FAQ Freemindtronic Technical Guides
Technical FAQ topic/h3>
Faq last revision date in this space: 03 February 2022
- Local Network configuration
- How to manually connect a phone to the web extension
- How to enable autofill in a phone
- How autofill works
- How does the NFC device work with the NFC phone?
- Automatic device authenticity check
- Protection against fake software
- Protection DDoS attack
- Invasive attack
- “Man in the middle” attack protection
- Operating system compatibility
- Encryption of EviCypher technology
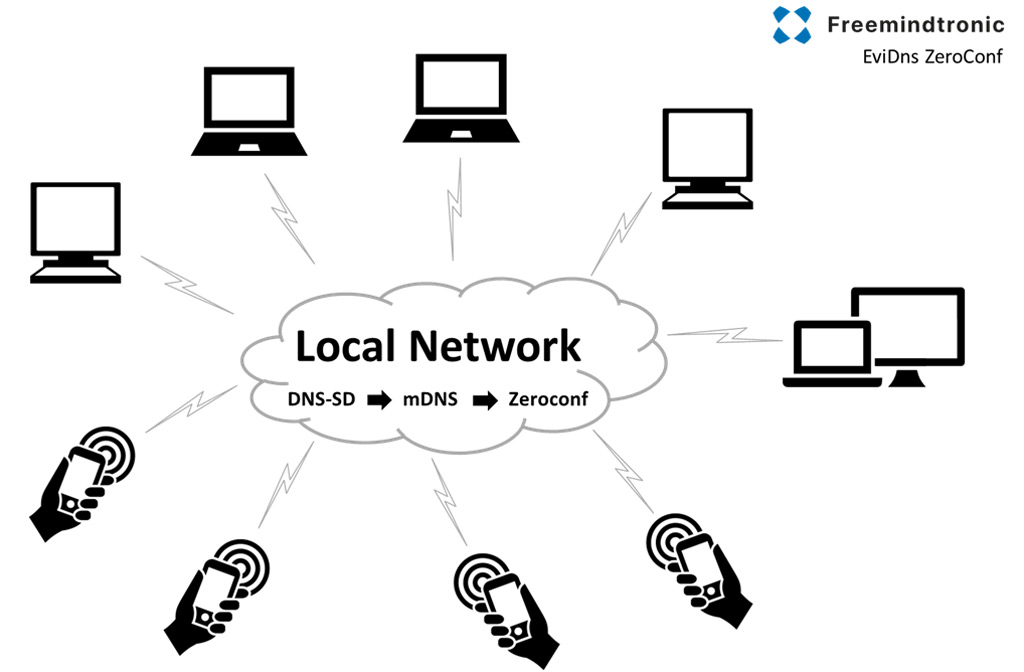
FAQ Technical: Configuring Your Local Network
Faq Technical review: 1.0.3
date: 22 April 2022
The Technical Guide will be updated to take into account technological developments related to computer systems.
The Freemindtronic App is able to communicate with a computer to share the data stored on the NFC device. More specifically, a browser extension is installed on your computer. This communication between the smartphone and the computer is local and do not pass through any remote servers.This is our choice to protect the user’s privacy and security. However, this leads to an increase of complexity for the user. Indeed, he now needs to discover the communication between two devices on the same network.
Let’s talk about service discovery. The Freemindtronic application provides an API for other devices to communicate with. Futhermore, each device on the network has a unique IP address. Communication between two devices is only possible if each device knows each other’s IP address. Two technologies are implemented in the extension for discovery of smartphone IP address with a running Freemindtronic application. The first one is called IP scan and the second, EviDNS.
IP scan is a simple way to discover compatible devices on the network. It simply puts all local IP’s of your network in a loop to fetch device’s information. This is similar to a brute force IP scan.
EviDNS is a less network intensive solution. It works by installing a specific software on your computer. This allows mDNS discovery of local services. For more information about mDNS, please visit: https://en.wikipedia.org/wiki/Multicast_DNS.
By default, the extension automaticaly chooses EviDNS if available and IP scan if not. It is possible to choose the technology wanted in the extension settings.
