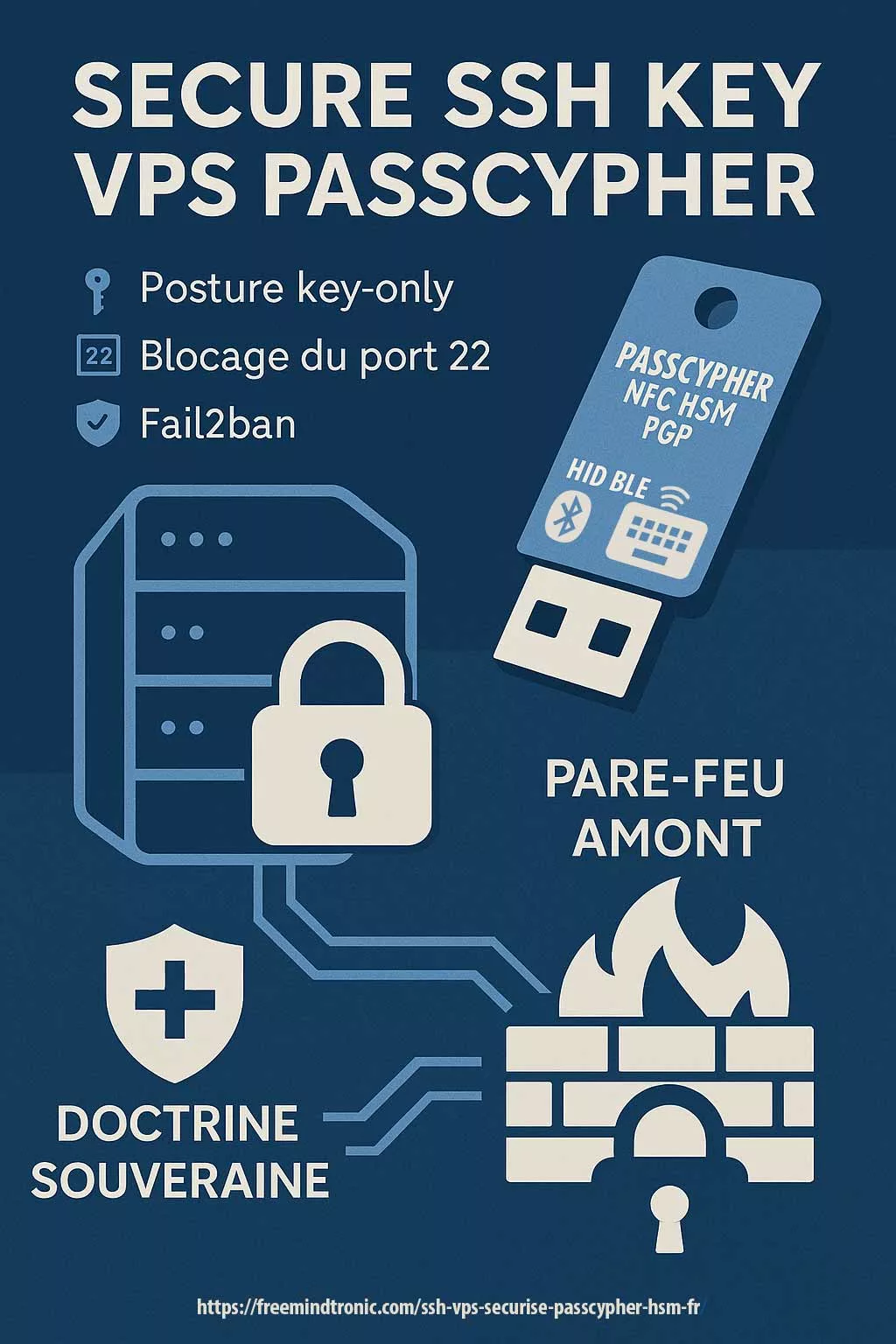
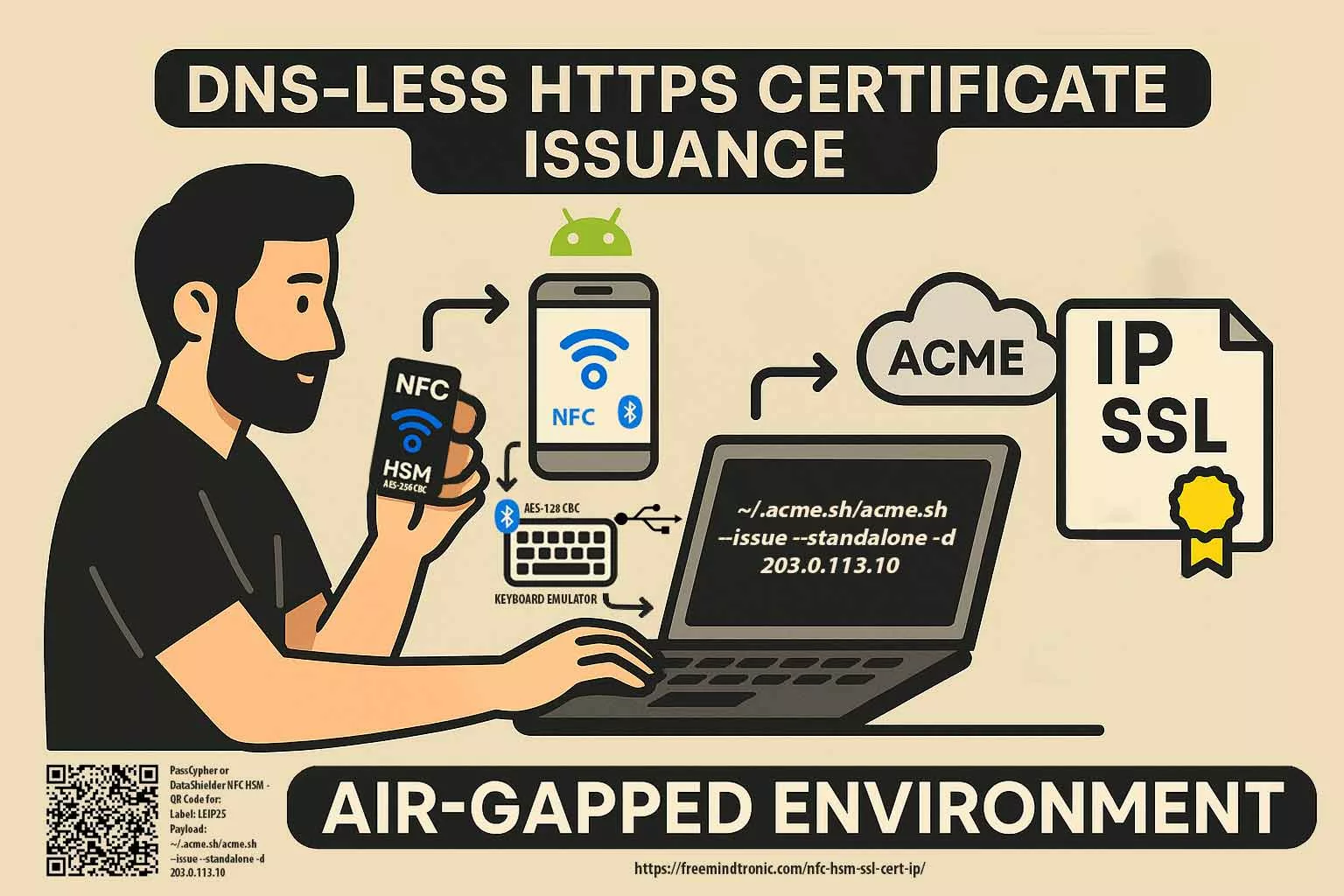
Let’s Encrypt IP SSL certificates can be autonomously issued via NFC HSM devices such as PassCypher NFC HSM and DataShielder NFC HSM. These devices integrate a secure Bluetooth USB keyboard emulator operating in AES 128 CBC mode, enabling fully offline and sovereign execution of commands.By embedding a complete ACME command (e.g.,
~/.acme.sh/acme.sh --issue --standalone -d 203.0.113.10) as a “password” (≤55 characters), the certificate issuance can be triggered securely on a Linux or Windows terminal without human typing. Combined with auto-enter, this setup ensures air-gapped, domainless HTTPS deployment for critical infrastructure, DevSecOps labs, or secure IoT environments.→ Full technical walkthrough: Trigger Let’s Encrypt IP SSL with NFC HSMSovereign Certificate Automation via NFC HSM
The diagram below demonstrates how a fully offline NFC HSM device can autonomously trigger HTTPS certificate issuance over raw IP — without DNS or manual typing. This approach, secured via AES-encrypted Bluetooth keyboard emulation, enables resilient deployments across air-gapped systems, DevSecOps pipelines, and critical infrastructure.