The EviDNS ZeroConf software developed by Freemindtronic makes possible to quickly find your terminals, such as NFC telephones connected on the same local network. It indicates the IP address and the port number of the terminal. Therefore, it offers a better user experience for Linux, IoS, Microsoft.
To learn more about Freemindtronic’s Zeroconf, click HERE.
The first one is called IP scan.
IP scan is a simple way to discover compatible devices on the network. It simply puts all local IP’s of your network in a loop to fetch device’s information. This is similar to a brute force IP scan.
Check that your router is not blocking any required port:
- 10_001: This is the port used by the Freemindtronic App. It can be modified on the app settings.
- 32728-65536: One random port used for the pairing process.
You should be aware that the operations of your local network are not guaranteed. Specific network rules and router can block requests between each device. In the case of a problem, please read through the following list of instructions until full service is restored.
- Check that your smartphone can display Freemindtronic app notification. More information on how to do it here.
- Check that Freemindtronic service is enabled and that a notification is displayed on your smartphone.
- Check that both devices are on the same network.
- Check that both devices are up to date.
- Disable / enable wifi connection on the phone
- Force stop the Android App and restart Android app
- Restart both devices.
- Try with your smartphone hotspot and tethering enabled and your computer connected to it.
If after all these actions it does not work, this means that your router is blocking the request.Try the following steps:
- Restart your router.
- Check that your router allows local devices to communicate with EviDNS. You also need to check if multicast is enabled.
- Check that your router is up to date.
- Check that your router is not blocking any required port:
- 5353: This is the port mDNS uses.
- 10_001: This is the port used by the Freemindtronic App. It can be modified on the App settings
- 32728-65536 One random port used for the pairing process.
Support Guide: Manual Phone Connection to Web Extensions
Faq Technical review: 1.1.
date: 10 February 2022
To make it simple, Freemindtronic software works on the basis of automation to enhance the user’s experience.
However, Freemindtronic solutions are dependent on computer systems and local network infrastructures.
In the case that automation does not work, you can configure it manually.
The extension is set to automatically detect compatible devices on your network. However, in some situations, your device is not detected. In that case, you can manually enter your device’s IP to proceed with the pairing process.
- Go to the extension, choose to add a new phone, a QRcode should be displayed.
- On your phone, go to the Freemindtronic App, open the tab for extension pairing and click on the “+” button. A QRcode reader should appear.
- Scan the QRcode of the extension with your phone and wait for 5 seconds.
- If nothing changed on the extension, in the meantime, you can try to manually enter the IP address of your phone.
- On the extension, click on “In case of failure” option.
- Enter your phone’s IP address and click next (Your phone’s IP should be displayed on your phone).
If your phone is within reach, the pairing continues, otherwise an error message will be displayed.
A successful pairing does not guarantee that the requests will work, as the mechanics involved are different.
If you got a network error, this means that your phone is not answering the requests. Your phone is either on another network, either the router rules prohibit communication. Try again with your smartphone hotspot feature enable and your computer connected to it.
If you got API error, this means that the connection between your smartphone and computer is established. The error could come from the phone not answering correctly. Try after a force close of the Freemindtronic application (see https://www.wikihow.tech/Force-Quit-Apps-on-Android)
Help Desk: Activating Autofill on Your Phone
Faq Technical review: 1.1.
date: 10 February 2022
The Freemindtronic application has an autofill service for Android phones. This service allows the user to autofill the fields from the NFC device where the secrets are stored encrypted. Everything is done in a secure contactless way.
Autofill works in principle with all applications used in your phone (like Facebook, Instagram, …) as well as web browsers.
To enable this feature, go to the application’s user settings and check the autofill box. A settings page should open with several choices, select the Freemindtronic application. The application becomes your default autofill software.
With Xiaomi devices running MIUI 11 or more, specific steps are required to make autofill work.
- Go to your phone settings
- Find the app info (it is were you can manage the app for example force stop the app)
- Go to Other permissions (this option is located below Application authorisation and may take a few seconds to show up)
- Enable “Display pop-up windows while running in the background”
Note: If the app you want to do autofill with was already running when you set the autofill service, it may not work with it. You need to close and reopen the app for it to take into account the new settings.