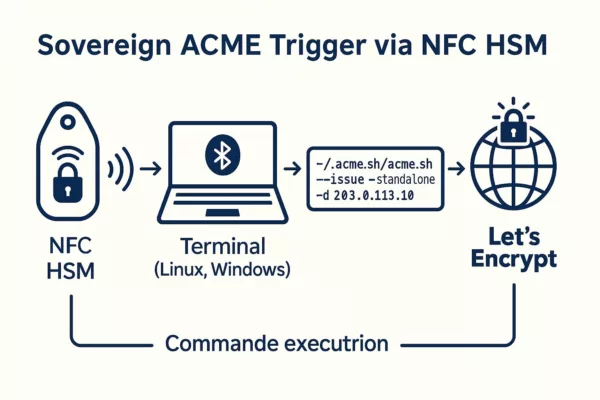
Other technical scenarios include:
- Landing page providers dynamically assigning IPs to tenants.
- DNS-over-HTTPS (DoH) endpoints using direct IP exposure.
- NAS and IoT devices offering direct web interfaces without FQDNs.
- Cloud back-end apps with ephemeral public IPs.
Source : Let’s Encrypt IP Announcement, July 2025
Validity and ACME Requirements
Let’s Encrypt IP certificates are valid for just 6 days. This short lifetime helps enhance security by quickly invalidating certificates in case of IP address changes or misconfigurations. Source: Let’s Encrypt Forum Post Certificate issuance requires the ACME protocol, defined in RFC 8555, using the http-01 or tls-alpn-01 challenges. DNS-based validation is not supported for IP certificates. Reference: Let’s Encrypt Challenge Types To automate certificate renewal, use compatible ACME clients such as:
⚠️ Rate Limit Notice: Let’s Encrypt enforces a rate limit of 50 certificates per IP address (or /64 IPv6 range) per 7-day window. You may also request up to 5 certificates per identical set of identifiers (IP + SAN/domain) per week. Let’s Encrypt currently restricts IP certificate access to allow-listed subscribers during the early access phase. Full production is scheduled to roll out by late 2025.
Source: Let’s Encrypt Rate Limits
Pros and Cons
| Criteria | Benefits | Drawbacks |
|---|---|---|
| No Domain Needed | Ideal for IP-only services | Not compatible with wildcard/domain combos |
| Valid Chain | Removes browser security alerts | Requires trusted CA, ACME setup |
| Full Automation | DevOps friendly | 6-day renewals are mandatory |
| Free of Charge | Cost-effective | No support for long-term issuance |
| In Staging Now | Available for tests | Not yet production-ready for all workflows |
DIY: Create Your Own SSL Certificate
For environments not requiring public trust, you can generate a free self-signed certificate with OpenSSL that works over an IP address.
Technical Note: Generating an IP-based certificate manually requires a Certificate Signing Request (CSR) or equivalent parameters, ensuring the IP address is declared in the SAN (Subject Alternative Name) field. Some modern browsers and systems will ignore the CN (Common Name) if the SAN is missing or incomplete.
openssl req -x509 -nodes -days 365 -newkey rsa:2048
-keyout server.key -out server.crt
-subj "/CN=203.0.113.10" -addext "subjectAltName=IP:203.0.113.10"⚠️ You’ll need to manually install this certificate in each client system or browser to avoid trust warnings.
OpenSSL directly builds this certificate inline, skipping the traditional CSR request step. Because it’s self-signed, a trusted certificate authority (CA) does not issue it. If you later decide to obtain a certificate from a CA, you’ll need to prepare a properly formatted CSR.
WordPress & IP SSL: Plugin Recommendation
In rare WordPress setups where the site is served over an IP:
- Generate an IP SSL certificate with
acme.sh - Modify
wp-config.phpto definesiteurlas the IP - Use the plugin Really Simple SSL to enforce HTTPS
⚠️ Some WordPress features may not function fully without a domain.
Comparison Table: Let’s Encrypt vs Other Free Alternatives
| Feature | Let’s Encrypt IP SSL | Self-Signed (OpenSSL) | mkcert |
| Trusted by Browsers | ✅ Yes | ❌ No | ⚠️ Dev only |
| Free of Cost | ✅ | ✅ | ✅ |
| Automation | ✅ (via ACME) | Manual | Limited |
| Certificate Lifetime | 6 days | Custom (e.g. 1 year) | Short/dev |
| Public IP Only | ✅ Required | ✅/❌ Any | Localhost |
Example: Benchmark with Shell Script
You can run a real benchmark Script using /usr/bin/time to compare performance between ACME and OpenSSL:
#!/bin/bash
echo "Benchmarking Let's Encrypt (acme.sh)..."
time acme.sh --issue --standalone -d 203.0.113.10 --server https://acme-staging-v02.api.letsencrypt.org/directory
echo "Benchmarking Certbot..."
time certbot certonly --standalone -d 203.0.113.10 --test-cert
echo "Benchmarking OpenSSL self-signed..."
time openssl req -x509 -nodes -days 365 -newkey rsa:2048
-keyout test.key -out test.crt
-subj "/CN=203.0.113.10" -addext "subjectAltName=IP:203.0.113.10"
Note:
- Replace
203.0.113.10with your actual public IP. - Root privileges and open ports 80/443 are required for ACME clients.
- Results can guide optimizations for secure, scalable deployments.
ACME vs OpenSSL — Performance Snapshot
ACME (Let’s Encrypt IP via acme.sh): ~6.4 seconds
ACME (Let’s Encrypt IP via Certbot): ~7.9 seconds
OpenSSL Self-Signed (RSA 2048): ~1.1 seconds
Tested on:
VPS OVHcloud – 2 vCPU – 4GB RAM
Ubuntu 22.04 LTS – Localhost Challenge
Tip: Self-signed is faster but not trusted by browsers. Use ACME for production and automation.
Live Benchmark Demo (Simulated)
Technical note: This benchmark runs as a simulated browser-side demo for educational purposes only. However, the displayed timing results reflect actual average measurements from real-world performance tests conducted under the following conditions:
- OVHcloud VPS — 2 vCPU, 4GB RAM
- Ubuntu 22.04 LTS with local ACME challenge
- ACME clients:
acme.shandcertbot - Execution timing measured via
/usr/bin/timeon shell scripts - OpenSSL version:
3.0.2
These metrics highlight practical performance differences between Let’s Encrypt ACME automation and self-signed OpenSSL certificates—especially relevant for DevOps pipelines and IP-only HTTPS deployments.
Click below to simulate certificate generation speed:
Waiting for input…
Cybersecurity Considerations for IP-Based SSL
Using Let’s Encrypt IP SSL certificates introduces new security and privacy considerations, especially when bypassing traditional DNS structures.