Guidance Queries: The Mechanics of Autofill
Faq Technical review:1.0.
date: 10 February 2022
This feature allows user-entered fields to be autofilled into a phone from a Freemindtronic NFC device. Freemindtronic’s application supports many different types of input fields. Remember to update Freemindtronic applications with this feature to get the latest developments in autofill and autologin.
Now click on the field to be filled in, a “search” button should appear next to it. Click on “search”. Place your NFC device under the antenna of your NFC phone. Then select the password, ID or public key of a cryptocurrency address you wish to use to fill in the field(s).
The fields will automatically fill in to authenticate you.
Understood, that the secrets automatically entered in the fields are not saved in your phone. This is the ultimate protection. The secrets are stored only in your NFC device and used on demand by your phone without backup.
Support Insights: NFC Device Integration with Phones
Faq Technical review:1.0.
date: 7 March 2022
Freemindtronic’s devices work only contactless with terminals such as Near Field Communication (NFC) enabled phones with proprietary applications designed and developed by Freemindtronic.
Freemindtronic’s NFC devices work with NFC terminals compatible with ISO/IEC 15693 and/or ISO/IEC 14443 in read & write mode.
In principle ISO/IEC 15693 NFC devices are used for solutions dedicated to safety and security of secrets. Whereas ISO/IEC 14443 NFC devices are used for other purposes.
Our NFC devices dedicated to security secrets do not use the Data Exchange Format (NDEF) to exchange data.
Data Exchange Format (NDEF) is used in some of our NFC devices to exchange non-sensitive, freely accessible data.
Freemindtronic’s NFC devices operate for life without a battery. It only uses energy harvesting via the NFC signal from the phone to operate.
Support Guide: Verifying Device Authenticity Automatically
Faq Technical review: 1.0.
date: 3 March 2022
Freemindtronic’s NFC devices have an automatic authenticity check to combat counterfeiting.
During the manufacturing of the NFC device, the tooling signs the device.
The signature is made on the basis of physical and digital parameters specific to the device. This makes it unique.
Here are the screenshot information message “Wrong signature, your device might be counterfeit”.
Keepser Application :
Freemindtronic Application :
When a Freemindtronic NFC device is presented to an NFC terminal, there is an automatic check to verify the authenticity of the device.
Indeed, each device has a unique signature. Thus, if the signature detected is not compliant, a counterfeit suspicion message is displayed.
The use of the detected counterfeit device is not allowed.
Support Insights: Safeguarding Against Counterfeit Software
Faq Technical review: 1.0.
date: 3 March 2022
The first protection is to download the application from official publishing platforms such as Google Play, App Store – Apple and Freemindtronic. The software is signed by these platforms. This guarantees the integrity of the application.
Freemindtronic software is signed. The signature is highly certified by Commodo. This is a guarantee against the risk of counterfeiting of Freemindtronic software.
Assistance Queries: DDoS Attack Mitigation Techniques
Faq Technical review: 1.0.
date: 3 March 2022
A multi-factor authentication protection system also prevents access to tools for formatting, deleting all or part of the secrets contained in the NFC device in order to perform a denial of service (DDoS).
NFC devices have a multi-factor authentication protection system. It allows to control the access to the systems, formatting, return to factory configuration, total or partial deletion of the secrets contained in the NFC device. This has the effect of preventing a non-invasive denial of service attack.
Help Desk: Defense Against Invasive Attacks
Faq Technical review: 1.0.
date: 3 March 2022
The secrets contained in the non-volatile memory of Freemindtronic NFC devices are encrypted via segmented keys of physical and digital origin.
Each secret can have several cumulative trust criteria that also serve as individual encryption keys. Moreover, some criteria can be randomly generated. For example, you can use the barcode of a book to protect the secret. In short, such a level of complexity makes it difficult to carry out an intrusive attack.
Guidance Queries: Protection Against “Man-in-the-Middle” Attacks
Faq Technical review: 1.0.
date: 3 March 2022
Protection against man-in-the-middle attacks is also provided throughout the entire value chain from design, manufacturing to the end user and final use of the solution via a phone and/or a computer.