- Public Exposure via CT Logs: Every Let’s Encrypt certificate is publicly logged through Certificate Transparency. Even without a domain name, an exposed IP may leak infrastructure details.
- Passive Scanning: Tools like Shodan or Censys index IPs with SSL. Consider firewalls or geo-fencing to restrict access where applicable.
- No PTR Record ≠ Anonymity: An IP without a reverse DNS entry may still be fingerprinted through TLS metadata or service banners.
- Short Validity, Frequent Rotation: The 6-day lifetime improves security by reducing exposure, but make sure automated renewal is robust to avoid service interruption.
- Zero Trust Implications: In Zero Trust or segmented environments, use IP SSL certificates alongside mTLS or gateway-based access control.
- GDPR Compliance: IP addresses can be considered personal data under GDPR. Ensure lawful basis and appropriate controls are in place.
Best Practice: Combine IP SSL with firewall rules, strong client authentication, logging, and certificate monitoring tools to reduce the attack surface.
Technical Glossary
- ACME: Automatic Certificate Management Environment. A protocol (RFC 8555) used to automate the issuance and renewal of certificates.
- SAN: Subject Alternative Name. A field in SSL certificates allowing multiple identifiers (e.g. IPs or domains).
- FQDN: Fully Qualified Domain Name. A complete domain name including all subdomains and the root domain.
- TLS: Transport Layer Security. The protocol that provides HTTPS encryption.
- CSR: Certificate Signing Request. A block of encoded text used when applying for an SSL certificate.
- HTTP-01: ACME challenge using a file served over HTTP.
- TLS-ALPN-01: ACME challenge using a temporary TLS certificate.
- SSL: Secure Sockets Layer. A deprecated cryptographic protocol once used for securing HTTP (HTTPS). Modern HTTPS uses TLS instead of SSL, but the term “SSL” is still commonly used to refer to HTTPS certificates.
- Benchmark Script: A shell-based automation script used to compare the performance of multiple certificate issuance methods (e.g. ACME clients vs OpenSSL) by measuring execution time and resource usage.
What This Article Didn’t Cover (Yet)
We should explore these topics in greater depth, and plan to revisit them in a future update.
- Wildcard + IP Certs: Exploring mixed SANs (domain + IP) and use cases.
- IP Certificates on Shared Infrastructures: Managing certs across virtual hosts or reverse proxies.
- Commercial vs. Free IP Certificates: Durability, legal liability, SLAs, and compatibility audits.
- Integration with Appliances and Industrial Hardware: Are SASE, ZTNA, and IoT ecosystems fully compatible?
Timeline Highlights
- January 2025: Launch of short-lived certificate support (6–7 days).
- July 1st, 2025: Let’s Encrypt issues the first SSL certificate for a public IP address in staging.
- Q3–Q4 2025 (est.): Planned production rollout of IP certificate issuance.
– Trend: Domainless HTTPS adoption accelerating for containerized apps
– Pattern: ACME automation spreading to staging and test environments
– Vector: First real IP SSL use cases emerging in industrial edge networks
Strategic Wrap-up: A Game Changer for HTTPS Adoption
The ability to secure raw IPs without domains makes HTTPS easier to adopt in automation, IoT, and internal infrastructures. DevOps teams benefit from agile deployments, while local services gain privacy and security.
Want to go further?
- Build CI/CD pipelines with auto-renewing IP certs
- Deploy encrypted services in air-gapped environments
- Explore compatibility with reverse proxies and smart gateways
- Benchmark ACME certificate issuance times vs OpenSSL self-signing
- Consider legal implications of public IP exposure without DNS
Legal & Security Considerations
Deploying SSL on raw IP addresses may have implications depending on jurisdiction, network policies, or data protection regulations:
- GDPR Compliance: Ensure IP-based SSL usage complies with data protection laws. See CNIL (France) or GDPR.eu.
- Network Trust Models: Some corporate firewalls and proxies might distrust certificates not tied to domains.
- Audit & Logging: Ensure secure logging and identity verification where ACME automation is involved.
- Certificate Transparency: All Let’s Encrypt certificates are public. Don’t expose sensitive IPs without awareness.
- Best Practices: Refer to NIST Cybersecurity Framework and ENISA Guidelines for secure deployment.
- Reverse DNS leaks: Serving an IP SSL without PTR can still expose servers via Certificate Transparency logs.
- Passive scanning: Some tools index IPs with SSL enabled, which can be a privacy concern (e.g., Shodan, Censys).
- Phishing via IP URLs: Untrusted users may be misled by IP‑based links with trusted padlocks; monitor Certificate Transparency and educate users.
FAQ
Let’s Encrypt IP SSL & NFC HSM
Can I extend the 6-day certificate validity?
Let’s Encrypt enforces this policy, and users cannot modify it.
Can I issue a certificate via an NFC HSM device?
Yes. You can trigger the issuance of a Let’s Encrypt IP SSL certificate fully offline using a sovereign NFC HSM device such as <strong>PassCypher NFC HSM</strong> or <strong>DataShielder NFC HSM</strong>. These devices emulate a secure AES 128 CBC encrypted Bluetooth USB keyboard. By storing a complete ACME command (e.g. <code>~/.acme.sh/acme.sh –issue –standalone -d 203.0.113.10</code>) as a secure string (≤55 characters), the device injects it into the terminal of a Linux or Windows machine, triggering certificate generation without any manual typing or internet dependency.
→ <a href=”https://freemindtronic.com/nfc-hsm-ssl-cert-ip/” target=”_blank” rel=”noopener”>Learn more: NFC HSM triggered HTTPS certificate over IP</a>
Can I issue certificates for private IPs (192.168.x.x)?
No. Only public, globally routable IP addresses are eligible.
Is a self-signed certificate a valid alternative?
Yes, in closed or dev environments, but clients must trust it manually.
Can I use both a domain and an IP in a single cert?
Not yet supported. You must issue separate certificates.
Chrome 126+, Firefox 128+, Edge 124+, Safari 17.5+
Yes, as long as the browser trusts Let’s Encrypt’s root certificate. Modern browsers like Chrome, Firefox, Edge, and Safari are all compatible.
[accordion-item_inner title=”Can the NFC HSM trigger HTTPS certificate issuance from a web page?”]
[/accordion-item_inner]
Yes, it can. When combined with a properly designed local web interface, the NFC HSM — acting as a secure Bluetooth USB keyboard — can inject a complete ACME command directly into a focused input field. Although browsers cannot execute system commands on their own, this injected command can be immediately picked up by a local daemon or background script for execution.
This configuration enables sovereign HTTPS certificate issuance entirely offline, without DNS or manual typing. It proves especially useful for touchless deployments in isolated environments, where the web page acts as a bridge between the NFC-triggered command and the host system’s ACME client.
To ensure compatibility:
- Serve the interface over HTTPS (self-signed or IP SSL)
- Autofocus the input field targeted by the HSM
- Run a listener process that executes the received input securely
As a result, this setup empowers critical systems to deploy valid SSL certificates with minimal attack surface — and no internet dependency.
Can I extend the 6-day certificate validity?
Let’s Encrypt enforces this policy, and users cannot modify it.
Can I issue a certificate via an NFC HSM device?
Yes. You can trigger the issuance of a Let’s Encrypt IP SSL certificate fully offline using a sovereign NFC HSM device such as <strong>PassCypher NFC HSM</strong> or <strong>DataShielder NFC HSM</strong>. These devices emulate a secure AES 128 CBC encrypted Bluetooth USB keyboard. By storing a complete ACME command (e.g. <code>~/.acme.sh/acme.sh –issue –standalone -d 203.0.113.10</code>) as a secure string (≤55 characters), the device injects it into the terminal of a Linux or Windows machine, triggering certificate generation without any manual typing or internet dependency.