The tooling for manufacturing the devices is not connected. Device pairing keys are automatically destroyed.
Each product is signed by the tooling with a secure private key.
All communication protocols are encrypted. This includes NFC, Wi-Fi, Bluetooth, SMS as well as webcam and image communications.
Several encryption systems are used to effectively combat man-in-the-middle attacks.
The data exchanged via the NFC signal between the NFC device and the NFC terminal (phone) is encrypted.
Thus, if the NFC signal is listened to by a man-in-the-middle attack, it is encrypted.
Following the pairing of the phone to a web browser extension, a master key is automatically created and encrypted in the phone. A visual integrity check code is also implemented during pairing between the terminal and the extension.
If the code is different, the user refuses the creation of the master pairing key. Thus, the man-in-the-middle attack is also protected when the master key is created.
Then, at each transfer request with the web extension to use a secret contained in the NFC device, a unique encryption key will be automatically generated to encrypt local, wifi, wired and Bluetooth network communications.
Freemindtronic NFC devices are not physically connected. It is therefore not possible to perform directly remote repudiation, formatting, copying, cloning, sharing actions. This protection makes it physically impossible to carry out a remote attack and a man-in-the-middle attack.
However, it is possible via the application to perform a number of actions such as repudiating secrets, resetting to factory configuration and blocking use. This type of service is tailor-made to the specifications of Freemindtronic customers.
Support Queries: Extension Compatibility with Web Browsers
Faq technical review: 1.0.
date: 9 March 2022
The web extensions developed by Freemindtronic are made to work with Chromium based browsers as well as the Mozilla Firefox based web browser.
Non-exhaustive list of web browsers based on Chromium and Mozilla Firefox.
- Mozilla
- Chromium
- Google Chrome
- Microsoft Edge
- Opera
- Vivaldi
- Brave
- Blisk
- Colibri
- Epic Browser
- Iron Browser
- SRWare Iron
- Ungoogled Chromium (S)
- Avast Secure Browser (0)
- Amazon Silk (0)
- Yandex Browser (0)
- Qihoo 360 Secure Browser (0)
- Torch Browser (0)
- Comodo Dragon (0)
- Aspen (Avast) (0)
- Coc Coc (1)
- Falkon (1)
- Xvast (1)
- Polarity (1)
- TheWorld Chrome (1)
- Naver Whale (1)
- Kinza (1)
- Iridium (1)
- Tungsten (1)
- Ghost Browser (1)
- Superbird (1)
- Lulumi (1)
- Chedot (1)
- Orbitum (1)
- Cent Browser (1)
- RockMelt (2)
- Maelstrom (2)
- Slim Browser (2)
- Aviator (2)
- Flock (2)
- Dartium (2)
- Beamrise (2)
- Sentria (2)
- Titan Browser (2)
- Sleipnir (2)
- WebFreer (2)
- Redcore (2)
- Kiwi Browser (3)
- Adventurer (3)
- Slimjet (3)
- UR (3)
- Avira Scout (3)
- Cent Browser (3)
- Ecosia (3)
- Chromodo (3)
- Lilo Browser (3)
(S) Browser based on a specific branch of Chromium
(0) Service provider specific Chromium based browser
(1) Browser based on Chromium may be known
(2) Very old Chromium-based browser
(3) Chromium-based browser
Support Guide: Operating System Compatibility
Faq Technical review: 1.0.
date: 9 March 2022
Freemindtronic’s web browser extensions are in principle compatible with all operating systems. See the list below.
Below is a non-exhaustive list of computer operating systems that allow the installation of web browsers based on Chromium and Mozilla Firefox.
- MS-Windows
- Linux
- Ubuntu
- Mac OS
- Fedora
- Solaris
- Free BSD
- Chrome OS
- CentOS
- Debian
- Deepin
- Fedora
- Red Star OS
- Syllable
FAQ Technical: Encryption of EviCypher technology
Faq Technical review: 1.0.
date: 24 March 2022
EviCypher technology uses AES with 256-bit keys for symmetric encryption and the 25519 curve (X25519) for asymmetric encryption.