→ <a href=”https://freemindtronic.com/nfc-hsm-ssl-cert-ip/” target=”_blank” rel=”noopener”>Learn more: NFC HSM triggered HTTPS certificate over IP</a>
Can I issue certificates for private IPs (192.168.x.x)?
No. Only public, globally routable IP addresses are eligible.
Is a self-signed certificate a valid alternative?
Yes, in closed or dev environments, but clients must trust it manually.
Can I use both a domain and an IP in a single cert?
Not yet supported. You must issue separate certificates.
Chrome 126+, Firefox 128+, Edge 124+, Safari 17.5+
Yes, as long as the browser trusts Let’s Encrypt’s root certificate. Modern browsers like Chrome, Firefox, Edge, and Safari are all compatible.
[accordion-item_inner title=”Can the NFC HSM trigger HTTPS certificate issuance from a web page?”]
[/accordion-item_inner]
Yes, it can. When combined with a properly designed local web interface, the NFC HSM — acting as a secure Bluetooth USB keyboard — can inject a complete ACME command directly into a focused input field. Although browsers cannot execute system commands on their own, this injected command can be immediately picked up by a local daemon or background script for execution.
This configuration enables sovereign HTTPS certificate issuance entirely offline, without DNS or manual typing. It proves especially useful for touchless deployments in isolated environments, where the web page acts as a bridge between the NFC-triggered command and the host system’s ACME client.
To ensure compatibility:
- Serve the interface over HTTPS (self-signed or IP SSL)
- Autofocus the input field targeted by the HSM
- Run a listener process that executes the received input securely
As a result, this setup empowers critical systems to deploy valid SSL certificates with minimal attack surface — and no internet dependency.
Let’s Encrypt enforces this policy, and users cannot modify it.
Yes. You can trigger the issuance of a Let’s Encrypt IP SSL certificate fully offline using a sovereign NFC HSM device such as <strong>PassCypher NFC HSM</strong> or <strong>DataShielder NFC HSM</strong>. These devices emulate a secure AES 128 CBC encrypted Bluetooth USB keyboard. By storing a complete ACME command (e.g. <code>~/.acme.sh/acme.sh –issue –standalone -d 203.0.113.10</code>) as a secure string (≤55 characters), the device injects it into the terminal of a Linux or Windows machine, triggering certificate generation without any manual typing or internet dependency.
→ <a href=”https://freemindtronic.com/nfc-hsm-ssl-cert-ip/” target=”_blank” rel=”noopener”>Learn more: NFC HSM triggered HTTPS certificate over IP</a>
No. Only public, globally routable IP addresses are eligible.
Yes, in closed or dev environments, but clients must trust it manually.
Not yet supported. You must issue separate certificates.
Yes, as long as the browser trusts Let’s Encrypt’s root certificate. Modern browsers like Chrome, Firefox, Edge, and Safari are all compatible.
[accordion-item_inner title=”Can the NFC HSM trigger HTTPS certificate issuance from a web page?”]
[/accordion-item_inner]Yes, it can. When combined with a properly designed local web interface, the NFC HSM — acting as a secure Bluetooth USB keyboard — can inject a complete ACME command directly into a focused input field. Although browsers cannot execute system commands on their own, this injected command can be immediately picked up by a local daemon or background script for execution.
This configuration enables sovereign HTTPS certificate issuance entirely offline, without DNS or manual typing. It proves especially useful for touchless deployments in isolated environments, where the web page acts as a bridge between the NFC-triggered command and the host system’s ACME client.
To ensure compatibility:
- Serve the interface over HTTPS (self-signed or IP SSL)
- Autofocus the input field targeted by the HSM
- Run a listener process that executes the received input securely
As a result, this setup empowers critical systems to deploy valid SSL certificates with minimal attack surface — and no internet dependency.